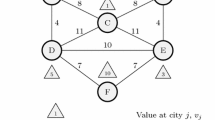
Abstract
The threat of nuclear terrorism has become an important issue for national security. A critical component in preventing a nuclear attack is to prevent nuclear material from being smuggled into the United States via any mode of transportation, including commercial air transportation. Screening baggage on incoming international commercial flights for nuclear material after the flights arrive in the United States makes the system vulnerable to a direct-to-target attack. A direct-to-target attack uses an aircraft to transport a nuclear bomb directly to a particular target prior to United States border screening. The encounter probability has been proposed for capturing the fraction of baggage that has been screened, which indirectly captures screening device utilization. This paper compares and analyzes potential performance measures for analyzing baggage screening systems given the impact of a direct-to-target attack. Seven discrete optimization models are formulated for determining how to screen checked baggage for nuclear material on incoming international flights given the performance measures, including four single-objective models and four goal programming models that analyze the tradeoffs across two performance measures. The models are compared to analyze the tradeoffs across the various performance measures. The results suggest that the encounter probability can be improved by considering one of the proposed performance measures, particularly the performance measure that focuses on targets. The goal programming model results suggest that multiple performance measures can be optimized with minimal trade-offs.





Similar content being viewed by others
References
Allison G (2004) Nuclear terrorism: the ultimate preventable catastrophe. Henry Hold and Company, New York
Bakir NO (2008) A decision tree model for evaluating countermeasures to secure cargo at United States Southwestern ports of entry. Decision Anal 5(4):230–248
Beged-Dov AG (1972) Lower and upper bounds for the number of lattice points in a simplex. SIAM J Appl Math 22(1):106–108
Brualdi RA (1999) Introductory combinatorics, 3rd edn. Prentice-Hall, Inc, Upper Saddle River
Candalino TJ Jr, Kobza JE, Jacobson SH (2004) Designing optimal aviation baggage screening strategies using simulated annealing. Comput Oper Res 31:1753–1767
Dimitrov NB, Michalopolous DP, Morton DP Nehme MV, Pan F, Popova E, Schneider EA, Thoreson GG (2011) Network deployment of radiation detectors with physics-based detection probability calculations. Ann Oper Res. doi:10.1007/s10479-009-0677-2
Dobson G (1982) Worst-case analysis of greedy heuristics for integer programming with nonnegative data. Math Oper Res 7:515–531
Dyer M (2003) Proceedings of the thirty-fifth annual acm symposium on theory of computing, chap. Approximate counting by dynamic programming. San Diego, CA, pp 693–699
El Baradi M (2007) Nuclear security report: measures to protect against nuclear terrorism. Tech. Rep., International Atomic Energy Agency. Vienna, Austria
Fritelli JF (2005) Port and maritime security: background issues for congress. CRS Report for Congress, Congressional Research Service, The Library of Congress, RL31733
Hillier FS, Lieberman J (1990) Introduction to operations research, 5th edn. McGraw-Hill, Inc., New York
International Atomic Energy Agency (2007) IAEA illicit trafficking database. Fact sheet. Vienna, Austria
Jacobson SH, McLay LA, Kobza JE, Bowman JM (2005a) Modeling and analyzing multiple station baggage screening security system performance. Nav Res Logist 52(1):30–45
Jacobson SH, McLay LA, Virta JL, Kobza JE (2005b) Integer program models for the deployment of airport baggage screening security devices. Optim and Eng 6(3):339–359
Jacobson SH, Virta JE, Bowman JM, Kobza JE, Nestor JJ (2001) Modeling aviation baggage screening security systems: a case study. IIE Trans 35(3):259–269
Kellerer H, Pferschy U, Pisinger D (2004) Knapsack problems. Springer-Verlag, Berlin, p 253
Kobza JE, Jacobson SH (1997) Probability models for access security system architectures. J Oper Res Soc 48(3):255–263
Lambe TA (1974) Bounds on the number of feasible solutions to a knapsack problem. SIAM J Appl Math 26(2):302–305
Martello S, Pisinger D, Toth P (2000) New trends in exact algorithms for the 0-1 knapsack problem. Eur J Oper Res 123:325–332
McLay LA, Jacobson SH, Kobza JE (2008) The tradeoff between technology and prescreening intelligence in checked baggage screening for aviation security. J Trans Secur 1(2):107–126
McLay LA, Lloyd JD, Niman E (2011) Interdicting nuclear material on cargo containers using knapsack problem models. Ann Oper Res. doi:10.1007/s10479-009-0667-4
Mullen M (2009) Welcome address, academic research initiative grantees conference. Washington, DC
Padberg MW (1971) a remark on An inequality for the number of lattice points in a simplex. SIAM J Appl Math 20(4):638–641
Sahin H, Feng QM (2008) A mathematical framework for sequential passenger and baggage screening to enhance aviation security. Comput Ind Eng 57:148–155
Sammon J (2009) TSA testimony on general aviation status. Statement, United States department of Homeland security transportation security administration before the subcommittee on transportation security and infrastructure protection, committee on Homeland security, United States House of Representatives, 15 July 2009
Schwartz SI, Choubey D (2009) Nuclear security spending: assessing costs, examining priorities. Tech. Rep., Carnegie Endowment for International Peace, Washington DC
Senju S, Toyoda Y (1968) An approach to linear progamming with 0-1 variables. Manage Sci 15:196–207
Sweet KM (2009) Aviation and airport security: terrorism and safety concerns, 2nd edn. Taylor & Francis Group, LLC, Boca Raton
United States Department of Transportation (2009) U.S. air carrier traffic statistics through September 2009. Research and Innovative Technology Administration, Bureau of Transportation Statistics. Washington, DC
US Homeland Security Council, Interagency Policy Coordination Subcommittee for Preparedness and Response to Radiological and Nuclear Threats (2009) Planning guidance for response to a nuclear detonation. Report, Executive Office of the President
US Transportation Security Administration (2009) Planning guidelines and design standards for checked baggage inspection systems. Washington, DC, 2nd edn.
Vojtech R (2009) Department of Homeland security. Personal Interview, Washington, DC.
Wein LM, Liu Y, Cao Z, Flynn SE (2007) The optimal spatiotemporal deployment of radiation portal monitors can improve nuclear detection at overseas ports. Sci Glob Secur 15:211–233
Acknowledgements
This material is based upon work supported by the U.S. Department of Homeland Security under Grant Award Number 2008-DN-077-ARI001-02. The computational work was done at Virginia Commonwealth University. The views and conclusions contained in this document are those of the authors and should not be interpreted as necessarily representing the official policies, either expressed or implied, of the U.S. Department of Homeland Security. The authors gratefully acknowledge Dr. J. Paul Brooks and Mr. Charles Stewart at Virginia Commonwealth University for their assistance with the computational results.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
Exact algorithms, such as branch and bound, can result in long computation times when solving the integer programming models, since all of the discrete optimization models are NP-hard. Several greedy heuristics are applied to the models introduced in Sections 4 and 5 in order to identify near-optimal solutions in a reduced amount of CPU time. Greedy heuristics for the multidimensional knapsack problem are used, since all of the discrete optimization models considered have a multidimensional knapsack sub-structure. Note that all of the greedy heuristics considered define an efficiency for each flight, e j , j = 1,2,...,n, or each target e k , k = 1,2,...,d. As with knapsack greedy heuristics, the flights or targets for all greedy heuristics introduced in this section are covered in non-increasing order of their efficiency values.
First, the two greedy heuristics used for the single objective models are introduced, which adapt the Dobson heuristic and the Toyoda and Senju heuristic (Kellerer et al. 2004) to the single objective discrete optimization models. The reader is referred to Dobson (1982) and Senju and Toyoda (1968) for more details.
The efficiency values of the Dobson heuristic consist of a ratio, whose numerator is the objective function coefficient and whose denominator consists of the sum of the coefficients across all of the constraints. The Dobson heuristic efficiency values for FCP, PCP, and BCP are
respectively, j = 1,2,...,n. The Dobson heuristic efficiency values for TCP are
Recall that \(W_{ik}=\sum_{j \in F_i \cap D_k} w_j\) for knapsacks i = 1,2,...,m (the sum of the baggage going from origin airport i to target k) and \(W_{(m+1)k}=\sum_{i=1}^{m} \sum_{j \in F_i \cap D_k} a_j\) for knapsack m + 1 (the total cost to screen the baggage going to target k), k = 1,2,...,d.
The efficiency values of the Toyoda and Senju heuristic capture the relative contribution of the constraints. Let h ij denote the excess capacity in knapsack i (either a capacity or the budget constraint) if all flights are covered. For FCP, PCP, and BCP,
and
If there is not some i (i = 1,2,...,m) for each j = 1,2,...,n such that h ij > 0, then Toyoda and Senju heuristic efficiency value e j = 0, j = 1,2,...,n. Otherwise, the Toyoda and Senju heuristic efficiency values for FCP, PCP, and BCP are
respectively, j = 1,2,...,n. Note that the Toyoda and Senju heuristic efficiency values are updated after each new flight is covered, which change the remaining capacities c 1,c 2,...,c m and the remaining budget B.
For TCP, let h ik denote the excess capacity in knapsack i (either a capacity or the budget constraint) if all targets are covered,
and
If there is not some i (i = 1,2,...,m + 1) for each k = 1,2,...,d such that h ij > 0, then the Toyoda and Senju heuristic efficiency value e k = 0. Otherwise, the Toyoda and Senju heuristic efficiency values for TCP are
k = 1,2,...,d. Note that the Toyoda and Senju heuristic efficiency values are updated after each new target is covered, which change the remaining capacities c 1,c 2,...,c m and the remaining budget B.
Next, consider the goal programming models (TCFCP, TCPCP, TCBCP). The greedy heuristics are applied in two stages. In the first phase, a greedy heuristic for TCP is used to cover targets until T targets are covered (the minimum number of targets to be covered). The three greedy heuristics for TCP include the Dobson heuristic and the Toyoda and Senju heuristic (introduced earlier) as well as the Scaled Dobson heuristic, whose efficiency values are
Note that e k > 0, k = 1,2,...,d, unless the budget and all origin capacities are zero. The efficiency values are updated after each new target is covered, which change the remaining capacities c 1,c 2,...,c m and the remaining budget B.
In the second stage, one of two greedy heuristics are used (the Dobson heuristic and the Toyoda and Senju heuristic) that correspond to the objective that maximizes either the FC, PC, or BC measure. The adjusted budget and capacities (e.g., after adjusting for the flights that were covered in order to cover T targets) are used to compute the efficiency values for the FCP, PCP, and BCP heuristics. Thus, six greedy heuristics are applied to each goal programming model, each of which uses one of three heuristics for the first stage and one of two heuristics for the second stage.
The long CPU times to solve several PCP, BCP, TCPCP, and TCBCP instances in Section “Computational example” motivate the use of greedy heuristics to efficiently identify near-optimal solutions. All heuristics were run using Matlab 7.9.0.529 (R2009b) on an Intel Xeon X5365 3 GHz processor with 3.25 GB of RAM. The results are illustrated for the scenarios when C = 2,500.
Tables 4, 5, 6 and 7 summarize the solution values for each performance measure from the Dobson heuristics and Toyoda & Senju (abbreviated as T & S) heuristics. Table 4 reports the values of the FC measure using the Dobson heuristic and the Toyoda and Senju heuristic for FCP, PCP, BCP, and TCP. For convenience, the optimal solution values for FCP are listed. Heuristic values that match the optimal solution values are in boldface. Both FCP heuristics identify the optimal solutions for all values of B. The PCP heuristics identify solutions whose FC values are at least a factor of 0.370 of the optimal solution values, the BCP heuristics identify solutions whose FC values are at least a factor of 0.227 of the optimal solution values, and the TCP heuristics identify solutions whose FC values are at least a factor of 0.244 of the optimal solution values. The PCP, BCP, and TCP heuristics all fail to cover many flights.
Table 5 reports the values of the PC measure using the Dobson heuristics and the Toyoda and Senju heuristics for FCP, PCP, BCP, and TCP. The PCP Dobson heuristic identifies one optimal solution (when B = $25K), and the PCP Toyoda and Senju heuristic does not identify any optimal solutions. The PCP Dobson heuristic and the Toyoda and Senju heuristics identify PC solutions whose values are at least a factor of 0.990 of the optimal solution values. The FCP heuristics identify solutions whose PC values are at least a factor of 0.904 of the optimal solution values, the BCP heuristics identify solutions whose PC values are at least a factor of 0.893 of the optimal solution values, and the TCP heuristics identify solutions whose PC values are at least a factor of 0.590 of the optimal solution values.
Table 6 reports the values of the BC measure using the Dobson heuristics and the Toyoda and Senju heuristics for FCP, PCP, BCP, and TCP. The BCP Dobson heuristic identifies two optimal BCP solutions (when B = $100K, $150K), and the BCP Toyoda and Senju heuristic identifies one optimal solution (when B = $100K). The BCP Dobson heuristic and the Toyoda and Senju heuristics identify solutions to BCP whose values are at least a factor of 0.980 of the optimal solution value. The FCP heuristics identify solutions whose BC values are at least a factor of 0.957 of the optimal solution values, the PCP heuristics identify solutions whose BC values are at least a factor of 0.985 of the optimal solution values, and the TCP heuristics identify solutions whose BC values are at least a factor of 0.608 of the optimal solution values. The FCP, PCP, and BCP heuristics tend to nearly fully-utilize the baggage screening capacity.
Table 7 reports the values of the TC measure using the Dobson heuristics and the Toyoda and Senju heuristics for FCP, PCP, BCP, and TCP. It reveals that both the TCP Dobson heuristic and the TCP Toyoda and Senju heuristic identify the optimal TCP solutions for all scenarios considered. The PCP heuristics do not cover any targets, whereas both FCP heuristics cover at most one target, and both BCP heuristics cover at most four targets. The results of Tables 4–7 suggest that the FCP, PCP, and BCP heuristics are effective in covering targets, and that the TCP heuristics are not effective for covering flights, passengers, or bags.
The Dobson heuristics identify solutions whose values are at least as good as the their corresponding Toyoda and Senju heuristic solution values in all but two scenarios across all four models considered (BCP with B = $25K, $175K), which suggests that despite its simplicity, the Dobson heuristic is more effective for FCP, PCP, BCP, and TCP.
Tables 8, 9 and 10 summarize the solution values identified by the heuristics used for the three goal programming models when C = 250), B = $275K, and T varies from 1 to 10. All heuristics cover T targets in the scenarios considered, and hence, only the objective function values are reported (either FC, PC, or BC values). Table 8 reports the FC values for all of the heuristics. The TCFCP heuristics identify FC solution values that are at least 0.985 of the optimal solution values, whereas the TCPCP heuristics identify FC solution values that are at least 0.898 of the optimal solution value, and the TCBCP heuristics identify FC solution values that are at least 0.811 of the optimal solution values. A heuristic dominates the other heuristics if it identifies solution values whose values are at least as good as the those identified by the other heuristics for all scenarios considered (in this case, across all values of T). None of the six TCFCP heuristics dominate the other heuristics in terms of the FC values. However, each of the three TCFCP heuristics that use the Toyoda and Senju heuristic in the FC phase dominate other heuristics in all but two or fewer scenarios, which suggests that the Toyoda and Senju heuristic in the FC phase identifies better solution values than the Dobson heuristic in the FC phase.
Table 9 reports the PC values for the heuristics. The TCPCP heuristics identify PC solution values that are at least 0.983 of the optimal solution values, whereas the TCFCP heuristics identify PC solution values that are at least 0.930 of the optimal solution value and the TCBCP heuristics identify PC solution values that are at least 0.926 of the optimal solution values. None of the six TCPCP heuristics dominate the other heuristics in terms of the PC values.
Table 10 reports the BC values for the heuristics. The TCBCP heuristics identify solution values that are at least 0.955 of the optimal BC solution values, whereas the TCFCP heuristics identify BC solution values that are at least 0.945 of the optimal solution values, and the TCPCP heuristics identify BC solution values that are at least 0.978 of the optimal solution values. The TCBCP heuristic that uses the Scaled Dobson heuristic in the TC phase and then the Toyoda and Senju heuristic in the BC phase dominates all other TCBCP heuristics. The three TCBCP heuristics that use the Toyoda and Senju heuristics in the BC phase identify significantly better BC values than the corresponding TCBCP heuristic that uses the Dobson heuristic in the BC phase. This observation mirrors that of the TCFCP heuristics (and, to a lesser extent, of the TCPCP heuristics), which suggests that the Toyoda and Senju heuristic for the second phase is more effective than using the Dobson heuristic. We also note that the three TCPCP heuristics that use the Dobson heuristic in the BC phase outperform the corresponding TCBCP heuristic in terms of the BC solution values they identify in all thirty instances. The TCPCP heuristics that use the Toyoda and Senju heuristic in the BC phase outperform the corresponding TCBCP heuristics in terms of the BC solution values they identify in fourteen of the thirty instances. This observation is surprising, since it suggests that heuristics aimed at covering the most passengers more fully utilize the baggage screening capacity than heuristics designed to fully utilize the baggage screening capacity. This is largely the result of the TCBCP having a Subset Sum Problem substructure, where the efficiency values are identical across many flights.
Rights and permissions
About this article
Cite this article
McLay, L.A., Dreiding, R.A. & Howe, G.L. Rethinking the encounter probability for direct-to-target nuclear attacks for aviation security. J Transp Secur 4, 247–280 (2011). https://doi.org/10.1007/s12198-011-0070-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12198-011-0070-7