Abstract
A cryptographic primitive with low multiplicative complexity (MC) makes various applications efficient, but it may lead to cryptographic vulnerabilities. To find a trade-off between cryptographic resistance and MC, we propose a new tool called A-box, which is constructed using AND gates. In this paper, we prove several important properties of A-boxes, which provide the theoretical lower bounds of differential uniformity and linearity of corresponding S-boxes by MC. Specifically, we show that the differential uniformity (resp. linearity) of an (n, m)-bit S-box is at least 2n−l, where its MC is \(\lfloor \frac {n-1}{2}\rfloor +l\) (resp. m − 1 + l). Furthermore, we develop an algorithm to find S-boxes with differential uniformity equal to the bounds with respect to their MC. We improve the algorithm previously proposed by Zajac and Jókay (Cryptogr. Commun. 6(3), 255–277, 2014), which is applicable only to S-boxes of size lower than 5 bits, whereas ours can run on larger-sized S-boxes. We found a bijective (8,8)-bit S-box with differential uniformity 16, linearity 128, and 8 nonlinear gates: this has better cryptographic security than the SKINNY S-box with differential uniformity 64, linearity 128, and 8 nonlinear gates. We believe that our results provide a better understanding of the relationship between cryptographic resistance and MC of S-boxes.






Similar content being viewed by others
References
Adomnicai, A., Berger, T.P., Clavier, C., Francq, J., Huynh, P., Lallemand, V., Le Gouguec, K., Minier, M., Reynaud, L., Thomas, G.: Lilliput-AE: a new lightweight tweakable block cipher for authenticated encryption with associated data. Submitted to NIST Lightweight Project (2019)
Albrecht, M.R., Rechberger, C., Schneider, T., Tiessen, T., Zohner, M.: Ciphers for MPC and FHE. In: Oswald, E., Fischlin, M. (eds.) Advances in Cryptology - EUROCRYPT 2015 - 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, April 26-30, 2015, Proceedings, Part I, Lecture Notes in Computer Science, vol. 9056, pp. 430–454. Springer. https://doi.org/10.1007/978-3-662-46800-5_17 (2015)
Andreeva, E., Bilgin, B., Bogdanov, A., Luykx, A., Mendel, F., Mennink, B., Mouha, N., Wang, Q., Yasuda, K.: PRIMATEs v1.02. CAESAR submission. http://competitions.cr.yp.to/round2/primatesv102.pdf (2015)
Beierle, C., Jean, J., Kölbl, S., Leander, G., Moradi, A., Peyrin, T., Sasaki, Y., Sasdrich, P., Sim, S.M.: The SKINNY family of block ciphers and its low-latency variant MANTIS. In: Robshaw, M., Katz, J. (eds.) Advances in Cryptology - CRYPTO 2016 - 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 14-18, 2016, Proceedings, Part II, Lecture Notes in Computer Science, vol. 9815, pp. 123–153. Springer. https://doi.org/10.1007/978-3-662-53008-5_5(2016)
Berger, T.P., Canteaut, A., Charpin, P., Laigle-Chapuy, Y.: On almost perfect nonlinear functions over \(\text {F}_{2}^{\text {n}}\). IEEE Trans. Inf. Theory 52 (9), 4160–4170 (2006). https://doi.org/10.1109/TIT.2006.880036
Biham, E., Shamir, A.: Differential cryptanalysis of DES-like cryptosystems. In: Menezes, A., Vanstone, S.A. (eds.) Advances in Cryptology - CRYPTO ’90, 10th Annual International Cryptology Conference, Santa Barbara, California, USA, August 11-15, 1990, Proceedings, Lecture Notes in Computer Science, vol. 537, pp. 2–21. Springer. https://doi.org/10.1007/3-540-38424-3_1 (1990)
Bilgin, B., Meyer, L.D., Duval, S., Levi, I., Standaert, F.: Low AND depth and efficient inverses: a guide on S-boxes for low-latency masking. IACR Trans. Symmetric Cryptol. 2020(1), 144–184 (2020). https://doi.org/10.13154/tosc.v2020.i1.144-184
Bilgin, B., Nikova, S., Nikov, V., Rijmen, V., Stütz, G.: Threshold implementations of all 3 ×3 and 4 ×4 S-boxes. In: Prouff, E., Schaumont, P. (eds.) Cryptographic Hardware and Embedded Systems - CHES 2012 - 14th International Workshop, Leuven, Belgium, September 9-12, 2012. Proceedings, Lecture Notes in Computer Science, vol. 7428, pp. 76–91. Springer. https://doi.org/10.1007/978-3-642-33027-8_5 (2012)
Bogdanov, A., Knudsen, L.R., Leander, G., Paar, C., Poschmann, A., Robshaw, M.J.B., Seurin, Y., Vikkelsoe, C.: PRESENT: An ultra-lightweight block cipher. In: Paillier, P., Verbauwhede, I. (eds.) Cryptographic Hardware and Embedded Systems - CHES 2007, 9th International Workshop, Vienna, Austria, September 10-13, 2007, Proceedings, Lecture Notes in Computer Science, vol. 4727, pp. 450–466. Springer. https://doi.org/10.1007/978-3-540-74735-2_31 (2007)
Boyar, J., Find, M.G.: Multiplicative complexity of vector valued Boolean functions. Theor. Comput. Sci. 720, 36–46 (2018). https://doi.org/10.1016/j.tcs.2018.02.023
Boyar, J., Matthews, P., Peralta, R.: Logic minimization techniques with applications to cryptology. J. Cryptol. 26(2), 280–312 (2013). https://doi.org/10.1007/s00145-012-9124-7
Boyar, J., Peralta, R.: Concrete multiplicative complexity of symmetric functions. In: Kralovic, R., Urzyczyn, P. (eds.) Mathematical Foundations of Computer Science 2006, 31st International Symposium, MFCS 2006, Stará Lesná, Slovakia, August 28-September 1, 2006, Proceedings, Lecture Notes in Computer Science, vol. 4162, pp. 179–189. Springer. https://doi.org/10.1007/11821069_16 (2006)
Boyar, J., Peralta, R., Pochuev, D.: On the multiplicative complexity of Boolean functions over the basis (∧, ⊕, 1). Theor. Comput. Sci. 235(1), 43–57 (2000). https://doi.org/10.1016/S0304-3975(99)00182-6
Bozilov, D., Bilgin, B., Sahin, H.A.: A note on 5-bit quadratic permutations’ classification. IACR Trans. Symmetric Cryptol. 2017(1), 398–404 (2017). https://doi.org/10.13154/tosc.v2017.i1.398-404
Canteaut, A., Perrin, L.: On CCZ-equivalence, extended-affine equivalence, and function twisting. Finite Fields Their Appl. 56, 209–246 (2019). https://doi.org/10.1016/j.ffa.2018.11.008
Carlet, C., Ding, C.: Nonlinearities of S-boxes. Finite Fields Their Appl. 13(1), 121–135 (2007). https://doi.org/10.1016/j.ffa.2005.07.003
Chabaud, F., Vaudenay, S.: Links between differential and linear cryptanalysis. In: Santis, A.D. (ed.) Advances in Cryptology - EUROCRYPT ’94, Workshop on the Theory and Application of Cryptographic Techniques, Perugia, Italy, May 9-12, 1994, Proceedings, Lecture Notes in Computer Science, vol. 950, pp. 356–365. Springer. https://doi.org/10.1007/BFb0053450 (1994)
Chase, M., Derler, D., Goldfeder, S., Orlandi, C., Ramacher, S., Rechberger, C., Slamanig, D., Zaverucha, G.: Post-quantum zero-knowledge and signatures from symmetric-key primitives. In: Thuraisingham, B.M., Evans, D., Malkin, T., Xu, D. (eds.) Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS 2017, Dallas, TX, USA, October 30 - November 03, 2017, pp. 1825–1842. ACM. https://doi.org/10.1145/3133956.3133997 (2017)
Courtois, N., Mourouzis, T., Hulme, D.: Exact logic minimization and multiplicative complexity of concrete algebraic and cryptographic circuits. Int. J. Adv. Intell. Syst. 6(3), 165–176 (2013)
Courtois, N.T.: How fast can be algebraic attacks on block ciphers? In: Biham, E., Handschuh, H., Lucks, S., Rijmen, V. (eds.) Symmetric Cryptography, 07.01. - 12.01.2007, Dagstuhl Seminar Proceedings, vol. 07021. Internationales Begegnungs- und Forschungszentrum fuer Informatik (IBFI), Schloss Dagstuhl, Germany. http://drops.dagstuhl.de/opus/volltexte/2007/1013 (2007)
Courtois, N.T., Hulme, D., Mourouzis, T.: Solving Circuit Optimisation Problems in Cryptography and Cryptanalysis. IACR Cryptol. ePrint Arch. 2011, 475. http://eprint.iacr.org/2011/475 (2011)
Daemen, J., Rijmen, V.: The block cipher rijndael. In: Quisquater, J., Schneier, B. (eds.) Smart Card Research and Applications, This International Conference, CARDIS ’98, Louvain-la-Neuve, Belgium, September 14-16, 1998, Proceedings, Lecture Notes in Computer Science, vol. 1820, pp. 277–284. Springer. https://doi.org/10.1007/10721064_26 (1998)
Giacomelli, I., Madsen, J., Orlandi, C.: ZKBoo: Faster zero-knowledge for boolean circuits. In: Holz, T., Savage, S. (eds.) 25th USENIX Security Symposium, USENIX Security 16, Austin, TX, USA, August 10-12, 2016, pp. 1069–1083. USENIX Association. https://www.usenix.org/conference/usenixsecurity16/technical-sessions/presentation/giacomelli (2016)
Goudarzi, D., Jean, J., Kölbl, S., Peyrin, T., Rivain, M., Sasaki, Y., Sim, S.M.: Pyjamask: Block Cipher and Authenticated Encryption with Highly Efficient Masked Implementation. IACR Trans. Symmetric Cryptol. 2020 (S1), 31–59 (2020). https://doi.org/10.13154/tosc.v2020.iS1.31-59
Grosso, V., Leurent, G., Standaert, F., Varici, K.: LS-designs: Bitslice encryption for efficient masked software implementations. In: Cid, C., Rechberger, C. (eds.) Fast Software Encryption - 21st International Workshop, FSE 2014, London, UK, March 3-5, 2014. Revised Selected Papers, Lecture Notes in Computer Science, vol. 8540, pp. 18–37. Springer. https://doi.org/10.1007/978-3-662-46706-0_2 (2014)
Halevi, S., Shoup, V.: Algorithms in HElib. In: Garay, J.A., Gennaro, R. (eds.) Advances in Cryptology - CRYPTO 2014 - 34th Annual Cryptology Conference, Santa Barbara, CA, USA, August 17-21, 2014, Proceedings, Part I, Lecture Notes in Computer Science, vol. 8616, pp. 554–571. Springer. https://doi.org/10.1007/978-3-662-44371-2_31 (2014)
Hatzivasilis, G., Fysarakis, K., Papaefstathiou, I., Manifavas, C.: A review of lightweight block ciphers. J. Cryptogr. Eng. 8(2), 141–184 (2018). https://doi.org/10.1007/s13389-017-0160-y
Kim, H., Jeon, Y., Kim, G., Kim, J., Sim, B., Han, D., Seo, H., Kim, S., Hong, S., Sung, J., Hong, D.: A New Method for Designing Lightweight S-boxes with High Differential and Linear Branch Numbers, and Its Application. IACR Cryptol. ePrint Arch. 2020, 1582. https://eprint.iacr.org/2020/1582 (2020)
Kocher, P.C.: Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In: Koblitz, N. (ed.) Advances in Cryptology - CRYPTO ’96, 16th Annual International Cryptology Conference, Santa Barbara, California, USA, August 18-22, 1996, Proceedings, Lecture Notes in Computer Science, vol. 1109, pp. 104–113. Springer. https://doi.org/10.1007/3-540-68697-5_9 (1996)
Kolesnikov, V., Schneider, T.: Improved garbled circuit: Free XOR gates and applications. In: Aceto, L., Damgård, I., Goldberg, L.A., Halldórsson, M.M., Ingólfsdóttir, A., Walukiewicz, I. (eds.) Automata, Languages and Programming, 35th International Colloquium, ICALP 2008, Reykjavik, Iceland, July 7-11, 2008, Proceedings, Part II - Track B: Logic, Semantics, and Theory of Programming & Track C: Security and Cryptography Foundations, Lecture Notes in Computer Science, vol. 5126, pp. 486–498. Springer. https://doi.org/10.1007/978-3-540-70583-3_40 (2008)
Matsui, M.: Linear Cryptanalysis Method for DES Cipher. In: Helleseth, T. (ed.) Advances in Cryptology - EUROCRYPT ’93, Workshop on the Theory and Application of of Cryptographic Techniques, Lofthus, Norway, May 23-27, 1993, Proceedings, Lecture Notes in Computer Science, vol. 765, pp. 386–397. Springer. https://doi.org/10.1007/3-540-48285-7_33 (1993)
Songhori, E.M., Hussain, S.U., Sadeghi, A., Schneider, T., Koushanfar, F.: TinyGarble: Highly Compressed and Scalable Sequential Garbled Circuits. In: 2015 IEEE Symposium on Security and Privacy, SP 2015, San Jose, CA, USA, May 17-21, 2015, pp. 411–428. IEEE Computer Society. https://doi.org/10.1109/SP.2015.32 (2015)
Stoffelen, K.: Optimizing s-box implementations for several criteria using SAT solvers. In: Peyrin, T. (ed.) Fast Software Encryption - 23rd International Conference, FSE 2016, Bochum, Germany, March 20-23, 2016, Revised Selected Papers, Lecture Notes in Computer Science, vol. 9783, pp. 140–160. Springer. https://doi.org/10.1007/978-3-662-52993-5_8 (2016)
Testa, E., Soeken, M., Amarù, L. G., Micheli, G.D.: Reducing the Multiplicative Complexity in Logic Networks for Cryptography and Security Applications. In: Proceedings of the 56th Annual Design Automation Conference 2019, DAC 2019, Las Vegas, NV, USA, June 02-06, 2019, p. 74. ACM. https://doi.org/10.1145/3316781.3317893 (2019)
Yao, A.C.: How to generate and exchange secrets (extended abstract). In: 27th Annual Symposium on Foundations of Computer Science, Toronto, Canada, 27-29 October 1986, pp. 162–167. IEEE Computer Society. https://doi.org/10.1109/SFCS.1986.25(1986)
Zajac, P.: Constructing S-boxes with low multiplicative complexity. Stud. Sci. Math. Hung. 52(2), 135–153 (2015)
Zajac, P., Jókay, M.: Multiplicative complexity of bijective 4×4 S-boxes. Cryptogr. Commun. 6 (3), 255–277 (2014). https://doi.org/10.1007/s12095-014-0100-y
Acknowledgements
This work was supported by Institute for Information & communications Technology Promotion(IITP) grant funded by the Korea government(MSIT) (No.2017-0-00520, Development of SCR-Friendly Symmetric Key Cryptosystem and Its Application Modes)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
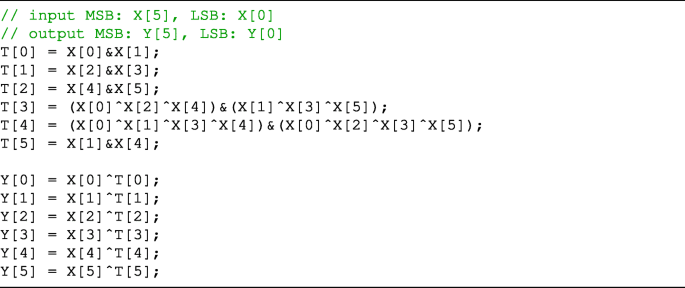
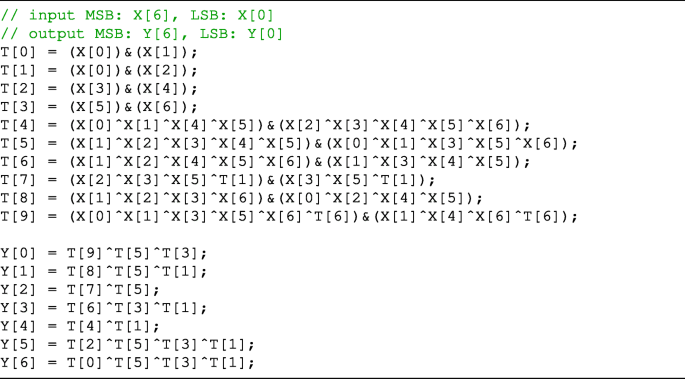
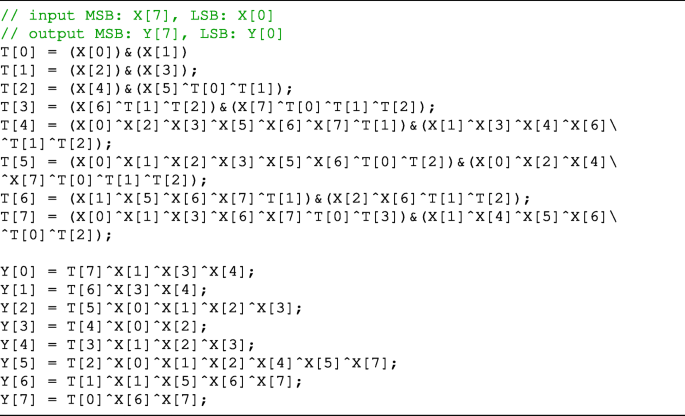
Appendix A: Bitsliced implementations of our S-boxes
Appendix A: Bitsliced implementations of our S-boxes
In this appendix, the method to implement the S-boxes presented in Table 2, which we found by experiments, is shown in Listing 1∼7.
These are written in the C language. In each listing, X is an input bit string, Y is an output bit string, and T is a temporary bit string.
Rights and permissions
About this article
Cite this article
Jeon, Y., Baek, S., Kim, H. et al. Differential uniformity and linearity of S-boxes by multiplicative complexity. Cryptogr. Commun. 14, 849–874 (2022). https://doi.org/10.1007/s12095-021-00547-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-021-00547-2