Abstract
A novel adaptive image watermarking methodology, robust to common signal processing attacks, is proposed in this paper. The introduced watermarking scheme uses prior knowledge in the form of IF–THEN fuzzy rules to intelligently decide the appropriate embedding strength applied to each coefficient in the moment domain carrying the watermark information. Initially, the prior knowledge regarding the amount of watermark information each moment coefficient of the original image has the capacity to hide is used to build an optimized rule-based fuzzy inference system. The resulted system is able to provide the appropriate embedding strength for each moment coefficient, ensuring high imperceptible watermarked images and high fidelity in watermark extraction. Extensive experiments under several attacking conditions demonstrate that the proposed methodology can improve the robustness of the watermarked images by a significant factor up to 32 %, without affecting their optical quality.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Watermarking of digital images constitutes the main subject of this work. Although this research topic has occupied the scientists for many years, it still draws attention. The increased interest in digital watermarking comes from the rapid growing of the digital contents’ interchange through computers, such as images, videos, sounds and documents. Due to this fact, special handling of the contents’ transfer is needed to secure the copyright and the authenticity of the owner.
This work concerns the watermarking of digital images, where the watermark information is embedded into a transform domain of the original (host) image. The embedding of the watermark information inside a transform domain of the image instead of the spatial image’s domain, exhibits some benefits [1] regarding the robustness of the watermark extraction under various attacking conditions.
Several transform domain watermarking methods have been proposed in the past, having as primary goal the utilization of the used transform properties to achieve robustness and imperceptibility. Liu and Tan [2] proposed a novel watermarking algorithm based on singular value decomposition (SVD) domain, in resolving rightful ownership and in resisting common attacks. Barni et al. [3] embedded watermark information in selected discrete cosine transform (DCT) coefficients to achieve robustness. Kang et al. [4] proposed a blind discrete wavelet and Fourier transform (DWT–DFT) composite image watermarking algorithm, which is robust to affine transformations and JPEG compression. Jayalakshmi et al. [5] introduced the contourlet transform showing more robust to mean filtering, quantization and JPEG compression than wavelet and DCT domains. More recently, Yang et al. [6] proposed a pioneer methodology to tackle both color information and geometric attacks using the quaternion polar harmonic transform.
Based on the above-mentioned robustness property of the transform domain watermarking, the moment transform according to which an image is described by a set of moment coefficients with respect to an orthogonal polynomial basis is considered herein. The representation of an image with moments has been proved to be accurate and compact with minimum information redundancy and high noise resistance.
In the last two decades, several watermarking methods [7] using image moments have been proposed. Although these methods share a common transform domain workbench, they differ to the type of the orthogonal polynomial basis used as kernels in constructing the moment coefficients.
The proposed methodology is independent of the polynomial type of the moment kernels, since it focuses on the mechanism of moment coefficients modification during the dither modulation procedure. More precisely, a conventional moment-based watermarking scheme, consisting of a novel adaptive dither modulation processing stage, is proposed in this work. The adaptive nature of the introduced dither modulation is demonstrated by the different quantization steps (deltas—\(\Delta \)s) applied to each moment coefficient in contrast to the single/uniform case [8] where the same delta is used for all moments. This adaptive modification of the moments controls the embedding strength of the watermark information and, therefore, the imperceptibility of the watermarked image and the robustness of the watermark extraction under several attacking conditions.
The application of the most appropriate quantization step for each moment coefficient is decided, for the first time herein, by incorporating prior knowledge through a fuzzy rule-based inference system calibrated by a genetic algorithm. Initially, the parameters that specify a moment coefficient (magnitude, polynomial order and repetition) are defined and their relations with the quantization step are determined with IF–THEN rules. In a next stage, the membership functions of each system’s input/output are optimally tuned through an optimization procedure aiming to maximize the quality of the watermarked image (imperceptibility) and the accuracy of the watermark extraction (robustness) in several attacking environments.
To summarize, the contribution of this work is the proposal of a blind watermarking methodology with significant enhanced robustness under signal processing attacks and imperceptibility of high levels. Moreover, the proposed method is transformation independent, hence can be applied to other transform domains (e.g., Fourier, Wavelet, etc.), while its complexity is very low.
The remainder of this paper is organized as follows: Sect. 2 reviews the application of orthogonal moments in image watermarking. A detailed discussion regarding the necessity of an adaptive watermarking scheme is presented in Sect. 3. The main functional principles along with the description of each processing step of the proposed methodology are discussed in Sect. 4. In Sect. 5, an extensive experimental study demonstrates the effectiveness of the proposed adaptive watermarking scheme. Finally, some very useful conclusions are summarized in Sect. 6.
Watermarking by the method of moments
Considering image watermarking in the transform domain, image’s orthogonal moment coefficients are used to carry the watermark information in the proposed methodology. Orthogonal image moments have gained significant attention as compact content descriptors with minimum information redundancy [9], in pattern recognition [10], computer vision [11–13] and image processing [14] applications.
In the last 20 years, several moment families were proposed in the literature each one showing different properties and description capabilities. Among them the Zernike [15], pseudo-Zernike [15], Legendre [16], Fourier–Mellin [14], Tchebichef [17] and Krawtchouk [18] moments are the most widely used.
Since the first introduction of image moments for watermarking purposes by Alghoniemy and Tewfik [19], in an attempt to take advantage of the inherent property of the orthogonal moment coefficients, to uniquely describe the content of an image, a lot of work has been performed in this direction through the years.
Some valuable works in the field of moment-based watermarking which constitute milestones for this research topic are the first introduction of the orthogonal moments in watermarking by Kim and Lee [20] and the application of the dither modulation as watermark embedding mechanism by Xin et al. [21]. The aforementioned three works have highly motivated the scientists to develop more robust and efficient moment-based watermarking techniques.
One rising research direction in this field is the embedding of multiple watermarks (to achieve crop robustness) after locating them by the use of a feature detector. Deng et al. [22] proposed such a watermarking method combining Tchebichef moments and Harris–Laplace detector. Initially a set of feature points are extracted, and then non-overlapped disks centered at extracted feature points are used to embed the watermarks. In the same direction, Wang et al. [23] applied multi-scale Harris detector and wavelet moments and Papakostas et al. [24] enhanced the robustness of the Harris detector in attacking conditions.
Another popular, moment-based watermarking research area is the watermarking of color images. Following the successful application of several quaternionic image transformations in image watermarking [6–25], Tsougenis et al. [26] introduced quaternion radial moments as the embedding domain of the color images for watermark insertion. Wang et al. [27] studied the quaternion exponent moments as alternative moment domain for color image watermarking to improve robustness.
Recently, Tsougenis and Papakostas [28] and Papakostas et al. [29] have focused on the locality property of the moment coefficients, specifically those produced by the Krawtchouk polynomials. They claimed that all the image portions are not appropriate (in terms of imperceptibility and robustness) for watermark embedding and thus by tackling the watermarking procedure as an optimization process, the watermarking locality behavior could be controlled.
Towards the improvement of the overall watermarking performance, the authors propose herein the adaptive dither modulation of the moment coefficients by considering prior knowledge regarding the amount of the information that each coefficient is able to hide. The information hiding capabilities of the moment coefficients are determined by their magnitudes, polynomial orders and repetitions, parameters that are highly connected with the imperceptibility of the watermarked image and the robustness of the watermark extraction in the presence of attacks.
By first analyzing the necessity of adaptive watermarking, in the following sections the main functional modules of the proposed methodology are discussed with emphasis on the design of the adaptive dither modulator.
Adaptive watermarking
The term adaptive is mainly used to describe a process, behavior and/or a system that is able to interact with its environment and adjusts its operation according to the environment’s factors that are closely connected with it.
In the context of watermarking, adaptation is achieved through different directions, so as to avoid watermark embedding in edged areas where changes are more detectable [30, 31] or to improve the imperceptibility of the watermarked image by simulating models based on the Human Visual System (HVS) [32, 33].
Recently, Tsougenis and Papakostas [28], Papakostas et al. [29] have proposed an adaptive watermarking scheme where the most appropriate image portion is adaptively selected, such that the imperceptibility and robustness of the watermarked image be improved.
Another, direction that merits attention is the adaptive modification of the moment coefficients (adaptive embedding strength) subject to some criteria. The first attempt that relates the embedding strength (quantization step—\(\Delta \)) with moments’ orders and repetitions was performed by Xin et al. [21]. They proposed an analytical formula that provides the appropriate quantization step (\(\Delta \)) subject to the used moment’s orders and repetitions and a desired quality in terms of PSNR index. However, this approach does not provide different quantization step for each moment coefficient, but it relates the selection of the embedding strength with the quality of the derived watermarked image. Following the same methodology, Tsougenis et al. [34] along with the extension of this strategy to the case of the Polar Harmonic coefficients proved experimentally the need for an adaptive mechanism, with considerable results.
However, the aforementioned technique that leads to adaptive quantization steps is applicable only for radial transformations/moments and, therefore, it cannot be used for all moment families such as the discrete, Tchebichef and Krawtchouk ones.
One possible solution to generalize the manipulation of all moment types is the use of an evolutionary optimization procedure to search for optimal quantization steps for each moment coefficient. However, this approach leads to a hard to solve optimization problem in the case of wide length watermark, where the number of moments is too big.
In this paper, a unified methodology, which is independent of the moment type used to embed the watermark information, is proposed. The introduced method is making use of experts’ knowledge encoded as IF–THEN rules under a fuzzy reasoning framework.
Proposed methodology
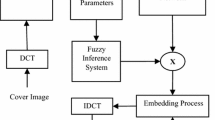
The watermarking method introduced herein is mainly based on an adaptive quantization module consisting of a genetically optimized Fuzzy Inference System (FIS), which provides the appropriate quantization step (\(\Delta )\) to each moment coefficient. The proposed watermarking methodology is illustrated in Fig. 1.
The proposed technique is divided into two different operation modes, namely the calibration mode where the FIS parameters are optimized through a genetic algorithm and the normal mode where the resulted FIS is used to provide quantization steps in an adaptive sense.
During the calibration phase the membership functions parameters of the FIS participated to the IF–THEN rules are genetically optimized in terms of imperceptibility of the watermarked image (PSNR quality index) and the robustness of the extraction procedure (BER) under several attacking conditions. Once the FIS parameters are determined in an optimization context, the resulted FIS can be used in the normal mode to provide the quantization steps for each moment coefficient independent of the image that needs to be watermarked.
The main procedures that constitute the methodology of Fig. 1 are analyzed in detail in the following sections.
Watermark embedding
The watermark embedding procedure constitutes the first part of the proposed methodology, which incorporates the processing tasks that aim to insert the watermark information into the host image in an imperceptible way, as illustrated in Fig. 2.
In Fig. 2, the original image corresponds to the host image where the L-bit length binary message (\(b_{\mathrm {1}}\), \(b_{\mathrm {2}}\), …, \(b_{{L}})\) is inserted, by constructing the final watermarked image. All the intermediate processing stages participating in the proposed watermarking embedding phase are described next.
Step 1: moments computation
Considering that each bit of the embedded message is inserted into one moment coefficient, a set of orthogonal moments up to a specific order P and repetition Q, such that the number of computed moments are equal to the inserted message length, are computed. The methodology of Fig. 1 is independent of the family/type of the used orthogonal moments and several moment types can be examined to select the most efficient one.
The general computation form of an orthogonal image moment of order p and repetition q for the case of an image f(x, y) with \(N \times N\) pixel size is:
where Kernel\(_{pq}()\) corresponds to the moment’s kernel consisting of specific polynomials of order p and q, which constitute the orthogonal basis and NF is a normalization factor. The type of Kernel’s polynomial gives the name to the moment family by resulting in a wide range of moment types [35].
At this stage, there is a need for key set \(K_{\mathrm {1}}\), which is also necessary at the detectors’ side and corresponds to the set of parameters \(K_{1} :\{ {P,Q} \}\).
Step 2: dither modulation
Dither modulation constitutes a significant methodology that embeds watermark information into a host signal, increases the embedding rate with minimum distortion of the original signal and ensures robustness under attacking conditions [8]. The dither modulation embedding scheme has been applied successfully in moment-based watermarking algorithms [28–30]. In this work, the orthogonal moments (\(M_{{pq}})\) of the original image is used as the host signal, where the L-bit length binary message (\(b_{\mathrm {1}}\), \(b_{\mathrm {2}}\), …, \(b_{{L}})\) is inserted according to (2).
where [\(\cdot \)] is the rounding operator, \(\Delta _{{i}}\) the quantization step and \(d_{{i}}(\cdot )\) the dither function satisfying \(d_{{i}}\)(1)\(=\Delta \)/2\(+\)d\(_{{i}}\)(0) of the ith moment coefficient. The dither vector (\(d_{\mathrm {1}}\)(0), \(d_{\mathrm {2}}\)(0),…, \(d_{{L}}\)(0)) is uniformly distributed in the range \([0, \Delta ]\). The quantization steps \(\{ {\Delta _{i} : i=1,\ldots ,L} \}\) used in this phase are different for each coefficient, in fact they are provided by the FIS module and, therefore, there is no need to send them to the detector’s side.
Step 3: watermark construction
The modified moments (\(\tilde{{M}}_{p_{i} q_{i}}\)) resulted by the application of the dither modulation of (2) are used to construct the watermark information. It is worth mentioning that there is not any reconstruction of the entire watermarked image, since the specific process consists of a laborious and time-consuming task due to the fact that it requires a large number of moments to achieve low reconstruction errors. The proposed method manages to isolate the watermark part of the modified moments (frequency domain) and construct a watermark image which is added to the original image (spatial domain), as depicted in the following Eqs. (3)–(5). The moments applied during the specific process are few and equal to the binary message length.
where quantity \(D_{pq} \) corresponds to the additional information inserted to the host image through moment of order p and repetition q, which is equal to the difference between the modified and original moments defined as:
By identifying that the first double summation of (3) corresponds to the (\(x_{{i}}\), \(y_{{j}})\) pixel of the original image and the second part of the equation to the inserted information, it is concluded that the entire watermarked image is obtained by the following (5).
Based on (5) it is evident that the watermark embedding has taken place in spatial domain, which constitutes an advantage of the proposed algorithm since it avoids any image reconstruction, many image moments need, adding a significant time overhead.
Watermark extraction
The watermark extraction procedure at the detector’s side consists of almost the same processing steps with those of the embedding stage, as illustrated in Fig. 3. The only difference is the application of the Minimum Distance Decoder (MDD) module, being applied to extract the embedded binary message from the dither modulated, modified orthogonal moments of the incoming (attacked) image.
The operation of the MDD is defined by the following formula:
where \(| {M_{p_{i} q_{i} }^{{\prime }} } |_{j} \) is the ith orthogonal moment of the attacked image which is quantized considering a bit value of \(j\in \left[ {0,1} \right] \). Therefore, a bit \(\hat{{b}}_{i} \) is decided to be 0 or 1 regarding to the distance between the corresponding quantized orthogonal moments and its original value \(M_{p_{i} q_{i} }^{{\prime }} \). The extracted bit is assigned depending on the j of the minimum distance \(\hat{{b}}_{i} \) value.
Finally, it is worthwhile noting that the usage of the dither modulation in both watermark embedding and extraction procedures enhances the blind nature of the proposed algorithm, since there is no longer need for the original orthogonal moments or the watermarked image to extract the hidden information. Instead, it is possible to extract the embedded information by just applying the same quantization module in combination with the MDD.
Fuzzy inference system (FIS): design principles
In both aforementioned watermark embedding and extraction procedures, a Fuzzy Inference System (FIS) is applied to provide the appropriate quantization step for each moment coefficient, by giving an adaptive nature to the whole watermarking process.
The initial idea behind the usage of such a module comes from the fact that each moment coefficient describes different part of the host image, with the low and high order and repetition moments being descriptors of the coarse- and fine-image information, respectively. Moreover, the amplitude of each moment corresponds to the amount of information they carry.
Therefore, based on the above observations a question is raised regarding the magnitude of the quantization step (\(\Delta \)) that is desirable to be applied to each moment coefficient. For example, a big quantization step for a moment of low order and repetition and small amplitude could cause high-image degradation, since the coarse image information will be modified significantly. On the other hand, if a small quantization step is applied to a moment of low order and repetition but with high amplitude, then the inserted information will be absorbed by the image’s content, and thus it could not be extracted on the detector’s side. As a matter of fact, the adaptivity property of the proposed method manages to cope with the specific tradeoff.
From the previous theoretical analysis, it is obvious that there is some empirical knowledge regarding the selection of the most appropriate quantization step (which controls the embedding strength), subject to moment’s order, repetition and amplitude parameters. However, this knowledge yet has not been taken into account of any moment-based watermarking algorithms to the best of the author’s knowledge.
An efficient way to represent this knowledge is using linguistic descriptions, instead of numerical ones, due to the absence of analytical mathematical expressions that describe the moments’ parameters relationships. In other words, some fuzziness is encountered, thus fuzzy logic and reasoning are the appropriate frameworks to deal with this problem.
For this purpose, an FIS of Mamdani type has been designed (Fig. 4) having moments’ order (p), repetition (q) and amplitude (\(| {M_{pq} } |)\) as input parameters, while the system’s output is the estimated quantization step (\(\Delta )\), for the incoming moment.
Following the fundamental design principles of fuzzy inference systems [36], there is a need to define the moments’ parameters that describe their qualitative and quantitative characteristics and control the watermarking performance, in terms of fuzzy logic. For this reason, the value of each moment parameter is characterized by three fuzzy linguistic terms {LOW, MEDIUM, HIGH} subject to a specific range, while three triangular membership functions (7) are selected to describe their behavior, as depicted in Fig. 5.
Each triangular membership function is determined by a set of three parameters \(\left\{ {f_{0} ,f_{1} ,f_{2} } \right\} \) that control its position, and is defined as:
After the definition of the input/output parameters of the FIS, the relationships between those variables have to be determined. As already mentioned in the previous sections, there is some knowledge regarding these relationships which can be described by appropriate fuzzy rules.
This knowledge comes from the meaning of LOW, MEDIUM, HIGH moments’ amplitudes, orders and repetitions in image representation. For example, moments of LOW orders (and/or repetitions), these moments describe the coarse image information and LOW amplitudes should not be modified enough, since this modification will be visible to the final watermarked image. For the case of LOW orders (and/or repetitions) and HIGH amplitudes, more modification could be applied, since these moments carry enough image’s content and, therefore, are able to hide more watermark information. Finally, the HIGH orders (and/or repetitions) (these moments describe the fine-image information) can be modified enough, since this modification will not be very visible.
Based on the above knowledge and considering that all the rules corresponding to the possible combinations of the system’s inputs/output could be implemented, it is decided to define the most obvious ones, avoiding in this way to include redundant rules defined as follows:
Rule 1: if order (p) is LOW and repetition (q) is LOW and amplitude ( \(| {M_{pq} } |\) ) is LOW then delta ( \(\varDelta \) ) is LOW
Rule 2: if order (p) is LOW and repetition (q) is LOW and amplitude ( \(| {M_{pq} } |\) ) is HIGH then delta ( \(\varDelta \) ) is MEDIUM
Rule 3: if order (p) is HIGH and repetition (q) is HIGH and amplitude ( \(| {M_{pq} } |\) ) is LOW then delta ( \(\varDelta \) ) is MEDIUM
Rule 4: if order (p) is HIGH and repetition (q) is HIGH and amplitude ( \(| {M_{pq} } |\) ) is HIGH then delta ( \(\varDelta \) ) is HIGH
There are several benefits of using a well-defined knowledge-based fuzzy inference system for deriving the appropriate quantization step for each moment coefficient. First of all, the designed FIS can provide the dither modulation with the appropriate quantization steps independent of the image’s content, since images with common moments will share the same quantization strengths. Moreover, the incorporation of knowledge easily interpreted and defined by humans gives the advantage to process the outcomes or even to adjust this knowledge according to the problem’s demands.
Genetic optimization
The proposed fuzzy inference system includes some configuration parameters that have to be optimally tuned for the system to behave appropriately. These are the three parameters that define each triangular membership function used to describe the system’s input/output variables, as illustrated in Fig. 6.
Considering that each input/output is described by three membership functions (Fig. 5), the number of 4 (input/output variables) \(\times \) 3 (membership functions) \(\times \) 3 (parameters) \(=\) 36 total parameters have to be configured. Moreover, the tuning of these parameters has to be performed in the direction of a high quality and a robust-to-attacking conditions watermarked image.
For this purpose, a simple genetic algorithm is used to optimize the set of membership functions’ parameters, in terms of watermarking performance. Genetic Algorithms (GAs) have played a major role in many applications of the engineering science, since they constitute a powerful tool for optimization. A simple genetic algorithm is a stochastic method that performs searching in wide search spaces, depending on some probability values that mimic the evolutionary process that characterizes the evolution of living organisms [37]. Due to the above reasons, GA has the ability to converge to the global minimum or maximum, depending on the specific application and to skip possible local minima or maxima [38], respectively.
The structure of the ith algorithm’s chromosome is defined as:
where \(\{ {f_{0}^{k} ,f_{1}^{k} ,f_{2}^{k} } \}, k=1,2,3,\ldots ,12\) are the three configuration parameters of the kth membership function.
Furthermore, the fitness function (F) which is used to evaluate the appropriateness of each candidate solution is defined as:
where T is the number of attacks encountered in the procedure, SF\(_{\mathrm {1}}\), SF\(_{\mathrm {2}}\) are scaling factors equal to 0.1 and 1, respectively, BER\(_{j}\) is the BER of the jth attacked image and PSNR\(_{\mathrm {target}}\) is a desired PSNR value equal to 40. The incorporation of the target PSNR transforms the optimization to a constrained procedure to ensure a minimum of image quality that must be acquired.
Experimental study
A set of experiments has been arranged to investigate the performance of the proposed watermarking scheme. As a matter of fact, specific software has been developed in the MATLAB environment, while all experiments were executed in an Intel i5 3.3 GHz PC with 8 GB RAM. Moreover, the three benchmark images of 256 \(\times \) 256 pixels size depicted in Fig. 7 were selected to participate in all the watermarking experiments.
The robustness of the proposed methodology will be analyzed by applying some well-known attacks using the Stirmark benchmark [39]. More precisely, the applied attack types are: median filtering (2 \(\times \) 2, 4 \(\times \) 4, 6 \(\times \) 6, 8 \(\times \) 8—window size), Additive White Gaussian Noise—AWGN (5, 10, 15, 20 %) and JPEG compression (\(Q=5\), 10, 15, 20, 40 %). It is noted that only signal processing attacks have been selected since the geometric attacks (rotation, scaling) can be easily handled with a pre-processing step of image normalization [40] or by incorporating geometric invariances to the moments computation [41].
Experiments configuration
The settings of the applied genetic algorithm are the same for all the experiments and are presented in the following Table 1.
Although the proposed methodology is applicable to any moment family, the Tchebichef (TMs) [17] and Krawtchouk (KMs) [18] discrete moments will be considered herein, since both of them show a remarkable watermarking performance [22–28]. The main characteristics of the used moment families according to (1) are presented in Table 2.
It is worth noting that during the optimization stage the range of each system’s input/output has to be defined to avoid the selection of unreliable solutions, by adding the so-called boundary constraints to the optimization procedure. Therefore, the ranges of the input/outputs are set to \(p:[0,\sqrt{L}-1] \), \(q:[0,\sqrt{L}-1]\), \(| {M_{pq} } |:[0,A_{\max } ]\) and \(\Delta :[0,\Delta _{\max } ]\), where L is the message length, \(A_{\max }\) is the maximum moment magnitude which depends on the image’s content and \(\Delta _{\max }\) is the maximum quantization step which is equal to 200 and 10 for KMs and TMs, respectively.
Simulations
The watermarking performance of the proposed methodology is measured using the PSNR quality index and the Bit Error Rate (BER) [7] at the detectors’ side, under various attacking conditions. The experiments were carried out for three different message bit lengths {100 bit, 300 bit, 500 bit} to analyze in depth the relation between the embedding strength and the frequency components of the image.
Moreover, an additional performance index (Reduction Factor—RF) is considered herein, to measure the achieved reduction of the mean BER, when the “Proposed” (PR) watermarking technique is used instead of the “Standard” (ST) (this with a single and uniform quantization step \(\Delta )\), defined as:
Finally, it has to be noted to fairly compare the two methodologies, each method is calibrated and a desired watermarked quality (PSNR \(=\) 40 dB) is achieved.
The corresponding results are summarized in Tables 3, 4 and 5, for the case of the Krawtchouk moments and for the Lena, Bike and Lighthouse images, respectively.
By examining the detection results of Tables 3, 4 and 5, it is obvious that the usage of a single quantization step (\(\Delta )\) is not the best choice, since it does not guarantee that each moment coefficient will be modified according to its capability to carry the inserted information. On the contrary, the usage of different quantization steps, through the proposed methodology seems to distribute the watermark information to the appropriate coefficients, by improving significantly the detection performance without sacrificing the quality of the watermarked image.
More precisely, the reduction of the mean BER is significant for the 100 bit length, which is 18 % on average for the three images, while it is reduced to 7 and 5 % for the 300 and 500 bits message length, respectively. Furthermore, a close look at the partial BER values of each attack type leads to the conclusion that the usage of variable quantization steps enforces the robustness of the watermarking process to the JPEG compression more than the other two attacks. This result is consistent with the principles of the compression theory, according to which the high-frequency components enclosed into the higher message’s coefficients are significantly affected and thus the added information will be more distorted than in the lower ones. Therefore, by applying appropriate quantization steps, the amount of information inserted into those coefficients that will be compressed more can be increased to be more robust during JPEG compression attack.
Additionally, the achieved gain is reduced with the increase of the message length. The greater the length of the message to be embedded, the higher order moment coefficients are needed to hide the information. However, as the moment order increases the magnitudes of the coefficients are decreased and, therefore, the coefficients are more sensitive to the attacks. However, the usage of different quantization steps to those high-order coefficients can adaptively control the amount of information the coefficients carry, according to their magnitude.
The aforementioned outcomes are also justified by the examination of the selected quantization steps in each case. The quantization steps for the case of the bicycle image (this with the highest performance) are illustrated in Fig. 8. In this figure, the dashed line corresponds to the single step assigned to all moment coefficients and the solid one to those derived by applying the proposed methodology.
The plots of Fig. 8 show that a more sophisticated assignment (non-blind) of the quantization steps to the moment coefficients, aiming that the inserted information is proportional to the capacity of the coefficients, can lead to more robust and of the same quality watermarked images.
The same experiments were carried out using the Tchebichef moments (TMs) instead of the KMs and the corresponding results are reported in Tables 6, 7 and 8.
It is worthwhile mentioning that the magnitudes of the TMs are significantly lower than those of the KMs and, therefore, the used quantization steps are smaller. This reduced range makes the process of finding the most appropriate quantization steps a hard task, since more coefficients need to have different strengths.
The detection results for the case of the TMs are even better than those of the KMs, with the mean BER being reduced by 32 % for the 100 bit message length on average for the three images, while this reduction is 20 and 16 % for the 300 and 500 bits message length, respectively. This outperformance is due to the inherent global nature of the TMs that makes them more robust to any non-local attack. In addition to the low detection errors for the JPEG attack, the distortion of the watermarked images from the Median filter and the AWGN are also better handled with the proposed methodology.
The selected quantization steps for the case of the Lighthouse image (this with the highest performance) are depicted in Fig. 9.
The above figures show that an increase to the embedding strength of the higher frequency coefficients does not affect the quality of the watermarked image, due to the more uniform compactness of the TMs, making the extraction procedure more robust to the attacks. However, this is achieved by simultaneous reduction of the inserted information into the lower coefficients.
Again, the main conclusion of the aforementioned study is that all coefficients do not show the same capabilities to hide the same amount of information and, therefore, the standard approach to use a single quantization step is somehow superficial. Instead, the selection of the appropriate quantization step for each coefficient, depending on the image’s content type, can lead to more robust behaviors preserving the high quality of the watermarked images. To this end, the proposed methodology constitutes an efficient way to assign the appropriate quantization steps to the moment coefficients leading to considerable performance.
Conclusion
A novel watermarking methodology, highly robust on signal processing attacks and with high-quality watermarked images was presented in the previous sections. The adaptive nature of the proposed moment-based watermarking method, owing to the optimized fuzzy inference systems embodying prior knowledge, controls the amount of watermark information each moment coefficient is capable to carry.
The main advantage of the introduced method is the ability to incorporate prior knowledge regarding the suitability of the quantization steps for each moment coefficient, by means of IF–THEN fuzzy rules. The designed fuzzy inference system is applied in an optimized framework where its membership functions are optimally defined, in terms of imperceptibility and robustness of the entire watermarking procedure.
The experiments have justified the initial theoretical claims regarding the need for different quantization steps for each moment coefficient. The improvements to the achieved detection performance are remarkable, since the mean BER is reduced up to 32 % for the case of 100 bit message length, while this improvement being 20 % and 16 % for 300 and 500 bits, for the case of TMs, respectively. This improvement is quite lower if KMs are used instead of TMs, but is still satisfactory with a mean BER reduction of 18, 7 and 5 % for the three different message lengths, respectively.
Although the proposed methodology reveals a significant performance, there are some more steps that could be scheduled for future work to further increase the watermarking performance. One possible issue that needs to be further investigated is the usage of more than four IF–THEN fuzzy rules, so the relations between the system’s input/output are defined more accurately. However, attention should be paid at this point to avoid the rapid increase of the rules, since this could cause the weakening of the generalization capabilities of the FIS system. Finally, since the proposed fuzzy dither modulation is independent of the coefficients used to embed the watermark information, it will be interesting to study its performance with other types of moments or even other coefficients (transformations) such as DCT, DWT and SVD.
References
Zheng D, Liu Y, Zhao J, Saddik AE (2007) A survey of RST invariant image watermarking algorithms. In: ACM computing surveys, vol 39(2), article 5
Liu R, Tan T (2002) An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans Multimed 4(1):121–128
Barni M, Bartolini F, Cappellini V, Piva A (1998) A DCT-domain system for robust image watermarking. Signal Process 66(3):357–372
Kang X, Huang J, Shi YQ, Lin Y (2003) A DWT-DFT composite watermarking scheme robust to both affine transform and JPEG compression. IEEE Trans Circuits Syst Video Technol 13(8):776–786
Jayalakshmi M, Merchant SN, Desai UB (2006) Digital watermarking in contourlet domain. In: 18th international conference on pattern recognition (ICPR), pp 861–864
Wang XY, Wang CP, Yang HY, Niu PP (2013) A robust blind color image watermarking in quaternion Fourier transform domain. J Syst Softw 86(2):255–277
Tsougenis ED, Papakostas GA, Koulouriotis DE, Tourassis VD (2012) Performance evaluation of moment-based watermarking methods: a review. J Syst Softw 85(8):1864–1884
Chen B, Wornell GW (2001) Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans Inf Theory 47(4):1423–1443
Papakostas GA (2014) Over 50 years of moments and moment invariants. In: Papakostas GA (ed) Moments and moment invariants—theory and applications, GCSR, vol 1, pp 253–274. Science Gate Publishing. doi:10.15579/gcsr.vol1.ch1
Papakostas GA, Boutalis YS, Karras DA, Mertzios BG (2009) Pattern classification by using improved wavelet compressed Zernike moments. Appl Math Comput 212(1):162–176
Papakostas GA, Boutalis YS, Karras DA, Mertzios BG (2007) A new class of Zernike moments for computer vision applications. Inf Sci 177(13):2802–2819
Papakostas GA (2015) Improving the recognition performance of moment features by selection. In: Stanczyk U, Jain LC (eds) Feature selection for data and pattern recognition. Studies in computational intelligence, vol 584, pp 305–327. Springer, New York
Kautsky J, Flusser J (2011) Blur invariants constructed from arbitrary moments. IEEE Trans Image Process 20(12):3606–3611
Mukundan R, Ramakrishnan KR (1998) Moment functions in image analysis. World Scientific Publishing, Singapore
Papakostas GA, Boutalis YS, Karras DA, Mertzios BG (2010) Efficient computation of Zernike and pseudo-Zernike moments for pattern classification applications. Pattern Recognit Image Anal 20(1):56–64
Hosny KM (2007) Exact Legendre moment computation for gray level images. Pattern Recognit 40(12):3597–3705
Mukundan R, Ong SH, Lee PA (2001) Image analysis by Tchebichef moments. IEEE Trans Image Process 10(9):1357–1364
Yap P-T, Paramesran R, Ong S-H (2003) Image analysis by Krawtchouk moments. IEEE Trans Image Process 12(11):1367–1377
Alghoniemy M, Tewfik AH (2000) Image watermarking by moment invariants. In: Proceedings of IEEE international conference on image processing, pp 73–76
Kim HS, Lee HK (2003) Invariant image watermark using Zernike moments. IEEE Trans Circuits Systems Video Technol 13(8):766–775
Xin Y, Liao S, Pawlak M (2007) Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recognit 40(12):3740–3752
Deng C, Gao X, Li X, Tao D (2009) A local Tchebichef moments-based robust image watermarking. Signal Process 89(8):1531–1539
Wang XY, Yang YP, Yang HY (2010) Invariant image watermarking using multi-scale Harris detector and wavelet moments. Comput Electr Eng 36(1):31–44
Papakostas GA, Tsougenis ED, Koulouriotis DE, Tourassis VD (2011) On the robustness of Harris detector in image watermarking attacks. Optics Commun 284(19):4394–4407
Yang HY, Wang XY, Niu PP, Wang AL (2015) Robust color image watermarking using geometric invariant quaternion polar harmonic transform. In: ACM transactions on multimedia computing communications and applications, vol 11(3), article no. 40
Tsougenis ED, Papakostas GA, Koulouriotis DE, Karakasis EG (2014) Adaptive color image watermarking by the use of quaternion image moments. Expert Syst Appl 41(14):6408–6418
Wang XY, Niu PP, Yang HY, Wang CP, Wang AL (2014) A new robust color image watermarking using local quaternion exponent moments. Inf Sci 277:731–754
Tsougenis ED, Papakostas GA (2014) Should we consider adaptivity in moment-based image watermarking? In: Papakostas GA (ed) Moments and moment invariants—theory and applications, GCSR, vol 1, pp 3–32, Science Gate Publishing. doi:10.15579/gcsr.vol1.ch11
Papakostas GA, Tsougenis ED, Koulouriotis DE, Tourassis VD (2014) Moment-based local image watermarking via genetic optimization. Appl Math Comput 227:222–236
Voloshynovskiy S, Deguillaume F, Pun T (1999) A stochastic approach to content adaptive digital image watermarking. Int Workshop Inf Hiding LNCS 1768:212–236
Qi H, Zheng D, Zhao J (2008) Human visual system based adaptive digital image watermarking. Signal Process 88(1):174–188
Podilchuk CI, Zeng W (1998) Image-adaptive watermarking using visual models. IEEE J Sel Areas Commun 16(4):525–539
Delaigle JF, Vleeschouwer CD, Macq B (1998) Watermarking algorithm based on a human visual model. Signal Process 66(3):319–335
Tsougenis ED, Papakostas GA, Koulouriotis DE, Tourassis VD (2013) Towards adaptivity of image watermarking in polar harmonic transforms domain. Optics Laser Technol 54:84–97
Papakostas GA, Koulouriotis DE, Karakasis EG (2010) Computation strategies of orthogonal image moments: a comparative study. Appl Math Comput 216(1):1–17
Guillaume S (2001) Design fuzzy inference systems from data: an interpretability-oriented review. IEEE Trans Fuzzy Syst 9(3):426–443
Holland JH (2001) Adaptation in natural and artificial systems, 6th edn. MIT Press, New York
Coley DA (2001) An introduction to genetic algorithms for scientists and engineers. World Scientific Publishing, Singapore
Petitcolas FAP, Anderson RJ, Kuhn MG (1998) Attacks on copyright marking systems. In: Second international workshop on information hiding, LNS, vol 1525, pp 218–238
Zhang L, Xiao W, Qian G, Ji Z (2007) Rotation scaling and translation invariant local watermarking technique with Krawtchouk moments. Chin Optics Lett 5(1):21–24
Zhang H, Shu H, Coatrieux G, Zhu J, Wu QMJ, Zhang Y, Zhu H, Luo L (2011) Affine Legendre moment invariants for image watermarking robust to geometric distortions. IEEE Trans Image Process 20(8):2189–2199
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Papakostas, G.A., Tsougenis, E.D. & Koulouriotis, D.E. Fuzzy knowledge-based adaptive image watermarking by the method of moments. Complex Intell. Syst. 2, 205–220 (2016). https://doi.org/10.1007/s40747-016-0023-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40747-016-0023-7