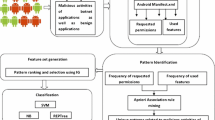
Abstract
A mobile botnet is a malicious software which as an advanced version of botnet can do destructive functions such as stealing important information, Denial of Service attack, sending malicious codes through Short Message Service (SMS), eavesdropping and recently extracting electronic crypto currency mining. Hyper Text Transfer Protocol, SMS, and Bluetooth are three protocols which are used by the mobile botnets to communicate. The Android Operating system (OS) has the largest number of users among other OS smartphones. In addition, it is an open source OS that allows attackers to exploit the bugs of the OS. However, there is no standard dataset which contain most of Android botnets families. Therefore, present study attempted to create a 28 Standard Android Botnet Dataset (28-SABD). Hence, 14 families of Android botnets including 1929 Android applications were exploited and their traffic was captured in execution and background manner. A small percentage of the captured data was labeled by a signature-based method. Then, the ensemble K-Nearest Neighbors (KNN) technique was used in order to improve the accuracy of the assigned labels by the signature-based method. As a result, the training dataset with reliable labels and the test dataset without labels were created. Finally, the remainder of the captured data (test dataset) was labeled using an ensemble Semi-Supervised KNN algorithm and the training dataset. Simulation results also indicated that more than 14 million packets of Android botnets traffic were collected to create 28-SABD. The data were also assigned labels with more than 94% accuracy.



Similar content being viewed by others
References
Abdul Kadir AF, Stakhanova N, Ghorbani AA (2015) Android botnets: what URLs are telling us. In: Qiu M, Xu S, Yung M, Zhang H (eds) International conference on network and system security, New York, NY, USA, 3–5 November 2015. Springer, Cham, pp 78–91. https://doi.org/10.1007/978-3-319-25645-0_6
Abdullah Z, Saudi MM (2018) RAPID-risk assessment of android permission and application programming interface (API) call for android botnet. Int J Eng Technol 7:49–54. https://doi.org/10.14419/ijet.v7i4.15.21370
Abdullah Z, Saudi MM, Badrul AN (2017) ABC: android botnet classification using feature selection and classification algorithms. Adv Sci Lett 23:4717–4720. https://doi.org/10.1166/asl.2017.8994
Alsumayt A, Haggerty J, Lotfi A (2017) Using trust to detect denial of service attacks in the internet of things over MANETs. Int J Space-Based Situat Comput 7:43–56. https://doi.org/10.1504/IJSSC.2017.0841231
Anwar S, Zolkipli MF, Inayat Z, Odili J, Ali M, Zain JM (2018) Android botnets: a serious threat to android devices. Pertanika J Sci Technol 26:37–70
Apvrille A (2012) Symbian worm Yxes: towards mobile botnets? J Comput Virol 8:117–131. https://doi.org/10.1007/s11416-012-0163-2
Arp D, Spreitzenbarth M, Hubner M, Gascon H, Rieck K, Siemens C (2014) DREBIN: effective and explainable detection of android malware in your pocket. In: Network and distributed system security symposium (NDSS), San Diego, CA, 23–26 February 2014. https://doi.org/10.14722/ndss.2014.23247
Arshad S, Shah MA, Khan A, Ahmed M (2016) Android malware detection and protection: a survey International. J Adv Comput Sci Appl 7:463–475. https://doi.org/10.14569/IJACSA.2016.070262
AsSadhan B, Moura JMF, Lapsley D, Jones C, Strayer WT (2009) Detecting botnets using command and control traffic. In: Eighth IEEE international symposium on network computing and applications, 9–11 July 2009. Cambridge, MA, USA, pp 156–162. https://doi.org/10.1109/NCA.2009.56
Azimi I, Rahmani AM, Liljeberg P, Tenhunen H (2017) Internet of things for remote elderly monitoring: a study from user-centered perspective. J Ambient Intell Humaniz Comput 8:273–289. https://doi.org/10.1007/s12652-016-0387-y
Celdrán AH, Pérez MG, Clemente FJG, Pérez GM (2018) Towards the autonomous provision of self-protection capabilities in 5G networks. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-018-0848-6
Chasaki D, Mansour C (2015) Security challenges in the internet of things. Int J Space-Based Situat Comput 5:141–149
Chen TM (2010) Stuxnet, the real start of cyber warfare? [Editor’s Note]. IEEE Netw 24:2–3. https://doi.org/10.1109/MNET.2010.5634434
Chen C-M, Lin H-C (2015) Detecting botnet by anomalous traffic. J Inf Secur Appl 21:42–51. https://doi.org/10.1016/j.jisa.2014.05.002
Choi B, Choi S, Cho K (2013) Detection of mobile botnet using VPN. In: Seventh international conference on innovative mobile and internet services in ubiquitous computing, 3–5 July 2013. Taichung, Taiwan, 3, pp 142–148. https://doi.org/10.1109/IMIS.2013.32
Cole A, Mellor M, Noyes D (2007) Botnets: the rise of the machines. In: 6th annual security conference, Las Vegas, NV, USA, 11–12 April 2007
Darwish A, Hassanien AE, Elhoseny M, Sangaiah AK, Muhammad K (2017) The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: opportunities, challenges, and open problems. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-017-0659-1
Deogirikar J, Vidhate A (2017) Security attacks in IoT: a survey. In: International conference on IoT in social, mobile, analytics and cloud) (I-SMAC), Palladam, India, 10–11 Feb 2017. IEEE, pp 32–37. https://doi.org/10.1109/I-SMAC.2017.8058363
Eslahi M, Yousefi M, Naseri MV, Yussof YM, Tahir NM, Hashim H (2016) Cooperative network behaviour analysis model for mobile botnet detection. In: IEEE symposium on computer applications and industrial electronics (ISCAIE), Batu Feringghi, Malaysia, 30–31 May 2016. IEEE, pp 107–112. https://doi.org/10.1109/ISCAIE.2016.7575046
Fernández Maimó L, Huertas Celdrán A, Gil Pérez M, García Clemente FJ, Martínez Pérez G (2018) Dynamic management of a deep learning-based anomaly detection system for 5G networks. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-018-0813-4
Ghafir I, Prenosil V, Hammoudeh M (2017) Botnet command and control traffic detection challenges: a correlation-based solution. Int J Adv Comput Netw Secur 7:27–31
Gil GD, Lashkari AH, Mamun M, Ghorbani AA (2016) Characterization of encrypted and VPN traffic using time-related features. In: 2nd international conference on information systems security and privacy (ICISSP 2016), Rome, Italy, 19–21 Feb 2016, pp 407–414. https://doi.org/10.5220/0005740704070414
Gu G, Perdisci R, Zhang J, Lee W (2008) BotMiner: clustering analysis of network traffic for protocol-and structure-independent botnet setection. In: 17th conference on security symposium, San Jose, CA, 28 July–1 August 2008, vol 2, pp 139–154
Geng G, Xu G, Zhang M, Yang Y, Yang G (2011) An improved SMS based heterogeneous mobile botnet model. In: IEEE international conference on information and automation, Shenzhen, China, 6–8 June 2011, pp 198–202. https://doi.org/10.1109/ICINFA.2011.5948987
Hamandi K, Elhajj IH, Chehab A, Kayssi A (2012) Android SMS botnet: a new perspective. In: Paper presented at the 10th ACM international symposium on Mobility management and wireless access, Paphos, Cyprus, 24–25 October 2012
Jiang RM, Jhang JS, Hsu FH, Hwang YL, Huang PW, Sheu YH (2013) Jokerbot—an android-based botnet. Appl Mech Materials 284:3454–3458. https://doi.org/10.4028/www.scientific.net/AMM.284-287.3454
Karim A, Salleh R, Shah SAA (2015) DeDroid: a mobile botnet detection approach based on static analysis. In: 12th Intl Conf on ubiquitous intelligence and computing and 12th Intl Conf on autonomic and trusted computing and 15th Intl Conf on scalable computing and communications and its associated workshops (UIC-ATC-ScalCom), Beijing, China, 10–14 Aug 2015, pp 1327–1332. https://doi.org/10.1109/UIC-ATC-ScalCom-CBDCom-IoP.2015.240
Karim A, Salleh R, Khan MK (2016) SMARTbot: a behavioral analysis framework augmented with machine learning to identify mobile botnet applications. PLos One 11:e0150077. https://doi.org/10.1371/journal.pone.0150077
Khattak S, Ramay NR, Khan KR, Syed AA, Khayam SA (2014) A taxonomy of botnet behavior, detection, and defense. IEEE Commun Surv Tutor 16:898–924. https://doi.org/10.1109/SURV.2013.091213.00134
Kirubavathi G, Anitha R (2018) Structural analysis and detection of android botnets using machine learning techniques. Int J Inf Secur 17:153–167. https://doi.org/10.1007/s10207-017-0363-3
Ko E, Kim T, Kim H (2018) Management platform of threats information in IoT environment. J Ambient Intell Humaniz Comput 9:1167–1176. https://doi.org/10.1007/s12652-017-0581-6
Lashkari AH, Draper-Gil G, Mamun MSI, Ghorbani AA (2017) Characterization of tor traffic using time based features. In: 3rd international conference on information systems security and privacy, Porto, Portugal, 19–21 Feb 2017, pp 253–262. https://doi.org/10.5220/0006105602530262
Li Y, Guan C, Li H, Chin Z (2008) A self-training semi-supervised SVM algorithm and its application in an EEG-based brain computer interface speller system. Pattern Recogn Lett 29:1285–1294. https://doi.org/10.1016/j.patrec.2008.01.030
Lu W, Rammidi G, Ghorbani AA (2011) Clustering botnet communication traffic based on n-gram feature. Sel Comp Commun 34:502–514. https://doi.org/10.1016/j.comcom.2010.04.007
Mas’ud MZ, Sahib S, Abdollah MF, Selamat SR, Yusof R (2014) Analysis of features selection and machine learning classifier in android malware detection. In: International conference on information science and applications (ICISA), Seoul, South Korea, 6–9 May 2014, pp 1–5. https://doi.org/10.1109/ICISA.2014.6847364
Meng X, Spanoudakis G (2016) MBotCS: a mobile botnet detection system based on machine learning. In: Lambrinoudakis C, Gabillon A (eds) 10th international conference on risks and security of internet and systems, Mytilene, Lesbos Island, Greece, 20–22 July 2016. Springer, Cham, pp 274–291. https://doi.org/10.1007/978-3-319-31811-0_17
Mtibaa A, Harras KA, Alnuweiri H (2015) From botnets to MobiBots: a novel malicious communication paradigm for mobile botnets. IEEE Commun Mag 53:61–67. https://doi.org/10.1109/MCOM.2015.7180509
Nadiammai GV, Hemalatha M (2014) Effective approach toward Intrusion Detection System using data mining techniques. Egypt Inform J 15:37–50. https://doi.org/10.1016/j.eij.2013.10.003
Pieterse H, Olivier MS (2014) Bluetooth command and control channel. Comput Secur 45:75–83. https://doi.org/10.1016/j.cose.2014.05.007
Sebastian S, Ayyappan S (2014) PV Framework for design of Graybot in social network. In: International conference on advances in computing, communications and informatics (ICACCI), New Delhi, India, 24–27 Sept 2014. IEEE, pp 2331–2336. https://doi.org/10.1109/ICACCI.2014.6968575
Shanthi K, Seenivasan D (2015) Detection of botnet by analyzing network traffic flow characteristics using open source tools. In: 9th international conference on intelligent systems and control (ISCO), Coimbatore, India, 9–10 Jan 2015. IEEE, pp 1–5. https://doi.org/10.1109/ISCO.2015.7282353
Sharafaldin I, Lashkari AH, Ghorbani AA (2018) Toward generating a new intrusion detection dataset and intrusion traffic characterization. In: 4th international conference on information systems security and privacy, Funchal, Maderia-Portugal, 22–24 January 2018, pp 108–116. https://doi.org/10.5220/0006639801080116
Stone-Gross B et al (2009) Your botnet is my botnet: analysis of a botnet takeover. In: Paper presented at the 16th ACM conference on computer and communications security, Chicago, Illinois, USA, 9–13 November 2009
Wang P, Zhang C, Li X, Zhang C (2014a) A mobile botnet model based on android system. In: Yuan Y, Wu X, Lu Y (eds) International conference on trustworthy computing and services, Berlin, Heidelberg. Springer, Berlin Heidelberg, pp 54–61. https://doi.org/10.1007/978-3-662-43908-1_7
Wang W, Wang X, Feng D, Liu J, Han Z, Zhang X (2014b) Exploring permission-induced risk in android applications for malicious application detection. IEEE Trans Inf Forensics Secur 9:1869–1882. https://doi.org/10.1109/TIFS.2014.2353996
Yan G (2013) Peri-Watchdog: Hunting for hidden botnets in the periphery of online social networks. Comput Netw 57:540–555. https://doi.org/10.1016/j.comnet.2012.07.016
Yin T, Zhang Y, Li S (2014) DR-SNBot: a social network-based botnet with strong destroy-resistance. In: 9th IEEE international conference on networking, architecture, and storage, Tianjin, China, 6–8 Aug 2014, pp 191–199. https://doi.org/10.1109/NAS.2014.37
Zeng Y, Shin KG, Hu X (2012) Design of SMS commanded-and-controlled and P2P-structured mobile botnets. In: Paper presented at the fifth ACM conference on security and privacy in wireless and mobile networks, Tucson, Arizona, USA
Zheng M, Sun M, Lui JCS (2013) Droid analytics: a signature based analytic system to collect, extract, analyze and associate android malware. In: 12th IEEE international conference on trust, security and privacy in computing and communications, Melbourne, VIC, Australia, 16–18 July 2013, pp 163–171. https://doi.org/10.1109/TrustCom.2013.25
Zhou Y, Jiang X (2012) Dissecting android malware: characterization and evolution. In: IEEE symposium on security and privacy, San Francisco, CA, USA, 20–23 May 2012, pp 95–109. https://doi.org/10.1109/SP.2012.16
Acknowledgements
The authors are grateful to Dr. Gholamreza Nakhaeizadeh (APL-Professor of Economics and Econometrics Karlsruhe Institute of Technology Institute of Economics Econometrics and Statistics), Dr. Arash Habibi Lashkari (research associate at the Faculty of Computer Science, University of New Brunswick, Canada), Dr. Mohammad GhasemiGol (Assistant Professor, University of Birjand, Iran) and Eng. Hossein Moodi (Faculty member of Birjand University of Technology) for their valuable contributions in this study. Authors also kindly appreciate Birjand University of Technology because experiments were carried out in its research Lab.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Moodi, M., Ghazvini, M. A new method for assigning appropriate labels to create a 28 Standard Android Botnet Dataset (28-SABD). J Ambient Intell Human Comput 10, 4579–4593 (2019). https://doi.org/10.1007/s12652-018-1140-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-018-1140-5