Abstract
Several approaches have been proposed to suppress multipath ghost in through-the-wall radar imaging (TWRI). One classical approach, called Aspect Dependent (AD), exploits locations of ghosts in the images without demanding prior knowledge of the reflecting geometry. This operation strategy makes the method superior over multipath exploitation-based approaches. However, the AD method assumes a point target that emulates unreal environment. Therefore, reconstructing extended targets with this method leads to incorrect scene interpretation. This work proposes a ghost suppression method for extended targets based on the AD feature that exploits duo sub-apertures. Firstly, we evaluate the best suppression method using a performance metric called relative clutter peak. Next, the evaluated method is extended to encompass a target extent during sub-images reconstruction. Following this strategy, an effective image fusion method suitable for extended targets is proposed. The method considers pixel neighborhood to effectively recover the given extended target. Simulation results show that, when signal-to-noise ratio is 20dB, the proposed method significantly improves signal-to-clutter ratio and relative clutter peak by 8.8% and 23.8%, respectively, relative to the existing AD based methods under point target assumption.
Similar content being viewed by others
1 Introduction
Through-the-wall radar imaging (TWRI) is an emerging radar imaging technique that allows visualization and identification of objects inside the building. The technique may be used to determine room layout or to recognize nature of the activities executed by people in the room. TWRI offers a wide range of applications, including rescue mission in natural disasters (fire, flood, and earthquake), criminal investigation, emergency relief operation, and military operations [1,2,3,4,5,6,7,8,9,10].
The TWRI technique involves generation of scenes through image reconstruction, where the technique provides visual representation of objects contained in the enclosure (e.g., room or building). Image reconstruction suffers from some technical challenges: firstly, clutters caused by strong reflections from the front wall; and secondly, multipath returns from secondary reflectors [11,12,13,14,15,16]. The first challenge can be addressed using appropriate wall mitigation technique [17,18,19,20]. The second challenge (multipath returns) introduces multipath ghosts that corrupt the scene, hence creating confusion with genuine targets [6, 10, 21,22,23,24].
Several methods have been devised to address the challenge of multipath ghosts, and these methods can broadly be categorized as Aspect Dependent (AD) and Multipath Exploitation (ME)-based methods [13, 21,22,23,24,25]. The AD-based approach does not require prior knowledge of the reflecting geometry, thus making it superior over ME-based approaches.
Currently, when addressing reconstruction challenges associated with multipath returns, the target is modeled as a point, implying that each target assumes a single pixel. In real situations, however, the target may span more than one pixel, resulting into extended targets. Unlike point target, the received signal from extended targets originates from the integration of signals from various parts of the same target [26]. Therefore, modeling extended target as point target gives the possibility of misinterpreting the target of interest—a consequence that adversely affects the target identification process.
Several works in TWRI have addressed multipath ghost by exploiting AD feature. Dong et al. [27] used N non-overlapping sub-apertures to reconstruct sub-images and combined them using multiplicative image fusion to produce a final image. Muqaibel et al. [28] developed a new multipath ghost suppression technique, based on the compressed sensing framework, which incorporates AD feature of the ghost. In their work, only a pair of measurement vectors were selected such that the AD feature is maximized; the authors strategically combined the corresponding images to suppress the effect of ghosts. Guo et al. [15] made an interesting contribution to realize AD feature through array rotation, assuming that the scene contains point targets—which rarely holds in various real situations. Measurements were collected at different array orientations, then back-projection and incoherent multiplication fusion methods were applied to achieve ghost-free images.
Scholars have attempted to incorporate extended targets into the point target model [9, 29,30,31,32,33]. Abdalla et al. [33] modeled extended targets with block sparse reconstruction. The proposed approach is agnostic to the target shape, size, and reflectivity distribution. The approach operates irrespective of the length, number, or distribution of the blocks. As an added advantage, the approach by Abdalla et al. can reconstruct scenes with mixed point targets and extended targets concurrently. Despite their promising results, the authors disregarded multipath effects for scenes with extended targets. Inspired by this limitation, the current work introduces a method that addresses multipath effects under the environment of extended targets. The proposed method is based on AD feature exploiting duo sub-apertures. Firstly, the best suppression method is evaluated using a performance metric called relative clutter peak (RCP); secondly, the method is further extended to encompass the target extent during sub-images reconstruction. In this work, we have devised an effective image fusion method, taking into account target pixels’ neighborhood, to recover extended targets.
2 Received signal and scene model
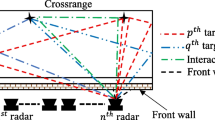
Consider a scene model representing possible first-order multipath returns with N different radar locations (Fig. 1). At every radar location, M monochromatic waves, equally spaced in frequency, are transmitted and received [28]. The scene is divided into \(N_x\) and \(N_y\) pixels along the cross-range and down-range directions, respectively. Let \(\sigma _p\) be the target reflectivity of the \(p^{th}\) pixel, where \(p=0, 1,\ldots , N_xN_y-1\); the value of \(\sigma _p=1\) signifies the presence of a target, otherwise no target exists in a given pixel location. If we considerR multipath returns, the target return, \(y_t[m,n]\), observed with the \(n^{th}\) transceiver when transmitting the \(m^{th}\) frequency, \(f_m\), in the presence of a Gaussian noise, \(\upsilon (m,n)\), can be expressed as [28, 34]
where \(\sigma _p^{(r)}\) and \(\sigma _w^{(r_w)}\) represent the target and wall pixel reflectivities, respectively, \(\tau _{pn}^{(r)}\) is the round-trip delay between the \(p^{th}\) target and the \(n^{th}\) transceiver due to the \(r^{th}\) return, and \(\tau _w^{(r_w)}\) is the time delay of the \(r_w^{th}\) front wall return. The first and the second terms on the right-hand side of (2.1) represent the target return and the return from the front wall, respectively, while the last term denotes the Gaussian noise.
3 Performance evaluation of point target-based reconstruction methods for extended target
The initial goal was to determine a superior suppression method, based on AD feature, which can then be improved to include extended targets. Ghost suppression methods based on AD feature, assuming point target model, can be categorized into three groups: multiple subarrays, hybrid subarray, and sparse arrays [26]. Maintaining the same environment, the best method is determined for each group. In evaluating the performance of these groups, the signal model presented in (2.1) was used.
An experimental simulation setup to mimic TWRI environment was performed using the MATLAB software, assuming a stepped frequency monostatic radar. The array element consisting of 77 array elements linearly spaced at 3.94 cm and parallel with the front wall and 1 m away was realized. The center of the array defines the origin of the system. A 2 GHz bandwidth ranging from 1 GHz to 3 GHz was used with 201 frequencies spaced at 10 MHz. The number of frequencies and radar locations were selected according to the compressive sensing theory that gives a threshold below which targets cannot be reconstructed correctly [37]. The room was assumed to be made of non-reinforced concrete with relative permittivity of 7.6 and wall thickness of 20 cm. Four first-order multipath returns were considered: direct return, return from the back wall, right-wall return, and left-wall return. As the signal undergoes multiple reflections, their corresponding ghosts either become very weak or reside outside the perimeter of the room in question. Thus, they can be fairly ignored as Leigsnering et al. [8] suggests. The effect of front wall was mitigated using spatial filtering [17]. The scene image resolution was set to \(64\times 64\) pixels. During simulation, one-fourth of the frequency bins and one-third of the radar locations were used to reconstruct the scene of interest.
Results show that non-overlapping duo subarray, hybrid subarray, and Pythagorean-based Displaced Subarrays (PDSA) [25, 26] are the best methods in their respective groups. To quantify the performance with respect to extended targets reconstruction, signal-to-clutter ratio (SCR), RCP, and precision were used to evaluate performance. Precision is quantified as the ratio of the number of true targets to the sum of the number of true targets and ghost targets. Figure 2a shows the original scene with the extended target. Figure 2b, c, d represents the final images generated by three methods, namely duo-subarray, hybrid, and sparse array configuration employing PDSA, respectively. Figure 3 shows that duo subarray generates images with higher SCR and RCP values, and this observation translates to high-quality images containing well-preserved target shapes. For the entire range of signal-to-noise ratio (SNR), duo subarray demonstrates the best performance, as supported by the precision curve in Fig. 4. Therefore, results suggest that duo sub-array can suppress multipath ghost more effectively compared with other methods.
4 Aspect dependent-based extended target signal modeling
Consider a signal model presented in (2.1), which can be re-written in matrix form as
where R is the number of multipath returns, \(R_w\) is number of returns due to wall reflections, \({\varvec{s}}^{(r)}\) and \({{\varvec{s}}}_{w}^{(r_{w})}\in {\mathbb {C}}^{(N_{x} N_{y}\times 1)}\) are their vectors of reflectivities for \(r=0, 1, 2,\ldots ,R-1\), and \(r_w=0, 1, 2,\ldots , R_{w}-1\); \({{\varvec{\phi }}^{(r)}}\) and \({{\varvec{\phi _{w}}}^{(r)}}\) are the phase information matrices defined as
and
for \(m=i\mod M, n=\lfloor i/M\rfloor , i=0,1,2,..,MN-1.\) Expressing (4.1) in terms of \(\phi ^{(0)}\) yields
Let a column vector, \({\varvec{z}}\), be defined as
Substituting (4.5) into (4.4) gives
Let \(\widetilde{{\textbf {s}}^{(0)}}= {\textbf {s}}^{(0)}+{\textbf {z}}\), which denotes the sum of the desired image vector and the multipath returns, then
Equation (4.7) indicates that only the direct path information is suffice to reconstruct the contaminated scene.
When the scene contains spatially extended targets, there exists a position in the image corresponding to the target extensions where the target pixels are contiguous. The position of these pixels is determined by their pixel indices within the image. Let the position of the entries be denoted as \(a={a_1, a_2, a_3,\ldots ,a_i}\). The vector of coefficients corresponding to the nonzero entries can be represented as
Equation (4.7) can be represented as
where \({\varvec{\phi }}_i^0\) is obtained from the measurement matrix, \({\varvec{\phi }}^0\), after removing columns with zero valued coefficients [35] such that
Taking the derivative of \(e^2\) in (4.10) with respect to \(\psi _i^H\), we get
Setting \(\frac{\partial e^2}{\partial \psi _i^H}=0\), we have
Then,
Assuming that \(\psi _0\) is an initial measurement estimate, we get
The position of the first element of the maximum value, \(a_1\), is determined as
Using the position, \(a_1\), obtained from (4.16), we obtain \(\psi _1\) from equation (4.14), and, subsequently, we obtain \({\varvec{y_1}}\) from (4.9). Then, the estimated nonzero component is removed from the measurement y. The second nonzero position is estimated as \(a_2=\mathop {\mathrm {\arg \!\max }}\limits |{{\varvec{\phi }}^{(0)}}^H\eta _1|\), with \(\eta _1=y-y_1\). This process continues until the acceptable error is achieved. The acceptable error, \(\epsilon =\sigma \sqrt{2\log (N_xN_y)}\), as given by Abdalla et al. [10], is a function of noise power. The entries in \({\varvec{s}}^{(0)}\) are modified by replacing the corresponding entries with the entries in \(\psi _i\) and with zero for entries not in \(\psi _i\) (Algorithm 1).
Let the modified signal coefficients be denoted by \(\widetilde{{\varvec{z_l}}^{(0)}}\). Then, equation (4.7) can be represented as
Let \(D_i\in \{0, 1\}^{J\times N_xN_y},~~i=1, 2,\ldots ,k\) with \(J<<MN\) be the downsampling matrices. Basically, D is a Bernoulli matrix obtained by randomly selecting J rows from identity matrix, \(I_{MN}\). Then, (4.17) can be downsampled to obtain
The contaminated subimage, \(\widetilde{{\varvec{z}}_l^{(0)}},\) in (4.18) is obtained by solving an optimization problem
using YALL1 algorithm, as recommended by AlBeladi and Muqaibel [36], and the resulting subimages are then strategically fused to obtain the final image. We should note that YALL1 algorithm does not converge to a good solution when nonzero elements extend in two dimensions. This is the situation when considering extended targets in through-the-wall-radar imaging applications.
5 Image fusion
In order to successfully eliminate ghosts resulting from different sub-images, the sub-images have to be strategically combined to yield the final image. Conventional masking, which involves pixel-by-pixel multiplication, has been widely used to achieve this objective. However, sometimes masking tends to suppress genuine target pixels at the target location. Therefore, a genuine target might be missed completely or its intensity be severely reduced [10]. In this work, we proposed a combined masking and weighted sum fusion strategy (Algorithm 2).
Suppose \(\widetilde{{\varvec{z_1}}^{(0)}}\) and \(\widetilde{{\varvec{z_2}}^{(0)}}\) are the individual sub-images reconstructed from the two subarrays. The final image is obtained by strategically combining the two sub-images as


6 Results and discussion
To obtain the final image, the scene was interrogated at two different locations to exploit the aspect dependent feature. In the first scenario, a rectangular target was imaged; in the second scenario, a complex target was simulated. Figure 5a shows the original scene with a rectangular target; Fig. 5b, c represents the images of the duo subarrays reconstructed using the point target model. Figure 5d is the final image after combining the two subimages. Evidently, the quality of the image is poor as the genuine target is completely missing in the final image, hence showing ineffectiveness of the point target model on extended target reconstruction.
Figure 6 shows images of a rectangular target reconstructed using the proposed extended target-based method. Figure 6a is the original scene; Fig. 6b and c is sub-images from the duo subarrays; and Fig. 6d is the final image. The results in Fig. 6d show that the developed method reconstructs the extended target more effectively compared with the point target-based method.
Figs. 7 and 8b, c, respectively, represent duo sub-images of the existing and proposed methods, while Figs. 7 and 8d show images of an irregular target reconstructed using the existing point target-based method and the proposed extended target-based method. Again, the final image obtained using the proposed method has a better quality compared with the existing point target-based method. Using the existing method, the target could not be recovered contrary to the proposed method where the image is clearly visible.
To quantify the performance, SCR, RCP, and precision were used. The SCR and RCP for the existing and the developed methods were evaluated at varying noise environments, and the results were averaged over 100 Monte Carlo runs for each SNR value. Figure 9 shows variation in SCR and RCP with SNR for the existing and proposed methods. When SNR=20 dB, the proposed method registered an improvement of 8.8% for SCR and 23.8% for RCP relative to the existing method.
To examine the target detection capability, precision was used as a performance measure. Figure 10 shows the variation in precision with the detection threshold for the existing and proposed methods. Evidently, the proposed method can more accurately detect the target in the presence of ghost, contrary to the existing method where the detection probability is low.
7 Conclusion
In this work, we have devised a method to combat the effect of multipath ghost in TWRI. Assuming a point target scenario, the proposed method serves as a generalization of the existing duo subarray-based reconstruction method. Furthermore, we have improved the existing method to incorporate extended targets during image reconstruction. Previous methods consider all targets as point targets, an assumption that cannot hold in real-world applications. Hence, inclusion of extended targets during reconstruction is inevitable to represent the scene more correctly. Simulation results show that our method reconstructs targets more effectively than the existing point target methods. As a possible future research avenue, researchers may consider the experimental validation of our simulation results to map the presented theoretical concepts and practice to a range of radar imaging modalities, including ground penetrating radar and through-the-wall radar. Furthermore, our work may be extended to use more advanced electromagnetic simulations of 3D objects to generate reliable results.
References
M. Leigsnering, F. Ahmad, M.G. Amin, A.M. Zoubir, Parametric dictionary learning for sparsity-based TWRI in multipath environments. IEEE Trans. Aerosp. Electron. Syst. 52(2), 532–547 (2016)
G. Gennarelli, F. Soldovieri, Multipath ghosts in radar imaging: physical insight and mitigation strategies. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 8(3), 1078–1086 (2014)
Y. Jia, R. Song, S. Chen, G. Wang, C. Yan, Preliminary results of multipath ghost suppression based on generative adversarial nets in TWRI, in 2019 IEEE 4th international conference on signal and image processing (ICSIP), IEEE, pp. 208–212 (2019)
V.H. Tang, A. Bouzerdoum, S.L. Phung, Compressive radar imaging of stationary indoor targets with low-rank plus jointly sparse and total variation regularizations. IEEE Trans. Image Process. 29, 4598–4613 (2020)
M.G. Amin, Through-The-Wall Radar Imaging (CRC Press, Boca Raton, 2017)
A. Abdalla, Through-the-wall radar imaging with compressive sensing; theory, practice and future trends-a review. Tanz. J. Sci. 44(3), 12–30 (2018)
A.T. Abdalla, M.T. Alkhodary, A.H. Muqaibel, Multipath ghosts in through-the-wall radar imaging: challenges and solutions. ETRI J. 40(3), 376–388 (2018)
M. Leigsnering, F. Ahmad, M. Amin, A. Zoubir, Multipath exploitation in through-the-wall radar imaging using sparse reconstruction. IEEE Trans. Aerosp. Electron. Syst. 50(2), 920–939 (2014)
Q. Wu, Y.D. Zhang, F. Ahmad, M.G. Amin, Compressive-sensing-based high-resolution polarimetric through-the-wall radar imaging exploiting target characteristics. IEEE Antennas Wirel. Propag. Lett. 14, 1043–1047 (2014)
A.T. Abdalla, A.H. Muqaibel, S. Al-Dharrab, Aspect dependent multipath ghost suppression in TWRI under compressive sensing framework, in 2015 international conference on communications, signal processing, and their applications (ICCSPA’15), IEEE, pp. 1–6 (2015)
V.H. Tang, A. Bouzerdoum, S.L. Phung, Radar stationary and moving indoor target localization with low-rank and sparse regularizations, in ICASSP 2019-2019 IEEE international conference on acoustics, speech and signal processing (ICASSP), IEEE, pp. 2172–2176 (2019)
W. Wang, D. Xiang, Y. Ban, J. Zhang, J. Wan, Enhanced edge detection for polarimetric SAR images using a directional span-driven adaptive window. Int. J. Remote Sens. 39(19), 6340–6357 (2018)
P. Setlur, G. Alli, L. Nuzzo, Multipath exploitation in through-wall radar imaging via point spread functions. IEEE Trans. Image Process. 22(12), 4571–4586 (2013)
K. Ashwini, R. Amutha, Compressive sensing based simultaneous fusion and compression of multi-focus images using learned dictionary. Multimed. Tools. Appl. 77(19), 25889–25904 (2018)
S. Guo, X. Yang, G. Cui, Y. Song, L. Kong, Multipath ghost suppression for through-the-wall imaging radar via array rotating. IEEE Geosci. Remote Sens. Lett. 15(6), 868–872 (2018)
M. Rani, S.B. Dhok, R.B. Deshmukh, A systematic review of compressive sensing: concepts, implementations and applications. IEEE Access 6, 4875–4894 (2018)
E. Lagunas, M.G. Amin, F. Ahmad, Nájar M, Wall mitigation techniques for indoor sensing within the compressive sensing framework, in IEEE 7th sensor array and multichannel signal processing workshop (SAM). IEEE, pp. 213–216 (2012)
Y.S. Yoon, M.G. Amin, Spatial filtering for wall-clutter mitigation in through-the-wall radar imaging. IEEE Trans. Geosci. Remote Sens. 47(9), 3192–3208 (2009)
F.H.C. Tivive, M.G. Amin, A. Bouzerdoum, Wall clutter mitigation based on eigen-analysis in through-the-wall radar imaging, in 2011 17th international conference on digital signal processing (DSP), IEEE, pp. 1–8 (2011)
F.H.C. Tivive, A. Bouzerdoum, M.G. Amin, A subspace projection approach for wall clutter mitigation in through-the-wall radar imaging. IEEE Trans. Geosci. Remote Sens. 53(4), 2108–2122 (2014)
Y. Ma, H. Hong, X. Zhu, Interaction multipath in through-the-wall radar imaging based on compressive sensing. Sensors 18(2), 549 (2018)
Y. Jia, R. Song, S. Chen, G. Wang, Y. Guo, X. Zhong, G. Cui, Multipath ghost suppression based on generative adversarial nets in through-wall radar imaging. Electronics 8(6), 626 (2019)
J. Liu, L. Kong, X. Yang, Q.H. Liu, First-order multipath ghosts’ characteristics and suppression in MIMO through-wall imaging. IEEE Geosci. Remote Sens. Lett. 13(9), 1315–1319 (2016)
X. Chen, W. Chen, Multipath ghost elimination for through-wall radar imaging. IET Radar Sonar Navig. 10(2), 299–310 (2016)
A.H. Muqaibel, A.T. Abdalla, M.T. Alkhodary, S.A. Alawsh, Through-the-wall radar imaging exploiting Pythagorean apertures with sparse reconstruction. Digit. Signal Process. 61, 86–96 (2017)
M. Rambika, A. Abdalla, B. Maiseli, A.J. Mwambela, Performance evaluation of aspect dependent-based ghost suppression methods for through-the-wall radar imaging. Tanz. J. Sci. 46(3), 903–913 (2020)
D. Yan, G. Cui, S. Guo, L. Kong, X. Yang, Liu T, Multipath ghosts location and sub-aperture based suppression algorithm for TWIR, in IEEE radar conference (RadarConf). IEEE 2016, pp. 1–4 (2016)
A.H. Muqaibel, A.T. Abdalla, M.T. Alkhodary, S. Al-Dharrab, Aspect-dependent efficient multipath ghost suppression in TWRI with sparse reconstruction. Int. J. Microw. Wirel. Technol. 9(9), 1839 (2017)
W. Zhang, M.G. Amin, F. Ahmad, A. Hoorfar, G.E. Smith, Ultrawideband impulse radar through-the-wall imaging with compressive sensing. Int. J. Antennas Propag. (2012). https://doi.org/10.1155/2012/251497
G. Gennarelli, G. Vivone, P. Braca, F. Soldovieri, M.G. Amin, Multiple extended target tracking for through-wall radars. IEEE Trans. Geosci. Remote Sens. 53(12), 6482–6494 (2015)
K. Granström, J. Bramstång, Bayesian smoothing for the extended object random matrix model. IEEE Trans. Signal Process. 67(14), 3732–3742 (2019)
M.G. Amin, High resolution through-the-wall radar imaging using extended target model, in IEEE radar conference. IEEE 2008, pp. 1–4 (2008)
A.T. Abdalla, M.T. Alkhodary, A. Muqaibel, Extended targets modelling and block agnostic sparse reconstruction in through-the-wall radar imaging: a different perspective. J. Eng. Res. 7(2) (2019)
E. Kokumo, B. Maiseli, A. Abdalla, Target-to-target interaction in through-the-wall radars under path loss compensated multipath exploitation-based signal model for sparse image reconstruction. Tanz. J. Sci. 45(3), 382–391 (2019)
L. Stanković, M. Daković, S. Stanković, I. Orović, Sparse signal reconstruction-introduction. Wiley encyclopedia of electrical and electronics engineering, pp. 1-21 (1999)
A.A. AlBeladi, A.H. Muqaibel, Evaluating compressive sensing algorithms in through-the-wall radar via F1-score. Int. J. Signal Imaging Syst. Eng. 11(3), 164–171 (2018)
D.L. Donoho, Compressed sensing. IEEE Trans. Inf. Theory 52(4), 1289–1306 (2006)
Acknowledgements
We would like to extend our sincere gratitude to the University of Dar es Salaam for funding this research under the project number COICT-ETE19048. In addition, we feel indebted to the College of Information and Communication Technologies for the financial support to finalize preparation and submission of the manuscript.
Author information
Authors and Affiliations
Contributions
MR executed experiments and produced the initial draft of the manuscript. ATA conceived the research idea and provided mathematical formulations to justify the validity of the research problem. BM wrote the final draft of the manuscript and edited language issues. IA assisted in the derivation of mathematical formulae and ensured the correctness of all mathematical formulations. AM proofread the manuscript, improved the Results and Discussion section, and corrected language issues. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Rambika, M., Abdalla, A.T., Maiseli, B. et al. Aspect dependent-based ghost suppression for extended targets in through-the-wall radar imaging under compressive sensing framework. EURASIP J. Adv. Signal Process. 2022, 63 (2022). https://doi.org/10.1186/s13634-022-00894-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13634-022-00894-z