Abstract
Spectrum sensing in a cognitive radio network involves detecting when a primary user vacates their licensed spectrum, to enable secondary users to broadcast on the same band. Accurately sensing the absence of the primary user ensures maximum utilization of the licensed spectrum and is fundamental to building effective cognitive radio networks. In this paper, we address the issues of enhancing sensing gain, average throughput, energy consumption, and network lifetime in a cognitive radio-based Internet of things (CR-IoT) network using the non-sequential approach. As a solution, we propose a Dempster–Shafer theory-based throughput analysis of an energy-efficient spectrum sensing scheme for a heterogeneous CR-IoT network using the sequential approach, which utilizes firstly the signal-to-noise ratio (SNR) to evaluate the degree of reliability and secondly the time slot of reporting to merge as a flexible time slot of sensing to more efficiently assess spectrum sensing. Before a global decision is made on the basis of both the soft decision fusion rule like the Dempster–Shafer theory and hard decision fusion rule like the “n-out-of-k” rule at the fusion center, a flexible time slot of sensing is added to adjust its measuring result. Using the proposed Dempster–Shafer theory, evidence is aggregated during the time slot of reporting and then a global decision is made at the fusion center. In addition, the throughput of the proposed scheme using the sequential approach is analyzed based on both the soft decision fusion rule and hard decision fusion rule. Simulation results indicate that the new approach improves primary user sensing accuracy by \(13\%\) over previous approaches, while concurrently increasing detection probability and decreasing false alarm probability. It also improves overall throughput, reduces energy consumption, prolongs expected lifetime, and reduces global error probability compared to the previous approaches under any condition [part of this paper was presented at the EuCAP2018 conference (Md. Sipon Miah et al. 2018)].
Similar content being viewed by others
1 Introduction
1.1 Motivation
The Internet of things (IoT) is a new machine-to-machine (M2M) communication paradigm that includes a variety of domains, protocols, and applications, which allow devices to communicate with each other using different communication technologies without human intervention [1]. The Internet of things will have a strong impact on many aspects of our daily life including assisted living, manufacturing, intelligent transportation of people/materials, e-health, and smart cities [2]. There are still many problems for applications on Internet of things including (i) the problem of interference between different IoT devices in heterogeneous networks, (ii) spectrum scarcity, i.e., the efficient allocation of spectrum bands to all Internet of things devices, and (iii) bandwidth requirements and energy constraints, particularly for multimedia applications [3]. To resolve the above-mentioned problems, research [4,5,6] is shifting towards cognitive radio networks (CRNs), presenting them as a potential solution for IoT applications. A paradigm shift of the cognitive radio-based Internet of things network, called CR-IoT network, has already been introduced. As a result, some of the potential applications of IoT that can benefit from CRNs are health care, social activities, environment-related applications, in-home applications, smart grid, smart cities and Internet of vehicles.
Cognitive radio is a vital technology that allows dynamic spectrum access in a CR-IoT network. It can dramatically enhance spectrum utilization as unused sections of the spectrum can be used by CR-IoT users [7]. A prerequisite of the CR-IoT user access is the prevention of unwanted interference that impacts on the primary users. If the primary user does not use it, the CR-IoT user automatically accesses the idle licensed spectrum of the primary network. In addition, when the primary user accesses it, the CR-IoT users instantly relinquish their momentarily allotted licensed spectrum.
Spectrum sensing plays a very important role in a CR-IoT network. In spectrum sensing, CR-IoT users detect the primary user spectrum occupancy status and identify spectrum holes in the licensed channels that can be used to communicate themselves. There are a variety of spectrum sensing methods, like matched filter detection [8], cyclostationary detection [9], energy detection [10], and eigenvalue detection [11, 12]. When the transmitting signal is recognized, matched filter detection is known as the best method for the detection of primary users. The main benefit of matched filter detection is that effective spectrum sensing requires a short period of time compared to other methods. However, it needs full knowledge of the primary user signal features, including operating frequency, bandwidth, modulation type as well as order, packet layout, and pulse shaping. Cyclostationary detection offers excellent performance, yet needs knowledge of the cyclic frequencies of the primary user and takes a long time to accomplish sensing. The energy detection technique is an interesting alternative method with a simple implementation and low computational complexity. However, it is highly susceptible to noise power uncertainty and is unable to distinguish between signal and noise. Its main drawback is that the signal intensity obtained at a particular geographic position can be severely reduced due to multipath fading and the shadow effect [13, 14]. On the other hand, the eigenvalue detection technique is a widely used method, because it can perform well in a noise uncertain environment.
There are two types of CR-IoT networks [15,16,17,18]: (i) homogeneous CR-IoT networks and (ii) heterogeneous CR-IoT networks. In homogeneous CR-IoT networks, all CR-IoT users have the same node capabilities, including equal antennae numbers, sampling rate, and a similar signal-to-noise ratio (SNR), which may be very minimal for detection purposes. In heterogeneous CR-IoT networks, each CR-IoT user may have different reporting errors and sensing qualities for different primary users. Cooperative spectrum sensing is more difficult because it requires a high SNR for each CR-IoT user. It is also faced by other difficulties including standardization, storage format, methods of processing, synchronization, and resolution of measurement.
With cooperative spectrum sensing, each CR-IoT user conducts local sensing independently and then sends the sensing results to the corresponding fusion center via a (noise-free or non-noise-free) control channel. The fusion center combines all sensing findings and makes a final global decision based on fusion rules [19,20,21,22]. The fusion rule can be categorized either as hard decision fusion rule or as soft decision fusion rule. Each CR-IoT user makes a one-bit decision on the existence of the primary user in a hard decision fusion rule (using the “n-out-of-k” rule, i.e., “OR” rule, “AND” rule, “M” rule [23], and “Optimal” rule [24]) and sends this decision to the fusion center, therefore needing only limited bandwidth. The sensing gain of the hard decision fusion rule is lower than that of the soft decision fusion rule, where each CR-IoT user sends the entire sensing result to the fusion center, making a decision using maximal ratio combining, square law combining, selection combining, and Dempster–Shafer theory. While it delivers better sensing gain than the hard fusion rule, the control channel needs wide bandwidth.
However, a CR-IoT user does not separate the primary signal from the noise signal in poor SNR conditions. In [25], the authors analyze a scheme using the “Dempster–Shafer theory I” to combine all decisions made by CR-IoT users with their self-assessed credibility of each decision. Moreover, authors introduce an approach in distributed CR-IoT networks using the more suitable basic probability assignment function and a reliability source analysis based on “Dempster–Shafer theory II” [26]. Nevertheless, it cannot enhance sensing gain for a homogeneous CR-IoT network. The same sensing gain was achieved here by both Qihang et al. [25] and Nhan et al [26]. Miah et al. [27] proposed an improved cooperative sensing gain for hybrid CRNs, where the detection performance is analyzed using the reporting framework via the soft decision fusion rule (i.e., the Dempster–Shafer theory). Here, the average throughput, energy consumption, network lifetime, and global error probability were not analyzed.
1.2 Contributions
The following major contributions are presented in this paper:
We propose a novel algorithm for heterogeneous CR-IoT networks under the sequential approach, in which each CR-IoT user uses a flexible sensing time slot by utilizing the reporting framework efficiently to sense the primary signal more accurately than the conventional scheme using a non-sequential approach.
We experimentally analyze the sensing gain at the fusion center with a flexible sensing time slot using both the soft decision fusion rule (i.e., the conventional Dempster–Shafer theory) and the hard decision fusion rule (i.e., the “n-out-of-k” rule); we demonstrate that the proposed Dempster–Shafer theory enhances the sensing gain for heterogeneous CR-IoT networks using the sequential approach compared to both the conventional Dempster–Shafer theory and the “n-out-of-k” rule.
The average throughput of all CR-IoT users and the primary user is analyzed considering the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks, hereby distinguishing between both the non-sequential approach and the sequential approach. Moreover, the energy consumption and the expected lifetime are analyzed where the expected lifetime is inversely proportional to the energy consumption in the proposed scheme.
Finally, the theoretical analysis has been confirmed by simulations. Overall, it will be shown that the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks using both a non-sequential and sequential approach obtains a better sensing gain, an enhanced average throughput, a more efficient energy consumption, a prolonged expected lifetime, and a lower global error probability compared to both the conventional Dempster–Shafer theory and “n-out-of-k” rule.
1.3 Organization
The rest of this paper is structured as follows: In the “Related works” section, the general motivation and background of this paper are outlined. “System model” explains the proposed scheme (consisting of the primary network and the CR-IoT network). “Energy detection technique” explains how the CR-IoT user measures its particular estimated energy from the primary user signal. “The conventional scheme using the non-sequential approach” outlines how each CR-IoT user underutilizes the reporting framework. In the “The proposed scheme based on the sequential approach” section, it is shown how each CR-IoT user utilizes the reporting framework. In the “Simulation results and discussion” section, the simulation metrics of the proposed scheme and comparisons are presented. Final remarks are addressed in “Conclusion and future work.” The mathematical notations used in this paper are briefly described in Table 1 in order to obtain the paper more readable.
2 Related work
Spectrum sensing can broadly be broken up into two groups, noncooperative spectrum sensing and cooperative spectrum sensing using non-sequential and sequential approaches. Thus, we examine the literature from these two perspectives:
In noncooperative spectrum sensing, the analysis of spectrum sensing in a cognitive radio network using a non-sequential approach is presented in [28,29,30]. These papers show different aspects of the problem of spectrum sensing studied from the context of cognitive radio. The authors in [30] propose a “Fast” and “Optimal” sensing approach with power allocation using a non-sequential approach.
An analysis of cooperative spectrum sensing using a non-sequential approach in a cognitive radio network is presented in [31, 32]. Cooperative spectrum sensing of a single sensing node can concurrently decrease both the probability of false alarm and the miss detection. It has been shown that fading, shadowing, uncertainty, and the hidden terminal problem affect the spectrum sensing accuracy [13, 14, 33]. In [34], the authors proposed to identify the portions of the spectrum that are unused by primary user systems and other CR systems, called existing user (EU) systems altogether, with the emphasis on conquering the challenge imposed by multipath fading channel where, in the first step, the maximum likelihood (ML) estimates of the frequency bands of EU systems were calculated; and in the second step, detection was performed at each suspected band to decide whether an EU system is truly in operation.
The relay-based spectrum sensing was studied in [35] to mitigate the fading problem. The benefits of cooperative spectrum sensing can be compromised due to noisy reporting channels, which are discussed in [36,37,38]. To solve these problems, several approaches have been proposed, such as cluster-based cooperative spectrum sensing and sequential cooperative spectrum sensing [39, 40]. Lee et al. [39] proposed the opportunistic non-orthogonal multiple access-based cooperative relaying network where if the transmit SNR is high and the average channel power of the sender to receiver link is low. However, the proposed method requires channel state information response or alternative response schemes with lower overhead and complexity. In [40], the authors analyzed a cluster-based sequential cooperative spectrum sensing scheme for cognitive radio networks to drastically reduce the number of direct reports to the fusion center from cognitive radio users, while also maintaining the same sensing gain compared to the conventional cooperative spectrum sensing scheme.
For distributed models, various fusion rules such as the “AND” rule, “OR” rule, and “M” rule [41] were outlined. Nguyen-Thanh et al. [41] showed that the “M” rule only works well when all CR-IoT users have identical thresholds. By combining results with a counting rule [42], an optimal fusion rule has been achieved. However, when the channel environment changes, the approach needs some time to converge.
In [43], a cluster-based cooperative spectrum sensing approach was introduced to attain a suitable assignment strategy with the aim of optimizing the average throughput of the cognitive radio network. Nevertheless, the noise-free reporting channels were considered. In addition, the average throughput was still not evaluated for the utilization reporting framework. Eryight et al. [44] tried to minimize total sensing and reporting energy consumption using the “OR” rule in an error-free cooperation environment. However, the soft decision fusion rule is already pointed out to be the best fusion rule in the context of additional SNR requirement which achieves optimal performance. Zhang et al. [45] used discrete convexity tools to maximize the achievable throughput in both homogeneous and heterogeneous scenarios. Yu [46, 47] introduced optimum channel sensing to optimize the sum rate in cognitive radio networks with cooperative secondary users evaluating the cognitive radio capacity. In addition, some interesting characteristics have been observed including asymptotic results. Nevertheless, the average throughput in the heterogeneous CR-IoT network was not evaluated for the utilization reporting framework. In [48], an efficient terminal assignment strategy for coordinated spectrum sensing was to determine the optimum number of cooperative sensing cognitive terminals that is provided to optimize the proposed metric. In [49], the authors proposed a new time-division energy-efficient (TDEE) sensing scheme in which the sensing period is divided into an optimal number of time slots and each secondary user (SU) is assigned to detect a different channel in one time slot. In [50], the authors proposed to investigate the joint impact of sensing probability, access probability, and energy queue capacity on the maximum achievable throughput in a multi-user CR network incorporating energy harvesting. In [51], the authors proposed a scheme which utilizes both the multi-user selection diversity and the inter-user transmission error comparison jointly where to reduce the transmission error of sending messages over fading channels. However, above papers [48,49,50,51] were not evaluated for the utilization reporting framework.
In [52], the authors presented optimizing the sum rate in amplify and forward-cognitive radio networks using the sequential method and “n-out-of-k” rule with the throughput of cognitive radio networks being analyzed. However, the average throughput was not analyzed using the soft decision fusion rule. In the cluster-based cognitive radio relay network [53], the authors introduced an improved sum rate using the sequential method to evaluate the sum rate. Nevertheless, the soft decision fusion rule did not evaluate the average throughput. In addition, due to the limited reporting control channel, the sequential approach was not evaluated because that would be a more desirable approach. In [54], an energy-efficient cooperative spectrum sensing scheme based on spatial correlation for cognitive Internet of things (CIoT) which mitigates the communication overhead and ensures sufficient sensing accuracy, the CR-based devices (CRDs) can be grouped into several clusters. However, the reporting time for the CRDs and the cluster heads are rigid frame structure, i.e., using the non-sequential approach.
To the best of our knowledge considering all the previous studies, no previous work has been published which improves sensing accuracy, enhances throughput, reduces energy consumption, prolongs expected lifetime, and reduces global error probability.
3 System model
We will model the primary network as well as the CR-IoT network in this section. In addition, the main assumptions are also presented.
3.1 Modeling of the primary network
A two-state Markov chain describes the modeling of the primary user’s activities in the licensed channel, as shown in Fig. 1. In the “ON” state, the licensed channel is presumed to be used by a primary user, while the licensed channel is free in the “OFF” state. The primary network consists of a transmitter and a receiver, where the transmitter sends data to its receiver in the allocated licensed channel. We consider that the primary user uses time division multiplexing access.
The primary network time slot structure [55]
3.2 Modeling of the CR-IoT network
A heterogeneous CR-IoT network consists of M users, i.e., transmitters and receivers, and a fusion center. In this model, all CR-IoT users are distributed in a \(heterogeneous\) region called a heterogeneous CR-IoT network in which there is a large distance between CR-IoT users as shown in Fig. 2 and every CR-IoT user has a different SNR sensing channel. All CR-IoT users use energy detectors to identify the primary user activities during the flexible sensing time slot due to utilizing the reporting framework in the sequential approach and then forwarding the local test statistics to its corresponding fusion center (FC) during the fixed reporting time slot. For simplicity, the reporting channel is assumed to be error-free. Finally, the global decision is conducted at the FC, which uses certain criteria to fuse the received decision results from all CR-IoT users. Also, we assume that the reporting links between the CR-IoT users and the FC will be perfect and the data fusion (hard fusion) rules are implemented.
In the primary user and CR-IoT user link, each CR-IoT user performs spectrum sensing during the sensing time slot to identify the primary user status on the licensed channel. The problem of spectrum sensing can be derived using a testing problem of binary hypothesis as follows:
where \(H_0\) and \(H_1\) indicate the primary user’s absence and presence in the desired licensed channel, respectively.
A binary hypothesis testing question can be used to formulate the received signal of the \(j{\rm th}\) CR-IoT user as follows:
where \(j=1,2,3, \ldots , M\), \(t=1,2,3, \ldots , N_{x,j}\); here, M is the total number of CR-IoT users, \(N_{x,j}\) is the total number of samples of the \(j{\rm th}\) CR-IoT user’s received signal that is specified as \(N_{x,j}=2\tau ^j_sf_s\), \(\tau ^j_s\) is the sensing duration of the \(j{\rm th}\) CR-IoT user, and \(f_s\) is the sampling frequency; \(x\left( t\right)\) is the signal transmitted from the primary user, \(h_j\left( t\right)\) is the channel gain between the \(j{\rm th}\) CR-IoT user and the primary user which is assumed that the channel is static during each sensing period, \(n_j\left( t\right)\) is the additive white Gaussian noise, and \(y_j\left( t\right)\) is the received signal of the \(j{\rm th}\) CR-IoT user. A common spectrum allocation scheme is shared by all CR-IoT users and the primary user.
4 The energy detection technique
The most popular sensing method employed to identify the primary user is the energy detection technique. This is due to its ease of implementation, compatibility with any type of signal, and low computational complexity. We assume that each CR-IoT user transmitter (\(CR-IoT_{tx}\)) senses the primary user signal using the energy detection technique. Fig. 3 demonstrates the structure of the channel sensing process at the \(CR-IoT_{tx}\) using the technique of energy detection.
With the proposed scheme, the sensing result, \(y_{E_{j}}\) obtained by the \(j{\rm th}\) CR-IoT user transmitter, is the signal power of a specific frequency in the time domain. A band-pass filter is applied to the received signal; then, this filter’s output is converted by an analog-to-digital converter (ADC), before being averaged and squared using the energy detection technique to estimate its own calculated energy as provided by
where \(y_j\left( t\right)\) is the \(t{\rm th}\) sample of an obtained signal of the \(j{\rm th}\) CR-IoT user and \(y_{E_j}\) is the received energy signal at the \(j{\rm th}\) CR-IoT user .
When \({N_{x,j}}\) is large, the probability distribution function (PDF) of \(y_{E_{j}}\) can be approximated with mean \(\left( \mu _{0j},\mu _{1j}\right)\) and variance \(\left( \sigma _{0j}^2, \sigma _{1j}^2\right)\) as a Gaussian random variable (Gaussian distribution) using central limit theorem (CLT) under both hypotheses \(H_0\) and \(H_1\), respectively as follows [56, 57]:
where \(\gamma _j\) is the SNR of the primary signal at the \(j{\rm th}\) CR-IoT user.
5 The conventional scheme using the non-sequential approach
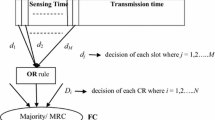
In the non-sequential approach, each CR-IoT user has obtained both a fixed/rigid time slot of sensing and a time slot of reporting. The time slots of sensing and reporting are not mergeable as shown in Fig. 4.
Proposition 1
Using the non-sequential approach, all CR-IoT users obtain a fixed time slot of sensing to detect the primary user because of the underutilized time slot of reporting framework as follows:
Proof
Please see the “Appendix.” \(\square\)
5.1 The hard decision fusion rule
The probability of detection, \(p_{d,j},\) is the probability that when the primary user is actually available on the licensed channel, the \(j{\rm th}\) CR-IoT user correctly proclaims that the primary user is active on the licensed channel. The probability of false alarm, \(p_{f,j},\) is the probability that the \(j{\rm th}\) CR-IoT user incorrectly proclaims that the primary user is active on the licensed channel, when the primary user is really absent. In a hard decision fusion rule, we consider that the overall probability of detection, \(p_{d,j}^{ED}(\tau _s^j(NSA))=Pr\left( H_1|H_1\right)\), and the probability of false alarm, \(p_{f,j}^{ED}(\tau _s^j(NSA))=Pr\left( H_1|H_0\right)\), of the \(j{\rm th}\) CR-IoT user using the non-sequential approach can be written as follows:
and
where \(\lambda _j\) denotes a local decision threshold of the \(j{\rm th}\) CR-IoT user as well as Q(.) denotes the right-tail probability of a normalized Gaussian distribution that is mathematically expressed as \(Q(x)=\frac{1}{\sqrt{2\pi }}\int _x^\infty exp(-\frac{t^2}{2})\mathrm{d}t\).
At the fusion center, all local decisions collected would be combined to make a global decision on the absence or presence of the primary user signal using the “n-out-of-k” rule test as follows:
and
where \(\lambda _{ED}\) is the global decision threshold of the “n-out-of-k” rule.
5.2 The soft decision fusion rule
In the soft decision fusion rule, all CR-IoT users perform local sensing independently during the time slot of sensing and then sent their sensing results to the fusion center during the reporting time slot. Based on the conventional Dempster–Shafer theory, the fusion center is made a global decision. In the conventional Dempster–Shafer theory using a non-sequential approach, each CR-IoT user will calculate the credibility of their self-assessed decision which is approximately equal to the conventional elementary assignment of probability for both hypotheses. We calculate an elementary assignment of probability as a cumulative density function based on the non-flexible time slot of sensing, \(\tau _s\left( NSA\right)\) as follows:
where \(m_j\left( H_0\right)\) and \(m_j\left( H_1\right)\) denote an elementary assignment of probability of the \(j{\rm th}\) CR-IoT user under \(H_0\) and \(H_1\), respectively.
5.3 Global decision
At the fusion center using the non-sequential approach, all the traditional basic probability calculations of the \(j{\rm th}\) CR-IoT user for both hypotheses will be combined to make a global decision on the absence or presence of the primary user signal based on the conventional Dempster–Shafer theory as follows:
and
where A denotes the discernment frame (defined as \(\left[ H_0, H_1, \Omega \right]\), any hypothesis, \(\Omega\) is valid that is defined as \({\overline{m}}\left( \Omega \right) =1-{\overline{m}}\left( H_1\right) -{\overline{m}}\left( H_0\right)\)) as well as \(\oplus\) refers to the orthogonal sum of \(\omega _1{m}_1\), \(\omega _2{m}_2, \ldots , \omega _M{m}_M\), which is both commutative and associative. The weight of the \(j{\rm th}\) CR-IoT user \(\omega _j\) is a function of the distance between the two mean values of both hypotheses, \(D_j\), which is defined as \(g(D_j)\) \(\omega _j =g\left( D_j\right) =\frac{\gamma _j}{max\left( \gamma _j\right) }\).
The fusion center collects the final combination result \({\overline{m}}\left( H_{0}\right)\) and \({\overline{m}}\left( H_{1}\right)\) from each CR-IoT user, and then it is made a global decision \((gd_{f}(\tau _s(NSA))/gd_{d}(\tau _s(NSA)))\) as follows:
and
Now, we can calculate the decision statistics using Algorithm 1. Here, each CR-IoT user of a heterogeneous CR-IoT network obtains a fixed sensing time slot \(\tau _s^j(NSA)\) (see line 4) for a single CR-IoT user and \(\tau _s^j(NSA)\) (see line 6) for a cooperative CR-IoT user. Then, the algorithm computes the weight of the \(j{\rm th}\) CR-IoT user for a heterogeneous CR-IoT network (see line 8). After that, it computes the \(j{\rm th}\) local decisions \(p_{d,j}^{ED}(\tau _s(NSA))\) and \(p_{f,j}^{ED}(\tau _s(NSA))\) based on the hard decision fusion rule (see lines 10 and 11), whereas it computes the basic probability assignment for both hypotheses (see lines 13 and 14) using the conventional Dempster–Shafer theory II. Finally, it computes the global detection gain \(gd_{d}^{ED}(\tau _s(NSA))\) and \(gd_{f}^{ED}(\tau _s(NSA))\) based on the hard decision fusion rule (see lines 19 and 20) and \(gd_f(\tau _s(NSA))/gd_d(\tau _s(NSA))\) based on the conventional Dempster–Shafer theory II (see lines 21 and 22).

6 The proposed scheme based on the sequential approach
The proposed Dempster–Shafer theory-based spectrum sensing in a heterogeneous CR-IoT network using the sequential approach is an impressive solution to the issue of spectrum shortages; it merges a time slot of reporting in a reporting framework which is shown in Fig. 5.
Proposition 2
In the sequential approach, CR-IoT users get a flexible time slot of sensing because the remainder of the CR-IoT user reporting time slots merging to the flexible time slot of sensing defined as follows:
Proof
Please see the “Appendix.” \(\square\)
In the sensing phase, the fusion center transmits a “sensing request message” across all CR-IoT users of the heterogeneous CR-IoT networks. After receiving the “sensing request message” from the fusion center, all CR-IoT users stay quiet as well as to detect the primary user signal during the flexible time slot of sensing using the energy detection technique based on Proposition 2. Once a “local decision” is made, each \(j{\rm th}\) CR-IoT user must send their “local decision” during the time slot of reporting to the corresponding fusion center, who collects all “local decisions” as well as then makes a “global decision” of the hypotheses like \(H_1\) or \(H_0\). Finally, the fusion center transmits the “global decision” across all CR-IoT users. After receiving the “global decision” from the fusion center, the CR-IoT users either commence or cease transmission, depending on the decision.
6.1 The hard decision fusion rule
In the proposed scheme using the sequential approach with the hard decision fusion rule, we consider that the overall probability of detection, \(p_{d,j}^{ED}\left( \tau _s^j(SA)\right) =Pr\left( H_1|H_1\right)\), and the probability of false alarm, \(p_{f,j}^{ED}\left( \tau _s^j(SA)\right) =Pr\left( H_1|H_0\right)\), of the \(j{\rm th}\) CR-IoT user can be written as follows:
and
At the fusion center, all local decisions collected would be combined to make a global decision on the absence or presence of the primary user signal using the hard decision fusion rule test as follows:
and
where \(\lambda _{ED}\) is the global decision threshold of the “n-out-of-k” rule.
6.2 The soft decision fusion rule
In the soft decision fusion rule, all CR-IoT users perform local sensing independently during the time slot of sensing as well as then send their sensing results to the fusion center during the time slot of reporting. Based on the proposed Dempster–Shafer theory, the fusion center is made a global decision. In the proposed Dempster–Shafer theory using the sequential approach, each CR-IoT user will calculate the credibility of their self-assessed decision that is approximately equal to the conventional elementary assignment of probability for both hypotheses. We calculate an elementary assignment of probability as a cumulative density function based on the flexible time slot of sensing, \(\tau _s^j\left( SA\right)\), as follows:
where \(m_j^{\prime }\left( H_0\right)\) and \(m_j^{\prime }\left( H_1\right)\) denote an elementary assignment of probability of the \(j{\rm th}\) CR-IoT under \(H_0\) and \(H_1\), respectively.
Proposition 3
In the proposed Dempster–Shafer theory for a heterogeneous CR-IoT network using the sequential approach, the weight of the \(j{\rm th}\) CR-IoT user \(\omega _j^{\prime }\) is a function of the distance between the two hypothesis mean values, \(D_j\), which is defined as \(g(D_j)\) and a function of attaining the flexible time slot of sensing, \(\tau _s^j\left( SA\right)\), that is defined as \(f\left( \tau _s^j\left( SA\right) \right)\) as follows:
Proof
Please see the “Appendix.” \(\square\)
Proposition 4
In the proposed Dempster–Shafer theory for a homogeneous CR-IoT network, the weight of the \(j{\rm th}\) CR-IoT user, \(\omega _j^{\prime }\), depends on only \(f\left( \tau _s^j\left( SA\right) \right)\) that is defined as follows:
Proof
Please see the “Appendix.” \(\square\)
Proposition 5
In the proposed Dempster–Shafer theory for a heterogeneous CR-IoT network, we obtain an improved self-assessed elementary assignment of probability of both hypotheses of the \(j{\rm th}\) CR-IoT user compared to the normal basic probability of assignment which is defined as follows:
6.3 The global decision
The proposed Dempster–Shafer theory has gained a great deal of attention in application areas like intelligence analysis, target identification, wireless sensor networks to name but a few. It achieves significant sensing performance improvements because of its ability to model uncertainty with regards to the propositions, that is a great approach for decision-making in a heterogeneous CR-IoT network.
At the fusion center, all the improved self-assessed elementary assignments of probability calculations of the \(j{\rm th}\) CR-IoT user for both hypotheses will be combined to make a global decision on the absence or presence of the primary user signal as follows:
and
where A denotes the discernment frame (defined as \(\left[ H_0, H_1, \Omega \right]\), any hypothesis, \(\Omega\) is valid that is defined as \(m^{\prime \prime }\left( \Omega \right) =1-m^{\prime \prime }\left( H_1\right) -m^{\prime \prime }\left( H_0\right)\)) as well as \(\oplus\) refers to the orthogonal sum of \(\omega _1^{\prime }{m}_1^{\prime }\), \(\omega _2^{\prime }{m}_2^{\prime }, \ldots\), and \(\omega _M^{\prime }{m}_M^{\prime }\), that is both associative and commutative.
The fusion center collects the final combination result \(m^{\prime \prime }\left( H_0\right)\) as well as \(m^{\prime \prime }\left( H_1\right)\) from each CR-IoT user, and then it is made a global decision (\(gd_f(\tau _s(SA))/gd_d(\tau _s(SA))\)) as follows:
and
6.4 Throughput analysis
In each transmission slot, if a \(CR-IoT_{tx}\) user do not identify the primary user signal, they decide that the channel is free and they transmit data to their own receiver; otherwise, they wait till the channel is available for transmission, that is scheduled round-robin. If the primary user is absent and this absence is perfectly detected by the CR-IoT user, the CR-IoT user accesses the licensed channel of the primary user with probability \((1-gd_{f}(\tau _s(SA)))\) as well as does not access the licensed channel of the primary user with the probability \(gd_d(\tau _s(SA))\). The successful (round-robin) transmission of data in a time slot relies on two things: (i) a free licensed channel of the primary user that is sensed accurately by the CR-IoT users, as well as (ii) error-free data are transmitted. In such a case, the average throughput of all CR-IoT users and the primary user is calculated using a sequential approach as follows [58]:
and
where \(c_0\) refers to the transmitter \((CR-IoT_{tx})\)–receiver \((CR-IoT_{rx})\) channel capacity of the link when the primary user is not present, \(c_1\) denotes the transmitter \((CR-IoT_{tx})\)–receiver \((CR-IoT_{rx})\) channel capacity of the link when the primary user is not absent, T is the length of a time slot, and \(p_1\) and \(p_0\) are the presence and absence probabilities of the primary user signal, respectively.
When the \(CR-IoT_{tx}\) transmits data under \(H_0\), the \(CR-IoT_{tx}\) and \(CR-IoT_{rx}\) link has a capacity \(c_0\) as follows:
where \(SNR_{CR-IoT}\) is the SNR in the \(CR-IoT_{tx}\)–\(CR-IoT_{rx}\) link.
When the \(CR-IoT_{rx}\) receives data under \(H_1\), the \(CR-IoT_{rx}\) receives the primary user signal as noise. In this case, the \(CR-IoT_{tx}\) and \(CR-IoT_{rx}\) link has a capacity \(c_1\) as follows:
where \(SNR_{PU}\) is the SNR in the \(PU_{tx}\) and \(CR-IoT_{rx}\) link.
6.5 Energy consumption analysis
The average energy consumption of the proposed scheme using a sequential approach can be calculated as follows [58]:
where \(e_s\) is the energy consumed for sensing time slot, \(e_t\) is the energy consumed for the transmission, \(t_t\) is the transmission time which is defined as \(t_t=T-\tau _s(SA)-\tau _r\), and T is the overall time slot duration.
6.6 Expected lifetime analysis
The expected lifetime of the proposed scheme using a sequential approach for a heterogeneous CR-IoT network based on the proposed Dempster–Shafer theory can be calculated as follows [58]:
where \(e_c\) is the capacity of battery.
Now, we can calculate the decision statistics using Algorithm 2. Here, each CR-IoT user for both a homogeneous and a heterogeneous CR-IoT network obtains a flexible time slot of sensing \(\tau _s(SA)\) (see line 6), whereas it obtains a non-flexible time slot of sensing \(\tau _s(SA)\) for a single CR-IoT user (see line 4). Then, the algorithm computes the weight of the \(j{\rm th}\) CR-IoT user for both a heterogeneous CR-IoT network (see line 8) and a homogeneous CR-IoT network (see line 9). After that, it computes the \(j{\rm th}\) CR-IoT user local decision \(p_{d,j}^{ED}\left( \tau _{s}^j(SA)\right)\) and \(p_{f,j}^{ED}\left( \tau _{s}^j(SA)\right)\) based on the hard decision fusion rule (see lines 11 and 12), and then it sets an enhanced self-assessed basic probability assignment for both hypotheses (see lines 17 and 18). Finally, it computes the global detection gain \(gd_{d}^{ED}(\tau _s(SA))/gd_{f}^{ED}(\tau _s(SA))\) using the hard decision fusion rule (see lines 21 and 22) and \(gd_f(\tau _s(SA))/gd_d(\tau _s(SA))\) using the proposed Dempster–Shafer theory (see lines 23 and 24), the average throughput \(R_{avg}(\tau _s(SA))\) (see line 25), the average energy consumption \(E_{avg}(\tau _s(SA))\) (see line 26), and the expected lifetime \(\eta \left( \tau _s(SA)\right)\) (see line 27).

7 Simulation results and discussion
The parameters used in simulations are provided in this chapter as well as a description of the simulation performance.
7.1 Simulation parameter setting
In this subsection, we confirm the theoretical findings and analyze the performance of the proposed throughput analysis of an energy-efficient spectrum sensing scheme for the CR-IoT networks. This is achieved by means of computational MATLAB simulations. The implementation of the proposed scheme was performed to computer machines running the Windows 10 operating system. The system includes a 8 GB built volatile memory capacity Intel(R) Core(TM)2 Duo CPU T7250 @ 2.00 GHz.
Simulations of Monte Carlo were performed using the parameter setting mentioned in Table 2.
7.2 Performance comparison
Under the conditions shown in Table 2, the receiver operating characteristics (ROC) are shown in Fig. 6. This shows that the proposed Dempster–Shafer theory-based spectrum sensing for homogeneous CR-IoT networks achieves better sensing gain compared to both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks. With the non-sequential approach, the detection probability of the “OR” rule is always higher compared to both the “M” rule and “AND” rule.
Moreover, the sensing gain of both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks is the same, as the SNR of all the CR-IoT users is identical.
In Fig. 7, it has been shown that the proposed Dempster–Shafer theory-based spectrum sensing for heterogeneous CR-IoT networks using the sequential approach achieves better detection gain compared to both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks. With the hard decision fusion rule, using the “n-out-of-k” rule, the probability of detection of “Optimal” rules using the non-sequential approach is always larger compared to the “AND” rule, “OR” rule, and “M” rule. Moreover, the probability of detection of the “OR” rule using the non-sequential approach is always larger compared to the “AND” rule and “M” rule. With the soft decision fusion rule, the probability of detection of the proposed Dempster–Shafer theory is higher compared to both the conventional Dempster–Shafer theories I and II.
When comparing the sensing gain at the FC, as shown in Table 3 where the proposed Dempster–Shafer theory-based spectrum sensing when the probability of false alarm \((gd_f=0.2)\) for homogeneous CR-IoT networks can detect the spectrum with \(80\%\) accuracy, whereas the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks only detect the primary user signal with a detection accuracy of \(70\%\). Moreover, the proposed Dempster–Shafer theory-based sensing gain when the probability of false alarm \((gd_f=0.2)\) for heterogeneous CR-IoT networks can detect the spectrum with \(93\%\) accuracy, whereas the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks detect the primary user signal with a detection accuracy of \(80\%\) and \(87\%\), respectively. Therefore, the proposed Dempster–Shafer theory-based spectrum sensing for both homogeneous and heterogeneous CR-IoT networks using the sequential approach is a better solution to address the scarcity problem for future IoT networks.
Figure 8 shows that the average throughput of the proposed method for homogeneous CR-IoT networks is higher compared to both the conventional “n-out-of-k” rule and the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks.
Figure 9 shows that the average throughput of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks is higher compared to the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks.
Table 4 shows that the throughput of the proposed Dempster–Shafer theory for homogeneous CR-IoT networks when the probability of false alarm \((gd_f=0.2)\) achieves an average throughput of 2.64Hz compared to both the conventional Dempster–Shafer theories I and II with 2.42Hz and 2.42Hz, respectively. Similarly, the throughput of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks when the probability of false alarm \((gd_f=0.2)\) achieves an average throughput of 2.82Hz compared to both the conventional Dempster–Shafer theories I and II with 2.60Hz and 2.71Hz, respectively. This enhanced average throughput would be much more acceptable to emerging IoT networks.
Figure 10 shows that the energy consumption of the proposed Dempster–Shafer theory for homogeneous CR-IoT networks is less when compared to the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks. Here, the average energy consumption \(E_{avg}\left( \tau _{s}^j(SA)\right)\) depends on the probability of false alarm, \(gd_f\left( \tau _{s}^j(SA)\right)\).
Figure 11 shows that the proposed Dempster–Shafer theory-based energy consumption for heterogeneous CR-IoT networks is lower when compared to the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks. Here, the average energy consumption \(E_{avg}\left( \tau _{s}^j(SA)\right)\) depends on the probability of false alarm, \(gd_f\left( \tau _{s}^j(SA)\right)\).
Table 5 shows that the energy consumption of the proposed Dempster–Shafer theory for homogeneous CR-IoT networks when the probability of false alarm \((gd_f=0.2)\) achieves an average energy consumption of 1.50J compared to both the conventional Dempster–Shafer theories I and II with 1.52J and 1.52J, respectively. Similarly, the average energy consumption of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks when the probability of false alarm \((gd_f=0.2)\) is 1.25J when compared to both the conventional Dempster–Shafer theories I and II with 1.45J and 1.35J, respectively. This lower average energy consumption makes it more applicable for future IoT networks.
Figure 12 compares the expected lifetime of the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks, and the proposed Dempster–Shafer theory for homogeneous CR-IoT networks. Here, the proposed Dempster–Shafer theory using the sequential approach enhances energy efficiency when compared to both the conventional Dempster–Shafer theories I and II.
Figure 13 compares the expected lifetime of the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks and the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks. Here, the proposed Dempster–Shafer theory using the sequential approach enhances energy efficiency when compared to both conventional Dempster–Shafer theories I and II.
Table 6 shows that the average throughput of the proposed Dempster–Shafer theory for homogeneous CR-IoT networks using the sequential approach for round 200 achieves an average throughput of 2.75 Hz compared to both the conventional Dempster–Shafer theories I and II with 2.53 Hz and 2.53 Hz, respectively. Similarly, the average throughput of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks using the sequential approach for round 200 achieves an average throughput of 2.90 Hz when compared to both the conventional Dempster–Shafer theories I and II with 2.65 Hz and 2.75 Hz, respectively. This enhanced average throughput makes it more applicable for future IoT networks.
Figure 14 shows that \(p_e\) for the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks and the proposed Dempster–Shafer theory for homogeneous CR-IoT networks decreases along with an increase in the probability of detection value from 0 to 0.7. In addition, \(p_e\) for the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks gets larger along with an increase in the probability of detection value from 0.6 to 0.8. On the other hand, the global error probability \(p_e\) in the conventional “AND” rule is always high along with an increase in the probability of detection from 0 to 1. Therefore, the global error probability \(p_e\) of the proposed Dempster–Shafer theory for homogeneous CR-IoT networks is lower than for the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks.
Figure 15 shows that \(p_e\) for the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks and the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks decreases along with an increase in the probability of detection value from 0 to 0.7. In addition, \(p_e\) for both the conventional “n-out-of-k” rule and the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks gets larger along with an increase in the probability of detection value from 0.6 to 0.8. On the other hand, the global error probability \(p_e\) in the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks is low with an increase in the probability of detection from 0 to 0.9. Therefore, the global error probability \(p_e\) of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks is lower than for the conventional “n-out-of-k” rule and both the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks.
When comparing the global error probability at the fusion center in Table 7, we can see that the proposed Dempster–Shafer theory for homogeneous CR-IoT networks can obtain an \(p_e\) of \(23\%\) when the probability of detection, \((gd_d)\), is 0.9, whereas the conventional Dempster–Shafer theories I and II for homogeneous CR-IoT networks can obtain the same \(p_e\) with \(30\%\). Similarly, the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks can obtain an \(p_e\) of \(11\%\) when the probability of detection, \((gd_d)\), is 0.9, whereas the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks can obtain a \(p_e\) of \(22\%\) and \(18\%\), respectively. Therefore, the proposed Dempster–Shafer theory-based spectrum sensing for heterogeneous CR-IoT networks is a better solution to address the global error probability problem for the future IoT networks.
8 Conclusion and future work
We calculate the weight ratio in this paper, that is specified as the ratio of the two mean values of both hypotheses. In the sensing gain, the proposed Dempster–Shafer theory for homogeneous CR-IoT networks demonstrates a 10% improvement over both the conventional Dempster–Shafer theories I and II. Moreover, the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks demonstrates a 13% and 10% improvement over both the conventional Dempster–Shafer theories I and II, respectively.
With respect to the average throughput for homogeneous CR-IoT networks, the proposed Dempster–Shafer theory is 7.14% and 50.35% better than both the conventional Dempster–Shafer theories I and II, respectively. Moreover, the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks is 13% and 10% better than the conventional Dempster–Shafer theories I and II for heterogeneous CR-IoT networks, respectively.
In comparison, the proposed scheme with the Dempster–Shafer theory for heterogeneous CR-IoT networks demonstrates for the probability of false alarm \((gd_f=0.1)\) a 30% and 20% lower energy consumption to both conventional Dempster–Shafer theories I and II, respectively.
With regard to the expected lifetime in terms of average throughput, the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks for round 200 shows a 10% and 25% improvement when compared to both conventional Dempster–Shafer theories I and II, respectively.
Finally, a global error probability of 10% is achieved in the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks, while 57% and 21% global error probabilities are achieved in both the conventional Dempster–Shafer theories I and II, respectively. Therefore, we conclude that our proposed Dempster–Shafer theory would be much more acceptable to emerging IoT networks because it alleviates the issue of spectrum shortage, enhances system throughput, improves energy efficiency, and prolongs the expected lifetime.
Our future research would entail a complexity evaluation of the proposed Algorithm 2. In addition, we will analyze the sensing gain, the average throughput, the average energy consumption, and the expected lifetime of the proposed Dempster–Shafer theory for heterogeneous CR-IoT networks that use the underlay approach. Furthermore, we will investigate the scalability of the proposed Dempster–Shafer theory with regard to network size and number of CR-IoT devices.
Availability of data and materials
Not applicable.
Abbreviations
- IoT:
-
Internet of things
- M2M:
-
Machine-to-machine
- CRNs:
-
Cognitive radio networks
- CR-IoT:
-
Cognitive radio-based IoT
- SNR:
-
Signal-to-noise ratio
- HDF:
-
Hard decision fusion
- SDF:
-
Soft decision fusion
- SA:
-
Sequential approach
- NSA:
-
Non-sequential approach
- ADC:
-
Analog-to-digital converter
- PDF:
-
Probability distribution function
- CLT:
-
Central limit theory
- CPU:
-
Central processing unit
- ROC:
-
Receiver operating characteristic
References
A.A. Khan, M.H. Rehmani, A. Rachedi, Cognitive-radio-based internet of things: applications, architectures, spectrum related functionalities, and future research directions. IEEE Wirel. Commun. 24(3), 17–25 (2017)
A.A. Khan, M.H. Rehmani, A. Rachedi, When cognitive radio meets the internet of things? in 2016 International Wireless Communications and Mobile Computing Conference (IWCMC) (IEEE, 2016), pp. 469–474
J. Zhu, Y. Song, D. Jiang, H. Song, Multi-armed bandit channel access scheme with cognitive radio technology in wireless sensor networks for the internet of things. IEEE Access 4, 4609–4617 (2016)
F.A. Awin, Y.M. Alginahi, E. Abdel-Raheem, K. Tepe, Technical issues on cognitive radio-based internet of things systems: a survey. IEEE Access 7, 97887–97908 (2019)
M. Farrukh, A. Krayani, M. Baydoun, L. Marcenaro, Y. Gao, C.S. Regazzoni, Learning a switching bayesian model for jammer detection in the cognitive-radio-based internet of things, in 2019 IEEE 5th World Forum on Internet of Things (WF-IoT) (IEEE, 2019), pp. 380–385
T. Li, J. Yuan, M. Torlak, Network throughput optimization for random access narrowband cognitive radio internet of things (NB-CR-IoT). IEEE Internet Things J. 5(3), 1436–1448 (2018)
X. Xing, T. Jing, W. Cheng, Y. Huo, X. Cheng, Spectrum prediction in cognitive radio networks. IEEE Wirel. Commun. 20(2), 90–96 (2013)
Q. Lv, F. Gao, Matched filter based spectrum sensing and power level recognition with multiple antennas, in 2015 IEEE China Summit and International Conference on Signal and Information Processing (ChinaSIP) (IEEE, 2015), pp. 305–309
V. Turunen, M. Kosunen, A. Huttunen, S. Kallioinen, P. Ikonen, A. Parssinen, J. Ryynanen, Implementation of cyclostationary feature detector for cognitive radios, in 2009 4th International Conference on Cognitive Radio Oriented Wireless Networks and Communications (IEEE, 2009), pp. 1–4
H. Reyes, S. Subramaniam, N. Kaabouch, W.C. Hu, A spectrum sensing technique based on autocorrelation and euclidean distance and its comparison with energy detection for cognitive radio networks. Comput. Electric. Eng. 52, 319–327 (2016)
M.S. Miah, M.M. Rahman, An eigenvalue and superposition approach based cooperative spectrum sensing in cognitive radio networks, in 2014 International Conference on Electrical Engineering and Information & Communication Technology (IEEE, 2014), pp. 1–7
N. Pillay, H. Xu, Blind eigenvalue-based spectrum sensing for cognitive radio networks. IET Commun. 6(11), 1388–1396 (2012)
J. Mu, X. Jing, H. Huang, N. Gao, Subspace-based method for spectrum sensing with multiple users over fading channel. IEEE Commun. Lett. 22(4), 848–851 (2017)
M. Sun, C. Zhao, S. Yan, B. Li, A novel spectrum sensing for cognitive radio networks with noise uncertainty. IEEE Trans. Veh. Technol. 66(5), 4424–4429 (2016)
C.-C. Wu, S.-H. Wu, On bridging the gap between homogeneous and heterogeneous rendezvous schemes for cognitive radios, in Proceedings of the Fourteenth ACM International Symposium on Mobile Ad Hoc Networking and Computing (ACM, 2013), pp. 207–216
A. Celik, A.E. Kamal, Green cooperative spectrum sensing and scheduling in heterogeneous cognitive radio networks. IEEE Trans. Cognit. Commun. Netw. 2(3), 238–248 (2016)
W. Liu, M. Chwalisz, C. Fortuna, E. De Poorter, J. Hauer, D. Pareit, L. Hollevoet, I. Moerman, Heterogeneous spectrum sensing: challenges and methodologies. EURASIP J. Wirel. Commun. Netw. 2015(1), 70 (2015)
S.K. Sharma, S. Chatzinotas, B. Ottersten, Cooperative spectrum sensing for heterogeneous sensor networks using multiple decision statistics, in International Conference on Cognitive Radio Oriented Wireless Networks (Springer, 2015), pp. 321–333
H. Guo, N. Reisi, W. Jiang, W. Luo, Soft combination for cooperative spectrum sensing in fading channels. IEEE Access 5, 975–986 (2016)
M. Emami, H. Zarrabi, M.R. Jabbarpour, M. Sadat Taheri, J.J. Jung, A soft cooperative spectrum sensing in the presence of most destructive smart PUEA using energy detector. Concurr. Comput. Pract. Exp. 30(15), 4524 (2018)
J. So, W. Sung, Group-based multibit cooperative spectrum sensing for cognitive radio networks. IEEE Trans. Veh. Technol. 65(12), 10193–10198 (2016)
S. Nallagonda, Y.R. Kumar, P. Shilpa, Analysis of hard-decision and soft-data fusion schemes for cooperative spectrum sensing in rayleigh fading channel, in 2017 IEEE 7th International Advance Computing Conference (IACC) (IEEE, 2017), pp. 220–225
M.S. Miah, M.M. Rahman, H. Yu, Superallocation and cluster-based cooperative spectrum sensing in 5g cognitive radio network. Towards 5G Wirel. Netw. Phys. Layer Perspect. 193 (2016)
W. Qian, D..-w YUE, Q..-n YAN, Optimal fusion rule for cooperative spectrum sensing in cognitive radio networks. J. China Univ. Posts Telecommun. 19(5), 58–65 (2012)
P. Qihang, Z. Kun, W. Jun, L. Shaoqian, A distributed spectrum sensing scheme based on credibility and evidence theory in cognitive radio context, in 2006 IEEE 17th International Symposium on Personal, Indoor and Mobile Radio Communications (IEEE, 2006), pp. 1–5
N. Nguyen-Thanh, I. Koo, An enhanced cooperative spectrum sensing scheme based on evidence theory and reliability source evaluation in cognitive radio context. IEEE Commun. Lett. 13(7), 492–494 (2009)
M.S. Miah, M. Schukat, E. Barrett, Enhanced cooperative spectrum sensing in hybrid homogeneous-heterogeneous cognitive radio networks, 1–5 (2018). IET
P.S. Yawada, A.J. Wei, Comparative study of spectrum sensing techniques base on techniques non-cooperative in cognitive radio networks, in 2016 5th International Conference on Computer Science and Network Technology (ICCSNT) (IEEE, 2016), pp. 517–520
B. Suseela, D. Sivakumar, Non-cooperative spectrum sensing techniques in cognitive radio—a survey, in 2015 IEEE Technological Innovation in ICT for Agriculture and Rural Development (TIAR) (IEEE, 2015), pp. 127–133
A.J. Fareduddin, R. Ujjinimatad, Fast optimal and explorative (fox) sensing and power allocation scheme for non-cooperative cognitive radio networks, in 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT) (IEEE, 2017), pp. 457–461
V.-D. Nguyen, O.-S. Shin, Cooperative prediction-and-sensing-based spectrum sharing in cognitive radio networks. IEEE Trans. Cogn. Commun. Netw. 4(1), 108–120 (2017)
M.A. Rahman, Y.-D. Lee, I. Koo, An efficient transmission mode selection based on reinforcement learning for cooperative cognitive radio networks. HCIS 6(1), 2 (2016)
G. Chandrasekaran, S. Kalyani, Performance analysis of cooperative spectrum sensing over k-μ shadowed fading. IEEE Wirel. Commun. Lett. 4(5), 553–556 (2015)
C.-H. Hwang, G.-L. Lai, S.-C. Chen, Spectrum sensing in wideband OFDM cognitive radios. IEEE Trans. Signal Process. 58(2), 709–719 (2009)
Q. Chen, M. Motani, W.-C. Wong, Cooperative spectrum sensing strategies with multiple relays, in 2010 IEEE International Conference on Communication Systems (IEEE, 2010), pp. 540–544
M. Gupta, G. Verma, R.K. Dubey, Cooperative spectrum sensing for cognitive radio based on adaptive threshold, in 2016 Second International Conference on Computational Intelligence & Communication Technology (CICT) (IEEE, 2016), pp. 444–448
A. Homayounzadeh, M. Mahdavi, Performance analysis of cooperative cognitive radio networks with imperfect sensing, in 2015 International Conference on Communications, Signal Processing, and Their Applications (ICCSPA’15) (IEEE, 2015), pp. 1–6
Y. Liao, T. Wang, L. Song, B. Jiao, Cooperative spectrum sensing for full-duplex cognitive radio networks, in 2014 IEEE International Conference on Communication Systems (IEEE, 2014), pp. 56–60
I.-H. Lee, H. Lee, Achievable rate analysis for opportunistic non-orthogonal multiple access-based cooperative relaying systems. JIPS 13(3), 630–642 (2017)
H. Vu-Van, I. Koo, A cluster-based sequential cooperative spectrum sensing scheme utilizing reporting framework for cognitive radios. IEEJ Trans. Electr. Electron. Eng. 9(3), 282–287 (2014)
N. Nguyen-Thanh, I. Koo, An efficient ordered sequential cooperative spectrum sensing scheme based on evidence theory in cognitive radio. IEICE Trans. Commun. 93(12), 3248–3257 (2010)
Z. Chair, P. Varshney, Optimal data fusion in multiple sensor detection systems. IEEE Trans. Aerosp. Electron. Syst. 1, 98–101 (1986)
W. Zhang, Y. Yang, C.K. Yeo, Cluster-based cooperative spectrum sensing assignment strategy for heterogeneous cognitive radio network. IEEE Trans. Veh. Technol. 64(6), 2637–2647 (2014)
S. Eryigit, S. Bayhan, T. Tugcu, Energy-efficient multichannel cooperative sensing scheduling with heterogeneous channel conditions for cognitive radio networks. IEEE Trans. Veh. Technol. 62(6), 2690–2699 (2013)
T. Zhang, D.H.K. Tsang, Cooperative sensing scheduling for energy-efficient cognitive radio networks. Google Patents. US Patent 9144083 (2015)
H. Yu, Optimal channel sensing maximising sum rate in cognitive radio with multiple secondary links. Trans. Emerg. Telecommun. Technol. 24(7–8), 777–784 (2013)
H. Yu, Optimal channel sensing for heterogeneous cognitive networks: An analytical approach. KSII Trans. Internet Inf. Syst. 7(12), 2987–3002 (2013)
D. Huang, G. Kang, B. Wang, H. Tian, Energy-efficient spectrum sensing strategy in cognitive radio networks. IEEE Commun. Lett. 17(5), 928–931 (2013)
Y. Liu, R. Yu, S. Xie, Y. Zhang, V.C. Leung, Efficient spectrum discovery with energy constraints in cognitive radio networks, in 2011 18th International Conference on Telecommunications (IEEE, 2011), pp. 38–43
Y.H. Bae, J.W. Baek, Achievable throughput analysis of opportunistic spectrum access in cognitive radio networks with energy harvesting. IEEE Trans. Commun. 64(4), 1399–1410 (2016)
Y. Wang, C. Feng, Z. Zeng, C. Guo, A robust and energy efficient cooperative spectrum sensing scheme in cognitive radio networks, in 2009 11th International Conference on Advanced Communication Technology, vol. 1 (IEEE, 2009), pp. 640–645
M.S. Miah, M. Schukat, E. Barrett, Maximization of sum rate in af-cognitive radio networks using superposition approach and n-out-of-k rule, in 2017 28th Irish Signals and Systems Conference (ISSC) (IEEE, 2017), pp. 1–6
M.S. Miah, M. Schukat, E. Barrett, An enhanced sum rate in the cluster based cognitive radio relay network using the sequential approach for the future internet of things. HCIS 8(1), 16 (2018)
R. Wan, M. Wu, L. Hu, H. Wang, Energy-efficient cooperative spectrum sensing scheme based on spatial correlation for cognitive internet of things. IEEE Access 8, 139501–139511 (2020)
A.U. Rehman, C. Dong, L.-L. Yang, L. Hanzo, Performance of cognitive stop-and-wait hybrid automatic repeat request in the face of imperfect sensing. IEEE Access 4, 5489–5508 (2016)
M.S. Miah, M. Schukat, E. Barrett, Sensing and throughput analysis of a mu-mimo based cognitive radio scheme for the internet of things. Comput. Commun. 154, 442–454 (2020)
M. Miah, K.M. Ahmed, M. Islam, M. Mahmud, A. Raihan, M. Rahman, H. Yu et al., Enhanced sensing and sum-rate analysis in a cognitive radio-based internet of things. Sensors 20(9), 2525 (2020)
V.-H. Vu, I. Koo, Throughput maximization for cognitive radio users with energy constraints in an underlay paradigm. J. Inf. Commun. Converg. Eng. 15(2), 79–84 (2017)
Acknowledgements
This work was supported by the Discipline of Information Technology (IT), National University of Ireland Galway (NUIG), Galway, Ireland, and in part by the Hardiman Scholarship Postgraduate Research Foundation of National University of Ireland Galway (NUIG), Galway, Ireland.
Funding
Funding was provided by Hardiman Scholarship, National University of Ireland Galway (NUIG), Galway, Ireland (Grant No. 16239003).
Author information
Authors and Affiliations
Contributions
MSM and EB provided the guideline to focus on issues, requiring solutions, and reviewed the overall manuscript. MMS conceived the study, drafting the article and revising it critically for intellectual content of the whole manuscript. They reviewed the technical contribution of the work and approved the final. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
This article does not contain any studies with human participants or animals performed by any of the authors.
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Proof of proposition 1
In the conventional scheme using a non-sequential approach, the \(j{\rm th}\) CR-IoT user can obtain a fixed both time slot of sensing and time slot of reporting as a result of the remainder of CR-IoT users time slots of reporting are not merged to the flexible time slot of sensing as shown in Fig. 4 which is defined as follows:
where \(\tau _s^j(NSA)\) is not a flexible time slot of sensing of the \(j{\rm th}\) CR-IoT user using the non-sequential approach and \(\tau _s\) is the sensing time slot which is a fixed for all CR-IoT users. \(\square\)
Proof of proposition 2
The proposed scheme using the sequential approach utilizes the reporting framework as shown in Fig. 5; it is seen that the 2nd CR-IoT user has acquired a flexible time slot of sensing to detect the primary user signal because of merging the time slot of reporting of the 1st CR-IoT user and the sensing time slot of the 2nd CR-IoT user. The time slot of sensing of the 2nd CR-IoT user is merged which is defined as follows:
where \(\tau _r^1\) is a reporting time slot of the 1st CR-IoT user which is a fixed for all CR-IoT users, i.e., \(\tau _r^1=\tau _r^2=\cdots =\tau _r^j=\tau _r\).
In addition, the flexible time slot of sensing for the \(3^{rd}\) CR-IoT user must be achieved which is defined as follows:
Finally, the flexible time slot of sensing of the \(j{\rm th}\) CR-IoT user can be calculated as follows:
\(\square\)
Proof of proposition 3
In the proposed Dempster–Shafer theory based on the sequential approach for a heterogeneous CR-IoT network, the weight, \(\omega _j^{\prime }\), can be expressed using Eq. (23) which is defined as follows:
In a heterogeneous CR-IoT network, the \(j{\rm th}\) CR-IoT user utilizes only the distance \(D_j\) of both hypotheses that is defined as follows:
The function \(f\left( .\right)\) will meet the specific constraints in order to assess an acceptable adjustment [27]:
-
i.
\(f\left( .\right)\) agrees a flexible time slot of sensing, \(\tau _s^j\left( SA\right)\), the weight function as an output \(\omega _j^{\prime }\epsilon [1, 0]\)
-
ii.
\(f\left( .\right) =0\) if \(\tau _s^{j}\left( SA\right) =\tau _s^{j}\left( NSA\right)\)
-
iii.
\(f\left( .\right) =1\) if \(\tau _s^{j}\left( SA\right) =2\tau _s^{j}\left( SA\right)\)
-
iv.
\(f\left( .\right) \sim |\tau _s^{j}\left( SA\right) -\tau _s^{j}\left( NSA\right) |\)
Now, we can normalize the flexible time slot of sensing based on the above specific constraints as follows:
In the proposed Dempster–Shafer theory based on the sequential approach for a heterogeneous CR-IoT network, the weight \(\omega _j^{\prime }\) of the \(j{\rm th}\) CR-IoT can be calculated by normalizing the distance using Eq. (41) as follows:
Now, based on both Eqs. (42) and (43), we can rewrite Eq. (40) as follows:
\(\square\)
Proof of proposition 4
In a homogeneous CR-IoT network using the sequential approach, the SNR of all CR-IoT users is identical, i.e.,\(\gamma _1=\gamma _2=\gamma _3=,\ldots ,=\gamma _{j-1}=\gamma _j=\gamma\). The weight of the \(j{\rm th}\) CR-IoT user, \(\omega _j\), is obtained by Eq. (42)
Now, we can rewrite Eq. (43) based on Eq. (44) as follows:
\(\square\)
Proof of proposition 5
In the proposed Dempster–Shafer theory-based heterogeneous CR-IoT network using the sequential approach [27], we obtained an improved self-assessed elementary probability assignment function of both hypotheses of the \(j{\rm th}\) CR-IoT user as a form of a flexible time slot of sensing, \(\tau _s^{j}\left( SA\right)\), instead of a non-flexible time slot of sensing, \(\tau _s^{j}\left( NSA\right)\), as follows:
where \({m}_j^{\prime }\left( H_0\right)\) as well as \({m}_j^{\prime }\left( H_1\right)\) denotes an improved self-assessed elementary probability assignment of the \(j{\rm th}\) CR-IoT under \(H_0\) and \(H_1\), respectively.
Now, we can compare with Eqs. (21, 22) and (11) as follows:
\(\square\)
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Miah, M.S., Schukat, M. & Barrett, E. A throughput analysis of an energy-efficient spectrum sensing scheme for the cognitive radio-based Internet of things. J Wireless Com Network 2021, 201 (2021). https://doi.org/10.1186/s13638-021-02075-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-021-02075-2