Abstract
The available studies on vulnerability evaluation of Supply Chain Networks (SCNs) oversimplify the availability of entities during disruptive events by classifying them into only two categories of “operational” and “not operational.” Yet, the literature has remained relatively silent on vulnerability analysis of SCNs in the case of capacity reduction. To sidestep this shortcoming, this paper develops an entropy-based method to quantify the vulnerability of SCNs to capacity reduction. This is achieved by measuring the flexibility inherent within the layout of SCNs, both at local and global levels. By performing simulation and sensitivity analyses, this paper predicts the impact of capacity reductions on the performance of SCNs. The results of our study favor the fact that incorporating more backups and increasing the capacity of various entities in the network reduces vulnerability and enhances the robustness of SCNs. The findings of this research may assist operations and supply chain managers in identifying the sensitive areas of SCNs, in turn facilitating the development of an effective risk management strategy to respond to disruptive events.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Supply Chain Networks (SCNs) face a myriad of disruptions, ranging from global pandemics such as SARS and COVID-19, geopolitical tensions, to natural disasters (Dwivedi et al., 2023; Zaoui et al., 2023). A notable recent challenge for SCNs is the semiconductor shortages impacting the automotive industry (Ramani et al., 2022). The automotive sector has grappled with these shortages due to a blend of factors such as supply chain complexities, the Russia–Ukraine conflict, and realignments in chip manufacturing, culminating in a global shortage of vehicles (Zarghami & Zwikael, 2024). The COVID-19 pandemic also spotlighted vulnerabilities in supply chains. For instance, the scarcity of intensive care beds in Daegu, South Korea, during the peak of the pandemic tragically resulted in patient fatalities (Emanuel et al., 2020). In the face of such events, entities within SCNs temporarily cease production or operate at partial capacity, resulting in supply and distribution reductions, whereby suppliers, manufacturers, distributors, and retailers operate at a reduced capacity, rather than complete closure.
There is continuing interest in the literature in evaluating the vulnerability of SCNs to disruptions. Available studies on vulnerability analysis of SCNs can be broadly fallen into five categories. The first focuses on reliability of SCNs, measuring the probability of entities functioning within SCNs during disruptions (Asadabadi & Miller-Hooks, 2020). The second assesses resilience, evaluating SCNs’ ability to sustain and recover from disruptions (Chowdhury et al., 2024). The third studies, robustness, emphasizing SCNs’ full capacity to supply products during disruptions (Zarghami & Dumrak, 2021b). The fourth category examines redundancy as an indicator of SCNs’ flexibility during disruptions (Kamalahmadi & Mellat Parast, 2017; Wadhwa & Rao, 2004). Lastly, the fifth category explores the impact of flexibility on various attributes of SCNs (Pandey et al., 2024; Varma et al., 2024). However, these studies often exhibit two major shortcomings.
First, while there is a growing emphasis on the role of structural properties of SCNs in addressing disruptions (Kiani Mavi et al., 2023 ), existing vulnerability analyses of SCNs predominantly focus on reliability, robustness, and resilience. They often overlook structural flexibility, which could provide insights into how SCNs adapt to disruptions. Second, the literature tends to oversimplify the availability of entities in SCNs during disruptive events by classifying them into only two categories: “operational” and “not operational” (Azad & Hassini, 2019). However, the literature has remained relatively silent on vulnerability analysis of SCNs in the case of capacity reduction. Indeed, recent examples of prolonged and varied reductions in the capacity of entities in SCNs caused by geopolitical conflicts in the Middle East and the Russia–Ukraine war have introduced unique disruptions to SCNs (Fukutomi, 2024; Xu et al., 2024). Without an understanding of how SCNs, particularly their structural flexibility, respond to capacity reductions, managers may develop ineffective strategies for managing challenges stemming from capacity reductions. This could potentially compromise the performance of SCNs.
This paper aims to address these research gaps by exploring the following question: “How can the vulnerability of supply chain networks to capacity reduction be assessed by considering their structural flexibility?” To achieve this, we introduce a novel method for evaluating the vulnerability of SCNs. The method developed herein incorporates two desirable features. First, it introduces for the first time an entropy-based flexibility index that reflects the reserve backup capacity of entities as the vulnerability-averse attribute of SCNs. Second, the proposed method allows the probabilistic nature of capacity reductions in SCNs to be integrally modeled within the network’s flexibility analysis. This approach leads to the development of a network flexibility index derived from information entropy, which measures the potential contribution of a collaborative link between two entities to the overall flexibility of an SCN. We then develop a method to quantify the overall availability of SCNs based on the availability-wise interdependencies among the entities. Finally, an attempt is made to yield a comprehensive vulnerability index as a function of network flexibility and network availability.
The organization of this paper is as follows: we proceed with an overview of the literature on vulnerability analysis of SCNs. Following this, we introduce the notation and preliminary definitions essential for developing our proposed method. We then present the development of the vulnerability evaluation method. The paper showcases the application of this method on an illustrative SCN, supplemented by simulation and sensitivity analyses and a discussion of the results. Subsequently, we present the research contributions and managerial implications. Finally, the paper wraps up by summarizing the findings and proposing potential avenues for future research.
Literature Review
In recent years, the vulnerability-averse behavior of SCNs has been the subject of considerable research. Most of this has focused on quantifying various qualitative attributes of SCNs as indicators for the evaluation of vulnerabilities, with this work falling into one of five categories.
The first category includes literature that deals with the reliability of SCNs as the probability that a given entity in an SCN remains operational and functions satisfactorily over time (Gunawan et al., 2017). In this context, Quigley and Walls (2007) proposed a reliability allocation model for SCNs by considering reliability targets across a supply chain. Hsu and Li (2011) developed a reliability evaluation model to assess the performance of SCNs under demand fluctuations. Lin et al., (2017) measured the probability of providing a sufficient supply of commodities to evaluate the reliability of the networks. Asadabadi and Miller-Hooks (2020) adopted game theoretic optimization models for reliability evaluation of logistics in SCNs during disruptive events.
Reliability-based studies predominantly center on the individual functionality of entities within SCNs, overlooking the network’s structural properties. This limited perspective often misses vulnerabilities stemming from disruptions that impact multiple nodes or links concurrently. Such an approach may not fully capture the interconnected nature of SCNs, where the failure of one node or link can trigger cascading effects throughout the entire network.
The second category includes articles that study the resilience of a disrupted SCN to assess its ability to sustain functionality and recover from disruptions (Dwivedi et al., 2023; Sharma et al., 2023). In this vein, Zhao et al., (2011) quantified the resilience of SCNs by adopting degree centrality. Berle et al., (2011) suggested a resilience framework for addressing the vulnerability of maritime supply chains to disruption risks. Carvalho et al., (2012) evaluated the resilience of SCNs when disruptive events strike by performing a simulation analysis. Kim et al., (2015) assessed the resilience of SCNs to unexpected disruptions by using betweenness and degree centrality indices. Beheshtian et al., (2017) utilized the concept of network resilience to measure the level of resilience in motor-fuel SCNs. Bottani et al., (2019) mapped a food supply chain to a graph of nodes and links and employed the Ant Colony Optimization (ANO) algorithm for the design of resilient SCNs. Dixit et al., (2020) assessed the resilience of SCNs by analyzing various structural properties of the network. Moghadasi et al., (2022) devised a scenario-based approach to evaluate the resilience of hardware supply chains within electric vehicle charging networks against disruptive events.
Resilience-based studies primarily focus on the network’s ability to recover and maintain functionality after disruptions. While resilience is crucial, these studies often miss the nuances of capacity reduction within SCNs. For example, a network might show resilience to a partial reduction in a manufacturer’s capacity but could be highly vulnerable if the manufacturer shuts down completely. As a result, resilience-based approaches might not accurately capture the SCN’s vulnerability to capacity reduction scenarios.
The third category includes papers that address the robustness of an SCN. These papers define such robustness as an SCN’s capability to maintain the required level of product supply in the face of disruptive events. Within this stream of research, Dong (2006) developed a graph theory-based robustness index by taking into account the degree of nodes as well as the indirect paths between nodes. Han and Shin (2016) analyzed the structural robustness of SCNs by employing graph theory quantities such as average path length and nodal degree. Liu et al., (2018) adopted a robustness analysis approach and performed centrality analysis to identify structural vulnerabilities in the maritime supply chain. Zhao et al., (2019) conducted a topological-based simulation analysis to explore the level of robustness exhibited by SCNs when confronted with disruptions. Zhou et al., (2019) calculated the reciprocal shortest paths between nodes in an airport logistics network, followed by a simulation analysis to assess the robustness of SCNs. Zarghami and Dumrak (2021b) quantified the vulnerability of SCNs by measuring the robustness of the global maritime network. The authors employed centrality analysis to measure multiple structural properties of the network, including closeness, eigenvector, and betweenness centrality. The degree of inequality in the distribution of centrality measures was employed to quantify the network’s overall vulnerability.
The usual approach in studying the robustness of SCNs to disturbances is to analyze the structural properties of these networks by performing network analysis. The prevailing approach in network analysis is to measure the criticality and importance of network elements by adopting centrality indices such as degree, closeness, and betweenness centrality. However, these measures do not differentiate between different nodal attributes of a network. This poses a real conundrum for SCNs where there exist several distinctive node categories such as suppliers, manufacturers, distributors, and retailers.
The fourth category includes literature that studies the performance of SCNs during disruptions by evaluating the redundancy as an indicator of the flexibility of these networks. In light of this, the extant literature attempts to explore the potential of backup supply sources to smooth the operation of disrupted networks. Though limited in number, the following recent articles are notable examples. Kamalahmadi and Mellat Parast (2017) evaluated the efficacy of three flexibility strategies–backup suppliers, protected suppliers, and pre-positioning inventory—in mitigating the negative impact of disruptive events. Tan et al., (2019) evaluated the global flexibility of SCNs by taking into account relationships between materials and products as well as the interrelationships between plants in an SCN. Pavlov et al., (2019) proposed an optimization model for network flexibility by paying simultaneous attention to supply and structural dynamics.
While studies in this category offer valuable insights into how flexibility can reduce vulnerabilities in SCNs to disruptions, they often overlook the structural vulnerabilities that can amplify the impact of these disruptions. Specifically, these studies rarely delve into the interdependencies between primary and backup entities within an SCN. Understanding such interdependencies is crucial, as they play a pivotal role in enhancing the network’s flexibility. This flexibility, in turn, can mitigate the adverse effects of disruptive events.
The fifth category predominantly examines the relationship between different attributes, particularly focusing on the influence of flexibility on various attributes of SCNs. For instance, Agrawal et al., (2023) surveyed supply chain managers in India and identified a statistically significant positive relationship between flexibility and the resilience and robustness of SCNs. Pandey et al., (2024) delved into how flexibility can shorten response times during disruptions, thereby bolstering resilience. Abdi et al., (2024) investigated the optimal allocation of backup entities in SCNs and its impact on network flexibility. Their findings suggest that this optimal allocation cannot only bolster the flexibility of these networks but also enhance their reliability.
Despite a broad understanding of how flexibility relates to other attributes of SCNs, this category falls short in directly assessing vulnerability. More explicitly, studies in this category often infer vulnerability indirectly through flexibility, robustness, reliability, or resilience measures without directly examining how susceptible the networks are to disruptions.
Table 1 offers an overview of prior research focusing on vulnerability analysis within SCNs.
Notation and Preliminary Definitions
Notation
This paper employs the following symbols.
\(S\) | A set representing suppliers |
\(M\) | A set representing manufacturers |
\(D\) | A set representing distributors |
\(R\) | A set representing retailers |
\(C\) | A set representing customers |
\(G = \left( {V,E} \right)\) | A graph representing an SCN with a set of nodes, \(V\), and a set of edges,\(E\) |
\(e_{i}\) | A link in SCNs |
\(S^{*}\) | A singleton set representing suppliers |
\(M^{*}\) | A singleton set representing manufacturers |
\(D^{*}\) | A singleton set representing distributors |
\(R^{*}\) | A singleton set representing retailers |
\(C^{*}\) | A singleton set representing customers |
\(K^{*} = \left( {V^{*} ,E^{*} } \right)\) | K-entity spanning tree of an SCN with a set of nodes, \(V^{*}\), and links,\(E^{*}\) |
\({\text{KC}}^{*}\) | K-entity co-spanning tree of an SCN |
\(H\) | Entropy of a distribution |
\(P\) | A set of probabilities |
\(F_{SN} \left( {e_{i} } \right)\) | Flexibility index of link \(e_{i}\) |
\(n\) | Number of entities in an SCN |
\(m\) | Number of K-entity spanning trees in an SCN |
\(n_{{{\text{KC}}^{*} }} \left( {e_{i} } \right)\) | Number of outcomes that link \(e_{i} { }\) is part of \(KC^{*}\) |
\(q\) | Cardinality of the links set in a K-entity co-spanning tree |
\(n_{{KC^{*} }}\) | Total number of the K-entity co-spanning trees of G |
\(H_{E}\) | Entropy of a set of flexibility indices |
\(H_{{E,{\text{max}}}}\) | Maximum entropy of a set of flexibility indices |
\({\text{FI}}_{{{\text{SCN}}}}\) | Network flexibility index |
\(X_{i}\) | A random variable representing the status of an entity |
\(\emptyset \left( {X_{{i{\text{S}}}} ,X_{{i{\text{M}}}} ,X_{iD} ,X_{iR} } \right)\) | Structure function of a K-entity spanning tree |
\(A_{{K_{i}^{*} }}\) | Availability of a K-entity spanning tree |
\(a_{i}\) | Availability of a K-entity spanning link |
\({\text{AI}}_{{{\text{SCN}}}}\) | Network availability index |
\({\text{VI}}_{{{\text{SCN}}}}\) | Network vulnerability index |
Preliminary Definitions
We first define \({ }S = \left\{ {s_{i} |i = 1,2, \ldots ,s_{n} } \right\}\), \(M = \left\{ {m_{i} |i = 1,2, \ldots ,m_{n} } \right\}\), \(D = \left\{ {d_{i} |i = 1,2, \ldots ,d_{n} } \right\}\), \(R = \left\{ {r_{i} |i = 1,2, \ldots ,r_{n} } \right\}\), and \(C = \left\{ {c_{i} |i = 1,2, \ldots ,c_{n} } \right\}\) as sets representing suppliers, manufacturers, distributors, retailers, and customers in an SCN, respectively. We then provide the following definitions used for crafting the proposed method.
Graph A graph \(G = \left( {V,E} \right) E = \left\{ {e_{i} |i = 1,2, \ldots ,n} \right\}\) is a mathematical representation of an SCN that contains a set of nodes, denoted by \(V\), an \(E\) d a set of distinct edges, denoted by E. The sets \(V\) and E can \(V = S \cup M \cup D \cup R \cup C\) be expressed as:
where \(V\) is the union of the set of various entities in an SCN, and \(e_{i}\) represents an edge in the network, which is identified with a pair of nodes from \(V\).
Directed graph A directed graph is a graph where edges possess a defined direction, indicating a flow or connection from one node to another. In this work, the edges in the associated graph of an SCN represent the material flow. Thus, we map an SCN into a directed graph where edges connect two entities asymmetrically.
Cardinality The cardinality of a set represents the count of elements within the set.
Singleton set A singleton set is a set that has exactly one element; in other words, the cardinality of a singleton set is 1.
K-entity spanning tree Let \(S^{*} \subset S\), \(M^{*} \subset M\), \(D^{*} \subset D\), \(R^{*} \subset R\), and \(C^{*} \subset C\) be the singleton sets of various entities in an SCN. A K-entity spanning tree of an SCN is defined as a tree-shape subgraph denoted by \(K^{*} = \left( {V^{*} ,E^{*} } \right)\), where \(E^{*}\) is a set that includes the minimum possible number of distinct links that ensures the connectedness of \(K^{*}\), and \(V^{*}\) is obtained as follows:
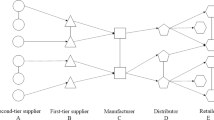
In simple terms, a K-entity spanning tree contains one primary entity from each set of suppliers, manufacturers, distributors, retailers, and customers. For enhanced visualization of this concept, Fig. 1 schematically depicts an example of a K-entity spanning tree.
K-entity co-spanning tree If \(K^{*} = \left( {V^{*} ,E^{*} } \right)\) is a K-entity spanning tree of graph \(G = \left( {V,E} \right)\); then, \({\text{KC}}^{*} = \left( {V - V^{*} ,E - E^{*} } \right)\) is a K-entity co-spanning tree of \(G\). Intuitively, each K-entity co-spanning tree contains the entities that can be used as backups when the primary entities in a K-entity spanning tree are unavailable.
K-entity spanning link A link in a K-entity spanning tree is called a K-entity spanning link.
K-entity co-spanning link We call the links in a K-entity co-spanning tree K-entity co-spanning links.
For clarity, Fig. 2 illustrates a representative SCN with seven nodes representing entities, and eight edges (\(e_{i}\)) representing the connection between entities. In this figure, the elements of set \(E\) are represented by solid lines, while the elements of set \(E^{*}\) are depicted by dashed lines.
Parallel entity configuration We define a parallel entity configuration as a network layout through which the network operates if, at any given time, one of the K-entity spanning trees operates. In other words, a parallel entity configuration represents redundancies in the network. Figure 3 graphs the conceptual sketch of a parallel entity configuration. To put it simply, as shown in Fig. 3, a parallel entity configuration contains a set of primary entities (\(s_{i} \in S\),\(m_{j} \in M\),\(d_{k} \in D\), \(r_{l} \in R\)), each of which is, respectively, supported by a number of backup entities from the sets \(S - \left\{ {s_{i} } \right\}\), \(M - \left\{ {m_{j} } \right\}\), \(D - \left\{ {d_{k} } \right\}\), \(R - \left\{ {r_{l} } \right\}\) that can be used as substitutes for the primary entities when a disruptive event occurs.
Information entropy The concept of information, or Shannon, entropy is widely used in different domains, serving as a metric for assessing heterogeneity and uncertainty. Information entropy is defined for a set of probabilities \(P = \left\{ {p_{i} |i = 1,2, \ldots ,n\} } \right.\) as (Sakhteh et al., 2024):
where H represents the entropy of distribution, and \(n\) denotes the total number of possible outcomes.
Proposed Method
To address the research question: “How can the vulnerability of supply chain networks to capacity reduction be assessed by considering their structural flexibility?”, we integrate two theories: graph theory and reliability theory. Our goal is to expand the application of the co-spanning tree technique, a tool from graph theory, beyond its traditional boundaries. With this aim, we apply the co-spanning tree technique to SCNs, a domain where it has not previously been utilized. Further, we utilize a tool from reliability theory known as the Availability Block Diagram (ABD) (Zarghami et al., 2020) to create an index that measures the impact of capacity reduction on SCN performance. While reliability theory has been widely applied in supply chain management, employing the ABD specifically for this purpose is a novel approach. This method offers a streamlined approach to evaluating vulnerability in the face of capacity reduction.
The proposed method is developed in three steps. In Step 1, we measure the level of flexibility in SCNs. Step 2 generates an index—the “network availability index”—to quantify the impacts of capacity reduction on the performance of SCNs. In Step 3, we define a vulnerability index, which is a function of network flexibility and network availability. Table 2 provides an overview of the procedural steps undertaken in this research, outlining the objective and methodology for each step.
Step 1—Measuring Network Flexibility
We first define a link-based statistical measure based on the concept of link flexibility in SCNs. The flexibility index of link \(e_{i}\) is defined as the probability that the link is part of a K-entity co-spanning tree of the SCN. That is:
where \(F_{SN} \left( {e_{i} } \right)\) is the flexibility index of link \(e_{i}\).
\(\Pr \left( {e_{i} \in E - E^{*} } \right)\) is the probability that \(e_{i}\) is a K-entity co-spanning link.
Let \({\rm{KC}}^{{\rm{*}}} = \left\{ {{\rm{KC}}_{{\rm{1}}}^{{\rm{*}}} {\rm{,KC}}_{{\rm{2}}}^{{\rm{*}}} {\rm{, \ldots ,KC}}_{{\rm{m}}}^{{\rm{*}}} } \right\}\) be the set of all K-entity co-spanning trees of an SCN. The flexibility index of link \({e}_{i}\) can then be obtained by calculating the following fraction:
where \({\text{F}}_{SN} \left( {e_{i} } \right)\) is the flexibility index of link \(e_{i}\), \(n_{{{\text{KC}}^{*} }} \left( {e_{i} } \right)\) is the number of outcomes in which this link is part of \({\text{KC}}^{*}\), \(n_{{{\text{KC}}^{*} }}\) represents the total number of K-entity co-spanning trees of G, \(q\) is the cardinality of the links set in a K-entity co-spanning tree, and \(qn_{{{\text{KC}}^{*} }}\) denotes the total number of K-entity co-spanning links in the SCN. It should be noted that \(q\) is a constant value, which can be obtained from the following equation:
where n represents the total number of entities within the SCN, and \(n_{{V^{*} }}\) represents the number of nodes (entities) in the set \(V^{*}\) in Eq. (3).
Numerically, \(F_{SN} \left( {e_{i} } \right)\) falls within the range \([0,1]\), where the lower extreme value,\(F_{SN} \left( {e_{i} } \right) = 0\), denotes the existence of a link in an SCN whose removal results in network disconnection. On the other hand, the upper extreme value, \(F_{SN} \left( {e_{i} } \right) \to 1\) (though not practically achievable), represents a highly redundant link, the removal of which seldom disrupts the network. A higher value of \(F_{SN} \left( {e_{i} } \right)\) signifies greater flexibility, while a lower value denotes reduced flexibility.
For an SCN with \(n\) links and \(n_{{{\text{KC}}^{*} }}\) K-entity co-spanning trees with cardinality of q, we arrive at:
Equation (8) can be written as:
Since \(F_{SN} \left( {e_{i} } \right)\) is defined as the ratio of the number of outcomes where link \(e_{i}\) is part of a K-entity co-spanning tree to the total number of K-entity co-spanning trees; the sum of the link flexibility indices in an SCN equals 1. This implies that if there are only a few links with exceptionally high flexibility indices, the frequency of other links appearing in K-entity co-spanning trees will decrease. From a flexibility standpoint, it is advantageous when the values of \(F_{SN} \left( {e_{i} } \right)\) are uniformly distributed. Intuitively, a uniformly distributed SCN indicates the presence of multiple alternative collaborative paths within the network, enhancing its flexibility. This concept resonates with the principle of maximum entropy, where greater uniformity in links participating in K-entity co-spanning trees results in higher information entropy. Thus, we propose information entropy as a method for assessing the overall flexibility of SCNs.
Let \(E = \left\{ {e_{i} |i = 1,2, \ldots ,n} \right\}\) be a set of links between various entities in an SCN and let \(F_{SN} \left( {e_{i} } \right)\) be the link flexibility index for entity \(i\). The set \(E\) is defined as:
where \(H_{E}\) is the information entropy of the probability distribution of \(\left\{ {F_{SN} \left( {e_{i} } \right)} \right\}\), and \(n\) is the number of entities in the SCN.
For an SCN with \(n\) entities, \(H_{E}\) is at its maximum when all link flexibility indices are equal. That is:
Substituting Eq. (11) into Eq. (10) gives:
where \(H_{{E,{\text{max}}}}\) is the maximum entropy of the probability distribution of \(\left\{ {F_{SN} \left( {e_{i} } \right)} \right\}\).
We now define the network flexibility index of an SCN, parametrized by \({\text{ FI}}_{{{\text{SCN}}}}\), as the fractional deviations between the entropy of a set \(F_{SN} \left( {e_{i} } \right)\) and its maximum achievable value. This relationship is represented by the following mathematical expression:
where the numerator represents the entropy of the probability distribution of \(\left\{ {F_{SN} \left( {e_{i} } \right)} \right\}\), and the denominator serves as a normalization factor ensuring that \({\text{FI}}_{{{\text{SCN}}}}\) ϵ[0,1].
Conceptually, \({\text{FI}}_{{{\text{SCN}}}}\) indicates the reserve capacity of an SCN, where a higher value of \({\text{FI}}_{{{\text{SCN}}}}\) denotes lower vulnerability due to the existence of redundant entities.
Step 2—Developing the Network Availability Index
We now use the Availability Block Diagram (ABD) as an analytical method to assess the impacts of capacity reduction on the performance of SCNs. Availability in an ABD refers to the ability of each entity to function once disruptions occur (Rakas & Hecht, 2007). More specifically, the availability of an entity addresses a condition of its partial operation and therefore accounts for the reduction in its capacity. The availability value, denoted by \(a_{i}\), falls in the range \(\left[ {0,1} \right]\), where 0 implies complete shutdown, and 1 represents the normal operation of the entity.
An ABD graphically illustrates the availability performance requirements through various functional blocks. Each functional block represents an entity of an SCN, such as supplier, manufacturer, distributor, and retailer. Figure 4 depicts a schematic representation of an ABD. As shown, the functional blocks interconnected through both serial and parallel arrangements of entities, as well as K-entity spanning trees. The overall system availability can be assessed based on the availability of its constituent entities.
Let \(K_{i}^{* }\) be a given K-entity spanning tree of an SCN. The structure function of \(K_{i}^{* }\) is then defined as a binary function that dictates the status of \(K_{i}^{* }\) based on the status of each constituent entity. The status of each entity is represented by a random variable, which assumes a value of 1 if the entity is operational and 0 otherwise. (Zarghami & Dumrak, 2021a). The status of \(K_{i}^{* }\) is then evaluated based on the binary function \(\emptyset \left( {X_{{i{\text{S}}}} ,X_{{i{\text{M}}}} ,X_{iD} ,X_{iR} } \right)\) given below:
where \(\emptyset \left( {X_{{i{\text{S}}}} ,X_{{i{\text{M}}}} ,X_{iD} ,X_{iR} } \right)\) is the structure function of \(K_{i}^{* }\), and \(X_{{i{\text{S}}}} , X_{{i{\text{M}}}} , X_{iD} ,\) and \(X_{iR}\) are random variables that, respectively, denote the status of a given supplier, manufacturer, distributor, and retailer in \(K_{i}^{* }\).
Given the structure function of each K-entity spanning tree, we define \(A_{{K_{i}^{*} }}\) as the availability of \(K_{i}^{* }\), which is the probability that \(K_{i}^{* }\) is capable of conducting its required function given the availability of its constituent entities. In other words, the functionality of a K-entity spanning tree depends not only on the functionality of the single entities but also on the cross-interactions between them. Hence, the following equation holds true:
This is because, for a successful supply of products, all constituent entities of \(K_{i}^{* }\) must function. Therefore,
Subsequently, \(A_{{K_{i}^{*} }}\) can be calculated using the subsequent mathematical formula:
where \(a_{iS}\), \(a_{iM}\),\({ }a_{iD}\), and \(a_{iR}\) are the availability of K-entity spanning links of \(K_{i}^{* }\), which refers to a condition of partial operation of an entity.
Up to this point, we have calculated the availability of a given K-entity spanning tree. We expand the method to assess the overall availability of an SCN. Let \(K^{*} = \left\{ {K_{1}^{*} ,} \right.K_{2}^{*} , \ldots , K_{m}^{*} \}\) be the set of all K-entity spanning trees in an SCN. To ensure the network operates effectively, at any given time, 1 out of \(m\) K-entity spanning trees must function. Therefore, the overall availability of the SCN is incorporated into the calculation of the probability that all K-entity spanning trees do not fail. This is reminiscent of the parallel arrangement of the functional blocks in the ABD, illustrated in Fig. 4. Thus, the network availability index of an SCN can be calculated using the subsequent mathematical formula:
where \({\text{AI}}_{{{\text{SCN}}}}\) denotes the network availability index, \(A_{{K_{i}^{*} }}\) represents the availability of a given K-entity spanning tree, and \(m\) is the number of K-entity spanning trees in the network.
Step 3—Measuring Network Vulnerability
We now define the vulnerability index of an SCN, parametrized by \({\text{VI}}_{{{\text{SCN}}}}\), as a function of network flexibility and network availability. \({\text{VI}}_{{{\text{SCN}}}}\) is defined as:
where \({\text{AI}}_{{\text{SCN }}}\) is the network availability index, which can be calculated from Eq. (18), and \({\text{FI}}_{{{\text{SCN}}}}\) is the network flexibility index, which can be obtained from Eq. (13).
Figure 5 shows the 3D plot of the vulnerability index,\({\text{ VI}}_{{{\text{SCN}}}}\), against the network flexibility,\({\text{ FI}}_{{{\text{SCN}}}}\), and network availability, \({\text{AI}}_{{{\text{SCN}}}}\). Examination of this figure reveals that: (1) \({\text{VI}}_{{{\text{SCN}}}} { }\) falls in the range \([0,1]\); (2) there is a negative correlation between \({VI}_{SCN}\) and \({FI}_{SCN}\), meaning an increase/decrease in the value of \({\text{FI}}_{{{\text{SCN}}}} { }\) results in a decrease/increase in the value of \({\text{VI}}_{{{\text{SCN}}}}\). A similar trend is observed in terms of the correlation between \({\text{VI}}_{{{\text{SCN}}}}\) and \({\text{AI}}_{{{\text{SCN}}}}\).
Conceptually, \({\text{VI}}_{{{\text{SCN}}}} { }\) exhibits the following properties. First, a higher value of \({\text{VI}}_{{{\text{SCN}}}}\) indicates greater vulnerability, while a lower value represents reduced vulnerability of an SCN. Second, where there exists no K-entity co-spanning tree in an SCN, \({\text{VI}}_{LN}\) attains its maximum value (\({\text{VI}}_{{{\text{SCN}}}} { = 1}\)). This implies that the vulnerability of an SCN with no backup entity is very high. Third, \({\text{VI}}_{{{\text{SCN}}}} { = 1}\) when the network is comprised of more than one K-entity spanning tree and at least, one entity in each K-entity spanning tree is not available. Fourth, \({\text{VI}}_{{{\text{SCN}}}}\) yields somewhat lower values where there are several K-entity co-spanning trees and all entities in the SCN are available. This denotes that the existence of multiple backup entities in the network reduces its vulnerability to disruptive events.
Numerical Illustration
An Illustrative Example
To illustrate the proposed vulnerability assessment method, we now turn to an illustrative SCN. Figure 6 depicts the structure of the example SCN, in which nodes represent entities and links denote material flows. The entities in this example include three suppliers (\(S_{1}\),\({ }S_{2}\), and \(S_{3}\)), two manufacturers (\(M_{1}\) and \(M_{2}\)), two distributors (\(D_{1}\) and \(D_{2}\)), and three retailers (\(R_{1}\),\({ }R_{2}\), and \({R}_{3}\)). These entities are connected by 13 collaborative links.
Suppose that, in the face of a pandemic, entities within the network temporarily cease production or operate at partial capacity, resulting in supply, manufacturing, and distribution reductions. For example, assume that entities in the example SCN implement new policies including social distancing restrictions to protect employees. These restrictions result in a decrease in the flow of products within entities, particularly in those where operating at full capacity necessitates close collaboration and coordination. In the following, the proposed method is used to evaluate the impact of such capacity reduction on the example network.
Results
Step 1—Measuring Network Flexibility
In the first step, the illustrative SCN is broken down into a combination of multiple K-entity spanning trees. Figure 7 illustrates all K-entity spanning/co-spanning trees of the example SCN. In this figure, K-entity spanning links are indicated by solid blue lines and K-entity co-spanning links are plotted by dashed red lines (in the online version of this paper).
We now calculate the flexibility value of each individual link using Eq. (6). For example, for link \(e_{1}\), \(n_{{{\text{KC}}^{*} }} \left( {e_{1} } \right) = 6\), \(q = 9\), and \(n_{{{\text{KC}}^{*} }} = 8;\); hence, we obtain \(F_{SN} \left( {e_{1} } \right) = \frac{6}{9 \times 8} = 0.08333\). After calculating the flexibility value for all links in the example network, Eq. (13) is used to obtain the network flexibility index (\({\text{FI}}_{{{\text{SCN}}}}\)). Table 3 summarizes the calculation process and the parameters used for obtaining \({\text{FI}}_{{{\text{SCN}}}}\).
The value of \(F_{SN} \left( {e_{i} } \right)\) for a link resembles the flexibility attribute of the link between two entities. As expected, \(e_{5}\),\(e_{6}\), and \(e_{12}\) attain lower values of flexibility compared with the other links in the network. This can be attributed to the comparatively lower redundancy of these links in establishing connections to the rest of the network. By contrast, \(e_{1}\), \(e_{2}\),\(e_{3}\),\(e_{4}\),\(e_{7}\),\(e_{8}\),\(e_{9}\),\(e_{10}\),\(e_{11}\), and \(e_{13}\) exhibit higher values of flexibility due to the higher number of alternative paths that pass through these links.
As can be seen from Table 3, a high value of the network flexibility index \({\text{FI}}_{{{\text{SCN}}}} { = 0}{\text{.9951 }}\) suggests a relatively low risk of service disruption in this example SCN. This is because the example network exhibits the property of a redundant structure with multiple parallel entities. In fact, the reserve capacity of two backup suppliers, one backup manufacturer, one backup distributor, and two backup retailers can be used to respond to disruptions. \({\text{FI}}_{{{\text{SCN}}}}\) precisely captures the inherent flexibility inherent network layout. The proposed flexibility index shows how well entities are linked together and gives a complete picture of the structural flexibility of SCNs.
Step 2- Developing the Network Availability Index
In the second step, we analyze a capacity reduction scenario by applying a reduced capacity to each collaborative link in the example SCN. In doing so, we construct an ABD for the network, as shown in Fig. 8.
The principle underlying an ABD is that the SCN can successfully operate if one of the K-entity spanning trees functions at any given time. The ABD includes eight K-entity spanning trees, indicated by blue lines in Fig. 7. Each K-entity spanning tree represents a functional pathway between a first echelon supplier and end-users. We associate each link in K-entity spanning trees with its availability, as a measure of reduced service capacity, and subsequently, calculate the availability of each K-entity spanning tree by using Eq. (17). The impact of the capacity reductions on the overall network performance is then quantified by using Eq. (18). To achieve this, we employ a range of capacity reduction values rather than fixed values for collaborative links within SCNs. This enables us to capture the inherent uncertainty in input data due to the uncertainty in the characteristics of a disruptive event. In line with this, we conduct a Monte Carlo simulation analysis, constructing a model to simulate potential outcomes. The triangular distribution is employed to represent the uncertainty range of link availability in the network. To ensure a high level of accuracy, the number of replicate simulations is set to 10,000.
Step 3—Measuring Network Vulnerability
The final step utilizes the results of simulation analysis to develop an index for measuring network vulnerability. The average value of 10,000 simulations, \({\text{VI}}_{{{\text{SCN}}}} { = 0}{\text{.31}}\), is taken as the vulnerability index of the proposed method. This relatively high value implies a certain degree of risk to disruption. More specifically, \({\text{VI}}_{{{\text{SCN}}}} { }\) describes how severe the consequences of failure or capacity reduction in entities in the network can be.
Additionally, this step also includes a sensitivity analysis to evaluate the impact of variables or key assumptions on the proposed vulnerability index. Sensitivity analysis shows how the vulnerability index responds to changes in assumptions and helps and helps bolster confidence in the outcomes of the proposed method. In this context, sensitivity is defined as the partial derivative of \({\text{VI}}_{{{\text{SCN}}}}\) concerning changes in the availability of a given link in the SCN. This can be done by computing the rank correlation coefficients between \({\text{VI}}_{{{\text{SCN}}}}\) and the availability of every link in the network while the simulation is running. In fact, the rank correlation coefficient is used to evaluate the strength of the associations between the network vulnerability and the availability of entities in the network.
Figure 9 illustrates the rank correlation coefficients in the example SCN. Negative coefficients in this figure indicate that an increase in the capacity of an entity is associated with a decrease in the overall vulnerability of the network. Examination of Fig. 9 reveals that network vulnerability is most sensitive to the availability of the link between \(M_{1}\) and \(D_{1}\). This can be attributed to the high uncertainty in the capacity reduction in \(M_{1}\) as well as the less-redundant characteristics of the link \(e_{5}\) compared to most other links in the network. Network vulnerability is less sensitive to \(e_{13}\) because there exist two backup retailers (\(R_{1}\) and \(R_{2}\)) that compensate for any possible loss of \(R_{3}\). In addition, as can be observed from Table 3, the uncertainty in the capacity reduction in \(R_{3}\) is relatively low, since \(a_{i,LL} = 0.67\) and \(a_{i,M} = 0.70\).
Discussion
Research Contributions
This research makes significant contributions to literature in two key aspects. First, it represents an important response to criticism of the lack of studies that address the explicit level of flexibility in SCNs. The concept of structural flexibility is implicit in the existing studies. In the current state, research attention lies in quantifying flexibility as an indirect measure of the resilience of SCNs to disruptive events (Pavlov et al., 2019; Tan et al., 2019). The present paper is among the first that build on a probabilistic method to quantify the explicit level of structural flexibility of SCNs. Further, the proposed method is among very few that capture the flexibility inherent within the layout of SCNs, both at local and global levels.
Second, recent examples of sustained global reductions in service capacity, such as reduced energy supplies and semiconductor shortages, present a novel challenge that the world is facing. While the literature increasingly emphasizes the vulnerability of SCNs to these challenges, a notable gap remains in quantitative research specifically addressing capacity reduction. As far as the available literature indicates, this research is the first to identify capacity reduction as a distinct disruption type and offers a quantitative method to assess its impact on SCNs.
Implications for Supply Chain Managers and Planners
This research provides three types of managerial implications. First, the proposed vulnerability evaluation method fulfills the objective of establishing a connection between the layout of an SCN and the vulnerability of the network. The outputs of the proposed method assist supply chain managers in discerning the impacts of different reconfiguration patterns on the vulnerability of the network. This allows for quantifying the vulnerability of an SCN due to the reconfiguration of the network, for example, through changes in link patterns by adding or removing the links between existing entities. To elaborate further, let’s consider the scenario where Retailer 2 (R2) has been forced to permanently close due to operational challenges. This closure necessitates managers restructure the supply chain network and subsequently reevaluate its vulnerability. Utilizing the proposed method, we derive the spanning/co-spanning trees for the reconfigured network, as depicted in Fig. 10. Using Eq. (19), the vulnerability index for this reconfigured network, denoted as \({\text{VI}}\prime_{{{\text{SCN}}}}\), is calculated to be 0.6201. This value signifies a notable escalation in the vulnerability of the restructured network compared to its original state, where \({\text{VI}}_{{{\text{SCN}}}}\) was 0.31. This substantial increase in the vulnerability index, from 0.31 to 0.6201, acts as a clear indicator for managers to ensure effective service levels, especially from retailers, within the reconfigured network. Addressing this elevated vulnerability may necessitate the adoption of new strategies, such as enhancing inventory management and diversifying retailers to reduce the vulnerability of the reconfigured network.
Second, the regular occurrence of disruptive events has highlighted the need for supply chain planners to take into account the risk of disruptions before a disruption occurs. The design of SCNs can be aided by using the suggested vulnerability index. By obtaining the proposed vulnerability index, we quantified the overall vulnerability of an SCN. As noted earlier, this value describes the severity of the consequences of capacity reduction and/or failures of entities in SCNs. A higher value of \({\text{VI}}_{{{\text{SCN}}}}\) indicates a higher magnitude of failures when disruption strikes. As such, \({\text{VI}}_{{{\text{SCN}}}} { }\) provides a decision support tool that can be used in the pre-structuring stage. By utilizing \({\text{ VI}}_{{{\text{SCN}}}}\), supply chain planners would be able to exclude network layouts with high values of \({\text{VI}}_{{{\text{SCN}}}}\) and to perform in-depth analysis of layouts with low values of \({\text{VI}}_{{{\text{SCN}}}}\). Disruption risk considerations indeed lead to the design of a reliable SCN that functions at an acceptable level during disruptive events.
Third, the proposed method enables operations and supply chain managers to identify entities that are more sensitive to disruptions, crucial for formulating effective mitigation strategies and highlighting SCN vulnerabilities. Through the sensitivity analysis, we scrutinized the overall sensitivity of an SCN to the capacity reduction in its constituent entities. We examined how a range of possible capacity reductions could have deleterious effects on the overall performance of the network. For instance, the sensitivity analysis revealed that the five most critical collaborative links between entities in terms of their influence on the vulnerability of the example SCN are \(e_{5}\), \(e_{12}\), \(e_{6}\), \(e_{7}\), and \(e_{2}\), respectively. From an operational perspective, enhancing collaboration among the entities linked through these channels can significantly reduce the SCN’s vulnerability to disruptions.
Implications for Policy Makers
This research offers two key implications for policy makers involved in overseeing and governing SCNs owned and managed by the public sector, such as healthcare supply chains in many countries (El Mokrini & Aouam, 2022). First, the proposed vulnerability evaluation method can be used by policy makers to identify critical areas for intervention, particularly those exhibiting lower levels of flexibility. This, in turn, empowers policy makers to design high-impact policies specifically targeted at enhancing the flexibility of SCNs in these critical areas.
Second, the proposed vulnerability evaluation method establishes a linkage between the flexibility of SCNs and the potential contributions of collaborative links among various network entities. This aspect enables policy makers to bolster collaborative links that exhibit the highest levels of contribution to the overall flexibility of an SCN. By formulating policies that promote relational governance between entities connected by these links, policy makers can strengthen coordination and information exchange effectively (Adetoyinbo et al., 2023). Indeed, enhancing procedures and policies to improve relational governance fosters trust, collaboration, and adaptability among entities. Consequently, this enhances the flexibility of SCNs and mitigates their vulnerability.
Conclusions
The literature pertaining to the questions “To what extent are our SCNs vulnerable to capacity reductions in an epidemic outbreak?” and “How can flexibility in the network layout be quantified as the vulnerability-averse behavior of SCNs?” offers little help in addressing them. The present article attempted to answer these questions via the development of an integrative method for vulnerability analysis of SCNs that accounts for both the capacity reductions of entities and the flexibility within the layout of the network. Within this framework, a new network vulnerability index as a function of network flexibility and the availability of entities was developed.
The proposed method was implemented on a four-echelon SCN. We conducted a Monte Carlo simulation analysis to replicate uncertainty regarding the extent of capacity reductions. Additionally, a sensitivity analysis was performed to assess the potential contribution of backup entities to the overall flexibility of the network. Our study yielded valuable insights that contribute to extending the existing literature. For instance, we forecasted the effects of capacity reductions on the performance of SCNs. Furthermore, our research highlights how the reserve capacity of backup suppliers, manufacturers, distributors, and retailers can enhance SCN performance against disruptions. The results of our method align with recent studies, reinforcing their findings (Kamalahmadi & Mellat Parast, 2017), and favor the fact that incorporating more backups and increasing the capacity of various entities in the network yields lower vulnerability and builds extra robustness in SCNs.
This research enriches supply chain management literature by introducing a novel method to explicitly quantify structural flexibility in SCNs and addressing capacity reduction as a distinct disruption. The proposed method directly connects the layout of a supply chain network to its vulnerability, assisting managers in assessing the impact of various network reconfigurations. The findings of this research empower planners to preemptively address disruption risks in SCN design, allowing for the elimination of high-risk layouts. Moreover, the findings enable operations and supply chain managers to identify critical network links, offering guidance for vulnerability reduction strategies within SCNs.
As a new method for vulnerability analysis of SCNs in the face of disruptions, this work opens up new research opportunities. However, it is important to acknowledge that this research is not without its limitations. First, the proposed method addresses the structural flexibility of SCNs by evaluating the reserve capacity of backup entities. It does not take into account the operational-based redundancies such as operational slack and inventory balance. Additional research is needed to incorporate operational redundancies into the proposed method. Second, the proposed method maps the entities of an SCN into an unweighted graph in which links represent the collaboration between the entities. Given the different level of interactions between various entities, a weighted graph provides a more complete representation of an SCN. Hence, future research can be built upon our method to develop a weighted graph that accounts for different levels of interaction between entities. Furthermore, future studies might seek to conduct empirical research to investigate best practices in reducing the vulnerability of SCNs to the COVID-19 pandemic, including incorporating backup and flexibility measures.
References
Abdi, F., Farughi, H., Sadeghi, H., & Arkat, J. (2024). Using common redundancy components for suppliers in a supply chain network design problem considering energy costs and environmental effects. Expert Systems with Applications, 245, 122989.
Adetoyinbo, A., Trienekens, J., & Otter, V. (2023). Contingent resource-based view of food netchain organization and firm performance: A comprehensive quantitative framework. Supply Chain Management: An International Journal, 28(6), 957–974.
Agrawal, N., Sharma, M., Raut, R. D., Mangla, S. K., & Arisian, S. (2023). Supply chain flexibility and post-pandemic resilience. Global Journal of Flexible Systems Management, 24(Suppl 1), S119–S138.
Asadabadi, A., & Miller-Hooks, E. (2020). Maritime port network resiliency and reliability through co-opetition. Transportation Research Part E, 137, 1–17.
Azad, N., & Hassini, E. (2019). A Benders decomposition method for designing reliable supply chain networks accounting for multimitigation strategies and demand losses. Transportation Science, 53(5), 1287–1312.
Beheshtian, A., Donaghy, K. P., Geddes, R. R., & Rouhani, O. M. (2017). Planning resilient motor-fuel supply chain. International Journal of Disaster Risk Reduction, 24, 312–325.
Berle, Ø., Asbjørnslett, B. E., & Rice, J. B. (2011). Formal vulnerability assessment of a maritime transportation system. Reliability Engineering & System Safety, 96(6), 696–705.
Bottani, E., Murino, T., Schiavo, M., & Akkerman, R. (2019). Resilient food supply chain design: Modelling framework and metaheuristic solution approach. Computer & Industrial Engineering, 135, 177–198.
Carvalho, H., Barroso, A. P., Machado, V. H., Azevedo, S., & Cruz-Machado, V. (2012). Supply chain redesign for resilience using simulation. Computer & Industrial Engineering, 62(1), 329–341.
Chowdhury, M. M. H., Chowdhury, P., Quaddus, M., Rahman, K. W., & Shahriar, S. (2024). Flexibility in enhancing supply chain resilience: Developing a resilience capability portfolio in the event of severe disruption. Global Journal of Flexible Systems Management. 25(2), 395–417. https://doi.org/10.1007/s40171-024-00391-2
Dixit, V., Verma, P., & Tiwari, M. K. (2020). Assessment of pre and post-disaster supply chain resilience based on network structural parameters with CVaR as a risk measure. International Journal of Production Economics, 227, 1–17.
Dong, M. (2006). Development of supply chain network robustness index. International Journal of Service Operations and Informatics, 1(1–2), 54–66.
Dwivedi, A., Srivastava, S., Agrawal, D., Jha, A., & Paul, S. K. (2023). Analyzing the inter-relationships of business recovery challenges in the manufacturing industry: Implications for post-pandemic supply chain resilience. Global Journal of Flexible Systems Management, 24(Suppl 1), S31–S48.
El Mokrini, A., & Aouam, T. (2022). A decision-support tool for policy makers in healthcare supply chains to balance between perceived risk in logistics outsourcing and cost-efficiency. Expert Systems with Applications, 201, 116999.
Emanuel, E. J., Persad, G., Upshur, R., Thome, B., Parker, M., Glickman, A., Zhang, C., Boyle, C., Smith, M., & Phillips, J. P. (2020). Fair allocation of scarce medical resources in the time of Covid-19. New England Journal of Medicine, 382(21), 2049–2055.
Fukutomi, M. (2024). Oil or geopolitical issues?: Quantitative rethinking of political instability in the Middle East and North Africa. GeoJournal, 89(2), 1–17.
Gunawan, I., Schultmann, F., & Zarghami, S. A. (2017). The four Rs performance indicators of water distribution networks: A review of research literature. International Journal of Quality & Reliability Management, 34(5), 720–732.
Han, J., & Shin, K. (2016). Evaluation mechanism for structural robustness of supply chain considering disruption propagation. International Journal of Production Research, 54(1), 135–151.
Hsu, C. I., & Li, H. C. (2011). Reliability evaluation and adjustment of supply chain network design with demand fluctuation. International Journal of Production Economics, 132(1), 131–145.
Kamalahmadi, M., & Mellat Parast, M. (2017). An assessment of supply chain disruption mitigation strategy. International Journal of Production Economics, 184, 210–230.
Kiani Mavi, R., Kiani Mavi, N., Hosseini Shekarabi, S. A., Pepper’s, M., & Arisian, S. (2023). Supply chain resilience: A common weights efficiency analysis with non-discretionary and non-controllable inputs. Global Journal of Flexible Systems Management. 24(Suppl 1), S77–S99. https://doi.org/10.1007/s40171-024-00380-5
Kim, Y., Chen, Y. S., Yan, T., & Linderman, K. (2015). Supply network disruption and resilience: A network structural perspective. Journal of Operations Management, 33, 43–59.
Lin, Y. Q., Huang, C. F., Liao, Y. C., & Yeh, C. C. (2017). System reliability of multistate intermodal logistics network with time windows. International Journal of Production Research, 55(7), 1959–1967.
Liu, H., Tian, Z., Huang, A., & Yang, Z. (2018). Analysis of vulnerabilities in maritime supply chains. Reliability Engineering & System Safety, 169, 475–484.
Moghadasi, N., Collier, Z. A., Koch, A., Slutzky, D. L., Polmateer, T. L., Manasco, M. C., & Lambert, J. H. (2022). Trust and security of electric vehicle-to-grid systems and hardware supply chains. Reliability Engineering & System Safety, 225, 108565.
Pandey, A. K., Daultani, Y., Pratap, S., Ip, A. W., & Zhou, F. (2024). Analyzing industry 4.0 adoption enablers for supply chain flexibility: Impacts on resilience and sustainability. Global Journal of Flexible Systems Management. https://doi.org/10.1007/s40171-024-00396-x
Pavlov, A., Ivanov, D., Pavlov, D., & Slinko, A. (2019). Optimization of network redundancy and contingency planning in sustainable and resilient supply chain resource management under conditions of structural dynamics. Annals of Operations Research. https://doi.org/10.1007/s10479-019-03182-6
Quigley, J., & Walls, L. (2007). Trading reliability targets within a supply chain using Shapley’s value. Reliability Engineering & System Safety, 92(10), 1448–1457.
Rakas, J., & Hecht, M. (2007). Airport availability modelling: A different perspective. International Journal of Critical Infrastructures, 3(3–4), 430–456.
Ramani, V., Ghosh, D., & Sodhi, M. S. (2022). Understanding systemic disruption from the Covid-19-induced semiconductor shortage for the auto industry. Omega, 113, 102720.
Sakhteh, S., Mohammadi, N., & Karimi, A. (2024). Factors affecting open innovation in digital entrepreneurship in Iran and the world. Global Journal of Flexible Systems Management, 25(1), 63–80.
Sharma, B., Mittal, M. L., Soni, G., & Ramtiyal, B. (2023). An implementation framework for resiliency assessment in a supply chain. Global Journal of Flexible Systems Management, 24(4), 591–614.
Tan, W. J., Zhang, A. N., & Cai, W. (2019). A graph-based model to measure structural redundancy for supply chain resilience. International Journal of Production Research, 57(20), 6385–6404.
Varma, S., Singh, N., & Patra, A. (2024). Supply chain flexibility: Unravelling the research trajectory through citation path analysis. Global Journal of Flexible Systems Management. 25(2), 199–222. https://doi.org/10.1007/s40171-024-00382-3
Wadhwa, S., & Rao, K. S. (2004). A unified framework for manufacturing and supply chain flexibility. Global Journal of Flexible Systems Management, 5(1), 29-36.
Xu, Y., Chou, J., Wang, Z., & Dong, W. (2024). Predicting the differences in food security with and without the Russia–Ukraine conflict scenarios over different regions of the world. Agricultural and Food Economics, 12(1), 5.
Zaoui, S., Foguem, C., Tchuente, D., Fosso-Wamba, S., & Kamsu-Foguem, B. (2023). The viability of supply chains with interpretable learning systems: The case of COVID-19 vaccine deliveries. Global Journal of Flexible Systems Management, 24(4), 633–657.
Zarghami, S. A., & Dumrak, J. (2021a). Aleatory uncertainty quantification of project resources and its application to project scheduling. Reliability Engineering & System Safety, 211, 107637.
Zarghami, S. A., & Dumrak, J. (2021b). Unearthing vulnerability of supply provision in logistics networks to the black swan events: Applications of entropy theory and network analysis. Reliability Engineering & System Safety. https://doi.org/10.1016/j.ress.2021.107798
Zarghami, S. A., Gunawan, I., & Schultmann, F. (2020). Exact reliability evaluation of infrastructure networks using graph theory. Quality and Reliability Engineering International, 36(2), 498–510.
Zarghami, S. A., & Zwikael, O. (2024). Building project resilience: A critical systems practice approach. Systems Research and Behavioral Science. https://doi.org/10.1002/sres.3010
Zhao, K., Kumar, A., Harrison, T. P., & Yen, J. (2011). Analyzing the resilience of complex supply network topologies against random and targeted disruptions. IEEE Systems Journal, 5(1), 28–39.
Zhao, K., Sheibe, K., Blackhurst, J., & Kumar, A. (2019). Supply chain network robustness against disruption: Topological analysis, measurement, and optimization. IEEE Transactions on Engineering Management, 66(1), 127–139.
Zhou, Y., Wang, J., & Huang, G. Q. (2019). Efficiency and robustness of weighted air transport networks. Transportation Research Part E, 122, 14–26.
Funding
Open Access funding enabled and organized by CAUL and its Member Institutions. The authors received no financial support for the research, authorship, and/or publication of this article.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declared no potential conflicts of interest with respect to the research, authorship, and/or publication of this article.
Ethical Approval
This research did not involve human participants or animals and did not involve data collection. Hence, there was no requirement for obtaining ethical approval.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Zarghami, S.A., Dumrak, J. Evaluating Vulnerability of Supply Chain Networks to Capacity Reduction. Glob J Flex Syst Manag 25, 629–646 (2024). https://doi.org/10.1007/s40171-024-00403-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40171-024-00403-1