Abstract
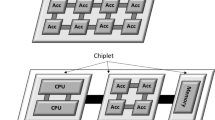
With advancements in VLSI technology, Tiled Chip Multicore Processors (TCMP) with packet switching Network-on-Chip (NoC) have evolved as the backbone of modern data intensive parallel systems. Manufacturers are looking at the prospect of using several third-party Intellectual Property (IP) cores in their TCMP designs due to strict time-to-market restrictions. Outsourcing IP from vendors across the world exposes System-on-Chip (SoC) designs to malicious implants such as Hardware Trojans (HTs). The performance of entire system is adversely affected by the presence of malicious HT in NoC routers, which can negatively disrupt communication between tiles. Generally, in buffered NoC, hardware trojans affect flits when they are in input buffers. Hardware trojans in bufferless NoC is a less explored area. In this paper, we model an HT that leads to antipode attack, which can occur on Permutation Deflection Network (PDN) of a bufferless router. In a bufferless router such as CHIPPER architecture, only the highest priority flit gets productive port, while other flits may or may not get productive port depending on port availability, leading to deflections. The modelled trojan misroutes all flits of HT-infected router to non-productive ports without modifying the flit control field. We investigate the effects of such an intermittent HT and analyse its effects at NoC level in terms of performance metrics such as average flit latency, deflection rate, throughput and router link utilisation. Experimental evaluations conducted on an \(8\times 8\) bufferless mesh NoC indicate that the modelled HT degrades network performance due to increased flit deflections and traffic across central routers which impacts system reliability.









Similar content being viewed by others
References
Charles S, Lyu Y, Mishra P. Real-time detection and localization of dos attacks in noc based socs. In: 2019 Design, automation & test in Europe conference & exhibition (DATE). IEEE; 2019. p. 1160–1165.
Manju R, Das A, Jose J, Mishra P. Sectar: secure noc using trojan aware routing. In: IEEE/ACM international symposium on networks-on-chip (NOCS), 2020.
Li H, Liu Q, Zhang J. A survey of hardware trojan threat and defense. Integration. 2016;55:426–37.
Areno M. Supply chain threats against integrated circuits. Intel Whitepaper, 2020.
Charles S, Mishra P. A survey of network-on-chip security attacks and countermeasures. ACM Comput Surv (CSUR). 2021;54(5):1–36.
Xiao K, Forte D, Jin Y, Karri R, Bhunia S, Tehranipoor M. Hardware trojans: lessons learned after one decade of research. ACM Trans Des Automat Electron Syst (TODAES). 2016;22(1):1–23.
Dally WJ, Towles BP. Principles and practices of interconnection networks. Amsterdam: Elsevier; 2004.
Dally WJ, et al. Virtual-channel flow control. IEEE Trans Parallel Distrib Syst. 1992;3(2):194–205.
Hoskote Y, Vangal S, Singh A, Borkar N, Borkar S. A 5-ghz mesh interconnect for a teraflops processor. IEEE Micro. 2007;27(5):51–61.
Taylor MB, Lee W, Miller J, Wentzlaff D, Bratt I, Greenwald B, Hoffmann H, Johnson P, Kim J, Psota J, et al. Evaluation of the raw microprocessor: an exposed-wire-delay architecture for ilp and streams. ACM SIGARCH Comput Architect News. 2004;32(2):2.
Moscibroda T, Mutlu O. A case for bufferless routing in on-chip networks. In: Proceedings of the 36th annual international symposium on Computer architecture, 2009. p. 196–207.
Fallin C, Craik C, Mutlu O. Chipper: a low-complexity bufferless deflection router. In: 2011 IEEE 17th international symposium on high performance computer architecture. IEEE; 2011. p. 144–155.
Mishra P, Charles S. Network-on-chip security and privacy. New York: Springer; 2021.
Rajan M, Das A, Jose J. Loki: a hardware trojan affecting multiple components of an soc. In: ISVLSI 2022-IEEE computer society annual symposium on VLSI, 2022.
Sudusinghe C, Charles S, Ahangama S, Mishra P. Eavesdropping attack detection using machine learning in network-on-chip architectures. In: 16th IEEE international symposium on networks-on-chip (NOCS), 2022. p. 21–28.
Bagga S, Gupta R, Jose J. Modeling and analysis of confluence attack by hardware trojan in noc. In: 5th International symposium on devices, circuits and systems (ISDCS-2022), 2022.
Khan MH, Gupta R, Jose J, Nandi S. Dead flit attack on noc by hardware trojan and its impact analysis. In: Proceedings of the 14th international workshop on network on chip architectures, 2021. p. 10–15.
Khan MH, Gupta R, Kulkarni VJ, Jose J, Nandi S. Hardware trojan mitigation for securing on-chip networks from dead flit attacks. In: 30th IFIP/IEEE international conference on very large scale integration (VLSI-SoC-2022), 2022.
Jiang N, Becker DU, Michelogiannakis G, Balfour J, Towles B, Shaw DE, Kim J, Dally WJ. A detailed and flexible cycle-accurate network-on-chip simulator. In: 2013 IEEE international symposium on performance analysis of systems and software (ISPASS). IEEE, 2013. p. 86–96.
Spradling CD. Spec cpu2006 benchmark tools. ACM SIGARCH Comput Architect News. 2007;35(1):130–4.
Binkert N, Beckmann B, Black G, Reinhardt SK, Saidi A, Basu A, Hestness J, Hower DR, Krishna T, Sardashti S, et al. The gem5 simulator. ACM SIGARCH Comp Architect News. 2011;39(2):1–7.
Huang W, Stan MR, Skadron K, Sankaranarayanan K, Ghosh S, Velusam S. Compact thermal modeling for temperature-aware design. In: Proceedings of the 41st annual design automation conference, 2004. p. 878–883.
Kahng AB, Li B, Peh L-S, Samadi K. Orion 2.0: a fast and accurate noc power and area model for early-stage design space exploration. In: 2009 Design, automation & test in Europe conference & exhibition. IEEE; 2009. p. 423–428.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Enabling Innovative Computational Intelligence Technologies for IOT” guest edited by Omer Rana, Rajiv Misra, Alexander Pfeiffer, Luigi Troiano and Nishtha Kesswani.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kunthara, R.G., Josna, V.R., Neethu, K. et al. Modelling and Impact Analysis of Antipode Attack in Bufferless On-Chip Networks. SN COMPUT. SCI. 4, 284 (2023). https://doi.org/10.1007/s42979-022-01622-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-022-01622-y