Abstract
Internet-of-Things (IoT) connects various physical objects through the Internet and it has a wide application, such as in transportation, military, healthcare, agriculture, and many more. Those applications are increasingly popular because they address real-time problems. In contrast, the use of transmission and communication protocols has raised serious security concerns for IoT devices, and traditional methods such as signature and rule-based methods are inefficient for securing these devices. Hence, identifying network traffic behavior and mitigating cyber attacks are important in IoT to provide guaranteed network security. Therefore, we develop an Intrusion Detection System (IDS) based on a deep learning model called Pearson-Correlation Coefficient - Convolutional Neural Networks (PCC-CNN) to detect network anomalies. The PCC-CNN model combines the important features obtained from the linear-based extractions followed by the Convolutional Neural Network. It performs a binary classification for anomaly detection and also a multiclass classification for various types of attacks. The model is evaluated on three publicly available datasets: NSL-KDD, CICIDS-2017, and IOTID20. We first train and test five different (Logistic Regression, Linear Discriminant Analysis, K Nearest Neighbour, Classification and Regression Tree,& Support Vector Machine) PCC-based Machine Learning models to evaluate the model performance. We achieve the best similar accuracy from the KNN and CART model of 98%, 99%, and 98%, respectively, on the three datasets. On the other hand, we achieve a promising performance with a better detection accuracy of 99.89% and with a low misclassification rate of 0.001 with our proposed PCC-CNN model. The integrated model is promising, with a misclassification rate (or False alarm rate) of 0.02, 0.02, and 0.00 with Binary and Multiclass intrusion detection classifiers. Finally, we compare and discuss our PCC-CNN model in comparison to five traditional PCC-ML models. Our proposed Deep Learning (DL)-based IDS outperforms traditional methods.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The Internet of Things, or IoT, is an interconnected system based on approved protocols that exchange information. Recent developments in the industry contribute to the development of intelligent smart cities [1], smart devices [2], smart homes [3], smart transportation [4], healthcare [5], agriculture [6], smart grid [7], military [8] and much more[9]. IoT provides the platform to interact with real-world applications via the Internet in the IoT domain [10,11,12]. Moreover, The Industrial Internet of Things (IIoT) is empowered by the rapid growth of integration between sensors and devices[13,14,15]. Therefore, to provide an intelligent industrial edge computing solution, the use of machine-learning, deep-learning, and artificial intelligence is paramount [16]. From statistics [17, 18], the number of smart devices for IoT applications is expected to grow by 21% in the year 2030 compared to 2019, which depicts that IoT will play a crucial role soon. The automotive market will grow to 195.7 billion endpoints during that period [17].
As the number of connected devices across the globe increases, multiple sensors are used to allow them to collect real-time data from physical objects remotely [19]. This data helps us build intelligent decision-making algorithms and effectively manage IoT settings. In parallel, the wide usage of real-world devices raises the risk of cybersecurity threats [18]. Malicious devices can spy on others without notice, manipulate traffic signals remotely and disrupt the networks [20,21,22]. The most notable real-time attacks are DDoS (Distributed Denial of Service)[23], Mirai botnet [24], DoS (Denial of Service)[25], Port Scan, and website crippling from botnet creators who also offer mitigation services at the victim’s expense [26,27,28]. IoT device protection against such intrusions is significant in the field of security. There is an increasing need to take the necessary actions to provide physical and cybersecurity against such powerful attacks. Hence, a detailed analysis of network protection is crucial [29].
Traditional intrusion detection technologies do not provide guaranteed security in IoT applications because of their limited bandwidth capacity and global connectivity [30,31,32]. This results in building an advanced Intrusion Detection System (IDS) to protect IoT devices against intrusions [33]. The IDS can alert the system administrator to suspicious activities or anomalies [34, 35]. The IDS is known as adaptive network security, which can offer valuable feedback to the network administrator about new attack types. It is also essential to update the network with an instance of the attack type before it can detect it [36]. IDS can be classified into three major categories signature-based, anomaly-based, and specification-based [37, 38]. Signature-based approaches can detect attacks based on known attack patterns and based on signatures [39]. An anomaly-based detection system detects a deviation from defined normal behaviors [40]. Similarly, A specification-based system uses the rules defined by the administrator [41]. It is challenging to keep IDS up-to-date due to the complex network and changing environment [42]. To enhance their benefits, researchers use adaptable methods such as machine learning (ML) and deep learning (DL) [43]. The machine learning model can be based on a single classifier, with one classifying model, or a multi-classifiers model, using multiple classification models in parallel [44,45,46]. IDS model can be further divided into binary and multiclass classification models. In binary classification, the traffic divides into either 0 or 1, which means normal (0) or abnormal (1). In contrast, multiclass classification discovers the type of attacks. The multiclass model is more complex than the binary model, leading to lower accuracy for unknown attacks when the data does not contain enough attack instances while training the model [47,48,49].
Furthermore, security attacks are categorized as active or passive attacks [50]. An active attack appears during the run-time conditions. It can disrupt and create damage to the physical device. It is difficult to perform and detect active attacks compared to passive attacks. Denial of Service is the most common example of an active attack [51]. Packet replay, spoofing, and message modification are also examples of active attacks [52,53,54]. Passive attack observes and monitors the information for the specific target [55]. The attackers hide and keep the communication line open to collect information, but the data remains unchanged. The most common threats are eavesdropping network mapping and traffic analysis [56, 57]. To reduce the impact of these attacks on IoT devices and the consumer, a real-time network Anomaly-based intrusion detection system is necessary to block adversaries.
In our previous study [58], we proposed a machine learning-based IDS for detecting DDoS attacks in the context of the CAV (connected and autonomous vehicle) setup, which represents IoT devices. We achieved 94% to 98% accuracy for five different ML models (LR (Logistic Regression), LDA (Linear Discriminant Analysis), CART (Classification and Regression Tree), KNN (K Nearest Neighbour), & SVM (Support Vector Machine)) for binary and multiclass classification on NSL-KDD dataset. Our previous study obtained promising results in binary classification. However, the model in our previous work did not perform well in multiclass classification because we did not use any outlier handling techniques for imbalanced attack instances. Moreover, we only used traditional machine learning approaches, which did not give the best model accuracy.
Therefore, in this current study, we explore different attacks against network layers of IoT devices. We review the current state-of-the-art methods for securing IoT devices against such attacks. We propose an advanced approach for anomaly-based IDS using a deep learning model named Pearson Correlation Coefficient - Convolution Neural Network (PCC-CNN) for anomaly detection with low misclassification rates. We experiment and evaluate binary classification and multiclass classification models. Finally, we discuss the results through a comparative analysis with five different ML algorithms, LR, LDA, CART, KNN, & SVM, using three benchmarking datasets, NSL-KDD, CICIDS2017, and IOTID20, to check the feasibility of binary and multiclass classification approaches. The PCC-CNN model is efficient and lightweight and can detect different cyber attacks.
This research is organized as follows: Sect. 2 presents the background and prior related work. Section 3 details the datasets and methods of ML/DL techniques used. Section 4 exhibits the experimental results with the comparative evaluation of the performance metrics, followed by the concluding research in Sect. 5.
2 Background
IoT is an interconnection of billions of heterogeneous objects through the Internet. The growth and usage of intelligent IoT devices have surpassed the human population. The application of IoT devices is vast, such as in healthcare, military, transportation, and agriculture [59]. It has become essential to know how IoT works and communicates. Mainly, IoT devices operate in three phases: collection, transmission, and utilization [60]. The collection phase starts with data collection from the physical devices. Then, the transmission phase transmits the data to the end-user or specific communication applications. Lastly, the utilization phase processes the received data to retrieve the environmental information. These phases need protection against the emergence of various threats [61]. The following sections provide current security attacks against IoT structures.
2.1 Attacks against IoT structure
Typically, IoT has three layers, four layers, and five layers of architecture [62,63,64]. Although, there is no standard model of the IoT architecture. This research assumes a three-layer architecture because many professionals accept it [65]. The layers are perception, transport, and network.
2.1.1 Perception layer
The perception Layer is also known as the control layer. It is the lowest layer in the three layers of the architecture of IoT. IoT devices, physical sensors, and actuators sense the environment and collect information about surroundings like temperature, humidity, force, etc. Once the information collection is finished, the perception layer completes the primary processing and packaging of this information. It will also receive information from the network layer for control operations. [66] The most common attacks in this layer are jamming and tampering. These attacks corrupt the network communication using high-frequency radio signals [67].
2.1.2 Transport layer
The transport layer is a top layer in IoT architecture. It is also known as the application layer. This layer analyzes and processes the information from the network and perception layer. It controls the end-to-end links [68]. Different network protocols, such as LAN, Bluetooth, and 3 G [69], transmit sensor data from the perception layer to the processing layer. It typically deals with three types of attacks, flooding, De-synchronization, and man-in-the-middle attack (MITM). The flooding attack takes the device’s memory resources and repeatedly drains them to mitigate the control signal [70]. In the De-synchronization attack, an intruder tries to interrupt the communication and exhaust the network resources [71]. The MITM attack appears when the attacker taps to manipulate or delete information. The transport layer establishes a communication link between the source and the destination. It assures the communication authority to the end side [72].
2.1.3 Network or data link layer
The data link layer is the middle layer in IoT architecture. It is a layer that uses various techniques, such as 3 G and WiFi, for communicating with physical devices. These wireless communication media use standard, well-known protocols and are prone to different network attacks, also known as routing attacks [73]. These attacks involve eavesdropping, denial of service (DoS), spoofing, network mapping, and traffic analysis. In eavesdropping, an attacker can listen to data and tries to alter it from the wireless channel [74]. DoS is the most common attack nowadays. It can affect the whole network’s data, network performance, and reliability. In spoofing, the attacker checks the actual sender information [75]. Network mapping is placed by defining the software on the system, and last, traffic analysis learns the model from the traffic patterns [76].
2.1.4 Intrusion detection system in IoT
The attacks discussed earlier are brutal and hard to mitigate with traditional techniques. To identify and minimize cyber-attacks, robust defense mechanisms are required. Moreover, IDS can help us interact with such attacks in perception, transport, and network layers. An IDS aims to find the occurrence of malicious activity by analyzing network traffic and raising an alert if it does [77]. Several methods and frameworks alleviate various layer attacks using ML and DL techniques [78,79,80]. Many kinds of literature have been published to classify anomalies using ML methods in the IoT infrastructure [81,82,83,84]. Depending upon the methods, we surveyed the literature to learn the recent algorithms used. An IDS system must differentiate anomalies accurately with a low detection time. Hence, it becomes more challenging to develop such a system that can handle complex data and make fast decisions for real-time detection with a low false alarm rate [85].
Depending upon the type of IDS, it can be classified broadly into three types: signature, specification, and anomaly. Signature-based approaches look for pattern similarities between the gathered data and the existing attributes [86, 87]. The signatures of the current activities are extracted and compared with the database signatures by using matching methods. This method is helpful in accurately deciding the type of attacks and preventing a false alarm, but it is challenging to detect unknown attacks [88,89,90]. This class of IDS can also be named misuse detection or knowledge-based detection [91]. The specification-based method uses predefined rules by the administrator. With new episodes, the administrator has the hurdle of updating old laws, which is the major problem with using this method. Anomaly-based methods detect unusual changes in network behavior [92]. This type of system can detect new intrusions, but on the other hand, it creates many false positives. Thus, it is crucial to promptly update the IDS in a complex network and changing environment. Anomaly-based IDS is difficult to exploit because target interaction would raise an alert [93, 94]. Current IDS methods mainly use ML and DL models to detect anomalies [95].
Many researchers have shown promising results in detecting network intrusions [96, 97]. However, there have been fewer targets for their research on IoT network datasets [98]. The commonly used datasets to design new IDS are the KDDCUP99 [99] and DARPA datasets [100]. The problem with these two datasets is that they were created a long time back, as well as the issue of redundancy of features between the classes [101]. The research studies [102] claim that ML algorithms are not producing good results in signature-based intrusion detection. On the other hand, some studies also claim ML algorithms have promising results for anomaly-based intrusion detection in IoT networks [103, 104]. Weka Data Mining Package performs ML techniques on network datasets [105]. Weka is a tool that has a collection of different ML and DL classifiers to predict and compare how different algorithms would perform. The research work in [106] represented an intrusion detection-based approach using the KDDCUP99 datasets to classify anomalies and types of attacks via Weka 3.6 software. The authors constructed the system with an accurate, flexible, and effective performance compared to other methods, but the only drawback is the high incorrectly predicted instances of 13%.
Anish Halimaa et al. [107] developed another ML approach for network IDS to classify the anomalies on NSL-KDD datasets. They used the support vector machine (SVM) and Naive Bayes (NB) techniques to calculate the performance based on accuracy and misclassification rate. However, they used three methods to compare the results: without prepossessed datasets, with normalized datasets, and with the reduced feature using cfsSubsetEval. The methods perform better with the SVM algorithm, with the highest accuracy of 97% achieved using the first method (without prepossessed datasets). NB algorithm has comparatively lower inaccuracies with a high misclassification rate varying from 32 to 44.
Similarly, the authors in [108] proposed supervised ML-based IDS for detecting network attacks in IoT devices. They selected the concept of normalization on the UNSW-NB15 dataset [109] to overcome the information leakage in the test data. The authors applied principal component analysis (PCA) for dimensionality reduction, followed by six different ML classifiers to evaluate the performance metrics: accuracy, precision, F1 Score, and Mathew correlation coefficient. Their findings are competitive with current works. However, they overlooked model overfitting. Biesiada et al. [110] propose an algorithm for extracting non-redundant features from Pearson’s correlation. This method works well on a high-dimensional biomedical dataset used to verify the results.
M.A.Ferrag et al. [114] compared the binary classification performance using the decision tree ML model on commonly used datasets, such as CICIDS and BOT-IOT. They achieved 96% detection accuracy for anomaly detection. However, they did not mention the false alarm rate of the model. Similarly, a research paper by I. Sharafaldin [115] discussed the selection of appropriate ML algorithms. They used the CICIDS-2017 dataset with seven different ML algorithms but only focused on anomaly detection. To minimize the computational complexity, N. Kunhare [116] proposed a swarm optimization technique to select features of importance for the ML algorithm. The model was tested with the random forest classifier for binary classification and achieved 99% accuracy. However, one major drawback of ML approaches for anomaly detection is the high false alarm rate, which can not be neglected in real-time.
Deep Learning techniques are widely used for anomaly-based IDS nowadays because the deep network can, on its own, learn valuable features without any feature selection techniques. Recurrent Neural Network (RNN)-based IDS was developed by Yin et al. [117] for binary and multiclass classification on the NSL-KDD dataset. The model achieved the best accuracy using 80 hidden nodes with 0.1 and 0.5 learning rates for the binary, and multiclass classification, respectively. Their results also depict that different hidden neurons and learning rates affect the model’s accuracy. However, the main disadvantage of this model is that it increases computational complexity, resulting in high training time and low detection rate. Table 1. shows published papers reviewed based on the Network IDS with different publicly available datasets.
A comparative study of different DL and ML-based IDS was conducted by Naseer et al. [118] for the NSL-KDD dataset. Their results showed that LSTM and deep CNN achieved higher detection accuracy when compared to other models. Xiao et al. [119] proposed the CNN-based model to perform feature extraction using Component Analysis and Auto Encoder, which transform the feature set of one-dimension into a two-dimensional matrix. The converted two-dimensional matrix is fed as an input into the Convolutional Neural Network. The model was performed on the KDD CUP’99 dataset, and the performance metric was the running time during the training and testing phase. However, this study is limited as it achieves a lower detection rate for the U2R and R2L attack classes when compared to other attack classes.
To address the limitation of class imbalance within the labeled class instances, Jiang et al. [120] proposed an IDS by combining CNN and bidirectional Long Short-Term Memory (LSTM). SMOTE is used to increase the minority samples that help the model to learn the whole features [121]. Experiments were performed using UNSWNB15 and NSL-KDD datasets. Their approach received higher performance in terms of accuracy and misclassification rates. Due to the complex structure, the model incurred a higher training time.
There are other recent deep-learning approaches in the literature for IDS that are worth mentioning. For instance, Albara et al. [122] proposed a DL-based IDS with a four-layer deep fully connected architecture and a probability distribution-based technique to classify attacks. The method achieved an average intrusion detection rate of 93.21%. However, the authors stated the need for a lightweight version of their system for effective and efficient IDS, which is a limitation. Also, a Deep Belief Network classifier was proposed by Malik et al. [123] to address security challenges, which are scalability, privacy, and trust in IOT devices. The model was evaluated on the TON_IoT weather dataset and achieved an average accuracy of 86.3%. However, the authors claim that a lack of hyperparameters evaluation in the study affects the model’s accuracy. Another study presented in [124] developed the FSO-LSTM model to detect the Denial of Service attack on their developed dataset and used CIDCC-001, UNSW-NB15, and NSL-KDD datasets to compare the results. This study used the firefly swarm optimization technique to extract the features and then applied the LSTM classifier to classify the attacks. The study gave promising results with an average of 98% detection accuracy. However, the high dimensionality of features increased the training time. Sharma et al. [125] developed a GAN-based DNN model with the UNSW-NB15 dataset and achieved 84% accuracy. The GAN was used to generate synthetic data of minority attacks to resolve the class imbalance in the dataset, and a 91% accuracy was achieved.
Some of the previously discussed machine learning and deep learning IDS with high accuracy neglect consideration of the overfitting problem and use of real-world IoT traffic data, which impacts their model accuracy, memory consumption, and detection rate. To overcome those impacts, we believe that our IDS should be capable of handling imbalanced datasets by using a superior method. For that, we propose an IDS using the PCC-CNN method to detect the anomalies in binary and multiclass classification. In this model, we focus on handling overfitting, using feature engineering and relevant IoT traffic datasets. Also, we manipulate our model to get the configuration with the best results. Finally, we compare the model performance and performance metric with the traditional ML methods.
3 Methodology
This section discusses the datasets, the preprocessing steps, and the evaluation metrics for our current study. The simulation was performed on a machine with a 3.30GHz CPU. We used Python programming language for implementing the ML algorithms with the following libraries: NumPy and Pandas for data manipulation, Scikit-Learn for implementing ML techniques, and Matplotlib to visualize the performance.
3.1 Dataset used
A total of three publicly available datasets were used. Each dataset is explained below.
3.1.1 NSL-KDD
This is the new version of the benchmark dataset KDDcup99. The critical limitation in the KDDcup99 dataset is a large number of redundant records, which causes the learning algorithm to be biased toward the expected records and causes evaluation results to be limited. The NSL-KDD dataset [126] contains two files, KDD_Test and KDD_Train, in a ċsv format. Both files are not recorded from the same probability distribution, which makes it more realistic. The measuring attack is DDoS or Distributed Denial of Service, a malicious attempt to disrupt the traffic of a targeted server. The simulated attacks can fall into any one of the following four categories.Footnote 1
-
1.
DoS (Denial of service): IT recorded when overloading the server with too many requests to be handled. Examples of this are Smurf, Neptune, and Teardrop attacks.
-
2.
Probe: The hacker scans the network to misuse a known vulnerability. Examples are Satan, ipsweep, and Nmap attacks.
-
3.
R2L (remote to local): attacks in which the attacker tries to gain local access to unauthorized information by sending packets to the victim’s machine. Examples are eject, load module, and Perl attacks.
-
4.
U2R (User to Root): the attacker gets core access to the system using his regular account to exploit the system vulnerabilities. Some examples are ftp_write, guess the password and imap attacks.
The attack instances are presented in Table 2.
3.1.2 CICIDS2017
This is a benchmark dataset for analyzing network traffic. It was developed within an emulated environment at the Canadian Institute for Cybersecurity (CIC), University of New Brunswick, Canada [128]. It contains 80 network features and provides reliable normal and malicious network flows. The data were collected for five days. ISCXFlow meter was used to generate the CSV files of the dataset from pcap files. Then, it extracted the normal and abnormal behavior based on the SSH, FTP, HTTP, and email protocols. It contains the 11 attack class instances besides the benign (standard) ones. The 11 attack types combine into four-attack categories: Botnet, DoS, Firewall, and Port Scan.Footnote 2
The simulated attacks can fall into the following four categories, ’BENIGN’; ‘Botnet’; ’DoS’; ’Firewall’; or ’Port Scan.’
-
1.
Botnet: The network created by malware-infected computers is called a botnet attack. The attacker tries to perform malicious activities without knowing their owners. This can be accomplished remotely and creates DDoS attacks. The bot masters control the computers.
-
2.
DoS: It is a Denial of Service attack. This attack is easy to perform as it does not require high bandwidth. Also, it is hard to detect because it takes longer to complete an HTTP request.
-
3.
Firewall: This is not a profound attack but a sub-attack category based on the Internet. Hence the name firewall. The attack consists of FTP-Patator, SSH-Patator, and infiltration (Same as Probe). The attacker tries to gain remote system access and complete control over the system.
-
4.
Port Scan: It is performed by the Nmap tool. This attack is used to collect information for attackers to access the system. The attacker can learn about the vital information of the connected devices, like the operating system, running devices, and port status.
The attack instances are presented in Table 3.
3.1.3 IOTID20
The IOTID20 [130] uses raw network packet files created by IOTID [131] dataset. The dataset is created for academic purposes, and it is publicly available. Making the IoT network by two intelligent home devices, NUGU (NU 100) is an AI-based speaker, and EZVIZ Wi-Fi camera (C2C Mini O plus 1080P) along with different smartphones and laptops were connected via WI-FI router. Attacks like spoofing, scanning, Dos, and Man in the Middle were simulated using Nmap tools.Footnote 3
The simulated attacks can fall into the following four categories [132]. ’Dos’, ’Mirai’, ’Scan’, ’MITM ARP’.
-
1.
Dos: A denial of Service attack occurs when a single source node or end node encounters malicious activities. The attacker tries to flood the target server by blocking the services to other devices.
-
2.
Mirai: The attacker tries to turn the victim’s software into a network of remotely controlled bots.
-
3.
Scan: The attacker tries manipulating the information during the process. They try to gather the data by hardware while scanning the devices.
-
4.
MITM ARP Spoofing: Man-in-the-Middle attack is widespread in cyberattacks. The attacker sits between the connection of two servers and manipulates the traffic.
The attack instances are shown in Table 4.
3.2 The pipeline
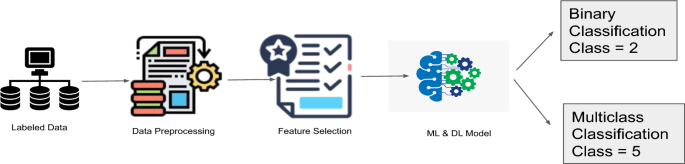
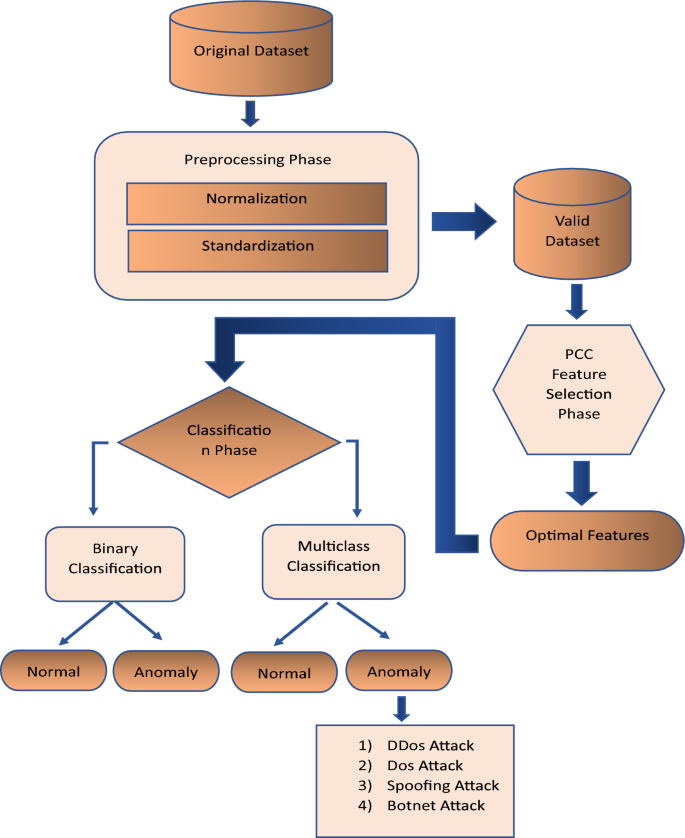
This section discusses the applied PCC-CNN model and ML algorithms employed for detecting malicious network traffic. We compare the performance of the designed PCC-CNN model with the ML models. Figure 1 shows an overview of the steps followed in this work. The three datasets used were in \(\cdot csv\) file format and followed the same methodology steps. First, we load the data and handle the datatype mismatch, missing or null values, and infinite values. Then, we preprocess the cleaned data to extract the features. Then, we performed feature selection and binary (normal or abnormal) and multiclass (4 class attack categories \(w \cdot r \cdot t \cdot\) each dataset) classification. The last step is to evaluate the performance metrics and compare the results.
Figure 2 shows the step-by-step process that followed to implement the model. For the classification phase, either CNN or ML models were used to predict the binary and multiclass classification. Details of all the steps are discussed in subsequent subsections.
3.2.1 Data pre-processing
It is also known as cleaning the data or data massaging. It includes removing redundant features. Null/Nan values must be deleted or replaced with substitute values, and the sub-attack instances must be merged into respected attack instances. For each dataset, we divided the output into binary and multiclass classifications. For binary classification, we used two classes, whereas for multiclass classification, we used five classes, including the regular class. Then, we normalize the data between 0 and 1. The critical dimension for this stage is that the data should be compatible with more than one algorithm for consistency and to reduce computation complexity.
3.2.2 Feature selection
Feature extraction is essential while applying ML or DL models as it influences prediction accuracy [134]. With the correct feature selection, we can reduce the over-fitting of the model, improve the accuracy, reduce the model cost, and also help to reduce the training time [135]. Feature extraction is needed to improve learning accuracy by removing irrelevant features and applying feature transformation. Our model uses the feature importance technique based on our proposed Pearson Correlation Coefficient method [136]. The proposed method evaluates the values of an attribute by measuring the correlation between the instances and class [137]. To reduce overfitting, we selected features contributing most to the classification. This method followed the three-stage approach mentioned in [138]. The method first calculates Pearson’s correlation, correlation attribute ranking, and lastly selects features of a new dataset. This method has mainly been used when two variables are normally distributed. We choose the cut-off value to reduce irrelevant features. The cut-off value is evaluated to get the best threshold. The threshold of feature importance is a correlation for this approach, which varies from 0.02 to 0.5 depending on the dataset. The threshold values for each dataset are shown below in Table 5.
With the defined threshold, we only allow the feature with an above 0.5 & 0.2 correlation between the components. We selected this value based on the research in [139], which concludes that correlation threshold values less than 0.2 are considered negligible, and the threshold value of 0.8 is considered the best-correlated value. The paper [140] states that to gain better results, the trial and tested thresholds are 0.2 to 0.5, which can be varied based on the attack instances within the datasets.
3.2.3 ML algorithm
We deployed a supervised ML methodology for designing and developing an anomaly-based IDS. This work used binary and multiclass classification on the datasets, including classifiers LR, LDA, KNN, CART, and SVM [141]. LR (Logistic Regression) estimates the probability of an event based on the previous data provided. LDA (Linear Discriminant Analysis) predicts the likelihood that a new set of inputs belongs to every class. KNN (K Nearest Neighbors) estimates how likely a data point is to be a member of one or more groups. CART (Classification and Regression Tree) is also a decision tree. A chart-like tree structure uses a branching method to demonstrate every possible decision outcome. SVM (Support Vector Machine) is a discriminative classifier that efficiently classifies new data instances in the neighboring location.
3.2.4 PCC-CNN
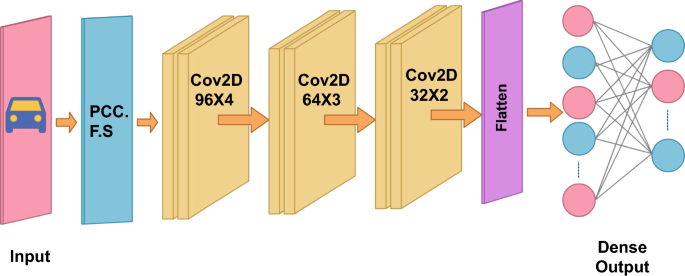
Our model aims to build an efficient and lightweight IDS. Our model uses Pearson Correlation Coefficient (PCC) for feature selection and Convolutional Neural Network (CNN) as the best classification model. It is nicknamed PCC-CNN. The PCC is a Filter based algorithm and is a well-known feature selection technique [142]. This feature selection method has been used in many IDS on variants of the dataset [143, 144]. The benefit of using a filter-based approach is that it is computationally efficient [145]. The features detected by PCC are fed to CNN for training (See Fig. 3).
CNN is a state-of-the-art model for classification tasks. It combines multiple filters to the data to learn the features and use them for classification. CNN contains input, hidden, and output layers. The input layer starts with the convolutional layers that apply an activation function. The hidden layer has pooling layers that scale down the data to reduce the feature dimensionality, and at last, fully connected layers perform classification.
The designed CNN model contains three convolution layers with respective sizes of 96 multiplied by 4, 64 multiplied by 3, 32 multiplied by 2, and a rectified linear unit activation function (RELU). RELU is a linear function that outputs the input directly if it is positive, or it will output zero if otherwise. The flattening layer reshapes the values from the previous layer into one-dimensional. Three dense layers with 512,128, 32 and 2 were applied with RELU activation in the dense layers except the last, which uses the Softmax activation function. Softmax will help normalize the output in probabilistic form. The dense layers see the values in non-linear form. The adaptive moment estimation (Adam) optimizer tunes the parameter values in the final layer. The number class parameter is set to 2 or 5 depending on whether the expected outcomes are binary or multiclass. Sparse categorical cross-entropy was used for the loss function because the output is in categorical labels. The model was trained over five epochs for binary classification and multiclass classification with 64 batch sizes.
3.2.5 Evaluation criteria
Evaluating a model is an integral part of any effective model. The criteria are different for each model depending upon the application and datasets used. The evaluation metrics help us decide which technique is best suited for a particular job. Following are some list criteria we used to evaluate the model’s performance.
-
Confusion matrix
It is used to visualize the performance of a method. It summarizes prediction results on a classification problem. True Positive (TP), True Negative (TN), False Negative (FN), and False Positive (FP) for multiple classes can be given from the confusion matrix. The definitions are given below:
TP: All instances of any particular class are classified as the correct class.
FP: All the non-instances of any particular class are classified as the correct class.
TN: All the non-instances of a class are not classified as the correct class.
FN: All instances of a particular class that are not classified as correct.
-
Accuracy
The accuracy of a model determines which model is best for identifying patterns between variables. The equation represents a measure of a single class.
$$\begin{aligned} Accuracy = \frac{TP+TN}{TP+TN+FP+FN} \end{aligned}$$ -
Precision
It measures the number of accurate optimistic predictions of a model classified by comparing the actual optimistic predictions. The equation is as follows.
$$\begin{aligned} Precision = \frac{TP}{TP+FP} \end{aligned}$$ -
Recall
It is an actual positive rate. It is a measure of optimistic predictions that the model classifies compared with the proper positive values in the real data. The equation is as follows.
$$\begin{aligned} Recall = \frac{TP}{TP+FN} \end{aligned}$$ -
F1-Score
It is a weighted average of precision and recall. Provides test accuracy.
$$\begin{aligned} F1-Score = \frac{2*Precision*Recall}{Precision+Recall} \end{aligned}$$ -
False Alarm Rate(FAR)
It is a probability of a false prediction. It measures the number of false alarms per the total number of non-events. The equation is as follows.
$$\begin{aligned} FAR = \frac{FP}{TP+FP} \end{aligned}$$ -
ROC-AUC Curve
ROC (Receiver operating characteristics) – AUC (Area under the curve) is used for the classification problems at different threshold settings. AUC represents the degree or measure of separability. ROC is a probability curve. It tells how much the model is capable of distinguishing between the classes. The higher the AUC, the better model is. The curve is plotted with a True positive rate (on the y-axis) against the false positive rate (on the x-axis).
4 Results
In this section, the outcome of the model is evaluated. The computer used for this work had the following specifications: i9-9820X 3.30GHz CPU, 2 TB of memory, and Linux Ubuntu 20.04.1 LTS operating system. Python scripts were developed under Anaconda Jupyter Notebook. The present study calculated the evaluation metrics from Python Sklearn metrics libraries and the confusion matrix. Accuracy and false alarm rate are frequently used metrics in anomaly-based intrusion detection research.
The model was trained and tested with 10-fold cross-validation. Training used 80% of the data, and testing used 20%. The supervised ML models are LR, LDA, KNN, DT, and SVM, and the DL model is PCC-CNN for each dataset. The PCC-CNN model iterates for five epochs. The results show several findings that need further evaluation. Tables 6, 7, and 8 present all the metrics results for three used datasets and binary and multiclass classification scenarios.
4.1 Binary classification: anomaly detection
In binary classification, the two classes were used as the outcome. 0 represents the regular instances, and 1 illustrates the abnormal (attack) instances. The obtained results are summarized in Tables 6,7 & 8, respectively.
Table 6 provides the classification accuracy of the ML models for each dataset. The supervised models, namely KNN and CART, outperform with 100% accuracy achieved compared to other ML models. However, other models reached approximately 92 to 97%. This indicates that with more extensive training sets, accuracy can be improved. The proposed PCC-CNN model obtained 99% accuracy but with a lower computational time when compared to all five ML models.
Tables 7 and 8 represent the performance metrics comparison of precision, recall, F1-score, and FAR (False Alarm Rate), which provides the model’s overall performance. Overall, accuracy and recall of 98% is achieved by KNN and CART algorithms. However, Our PCC-CNN model performed better on the test samples and achieved 98% in both precision and recall for all three datasets compared to the ML Algorithm, except KNN and CART models. In the F1-score evaluation, 97% was obtained, with approximately the lowest false alarm rate of 0.00. On the other hand, PCC-CNN achieved a better false alarm rate in the case of KDD_Test results. This indicates that it is well suited for detecting anomalies in unseen data. On the other hand, ROC curve plots (Figs. 4 & 5) imply that the smaller the training sets, the lower numbers retrieved. Hence, larger datasets are required for the training process to be effective in the initial phase. Refer to Figs. 4 & 5.
4.2 Multiclass classification: attack classification
In multiclass classification, the five classes were used as the outcome. 0 represents the regular instances, and the remaining (1-4) illustrates the abnormal (attack) instances. The obtained results are summarized in Tables 9,10 & 11, respectively.
Table 9 provides the classification accuracy of each dataset’s ML and PCC-CNN models. The Supervised models, namely, KNN and CART, outperform better with 98% and 99% accuracy achieved compared to other ML models. On the contrary, the SVM model provides inferior results, particularly for the unbalanced datasets (IOTID20 datasets). That indicates the models could not perform effectively under the training phase with varying class instances. The flip slide is that the PCC-CNN model achieved varying accuracy for individual datasets and took more time to train the model.
Tables 10, &11 represent the performance metrics comparison of precision, recall, F1-score, and FAR (False Alarm Rate), which provides the model’s overall performance. Overall, accuracy and recall of 98% are achieved. In contrast, PCC-CNN has a precision of 76% and recall of 70& compared to the ML models. In the F1-score evaluation, overall, 97% was obtained with a comparatively high false alarm rate. The proposed PCC-CNN model performs better with a low false alarm rate. This indicates that it is well suited for detecting anomalies in unseen data. On the other hand, ROC curve plots (Figs. 6 & 7) imply that the smaller the training sets, the lower the obtained true positive rate. Hence, larger datasets are required for the training process to be effective in the initial phase.
Overall, the analyzed ML and PCC-CNN models achieved a good multi-class classification performance on the datasets with relatively unbalanced class proportions. The obstacles remain the lack of underrepresented classes. Therefore, for these models to distinguish between the different types of cyber-attacks, training them with a balanced flow of each type is essential.
5 Discussion
The developed PCC-CNN model was evaluated and compared with PCC-ML models. Its performance is based on binary and multiclass classification, with 2 and 5 classes, respectively. The preprocessing steps follow the same approach for both classifications. After extracting the important features using the Pearson Correlation Coefficient technique, five supervised models, LR, LDA, KNN, CART, and SVM, were deployed to provide IDS for an IoT system. The 10-fold cross-validation is used with 20% as the test dataset. The performance metrics are accuracy, precision, recall, and F1 scores. The most important metric (false alarm rate) was also calculated from the confusion matrix to evaluate the model’s performance. Afterward, the proposed PCC-CNN model was compared with the traditional ML models. The ML models achieved reliable performance in both scenarios and scored higher when trained with more significant attack instances. KNN and CART algorithms obtained the best results for both binary and multiclass classification scenarios with approximately 98% and 99% respectively in accuracy and less than 0.005 false alarm rate. As KNN takes the entire dataset for training, it takes longer for a prediction. Also, the CART algorithm overfits in multiclass classification. Despite the significantly lower accuracy results (approximately 78% to 88%) in the multiclass classification, specifically with LR, LDA, and SVM models, they are advantageous in detecting intrusions. However, our model for both classification scenarios achieved an excellent overall performance, highlighting its suitability for anomaly detection when trained with smaller and more unbalanced datasets.
We compared the proposed model with the above-mentioned ML models. We received an overall 99% accuracy for the binary classification for all three datasets (NSL_KDD, CICIDS-2017, and IOTID20). We also observed comparatively similar and better performance in Precision, Recall, F1-Score, and importantly false alarm rate with less computational complexity. On the other side, multiclass classification did not perform better compared to binary classification. However, the multiclass classification model shows promising results with consistent performance metrics and a lower false alarm rate. Yet, We believe that increasing the number of epochs during the training will improve the model’s accuracy. Also, we observe that our proposed PCC-CNN model predicts the intrusions efficiently even with the imbalanced attack instances in the datasets used.
WE state that multiclass classification is more complex than binary classification, as it covers a variety of attacks. The major challenge of performing multiclass classification is the lack of attack instances in the dataset. Moreover, multiclass classification predicts multiple intrusions, which results in computationally complex training time.
6 Conclusion
The presented work developed an Anomaly-based intrusion detection system based on PCC-CNN. Three datasets (NSL-KDD, CICIDS2017, and IOTID20) covered different network attack instances. Our Deep Learning (PCC-CNN) model performed better when compared with the state-of-the-art ML approaches. We observed that our classification accuracy for multiclass classification is lower than the binary classification, but it can be improved if we train the model for more than five epochs. Compared to the ML model, the PCC-CNN model is computationally efficient. The proposed PCC-CNN model is crucial for any application of IDS. This can be deployed in real-time for measuring abnormal events or novel attacks in a network domain.
Future research is necessary to address the limitations of the presented work. To enhance the performance and strengthen the IDS, combinations of different model types can be used, such as combining deep learning and ensemble learning techniques. Additionally, steps should be taken to improve the missing data and outlier techniques since that is challenging for complex data. Use of various feature selection and extraction techniques can be implemented to observe the change in performance compared to the PCC-CNN model. A future study should aim to use the real-time dataset. Future research will consider the pipeline of real-time anomaly detection, which may result in unforeseen novel requirements in the present study. Moreover, future research should include different imbalanced attacks and data handling techniques to provide a more reliable and robust IoT intrusion detection.
Data availability
The NSL-KDD dataset and CICIDS-2017 dataset are provided by the Canadian Institute of Cybersecurity (CIC), University of New Brunswick, and are publicly available for researchers upon request. The NSL-KDD dataset can be downloaded from this link: https://www.unb.ca/cic/datasets/nsl.html.(last accessed Apr 20,2023)[127]. Details of the dataset and its underlying principles are outlined in [126]. The CICIDS-2017 dataset can be downloaded from this link: https://www.unb.ca/cic/datasets/ids-2017.html.(last accessed Apr 20,2023)[129] Details of the dataset and its underlying principles are outlined in [128]. The IOTID-20 dataset is provided by the IEEE Dataport, and it is created for academic purposes. The IOTID-20 dataset is publicly available for researchers upon request. The IOTID-20 dataset can be downloaded from this link: https://ieee-dataport.org/open-access/iot-network-intrusion-dataset.(last accessed Apr 20,2023)[133]. Details of the dataset and its underlying principles are outlined in [130].
Notes
The NSL-KDD dataset can be accessed and downloaded from the provided link: https://www.unb.ca/cic/datasets/nsl.html. (last accessed Apr 20, 2023) [127].
The CICIDS2017 dataset can be accessed and downloaded from the provided link: https://www.unb.ca/cic/datasets/ids-2017.html.(last accessed Apr 20, 2023) [129].
The IOTID20 dataset can be accessed and downloaded from the provided link: https://ieee-dataport.org/open-access/iot-network-intrusion-dataset.(last accessed Apr 20, 2023) [133].
References
Kyriazis D, Varvarigou T, White D, Rossi A, Cooper J. “Sustainable smart city IoT applications: Heat and electricity management & Eco-conscious cruise control for public transportation,”. IEEE 14th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM). Madrid, Spain. 2013;2013:1–5. https://doi.org/10.1109/WoWMoM.2013.6583500.
Shanzhi Chen, et al. A vision of IoT: Applications, challenges, and opportunities with china perspective’’. IEEE Int Things J. 2014;1(4):349–59.
Malche Timothy, Maheshwary Priti. “Internet of Things (IoT) for building smart home system.” 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC). IEEE, 2017.
Fotios Zantalis, et al. A review of machine learning and IoT in smart transportation’’. Future Int. 2019;11(4):94.
Mezghani Emna, Exposito Ernesto, Drira Khalil. A model-driven methodology for the design of autonomic and cognitive IoT-based systems: Application to healthcare. IEEE Trans Emerg Topics Comput Intel. 2017;1(3):224–34.
Zhao Ji-chun et al. “The study and application of the IOT technology in agriculture.” 2010 3rd international conference on computer science and information technology. Vol. 2. IEEE, 2010.
Ou Qinghai et al. “Application of internet of things in smart grid power transmission.” 2012 third FTRA international conference on mobile, ubiquitous, and intelligent computing. IEEE, 2012.
Bichi BY, Islam SU, Kademi AM, Ahmad I. An energy-aware application module for the fog-based internet of military things. Discov Internet Things. 2022;2(1):4.
Khanna A, Kaur S. Internet of Things (IoT), Applications and Challenges: A Comprehensive Review. Wireless Pers Commun. 2020;114:1687–762. https://doi.org/10.1007/s11277-020-07446-4.
Saba T, Saba T, et al. Real-time anomalies detection in the crowd using convolutional extended short-term memory network. J Inform Sci. 2021. https://doi.org/10.1177/01655515211022665.
Khanna Abhishek, Kaur Sanmeet. Internet of things (IoT), applications and challenges: a comprehensive review. Wirel Pers Commun. 2020;114:1687–762.
Kraijak Surapon, Tuwanut Panwit. “A survey on IoT architectures, protocols, applications, security, privacy, real-world implementation and future trends.” 11th international conference on wireless communications, networking and mobile computing (WiCOM 2015). IET, 2015.
Schneider S. The industrial internet of things (iiot) applications and taxonomy. Internet Things Data Anal Handb. 2017;41–81.
Khan WZ, et al. Industrial internet of things Recent advances enabling technologies and open challenges. Comput Electr Eng. 2020;81: 106522.
Li Shan, Iqbal Muddesar, Saxena Neetesh. “Future industry internet of things with zero-trust security.” Information Systems Frontiers 2022;1–14.
Ahmad I. Discover Internet of Things editorial, inaugural issue: Welcome from Editor-in-Chief. Discov Internet Things. 2021;1:1–4.
Alkahtani H, Aldhyani THH, Al-Yaari M. Adaptive anomaly detection framework model objects in cyberspace. Appl Bionics Biomech. 2020;6660489:14.
Tang M, Alazab M, Luo Y. Big data for cybersecurity: vulnerability disclosure trends and dependencies. Inst Electr Electron Eng Trans Big Data. 2019;5(3):317–29.
Zerihun BM, Olwal TO, Hassen MR. Design and Analysis of IoT-Based Modern Agriculture Monitoring System for Real-Time Data Collection. In: Computer Vision and Machine Learning in Agriculture, vol. 2. Singapore: Springer Singapore; 2022. p. 73–82.
AL-Sarawi Shadi, Anbar Mohammed, Abdullah Rosni, AI Hawari Ahmed B. Internet of things market analysis forecasts,2020-2030. Worlds4, 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability, IEEE,2020, 978-1-7281-6823-4/20.
Tanzila Saba, Amjad Rehman, Tariq Sadad, Hoshang Kolivand, Ali Bahaj Saeed. Anomaly-based intrusion detection system for IoT networks through deep learning model. Comput Electr Eng. 2022;99: 107810.
Misbahuddin S, Zubairi JA, Saggaf A, Basuni J, A-Wadany S, Al-Sofi A. “IoT based dynamic road traffic management for smart cities,” 2015 12th International Conference on High-capacity Optical Networks and Enabling/Emerging Technologies (HONET), Islamabad, 2015:1- 5, DOIurlhttps://doi.org/10.1109/HONET.2015.7395434.
Ahmed Bahaa, et al. Monitoring real time security attacks for IoT systems using DevSecOps: a systematic literature review’’. Information. 2021;12(4):154.
Marzano Artur et al. “The evolution of bashlite and mirai iot botnets.” 2018 IEEE Symposium on Computers and Communications (ISCC). IEEE, 2018.
Tomer Vikas, Sharma Sachin. Detecting iot attacks using an ensemble machine learning model. Future Int. 2022;14(4):102.
Jacobs S. “Researchers Hack Into Michigan’s Traffic Lights.” MIT technology review. https://www.technologyreview.com/2014/08/19/171586/researchershack-into-michigans-traffic-lights/. Accessed 29 Sept 2020.
Khan MA, Salah K. IoT security: Review, blockchain solutions, and open challenges. Future Gen Comput Syst. 2018;82:395–411. https://doi.org/10.1016/j.future.2017.11.022.
Zahra A, Shah MA. “IoT-based ransomware growth rate evaluation and detection using command and control blacklisting,” 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, 2017;1-6, DOIurlhttps://doi.org/10.23919/IConAC.2017.8082013
Gurulakshmi K, Nesarani A. “Analysis of IoT Bots Against DDOS Attack Using Machine Learning Algorithm,” 2018 2nd International Conference on Trends in Electronics and Informatics (ICOEI), 1 Sept. 2017, https://doi.org/10.1109/icoei.2018.8553722
Dong Bo, Wang Xue. “Comparison deep learning method to traditional methods using for network intrusion detection.” 2016 8th IEEE international conference on communication software and networks (ICCSN). IEEE, 2016.
Kruegel C, Valeur F, Vigna G. Intrusion detection and correlation: challenges and solutions, vol. 14. Springer Science & Business Media; 2004.
Benkhelifa Elhadj, Welsh Thomas, Hamouda Walaa. A critical review of practices and challenges in intrusion detection systems for IoT: Toward universal and resilient systems. IEEE Commun Surv Tutor. 2018;20(4):3496–509.
Kocher Geeta, Kumar Gulshan. Machine learning and deep learning methods for intrusion detection systems: recent developments and challenges. Soft Computing. 2021;25(15):9731–63.
Margolis J, Oh TT, Jadhav S, Kim YH, Kim JN. “An In-Depth Analysis of the Mirai Botnet,” 2017 International Conference on Software Security and Assurance (ICSSA), Altoona, PA, 2017, pp. 6-12, https://doi.org/10.1109/ICSSA.2017.12
Anthi E, Williams L, Slowinska M, Theodorakopoulos G, Burnap p. A supervised intrusion detection system for smart home IoT devices. IEEE Int Things J. 2019;6(5):9042–53.
Arshad J, Azad MA, Abdeltaif MM, Salah K. An intrusion detection Framework for energy-constrained IoT devices. Mech Syst Signal process. 2020;136: 106436.
Liao H-J, Lin C-HR, Lin Y-C, Tung K-Y. Intrusion Detection System: A Comprehensive Review. J Netw Comput Appl. 2013;36(1):16–24. https://doi.org/10.1016/j.jnca.2012.09.004.
Shakhov V, Jan SU, Ahmed S, Koo I. “On Lightweight Method for Intrusions Detection in the Internet of Things,” 2019 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Sochi, Russia, 2019;1-5.
Mell Peter. Understanding intrusion detection systems, IS Management Handbook, 2003;409–418, Auerbach Publications
Jyothsna VVRPV, Rama Prasad, Munivara Prasad K. A review of anomaly based intrusion detection systems’’. Int J Comput Appl. 2011;28(7):26–35.
Anhtuan Le, et al. A specification-based IDS for detecting attacks on RPL-based network topology’’. Information. 2016;7(2):25.
Mehmood Yasi, et al. “Intrusion detection system in cloud computing: challenges and opportunities.” 2013 2nd national conference on information assurance (NCIA). IEEE, 2013.
Morin Benjamin, Me Ludovic, Debar Herve, Ducasse Mireille. M2D2: A formal data model for IDS alert correlation, International Workshop on Recent Advances in Intrusion Detection, 115–137,2002
Pacheco Jesus, Hariri Salim. “IoT security framework for smart cyber infrastructures.” 2016 IEEE 1st International Workshops on Foundations and Applications of Self Systems (FAS W). IEEE, 2016.
Fadlullah ZM, et al. State-of-the-art deep learning Evolving machine intelligence toward tomorrow intelligent network traffic control systems. IEEE Commun Surv Tutor. 2017;19(4):2432–55.
Wang X, Davidson NJ. “The Upper and Lower Bounds of the Prediction Accuracies of Ensemble Methods for Binary Classification,” 2010 Ninth International Conference on Machine Learning and Applications, Washington, DC, 2010:373-378.
Peddabachigari S, Abraham A, Grosan C, Thomas J. Modeling intrusion detection system using hybrid intelligent systems. J Netw Comput Appl. 2007;30(1):114–32. https://doi.org/10.1016/j.jnca.2005.06.003.
Gang Kou, et al. Multiple criteria mathematical programming for multi-class classification and application in network intrusion detection. Inform Sci. 2009;179(4):371–81.
Mulay Snehal A, Devale PR, Garje GV. Intrusion detection system using support vector machine and decision tree. Int J Comput Appl. 2010;3(3):40–3.
Uma M, Ganapathi P. A Survey on Various Cyber Attacks and their Classification. Int J Netw Secur. 2013;15(5):390–6.
Jhaveri Rutvij H, Patel Sankita J, Jinwala Devesh C. “DoS attacks in mobile ad hoc networks: A survey.” 2012 second international conference on advanced computing & communication technologies. IEEE, 2012.
Goyal Priyanka, Batra Sahil, Singh Ajit. A literature review of security attack in mobile ad-hoc networks. Int J Comput Appl. 2010;9(12):11–5.
Pradip JM, et al. A survey of mobile ad hoc network attacks. Int J Eng Sci Technol. 2010;2(9):4063–71.
DasGupta Bhaskar, Mobasheri Nasim, Yero Ismael G. On analyzing and evaluating privacy measures for social networks under active attack. Inform Sci. 2019;473:87–100.
Keerthika M, Shanmugapriya D. Wireless sensor networks: Active and passive attacks-vulnerabilities and countermeasures. Global Trans Proc. 2021;2(2):362–7.
Keerthika M, Shanmugapriya D. Wireless sensor networks: Active and passive attacks-vulnerabilities and countermeasures. Global Trans Proc. 2021;2(2):362–7.
Raich Anagha, Gadicha Vijay. “Overview of passive attacks in cloud environment.” AIP Conference Proceedings. Vol. 2424. No. 1. AIP Publishing LLC, 2022.
Bhavsar M, Roy K, Liu Z, Kelly J, Gokaraju B. Intrusion-Based Attack Detection Using Machine Learning Techniques for Connected Autonomous Vehicle. In Fujita,H., Fournier-Viger, P., Ali, M., Wang, Y. (eds) Advances and Trends in Artificial Intelligence. Theory and Practices in Artificial Intelligence. IEA/AIE 2022. Lecture Notes in Computer Science(), 2022;13343. Springer, Cham. https://doi.org/10.1007/978-3-031-08530-7_43.
AI-Hamar Y, Kolivand H, Tajdini M, Saba T, Ramachandran V. Enterprise Credential Spear-phishing attack detection. Comput Electr Eng. 2021;94:107363.
Tabassum A, Lebda W. Security framework for iot devices against cyber-attacks. arXiv preprint arXiv:1912.01712. 2019.
Vemuri VR. Enhancing computer security with smart technology. Auerbach Publications; 2005.
Xiaocong Qian, Jidong Zhang. “Study on the structure of “Internet of Things(IOT)” business operation support platform,” 2010 IEEE 12th International Conference on Communication Technology, Nanjing, China, 2010;1068-1071, https://doi.org/10.1109/ICCT.2010.5688537.
Aziz Rao Tariq, Haq EU. Security challenges facing IoT layers and its protective measures’’. Int J Comput Appl. 2018;179(27):31–5.
Zhong C-L, Zhu Z, Huang R-G. Study on the IOT Architecture and Gateway Technology,.” 14th International Symposium on Distributed Computing and Applications for Business Engineering and Science (DCABES). Guiyang, China. 2015;2015:196–9. https://doi.org/10.1109/DCABES.2015.56.
Wu Miao, Lu Ting-Jie, Ling Fei-Yang, Sun Jing, Du Hui-Ying. “Research on the architecture of Internet of Things,” 2010 3rd International Conference on Advanced Computer Theory and Engineering(ICACTE), Chengdu, 2010;V5-484-V5-487, https://doi.org/10.1109/ICACTE.2010.5579493.
Zhong C-l, Zhu Z, Huang R-G. “Study on the IOT Architecture and Access Technology,.” 16th International Symposium on Distributed Computing and Applications to Business, Engineering and Science (DCABES). Anyang, China. 2017;2017:113–6. https://doi.org/10.1109/DCABES.2017.32.
Alaba FA, Othman M, Hashem IA, Alotaibi F. Internet of Things security: A survey. J Netw Comput Appl. 2017;15(88):10–28.
Sethi P, Sarangi SR. Internet of things: architectures, protocols, and applications. J Electr Comput Eng. 2017;2017.
Karthik Kumar Vaigandla. SandyaRani Bolla, Radhakrishna Karne, “A Survey on Future Generation Wireless Communications-6G: Requirements, Technologies, Challenges and Applications". Int J Adv Trends Comput Sci Eng. 2021;10(5):3067–76.
Sula Edvald. A Review of Network Layer and Transport Layer Attacks on Wireless Networks. Int J Mod Eng Res (IJMER). 2019;8(12):23–7.
Farhad AS, Maede A-T, Hamid M. DoS, impersonation and de-synchronization attacks against an ultra-lightweight RFID mutual authentication protocol for IoT. J Supercomput. 2018;74:509–25.
Eirini Anthi, et al. A Supervised Intrusion Detection System for Smart Home IoT Devices’’. IEEE Int Things J. 2019;6(5):9042–53.
Madoka S, Ramaswamy R, Tripathi S. Internet of Things (IoT): A literature review. J Comput Commun. 2015;3(5):164.
Mahmoud R, Yousuf T, Aloul F, Zualkernan I. Internet of things (IoT) security: current status, challenges, and prospective measures. 10th International Conference for Internet Technology and Secured Transactions (ICITST) 2015, Dec 14 (pp. 336-341). IEEE.
Ioannou Christiana, Vassiliou Vasos. “The impact of network layer attacks in wireless sensor networks.” 2016 International Workshop on Secure Internet of Things (SIoT). IEEE, 2016.
King J, Awad AI. A distributed security mechanism for resource constrained IoT devices. Informatica (Slovenia). 2016;40(1):133–43.
Vaigandla K, Azmi N, Karne R. Investigation on intrusion detection systems (IDSs) in IoT. Int J Emerg Trends Eng Res. 2022;10(3).
Pea G-T. Anomaly-based network intrusion detection: Techniques, systems and challenges. Comput Secur. 2009;28(1):18–28.
Nguyen TTaGA. “A survey of techniques for internet traffic classification using machine learning,” IEEE Communications Surveys & Tutorials, 2008;10.4:56-76.
Lei JZaAG. “Network intrusion detection using an improved competitive learning neural network,” Communication Networks and Services Research, Vols. Second Annual Conference on. IEEE, 2004., p. Proceedings, 2004.
Deng CaHQ. “Network security intrusion detection system based on incremental improved convolutional neural network model,” Communication and Electronics Systems (ICCES), pp. International Conference on. IEEE, 2016.
Spadaccino P, Cuomo F. Intrusion detection systems for iot: opportunities and challenges offered by edge computing. J Future Evol Technol; 2022
Ghorbani AA, Lu W, Tavallaee M. Network Attacks. In: Network Intrusion Detection and Prevention. Advances in Information Security, vol. 47. Springer: Boston, MA; 2010. https://doi.org/10.1007/978-0-387-88771-5_1.
Anwar S, Mohamad Zain J, Zolkipli MF, Inayat Z, Khan S, Anthony B, Chang V. From intrusion detection to an intrusion response system: Fundamentals, requirements, and future directions. Algorithms. 2017;10(2):1–24.
Shaver A, Liu Z, Thapa N, Roy K, Gokaraju B, Yuan X. Anomaly based intrusion detection for iot with machine learning. In: 2020 IEEE Applied Imagery Pattern Recognition Workshop (AIPR). IEEE; 2020. p. 1–6.
Tabassum Aliya, Erbad Aiman, Guizani Mohsen. “A Survey on Recent Approaches in Intrusion Detection System in IoTs.” 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC). IEEE, 2019.
Wu H, Schwab S, Peckham RL. U.S. Patent No. 7,424,744. Washington, DC: U.S. Patent and Trademark Office; 2008.
Kruegel C, Toth T. Using Decision Trees to Improve Signaturebased Intrusion Detection," in Recent Advances in Intrusion Detection, RAID 2003. Lecture Notes in Computer Science. Berlin: Springer; 2003. p. 173–91.
Saba T, Sadad T, Rehman A, Mehmood Z, Javaid Q. Intrusion detection system through advanced machine learning for the Internet of things networks. IT prof. 2021;23(2):58–64.
Buczak AL, Guven E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun Surv Tutor. 2015;18(2):1153–76.
Pacheco, Jesus, Hariri Salim. “IoT security framework for smart cyber infrastructures.” 2016 IEEE 1st International Workshops on Foundations and Applications of Self Systems (FAS W). IEEE, 2016.
Khraisat A, Gondal I, Vamplew P. An Anomaly Intrusion Detection System Using C5 Decision Tree Classifier. Cham: Springer International Publishing; 2018. p. 149–55.
Chauhan H, Kumar V, Pundir S, Pilli ES. “A Comparative Study of Classification Techniques for Intrusion Detection,.” International Symposium on Computational and Business Intelligence. New Delhi. 2013;2013:40–3.
Khraisat A, Gondal I, Vamplew P, Kamruzzaman J. Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity. 2019;2(1):1–22.
Liao H-J, Richard Lin C-H, Lin Y-C, Tung K-Y. Intrusion detection system: a comprehensive review. J Netw Comput Appl. 2013;36(1):16–24.
Fadlullah Zubair Md, et al. State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems’’. IEEE Commun Surv Tutorials. 2017;19(4):2432–55.
SAADI C, CHAOUI H. Proposed security by IDSAM in the Android system. In 2019 5th International Conference on Optimization and Applications (lCOA) (pp. 1-7). IEEE. 2019, April.
Tong Z, Ying H. Application of frequent item set mining algorithm in IDS based on Hadoop framework. In 2018 Chinese Control And Decision Conference (CCDC) (pp. 1908-1911). IEEE. 2018, June
Bakhtiar FA, Pramukantoro ES, Nihri H. A Lightweight IDS Based on J48 Algorithm for Detecting DoS Attacks on loT Middleware. In 2019 IEEE 1st Global Conference on Life Sciences and Technologies (LifeTech) (pp. 41-42). IEEE. 2019, March
Sonali R, Saxen A, Manoria M. Intrusion detection system on KDDcup99 dataset: A survey IJCSIT. Int J Comput Sci Inform technol. 2015;6(4):3345–8.
Thomas R, Pavithra, D. A survey of intrusion detection models based on NSL-KDD data set. In: 2018 Fifth HCT Information Technology Trends (ITT); 2018, p. 286–91.
Divekar Abhishek, Parekh Meet, Savla Vaibhav, Mishra Rudra, Shirole Mahesh. Benchmarking datasets for Anomaly-based network intrusion detection: KDD CUP 99 alternatives, arXiv:1811.0537v1 [cs.LG] Nov 2018.
Ieracitano C, Adeel A, Morabito FC, Hussain A. A novel statistical analysis and autoencoder driven intelligent intrusion detection approach. Neurocomputing. 2020;387:51–62.
Bakhtiar FA, Pramukantoro ES, Nihri H. A Lightweight IDS Based on J48 Algorithm for Detecting DoS Attacks on loT Middleware. In 2019 IEEE 1st Global Conference on Life Sciences and Technologies (LifeTech) (pp. 41-42). IEEE. 2019 March
Abaas Hassan Asma, Sheta Alaa F, Wahbi Talaat M. Intrusion detection system using Weka Data Mining tool. Int J Sci Res. 2017;6(9):1091703.
Sharafaldin Iman, Lashkari Arash Habibi, Hakak Saqib, Ghorbani Ali A. “Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy,” IEEE 53rd International Carnahan Conference on Security Technology, Chennai, India, 2019
Anish Halimaa A, DR. K. Sundarakantham, Machine learning based intrusion detection system, 978-1-5386-9439-8/19, 2019 IEEE, proceeding of 3rd ICOEI 2019.
Saheed Yakub Kayode, Abiodum Aremu Irdis, Misra Sanjay, Holone Monica Kristiansen, Colomo-Palacios Ricardo. A machine learning-based intrusion detection for detecting internet of things network attacks, by Elsevier BV on behalf of faculty of engineering, Alexandria University, https://doi.org/10.1016/j.aej.2022.02.063.
Moustafa N, Slay J. “UNSW-NBI5: a comprehensive data set for network intrusion detection systems (UNSW-NBI5 network data set),”. Military Communications and Information Systems Conference (MilClS). Canberra, ACT. 2015;2015:1–6.
Biesiada J, Duch W. Feature selection for high-dimensional data—a Pearson redundancy based filter. In: Computer recognition systems 2. Berlin, Heidelberg: Springer; 2007. p. 242–9.
Chebrolu S, Abraham A, Thomas JP. Feature deduction and ensemble design of intrusion detection systems. Comput Secur. 2005;24(4):295–307.
Suresh M, Anitha R. “Evaluating machine learning algorithms for detecting DDoS attacks,” in International Conference on Network Security and Applications, 2011, pp. 441-452: Springer.
Yassin W, Udzir NI, Muda Z, Sulaiman MN. “Anomaly-based intrusion detection through k-means clustering and naives bayes classification,” in Proc. 4th Int. Conf. Comput. Informatics, ICOCI, 2013, no. 49, pp. 298-303.
Ferrag MA, Maglaras L, Ahmim A, Derdour M, Janicke H. RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks. Future Int. 2020;12(44):1–14.
Sharafaldin I, Gharib A, Lashkari AH, Ghorbani AA. Towards a reliable intrusion detection benchmark dataset. Softw Netw. 2017;1(1):177–200.
Kunhare N, Tiwari R, Dhar J. Particle swarm optimization and feature selection for intrusion detection system. Sadhana. 2020;45(109):1–14.
Yin C, Zhu Y, Fei J, He X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access. 2017;5:21954–61.
Naseer S, Saleem Y, Khalid S, et al. Enhanced network anomaly detection based on deep neural networks. IEEE Access. 2018;6:48231–46.
Xiao Y, Xing C, Zhang T, Zhao Z. An intrusion detection model based on feature reduction and convolutional neural networks. IEEE Access. 2019;7:42210–422019.
Jiang K, Wang W, Wang A. Network intrusion WH. Detection combined hybrid sampling with deep hierarchical network. IEEE Access. 2020;8:32464–746.
Chawla Nitesh V, et al. SMOTE: synthetic minority over-sampling technique. J Artif Intel Res. 2002;16:321–57.
Awajan Albara. A Novel Deep Learning-Based Intrusion Detection System for IoT Networks. Computers. 2023;12(2):34.
Rayeesa Malik, Yashwant Singh, Ahmad Sheikh Zakir, Pooja Anand, Kumar Singh Pradeep, Chekole Workneh Tewabe. An Improved Deep Belief Network IDS on IoT-Based Network for Traffic Systems. J Adv Transp. 2022. https://doi.org/10.1155/2022/7892130.
Alqahtani AS. FSO-LSTM IDS: hybrid optimized and ensembled deep-learning network-based intrusion detection system for smart networks. J Supercomput. 2022;78:9438–55. https://doi.org/10.1007/s11227-021-04285-3.
Sharma Bhawana, et al. Anomaly based network intrusion detection for IoT attacks using deep learning technique. Comput Electr Eng. 2023;107: 108626.
Tavallaee M, Bagheri E, Lu W, Ghorbani AA. A detailed analysis of the KDD CUP 99 data set. In 2009 IEEE symposium on computational intelligence for security and defense applications. IEEE; 2009. p. 1–6.
https://www.unb.ca/cic/datasets/nsl.html. Accessed 20 Apr 2023.
Sharafaldin Iman, Lashkari Arash Habibi, Ghorbani Ali A. “ Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization,” 4th International Conference on Information Systems Security and Privacy (ICISSP), Portugal, January 2018
https://www.unb.ca/cic/datasets/ids-2017.html. Accessed 20 Apr 2023.
Kang H, Ahn DH, Lee GM, Yoo JD, Park KH, Kim HK. “IoT Network Intrusion Dataset,” IEEE DataPort, 2019. [Online]. Available: https://ieeedataport.org/open-access/iot-network-intrusion-dataset. Accessed 2020.
Jingyi Su, He Shan. Yan Wu. Features selection and prediction for IOT attacks, high conference computing. 2022;2: 100047. https://doi.org/10.1016/j.hcc.2021.100047.
https://github.com/abhinav-bhardwaj/Network-Intrusion-Detection-Using-Machine-Learning/blob/master/README.md. Accessed Apr 2022.
https://ieee-dataport.org/open-access/iot-network-intrusion-dataset. Accessed 20 Apr 2023.
Alhowaide A, Alsmadi I, Tang J. “PCA, Random-Forest and Pearson Correlation for Dimensionality Reduction in IoT IDS,”. IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS). Vancouver, BC, Canada. 2020;2020:1–6. https://doi.org/10.1109/IEMTRONICS51293.2020.9216388.
Zhou H, Deng Z, Xia Y, Fu M. A new sampling method in particle filter based on Pearson correlation coefficient. Neurocomputing. 2016;216:208–15. https://doi.org/10.1016/j.neucom.2016.07.036.
Mukaka MM. Statistics Corner: A guide to the appropriate use of Correlation coefficient in medical research. Malawi Med J. 2012;24:69–71.
Hall M. “CorrelationAttributeEval.” [Online]. Available: http://weka.sourceforge.net/doc.dev/weka/attributeSelection/Correlation AttributeEval.html. Accessed 06 Nov 2019
Sugianela Y, Ahmad T. “Pearson Correlation Attribute Evaluation-based Feature Selection for Intrusion Detection System,” 2020 International Conference on Smart Technology and Applications (ICoSTA), Surabaya, Indonesia, 2020, pp. 1-5, https://doi.org/10.1109/ICoSTA48221.2020.1570613717.
Mukaka MM. Statistics Corner: A guide to appropriate use of Correlation coefficient in medical research. Malawi Med J. 2012;24:69–71.
https://www.sas.com/en_gb/insights/articles/analytics/machine-learning-algorithms.html. Accessed Jan 2023.
Khatib Amine, Hamlich Mohamed, Hamad Denis. Machine learning based intrusion detection for cyber-security in IoT networks, https://doi.org/10.1051/e3sconf/202129701057, E3S Web of conferences 297, 01057(2021), ICCSRE2021.
Bolón-Canedo V, Alonso-Betanzos A. Ensembles for feature selection: a review and future trends. Inf Fus. 2019;52:1–12.
Chelvan M, Perumal K. On Feature Selection Algorithms and Feature Selection Stability Measures: A Comparative Analysis. Int J Comput Sci Inf Technol. 2017;9(3):159–68.
Beheshti I, Demirel H, Farokhian F, Yang C. Structural MRI-based detection of Alzheimer’s. Comput Methods Programs Biomed. 2016;137(177):193.
Alaiz-Rodriguez R, Parnell AC. An information theoretic approach to quantify the stability of feature selection and ranking algorithms. Knowl Based Syst. 2020;195: 105745.
Acknowledgements
This work was supported partially by Palo Alto Networks under Cyber Defense and AI Research Lab at North Carolina A &T State University. The authors are thankful for the support.
Author information
Authors and Affiliations
Contributions
Mansi Bhavsar (MB), John Kelly (JK), and Kaushik Roy (KR) conceived the presented thought. All developed the theory, and MB performed the computations. JK, KR, and Olusola Odeyomi (OO) verified the analytical methods and encouraged MB to investigate and supervise the findings of this work. MB wrote the manuscript, and all the authors reviewed the manuscript, gave feedback, and updated the manuscript. Finally, All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no conflict of interest for this publication.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Bhavsar, M., Roy, K., Kelly, J. et al. Anomaly-based intrusion detection system for IoT application. Discov Internet Things 3, 5 (2023). https://doi.org/10.1007/s43926-023-00034-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s43926-023-00034-5