Abstract
As Edge AI systems become more prevalent, ensuring data privacy and security in these decentralized networks is essential. In this work, a novel hybrid cryptographic mechanism was presented by combining Ant Lion Optimization (ALO) and Diffie–Hellman-based Twofish cryptography (DHT) for secure data transmission. The developed work collects the data from the created edge AI system and processes it using the Autoencoder. The Autoencoder learns the data patterns and identifies the malicious data entry. The Diffie–Hellman (DH) key exchange generates a shared secret key for encryption, while the ALO optimizes the key exchange and improves security performance. Further, the Twofish algorithm performs the data encryption using a generated secret key, preventing security threats during transmission. The implementation results of the study show that it achieved a higher accuracy of 99.45%, lower time consumption of 2 s, minimum delay of 0.8 s, and reduced energy consumption of 3.2 mJ.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The past few years have seen a rise in Artificial Intelligence (AI) services and applications, ranging from audio and video surveillance to personal assistants and recommendation engines, thanks to advances in deep learning [1]. Since mobile computing and the Internet of Things (IoT) have become so popular in recent years, millions of IoT and mobile devices have been connected to the Internet, producing billions of information at the network edge [2]. Motivated by this trend, it is imperative to push the boundaries of AI to the edge of the network to fully realize the potential of edge big data [3]. It acknowledged that Edge Computing (EC), a new paradigm that shifts computing services and workloads from the network core to the edge, is a potential way to meet this demand [4]. Social scientists, philosophers, and lawyers have historically been the ones to address privacy as a social and legal issue [5]. However, the widespread use of different software programs in the framework of fundamental e-services necessitates the adoption of additional technological safeguards to ensure people's electronic privacy [6]. In these days, maintaining privacy involves minimizing the amount of data gathered and kept on file and erasing it as soon as it is no longer needed [7]. Most e-services available today rely on stored data to identify customers, their preferences, and their past transaction history. Integrating such data, however, will frequently result in a privacy violation [8].
A significant step toward the next revolution in the IoT space is believed to be taken by intelligent edge or the combination of EC with digital innovations like AI, data analytics, machine learning (ML), big data, and cloud computing [9]. To optimize the possibility of data analytics in real-time with the slightest delay, EAI is used for intelligently researching, gathering, storing, and processing massive amounts of IoT data [10]. Furthermore, intelligent edge systems can handle erratic and imprecise problems like mobility, security, and dependability in addition to lowering bandwidth usage and speeding up response times [11]. Soft Computing (SC), which aims to provide tractable, reliable, and affordable solutions, encompasses numerous methods that can facilitate the shift to intelligent edge systems. Smart speakers, head-mounted displays, car sensors, drones, security cameras, business and consumer robots, PCs, smartphones, and tablets will be the leading-edge devices generated by AI and SC in quantity [12, 13]. SC approaches can handle various EC issues, including mobility, data accumulation, interoperability, and security, by combining algorithms, approximate models, and unpredictable and random algorithmic actions [14]. The use of SC methods is becoming more popular in various academic and industrial domains. One of the most noteworthy features of these tools is their capacity to handle when making decisions using hazy or inaccurate info [15, 16]. Similar circumstances frequently arise in requirements engineering. Through data processing at the source, edge-based SC can offer increased privacy and security in IoT [17]. The most challenging tasks in data mining are high-dimensionality datasets, incomplete and non-standard data, changing data, overfitting, integration, mixed media data, and knowledge [18]. Due to their dispersed nature and frequent placement in public or semi-public areas, edge AI devices are vulnerable to physical and cyberattacks. Furthermore, handling sensitive data by these devices frequently raises the possibility of data breaches. Concerns about data leaks and exploitation are prevalent when using AI systems. Data breach and misuse are risks because an AI model needs a lot of personal information to be trained. Large volumes of (personal) data are required for AI systems, and if this data ends up in the wrong hands, it could be exploited for evil things like identity theft.
Due to various limitations, i.e., computational complexity and more delay in cloud computing are overtaken by EC for efficient and fair resource allocation, such as power and battery lifetime in IoT-based industrial applications [19]. However, the challenging issue in these power-hungry, short battery lifetime, and delay-intolerant portable devices needs to be more appropriate and efficient classical trends of fair resource allotment [20]. So, in this paper, we design an Ant Lion Optimization assisted Diffie–Hellman-based Twofish cryptography (ALO-DHT) to enhance security and privacy. The developed model reduces the computational cost and latency and provides better security. The created model's primary goal is to create a shared secret without sending it over the Internet. The two can encrypt and decode data or conversations using a public key using symmetric cryptography and the developed model. Protect the data from attacks and unlawful access as well. The main motive is to generate effective Data Transmission in Edge AI Networks to enhance security and privacy. The main aim of the developed model is to enhance the security of the edge AI system using soft computing and cryptographic techniques. The developed model preserves security and privacy during data transmission using an optimized hybrid cryptographic algorithm. The key contribution of the developed model is detailed below:
-
Design an optimized hybrid cryptographic algorithm for preserving security and privacy during data transmission.
-
Combines the Ant-lion optimization with the hybrid Diffie–Hellman-based Twofish approach (ALO-DHT) for enhancing security.
-
An edge AI environment is created with edge computing devices and AI-enabled sensors.
-
To check the malicious data entry in the created environment, an autoencoder neural network-based attack prediction module was designed.
-
Further, the processed data is encrypted using the proposed cryptography to ensure privacy and security during transmission.
-
The Diffie–Hellman approach facilitates the secure key exchange process between the source and destination devices, while the Twofish algorithm performs encryption using the shared key.
-
Finally, the gain performance of the developed model is validated with other prevailing techniques in terms of accuracy, recall, time, delay, precision, and energy consumption.
The organization of the paper is as follows: Sect. 2 details the literature survey, Sect. 3 describes the proposed methodology, Sect. 4 details the results and discussion of the developed model, and Sect. 5 ends with a conclusion.
2 Related Works
To distinguish Edge Intelligence (EI) into AI on edge and AI for edge, Shuiguang et al. [21] created an entirely new computing paradigm. With the aid of well-liked and beneficial AI technologies, the former concentrates on offering more optimal solutions to significant EC problems, while the latter investigates how to complete the entire AI model-building process, that is model training and inference on edge. With a more comprehensive viewpoint, this paper offers insights into this emerging interdisciplinary field. Discussing the fundamental ideas and the research roadmap should give prospective future EI researchers the necessary background knowledge.
Meanwhile, AI-based precise and intelligent resource management has gained significant attention, particularly in industrial applications. The availability and computation speed of IoT-based devices in industries will be increased using the integration of AI at the edge. A forward central dynamic and available (FCDA) system was proposed by Hassan et al. [22] by modifying the sensing and transfer processes' running times in portable IoT devices. Create a data reliability model for edge AI-powered IoT devices. For appropriate industrial platform monitoring, two key cases are presented, namely product processing and noise and fault diagnosis. The suggested FCDAA improves energy utilization and battery lifetime, according to an experimental test-bed.
Sheikh et al. [23] suggest a novel EI computing system for confidentiality image classification in the IoT. In particular, the autoencoder will be developed independently at each edge device, and the edge server will receive the latent vectors for classification training. Without involving the server, every edge device's autoencoder is developed independently. By sending latent vectors, the suggested method protects end users' confidentiality and does not have a high communication cost. The experimental results show how well images are classified with different design parameters, like the autoencoder's data compression ratio and complexities.
Because of distributed denial of service (DDOS) attacks, the improper use of cloud design services and resources has become a regular problem in day-to-day operations. Since DDOS attacks are highly sophisticated and are expanding quickly, identifying and implementing countermeasures is a difficult task. Mugunthan [24] created autonomous detection with the SC method to counteract rate-DDOS assaults in the cloud's structure. The suggested approach makes use of the Random Forest to categorize detected attacks. Moreover, the Hidden Markov Model is developed to observe network flow. The recommended method is assessed to gage the level of enhancement in performance.
The utilization of SC techniques facilitates the identification of malicious activities within social networks. SC dominates research in this field because of its robustness and low-cost solutions for identifying undesired activities. Sathish [25] employs a combination of SC methodologies and an improved SC method to identify intrusions that result in security problems within social networks. The suggested approach uses an improved SC procedure involving feature reduction, pre-processing, clustering, and classification to create a security model that is more successful than conventional computations at recognizing social network misuse.
One encoding method that aids in the encoding of data that must be saved in the cloud is homomorphic encryption. The Modified Particle Swarm Optimization Algorithm, which Adwait et al. [26] presented, is a unique encryption technique that helps generate the optimal key by reducing resource consumption and encryption execution time. The research aims to improve the current encryption technique for faster encryption by merging the Ant Lion Optimization algorithm with the PSO algorithm. Additionally, the concept of RandomWalkOfAnts is utilized to identify the ideal encryption key. Matlab is used to carry out the suggested research, and the results of the devised technique improved execution time and resource utilization.
Hybrid Rivest–Shamir–Adleman (RSA) and ALO algorithms were created by Khalid et al. [27] to increase the safety of wireless sensor networks. Over the past few decades, two significant advancements in the specifications for information security inside a wireless sensor network have been made. These systems employ hash functions each time Rebalanced RSA is used to encrypt a message. Another approach that is being looked into is the second one, which involves transforming the ciphertext into binary format. A new index called the “Threat Severity Index” (TSI) has been created to assess the overall security of each particular system. Furthermore, investigation and comparison of the decryption performance of RSA-type cryptosystems with other RSA-type cryptosystems are conducted.
Performance and scalability problems may arise with the current decentralized AI technology because each transaction needs to be verified and documented on several nodes. Traditional blockchain architectures have the drawback of typically requiring the sacrifice of security, decentralization, or both to achieve scale. Malicious nodes on the network could jeopardize the security of the data saved. Decentralized storage systems also largely depend on the network infrastructure for their performance. Data stored on the network may not always be accessible during network interruption. Some common edge AI defense include: data encryption using well-known and robust algorithms like AES, SSL/TLS, or VPN; model encryption using homomorphic encryption, federated learning or secure multiparty computation, antivirus software, firewalls, device security through updating and network.
The summary of the literature survey is detailed in Table 1.
3 Proposed Alo-Dhb for Secure Transmission in Edge AI Network
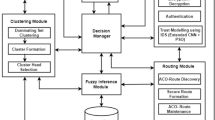
In this work, we designed an optimized hybrid cryptographic algorithm for preserving security and privacy during data transmission. The proposed method combines the Ant Lion optimization with the hybrid Diffie–Hellman-based Twofish approach (ALO-DHT). Initially, an edge AI environment is created with edge computing devices and AI-enabled sensors. To check the malicious data entry in the built environment, an autoencoder neural network-based attack prediction module was designed. Further, the processed data is encrypted using the proposed cryptography to ensure privacy and security during transmission. In presented cryptography, the Diffie–Hellman approach facilitates the secure key exchange process between the source and destination devices, while the Twofish algorithm performs encryption using the shared key.
The ALO technique in the presented framework optimizes the key generation phase, thereby reducing energy consumption and processing time. The proposed methodology is shown in Fig. 1.
3.1 Edge AI Network
The proposed framework commences with the collection of dataset from the Edge AI network. An edge AI network is a distributed computing infrastructure, which utilizes the efficiency of edge computing (EC) and artificial intelligence. This network was created using AI approaches on the edge devices of the IoT network. The commonly used edge devices include sensors, edge-computing devices like routers, switches, etc. This feature of edge AI network offers real-time data processing and analysis. In the proposed work, the data was collected from the medical edge AI network. The medical edge AI network includes different kinds of sensors, and EC devices for collecting details from the patients. This network ensures real-time monitoring of patient health and assist in healthcare decision-making. The data collected from the network includes electronic health records (EHRs) like blood pressure level, sugar level, cholesterol level, blood glucose level, etc. It also includes information regarding body temperature, oxygen saturation level, heart beat rate, and respiratory rate. This collected information is embedded into a comprehensive database. Since this database was collected using IoT devices, sensors, EC devices, etc., it is prone to security threats. Hence, protecting the data from cyber threats is significant for effective decision-making in healthcare units.
3.2 Autoencoder Neural Network
An autoencoder is an artificial neural network that utilizes unsupervised learning methodology to capture the patterns and interconnection in the data. In the proposed work, the autoencoder was employed to identify and eliminate malicious data entry in edge AI networks [28]. The architecture of an autoencoder consists of an encoder component and a decoder component. The autoencoder has two phases: encoding and decoding. During encoding, the neural network compresses the data into lower-dimensional representation. In this step, the neural network captures the important features and patterns present in the input data. On the other hand, during decoding step, the neural network was trained to reconstruct the input data. In the training phase, the network adjusts its parameters to reduce the deviation between the input data and the reconstructed data, effectively learning the patterns of the data. Initially, we use normal (non-malicious) data for both encoding and decoding, so that the system can learns the patterns of abnormal data. In attack detection phase, we compare the features of new data (data from the Edge AI network) with the patterns identified by the autoencoder during training. If the deviation between the patterns of new input data and the reconstructed output is high, it is identified as attack or malicious data. The training with the non-malicious data ensures that the system can identify all types of attacks in the Edge AI environment. The encoder module consists of multiple layers of neurons that map the input data into lower-dimensional representation. The encoder is expressed in Eq. (1).
where \(Y\) indicates the encoder data representation, \(A_{ct}\) denotes the activation function,\(w_{gt}\) represents the weight matrix, \(B_{s}\) refers to the bias vector, and \(X\) defines the input data. While compressing the data into lower-dimensional latent space, it intends to capture the important features and data patterns. In malicious data prediction, the encoders capture the features that distinguish the normal and malicious data. On the other hand, the decoder takes the latent data representation as input and aims to reconstruct the original data. In the decoder module, the reverse operation of the encoder is performed, and it is expressed in Eq. (2).
where \(A_{ct}^{\prime }\) denotes the decoder’s activation function, \(w_{gt}^{\prime }\) represents the weight matrix of the decoder, \(B_{s}^{\prime }\) refers to the bias vector of decoder, and \(X^{\prime }\) defines the reconstructed data. The decoder performs a reconstruction function and produces the data that resembles the input data. The malicious data entry was identified by evaluating the reconstruction error. The reconstruction error of the encoder is measured using the Eq. (3).
where \(L_{fn}\) defines the reconstruction error and \(m\) denotes the number of data. The system predicts the malicious data based on the reconstruction error. That is, if the reconstruction error is above the threshold value, the system predicts it as malicious. Once the malicious data is predicted, the scheme intends to eliminate it from the network to provide maximum security and privacy to the data.
3.3 Cryptography
After attack prediction and elimination, the data is passed to the cryptography block. The cryptography is the process of securing the data during transmission by converting or encoding the raw data into another form. In this work, we proposed an innovative cryptographic algorithm by combing the Ant Lion Optimization, Diffie–Hellman, and Twofish algorithm. Typically, edge AI network collects the information from different sources like sensors, EC devices, IoT devices, etc. Securely storing the collected information is a challenging task in edge AI network. The proposed work aims to secure the data during data transmission and storage using the developed mechanism. The ALO approach integrated into the cryptographic approach optimizes the key exchange process by optimally selecting the initial parameters of Diffie–Hellman cryptography. In Diffie–Hellman approach, the parameters, such as prime number, primitive modulo, etc., directly influence the key generation process, and the choice of these parameters plays an important role in evaluating the key strength. Hence, the optimal selection of these parameters is significant for generating keys with better strength. The ALO process aims to maximize the key strength by refining and fine-tuning the DH parameters. The key generated using the optimized DH mechanism is used for data encryption using Twofish algorithm. The key with greater strength makes the third parties difficult to encode the data during transmission. Since ALO is an iterative process, the parameter values change at each iteration, ensuring adaptability and improved security in the network. At each iteration, the ALO selects the parameter values, which increases the strength of the key. Thus, the hybrid cryptographic mechanism resolves the security and privacy challenges associated with the edge AI network.
3.3.1 Diffie–Hellman Key Exchange
The DH key exchange is a cryptographic mechanism that enables two parties (source and destinations) to establish a shared secret key over an insecure communication medium securely. The Twofish algorithm further uses its shared secret key for performing data encryption. In the context of secure communication, the DH mechanism offers a shared secret key between the communicating parties over the insecure communication medium. In the proposed work, it utilizes the optimal parameters from the ALO for key generation, ensuring adaptability and high security in the network. In addition, it allows numerous numbers of participants to share the keys without increasing the computational complexity. Thus, it offers scalability in the network.
In key exchange process, both parties (sender and receiver) agree on the public parameters and select the private key. Using the selected parameters, they independently generate public keys and exchange them. Then, they independently generate the shared secret key using the received private key and their own private key. This key is integrated into the Twofish algorithm for encryption, providing improved security during data transmission. In DH mechanism, initially, the source and the destination agree to establish key exchange over the communication medium [29]. Then, both source and destination agree on two public parameter \(u\) and \(v\) in which the parameter \(u\) is a large prime number and \(v\) is the primitive modulo of \(u\). Each participant selects a private key, which is kept secret. The private keys chosen by both parties are random integers. Then, they determine their public keys and share them over the insecure communication medium. The calculation of the public keys of both parties is expressed in Eqs. (4), and (5).
where \(P_{ka}\) indicates the public key of the sender, \(P_{ra}\) represents the private key of the sender, \(P_{kb}\) denotes the public key of the receiver, and \(P_{rb} \,\) defines the private key of the receiver. These \(P_{ka}\) and \(P_{rb} \,\) are exchanged over the communication channel. Then, both parties calculate their secret key, expressed in Eqs. (6) and (7).
where \(S_{k}\) is the shared secret key, which is utilized by the Twofish approach for data encryption operation. In Diffie–Hellman key exchange, selecting initial parameters, such as \(u\) and \(v\), is crucial for effective secret key generation. Hence, the ALO algorithm was employed for the optimal selection of initial parameters of DH key exchange.
3.3.2 Ant Lion Optimization
The ALO is a meta-heuristic approach inspired by the foraging characteristics of ant lions [30]. In the proposed method, the ALO approach was employed for optimizing the selection of initial parameters of Diffie–Hellman (DH) key exchange including large prime numbers and primitive modulo. This optimization mechanism improves the efficiency of the DH algorithm by dynamically tuning its parameters to changing environment conditions. Thus, the ALO enables the system to adapt in real-time changes in the Edge AI environment, improves the system security by iteratively tuning the key exchange process, thereby making the system more effective in handling the threats, and offers greater level of security during transmission. The ALO approach considers the parameters of the DH key exchange as input and the objective function is to find the optimal value for those key generation parameters. This approach explores the parameter space and updates the parameters based on their fitness values, which is determined based on performance of the DH key exchange for particular parameter value. The performance of the DH key exchange was determined in terms of generation time, complexity, level of security, etc. After exploration, the parameter with greater fitness value will be selected for key generation in DH mechanism. This iterative mechanism improves the efficiency of parameter selection and ensures greater level of security. The optimization process begins with initializing the parameters of the DH key exchange. The initialization of the parameter population is indicated in Eq. (8).
where \(Pa_{p}\) denotes the parameter population and \(pa\) indicates the parameter set present in the parameter space and they have parameters like \(u\), \(v\), \(P_{ra}\), and \(P_{rb}\) with different values. Then, the fitness value of each parameter set is estimated, and it depends on the efficiency of the DH key exchange process. The fitness value of the parameter set is directly proportional to the performance of the DH mechanism. If the DH algorithm acquires improved security and less computational error for the parameter group [31], the particular set has an excellent fitness value. Further, these parameters move through the parameter space randomly, and the random walk of the parameters is represented in Eq. (9).
where \(P_{pa} \left( t \right)\) indicates the position of the parameters at a time \(t\), \({\text{cumcum}}\) represents the cumulative function, which calculates the sum of values, and \(s\left( t \right)\) defines the stochastic process, which influences the direction of the random walk. After the exploration phase, the positions of the parameters are updated by the optimal solutions, and it is expressed in Eq. (10).
where \(P_{pa} \left( {t + 1} \right)\) indicates the updated position of the parameter at a time \(t\), \(m_{r} \left( t \right)\) denotes the minimum of random walk, \(mxf_{pa} \left( t \right)\) represents the maximum fitness of the parameter, and \(mif_{pa} \left( t \right)\) indicates the minimum fitness value of the parameter at a time \(t\). After position update, the fitness of the parameters is updated based on their new positions. Finally, the initial parameters with greater fitness value were chosen for DH key exchange process. Using these initial parameters, the DH approach generates the shared secret key, which is utilized by the Twofish cryptography for data encryption. Moreover, it is important to note that this initial parameters change iteratively, ensuring adaptability to the network.
3.3.3 Twofish Algorithm
The Twofish technique is a symmetric-key cryptographic mechanism employed for data encryption [32]. This technique utilizes single key for performing encryption and decryption tasks. In the presented work, the primary of Twofish algorithm is to provide security and privacy to the data during communication. It utilizes the shared secret key from optimized DH key exchange, and encodes the data into another form. This method of data encryption protects the data from network threats, and offers high level of security. This algorithm works by splitting the dataset into fixed size blocks and then, encodes those blocks using the shared secret key generated using optimized DH approach. It combines substitution, permutation, and confusion–diffusion mechanisms to transform plaintext into cipher text. Initially, the shared secret key is expanded into a sequence of subkeys for the encryption rounds using the key expansion algorithm. Then, each data block undergoes whitening, substitution, permutation, and Feistel network-based processing. In whitening, the input data block is combined with the whitening subkey through XOR operation and expressed in Eq. (11).
where \(D_{wh}\) denotes the whitened data, \(D_{ip}\) indicates the input data, and \(S_{whk}\) refers to the whitening subkey. Then, the Twofish approach utilizes the Feistel network-based processing, where the input data is divided into two halves (left and right), and each half goes through multiple rounds of processing. In each round, both left and right halves undergo the following operations in Eqs. (12) and (13).
where \(R_{h}^{\prime }\) defines the new right half of data after the first round, \(L_{h}\) indicates the left half of data,\(F_{e}\) represents the Feistel network function, \(R_{h}\) refers to the right half of data, \(R_{sbk}\) defines the round subkey, and \(L_{h}^{\prime }\) indicates the new left half of data after the first round. However, in case of real-time implementation, undergoing functions like permutations, substitutions, etc., are difficult. Therefore, proper understanding of the concept is required for accurate implementation of this algorithm. The pseudo-code of the proposed approach is presented in Algorithm 1.
For each round, the new right and left half becomes the right and left values. After a series of encryption rounds, combining the final left and right halves of the data produces the cipher text, which is transmitted over the communication channel to the receiver (cloud storage). In the receiver end, the decryption process was performed by reversing the order of the subkeys and applying the inverse of the Feistel function [33].
4 Results and Discussion
It's critical to protect data security and privacy in these decentralized networks as Edge AI systems. This work presented a new hybrid cryptography mechanism that combines DHT and ALO to provide secure data transmission. The generated work gathers data from the developed edge AI system and uses the Autoencoder to process it. To detect malicious data entry, the Autoencoder learns patterns in the data. While the ALO enhances security performance and optimizes key exchange, the DH key exchange creates shared secret keys for encryption. Additionally, to guard against security risks during transmission, the Twofish algorithm encrypts data using a secret key generated by DH. The developed model is implemented in a MATLAB tool, and the gained performance is validated with other prevailing techniques.
4.1 Simulation Details
The suggested investigation was implemented using the Matlab program. Matlab makes testing various methods, like Particle Swarm Optimization and Ant Lion Optimization, easier. Additionally, simulation aids in the identification of mistakes that can be prevented when the implementation is deployed in real-time. The simulation was run on a 64-bit Windows platform machine with an AMD Ryzen 7 CPU with eight cores. Additionally, Matlab was used to replicate the experiment's proposed case using the C programming language.
4.2 Performance Analysis
The developed ALO-DHT model gained performance is validated with other conventional models regarding accuracy, recall, precision, F1 score, time consumption, delay and energy consumption. To prove the reliability of the developed model, compare gained outcome of the designed model with other techniques such as EC model with AI mechanism (EC-AI) [22] EI computing framework in IoT (EI-IoT) [23], SC-based Attack Detection and Security model (SC-ADS) [24] Enhanced SC approach for Intrusion Detection (SC-ID) schemes [25].
4.2.1 Accuracy
The gained accuracy of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The performance is validated with five types of data rates: 50, 100, 150, 200, and 250 Kbps. The comparison of the accuracy is shown in Fig. 2.
The existing model reached a low accuracy rate compared to the proposed technique. The EC-AI model gained 95%, the EI-IoT technique gained 85.6%, the SC-ADS model reached 97.34%, and the SC-ID technique reached 90% for a 50 Kbps data rate. The designed ALO-DHT model achieved accuracy of 99.45%, 99.32%, 99.11%, 99%, and 98.86% for 50, 100, 150, 200, and 250 Kbps data rates. It shows the effectiveness and reliability of the model to secure the EAI.
4.2.2 Precision
The gained precision of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The performance is validated with five types of data rates: 50, 100, 150, 200, and 250 Kbps. The comparison of the precision is shown in Fig. 3.
The existing model reached a low precision rate compared to the proposed technique. The EC-AI model gained 93.64%, the EI-IoT technique gained 83%, the SC-ADS model reached 95.45%, and the SC-ID technique reached 90.86% for a 50 Kbps data rate. The designed ALO-DHT model achieved precision of 99.15%, 99.03%, 98.74%, 98.12%, and 97.98% for 50, 100, 150, 200, and 250 Kbps data rates.
4.2.3 Recall
The gained recall of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The performance is validated with five types of data rates: 50, 100, 150, 200, and 250 Kbps. The comparison of the recall is shown in Fig. 4.
The existing model reached a low recall rate compared to the proposed technique. The EC-AI model gained 96.54%, the EI-IoT technique gained 84%, the SC-ADS model reached 95.45%, and the SC-ID technique reached 91.2% for a 50 Kbps data rate. The designed ALO-DHT model achieved recall of 99.77%, 99.52%, 99.12%, 98.68%, and 98.12% for 50, 100, 150, 200, and 250 Kbps data rates.
4.2.4 F1 Score
The gained F1 score of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The performance is validated with five types of data rates: 50, 100, 150, 200, and 250 Kbps. The comparison of the F1-score is shown in Fig. 5.
The existing model reached a low F1 score rate compared to the proposed technique. The EC-AI model gained 93.87%, the EI-IoT technique gained 90%, the SC-ADS model reached 75.6%, and the SC-ID technique reached 85.7% for a 50 Kbps data rate. The designed ALO-DHT model achieved 98.3%, 98.03%, 97.86%, 97.34%, and 97% for 50, 100, 150, 200, and 250 Kbps data rates.
4.2.5 Time Consumption
The gained time consumption of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The comparison of the time consumption is shown in Fig. 6.
The existing model required a large amount of time to execute the process when compared to the proposed technique. The EC-AI model gained 5 s, the EI-IoT technique gained 2.7 s, the SC-ADS model reached 3 s, and the SC-ID technique reached 4.5 s to secure the edge AI system. Finally, the developed method required time consumption of 2 s for securing the data. It needs less time and saves the energy consumption.
4.2.6 Delay
The gained delay of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The comparison of the delay is shown in Fig. 7.
The existing model required a large delay rate to execute the process compared to the proposed technique. The EC-AI model gained 3 s, the EI-IoT technique gained 2.5 s, the SC-ADS model reached 1.8 s, and the SC-ID technique reached 5 s to secure the data. Finally, the developed method required delay rate of 0.8 s for securing the data. The developed model needs less delay rate.
4.2.7 Energy Consumption
The gained energy consumption of the developed ALO-DHT model results is validated with other prevailing techniques, such as EC-AI, EI-IoT, SC-ADS, and SC-ID. The comparison of the energy consumption is shown in Fig. 8.
The existing model required a large energy consumption to execute the process compared to the proposed technique. The EC-AI model gained 6.5 mJ, the EI-IoT technique gained 8.4 mJ, the SC-ADS model reached 11.6 mJ, and the SC-ID technique reached 7 mJ to secure the data. Finally, the developed method required energy consumption of 3.2 mJ for securing the data. The developed model needs less energy consumption.
4.2.8 Security and Confidentiality
Security and privacy goals are supported by the fundamental idea of security. Data security and confidentiality are frequently used interchangeably. While privacy safeguards allow individuals to regulate the information they collect, maintain, and share with others, confidentiality controls guard toward unauthorized utilization of information previously in the control of an edge AI system. The gained security and the confidentiality of the developed ALO-DHT model results are validated with other prevailing techniques, such as FHE, AES, RSA, and PHE. The comparison of the security is shown in Fig. 9.
The existing model reached a less security and less confidentiality rate compared to the proposed technique. The FHE model gained 88%, the AES technique gained 81%, the RSA model reached 92%, and the PHE technique reached 94% for security. The designed ALO-DHT model achieved security of 99.74%. Additionally, the FHE model gained 85%, the AES technique gained 83%, the RSA model reached 90%, and the PHE technique reached 96% for confidentiality. The designed ALO-DHT model achieved confidentiality of 99%.
4.3 Discussion
Cryptography does not mitigate the risks and vulnerabilities resulting from shoddy system, protocol, and procedure design. These must be resolved by carefully planning and establishing a defensive infrastructure. There is a delay when cryptographic techniques are added to information processing. Manu cryptographic methods have been previously employed in Edge AI systems for data security, such as fully homomorphic encryption (FHE) [9], MSIAP [34], Convergent and Modified Elliptic Curve Cryptography (MECC) [35], Paillier Homomorphic Encryption (PHE) [36], lightweight Speck encryption [37], Shamir threshold cryptography [38], and ciphertext policy attribute-based encryption [39, 40]. The strength and weakness of the cryptographic technique is detailed in Table 2.
The suggested technique combines the hybrid Diffie–Hellman-based Twofish approach (ALO-DHT) with Ant-lion optimization. First, AI-enabled sensors and edge computing devices are used to create an edge AI environment. An attack prediction module with autoencoder neural networks is created to verify malicious data entry in the built environment. The processed data is additionally encrypted using the suggested cryptography to guarantee security and privacy during transmission. The developed model enhances security using cryptographic and optimization techniques. The security performance of the developed model is validated with other models and is detailed in Table 3.
Table 3 compares the performance rendered by the proposed ALO-DHT technique with the prevailing methods concerning encryption time, decryption time, key generation time, and security level. The proposed ALO-DHT model takes 5.64 s to encrypt the data, 4.28 s to decrypt the data, and 347.21 ms to generate a key. The existing FHE, AES, RSA, and PHE methods take 612.54 ms, 873.76 ms, 569.34 ms, and 773.29 ms to create a key. Here, the existing process takes more time for key generation. However, when compared to other techniques, the proposed ALO-DHT takes less time to create a key. Furthermore, the security level of the proposed and existing methods is compared with existing techniques. The proposed ALO-DHT gives the highest security value (99.74%), but the existing FHE, AES, RSA, and PHE methods give 88%, 81%, 92%, and 94% security. So, it is inferred that the proposed ALO-DHT proffers high performance for both key generation and safety.
The capacity to achieve a desired outcome with the least time, effort, or resource waste is known as efficiency. The capacity to provide a better result—one that adds more value or accomplishes a better goal—is known as effectiveness. These apps are speedy, have minimal latency, robust security, better privacy management, and use less power. Additionally, Edge AI helps businesses maximize their energy, network, and computing resources, raising the total cost-effectiveness of AI applications. It shows the security performance, execution time, encryption, and decryption process. Better efficiency and effectiveness offer the excellent security and privacy of a decentralized edge AI system.
The stable performance of the system over increasing data size demonstrates that the proposed method is capable of dealing large databases, ensuring its scalability for growing network. Moreover, the increased performance of the system under increasing data size indicates that the system maintains its efficiency and responsiveness over extensive networks. This positive outcome illustrates that proposed systems robustness and its capacity in handling the complex edge AI network. However, the system performances are not evaluated under different network conditions like different network threats, bandwidth variations, time, etc. This may reduce its applicability in real-time environment and also reduces its scalability. Moreover, the developed model is limited to high computational cost and high data.
Many technologies, including Computer Vision, Multi-modal AI, AutoML, Digital Twins, Explainable AI, Neural Networks, and more, are part of the current AI trends. These AI trends are revolutionizing how we engage with and utilize technology while fostering sustainable growth for companies across all industries. With a low latency and fast cellular speed, 5G offers robust wireless connectivity to EC, opening up exciting new possibilities like autonomous drones, remote telesurgery, innovative city projects, and much more.
4.4 Limitations of the Study
The limitations of the study are listed below—
-
Since the key generation process is optimized by ALO mechanism, it indirectly increases the latency. The iterative refinement of DH parameters potentially increases the key generation time, inducing latency in real-time network.
-
Combining different algorithms, like Autoencoder neural network, Ant Lion Optimization, Diffie–Hellman, and Twofish algorithm into a single framework introduces computational complexity.
-
The DH parameter optimization through ALO demands significant amount of computational resources. This makes the system ineffective in resource-constrained edge AI network.
-
Since the system adaptability relies on the iterative nature of ALO approach, it faces difficulty in adapting the rapidly changing network conditions.
-
Although the Twofish algorithm is robust and offers security, it limits the system’s interpretability, and demands a knowledge expertise for precise implementation of this approach in real-world applications.
5 Conclusion
In this study, optimized hybrid cryptography (ALO-DHT) is presented to ensure security and privacy during data transmission. The proposed model utilizes the data collected from the edge AI network as input and processes it using the Autoencoder for malicious data prediction. Further, to ensure data security, the processed data is encrypted using the proposed ALO-DHT approach. The DH key exchange produces the shared secret key, and the Twofish approach performs data encryption using the shared secret key. The ALO optimizes the key exchange and encryption process, thereby improving the system performance. The presented framework is implemented in a MATLAB environment, and the results are examined as accuracy, precision, delay, time consumption, recall, f-measure, and energy consumption. The experimental results illustrate that the proposed method acquired improved accuracy of 99.45%, 99.15% precision, 99.77% recall, and 98.3% f-measure. In addition, the energy consumption, delay, and time consumption are minimized to 3.2 mJ, 0.8 s, and 2 s, respectively. Also, the proposed methodology obtained minimum encryption time of 5.64 s, less key generation time of 347.21 s, lower decryption time of 4.28 s, and maximum security rate of 99.74. Furthermore, we made a comparative study with the conventional algorithms, such as EC-AI, EI-IoT, SC-ADS, and SC-ID, to validate the effectiveness of the proposed framework. The comparative analysis highlights that the proposed framework outperformed the existing techniques in terms of parameters, such as accuracy, precision, recall, and f-measure.
Although the proposed ALO-DHT method offers greater security in data transmission, yet it faces some demerits like computational overhead, high cost, limited scalability, etc. Therefore, the future study must concentrate on developing an intelligent security framework to work optimally under resource-constrained and dynamic network conditions. Also, the future study should focus on reducing the computational complexity using some compression mechanisms, which makes them more effective and reliable in real-time edge AI applications.
Data Availability
Not Applicable.
References
Singh, S., et al.: Machine-learning-assisted security and privacy provisioning for edge computing: a survey. IEEE Internet Things J. 9(1), 236–260 (2021)
Al-Doghman, F., et al.: AI-enabled secure microservices in edge computing: Opportunities and challenges. IEEE Trans. Serv. Comput. (2022). https://doi.org/10.1109/TSC.2022.3155447
Xu, Z., et al.: Artificial intelligence for securing IoT services in edge computing: a survey. Secur. Commun. Netw. 2020, 1–13 (2020)
Alwarafy, A., et al.: A survey on security and privacy issues in edge-computing-assisted internet of things. IEEE Internet Things J. 8(6), 4004–4022 (2020)
Hua, H., et al.: Edge computing with artificial intelligence: a machine learning perspective. ACM Comput. Surv. 55(9), 1–35 (2023)
Sachdev, R.: Towards security and privacy for edge AI in IoT/IoE based digital marketing environments. 2020 Fifth International Conference on Fog and Mobile Edge Computing (FMEC). IEEE, (2020)
Ranaweera, P., Jurcut, A.D., Liyanage, M.: Survey on multi-access edge computing security and privacy. IEEE Commun. Surv. Tutor. 23(2), 1078–1124 (2021)
Zhou, Z., et al.: Edge intelligence: paving the last mile of artificial intelligence with edge computing. Proc. IEEE 107(8), 1738–1762 (2019)
Rahman, M.S., et al.: Towards privacy preserving AI based composition framework in edge networks using fully homomorphic encryption. Eng. Appl. Artif. Intell. 94, 103737 (2020)
Zhang, P., et al.: A security-and privacy-preserving approach based on data disturbance for collaborative edge computing in social IoT systems. IEEE Trans. Comput. Soc. Syst. 9(1), 97–108 (2021)
Li, J., et al.: A secured framework for sdn-based edge computing in IOT-enabled healthcare system. IEEE Access 8, 135479–135490 (2020)
Singh, A., Satapathy, S.C., Roy, A. et al.: AI-based mobile edge computing for iot: Applications, challenges, and future scope. Arab J Sci Eng 47, 9801–9831 (2022). https://doi.org/10.1007/s13369-021-06348-2
Gao, H., Huang, W., Liu, T., Yin, Y., Li, Y.: Ppo2: location privacy-oriented task offloading to edge computing using reinforcement learning for intelligent autonomous transport systems. IEEE Trans Intell Transport Syst 24(2), 7599–7612 (2022). https://doi.org/10.1007/s13369-021-06348-2
Ranaweera, P., Anca D.J., Madhusanka L.: Realizing multi-access edge computing feasibility: Security perspective. 2019 IEEE Conference on Standards for Communications and Networking (CSCN). IEEE, (2019)
Ansari, M.S., Alsamhi, S.H., Qiao, Y., Ye, Y., Lee, B.: Security of distributed intelligence in edge computing: threats and countermeasures. In: Lynn, T., Mooney, J., Lee, B., Endo, P. (eds.) The Cloud-to-Thing Continuum. Palgrave Studies in Digital Business & Enabling Technologies. Palgrave Macmillan, Cham (2020). https://doi.org/10.1007/978-3-030-41110-7_6
Rajendran, S., et al.: Emphasizing privacy and security of edge intelligence with machine learning for healthcare. Int. J. Intell. Comput. Cybern. 15(1), 92–109 (2021)
Latif, S.A., et al.: AI-empowered, blockchain and SDN integrated security architecture for IoT network of cyber physical systems. Comput. Commun. 181, 274–283 (2022)
Rodríguez-Barroso, N., et al.: Federated Learning and differential privacy: software tools analysis, the Sherpa. AI FL framework and methodological guidelines for preserving data privacy. Inf. Fusion 64, 270–292 (2020)
Xiong, J., et al.: An AI-enabled three-party game framework for guaranteed data privacy in mobile edge crowdsensing of IoT. IEEE Trans. Ind. Inf. 17(2), 922–933 (2019)
Wan, Y., et al.: Privacy-preserving blockchain-enabled federated learning for B5G-Driven edge computing. Comput. Netw. 204, 108671 (2022)
Deng, S., et al.: Edge intelligence: the confluence of edge computing and artificial intelligence. IEEE Internet Things J. 7(8), 7457–7469 (2020)
Sodhro, A.H., Sandeep, P., Victor, H.C.D.A.: Artificial intelligence-driven mechanism for edge computing-based industrial applications. IEEE Trans. Ind. Inf. 15(7), 4235–4243 (2019)
Fagbohungbe, O., et al.: Efficient privacy preserving edge intelligent computing framework for image classification in iot. IEEE Trans. Emerg. Topics Comput. Intell. 6(4), 941–956 (2021)
Mugunthan, S.R.: Soft computing based autonomous low rate DDOS attack detection and security for cloud computing. J. Soft Comput. Paradig. 1(2), 80–90 (2019)
Sathesh, D.A.: Enhanced soft computing approaches for intrusion detection schemes in social media networks. J. Soft Comput. Paradig. 1(2), 69–79 (2019)
Sawant, D.S.: Enhancing encryption in cloud computing and reducing energy usage by using PSO-ALO algorithm to improve homomorphic encryption technique. Diss. Dublin, National College of Ireland, (2022)
Almuzaini, K.K., et al.: Secured wireless sensor networks using hybrid Rivest Shamir Adleman with ant lion optimization algorithm. Wirel. Netw. (2023). https://doi.org/10.1007/s11276-023-03372-y
Bank, D., Koenigstein, N., Giryes, R.: Autoencoders. In: Rokach, L., Maimon, O., Shmueli, E. (eds) Machine Learning for Data Science Handbook. Springer, Cham (2023). https://doi.org/10.1007/978-3-031-24628-9_16
Glhamari, S.M., Narm, H.G., Mollaee, H.: Fractional-order fuzzy PID controller design on buck converter with antlion optimization algorithm. IET Control Theory Appl. 16(3), 340–352 (2022)
Hadi, H.H., Ammar, A.N.: Diffie-Hellman key exchange based on block matrices combined with elliptic curves. Int. J. Intell. Syst. Appl. Eng. 11(5s), 353–360 (2023)
Almalawi, A., Khan, A.I., Alsolami, F., Abushark, Y.B., Alfakeeh, A.S.: Managing security of healthcare data for a modern healthcare system. Sensors 23(7), 3612 (2023)
Jain, S., Muntean C.H., Verma, R.: Honey2Fish-a hybrid encryption approach for improved password and message security. 2023 IEEE 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS). IEEE, (2023)
Barukab, O.M., Khan, A.I., Shaik, M.S., Murthy, M.R., Khan, S.A.: Secure communication using symmetric and asymmetric cryptographic techniques. Int. J. Inf. Eng. Electron. Bus. 4(2), 36 (2012)
Fan, K., et al.: Msiap: a dynamic searchable encryption for privacy-protection on smart grid with cloud-edge-end. IEEE Transactions on Cloud Computing (2021)
Shynu, P.G., Nadesh R. K., Menon, V.G., Venu P., Abbasi, M., Khosravi, M.R.: A secure data deduplication system for integrated cloud-edge networks. J. Cloud Comput. 9, 61 (2020). https://doi.org/10.1186/s13677-020-00214-6
Kumar, K.P.S., et al.: Security and privacy-aware artificial intrusion detection system using federated machine learning. Comput. Electr. Eng. 96, 107440 (2021)
AbdulRaheem, M., et al.: An efficient lightweight speck technique for edge-IoT-based smart healthcare systems. In: 5G IoT and edge computing for smart healthcare, pp. 139–162. Academic Press, Cambridge (2022)
Yu, K., et al.: A blockchain-based shamir’s threshold cryptography scheme for data protection in industrial internet of things settings. IEEE Internet Things J. 9(11), 8154–8167 (2021)
Zheng, W., Chen, B., He, D.: An adaptive access control scheme based on trust degrees for edge computing. Comput. Stand Interfaces 82, 103640 (2022)
Sarker, I.H., Abushark, Y.B., Alsolami, F., Khan, A.I.: Intrudtree: a machine learning based cyber security intrusion detection model. Symmetry 12(5), 754 (2020)
Acknowledgements
The Deanship of Scientific Research (DSR) at King Abdulaziz University (KAU), Jeddah, Saudi Arabia, has funded this Project, under grant no. (KEP-MSc: 78-611-1443).
Funding
This research work was funded by Deanship of Scientific Research (DSR) under grant no. KEP-MSc: 78-611-1443.
Author information
Authors and Affiliations
Contributions
Conceptualization, AA; methodology, SH and AIK; validation, AF, AA and SH; formal analysis, SH and AA; investigation, AF, SH and AIK; resources, AA; writing—review and editing, SH, AA and AIK. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interest or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Almalawi, A., Hassan, S., Fahad, A. et al. A Hybrid Cryptographic Mechanism for Secure Data Transmission in Edge AI Networks. Int J Comput Intell Syst 17, 24 (2024). https://doi.org/10.1007/s44196-024-00417-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s44196-024-00417-8