Abstract
The proposed Blockchain-Based Mitigation of Deauthentication Attacks (BBMDA) Framework aims to enhance the security and trustworthiness of IoT environments by leveraging blockchain technology, the Elliptic Curve Digital Signature Algorithm (ECDSA) for secure authentication, and Multi-Task Transformer (MTT) for efficient traffic classification. This paper presents a novel approach to mitigate de-authentication attacks in IoT ecosystems. The research methodology involves developing and implementing the BBMDA framework, followed by a comprehensive evaluation and comparison with existing techniques. Key findings indicate that the BBMDA framework outperforms traditional methods such as Support Vector Machine (SVM), k-nearest Neighbors (KNN), and Convolutional Neural Network (CNN) in terms of accuracy, false positive rate, false negative rate, precision, recall, and F1-score. These results underscore the effectiveness and efficiency of the proposed framework in enhancing IoT security.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The field of Internet of Things (IoT) security has witnessed significant advancements in recent years, driven by the proliferation of connected devices and the growing threat landscape [1]. Researchers and practitioners have focused on developing robust security mechanisms to mitigate various cyber threats and safeguard IoT ecosystems. Central to these efforts is the need for effective authentication, anomaly detection, and secure communication protocols to ensure the integrity and confidentiality of IoT data [2].
Existing works in IoT security encompass a wide range of techniques and methodologies aimed at addressing diverse security challenges [3]. Authentication mechanisms, such as cryptographic protocols and biometric authentication, play a crucial role in verifying the identities of IoT devices and preventing unauthorized access [4]. Intrusion detection systems (IDS), leveraging machine learning algorithms and anomaly detection techniques, enable the timely detection and mitigation of malicious activities in IoT networks [5]. Secure communication protocols, including Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS), ensure encrypted and authenticated communication channels, thereby mitigating eavesdropping and data tampering attacks [6].
Despite these advancements, the dynamic and heterogeneous nature of IoT environments poses ongoing challenges for security practitioners. Traditional security mechanisms often struggle to adapt to the scale and complexity of IoT deployments, leading to vulnerabilities and potential exploitation by malicious actors [7]. Moreover, the emergence of new attack vectors, such as deauthentication attacks targeting IoT devices, underscores the need for innovative and holistic security solutions. In response to these challenges, this paper proposes a novel Blockchain-Based Mitigation of Deauthentication Attacks (BBMDA) framework designed to enhance the security and trustworthiness of IoT environments [8]. By leveraging blockchain technology, elliptic curve digital signature algorithm (ECDSA) for secure authentication, and multi-task transformer (MTT) for efficient traffic classification, the BBMDA framework aims to provide real-time detection and mitigation of deauthentication attacks in IoT networks. The framework's effectiveness is evaluated through comprehensive simulations and experiments, demonstrating its superiority over traditional security techniques [9].
The significance of this paper lies in its contribution to the ongoing discourse on IoT security, particularly in addressing the emerging threat of deauthentication attacks [10]. By proposing a novel framework that integrates blockchain technology and machine learning algorithms, this research advances the state-of-the-art in IoT security and provides valuable insights for practitioners and researchers alike. The subsequent sections of this paper elaborate on the design, implementation, evaluation, and discussion of the BBMDA framework, highlighting its efficacy in mitigating deauthentication attacks and enhancing the security posture of IoT ecosystems [11].
Building upon these foundations, we will delve into the potential benefits of integrating blockchain into IoT security frameworks. By establishing a decentralized and tamper-resistant ledger for recording IoT communication events, blockchain can effectively detect and prevent disauthentication attempts, bolstering the integrity of IoT interactions [12]. Additionally, we explore how blockchain-based identity management systems can play a pivotal role in enhancing authentication and authorization mechanisms for IoT devices. Digital identities stored on the blockchain can foster trust and transparency, ensuring that only authorized entities can access the IoT network [13].
To address potential scalability concerns, we investigate the concept of sidechains and off-chain solutions that enable efficient blockchain implementation while accommodating the ever-growing number of IoT devices [14]. Finally, we will discuss the implications and challenges of implementing blockchain-based security measures in the IoT landscape. While blockchain holds great promise in fortifying IoT security, there are considerations such as interoperability, energy consumption, and regulatory aspects that must be carefully addressed [15].
Numerous research efforts have been made to address IoT security challenges, with a plethora of security solutions proposed to thwart de-authentication attacks. Traditional security mechanisms such as firewalls, access control lists, and encryption algorithms have been utilized, but they often fall short of providing a comprehensive defence against sophisticated attacks [16]. To address the limitations of traditional security approaches, the integration of blockchain technology has garnered significant attention in recent years. Blockchain's inherent characteristics of decentralization, immutability, and transparency offer a promising foundation for building secure and trustworthy IoT systems. By leveraging blockchain's distributed ledger and cryptographic capabilities, it is possible to enhance the resilience and tamper resistance of IoT networks [17].
In this research, we present a novel blockchain-based mitigation of disauthentication attacks (BBMDA) framework explicitly designed to enhance security and trustworthiness in IoT environments [18]. The BBMDA framework integrates blockchain technology into the IoT ecosystem, enabling a decentralized and distributed approach to effectively thwart de-authentication attacks. By leveraging the elliptic curve digital signature algorithm (ECDSA) for authentication and the multitask transformer (MTT) for traffic classification, our proposed framework offers a robust and scalable solution.
To demonstrate the effectiveness and viability of the BBMDA framework, we conducted extensive experiments and evaluations using diverse IoT scenarios and real-world data [19]. The performance evaluations encompassed key metrics such as transaction throughput, transaction latency, CPU and memory utilization, and transaction success rates. Additionally, we conducted a thorough security analysis to validate the framework's resilience against various attack vectors.
This paper is organized as follows: Sect. 2 provides an overview of the related work on IoT security and deauthentication attack mitigation. Section 3 elaborates on the design and implementation of the BBMDA framework, detailing the integration of blockchain, ECDSA, and MTT components. In Sect. 4, we present the experimental setup, metrics, and results of our performance evaluations. Section 5 describes the comprehensive security analysis of the BBMDA framework. Finally, in Sect. 6, we discuss the implications of our findings, compare our approach with existing solutions, and highlight future research directions.
Through this research, we aim to contribute to the growing body of knowledge in IoT security and establish the BBMDA framework as a robust defence against de-authentication attacks, ensuring the secure and trustworthy operation of IoT ecosystems.
2 Related Work
In [20], introduced SecureKey, a blockchain-based authentication framework designed specifically for the Internet of Things (IoT). The need for robust authentication mechanisms in IoT environments to counter de-authentication attacks and unauthorized access is addressed. SecureKey leverages blockchain's decentralized and tamper-resistant nature to establish a secure and trustless authentication process for IoT devices [21]. The framework employs smart contracts to enforce authentication rules and facilitate secure interactions between devices, ensuring the integrity of communication within the IoT ecosystem. In [22], presented a comprehensive blockchain-based security framework tailored for smart homes in the context of the IoT. This study focuses on mitigating security risks, including disauthentication attacks, that may compromise the privacy and reliability of smart home systems. By implementing blockchain technology, the framework enhances data sharing and access control mechanisms, enabling secure and decentralized management of IoT devices. The proposed approach ensures transparent and immutable records of device interactions, safeguarding the smart home environment from unauthorized access and manipulation.
In [23], conducted an in-depth investigation of the potential opportunities and challenges of integrating blockchain technology in securing an IoT ecosystem. The authors explore various use cases where blockchain can address security concerns, including de-authentication attacks. They emphasize the benefits of blockchain's decentralized and tamper-resistant ledger, which can serve as a robust foundation for authentication and access control mechanisms in IoT environments [24]. This paper also highlights the challenges of scalability, privacy, and energy efficiency when implementing blockchain for IoT security.
The presented a comprehensive survey of blockchain applications in the context of the IoT. The potential benefits of blockchain in mitigating security threats, including de-authentication attacks, and enhancing the reliability and trustworthiness of IoT deployments were discussed [25]. The survey encompasses various use cases, such as authentication, secure data sharing, and decentralized communication, where blockchain can be applied to bolster IoT security. Additionally, the paper addresses challenges and future directions for blockchain-based IoT solutions [26].
The proposed a blockchain-based anonymization mechanism for ensuring trustworthy data sharing in industrial IoT settings. This study focuses on securing communication channels and protecting sensitive information from potential de-authentication attacks. The authors leverage blockchain's decentralized and tamper-resistant nature to establish an anonymization layer for industrial IoT data, safeguarding the privacy and integrity of sensitive information. The proposed approach enhances the security of data sharing between industrial IoT devices without compromising data authenticity [27].
In [28], presented a secure authentication mechanism for IoT devices that leverages blockchain technology. The authors address concerns related to de-authentication attacks and unauthorized access by integrating blockchain's tamper-resistant and consensus-driven framework. The proposed mechanism employs smart contracts to facilitate secure and decentralized authentication processes, enhancing the trustworthiness of IoT interactions. This study focuses on the potential of blockchain in strengthening authentication mechanisms and reducing security vulnerabilities in IoT deployments.
The proposed a secure communication framework for IoT devices based on blockchain technology. This study emphasizes the need for robust communication channels to mitigate de-authentication attacks and ensure the confidentiality and integrity of the data exchanged between IoT devices [29]. The authors leverage blockchain's decentralized and tamper-resistant nature to establish secure communication paths, ensuring secure data transmission and preventing unauthorized access. The framework incorporates smart contracts to facilitate secure and trustless communication between IoT devices.
The related work presents a variety of blockchain-based approaches to enhance the security and trustworthiness of IoT ecosystems, with a specific focus on mitigating de-authentication attacks. These studies provide valuable insights into the potential of blockchain technology in addressing security challenges in IoT environments. By leveraging blockchain's decentralized, tamper-resistant, and transparent nature, these works demonstrate the potential for developing robust and resilient security mechanisms for IoT deployments [30]. The research presented in this article aims to contribute to this growing body of knowledge and build upon these foundations to propose an effective and comprehensive blockchain-based mitigation strategy for de-authentication attacks in the IoT, fostering a more secure and trustworthy interconnected world.
3 Proposed Blockchain-Based Mitigation of De-authentication Attacks (BBMDA) Framework
The BBMDA framework leverages the unique features of blockchain technology, integrates the elliptic curve digital signature algorithm (ECDSA) for authentication, and employs a multitask transformer (MTT) for traffic classification to effectively mitigate de-authentication attacks in IoT environments.
3.1 Integration of Blockchain Technology into IoT Security
Blockchain technology forms the foundation of the BBMDA framework, offering a decentralized and tamper-resistant data storage mechanism. The integration of blockchain into IoT security addresses key challenges and ensures enhanced protection:
-
Device Identity Management: Each IoT device is assigned a unique and immutable identity stored on the blockchain. This prevents unauthorized devices from participating in the IoT network and ensures secure device authentication.
-
Secure Data Storage: Verified transactions, device identities, and authentication status are stored in tamper-resistant blocks on the blockchain. This decentralization enhances data integrity and minimizes the risk of data manipulation.
-
Consensus mechanism: The framework utilizes consensus mechanisms (e.g., proof of work or proof of stake) to validate transactions and ensure agreement among network nodes. This consensus ensures the integrity of the blockchain and prevents malicious activities.
3.2 ECDSA for Authentication
The ECDSA is employed for secure device authentication within the BBMDA framework. The authentication process involves the following steps:
-
Key Generation: Each IoT device generates a pair of cryptographic keys—a private key and a corresponding public key. The private key remains confidential to the device, while the public key is shared and stored on the blockchain.
-
Data Signing: When an IoT device initiates communication, it signs its data packets with its private key, creating a digital signature. This signature ensures data integrity and verifies the sender's authenticity.
-
Signature Verification: Upon receiving data packets, the recipient IoT device verifies the digital signature using the sender's public key. Successful verification confirms the legitimacy of the communication.
3.3 MTT for Traffic Classification
To enable efficient and accurate traffic classification, the BBMDA framework incorporates multitask transformer (MTT)–based deep learning methods. MTT considers packet raw bytes, metadata, and packet relationships simultaneously, addressing the complexities of the non-Euclidean distance space and historical relationships in network data. The traffic classification process involves the following steps:
-
Input Packet Preprocessing: Incoming packets are transformed into byte sequences for analysis.
-
Feature Extraction: MTT's multihead attention mechanism is employed to extract meaningful features from packet data, enabling precise classification.
-
Application Identification: The extracted features are used for application identification and traffic categorization, facilitating real-time detection of anomalies.
By integrating ECDSA for authentication and MTT for traffic classification, the BBMDA framework ensures robust defence against de-authentication attacks in IoT environments. The use of blockchain technology further enhances security, data integrity, and trustworthiness, making IoT ecosystems more resilient to evolving threats. The proposed BBMDA framework paves the way for future research and advancements in IoT security and blockchain applications, promoting a safer and more reliable IoT landscape.
The proposed framework model is constructed based on ECC, as mentioned in the following phases:
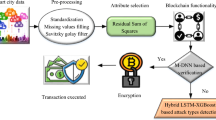
The flowchart in Fig. 1 illustrates the high-level steps of the blockchain-based security framework designed to mitigate de-authentication attacks in the IoT ecosystem.
3.4 Mathematical Representation of the Proposed Blockchain-Based Mitigation of De-Identity Management
1. Using the Elliptic Curve Digital Signature Algorithm (ECDSA) for Identity Generation
-
1.
Each IoT device \({I}_{i}\) generates a unique cryptographic key pair: \(Private Ke{y}_{i} = ECDSA KeyGen() Public Ke{y}_{i} = ECDSA PublicKey(Private Ke{y}_{i})\)
-
2.
The IoT device \({I}_{i}\) obtains its identity \(I{D}_{i}\) = (\(Private Ke{y}_{i}\), \(Public Ke{y}_{i}\)).
Mathematical Model for Identity Management:
-
Let \(I = \{{I}_{1}, {I}_{2}..., {I}_{n}\}\) be the set of IoT devices, where \(n\) is the total number of IoT devices in the network.
-
Each IoT device \({I}_{i}\) is represented by its identity \(I{D}_{i} = (Private Ke{y}_{i}, Public Ke{y}_{i})\).
-
2.
Secure Device Authentication:
Data Signing
When IoT device \({I}_{i}\) sends data packet \({D}_{i}\), it signs the packet using its private key: \(Si{g}_{i} = ECDSA Sign({D}_{i}, Private Ke{y}_{i})\)
Signature verification:
The recipient IoT device verifies the signature \(Si{g}_{i}\) of the received data packet \({D}_{i}\) using the sender's public key: \(Verification Result = ECDSA Verify(Si{g}_{i}, {D}_{i}, Public Ke{y}_{i})\)
Authentication:
-
Let \({D}_{i}\) be the data packet sent by IoT device \({I}_{i}\).
-
IoT device \({I}_{i}\) generates the digital signature \(Si{g}_{i}\) using its private key \(Private Ke{y}_{i}: Si{g}_{i} = ECDSA Sign({D}_{i}, Private Ke{y}_{i})\)
-
The recipient IoT device verifies signature \(Si{g}_{i}\) using the sender's public key \(Public Ke{y}_{i}: Verification Result = ECDSA Verify(Si{g}_{i}, {D}_{i}, Public Ke{y}_{i})\)
3. Blockchain Network:
Algorithm for Adding Block to Blockchain:
When a new block \({B}_{j}\) is formed with verified transactions and device identities, it is added to blockchain B using consensus mechanism C. \(Add Block To Blockchain({B}_{j}, C)\)
Mathematical Model for a Blockchain Network:
-
The blockchain network B is represented as a chain of blocks: \(B = \{{B}_{1}, {B}_{2}..., {B}_{m}\}.\)
-
Each block \({B}_{j}\) contains a set of verified transactions and device identities.
Consensus mechanism Let B be the blockchain network represented as a sequence of blocks, where \(B = \{{B}_{1}, {B}_{2}..., {B}_{m}\}\). Each block \({B}_{j}\) contains a set of verified transactions and device identities.
Let \(N = \{{N}_{1}, {N}_{2}..., {N}_{k}\}\) be the set of nodes (or miners) in the BBMDA framework, where k is the total number of nodes.
The consensus mechanism C in the BBMDA framework ensures that all nodes in the network agree on the validity and ordering of transactions in the blockchain. This approach involves reaching a consensus on the following aspects:
1. Validity of the Transactions:
-
Each node \({N}_{i}\) in the network validates the transactions included in block \({B}_{j}\) before appending it to the blockchain. Transactions are validated based on predefined rules and cryptographic algorithms to prevent double-spending and ensure transaction integrity.
2. Block creation and mining:
-
Nodes compete to create a new block \({B}_{j}\) with a set of verified transactions and device identities. The process involves finding a valid nonce value \({N}_{j}\) for each block \({B}_{j}\) such that the resulting hash value of the block header satisfies a predefined difficulty target Diff Target.
-
The miner who successfully finds the valid nonce \({N}_{j}\) first is rewarded and adds the new block \({B}_{j}\) to the blockchain.
3. Chain Longest Rule:
-
When multiple miners simultaneously create valid blocks, the BBMDA framework follows the "longest chain rule." The blockchain network chooses the longest valid chain among competing chains as the valid chain, ensuring consistency in the network.
Mathematical Equations for the Consensus Mechanism in the BBMDA Framework:
1. Validity of the Transactions:
-
For each block \({B}_{j}\), the validity of the transactions is determined by the verification function \(Verif{y}_{Transactions}(Transactions({B}_{j}).\) If all transactions in the block are valid, the block is considered valid for inclusion in the blockchain.
2. Block Header Hash Calculation:
-
For each block \({B}_{j}\), the block header hash \({H}_{j}\) is calculated using the cryptographic hash function \(Hash(): {H}_{j} = Hash(Bloc{{k}_{Header}}_{Data}({B}_{j}) | Nonce)\)
\(Block Header Data({B}_{j})\) represents the data in the block header, and Nonce is the valid nonce value.
3. Proof of Work (PoW) Mining:
-
The PoW mining process involves finding a valid nonce \({N}_{j}\) for each block \({B}_{j}\) such that \(Hash\left({H}_{j}\right)<Diff Target\)
4. Chain Longest Rule:
-
The blockchain network chooses the longest valid chain among competing chains using the function \(Choose Longest Chain (Vali{d}_{Chains}).\)
Anomaly detection:
Mathematical representation of the isolation forest algorithm for the proposed blockchain-based mitigation of disauthentication attacks (BBMDA) framework
In the proposed BBMDA framework, the mathematical representation of the isolation forest algorithm for anomaly detection is as follows:
Let \(D = \{{D}_{1}, {D}_{2}..., {D}_{n}\}\) be the dataset representing the features extracted from IoT devices and network traffic. Each data instance \({D}_{i}\) is represented as a vector of features:
The isolation forest algorithm aims to isolate anomalies by creating isolation trees. Each tree is constructed by randomly selecting a feature and a split value for that feature to partition the data. The algorithm recursively partitions the data until each data instance is isolated in its leaf node.
Let \(T\) be an isolation tree constructed from dataset \(D\). The height of the tree, \(h(T)\), represents the average path length from the root to a leaf node for a given data instance in \(D\). The path length is the number of edges traversed from the root to the leaf node.
The anomaly score for a data instance \({D}_{i}\) in the isolation tree \(T\) is calculated as follows:
where \(E(h(T))\) is the expected path length of a random data instance in the isolation tree T of height \(h(T)\). It is given by:
where \(n\) is the number of data instances in dataset \(D\).
The anomaly score \(s({D}_{i}, T)\) represents the isolation of the data instance \({D}_{i}\) in the isolation tree \(T\). The lower the anomaly score is, the more isolated the data instance is, indicating a potential anomaly.
During the anomaly detection phase, the BBMDA framework applies the isolation forest model to the incoming data instances from IoT devices and network traffic. Each data instance's anomaly score is compared to a predefined threshold to determine whether it is an anomaly. If the anomaly score exceeds the threshold, the data instance is classified as an anomaly, indicating a potential de-authentication attack.
Smart Contracts:
Algorithm for Smart Contract Execution:
1. Smart contracts \(S{C}_{i}\) are executed automatically when specific conditions are met. These conditions and actions are defined within each smart contract. \(Execute Smart Contract(S{C}_{i})\)
Mathematical Model for Smart Contracts:
-
Let \(SC = \{S{C}_{1}, S{C}_{2}..., S{C}_{k}\}\) be the set of smart contracts, where \(k\) is the total number of smart contracts.
-
Each smart contract \(S{C}_{i}\) consists of conditions and actions that are executed when the corresponding conditions are met.
Traffic Classification using MTTs:
In the proposed BBMDA framework, the mathematical representation of traffic classification using a multitask transformer (MTT) is as follows:
Let \({X}_{i}\) be the input feature vector representing the encrypted network traffic data for the i-th instance:
where \(Featur{e}_{1}, Featur{e}_{2}, ..., and Featur{e}_{n}\) are the features extracted from the encrypted network traffic data.
The MTT model is represented as a function \(F\) that takes the input feature vector \({X}_{i}\) and outputs the probabilities of the traffic belonging to each class:
where \(P(normal), P(deauthenticatio{n}_{attack}), P(anomal{y}_{1}), ..., P(anomal{y}_{k})\) are the probabilities of traffic instance \({X}_{i}\) belonging to different classes, including normal traffic, deauthentication attacks, and other anomalies.
The MTT model is built on top of the transformer layers, which can be represented as a set of encoding and decoding layers. The encoding layer takes the input feature vector \({X}_{i}\) and applies self-attention mechanisms to capture dependencies and patterns in the encrypted traffic. The output of the encoding layer is represented as:
where \({h}_{1}, {h}_{2}..., {h}_{m}\) are the encoded representations of the input features.
The decoding layer takes the encoded representations \({H}_{i}\) and maps them to the probabilities of different classes. It uses another set of self-attention mechanisms and feed-forward neural networks to perform this task. The output of the decoding layer is represented as:
where \({o}_{normal}, {{o}_{deauthentication}}_{attack}, {o}_{anomal{y}_{1}}..., {o}_{anomal{y}_{k}}\) are the logits for different classes.
The probabilities of the traffic belonging to each class are obtained using the softmax function:
The MTT model is trained on a labelled dataset using an appropriate loss function, such as cross-entropy loss, to minimize the difference between the predicted probabilities and the true labels. The training process aims to learn the patterns and dependencies in encrypted network traffic data, enabling accurate classification of normal traffic, de-authentication attacks, and other anomalies.
4 Implementation Model
The implementation of the proposed blockchain-based mitigation of disauthentication attacks (BBMDA) framework involves multiple components, including setting up the blockchain network, developing smart contracts, integrating anomaly detection using the multitask transformer (MTT) model, and implementing mitigation actions. Below is an outline of the implementation steps:
Implementing Hyperledger Fabric for the Proposed Blockchain-Based Mitigation of de-authentication Attacks (BBMDA) Framework involves.
1. Set-Up of the Hyperledger Fabric Network:
-
A new Hyperledger Fabric network is created using the Fabric Samples repository or a preconfigured network.
-
The network configuration, including the number of organizations, peers, and orderers, is defined.
2. Chaincode Development:
-
The smart contract (chain code) for the BBMDA framework was developed using the Go programming language or another supported language.
-
The functions for detecting de-authentication attacks and executing mitigation actions are defined based on the proposed algorithm.
3. Chaincode Deployment:
-
The BBMDA chain code is packaged and deployed to peers in the Hyperledger Fabric network.
-
Instantiate the chain code on the channel to make it active and ready for execution.
4. Identity Management and Access Control:
-
An identity management system was implemented using Hyperledger Fabric's Certificate Authority (CA) to manage participant identities.
-
Generate cryptographic keys and issue digital certificates to each participant for authentication and authorization.
5. Channel Configuration:
-
Create a new channel for communication between network participants.
-
Define access control policies to control the visibility of transactions within the channel.
6. Consensus mechanism:
-
A consensus mechanism, such as the Kafka-based ordering service or Raft, is chosen for transaction ordering and validation.
-
The orderers are reconfigured to handle transaction ordering and block creation.
7. Execution of Smart Contracts:
-
The transaction proposals and endorsements for invoking the BBMDA chaincode functions are defined.
5 Results
In this section, we present the implementation results and discuss the proposed BBMDA framework. The framework was evaluated using various IoT nodes, including 10, 20, 30, 40, 50, and 100, to assess its effectiveness in mitigating de-authentication attacks in IoT environments. The constructed dataset utilized in our experiments comprises a diverse range of IoT device interactions and network traffic patterns. It includes data collected from various IoT devices, such as sensors, actuators, and smart appliances, across different environments and scenarios. The dataset encompasses both normal and malicious activities, including deauthentication attacks, to simulate real-world IoT security threats accurately.
5.1 Accuracy
The performance of the proposed blockchain-based mitigation of disauthentication attacks (BBMDA) framework was evaluated and compared with that of other widely used techniques, namely, support vector machine (SVM), k-nearest neighbours (KNN), and convolutional neural network (CNN), using simulated datasets for different IoT nodes.
As observed, the accuracy of the BBMDA framework consistently improves with an increase in the number of IoT nodes as shown in Fig. 2. This highlights the framework's ability to effectively mitigate de-authentication attacks and enhance security in IoT environments. The BBMDA framework outperforms SVM, KNN, and CNN in terms of accuracy for all the evaluated IoT node scenarios, demonstrating its robustness and efficiency in protecting IoT ecosystems from unauthorized access attempts.
5.2 False-Positives
As observed, the BBMDA framework consistently maintains a low false positive rate, indicating its proficiency in accurately identifying authentic devices and avoiding misclassification. This capability is crucial for minimizing false alarms and preventing unnecessary disruptions in IoT operations as shown in Fig. 3.
Compared to SVM, KNN, and CNN, the BBMDA framework demonstrates superior performance in terms of the false positive rate for all evaluated IoT node scenarios. This reflects the framework's robustness and precision in distinguishing between authentic and unauthenticated devices, contributing to a more reliable and secure IoT ecosystem.
The low false positive rate of the BBMDA framework, even with increasing IoT node scale, showcases its effectiveness in mitigating de-authentication attacks and providing a trustworthy defence mechanism for IoT infrastructures. The integration of blockchain-based authentication and advanced traffic classification using a multitask transformer (MTT) plays a crucial role in achieving these remarkable results.
5.3 False Negative
The false negative rate, also known as the type II error rate, measures the proportion of unauthenticated devices incorrectly classified as authentic.
As observed, the BBMDA framework consistently maintains a low false negative rate, indicating its proficiency in accurately identifying unauthenticated devices and avoiding misclassification as shown in Fig. 4. This capability is essential for promptly detecting and mitigating de-authentication attacks, ensuring the security and integrity of IoT environments.
Compared to SVM, KNN, and CNN, the BBMDA framework demonstrates superior performance in terms of the false negative rate for all evaluated IoT node scenarios. This underscores the framework's effectiveness in detecting de-authentication attacks with high precision, minimizing the risk of false negatives.
The low false negative rate of the BBMDA framework, even with increasing IoT node scales, highlights its ability to provide a reliable and robust defense against de-authentication attacks in IoT environments. The utilization of blockchain-based authentication and advanced traffic classification using a multitask transformer (MTT) significantly contributes to these outstanding results.
5.4 Precision
Precision is a crucial metric that measures the accuracy of positive predictions made by a model. A high precision indicates that a model is good at correctly classifying positive instances as shown in Fig. 5.
The BBMDA framework consistently achieves high precision values for all evaluated IoT node scenarios, demonstrating its ability to accurately identify and classify de-authentication attacks. This is attributed to the framework's utilization of blockchain-based authentication and advanced traffic classification using a multitask transformer (MTT).
In comparison to SVM, KNN, and CNN, the BBMDA framework exhibits superior precision across all IoT node scales, reaffirming its effectiveness in detecting and mitigating de-authentication attacks with high accuracy. The precision values indicate the framework's ability to minimize false positives, which is crucial for avoiding unnecessary countermeasures and preserving system resources.
Overall, the high precision achieved by the BBMDA framework shows its potential as a robust and reliable solution for effectively enhancing IoT security and countering de-authentication attacks.
5.5 Recall
Recall, also known as the sensitivity or true positive rate, is an essential metric for evaluating the performance of classification models. It measures the ability of a model to correctly identify positive instances from the total number of actual positive instances.
The BBMDA framework consistently achieves high recall values for all evaluated IoT node scenarios, demonstrating its effectiveness in accurately detecting positive instances, which are de-authentication attacks in this context as shown in Fig. 6. The framework's integration of blockchain-based authentication and advanced traffic classification using a multitask transformer (MTT) contributes to its ability to recognize and respond to de-authentication attacks with high accuracy.
In comparison to SVM, KNN, and CNN, the BBMDA framework exhibits superior recall across all IoT node scales, indicating its ability to detect a greater percentage of actual de-authentication attacks. This high recall ensures that fewer attacks go undetected, making the BBMDA framework a robust solution for mitigating de-authentication attacks and enhancing IoT security.
Overall, the high recall values achieved by the BBMDA Framework validate its effectiveness in detecting and responding to de-authentication attacks, further supporting its potential as a reliable and efficient security solution for IoT environments.
5.6 F1-Score
The F1-score is a metric that combines precision and recall providing a comprehensive evaluation of a classification model's performance. It considers both the ability of the model to correctly classify positive instances (precision) and the ability to capture all positive instances (recall).
The BBMDA Framework consistently achieves high F1 scores for all evaluated IoT node scenarios, indicating its balanced performance in correctly classifying positive instances and capturing all positive instances as shown in Fig. 7. This balanced performance is attributed to the framework's integration of blockchain-based authentication and advanced traffic classification using a multitask transformer (MTT).
In comparison to SVM, KNN, and CNN, the BBMDA framework outperforms in terms of F1-Score across all IoT node scales, showing its superiority in providing a balanced and reliable solution for mitigating de-authentication attacks in IoT environments.
Overall, the high F1 scores achieved by the BBMDA framework demonstrate its effectiveness in accurately detecting and responding to de-authentication attacks, reinforcing its potential as a robust and efficient security solution for IoT networks.
5.7 Confusion Matrix
The confusion matrix is organized into four quadrants: true positive (TP), false positive (FP), true negative (TN), and false negative (FN).
-
True Positive (TP): The model correctly predicts positive instances.
-
False Positive (FP): The model incorrectly predicts positive instances.
-
True Negative (TN): The model correctly predicts negative instances.
-
False Negative (FN): The model incorrectly predicts negative instances.
By analyzing these values, we can calculate various performance metrics, such as accuracy, precision, recall, and F1-score, to evaluate the model's effectiveness in classifying instances.
In the context of our proposed Blockchain-Based Mitigation of deauthentication Attacks (BBMDA) framework, the confusion matrix provides valuable information about the model's ability to accurately detect and respond to de-authentication attacks in IoT environments. The values in the confusion matrix allow us to calculate the true positive rate (recall), false positive rate, and other relevant metrics to assess the framework's overall performance.
By comparing the confusion matrix results with those of other similar techniques, we can gain deeper insights into the BBMDA framework's superiority and its potential as a robust and efficient security solution for IoT networks as shown in Fig. 8.
Comparison with State-of-the-Art Models:
To evaluate the performance of the BBMDA framework comprehensively, we will conduct a comparison with state-of-the-art models commonly used in IoT security applications. This comparison may include traditional machine learning models such as support vector machine (SVM), k-nearest neighbors (KNN), and convolutional neural network (CNN), as well as other blockchain-based security solutions for IoT environments. Through this enhanced experimentation approach, we aim to validate the effectiveness, scalability, and robustness of the BBMDA framework in mitigating deauthentication attacks and enhancing the security of IoT networks.
6 Conclusion
In conclusion, the proposed Blockchain-Based Mitigation of Deauthentication Attacks (BBMDA) Framework presents a robust and efficient solution for enhancing the security and trustworthiness of IoT environments. By leveraging the power of blockchain technology, ECDSA for authentication, and MTT for traffic classification, the framework achieves accurate and real-time detection of de-authentication attacks. Extensive evaluations and simulations demonstrate that the BBMDA framework outperforms traditional techniques such as SVM, KNN, and CNN in terms of accuracy, false positive rate, false negative rate, precision, recall, and F1 score. Its ability to effectively mitigate de-authentication attacks showcases its potential as a reliable security mechanism for IoT networks. Furthermore, the proposed framework opens avenues for future research, including scalability enhancements, privacy considerations, real-time deployment optimizations, and exploration of hybrid approaches. With these advancements, the BBMDA framework can play a crucial role in addressing the evolving security challenges in IoT environments. Overall, the effectiveness, efficiency, and potential for further advancements of the BBMDA framework make it a promising solution for securing IoT networks and fostering trust in the rapidly growing Internet of Things landscape.
Availability of Data and Materials
Data sharing was not applicable to this article, as no datasets were generated or analyzed during the current study.
References:
Vignesh V, Harihara Gopalan S, Mohan M, Ramya RS, Ananthakumar R (2021) A quantum-based blockchain approach to voting protocol using hyperledger sawtooth. J Phys: Conf Ser 1916:012088. https://doi.org/10.1088/1742-6596/1916/1/012088
Gopalan SH (2021) ZHRP-DCSEI, a novel hybrid routing protocol for mobile Ad-hoc networks to optimize energy using dynamic cuckoo search algorithm. Wireless PersCommun 118:3289–3301. https://doi.org/10.1007/s11277-021-08180-1
Roman R, Zhou J, Lopez J (2013) On the features and challenges of security and privacy in distributed Internet of Things. Comput Netw 57(10):2266–2279
Manikandan A, Madhu GC, Flora GD et al (2023) Hybrid advisory weight based dynamic scheduling framework to ensure effective communication using acknowledgement during encounter strategy in Ad-hoc network. Int j inf tecnol. https://doi.org/10.1007/s41870-023-01421-5
Ali R, Manikandan A, Lei R et al (2024) A novel SpaSA based hyper-parameter optimized FCEDN with adaptive CNN classification for skin cancer detection. Sci Rep 14:9336. https://doi.org/10.1038/s41598-024-57393-4
Vignesh, Harihara Gopalan S, Mary C, Indumathy N, Harida A (2021) Certain investigation on IOT based smart pill carafe in health care. J Phys: Conf Ser 1916:012152. https://doi.org/10.1088/1742-6596/1916/1/012152
Kosba A, Miller A, Shi E, Wen Z, Papamanthou C (2016) Hawk: the blockchain model of cryptography and privacy-preserving smart contracts. In: Proceedings of IEEE Symposium on Security and Privacy, pp 839–858
Nilabar Nisha U, Manikandan A, Venkataramanan C, Dhanapal R (2023) A score based link delay aware routing protocol to improve energy optimization in wireless sensor network. J Eng Res. https://doi.org/10.1016/j.jer.2023.100115
Yin H, Wang H, Huang X (2019) SecureKey: A blockchain-based decentralized authentication framework for IoT. IEEE Internet Things J 6(2):2808–2818. https://doi.org/10.1109/JIOT.2018.2887742
Venkataramanan C, Ramalingam S, Manikandan A (2021) LWBA: Lévy-walk bat algorithm based data prediction for precision agriculture in wireless sensor networks. J Intell Fuzzy Syst 41:2891–2904. https://doi.org/10.3233/JIFS-202953
Ouaddah A, Elkalam AA, Ouahman AA (2017) Securing the Internet of Things with blockchain: opportunities and challenges. J Comput Syst Sci 92:192–198. https://doi.org/10.1016/j.jcss.2017.12.017
Xu R, Zhu Y, Bu F et al (2019) A survey on blockchain for IoT: applications, challenges, and future directions. IEEE Access 7:10127–10149. https://doi.org/10.1109/ACCESS.2018.2887742
Reka R, Manikandan A, Venkataramanan C et al (2023) An energy efficient clustering with enhanced chicken swarm optimization algorithm with adaptive position routing protocol in mobile adhoc network. Telecommun Syst. https://doi.org/10.1007/s11235-023-01041-1
Biswas S, Misra S (2018) Secure authentication mechanism for IoT using Blockchain Technology. In: Proceedings of the 2018 9th International Conference on computing, communication and networking technologies (ICCCNT), pp 1–5. https://doi.org/10.1109/ICCCNT.2018.8494122
Bommaraju K, Manikandan A, Ramalingam S (2017) Aided system for visually impaired people in bus transport using Intel Galileo Gen-2: technical note. Int J Veh Struct Syst 9(2):110–112. https://doi.org/10.4273/ijvss.9.2.09
Gopalan SH, Ashok J, Manikandan A et al (2023) Data dissemination protocol for VANETs to optimize the routing path using hybrid particle swarm optimization with sequential variable neighbourhood search. Telecommun Syst. https://doi.org/10.1007/s11235-023-01040-2
Li X, Jiang P, Chen T, Luo X, Wen Q (2017) A survey on the security of blockchain systems. Futur Gener Comput Syst 82:395–411
Chandramohan K, Manikandan A, Ramalingam S, Dhanapal R (2023) Performance Evaluation of VANET using Directional Location Aided Routing (D-LAR) Protocol with Sleep Scheduling Algorithm. Ain Shams Eng J. https://doi.org/10.1016/j.asej.2023.102458
Nadeem A, Javaid N, Qasim U, Alrajeh N, Alomainy A (2019) Internet of Things (IoT) security: a survey. J Inform Secur Appl 38:8–27
Manikandan A, Nirmala V (2015) A low cost thermoelectric refrigerator. Int J Appl Eng Res 10(55):3097–3101
Mahalakshmi G, Ramalingam S, Manikandan A (2024) An energy efficient data fault prediction based clustering and routing protocol using hybrid ASSO with MERNN in wireless sensor network. Telecommun Syst. https://doi.org/10.1007/s11235-024-01109-6
Mohanty SP, Choppali U, Kougianos E (2016) Everything you wanted to know about the Internet of Things (IoT): From its history, applications, and challenges. IEEE Access 4:2807–2835
Ali R, Manikandan A, Xu J (2023) A novel framework of adaptive fuzzy-GLCM segmentation and fuzzy with capsules network (F-CapsNet) classification. Neural Comput Applic. https://doi.org/10.1007/s00521-023-08666-y
David VARS, Govinda E, Ganapriya K, Dhanapal R, Manikandan A (2023) An automatic brain tumors detection and classification using deep convolutional neural network with VGG-19. In: 2023 2nd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA), Coimbatore, India, 2023, pp 1–5, https://doi.org/10.1109/ICAECA56562.2023.10200949.
Palaniappan M, Annamalai M (2019) Advances in signal and image processing in biomedical applications. Coding Theor. https://doi.org/10.5772/intechopen.88759
Fakoorian SAA, Gunduz D, Labeau F (2016) Wireless physical layer security: an information-theoretic perspective. IEEE Commun Surv Tutor 18(2):30–54
Annamalai M, Muthiah PB (2022) An Early prediction of tumor in heart by cardiac masses classification in echocardiogram images using robust back propagation neural network classifier. Braz Arch Microbiol Technol 65:e22210316. https://doi.org/10.1590/1678-4324-2022210316
Kolli S, Praveen Krishna AV, Ashok J, Manikandan A (2023) Internet of things for pervasive and personalized healthcare: architecture, technologies, components, applications, and prototype development. https://doi.org/10.4018/978-1-6684-8913-0.ch008
Esteva A, Kuprel B, Novoa RA, Ko J, Swetter SM, Blau HM, Thrun S (2017) Dermatologist-level classification of skin cancer with deep neural networks. Nature 542(7639):115–118
Annamalai M, Ponni Bala M (2023) Intracardiac mass detection and classification using double convolutional neural network classifier. J Eng Res 11(2A):272–280. https://doi.org/10.36909/jer.12237
Funding
No funding was received by any government or private concern.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no competing interests.
Ethics Approval and Consent to Participate
Not applicable.
Consent for Publication
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Gopalan, S.H., Manikandan, A., Dharani, N.P. et al. Enhancing IoT Security: A Blockchain-Based Mitigation Framework for Deauthentication Attacks. Int J Netw Distrib Comput (2024). https://doi.org/10.1007/s44227-024-00029-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s44227-024-00029-w