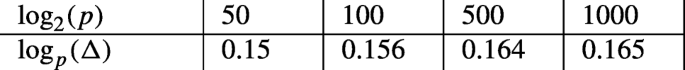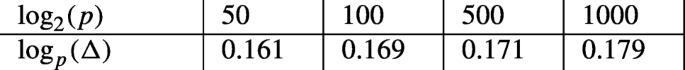Abstract
In this paper we study the linear congruential generator on elliptic curves from the cryptographic point of view. We show that if sufficiently many of the most significant bits of the composer and of three consecutive values of the sequence are given, then one can recover the seed and the composer (even in the case where the elliptic curve is private). The results are based on lattice reduction techniques and improve some recent approaches of the same security problem. We also estimate limits of some heuristic approaches, which still remain much weaker than those known for nonlinear congruential generators. Several examples are tested using implementations of ours algorithms.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
A PseudoRandom Bit Generator(PRBG) is a deterministic algorithm that, once initialized with some random value (called the seed), outputs a sequence that appears random, in the sense that an observer who does not know the value of the seed cannot distinguish the output from that of a (true) random bit generator. PRBG’s have important applications on simulations (e.g. for the Monte Carlo method), electronic games (e.g. for procedural generation), and cryptography. Good statistical properties are a vital requirement for the output of a PRBG. Cryptographic applications require the output not to be predictable from earlier outputs, and more elaborate algorithms, which do not inherit the linearity of simpler PRBGs, are needed.
There is a vast literature devoted to generating pseudorandom numbers using arithmetic of finite field and residue rings, see [33, 37, 38, 45]. In 1994, Hallgreen [21] proposed a pseudorandom number generator based on the group of points of an elliptic curve defined over a prime finite field.
For a prime p, denote by \(\mathbb {F}_{p}\) the field of p elements and always assume that it is represented by the set {0,1,…,p − 1}. Accordingly, sometimes, where obvious, we treat elements of \(\mathbb {F}_{p}\) as integer numbers in the above range.
Let E be an elliptic curve defined over \(\mathbb {F}_{p}\) given by an affine Weierstrass equation, which for \(\gcd (p,6)=1\) takes form
for some \(a,b \in \mathbb {F}_{p}\) with 4a3 + 27b2≠ 0.
We recall that the set \(E(\mathbb {F}_{p})\) of \(\mathbb {F}_{p}\)-rational points forms an abelian group, with the point at infinity \(\mathcal {O}\) as the neutral element of this group (which does not have affine coordinates).
For a given point \(G \in E(\mathbb {F}_{p})\) the Linear Congruential Generator on Elliptic Curves, EC-LCG is a sequence Un of pseudorandom numbers defined by the relation
where ⊕ denotes the group operation in \(E(\mathbb {F}_{p})\) and \(U_{0} \in E(\mathbb {F}_{p})\) is the initial value or seed. We refer to G as the composer of the EC-LCG.
It is clear that the period of the sequence (2) is equal to the order of G. The EC-LCG provides a very attractive alternative to linear and non-linear congruential generators with many applications to cryptography and it has been extensively studied in the literature, see [3, 12, 17, 18, 21, 22, 34, 35, 39, 40].
In the cryptographic setting, the initial value U0 = (x0,y0) and the constants G, a, and b are assumed to be the secret key, and we want to use the output of the generator as ephemeral key of a stream cipher. Of course, if two consecutive values Un are revealed, it is almost always easy to find U0 and G. So, we output only the most significant bits of each Un in the hope that this makes the resulting output sequence difficult to predict.
It is known that not too many bits can be output at each stage: the EC-LCG is unfortunately predictable if sufficiently many bits of its consecutive elements are revealed, see [20, 31, 32].
Now, we are formalising the results. Assume that the sequence (Un) is not known, but for some n, approximations Wj of two consecutive values Un+j, j = 0,1 are given. The results involve another parameter Δ which measures how well the values Wj approximate the terms Un+j. This parameter is assumed to vary independently of p subject to satisfying the inequality Δ < p (and is not involved in the complexity estimates of our algorithms). More precisely, we say that \(W=(x_{W},y_{W}){\in {\mathbb {F}}_{p}^{2}}\) is a Δ-approximation to \(U=(x_{U},y_{U}){\in \mathbb {F}_{p}^{2}}\) if there exist integers e,f satisfying:
In general, we say that \(W=(\alpha _{1},\alpha _{2},\ldots ,\alpha _{n}) {\in \mathbb {F}_{p}^{n}}\) is a Δ-approximation to \(U=(x_{1},x_{2},\ldots ,x_{n}) {\in \mathbb {F}_{p}^{n}}\) if there exist integers 𝜖i, (i = 1,…,n) satisfying:
The case where Δ grows like a fixed power pδ where 0 < δ < 1 corresponds to the situation where a positive proportion δ of the least significant bits of terms of the output sequence remain hidden. The goal is to get δ as much larger as possible, recovering the rest of the bits in polynomial time.
The problem is a particular case of the following computational problem: given f1(X1,…,Xn),…,fs(X1,…,Xn) irreducible multivariate polynomials defined over the integer ring \({\mathbb {Z}}\), having a common root (x1,…,xn) modulo a known integer N, namely,
The root should be small root, in the sense that each xi is bounded by a known value Δ. We require to bound the sizes of Δ allowing to recover the desired root in polynomial time. For polynomial in one variable an algorithm has been given by Coppersmith in [9]. For bivariate polynomials does exist different methods in [6, 10, 11, 16] and, for general multivariate polynomials in [16, 24]. All of them are based on the so called lattice reduction techniques, also called the LLL techniques, because the celebrated LLL algorithm of Lenstra, Lenstra and Lovász [30]. However in the general case only heuristic results are known, which are just generalization of the original result by Coppersmith.
An algorithm to recover the seed U0 in deterministic polynomial time if Δ < p1/6, requiring compute a closest vector of a lattice of dimension 8 and coefficients size \(\log p\) is presented in [20]. The recent results [31, 32] recover ‘heuristically’ the seed U0 if Δ < p1/5. The heuristic method, since there is no guarantee of success, may fail by several reason, among them the difficulty of finding a short vector in a high dimensional lattice. Since the number of the monomials is quite large; those results does not imply practical attacks, since the naive application of Coppersmith method is impractical for high dimensional lattice.
The computation which is theoretically polynomial-time becomes in practice prohibitive, for instance and according to [32], if the quality is 0.187 < 0.2 = 1/5 requires 188 polynomials and 314 monomials, so the lattice dimension is 502.
In this paper, we prove a deterministic algorithm to recover the seed U0 in polynomial time if Δ < p1/6, requiring compute a closest vector of a lattice of dimension 5. Previous result in [20] required a lattice of dimension 8.
We also provide an heuristic method to recovering U0 if \({\Delta } < p^{\frac {k-1}{4k-2}}\), requiring compute a closest vector for a lattice of dimension 3k − 1, when k > 2 consecutive Δ −approximations to points Ui, (0,…,k − 1) of the curve E are given. A similar result is also presented in [31, 32] with a theoretical better bound \({\Delta } < p^{\frac {3k}{11k+4}}\), but again requiring computing LLL’s algorithm for a lattice of huge dimension. In fact, there is no practical way of testing their methods, not only because the lattice large dimension used, but the size of the prime p should be several hundreds of bits. On the other hand, for instance, we can recover the sequence produced by EC-LCG if only three consecutive Δ −approximations are given as soon as Δ < p1/5 requiring, the most time consuming, to find a closest vector for a lattice of dimension 7, and it matched by primes p of only 1000 bits.
In principle, we cannot obtain any approximation to composer G from any approximations to two consecutive values Un,Un+ 1 of the EC-LCG, because the elliptic curve group operation. We also rigorously demonstrate our approach in the special case when we have an approximation to composer G; we show that given Δ if sufficiently many of the most significant bits of G and of three consecutive values Un,Un+ 1,Un+ 2 of the EC-LCG are given, one can recover the seed U0 and the composer G as soon as O(Δ) < p1/6 requiring compute two closest vector for two lattices of dimension 7. And heuristic algorithm if O(Δ) < p5/12 by computing a short vector for a lattice of dimension 9. Finally, we obtain an heuristic method to recovering the whole sequence if \({\Delta } < p^{\frac {k-1}{5k-4}}\), by computing a closest vector of a certain lattice of dimension 4k − 3 when k > 2 consecutive Δ −approximations to points Ui, (0,…,k − 1) of the curve E and an Δ −approximation to composer G are given.
This suggests that for cryptographic applications EC-LCG should be used with great care. For the linear congruential generator similar problems have been introduced by Knuth [26] and then considered in [7, 13, 23, 27]; see also the surveys [8, 28]. The quadratic congruential generator and the inverse congruential generator have been studied in [4] and [15], see also the recent paper [44] for a more general problem
On the other hand, our results are substantially weaker than those known for the linear and nonlinear congruential generators.
The remainder of the paper is structured as follows. We start with a very short outline of some basic facts about the Closest Vector Problem (CVP), and the polynomial equations associated to the elliptic curve abelian group in Section 2. In Section 3 we attack the EC-LCG when the composer G is known. Section 4 is dedicated to study the case when the composer G is private. Then in Section 5 we discuss the results of numerical tests of pour approaches. We conclude with Section 6, which makes some final comments and poses open questions.
Throughout the paper, we use the convention that the parameters on which the implied constant in a Landau symbol O are written in the subscript of O. A symbol O without a subscript indicates and absolute implied constant.
2 Preliminaries
2.1 Closest vector problem in lattices
Here we review some results and definitions concerning the Closest Vector Problem, all of which can be found in [19]. For more details and more recent references, we recommend consulting [23].
Let {b1,…,bs} be a set of linearly independent vectors in \({\mathbb {R}}^{r}\). The set
is an s-dimensional lattice with basis {b1,…,bs}. If s = r, the lattice \({\mathscr{L}}\) is of full rank.
One basic lattice problem is the Closest Vector Problem (CVP): given a basis of a lattice \({\mathscr{L}}\) in \(\mathbb {R}^{s}\) and a shift vector t in \(\mathbb {R}^{s}\), the goal is finding a vector in the lattice \({{\mathscr{L}}}\) closest to the target vector t. It is well known that this problem is NP-hard when the dimension grows. However, it is solvable in deterministic polynomial time provided that the dimension of \({{\mathscr{L}}}\) is fixed (see [25], for example).
In fact, lattices in this paper consist of integer solutions:
\(\textbf x=(x_{0},\ldots ,x_{s-1})\in ~\mathbb {Z}^{s}\) of a system of congruences
modulo some positive integers q1,…,qm. Typically (although not always) the volume of such a lattice is the product Q = q1⋯qm. Moreover, all the aforementioned algorithms, when applied to such a lattice, become polynomial in \(\log Q\). If textbfb1,…,bs} is a basis of the above lattice, by the Hadamard inequality we have:
For a slightly weaker task of finding a sufficiently close vector, the celebrated LLL algorithm of Lenstra, Lenstra and Lovász [30] provides a desirable solution, as noticed by [2], that is, a polynomial time algorithm in the bit size coefficients of the lattice basis and also of the lattice dimension. Here, we state this result as Lemma 1.
Lemma 1
There exists a deterministic polynomial time algorithm which, when given an s-dimensional full rank lattice \({\mathscr{L}}\) and a shift vector t, finds a lattice vector \(\textbf {u}\in {\mathscr{L}}\) satisfying the inequality
An outline of the algorithms presented in this paper goes as follows. They are divided into two stages.
-
Stage 1: We construct a certain lattice \({{\mathscr{L}}}\) of dimension s; this lattice depends on the given approximations. We also show that a certain vector E directly related to missing information is a very short vector. A closest vector F is found; see [25] for fixed dimension and Lemma 1 the approximation solution for arbitrary dimension.
-
Stage 2: We show that F provides the required information about E if the approximation is good enough.
Many other results on both exact and approximate finding of a closest vector in a lattice are discussed in [19, 23].
2.2 The polynomial equation of the group associated to an elliptic curve
The operation ⊕ acts over the points P = (xP,yP) and Q = (xQ,yQ) of \(E(\mathbb {F}_{p})\) with \(P, Q \not = \mathcal {O}\) as follows:
-
If xP≠xQ, then
$$ \begin{array}{cc} x_{R}=m^{2}-x_{P}-x_{Q}, \qquad &y_{R}=m(x_{P}-x_{R})-y_{P}, \\ &\text{~where}\qquad m =\frac{y_{Q}-y_{P}}{x_{Q}-x_{P}}. \end{array} $$(4) -
If xP = xQ but yP≠yQ, then \(P \oplus Q =\mathcal {O}\).
-
If P = Q and yP≠ 0, then
$$ \begin{array}{ll} x_{R}=m^{2}-2x_{P}, \qquad &y_{R}=m(x_{P}-x_{R})-y_{P}, \\ &~~\text{where}\quad m =\frac{3{x_{P}^{2}}+a}{2y_{P}}. \end{array} $$(5) -
If P = Q and yP = 0, then \(P \oplus Q =\mathcal {O}\).
See [1, 5, 43] for these and other general properties of elliptic curves.
Our context is a pseudorandom bit generator which outputs affine points in an elliptic curve. One obtains recursively them by operating a fixed composer G to the previous value. So, almost always, the above equations in the first case (4) will determine the process.
If P is not Q or − Q, then, clearing denominators in (4), we can translate P ⊕ Q = R into the following identities in the field \(\mathbb {F}_{p}\):
and
where
Lemma 2
Let L1(XQ,YQ,XP,YP,XR),L2(XQ,YQ,XP,YP,XR,YR) be elements of the polynomial ring \(\mathbb {F}_{p}[X_{Q},Y_{Q},X_{P},Y_{P},X_{R},Y_{R}]\) and let U,V,W be algebraically independent variables.
-
1.
Let Φ be the linear transformation:
$$(X_{P} \to X_{P}, Y_{P}\to Y_{P}, X_{Q}\to X_{P}+U, Y_{Q} \to Y_{P} +V, X_{R} \to X_{P} +W)$$we have Φ(L1) = 3XPU2 + U3 + U2W − V2.
-
2.
$$ L_{1}(X_{Q},Y_{Q}+U,X_{P}, Y_{P}+U, X_{R}) = L_{1}(X_{Q},Y_{Q},X_{P},Y_{P},X_{R})$$$$ L_{2}(X_{Q}+U,Y_{Q},X_{P}+U, Y_{P}, X_{R}+U, Y_{R}) = L_{2}(X_{Q},Y_{Q},X_{P},Y_{P},X_{R},Y_{R})$$
Proof
It is straightforward. □
On the other hand, since P = (xP,yP), Q = (xQ,yQ) and R = (xR,yR) are points of the elliptic curve E, we have:
Eliminating the curve parameters a, b and assuming that xP≠xR, we obtain the following polynomial \(L_{3} \in \mathbb {F}_{p}[X_{Q},Y_{Q},X_{P},Y_{P},X_{R},Y_{R}]\)
verifying L3(xQ,yQ,xP,yQ,xR,yR) ≡ 0 mod p. Now, we consider the linear map Θ :
where degree of \(A\in \mathbb {F}_{p}[X_{Q},Y_{Q},X_{P},Y_{P},X_{R},Y_{R}, U,V] \) with respect the variable YP is zero.
3 Predicting EC-LCG for Known composer
Assume that a, b are unknown, but the prime p is given to us. In [20] shows that when we are given Δ-approximations Wn, Wn+ 1 to (respectively) two consecutive affine values Un, Un+ 1 produced by the EC-LCG; we can recover the exact values, provided that x0 does not lie in a certain set, whose size is bounded by O(Δ6). Note that once two affine points in a curve as (1) are given, such that their first component is different, the curve (the parameters a and b) are determined. Then, after discovering the values Un and Un+ 1, we can reproduce (backwards and forwards) the whole sequence. To simplify the notation, we assume that n = 0 from now on.
We write Wj = (αj,βj), Uj = (xj,yj), for j = 0,1; so there exist integers ej, fj for j = 0, 1 with:
Theorem 1
[20] With the above notations and definitions, there exists a set \(\mathcal {U}({\Delta };a,x_{G},\) \(y_{G})\subseteq \mathbb {F}_{p}\) of cardinality \(\# \mathcal {U}({\Delta };a,x_{G},y_{G}) = O({\Delta }^{6})\) with the following property: whenever \(x_{0} \not \in \mathcal {U} ({\Delta };a,x_{G},y_{G})\) then, given Δ −approximations W0, W1 to two consecutive affine values U0,U1 produced by linear congruential generator on elliptic curves (2), and given the prime p one can recover the seed U0 in deterministic polynomial time.
The proof of this result in [20], the ‘bad’ set of values \(\mathcal {U}({\Delta };a,x_{G},y_{G})\) for the components x0 is described, proving whenever that value lies outside the set, the algorithm works correctly. Furthermore, the size of the set is asymptotically bounded with Δ6. This means that if Δ = o(p1/6) and p is large enough, assuming an uniform distribution of probabilities for \(x_{0} \in {\mathbb {F}}_{p}\), the method is unlikely to fail.
The proof in [20] requires the two polynomials L1 and L2 of (6) and 8 monomials, so the involved lattice has dimension 8. Here, we use only the polynomial L2 of (6), then the corresponding lattice dimension is only 5. The present proof is a simple observation of the same strategy, we have included here a significant part of the details for the reader convenience.
Proof
We assume that \(x_{0} \in \mathbb {F}_{p}\) is chosen so as not to lie in a certain subset \(\mathcal {U}({\Delta };a,x_{G},y_{G})\) of \(\mathbb {F}_{p}\) We place the value \(x_{G}\in \mathcal {U}({\Delta };a,x_{G},y_{G})\), so that U0 is not G or − G. Then, clearing denominators in (4),
we obtain
Using the equalities xj = αj + ej and yj = βj + fj for j = 0,1, the polynomial L2 of (6) become:
\( \left (-{\upbeta }_{1}-y_{G}\right )e_{0}+\left (x_{G}-\alpha _{1}\right )f_{0}+\left (y_{G}-{\upbeta }_{0}\right )e_{1}+\left (x_{G}-\alpha _{0}\right )f_{1}-[e_{0}f_{1}+e_{1}f_{0}] =\)
Now, we linearize this polynomial system. Writing
is it easy to check that the vector
is a solution to the following linear system of congruences:
Moreover, bounds (9) implies E is a relatively short vector. We have:
Let \({{\mathscr{L}}}\) be the lattice consisting of integer solutions \(\textbf {X}=(X_{1},X_{2},\ldots ,X_{5})\in {\mathbb {Z}}^{5}\) of the system of congruences:
We compute a solution T of the system of congruences (12), using linear diophantine equations methods. Applying an algorithm solving the CVP for the shift vector T and the lattice (14), we obtain a vector
We have F = v + T (where v is the lattice vector returned by the CVP algorithm) is the vector of minimal norm satisfying (12), hence F must have norm at most equal to the norm of the solution E. Using the bounds (13), we get:
Note that we can compute F in polynomial time from the information we are given. We might hope that E and F are the same, or at least, that we can recover the approximations errors from F. If not, we will show that x0 belongs to a subset \(\mathcal {U}({\Delta };a,x_{G},y_{G}) \subseteq \mathbb {F}_{p}\) of cardinality \(\# \mathcal {U}({\Delta };a,x_{G},y_{G}) = O({\Delta }^{6})\). Vector D = E −F lies in \({{\mathscr{L}}}\):
Bounds (13) and (15) imply ∥D∥≤ 4Δ2 and
From here, by closely following the proof in [20], since only depends on L2 and Di, we bound the “bad” possibilities for which this process does not succeed. □
We now present some heuristic arguments showing that Theorem 1 could possibly be strengthened so that it becomes nontrivial when the precision Δ is of the order of p1/4 rather than of order p1/6 as currently.
The heuristic that we use is of a totally different nature than that used in the so called Coppersmith’s method, where the heuristic assumption is that all created polynomials define a zero dimension algebraic variety. Here, we use the so-called “Gaussian heuristic” that suggests that and s-dimensional lattice \({\mathscr{L}}\) with volume \(vol({\mathscr{L}})\) is unlikely to have a nonzero vector which is substantially shorter than \(vol({\mathscr{L}})^{1/s}\). Moreover, if it is known that such a very short vector does exist, then up to a scalar factor it is likely to be the only vector with this property.
Let us formalise the problem. Again, we assume that a, b are unknown, but the prime p is given to us. Suppose that we are given k ≥ 2 consecutive Δ −approximations Wj = (αj,βj) to \(U_{j} =(x_{j},y_{j}) \in E({\mathbb {F}}_{p})\) (j = 0,…,k − 1), produced by the EC-LCG, so there exist integers ej, fj with:
Theorem 2
With above notation, under the ‘Gaussian heuristic’ we can recovering the seed U0 in polynomial time in \(\log p\) as soon as \({\Delta } < p^{\frac {k-1}{4k-2}}\) by computing a closest vector of a certain lattice of dimension 3k − 1.
Proof
As in the previous Theorem 1 we use only the polynomial L2 in (6) for a pair of points (Uj,Uj+ 1) for j = 0,…,k − 2. Again, we translate Uj+ 1 = Uj ⊕ G into a polynomial system of equation:
Using the equalities (16) the above polynomial \(L^{(j)}_{2}\), for j = 0,…,k − 2, becomes:
\( \left (-{\upbeta }_{j+1}-y_{G}\right )e_{j}+\left (x_{G}-\alpha _{j+1}\right )f_{j}+\left (y_{G}-{\upbeta }_{j}\right )e_{j+1}+\left (x_{G}-\alpha _{j}\right )f_{j+1}-[e_{j}f_{j+1}+e_{j+1}f_{j}] =\)
Now, we linearize this polynomial system. Writing, for j = 0,…,k − 2 and for i = 0,…,k − 1:
we obtain that vector E =
is a solution to the following linear system of congruences (j = 0,…,k − 2):
Moreover, bounds (16) imply E is a relatively short vector. We have:
Let \({{\mathscr{L}}_{k}}\) be the lattice consisting of integer solutions:
of the system of congruences, (j = 0,…,k − 2):
We compute a solution T of the system of congruences (17), using linear diophantine equations methods. Applying an algorithm solving the CVP for the shift vector T and the lattice (19) we obtain a vector
We have F = v + T (where v is the lattice vector returned by the CVP algorithm) is the vector of minimal norm satisfying (17), hence F must have norm at most equal to the norm of the solution E. Using the bounds (18), we get:
Note that we can compute F in polynomial time from the information we are given, see Lemma 1. We might hope that E and F are the same, or at least, that we can recover the approximations errors from F. The volume of the lattice (19) is pk− 1Δ2k (see Section 2.1) Then, using (20) and Gaussian heuristic vector E is likely to be the one founded whenever \({\Delta }^{2} < p^{\frac {k-1}{3k-1}}{\Delta }^{\frac {2k}{3k-1}}\), this is:
This finishes the proof. □
This time, we did not provide a rigorous proof to bound the number of possibilities for which this method could fail. We will see in Section 5 that our SageMath implementation certifies the above bound.
The following illustrates the importance of knowledge parameter a of the elliptic curve (1).
Remark 1
If three consecutive values of the EC-LCG are given, then can eliminated G from U0 ⊕ G = U1 and U1 ⊕ G = U2:
So, given three Δ −approximations to U0,U1,U2 and, assuming that U0 and U1 are not G or − G and y0y1≠ 0, clearing denominators in (4) and (5) we can translate equation U2 ⊕ U0 = 2U1 into two polynomial identities in the field \({\mathbb {F}}_{p}\), but involving the unknown parameter a.
On the other hand, given the parameters a and b of the elliptic curve (1) and Δ −approximation (α0,β0) to point P = (x0,y0) of the curve we can recover P as soon as Δ < p1/7, see [14, 16].
4 Predicting EC-LCG for unknown composer
In previous section, it has been assumed that the cryptanalyst has access to the composer G, which places his task in a quite optimistic frame. This section is devoted to the case that the parameter G is also private. This case is studied in [20] and also [32] requiring three approximations, no necessarily consecutive, instead of two. They consider the information given as approximations to arbitrary points in the same elliptic curve, in such a way that they are not taking advantage from the knowledge of the procedure which has generated them. In other words, they provide a method to recover three points lying in an elliptic curve in the form (1), given corresponding approximations. And then use that method in the frame of an EC-LCG and three values partially revealed. Both methods are heuristics. In [20] requieres a Δ −approximations such that Δ < p1/46, a better result is presented in [31, 32], which requieres Δ < p1/24. Both methods are looking for small roots of polynomial (7) \(L_{3} \in {\mathbb {F}}_{p}[X_{Q},Y_{Q},X_{P},Y_{P},X_{R},Y_{R}]\).
We assume that approximations to the coordinates of \(G =(x_{G},y_{G}) \in E(\mathbb {F}_{p})\) and also Wn, Wn+ 1 to (respectively) two consecutive affine values Un, Un+ 1 produced by the EC-LCG; we are trying to recover the exact values, provided that the approximations are good enough.
We write \(\bar {G}=(\gamma _{x},\gamma _{y})\) and Wj = (αj,βj), Uj = (xj,yj), for j = 0,1; so there exist integers hx,hy and ej, fj for j = 0, 1 with:
The first attempt to design a such procedure would be, as in the previous Theorem 1, translate (10) into the identity in the fielp \(\mathbb {F}_{p}\) getting
and looking for small roots of L2. However, Lemma 2-(2) shows it is no possible recovering the seed. Neither from L1 ≡ 0 mod p, again by Lemma 2-(2). So, we have to involve both polynomials:
First, we rigorously demonstrate how recovering only abscissa coordinates if Δ < p1/6.
Lemma 3
With the above notations and definitions, there exists a set \(\mathcal {U}({\Delta }){\subseteq \mathbb {F}_{p}^{6}}\) of cardinality \(\# \mathcal {U}({\Delta }) = O(p^{5}{\Delta }^{6})\) with the following property: whenever P = (xG,yG,x0,y0, \(x_{1},y_{1}) \not \in \mathcal {U} ({\Delta })\) then, given Δ −approximation
to point P and given the prime p, one can recover xG,x0,x1 in deterministic polynomial time by computing a closest vector of a certain lattice of dimension 5.
Proof
First, we place all points of the form \((x_{0},y_{G},x_{0},x_{1},y_{0},y_{1}) \in \mathcal {U}({\Delta })\), so that U0 is not G or − G. We write L2 as
Taking W0 = YP + YR,V0 = XQ − XP,W1 = YP − YQ,V1 = XP − XR, we consider polynomial \(\bar {L}_{2} \in \mathbb {F}_{p}[W_{0},W_{1},V_{0},V_{1}]\):
We write
From (21), we obtain (β0 + β1,γx − α1,β1 − γy,α0 − α1) = (b0,a0,b1,a1) is 2Δ-approximation to the root \((w_{0},v_{0},w_{1},v_{1}) \in {{\mathbb {F}}_{p}^{4}}\) of \(\bar {L}_{2}\). So, rewriting the (21) and (22):
The polynomial \(\bar {L}_{2} \in \mathbb {F}_{p}[W_{0},W_{1},V_{0},V_{1}]\) becomes:
Writing:
we obtain that vector
is a solution to the following linear system of congruences:
Moreover, bounds (23) imply E is a relatively short vector. We have:
Let \({{\mathscr{L}}}\) be the lattice consisting of integer solutions \(\textbf {X}=(X_{1},X_{2},\ldots ,X_{5})\in {\mathbb {Z}}^{5}\) of the system of congruences:
We compute a solution T of the system of congruences (24), using linear diophantine equations methods. Applying an algorithm solving the CVP for the shift vector T and the lattice (26), we obtain a vector
F = (ΔF1,ΔF2,ΔF3,ΔF4,F5)
We have F = v + T (where v is the lattice vector returned by the CVP algorithm) is the vector of minimal norm satisfying (24), hence F must have norm at most equal to the norm of the solution E. Using the bounds (25), we get:
Note that we can compute F in polynomial time from the information we are given. We might hope that E and F are the same, or at least, that we can recover the approximations errors from F. If not, we will show that (xG,yG,x0,y0,x1,y1) belongs to a subset \(\mathcal {U}({\Delta }) \subseteq {\mathbb {F}_{p}^{6}}\) of cardinality \(\# \mathcal {U}({\Delta }) = O(p^{5}{\Delta }^{6})\).
Vector D = E −F lies in \({{\mathscr{L}}}\):
Bounds (25) and (27) imply \(\| \textbf D \| \le 8\sqrt {2} {\Delta }^{2} \) and
Now, we distinguish two cases:
-
1.
Di ≡ 0 mod p,i = 1,…,4,
-
2.
Di is nonzero for some i,i = 1,…,4
In the first case, we can recover the root (w0,v0,w1,v1) of the polynomial \(\bar {L}_{2}(W_{0},V_{0},\) W1,V1), then by (22), we have
Substituting those equalities into (6) polynomial L1 and since xG≠x0, that is v0≠ 0, then by Lemma 2-(1) we can recover xG,x0,x1.
Hence, we may assume that Di is nonzero for some i,i = 1,…,4. Substituting bj = Wj − ej,aj = Vj − fj,j = 0,1 in the first equation of lattice (26), we obtain a nonzero polynomial: G = G(W0,V0,W1,V1) =
whose coefficients are in \(\mathbb {Z}[D_{i}, e_{j},f_{j}]\), for i = 0,…,5 and j = 0,1 and such that:
For every choice of Di,ej,fj, for i = 0,…,5 and for j = 0,1, the specialised \(\bar {G}(W_{0},W_{0},W_{1},V_{1}) \in \mathbb {F}_{p}[(W_{0},W_{0},W_{1},V_{1})]\) is a linear polynomial, so the number of solutions in \({\mathbb {F}_{p}^{4}}\) is exactly p3. Now, for every zero (w0,v0,w1,v1) of \(\bar {G}\) we have exactly p2 points of the form (y0 + y1,xG − x0,y0 − yG,x0 − x1). In total we have p5 points \((x_{G},y_{G},x_{0},x_{1},y_{0},y_{1}) \in {{\mathbb {F}}_{p}^{6}}\) such that L2(xG,yG,x0,x1,y0,y1) ≡ 0 mod p, we place all of then into the set \({\mathcal {U}}({\Delta }){\subseteq {\mathbb {F}}_{p}^{6}}\). We need to show that the cardinality of \({\mathcal {U}}({\Delta })\) is as claimed in the statement of the theorem. In other words, we need to prove that for every choice of Di,ej,fj, (i = 0,…,5 and j = 0,1), the number of non zero specialized polynomials \(\bar {G}(W_{0},W_{0},W_{1},V_{1}) \in {\mathbb {F}}_{p}[(W_{0},W_{0},W_{1},V_{1})]\) are bounded by O(Δ6).
We write
where C ≡ D5 − (e0D1 + f0D2 + e1D3 + f1D4) mod p. By (28) the number of possible choices for D1,D2,D3,D4 is O(Δ4). On the other hand, C can take O(Δ2) distinct values, because from bounds (23) and (28) we obtain that \(D_{5}-(e_{0}D_{1}+f_{0}D_{2}+e_{1}D_{3}+f_{1}D_{4})=O({\Delta }^{2})\). So, the number of nonzero polynomials G are bound by O(Δ6), which finishes the proof. □
The above result also finds the values U = y0 + y1 and V = y0 − yG. Plugging y1 = −y0 + U and yG = y0 + V to polynomial L3 defined in (7), then from (8) we have
So, we cannot recover yG,y0,y1 from L3.
On the other hand, substituting y1 = −y0 + U and yG = y0 + V in the elliptic curve (1):
We can derive a linear equation in a and y0:
Now, we can recover a and y0 if a0 is 𝜖-approximation to a with 𝜖 < p1/2 using the same lattice technique’s.
As previous remark, we can also obtain from (4) a linear equation in b and quadratic in y0
where \(A,B,C \in \mathbb {Z}[x_{0},x_{1},x_{G},U,V]\) and A,B,C≢0 mod p. Again, we can recover b and y0 if b0 is 𝜖-approximation to b as soon as 𝜖 < p1/3.
Then, as consequence of Lemma 3 we have the following:
Corollary 1
With the above notations and definitions, there exists a set \(\mathcal {U}({\Delta }){\subseteq \mathbb {F}_{p}^{6}}\) of cardinality \(\# \mathcal {U}({\Delta }) = O(p^{5}{\Delta }^{6})\) with the following property: whenever P = (xG,yG,x0, \(y_{0},x_{1},y_{1}) \not \in \mathcal {U} ({\Delta })\) then, given Δ −approximation to U0 = (x0,y0),U1(x1,y1) and to G = (xG,yG) and 𝜖 −approximation to a with 𝜖 < p1/2 or an 𝜖 −approximation to b with 𝜖 < p1/3 one can recover the sequence produced EC-LCG in deterministic polynomial time.
Previous result it has been assumed that we have access to approximations to elliptic curve (1) parameters a or b, which again places this task in a quite optimistic frame.
Then suppose Δ-approximations to U0 = (x0,y0), U1 = (x1,y1) and U2 = (x2,y2) points generated by the EC-LCG and to G = (xG,yG) then applying Lemma 3 to equation U0 ⊕ G = U1 we recovering (xG,x0,x1) and also
Again applying the same Lemma 3 but in this case to equation U1 ⊕ G = U2, we are able to recovering xG,x1,x2 and
as soon as Δ < p1/6. We obtain the following linear system of equation in \(\mathbb {F}_{p}\):
Since \(\det \left (\begin {array}{rrrr}-1 &1 &0 &0 \cr 0 &1 &1 &0 \cr 0 & 0 &1 &1 \cr -1 &0 &1 &0 \end {array}\right )=1\) it has a unique solution and we can recovering all the missing information.
Theorem 3
With the above notations and definitions, there exists two sets \(\mathcal {U}({\Delta }){\subseteq \mathbb {F}_{p}^{6}}\) and \(\mathcal {V}({\Delta }){\subseteq \mathbb {F}_{p}^{6}}\) both the cardinality O(p5Δ6) with the following property: whenever \(P=(x_{G},y_{G}, x_{0},y_{0},x_{1},y_{1}) \not \in {\mathcal {U}} ({\Delta })\) and \(Q=(x_{G},y_{G}, x_{1},y_{1},x_{2},y_{2}) \not \in {\mathcal {V}} ({\Delta })\) then, given Δ −approximation to U0 = (x0,y0), U1(x1,y1),U2 = (x2,y2) and to G = (xG,yG), one can recover the whole sequence produced by EC-LCG in deterministic polynomial time.
Notice that we can not applies Remark 1 because the parameter a of the elliptic curve (1) is unknown.
On one hand the previous result requires computing a closest vector of two distinct lattices. On the other hand, it would be interesting attacking EC-LCG when we have access to several consecutive approximations and having an approximation to composer G. The following result try to answer those interesting computational problems.
Let us formalise the problem. Again, we assume that a, b and the composer G are unknown, but we have a Δ −approximation \(\bar {G}=(\gamma _{x},\gamma _{y})\) to G = (xG,yG). Suppose that we are given k + 1 ≥ 2 consecutive Δ −approximations Wj = (αj,βj) to \(U_{j} =(x_{j},y_{j}) \in E({\mathbb {F}}_{p})\) (j = 0,…,k − 1), produced by the EC-LCG, so there exist integers hx,hy and ej, fj with:
Theorem 4
With above notation, under the ‘Gaussian heuristic’ we can recovering the whole sequence (2) in polynomial time in \(\log p\) as soon as \({\Delta } < p^{\frac {k-1}{5k-4}}\) by computing the closest vector of a certain lattice of dimension 4k − 3.
Proof
For every pair of points of the form Ui− 1 = (xi− 1,yi− 1),Ui = (xi,yi),i = 1,…,k − 1, we denote by
By Ui− 1 ⊕ G = Ui, we have \(\bar {L}_{2}^{(i)}(w_{i},s_{i},v_{i},t_{i}) \equiv 0 \bmod p\) and we obtain the following system of congruences:
From (29), we have
is 2Δ-approximation to the root (wi,si,vi,ti) of \(\bar {L}^{i}_{2}\). So, rewriting the (29)
Using the equalities (30) the polynomial \(\bar {L}^{(i)}_{2}\) becomes:
Since \(\bar {m}_{i}= h_{x}-e_{i-1}= \bar {m}_{i-1}+ \bar {e}_{i-1}\), writing \(\bar {e}_{0} =0\) and \(\bar {m}_{1} =\bar {m}\) then polynomial \(\bar {L}^{(i)}_{2}\) for i = 1,…,k − 1 becomes:
Now, we linearize this polynomial system. Writing, for i = 1,…,k − 1 and for j = 1,…,k − 1:
we obtain that vector E =
is a solution to the following linear system of congruences (i = 1,…,k − 1):
Moreover, from (30) we have E is a relatively short vector. We have:
Let \({{\mathscr{L}}_{k}}\) be the lattice consisting of integer solutions
of the system of congruences, (i = 0,…,k − 1):
We compute a solution T of the system of congruences (31), using linear diophantine equations methods. Applying an algorithm solving the CVP for the shift vector T and the lattice (33), we obtain a vector
We have F = v + T (where v is the lattice vector returned by the CVP algorithm) is the vector of minimal norm satisfying (31), hence F must have norm at most equal to the norm of the solution E. Using the bounds (32), we get:
Note that we can compute F in polynomial time from the information we are given, see Lemma 1. We might hope that E and F are the same, or at least, that we can recover the approximations errors from F. This time, we are not giving a rigorous proof to bound the number of possibilities for which this method could fail. The volume of the lattice (33) is pk− 1Δ3k− 2 (see Section 2.1) Then, by Gaussian heuristic and (34) vector E is likely to be the one founded whenever \({\Delta }^{2} < p^{\frac {k-1}{4k-3}}{\Delta }^{\frac {3k-2}{4k-3}}\), this is:
□
As we can see, if k = 3, we obtain from Theorem 4 that O(Δ) = p2/11 which is an improvement of Theorem 3.
5 Numerical results
We have proposed algorithms to recover a sequence of pseudorandom numbers produced by EC-LCG. The input required by all of them include approximations to some pseudorandom values. The first Theorem 1 and the second one Theorem 2 requires additionally precise knowledge of the parameter G. The rest require an approximation to the composer G. The quality of those approximations is the measure used to characterise when the algorithms output the expected sequence.
In Theorem 1 a “bad” set of values for the components x0 is described, proving that whenever that value lies outside the set, the algorithm works correctly. Furthermore, the size of the set is asymptotically bounded with O(Δ6). This means that if Δ < p1/6 and p is large enough, assuming a uniform distribution of probabilities for \(x_{0}\in \mathbb {F}_{p}\), the method is unlikely to fail. The same applies in Theorem 3 where the two “bad” subsets of \({{\mathbb {F}}_{p}^{6}}\) are asymptotically bounded with O(p5Δ6), again it means that if Δ < p1/6 and p is large enough the method is unlikely to fail.
In Theorem 2 the heuristic algorithm requires k consecutive Δ −approximations with \({\Delta } < p^{\frac {k-1}{4k-2}}\) when G is public. Finally, the heuristic method described in Theorem 4 when an approximation to composer G and k consecutive Δ −approximations are given recovering the whole sequence if \({\Delta } < p^{\frac {k-1}{5k-4}}\)
However, two aspects must be taken into account before considering those bounds as the threshold for the error tolerance upon which the algorithms fail. On the one side, the constants hidden in the asymptotic reasoning (namely, the size of the prime p). On the other one, the threshold could be higher, as the “bad” set does not guarantee that the methods indeed fails.
We have performed some numerical tests with a SageMath implementation of all methods. Firstly, we generate an elliptic curve over a prime finite field of a desired size by chossing randomly in \({\mathbb {F}}_{p}\) parameters a, b to fix (1). Then, we generate randomly points in the curve (1). For several pairs of points, an EC-LCG is simulated, and approximations to some consecutive values are given as input to our algorithms.
size_prime = 1024 p=next_prime(ZZ.random_element(2**size_prime)) a=ZZ.random_element(p); b=ZZ.random_element(p) if (4*a**3+27*b**2) C =EllipticCurve(GF(p),[a,b]) G=C.random_element(); U_0=C.random_element() U_1= U_0 + G d=int(p**(0.14)) # We use the ZZ.random_element SageMath method ZZ.random_element(-d+int(U_1[0]), d+int(U_1[0]))
And it is certified that both heuristic and deterministic methods confirm the obtained bounds. We show the numerical results of the heuristic algorithms, which, on the other hand, also include the deterministic ones. We summarize its results in the following tables. We have selected primes of several sizes, and note the obtained success threshold.
-
Theorem 2: Δ −approximations to k consecutive values and G public.
-
\(k=2, {\Delta }=O(p^{1/6}), \frac {1}{6}= 0.16666\). Lattice dimension: 5.
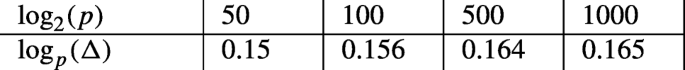
-
\(k=3, {\Delta }=O(p^{1/5}), \frac {1}{5}= 0.2 \). Lattice dimension: 8

-
\(k= 13, {\Delta }=O(p^{6/25}), \frac {6}{25}= 0.24 \). Lattice dimension: 38

-
-
Theorem 4: Δ −approximation to G and to k consecutive values.
-
\(k=3, {\Delta }=O(p^{2/11}), \frac {2}{11}= 0.1818 \). Lattice dimension: 9
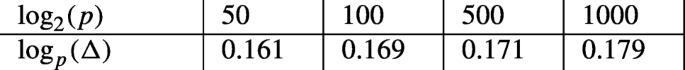
-
\(k= 13, {\Delta }=O(p^{12/61}), \frac {12}{61}= 0.1967 \). Lattice dimension: 49

-
We have implemented the attack in SageMath-8.1 on a MacBook Pro laptop computer (3,3 GHz Intel Core i7, 16 GB RAM 2133 MHz LPDDR3 Mac OSX 10.12.6). Since the lattice dimension is very low -the biggest one is 49 which correspond the case k = 13 in Theorem 4- the time consuming in any trail is, as maximum, a couple of seconds.
6 Remarks and open questions
We have presented efficient algorithms for predicting the sequence produced by the linear congruential generator on elliptic curves. In fact, they only require computing a closest vector for a lattice of very low dimension, and for practical purposes can be used Babai’s Nearest Plane algorithm, see [2].
Following the ideas in [9] by generating more non-linear equations by multiplication of several non-linear equations before the linearization step, papers [31] and [32] present theoretical better bound O(p1/5) for Theorem 1 and \(O(p^{\frac {3k}{11k+4}})\) for Theorem 2, under the heuristic assumption that the created polynomials define a zero dimensional ideal. Their algorithm need to compute the LLL algorithm of a certain lattice of huge dimension and, after that, it also requires a Groebner Basis computation or alternatively any other elimination polynomial method. In practice the performance of the so called of Coppersmith’s methods in those cases are very bad because of large dimension of the lattice as it is shown in that papers. In fact, they can not test the bound \(O(p^{\frac {3k}{11k+4}})\) not only because the large dimension but the size of the prime p should be several hundreds of bits. On the other hand, for instance, we can recover the sequence produced by EC-LCG if only three consecutive Δ −approximations are given as soon as Δ < p1/5 requiring, the most time consuming, to compute a closest vector for a lattice of dimension 7 and it it matched by primes p of only 1000 bits.
As papers [31] and [32] show the bound of the size of the set of exceptional values of u0 given in Theorem 1 is not tight and might be improved by more careful examination of the structure of (4) and (5) and this applies to Theorem 2.
Obviously the result in Theorem 3 is nontrivial only for Δ = O(p1/6), we believe that this can be improvement to Δ = O(p2/11) as Theorem 4 shows.
Giving rigorous proofs of our heuristic Theorem 2 and Theorem 4 is a challenging open question as well.
Same question has been studied in [32] for the Power Generator on elliptic curves: for a positive integer e > 1 and a point \(G \in E(\mathbb {F}_{p})\) of order l with \(\gcd (e,l)=1\), the elliptic curve Power Generator, (see [29]) generate a sequence of points Vn defined by the relation
Requiring the prime p, integer e, constants a and b of the elliptic curve (1), and Δ −approximations W0,W1 to two consecutive values V0,V1 for \({\Delta } < p^{\frac {1}{2e^{2}}}\). An improvement is presented in [14] recovering the root U0 = (x0,y0) of the polynomial (1) from a Δ −approximation to (x0,y0) as soon as Δ < p1/7, considering the information given as approximation to the seed, in such a way that it is not taking advantage from the knowledge of the procedure which has generated them, see also [16]. We also think that better bounds are expected.
Another open problem is to mount an attack when the modulo p is unknown. Unfortunately, we do not know how to predict the EC-LCG when the modulus p is secret.
Finally, it would be interesting to study the security other PRBG based on elliptic curves under these type of attacks. In particular, it is not clear how to mount an attack based on the lattices to the Naor-Reingold Generator on Elliptic curves, see [36, 41, 42].
References
Avanzi, R., Cohen, H., Doche, C., Frey, G., Lange, T., Nguyen, K.K.: Elliptic and hyperelliptic curve crytography: Theory and practice. CRC Press (2005)
Babai, L.: On lovasz lattice reduction and the nearest lattice point problem. Combinatorica 6, 1–6 (1986)
Beelen, P., Doumen, J.: Pseudorandom Sequences from Elliptic Curves. Finite Fields with Applications to Coding Theory Cryptography and Related Areas, pp 37–52. Springer, Berlin (2002)
Blackburn, S., Gomez-Perez, D., Gutierrez, J., Shparlinski, I.: Predicting nonlinear pseudorandom number generators. Math. Comput. 74, 1471–1494 (2005)
Blake, I., Seroussi, G., Smart, N.: Elliptic curves in cryptography. London Math. Soc., Lecture Note Series, vol. 265. Cambridge Univ Press (1999)
Bloemer, J., May, A.: A tool kit for Finding small roots of Bivariate Polynomial over the Integers. Advances in Cryptology-Crypt. LNCS 2729, pp. 27–43. Springer (2003)
Boyar, J.: Inferring sequences produced by pseudo-random number generators. J. ACM 36, 129–141 (1989)
Brickell, E., Odlyzko, A.M.: Cryptanalysis: A survey of recent results. Contemp. cryptology, pp. 501–540. IEEE Press, NY (1992)
Coppersmith, D.: Small solutions to polynomial equations and low exponent RSA vulnerabilities. J. Cryptol. 10(4), 233–260 (1997)
Coppersmith, D.: Finding a Small Root of a Bivariate Integer Equations; Factoring with High Bits Known’. In: Maurer, U. (ed.) Proc. EUROCRYPT-96, LNCS 1070,155–156. Springer, Berlin (1996)
Coron, J. S.: Finding small roots of Bivariate Integer Polynomial Equations Revisted. Proc. Advances in Cryptology- Eurocrypt’04, LNCS, 3027, pp. 492–505. Springer (2004)
El Mahassni, E., Shparlinski, I.: On the Uniformity of Distribution of Congruential Generators over Elliptic Curves. Proc. Intern. Conf. on Sequences and Their Applications, 257–264 Bergen 2001. Springer, London (2002)
Frieze, A., Håstad, J., Kannan, R., Lagarias J. C., Shamir, A.: Reconstructing truncated integer variables satisfying linear congruences. SIAM J. Comp. 17, 262–280 (1988)
Gutierrez, J.: Reconstructing Points of Superelliptic Curves over a Prime Finite Field, Preprint. University of Cantabria (2021)
Gomez-Perez, D., Gutierrez, J., ibeas, A.: Attacking the Pollard Generator. IEEE. Trans. Inf. Theory. 52(12), 5518–5523 (2006)
Gomez-Perez, D., Gutierrez, J.: Recovering zeros of polynomials modulo a prime’. Math. Comput. 83(290), 2953–2965 (2014)
Gong, G., Berson, T., Stinson, D.: Elliptic Curve Pseudorandom Sequence Generators. Lect. Notes in Comp. Sci., vol. 1758, pp. 34–49. Springer, Berlin (2000)
Gong, G., Lam, C.: Linear recursive sequences over elliptic curves. Proc. Intern. Conf. on Sequences and their Applications, Bergen 2001, pp. 182-196. Springer, London (2002)
Grötschel, M., Lovász, L., Schrijver, A.: Geometric Algorithms and Combinatorial Optimization. Springer, Berlin (1993)
Gutierrez, J., Ibeas, A.: Inferring sequences produced by a linear congruential generator on elliptic curves missing high-order bits. Des. Codes Cryptogr. 45(2), 199–212 (2007)
Hallgren, S.: Linear congruential generators over elliptic curves. Preprint CS-94-143, pp. 1–10. Dept. of Comp. Sci. Cornegie Mellon University (1994)
Hess, F., Shparlinski, I.: On the linear complexity and multidimensional distribution of congruential generators over elliptic curves. Des. Codes Cryptogr. 35, 111–117 (2005)
Joux, A., Stern, J.: Lattice reduction: a toolbox for the cryptanalyst. J. Cryptol. 11, 161–185 (1998)
Jochemz, E., May, A.: A Strategy for Finding Roots of Multivariate Polynomials with New Applications in Attacking RSA Variants Advances in Cryptology (Asiacrypt 2006), Lecture Notes in Computer Science. Springer (2006)
Kannan, R.: Minkowski’s convex body theorem and integer programming. Math. Oper. Res. 12, 415–440 (1987)
Knuth, D.: Deciphering a linear congruential encryption. IEEE Trans. Inf. Theory. 31, 49–52 (1985)
Krawczyk, H.: How to predict congruential generators. J. Algorithm. 13, 527–545 (1992)
Lagarias, J.: Pseudorandom number generators in cryptography and number theory, vol. 42, pp. 115–143. Proc. Symp. in Appl. Math. Amer. Math. Soc., Providence (1990)
Lange, T., Shparlinski, I.: Certain exponential sums and random walks on elliptic curves. Canad. J. Math. 57, 338–350 (2005)
Lenstra, A., Lenstra, H., Lovász, L.: Factoring polynomials with rational coefficients. Math. Annalen. 261, 515–534 (1982)
Mefenza, T.: Inferring sequences produced by a linear congruential generator on elliptic curves using coppersmith’s methods. COCOON 2016 LNCS, vol. 9797, pp .293–304 (2016)
Mefenza, T., Vergnaud, D.: Inferring sequences produced by a elliptic Curves generators y using Coppersmith’s methods. Theor. Comput. Sci. 280, 20–42 (2020)
Meidl, W., Winterhof, A.: Linear Complexity of sequences and multisequences. , pp. 324–334. Handbook of Finite Fields, CRC Press, Taylor and Francis, Group. edits G. Mullen and D. Panario (2013)
Mérai, L.: Remarks on pseudorandom binary sequences over elliptic curves. Fund. Inf. 114(3-4), 301–308 (2012)
Mérai, L.: Predicting the elliptic curve congruential generator. Applicable Algebra in Engineering. Commun. Comput. 28(3), 193–203 (2017)
Naor, M., Reingold, O.: Number theoretic constructions of efficient pseudo-random functions. Proc 38th IEEE Symp. on Found. of Comp. Sci., pp. 458–467. IEEE (1997)
Niederreiter, H.: Design and Analysis of Nonlinear Pseudorandom Number Generators. In: Schueller, G.I., Spanos, P. D. (eds.) Monte Carlo Simulation, pp 3–9. A. Balkema Publishers, Rotterdam (2001)
Shparlinski, I.: Cryptographic applications of analytic number theory. Birkhauser (2003)
Shparlinski, I.: Orders of points on elliptic curves. Affine Algebraic Geometry. Amer. Math. Soc., pp. 245–252 (2005)
Shparlinski, I.: Pseudorandom Points on Elliptic Curves over Finite Fields. Recent trends in Cryptography. Contemporary Mathematics, v.477, Amer.Math. Soc., pp. 121–141 (2009)
Shparlinski, I: On the Naor-Reingold pseudo-random function from elliptic curves. Appl. Algebra Engin. Commun. Comput. 11, 27–34 (2000)
Shparlinski, I., Silverman, J.: On the linear complexity of the Naor-Reingold pseudorandom function from elliptic curves. Des. Codes Cryptogr. 24, 279–289 (2001)
Silverman, J.: The Arithmetic of Elliptic Curves. Springer, Berlin (1995)
Sun, H., Zhu, X., Zheng, Q.: Predicting truncated multiple recursive generators with unknown parameters. Des. Codes Cryptogr., pp. 1–20 (2020)
Winterhof, A.: Recent results on recursive nonlinear pseudorandom number generators. (Invited Paper). SETA 2010: 113–124 (2010)
Acknowledgements
The author wishes to thank Arne Winterhof for reading and commenting on a draft version.
Funding
Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Gutierrez, J. Attacking the linear congruential generator on elliptic curves via lattice techniques. Cryptogr. Commun. 14, 505–525 (2022). https://doi.org/10.1007/s12095-021-00535-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-021-00535-6