Abstract
A visually meaningful double-image encryption scheme using 2D compressive sensing and multi-rule DNA encoding is presented. First, scrambling, diffusing and 2D compressive sensing are performed on the two plain images, and two privacy images are obtained, respectively. Then, the two privacy images are re-encrypted using DNA encoding theory to obtain two secret images. Finally, integer wavelet transform (IWT) is performed on the carrier image to obtain the wavelet coefficients, then the two secret images are embedded into the wavelet coefficients and 2k correction is performed, and the obtained result is processed by inverse IWT to obtain a visually meaningful encrypted image. DNA encoding rules selected for the pixel values of different positions in the two privacy images, and DNA operations performed between the two privacy images and the key streams at different positions are controlled by the chaotic system. The application of 2D compressive sensing reduces the amount of data, thus increasing the encryption capacity of the system. The introduction of DNA encoding theory and the double-image embedding process increases the security of the system. The simulation results demonstrate the feasibility of the scheme, and it has high data security and visual security.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Background
With the rapid development of information technology, a large amount of digital image is generated and spreads to various types of public channels. In addition to the image itself, a digital image also contains many other types of information. For example, an image of a military oil depot can not only reflect the size of the oil depot and the quantity of gasoline, but also roughly reflect the location of the oil depot; a face image not only shows the person’s appearance, but also reflects his or her gender, race and approximate age. Due to theirs intuitive visual effects, digital images have become one of the most widely used information carriers, but at the same time, they are facing security threats in storage and transmission. Since the copying, cutting and forwarding of digital images are extremely simple and convenient, important information of users may be obtained through public channel or cloud storage, which seriously violates the privacy of users. Encrypting plain images before transmitting them is one of the commonly used methods to ensure the data security of digital images.
For the data security of digital images, different technologies are used to design a variety of image encryption algorithms: Chaotic systems are very useful tools for generating pseudo-random sequences for image encryption [1,2,3,4,5,6]; The optical encryption method has the inherent advantages of parallel and high-speed processing of multi-dimensional data, and optical parameters can be arbitrarily selected as additional keys [7,8,9,10]; DNA encoding replaces pixel manipulation and encodes images into pseudo-DNA sequences [11,12,13,14,15]; Compressive sensing (CS) can realize the functions of image encryption and compression at the same time [16,17,18,19,20,21]; Cellular automata can produce complex dynamic behaviors and has good application value for image encryption [22,23,24]. These image encryption algorithms have a common feature, that is, they can encrypt plain images to generate images similar to noise or texture, as shown in Fig. 1a. However, information security includes data security and visual security. Data security means that the attacker cannot obtain the content of the plain image, and visual security means that the attacker cannot know the existence of the plain image. Encrypting a plain image into a noise-like or texture-like encrypted image only achieves data security. And the noise-like or texture-like encrypted image is likely to be discovered and attacked by attackers during the transmission by the public channel. As a result, this type of encrypted image is subject to more ciphertext analysis attacks. Even if it is difficult for an attacker to crack the encryption system, he can also interfere with the decryption system by cropping, tampering, and adding noise to the encrypted image, making it difficult for legitimate users to use the decryption system to obtain the correctly decrypted image.
To solve the above problems, it is necessary to achieve visual security of encrypted images, that is, the existence of encrypted images cannot be discovered by attackers. Bao et al. presented a visually meaningful image encryption (VMIE) scheme in 2015 [25]. The scheme includes pre-encryption process and embedding process. In the pre-encryption process, a plain image with size of \(N \times N\) is first encrypted according to some traditional encryption algorithms to obtain an equal size noise-like secret image. In the embedding process, discrete wavelet transform is performed on a carrier image with size of \(2N \times 2N\) to obtain the wavelet coefficients of LL, LH, HL and HH, the size of these four parts are all \(N \times N\), and then the secret image is divided into two parts, replacing the LH and HL parts of the wavelet coefficients, respectively. Finally, the inverse discrete wavelet transform is performed on the updated four wavelet coefficients to obtain a visually meaningful encrypted image (VMEI), which has the same size as that of the carrier image and is visually similar to the carrier image. It should be pointed out that since the embedding of the secret image changes the LH and LH parts of the wavelet coefficients of carrier image, the VMEI is visually similar to the carrier image, but actually they are different. In general, the more element values in the wavelet coefficients are changed, the greater the difference between the VMEI and the carrier image. Since the human vision system is not sensitive to high-frequency changes in images, the resulting VMEI has certain visual security. In the subsequent VMIE algorithm, the algorithm proposed by Bao et al. are optimized from two aspects:
One type of optimization focuses on the improvement of the pre-encryption algorithm [26,27,28,29,30,31,32,33,34,35,36,37]. The size of a VMEI is several times larger than that of a plain image, as shown in Fig. 1b. CS theory provides an effective way to reduce the size of encrypted images. Because it makes full use of the prior information that the signal can be sparsely represented, it can directly sample the signal at a frequency lower than Shannon’s sampling frequency through incoherent sampling. And CS theory provides a method to reconstruct the original signal from less sampled data [16,17,18,19,20,21]. It should be pointed out that using the same CS recovery algorithm, the lower the sampling rate, the lower the similarity between the decrypted image and the plain image. To reduce the size of the VMEI, Chai et al. proposed to introduce CS into the pre-encryption process of VMIE scheme. In the pre-encryption process, a plain image with size of \(N \times N\) is first encrypted according to CS theory to obtain a noise-like secret image with size of \(\frac{N}{4} \times N\), and the sampling rate is set to \(25\%\). Due to the use of CS theory, the size of the secret image becomes \(\frac{1}{4}\) of that of the plain image, so the size of the carrier image required in the embedding process also becomes \(\frac{1}{4}\) of that of the carrier image when CS theory is not used, that is, the size of the carrier image changes from \(2N \times 2N\) to \(N \times N\). And then embed the secret image into the carrier image to obtain a VMEI with the same size as the plain image, as shown in Fig. 1c. In addition, the scheme uses the hash value of the plain image to calculate the parameters used during encryption process, which further enhances the security of the system [26, 27]. However, since the embedding method used in this algorithm [26] is similar to the embedding method used by Bao et al., the visual quality of the encrypted image is poor. Moreover, the traditional CS reconstruction algorithm takes a long time. To reduce the computational complexity of encryption schemes, researchers have proposed many VMIE schemes based on CS, including block compressive sensing [28, 29], semitensor product compressive sensing [30], two-dimensional compressive sensing (2DCS) [31,32,33], parallel compressive sensing [34, 35], bayesian compressive sensing [36] and so on [37, 38].
The other type of optimization focuses on the improvement of the embedding process [39,40,41,42,43,44]. To overcome the defect that VMEIs have certain texture features, Yang et al. presented an image encryption scheme by using discrete quantum walks and discrete wavelet transform [39]. Kanso et al. used two-dimensional lifting wavelet transform to improve the algorithm proposed by Bao. Since the wavelet transform used in this scheme is a transformation from integer to integer, its lossless embedding and extraction methods reduce the distortion of the image, and the visual quality of the encrypted image is improved to a certain extent [40]. Tuncer et al. presented an embedding method based on 2k corrected integer wavelet transform, which improves the visual quality of VMEI and reduces the execution time [41]. Yang et al. further improved the visual quality of VMEIs through the use of the generalized embedding model method and error correction strategy to embed four different virtual bit depth matrices into the carrier image [42]. To further improve the robustness of the scheme and the quality of the decrypted image, Jiang et al. presented an adaptive embedding algorithm by using the lossy transform domain, which embeds unquantized cryptographic data into the carrier image [43]. Ping et al. presented a VMIE scheme, which uses a partial block pairing-substitution strategy to embed the secret image into the carrier image. Since the embedding process is carried out in the spatial domain, the capacity is increased [44].
Motivation
Although researchers have made various improvements to the method proposed by Bao in the VMIE algorithm, the current VMIE algorithm still has limitations, and there leaves room for further improvements: 1. Internet users may no longer be satisfied with compressing and encrypting a single image. This calls for designing a 2DCS-based visual security multi-image encryption scheme to increase the encryption capacity of the system. 2. CS-based encryption algorithms are often linear, and linear encryption algorithms are often unable to resist differential attack and chosen-plaintext attack. Therefore, a non-linear process is needed to enhance the system’s ability to resist differential attack and chosen-plaintext attack. 3. The embedding process of current visual security encryption schemes is often too simple. It often replaces the “bit” of the carrier image coefficient matrix with the “bit” of the secret image. There is a need to design a embedding process to enhance the security of the encryption scheme. For the above reasons, this paper attempts to construct a visually meaningful double-image encryption scheme using 2DCS and multi-rule DNA encoding, in which non-linear operations are introduced in the encryption process, and new keys are introduced in the embedding process.
Our contribution
The main contribution of this paper lies in:
-
1.
Two plain images are scrambled, diffused, and processed by 2DCS to obtain two private images. After re-encryption with DNA encoding theory, two secret images are obtained, and then they are embedded into the carrier image through double-image embedding process, and finally a visually meaningful encrypted image is generated. The size of the encrypted image is the same as that of the plain images. This solution ensures the data security and visual security of the plain images, while saving half of the storage space.
-
2.
Before the two plain images are compressed and sampled, their pixel values are changed nonlinearly to reduce the dynamic range of compressed sampling. This operation improves system security while reducing computational complexity.
-
3.
The essence of DNA encoding theory is binary encoding and operation. Before the two privacy images are embedded, we use DNA encoding theory to further encrypt them. DNA encoding rules selected for the pixel values at different positions of the two privacy images are controlled by the chaotic system, and DNA operations performed on the pixel values of the two privacy images at different positions and key streams are also controlled by the chaotic system. Then, a double-image embedding algorithm based on 2k correction is presented to enhance the security of the system while the visual quality of the encrypted image does not significantly decrease.
Organization
The rest of this article is organized as follows: in section “Fundamental knowledge”, the fundamental knowledge of piecewise linear chaotic map, 2DCS, DNA encoding and operation, image encryption scheme based on DNA encoding and \(2^k\) correction of embedded bits are introduced. The process of a visually meaningful double-image encryption and embedding scheme by using 2DCS and multi-rule DNA encoding are described in detail in section “Description of the scheme”. The numerical simulation results and security analysis of the encryption scheme are given in section “Performance analysis”. Finally, the full article is summarized in the “Conclusion” section.
Fundamental knowledge
Piecewise linear chaotic map
As a chaotic system, the piecewise linear chaotic map (PWLCM) is defined as
where p is control parameter and \(x_0\) is initial value. While \(p \subseteq (0,0.5)\) and \(x_0 \subseteq (0,1)\), the system is in a chaotic state, and for all ordinal number l, there will be \(x_l \subseteq (0,1)\).
2D compressive sensing
CS theory completes the signal compression synchronously in the process of signal sampling, so this theory has been widely used in image compression and encryption. As for the CS theory, a grayscale image X of size \(N \times N\) can be sparsely represented as
where \(\Psi \) is an \(N \times N\) orthogonal basis, \( \beta \) is an \(N \times N\) coefficient matrix and it is a sparse representation of X.
For the compression and sampling process of a compressible 2D image X, two measurement matrices \(\Phi _1\) and \(\Phi _2\) are used to perform the following operation [45,46,47,48]:
where the two measurement matrices size both are \(M \times N (M<N)\), \(\Phi _2^T\) is the transpose of \(\Phi _2\), and Y represents measurement value matrix of size \(M \times M\).
If the two measurement matrices \(\Phi _1\) and \(\Phi _2\) satisfy the Restricted Isometry Property (RIP), we can accurately reconstruct X from Y by solving the following equation [45,46,47,48]:
where \( \Vert \beta \Vert _{0}\) is the \(l_0\) norm of \(\beta \). A variety of effective reconstruction algorithms have been proposed, such as 2D smoothed \(l_0\) algorithm, Newton smoothed \(l_0\) norm, 2D orthogonal matching pursuits algorithm, 2D projected gradient algorithm, etc [45,46,47,48].
DNA encoding and operation
Deoxyribonucleic Acid (DNA) is composed of four types of nucleic acid bases, which are A (adenine), T (thymine), C (cytosine) and G (guanine). According to the Watson-Crick complement rule, A and T are complementary, and G and C are also complementary. The binary number system consists of only two complementary numbers, 0 and 1. Similarly, 10 and 01 are complementary, while 00 and 11 are also complementary. There are \(4! = 24\) encoding rules to encode two binary numbers (10, 01, 00, and 11) using four bases (A, C, G, and T), but only 8 encoding rules satisfy complement rule, which are shown in Table 1. For an eight-bit grayscale image, using 00, 01, 10, and 11 as metadata, a single pixel value can be represented by four bases. Encoders can use four bases to encode a single pixel value under eight encoding rules. For example, the pixel value 141 corresponds to the binary number \((10001101)_2\), and the eight encoding rules in Table 1 are used in turn to obtain the base sequence (CATG), (GATC), (TGCA), (TCGA), (AGCT), (ACGT), (CTAG), (GTAC).
Encoders can define a variety of DNA operations according to their needs. Commonly used DNA operations include addition operation (+), subtraction operation (-), and exclusive OR operation (XOR). The addition (or subtraction) operation in DNA theory ignores the carry (or borrow) of the highest bit, and the XOR operation is the same as the XOR operation in traditional binary. Examples of the three operations are shown in Tables 2, 3, and 4, respectively.
Image encryption scheme based on DNA encoding
The image encryption scheme based on DNA encoding needs to first encode the plain image and the key image according to certain DNA encoding rules, and then perform certain DNA operations on the two encoded images to obtain an encoded cipher image. Finally, the encoded cipher image is decoded according to certain DNA decoding rules to obtain a cipher image, as shown in Fig. 2.
Let us take a pixel value as an example to illustrate the encryption and decryption process. Let the pixel values in the plain image and the key image be 141 and 78, convert them to binary as \([10001101]_2\) and \([01001110]_2\), respectively, and use DNA encoding rule 1 (there are 8 rules, as shown in Table 1) to encode them to get DNA sequences [CATG] and [GATC]. Then perform XOR operation (there are three DNA operations, as shown in Tables 2, 3, 4) on these two DNA sequences to obtain the DNA sequence [TAAT]. Finally, it is decoded according to DNA decoding rule 2 (there are 8 rules, as shown in Table 1), and the binary sequence \([11000011]_2\) is obtained, and then the sequence is converted into decimal to obtain 195, which is the pixel value of the cipher image.
The decryption process is the reverse process of the encryption process, and it requires key images, encoding rules, decoding rules, and operation rules as keys. The encoding and decoding rules in the decryption process need to correspond to the rules used in the encryption process. The addition and subtraction operations are mutually inverse operations, and the inverse operation of XOR is still XOR. When decrypting, first convert the cipher image pixel value 195 and the key image pixel value 78 into binary to get \([11000011]_2\) and \([01001110]_2\) respectively, and then encode \([11000011]_2\) according to encoding rule 2 to get [TAAT], and encode \([01001110]_2\) according to encoding rule 1 to obtain [GATC]. Then, perform the XOR operation on the two DNA sequences to obtain [CATG], and decode [CATG] according to rule 1 to get \([10001101]_2\), and finally convert \([10001101]_2\) to decimal to obtain 141, which is the pixel value of decrypt image.
\(2^k\) correction of embedded bits
The 2k correction method can significantly improve the visual quality of encrypted images. This method is modified by adding (or subtracting) \(2^k\) to part of the embedded data, and does not affect the extraction of secret information at all, which is defined as [41, 42, 49]
where SD stands for the secret data that needs to be embedded, OP represents the original pixel value before the secret data are embedded, \(\left\lfloor \bullet \right\rfloor \) is the rounding down function, SP is the stego pixel value after the secret data are embedded. NSP is the new stego pixel value after \(2^k\) correction of SP.
Let us take the embedded SD with 4 bits (that is, \(k=4\)) as an example to illustrate the correction method. Assuming that the SD is \(14 = (\underline{1110})_2\), and the OP is \(209 = (1101\underline{0001})_2\). The uncorrected SP is \((1101\underline{1110})_2 = 222\), so the error value between SP and OP is \(|SP-OP| =|222 - 209| = 13 > 2^{(4-1)}\). The NSP after the \(2^k\) correction operation is \(222 - 2^4 = 206\). Obviously, the corrected new error value \(|206 - 209| = 3\) is smaller than the uncorrected error value 13. It can be seen that the \(2^k\) correction method makes the corrected NSP closer to the OP without affecting the SD.
Description of the scheme
Both the plain images and the carrier images used in this article are 8-bit grayscale images of size \(N \times N\). In the compression sampling process, the compression rate is set to \(25\%\), so the size of the secret images is \(N/2 \times N/2\). Table 5 gives the description of the notations used in this section.
Encryption scheme
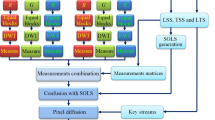
As illustrated in Fig. 3, a visually meaningful double image encryption by using 2DCS and multi-rule DNA encoding is proposed. Firstly, scrambling, diffusing and 2DCS are performed on the two plain images, then the two measurement value matrices are quantized, and then two privacy images are obtained respectively. Next, DNA encoding is performed on the two privacy images respectively, then DNA operations \((+, -, XOR)\) are performed on the encoded sequences and the key streams, and then the obtained sequences are decoded to obtain two secret images. Finally, the two secret images are embedded into the wavelet coefficients of the carrier image and 2k correction is performed, and the obtained result is performed by inverse IWT to obtain a visually meaningful encrypted image. PWLCM is used to generate the parameters needed in the encryption process. Figure 4 shows a visual example of this encryption scheme, and the detailed encryption and embedding process can be found in “Compressing and encrypting two plain images” section and “DNA encoding and embedding process” section.
Compressing and encrypting two plain images
This subsection is about the process of compressing and encrypting two plain images, that is, randomly scrambling, diffusing and 2DCS the two plain images, respectively, and then quantizing the two obtained measured value matrices, thereby obtaining two privacy images. The detailed steps are as follows:
Step 1.1: Set the initial state value \(x_0^1\) and control parameter \(p_1\) of the PWLCM, to generate a sequence \(w_1\) of length \(N^2\), then sort it in ascending order, and record the index sequence
Then put the \(index_1\) into the 2D matrix of size \(N \times N\), marked as \(I_1\). For example, if \(w_1 = [0.33, 0.11, 0.82, 0.69]\), after performing the sorting operation, we get \(w_1' = [0.11, 0.33, 0.69, 0.82]\), so \(index_1 =sort(w_1) = [2,1,4,3]\), and then arrange it into a 2D matrix to form \(I_1 = \left[ \begin{array}{cc}2 &{}\quad 1 \\ 4 &{}\quad 3\end{array}\right] \). This step requires initial state value \(x_0^1\) and control parameter \(p_1\) as keys.
Step 1.2: Use the index matrix \(I_1\) to scramble the plain image \(X_1\)
\(X'_1\) is the scrambled plain image 1. For example, if \(X_1 = \left[ \begin{array}{cc}x_{11} &{}\quad x_{12} \\ x_{21} &{}\quad x_{22}\end{array}\right] \) and \(I_1 = \left[ \begin{array}{cc}2 &{}\quad 1 \\ 4 &{}\quad 3\end{array}\right] \), after performing the scrambling operation, we can get \(X_{1}'=X_1(I_1)=\left[ \begin{array}{cc}x_{12} &{}\quad x_{11} \\ x_{22} &{}\quad x_{21}\end{array}\right] \).
Step 1.3: Set the initial state value \(x_0^2\) and control parameter \(p_2\) of the PWLCM, to generate a sequence \(w_2\) of length \(N^2\), and then put it into the 2D matrix with size of \(N \times N\), marked as \(W_2\). This step requires initial state value \(x_0^2\) and control parameter \(p_2\) as keys.
Step 1.4: Since the histograms of \(X_1'\) and \(X_1\) are the same, in order to further improve the security of the system, the pixels in \(X_1'\) need to be diffused. Process each pixel value of \(X_{1}'\) by using
\(X''_1\) is the diffused plain image 1. The pixel value \(X_1'' (i,j)\) thus obtained is an integer from \(-128\) to 128. This non-linear operation changes the histogram by selectively changing the gray value of the image, thereby avoiding leakage of plaintext statistics. In addition, mapping the pixel value data from -128 to 128 reduces the dynamic range of the next 2DCS sampling process.
Step 1.5: Use two measurement matrices \(\Phi _1\) and \(\Phi _2\) to perform the following operation on \(X_1''\):
where \(Y_1\) is the measurement value matrix with size of \(M \times M\). Since the pixel value \(X_1''(i,j)\) is an integer from -128 to 128, a smaller measurement value \(Y_1(i,j)\) is obtained. This step requires two random matrices \(\Phi _1\) and \(\Phi _2\) as keys.
Step 1.6: Quantize all the elements of measurement value matrix \(Y_1\), and according to the following formula convert each element value to the range of 0 to 255
Here \(Y_{1min}\) and \(Y_{1max}\) represent the minimum and maximum values in \(Y_1\), respectively, and the quantized result \(Y_{p1}\) is the privacy image 1. Here \(Y_{1min}\) and \(Y_{1max}\) need to be stored as decryption keys.
Step 1.7: For plain image \(X_2\), repeat steps 1.1–1.6 with different parameters to obtain the corresponding privacy image 2 (\(Y_{p2}\)). Similarly, this step requires two sets of PWLCM parameters \(x_0^i,p_i (i = 3,4)\), and two random matrices (\(\Phi _3\), \(\Phi _4\)) as keys. At the same time, \(Y_{2min}\) and \(Y_{2max}\) need to be stored as decryption keys.
DNA encoding and embedding process
In this subsection, the two privacy images \(Y_{p1}\) and \(Y_{p2}\) are first encoded by DNA multi-rule to obtain two encoded privacy images, then the two encoded privacy images and the corresponding key streams are subjected to a certain DNA operation to obtain corresponding encoded secret images, and then the two encoded secret images are decoded by DNA multi-rule to obtain two secret images. Finally, the two secret images are embedded into the wavelet coefficients of the carrier image and 2k correction is performed, and the obtained result is recorded as the modified coefficient matrix, and then it is processed by inverse IWT to obtain a visually meaningful encrypted image. The way of embedding the two secret images into the carrier image coefficient matrix is shown in Fig. 5. To ensure the safety of the system, 8 types of DNA rules and 3 types of DNA operations are used in DNA encoding and operation process, which are controlled by the PWLCM system, and the detailed steps are as follows:
Step 2.1: Set the initial state value \(x_0^5\) and control parameter \(p_5\) of the PWLCM, to generate a sequence \(w_5\) of length \(N^2/4\), and then put it into the 2D matrix with size of \(N/2 \times N/2\), marked as \(W_5\). In accordance with the DNA encoding theory, the privacy image 1 \((Y_{p1})\) is DNA-encoded, and the encoding rule is determined by
where \(W_5(i,j) \in \left( {0,1} \right) \) is element value of the position (i, j) of the matrix \(W_5\). rule(i, j) is the DNA encoding rule of \(Y_{p1}(i, j)\). Encode the secret image 1 pixel by pixel until all pixels of \(Y_{p1}\) are encoded. One pixel value is encoded to obtain four bases, and since the size of secret image 1 is \(N/2 \times N/2\), after DNA encoding, it is an \(N \times N\) encoded secret image 1. This step requires \(x_0^5\) and \(p_5\) as keys.
Step 2.2: Set the initial state value \(x_0^6\) and control parameter \(p_6\) of the PWLCM, to generate a sequence \(w_6\) of length \(N^2\), and then put it into the 2D matrix with size of \(N \times N\), marked as \(W_6\). According to the following formula the key stream 1 is produced
The key(i, j) value thus obtained can be 0, 1, 2, 3, which correspond to A, G, C, and T, respectively. This step requires \(x_0^6\) and \(p_6\) as keys.
Step 2.3: Set the initial state value \(x_0^7\) and control parameter \(p_7\) of the PWLCM, to generate a sequence \(w_7\) of length \(N^2\), and then put it into the 2D matrix with size of \(N \times N\), marked as \(W_7\). According to the following formula the operation stream 1 is generated
The operation(i, j) value thus obtained can be 0, 1, 2, which correspond to \(+, -\) and XOR, respectively. This step requires \(x_0^7\) and \(p_7\) as keys.
Step 2.4: Each pixel performs the following operation
After all the elements are processed in this way, a \(N \times N\) encoded secret image 1 is obtained.
Step 2.5: Repeat step 2.1, to generate DNA decoding rules, and then decode the encoded secret image 1 element by element to obtain a secret image 1. Four bases correspond to one pixel value, so the size of the secret image 1 is \(N/2 \times N/2\). This step requires \(x_0^8\) and \(p_8\) as keys.
Step 2.6: Repeat steps 2.1–2.5 to get a secret image 2 after DNA encoding, operation, and DNA decoding of the privacy image 2. This step requires four sets of keys \(x_0^i,p_i (i = 9,10,11,12)\).
Step 2.7: To prevent data overflow, the pixel value greater than 245 in the carrier image is set to 245, and that less than 10 is set to 10. Transform the carrier image to the wavelet domain by integer wavelet transform, then quantization (as shown in Eq. (11)) is performed to obtain a quantized wavelet coefficient, which is composed of LL, HL, LH and HH. In this process, the type of IWT can be used as the keys.
Step 2.8: Decompose the secret image 1 with size of \(N/2 \times N/2\) into the \(a_1 bits\), \(b_1 bits\), \(c_1 bits\) and \(d_1 bits\). Since each pixel value of an eight-bit grayscale image can be decomposed into an eight-bit binary number, therefore \(a_1 + b_1 + c_1 + d_1 = 8\). And the four numbers \(a_1\), \(b_1\), \(c_1\), and \(d_1\) are all less than or equal to 4. The process is shown in Fig. 5. This step requires \(a_1\), \(b_1\), \(c_1\) and \(d_1\) as keys.
Step 2.9: Decompose the secret image 2 with size of \(N/2 \times N/2\) into the \(a_2 bits\), \(b_2 bits\), \(c_2 bits\) and \(d_2 bits\), where \(a_2 + b_2 + c_2 + d_2 = 8\), and the four numbers \(a_2\), \(b_2\), \(c_2\), and \(d_2\) are all less than or equal to 4. This step requires \(a_2\), \(b_2\), \(c_2\) and \(d_2\) as keys.
Step 2.10: Embed \(a_1 bits\) and \(a_2 bits\) into the LL part of the coefficient matrix. When binary data is embedded, it is embedded from the lowest bit of the pixel. Below we set \(a_1=a_2=2\), and take a pixel value as an example to illustrate the data embedding process. If the numbers to be embedded are \((\underline{11})_2\) and \((\underline{01})_2\) respectively, and the pixel value to be embedded in LL is \(122=(01111010)_2\), the embedded pixel value will be \((0111\underline{11} \underline{01})_2\). Similarly, \(b_1 bits\) and \(b_2 bits\) are embedded in the HL part of the coefficient matrix, \(c_1 bits\) and \(c_2 bits\) are embedded in the LH part of the coefficient matrix, and \(d_1 bits\) and \(d_2 bits\) are embedded in the HH part of the coefficient matrix, as shown in Fig. 5. Then, perform 2k correction according to the method in “Image encryption scheme based on DNA encoding” section. The matrix obtained after two secret images are embedded is marked as the modified coefficient matrix.
Step 2.11: Process the modified coefficient matrix by inverse IWT to obtain a VMEI. The type of IWT used in this process is the same as that in step 2.7.
Decryption scheme
Figure 6 shows the flowchart of the decryption scheme. The decryption scheme includes extracting process and reconstruction process. Since the extracting process and reconstruction process are the inverse process of the embedding process and encryption process, here we will briefly discuss the decryption scheme.
Extracting and DNA decoding process
Step 3.1: Perform IWT on the visually meaningful encrypted image to obtain the modified coefficient matrix, which consists of four parts, marked as MLL, MHL, MLH and MHH. It should be pointed out that the type of IWT used here is the same as that in the encryption process.
Step 3.2: Through inverse 2k correction, extract \(a_1 bits\) and \(a_2 bits\) from MLL. Similarly, extract \(b_1 bits\) and \(b_2 bits\) from MHL, extract \(c_1 bits\) and \(c_2 bits\) from MLH, and extract \(d_1 bits\) and \(d_2 bits\) from MHH. Then use \(a_1 bits\), \(b_1 bits\), \(c_1 bits\) and \(d_1 bits\) to synthesize secret image 1. Similarly, use \(a_2 bits\), \(b_2 bits\), \(c_2 bits\) and \(d_2 bits\) to synthesize secret image 2. This step requires \(a_i,b_i,c_i,d_i (i=1,2)\) as decryption keys. This process is the reverse process of Fig. 5.
Step 3.3: Use the decryption keys \(x_0^8\) and \(p_8\) to generate the sequence \(w_8\) of length \(N^2/4\) according to Eq. 1. Then put the sequence into the 2D matrix of size \(N/2 \times N/2\), marked as \(W_8\). The encoding rule is determined by the Eq. 12, and replace \(w_5(i,j)\) in the formula with \(w_8(i,j)\), and then the secret image 1 is encoded element by element to obtain an encoding secret image 1. This step requires \(x_0^8\) and \(p_8\) as decryption keys.
Step 3.4: Use the decryption keys \(x_0^7\) and \(p_7\) to generate the sequence \(w_7\) of length \(N^2\) according to Eq. 1. Then put \(w_7\) into the 2D matrix of size \(N \times N\), marked as \(W_7\). According to Eq. 14, produce the operation stream 1. The operation(i, j) value thus obtained can be 0, 1, 2, which correspond to \(-, +\) and XOR, respectively. It should be pointed out that \(+\) and − are mutually inverse operations, and the inverse operation of XOR is also XOR. Therefore, the operation(i, j) of 0, 1, 2 corresponds to \(+, -, XOR\) in the encryption process, and it corresponds to \(-,+,XOR\) in the decryption process. This step requires \(x_0^7\) and \(p_7\) as decryption keys.
Step 3.5: Use the decryption keys \(x_0^6\) and \(p_6\) to generate the sequence \(w_6\) of length \(N^2\) according to Eq. 1. Then, put \(w_6\) into the 2D matrix of size \(N \times N\), marked as \(W_6\). According to Eq. 13, produce the key stream 1. The key(i, j) value thus obtained can be 0, 1, 2, 3, which correspond to A, G, C, and T respectively. This step requires \(x_0^6\) and \(p_6\) as decryption keys.
Step 3.6: Each pixel performs the following operation
After all the elements are processed in this way, a \(N \times N\) encoded privacy image 1 is obtained.
Step 3.7: Use the decryption keys \(x_0^5\) and \(p_5\) to generate the sequence \(w_5\) of length \(N^2/4\) according to Eq. 1. Then put \(w_5\) into the 2D matrix, marked as \(W_5\). According to Eq. 12, produce the DNA decoding rule rule(i, j), as shown in Table 1. When all pixels are decoded, a privacy image 1 (\(Y_{p1}\)) of size \(N/2 \times N/2\) is obtained. This step requires \(x_0^5\) and \(p_5\) as decryption keys.
Step 3.8: Repeat steps 3.3–3.7 to get a privacy image 2 (\(Y_{p2}\)) after 2k correction extracting, DNA encoding, DNA operation, and DNA decoding of the secret image 2. This step requires four sets of keys \(x_0^i,p_i (i = 9,10,11,12)\).
Decrypted image recovering process
The decrypted image recovering process is the process of reconstructing the decrypted image from the privacy image by the CS reconstruction algorithm. The detailed steps are as follows:
Step 4.1: The measurement value matrix \(Y_1\) is inversely quantized from the privacy image \(Y_{p1}\) according to Eq. 17
This step requires \(Y_{1max}\) and \(Y_{1min}\) as decryption keys.
Step 4.2: Solve Eq. 4 using \(\Phi _1\) and \(\Phi _2\) as decryption keys to obtain \(X_1''\). Here, the 2DPG-ED algorithm [48] is used.
Step 4.3: Use the decryption keys \(x_0^2\) and \(p_2\) to generate the sequence \(w_2\) of length \(N^2\) according to Eq. 1. Then put \(w_2\) into the 2D matrix of size \(N \times N\), marked as \(W_2\). Process each pixel value of \(X_{1}''\) according to
Step 4.4: Use the decryption keys \(x_0^1\) and \(p_1\) to generate the sequence \(w_1\) of length \(N^2\) according to Eq. 1, sort it in ascending order, and record the \(index_1\) sequence according to Eq. 7. Then, put the \(index_1\) into the 2D matrix with size of \(N \times N\), marked as \(I_1\).
Step 4.5: Perform inverse scrambling operation on \(X_1'\),
\(X_1\) obtained by the above equation is the decrypted image 1. For example, if \(X_{1}'=X_1(I_1)=\left[ \begin{array}{cc}x_{12} &{}\quad x_{11} \\ x_{22} &{}\quad x_{21}\end{array}\right] \) and \(I_1 = \left[ \begin{array}{cc}2 &{}\quad 1 \\ 4 &{}\quad 3\end{array}\right] \), after performing the inverse scrambling operation, we can get \(X_1 =X_1'(I^{-1}_1) = \left[ \begin{array}{cc}x_{11} &{}\quad x_{12} \\ x_{21} &{}\quad x_{22}\end{array}\right] \).
Step 4.6: Repeat steps 4.1–4.5 to get a decrypted image 2 after inversely quantization, 2DCS reconstruction, and inverse scrambling of the privacy image 2. This step requires \(Y_{2max}\) and \(Y_{2min}\), \(x_0^i,p_i (i = 3,4)\) and two measurement matrices \(\Phi _3\) and \(\Phi _4\) as decryption keys.
Performance analysis
In this section, we will demonstrate the effectiveness, data security and visual security of the encryption scheme through simulation experiments. The experiments were carried out by Matlab R2019a on a computer with a 3.0 GHz CPU and the Windows 10 operating system. The size of the plain images and the carrier images are both \(256 \times 256\), and the compression rate is set to \(25\%\), so the size of the secret images is \(128 \times 128\). Here, we will first show the simulation results (“Simulation results” section) to demonstrate the feasibility of the scheme; secondly, through statistical analysis (“Statistical analysis” section), including histogram analysis, correlation coefficient analysis, and information entropy analysis, we demonstrate the visual security of the scheme; Then, through the time-consuming calculation of encryption and decryption (“Time complexity analysis” section), we illustrate its time feasibility; Finally, through the analysis of key sensitivity (“Key sensitivity analysis” section) and attack analysis (“Various attacks” section), including brute force attack, differential attack and chosen-plaintext attack, we demonstrate the data security of the scheme.
Simulation results
The algorithm proposed in this paper encrypts two grayscale images and embeds them into a carrier image of equal size. First, the two plain images are scrambled and diffused, then they are compressed and encrypted by 2DCS theory and DNA encoding theory to obtain two secret images, and then the two secret images are embedded into the carrier image through the embedding and correction algorithm to obtain a visually meaningful encrypted image. Figure 7 shows the simulation results of three groups of plain images when different carrier images are used. The left two columns are the first group of results, the middle two columns are the second group of results, and the right two columns are the third group of results. The first row shows six plain images, which are “House”, “Parrots”, “Cameraman”, “Monarch”, “Boats” and “Foreman”, and the second row shows 6 secret images, which in turn correspond to the six plain images. These secret images are obtained from two plain images through 2DCS and DNA encoding process, respectively. It can be seen that they are stationary white noise images. There are three carrier images in the third row. The two secret images are embedded into the wavelet coefficients of the carrier image and 2k correction is performed, and the obtained result is performed by inverse IWT to obtain a VMEI, as shown in the fourth row of Fig. 7. According to the decryption process shown in Fig. 6, the visually secure encrypted image are decrypted, as shown in the fifth row in Fig. 7.
To quantitatively analyze the encryption and decryption effect, we calculated the peak signal-to-noise ratio (PSNR) and the mean structural similarity index (MSSIM) [50, 51] of the two decrypted images and the two plain images, as well as the carrier image and the visually secure encrypted image. MSSIM can qualitatively describe the structural similarity of two images, which is defined as
where X and Y represent the two images whose similarity needs to be compared, K represents the total number of partitioned image block, and in this paper \(K=64\). The structural similarity index (SSIM) can be obtained by equation
where \(\mu _i\) and \(\sigma _i \) stand for the average value and variance value of image block i, and \(\sigma _{xy}\) denotes cross covariance of image blocks x and y, respectively. \(c_1\) and \(c_2\) are two constant to avoid zero in the denominator. According to the literature [50], we let \(c_1=(0.01 \times 255)^2\) and \(c_2=(0.03 \times 255)^2\).
The PSNRs and MSSIMs between the decrypted and plain images, and between the carrier and encrypted images are shown in Table 6. The average PSNR between the decrypted image and the plain image is 32.76dB, and the average MSSIM value is 0.8923, which indicates that the quality of the decrypted image is very good. The average PSNR between the encrypted image and the carrier image is 28.51dB, and the average MSSIM value is 0.8879, indicating high visual security of encrypted image. It can be seen that the VMIE scheme proposed in this paper has a good encryption and decryption effect, and can achieve visual security of encrypted images. We also compare the quality of the decrypted images of this scheme with that of other schemes, and the results are shown in Table 7. It should be pointed out that since two plain images are encrypted in this paper, the PSNR and MSSIM of the encrypted image are lower than those in some literatures. For example, in Ref. [35], the PSNR of the encrypted image is as high as 40.92dB, and the MSSIM of the encrypted image is as high as 0.9871, but only one image is encrypted in that scheme. The increase in encryption capacity makes PSNR and MSSIM slightly lower. Therefore, our proposed scheme slightly reduces the similarity, and doubles the system encryption capacity. In fact, as the carrier image is unknown, the similarity between the encrypted image and the carrier image is difficult to measure.
Histogram analysis: the first row denote the histograms of the plain image ‘House’ and ‘Parrots’, the second row denote the histograms of the two secret images, the third row denote the histograms of the carrier image ‘Lena’ and encrypted image ‘Lena’, the fourth row denote the histograms of the decrypted image ‘House’ and ‘Parrots’, respectively
Statistical analysis
In this subsection, we demonstrate the ability of the proposed VMIE scheme to resist statistical analysis attacks through histogram analysis, correlation coefficients analysis, and information entropy analysis.
Histogram analysis
A histogram can reflect the distribution of pixel values in the image. Generally, for plain image and carrier image, the distribution of the histogram is generally non-uniform. Since the visually meaningful encrypted image is visually similar to the carrier image, its histogram distribution should also be similar to that of the carrier image. We select the first group of images in Fig. 7 (i.e., the two columns on the left) for histogram analysis. As shown in Fig. 8, the histogram distribution of the carrier image and the encrypted image is similar, and the histograms of the two plain images and its corresponding decrypted images are also similar, indicating that the encrypted image has visual security and the quality of the two decrypted images is good. The distribution of the histograms of the two secret images is very uniform, indicating that the pre-encryption scheme based on 2DCS and DNA coding has good encryption effect, and it is impossible to obtain the relevant information of the corresponding plain images from the secret images through the histogram analysis.
The correlation plots in horizontal (first row), vertical (second row) and diagonal (third row) directions of plain image ‘House’, decrypted image ‘House’, plain image ‘Parrots’, decrypted image ‘Parrots’, carrier image ‘Lena’ and encrypted image ‘Lena’ are listed from the first to the sixth columns, respectively
Correlation coefficients analysis
For visually meaningful images, the correlation between adjacent pixels is high. The correlation between adjacent pixels of the VMEI obtained in this paper should also be high, and should be close to the correlation coefficient of the carrier image. In this subsection, we randomly select 1000 pairs of adjacent pixels from the plain images, decrypted images, carrier images and encrypted images, and then calculate the correlation coefficients in the horizontal, vertical and diagonal directions via the following formula
where N is the total number of the selected pixels, \(x_i\) and \(y_i\) are the grayscale values of two adjacent pixels in the image, \({\bar{x}} = \frac{1}{N}\sum \nolimits _{i = 1}^N {x_i}\) and \({\bar{y}} = \frac{1}{N}\sum \nolimits _{i = 1}^N {y_i}\) are mean values, respectively.
Table 8 gives the correlation coefficients of the carrier images and encrypted images in horizontal, vertical and diagonal directions, respectively. Table 9 gives the correlation coefficients of the plain images and decrypted images in horizontal, vertical and diagonal directions, respectively. The correlation of each image in different directions is strong. Figure 9 plots the correlation distributions of the images in the first group in horizontal, vertical and diagonal directions in turn. The correlation coefficients and correlation distributions of the plain image and the corresponding decrypted image in all directions are very close, and the correlation coefficients and correlation distributions of the carrier image and the encrypted image in all directions are also very close. The correlation of the decrypted image in all directions is almost the same as that of the corresponding plain image, indicating that the decryption effect is good. The correlation of encrypted image in all directions is almost the same as that of corresponding carrier image, indicating that the encrypted image has strong visual security.
Information entropy analysis
Information entropy is often used to analyze the randomness of grayscale images, which can be calculated by
where \(p(x_i)\) represents the probability of ith possible value \(x_i\). For an 8-bit grayscale image, \(n=255\) represents the total number of pixel values, and the closer the information entropy is to 8, the more uniform the image pixel distribution is.
The information entropy values of the carrier images, encrypted images, secret images, plain images and decrypted images are shown in Table 10. The visual effect and information entropy of the plain image and the corresponding decrypted image are very similar, indicating that decryption effect of the scheme is good. The information entropy of the secret image is close to 8, indicating that the encryption effect of the pre-encryption algorithm is good. Further, the information entropy of the carrier image is very close to that of the corresponding encrypted image, indicating that the visual security of the encrypted image is very strong. We also compare the information entropy of secret images in this scheme with that of other schemes, and the results are shown in Table 11. The results show that the secret image information entropy obtained by the pre-encryption algorithm in this scheme is similar to that in other schemes.
Time complexity analysis
Time consumption of encryption and decryption algorithms is also an important index to evaluate the performance of the encryption scheme. Table 12 gives the time consumed for the encryption, embedding, extraction and decryption of the three groups of images in Fig. 7, where “Encryption” means the time required to encrypt one plain image to obtain the corresponding secret image, “Embedding” represents the time consumed to embed the two secret images into the carrier image, “\(\text {total}_{{en}}\)” is the total time required in the “Encryption” and “Embedding” process, “Extraction” means the time consumed in two secret image extracting process, “Decryption” means the time consumed in the decryption process, and “\(\text {total}_{{de}}\)” is the total time required in the “Extraction” and “Decryption” process. Table 12 shows that the encryption process takes an average of 0.0450 s to encrypt one image. This scheme encrypts two images, so the time is multiplied by 2, which is 0.090 s. The average time consumed in the embedding process of the two images is 0.1572 s, and the entire encryption process takes 0.2471 s. It can be seen that the encryption and embedding process takes less time. The average time consumed in the extraction process of the two secret images is 0.0942 s, and it takes an average of 1.4457 s to decrypt one image. This scheme decrypts two images, so the time is multiplied by 2, which is 2.8914 s, and the entire decryption process takes 2.9855 s.
We compare the time consumed of pre-encryption, embedding, extraction and decryption in this scheme with that of other schemes, and the results are shown in Table 13. “−” in the Table 13 indicates that we did not find relevant data. It can be seen that this scheme and other schemes take less time in the process of pre-encryption, embedding and extraction. The decryption process in Ref. [42] takes the shortest time, only 0.0504 s. However, this scheme does not introduce CS theory, so that the size of the encrypted image is four times larger than that of the plain image. The CS theory is introduced into the pre-encryption process in Refs. [26] and [27], so that the time consumed in the decryption process of Refs. [26] and [27] is similar to that of the decryption process in this paper. In the decryption process, the 2DCS reconstruction algorithm needs to solve the convex optimization equation of the underdetermined problem under the sparse constraint, so the decryption process takes a certain time.
Key sensitivity analysis
Key sensitivity is also an important index for evaluating the security of an encryption scheme. In this paper, some keys are controlled by the PWLCM. We analyze the sensitivity of the decrypted image to the initial value \(x_0\), and the results are shown in Fig. 10. The first row is two decrypted images obtained by decrypting the encrypted image with the correct decryption keys; the second row is two decrypted images obtained by decrypting the encrypted image using the wrong key \(x_0^1+10^{-15}\), and the other keys are correct. It can be seen that the correct decrypted image 1 cannot be obtained even if the deviation of \(x_0^1\) is \(10^{-15}\), but the wrong \(x_0^1\) does not affect the acquisition of the decrypted image 2 at all. In fact, an error in \(x_0^i, p^i, (i=1,2,5,6,7,8)\) will result in similar results, since these keys are only relevant to decrypted image 1, not to decrypted image 2. The third row is two decrypted images obtained by decrypting the encrypted image using the wrong key \(x_0^2+10^{-15}\), and the other keys are correct. It can be seen that the correct decrypted image 2 cannot be obtained even if the deviation of \(x_0^2\) is \(10^{-15}\), but the wrong \(x_0^2\) does not affect the acquisition of the decrypted image 1 at all. In fact, an error in \(x_0^i, p^i, (i=3,4,9,10,11,12)\) will result in similar results, since these keys are only relevant to decrypted image 2, not relevant to decrypted image 1. To sum up, the decrypted image is very sensitive to the corresponding chaotic initial value \(x_0^i\). Even if the deviation is \(10^{-15}\), the corresponding correct decrypted image cannot be obtained. If \(p^i\) is off by \(10^{-15}\), it will also lead to the same result. That is to say, the precision of \(p^i\) is also \(10^{-15}\), so the key space corresponding to a set of chaotic parameters (\(x_0^i, p^i\)) is \(10^{-30}\).
Various attacks
In this subsection, we demonstrate the ability of the proposed VMIE scheme to resist brute force attack, differential attack, and chosen-plaintext attack.
Brute force attack
Key space is one of the important indicators to measure the ability of an encryption scheme to resist brute force attack. When decrypting plain image 1, we need to use \(x_0^i, p^i, (i=1,2,5,6,7,8)\), \( \Phi _1, \Phi _2, a_1, b_1, c_1, d_1\), \( Y_{1max}, Y_{1mix}\) as the decryption keys. When decrypting plain image 2, we need to use \(x_0^i, p^i, (i=3,4,9,10,11,12)\), \( \Phi _3, \Phi _4, a_2, b_2, c_2, d_2\), \( Y_{2max}, Y_{2min}\) as the decryption keys. From the key sensitivity analysis, it can be seen that the precision of PWLCM parameters \(x_0^i, p^i\) is \(10^{-15}\), and we set the precision of the maximum and minimum values of the sampled value matrix to be \(10^{-15}\). Decrypting an image requires 6 sets of PWLCM parameters, one maximum value and one minimum value as keys, and the corresponding key space turns out to be \(10^{30 \times 6} \times 10^{15 \times 2} = 10^{210}\). The comparison results of this encryption scheme and other encryption schemes in terms of key space are shown in Table 14. Two plain images are encrypted in the presented encryption scheme, and \(10^{210}\) in Table 14 refers to the key space required to decrypt one plain image. The key space of this encryption scheme is larger than that in Refs. [27, 29, 31, 34, 42] and smaller than that in Ref. [43]. In addition, in the process of decrypting plain image 1, multiple parameters (\( \Phi _1, \Phi _2,a_1, b_1, c_1, d_1\)) are required as additional keys, which are sufficient to resist brute force attack.
Differential attack
By changing one or more pixel values in the plain image, a cryptanalyst can obtain a new encrypted image, and by observing the difference in the pixel values of the two encrypted images, the cryptanalyst can explore the method used to crack the encryption scheme. Two important indexes to evaluate the resistance of encryption system to differential attack are the number of pixels change rate (NPCR) and the unified average changing intensity (UACI).
In order to study the ability of the pre-encryption algorithm based on 2DCS and DNA encoding to resist differential attack, we change the plain image by 1 bit and calculate the NPCR and UACI of the two secret images, and the results are shown in Table 15. The obtained mean values of NPCR and UACI are \(99.44\%\) and \(33.47\%\), respectively. It can be seen that the pre-encryption algorithm can resist differential attack. To illustrate the visual security of the encrypted image, we also calculate the NPCR and UACI of the two encrypted images when only plain image 1 changes by one bit. Then, use the same keys and carrier image to obtain two encrypted images according to the encryption and embedding process, and then calculate the NPCR and UACI values of the two encrypted images, and the results are shown in Table 15. When plain image 1 changes by 1 bit, the average NPCR of the corresponding two encrypted images is \(81.02\%\), while the UACI is very low, only \(0.6316\%\). It shows that when only one pixel value of the plain image 1 changes, \(81.02\%\) of the pixel values in the obtained encrypted image change, but the change intensity is very low, only \(0.6316\%\), so the visual security of the encrypted image is guaranteed.
Chosen-plaintext attack
In terms of the analysis of the cryptographic system, the method of chosen-plaintext attack is commonly used to obtain plain image, and this attack is used to crack some image encryption schemes. The pre-encryption process of the encryption scheme presented in this paper contains a scrambling operation, and an image with equal pixel values (for example, an all-zero image) can make the scrambling effect invalid. Therefore, attackers can choose such images to try to attack encryption schemes that include scrambling operations. For the all-zero image, the scrambling operation in the pre-encryption process is invalid, that is to say, Eqs. 7 and 8 are invalid, and the all-zero image is converted into a matrix with only \(-128\) and 127 using Eq. 9, and then the binary matrix is sampled by 2DCS and DNA encoding to obtain a secret image. From Section 4.8, even though the plain image only changes by one bit, the average NPCR of the obtained secret image is \(99.44\%\), and the average UACI is \(33.47\%\), so the pre-encryption algorithm can resist the chosen-plaintext attack.
Conclusion
This paper proposes a visually meaningful double-image encryption scheme by using 2DCS and multi-rule DNA encoding, which realizes simultaneous encryption, compression and hiding of two plain images. In our work, the two plain images undergo a pre-encryption scheme by using 2DCS and DNA encoding theory to obtain two secret images. Then, through the IWT-based double-image embedding process and 2K correction process, the two secret images are embedded into the coefficient matrix of the carrier image, and the obtained result is performed by inverse IWT to acquire a visually meaningful encrypted image. In addition, PWLCM is used in this paper to generate some of the keys needed. The 2DCS and DNA encoding process improves the data security of the plain image, and the 2k correction process improves the visual security of the encrypted image. Encrypting two plain images into an equal-sized encrypted image further reduces transmission bandwidth and storage space. The simulation results and comprehensive analysis show that the VMIE scheme has good encryption and decryption effect, high key sensitivity, large key space and short time consumption, and can resist differential attack and chosen-plaintext attack.
In future work, we will try to encrypt more images into a VMEI. Due to the limited size of the encrypted image, there are two ways to encrypt more plain images in it: 1. Reduce the sampling rate of the CS process, which will reduce the quality of the decrypted image; 2. Increase the amount of data embedded in the carrier image coefficient matrix, which will reduce the visual security of encrypted image. To solve the above two problems, it is necessary to design a better CS recovery algorithm and a better embedding correction algorithm.
References
Zhang Y, Xiao D (2013) Double optical image encryption using discrete chirikov standard map and chaos-based fractional random transform. Optics and Lasers in Engineering 51(4):472–480
Tang Z, Song J, Zhang X, Sun R (2016) Multiple-image encryption with bit-plane decomposition and chaotic maps. Optics and Lasers in Engineering 80:1–11
Hua Z, Zhu Z, Yi S, Zhang Z, Huang H (2021) Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Information Sciences 546:1063–1083
Talhaoui MZ, Wang X (2021) A new fractional one dimensional chaotic map and its application in high-speed image encryption. Information Sciences 550:13–26
S KU, Mohamed A (2021) Novel hyper chaotic color image encryption based on pixel and bit level scrambling with diffusion. Signal Processing: Image Communication 99, 116,495
Alahmadi Ah (2022) Chaos coordinated neural key synchronization for enhancing security of iot. Complex & Intelligent Systems 8(2):1619–1637
Situ G, Zhang J (2004) Double random-phase encoding in the fresnel domain. Optics Letters 29(14):1584–1586
Zhou N, Wang Y, Gong L (2011) Novel optical image encryption scheme based on fractional mellin transform. Optics communications 284(13):3234–3242
Li X, Wang Y, Wang Q, Kim S, Zhou X (2019) Copyright protection for holographic video using spatiotemporal consistent embedding strategy. IEEE Transactions on Industrial Informatics 15(11):6187–6197
Zhou L, Xiao Y, Chen W (2020) Learning complex scattering media for optical encryption. Opt. Lett. 45(18):5279–5282
Zheng X, Xu J, Li W (2009) Parallel dna arithmetic operation based on n-moduli set. Applied Mathematics and Computation 212(1):177–184
Wang X, Liu C (2016) A novel and effective image encryption algorithm based on chaos and dna encoding. Multimedia Tools & Applications 76(5):1–17
Huo D, Zhu X, Dai G, Yang H, Feng M (2020) Novel image compression-encryption hybrid scheme based on dna encoding and compressive sensing. Applied Physics B 126(45):1–9
Zhang S, Liu L (2021) A novel image encryption algorithm based on spwlcm and dna coding. Mathematics and Computers in Simulation 190:723–744
Uddin M, Jahan F, Islam MK, Rakib Hassan M (2021) A novel dna-based key scrambling technique for image encryption. Complex & Intelligent Systems 7(6):3241–3258
Rawat N, Kim B, Muniraj I, Situ G, Lee BG (2015) Compressive sensing based robust multispectral double-image encryption. Appl. Opt. 54(7):1782–1793
Zhou N, Li H, Wang D, Pan S, Zhou Z (2015) Image compression and encryption scheme based on 2d compressive sensing and fractional mellin transform. Optics Communications 343:10–21
Zhou K, Fan J, Fan H, Li M (2020) Secure image encryption scheme using double random-phase encoding and compressed sensing. Optics & Laser Technology 121(105):769
Jiang X, Xiao Y, Xie Y, Liu B, Ye Y, Song T, Chai J, Liu Y (2021) Exploiting optical chaos for double images encryption with compressive sensing and double random phase encoding. Optics Communications 484(126):683
Wang X, Su Y (2021) Image encryption based on compressed sensing and dna encoding. Signal Processing: Image Communication 95(116):246
Gan Z, Chai X, Bi J, Chen X (2022) Content-adaptive image compression and encryption via optimized compressive sensing with double random phase encoding driven by chaos. Complex & Intelligent Systems pp. 1–19
Li X, Wang Y, Wang QH, Liu Y, Zhou X (2019) Modified integral imaging reconstruction and encryption using an improved sr reconstruction algorithm. Optics and Lasers in Engineering 112:162–169
Zhang H, Wang X qing, Sun Y jie, Wang X yuan (2020) A novel method for lossless image compression and encryption based on lwt, spiht and cellular automata. Signal Processing: Image Communication 84, 115,829
Roy S, Shrivastava M, Rawat U, Pandey CV, Nayak SK (2021) Iesca: An efficient image encryption scheme using 2-d cellular automata. Journal of Information Security and Applications 61(102):919
Bao L, Zhou Y (2015) Image encryption: Generating visually meaningful encrypted images. Information Sciences 324:197–207
Chai X, Gan Z, Chen Y, Zhang Y (2017) A visually secure image encryption scheme based on compressive sensing. Signal Processing 134:35–51
Chai X, Wu H, Gan Z, Zhang Y, Chen Y, Nixon KW (2020) An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic lsb embedding. Optics and Lasers in Engineering 124(105):837
Pan C, Ye G, Huang X, Zhou J (2019) Novel meaningful image encryption based on block compressive sensing. Security and Communication Networks 2019:1–12
Zhu L, Song H, Zhang X, Yan M, Zhang T, Wang X, Xu J (2020) A robust meaningful image encryption scheme based on block compressive sensing and svd embedding. Signal Processing 175(107):629
Wen W, Hong Y, Fang Y, Li M, Li M (2020) A visually secure image encryption scheme based on semi-tensor product compressed sensing. Signal Processing 173(107):580
Chai X, Wu H, Gan Z, Zhang Y, Chen Y (2020) Hiding cipher-images generated by 2-d compressive sensing with a multi-embedding strategy. Signal Processing 171(107):525
Huo D, Zhu Z, Wei L, Han C, Zhou X (2021) A visually secure image encryption scheme based on 2d compressive sensing and integer wavelet transform embedding. Optics Communications 492(126):976
Chai X, Wu H, Gan Z, Han D, Zhang Y, Chen Y (2021) An efficient approach for encrypting double color images into a visually meaningful cipher image using 2d compressive sensing. Information Sciences 556:305–340
Wang H, Xiao D, Li M, Xiang Y, Li X (2019) A visually secure image encryption scheme based on parallel compressive sensing. Signal Processing 155:218–232
Hua Z, Zhang K, Li Y, Zhou Y (2021) Visually secure image encryption using adaptive-thresholding sparsification and parallel compressive sensing. Signal Processing 183(107):998
Zhu L, Jiang D, Ni J, Wang X, Rong X, Ahmad M, Chen Y (2022) A stable meaningful image encryption scheme using the newly-designed 2d discrete fractional-order chaotic map and bayesian compressive sensing. Signal Processing 195(108):489
Ye G, Pan C, Dong Y, Jiao K, Huang X (2021) A novel multi-image visually meaningful encryption algorithm based on compressive sensing and schur decomposition. Trans. Emerg. Telecommun. Technol. 32(2):1–14
Singh O, Singh A (2021) Data hiding in encryption–compression domain. Complex & Intelligent Systems pp. 1–14
Yang YG, Zhang YC, Chen XB, Zhou YH, Shi WM (2018) Eliminating the texture features in visually meaningful cipher images. Information Sciences 429:102–119
Kanso A, Ghebleh M (2017) An algorithm for encryption of secret images into meaningful images. Optics and Lasers in Engineering 90:196–208
Tuncer T, Dogan S, Tadeusiewicz R, Pławiak P (2019) Improved reference image encryption methods based on 2 correction in the integer wavelet domain. International Journal of Applied Mathematics and Computer Science 29(4):817–829
Yang YG, Wang BP, Pei SK, Zhou YH, Shi WM, Liao X (2021) Using m-ary decomposition and virtual bits for visually meaningful image encryption. Information Sciences 580:174–201
Jiang D, Liu L, Zhu L, Wang X, Rong X, Chai H (2021) Adaptive embedding: A novel meaningful image encryption scheme based on parallel compressive sensing and slant transform. Signal Processing 188(108):220
Ping P, Yang X, Zhang X, Mao Y, Khalid H (2022) Generating visually secure encrypted images by partial block pairing-substitution and semi-tensor product compressed sensing. Digital Signal Processing 120(103):263
Ghaffari A, Babaie-Zadeh M, Jutten C (2009) in 2009 IEEE International Conference on Acoustics, Speech and Signal Processing , pp. 3157–3160
Fang Y, Wu J, Huang B (2012) 2d sparse signal recovery via 2d orthogonal matching pursuit. Science in China Series F: Information Sciences 55(4):889–897
Chen G, Li D, Zhang J (2014) Iterative gradient projection algorithm for two-dimensional compressive sensing sparse image reconstruction. Signal Processing 104:15–26
Zhang B, Xiao D, Xiang Y (2020) Robust coding of encrypted images via 2d compressed sensing. IEEE Transactions on Multimedia 23:2656–2671
Sun S (2016) A novel edge based image steganography with 2k correction and huffman encoding. Information Processing Letters 116(2):93-99
Zhou W, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13(4)
Setiadi DRIM (2020) Psnr vs ssim: imperceptibility quality assessment for image steganography. Multimedia Tools and Applications pp. 1–22
Acknowledgements
The authors are grateful to Minghui Feng for her sincere and patient help on English expression.
Funding
The work was supported by the National Natural Science Foundation of China (61475104 and 61177009); the Regional Innovation and Development Joint Funds of the National Natural Science Foundation of China (U22A2079); the Key projects of Natural Science Research of Universities in Anhui Province (KJ2020A0346); the Major projects of Natural Science Research of Universities in Anhui Province (KJ2020ZD39); the Open Research Fund of Anhui Key Laboratory of Detection Technology and Energy Saving Devices, Anhui Polytechnic University (DTESD 2020A02 and DTESD 2020A06); the Anhui Province College Students’ Innovative Training Program (S202110363196); the Anhui Polytechnic University Research Startup Foundation (2019YQQ007).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Huo, D., Qiu, Y., Han, C. et al. A visually meaningful double-image encryption scheme using 2D compressive sensing and multi-rule DNA encoding. Complex Intell. Syst. 9, 4783–4803 (2023). https://doi.org/10.1007/s40747-023-00989-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40747-023-00989-6