Abstract
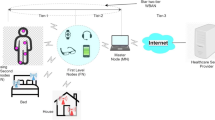
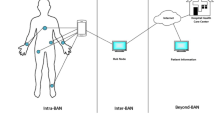
In the medical field, a wearable body area network is a wireless network in which wearable sensors are implemented in or on patients' bodies to gather their sensitive health information and send it to the medical servers accordingly. These multi-functional sensors provide all users with optimized and convenient services, such as homecare monitoring of people’s health conditions. Ensuring the privacy of users' information during its transfer between users and medical personnel necessitates a secure wireless environment. Mobility and insecure communication channels introduce a substantial threat from unauthorized entities, jeopardizing the privacy of the transferred information within this network. To mitigate this risk, researchers have proposed various authentication and key agreement schemes, aiming to enhance the safety of the communication channel and preserve user privacy. Additionally, the wearable body area network comprises resource-constrained devices, emphasizing the need for lightweight protocols to guarantee the transmitted information's authenticity, confidentiality, and integrity. Ankur Gupta and his colleagues recently proposed a mutual authentication and key agreement protocol and proved its security against well-known attacks. However, after in-depth analysis, we discovered that their proposed protocol is vulnerable to sensor node impersonation and sensor node capture attacks. In this paper, we propose a new lightweight mutual authentication and key agreement scheme in WBAN based on basic symmetric cryptosystems (Exclusive OR and Hash functions) to overcome the security weaknesses in Gupta's protocol and provide indispensable security for communicating data. Unlike Gupta’s protocol, our proposed scheme is safe in the CK-adversary threat model. The security of the presented scheme is evaluated using BAN-Logic, the AVISPA tool, and the Real or Random (ROR) model. Overall, the performance comparison of the proposed protocol with the existing related protocols depicts that our new scheme is more efficient than others in terms of communication and computational complexities.





Similar content being viewed by others
Data availability
Not applicable.
References
Gupta A, Tripathi M, Sharma A (2020) A provably secure and efficient anonymous mutual authentication and key agreement protocol for wearable devices in WBAN. Comput Commun 160:311–325. https://doi.org/10.1016/j.comcom.2020.06.010. (ISSN01403664)
Xu Z, Xu C, Liang W, Xu J, Chen H (2019) A lightweight mutual authentication and key agreement scheme for medical Internet of Things. IEEE Access 7:53922–53931
Narwal B, Mohapatra AK (2021) A survey on security and authentication in wireless body area networks. J Syst Archit 113:101883
Almuhaideb AM, Alqudaihi KS (2020) A lightweight and secure anonymity preserving protocol for WBAN. IEEE Access 8:178183–178194
Shi L, Yuan J, Yu S, Li M (2013) ASK-BAN: authenticated secret key extraction utilizing channel characteristics for body area networks. In: Proceedings of the sixth ACM conference on Security and privacy in wireless and mobile networks, pp 155–166
Xu Z et al (2019) A lightweight anonymous mutual authentication and key agreement scheme for WBAN. Concurr Comput: Pract Exp 31.14:e5295
Liu J et al (2014) Certificateless remote anonymous authentication schemes for wireless body area networks. IEEE Trans Parallel Distrib Syst 25(2):332–342
He D, Zeadally S, Kumar N, Lee JH (2016) Anonymous authentication for wireless body area networks with provable security. IEEE Syst J 11(4):2590–2601
Drira W, Renault É, Zeghlache D (2012) A hybrid authentication and key establishment scheme for wban. In: 2012 IEEE 11th international conference on trust, security and privacy in computing and communications. IEEE, pp 78–83
Li X, Ibrahim MH, Kumari S, Sangaiah AK, Gupta V, Choo K-KR (2017) Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput Netw 129:429–443
Koya AM, Deepthi PP (2018) Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput Netw 140:138–151
Chen C-M et al (2018) An anonymous mutual authenticated key agreement scheme for wearable sensors in wireless body area networks. Appl Sci 8.7:1074
Ostad-Sharif A, Nikooghadam M, AbbasinezhadMood D (2019) Design of a lightweight and anonymous authenticated key agreement protocol for wireless body area networks. Int J Commun Syst 32(12):e3974
Kompara M, Islam SKH, Hölbl M (2019) A robust and efficient mutual authentication and key agreement scheme with untraceability for WBANs. Comput Netw 148:196–213
Ibrahim MH et al (2016) Secure anonymous mutual authentication for star two-tier wireless body area networks. Comput Methods Programs Biomed 135:37–50
Narwal B, Mohapatra AK (2021) SAMAKA: secure and anonymous mutual authentication and key agreement scheme for wireless body area networks. Arab J Sci Eng 469:9197–9219
Dolev D, Yao AC (1983) On the security of public key protocols. IEEE Trans Inf 29(2):198–208
Canetti R, Krawczyk H (2001) Analysis of key-exchange protocols and their use for building secure channels. In: Advances in cryptology–EUROCRYPT 2001. Springer, Innsbruck, pp 453–474
Wang C et al (2020) Understanding node capture attacks in user authentication schemes for wireless sensor networks. IEEE Trans Dependable Secure Comput 19.1:507–523
Burrows M, Abadi M, Needham R (1989) A logic of authentication. R Soc Lond Math Phys Eng Sci 426:233–271
Abdalla M, Fouque PA, Pointcheval D (2005) Password-based authenticated key exchange in the three-party setting. In: Proceedings of the international workshop on public key cryptography. Springer, Berlin, pp 65–84
Reddy AG, Das AK, Odelu V, Ahmad A, Shin JS (2019) A privacy preserving threefactor authenticated key agreement protocol for client–server environment. J Ambient Intell Humaniz Comput 10(2):661–680. https://doi.org/10.1007/s12652-018-0716-4
Srinivas J, Das AK, Kumar N, Rodrigues J (2018) Cloud centric authentication for wearable healthcare monitoring system. IEEE Trans Dependable Secure Compute1. https://doi.org/10.1109/TDSC.2018.2828306
Park K, Park Y, Park Y, Das AK (2018) 2PAKEP: provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 6:30225–30241
Zhang L et al (2019) A lightweight authentication scheme with privacy protection for smart grid communications. Futur Gener Comput Syst 100:770–778
Sadhukhan D et al (2021) A secure and privacy preserving lightweight authentication scheme for smart-grid communication using elliptic curve cryptography. J Syst Archit 114:101938
Nikoomoghadam M et al (2021) A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J Syst Archit 115:101955
Reddy A, Das AK, Odelu V, Ahmad A, Shin JS (2019) A privacy preserving three-factor authenticated key agreement protocol for client–server environment. J Ambient Intell Humaniz Comput. 10. https://doi.org/10.1007/s12652-018-0716-4
Sahu AK, Sharma S, Nanda A (2020) A secure lightweight mutual authentication and key agreement protocol for healthcare systems. In: Intelligent Data security solutions for e-health applications. Elsevier, pp 293–308
AVISPA-Automated Validation of Internet Security Protocols and Applications. [Online]. Available: http://www.avispa-project.org
HLPSL Tutorial- A Beginner’s Guide to Modeling and Analyzing Internet Security Protocols. [Online]. Available: http://www.avispa-project.org
Fotouhi M et al (2020) A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput Netw 177:107333
Funding
There was no funding.
Author information
Authors and Affiliations
Contributions
The idea of the attack is presented by farokhlagha moazami. The new scheme is designed by saba marandi and amire malekinejad and is checked by farokhlagha moazami. The security of the presented scheme is evaluated using BAN-Logic by Amir and using the AVISPA tool by Saba, and in the Real or Random (ROR) model by Farokhlagha. All the authors contributed with each other to write the paper.
Corresponding author
Ethics declarations
Ethics approval
We admit that:
a) This manuscript has not been submitted for publication anywhere, completely or in part, and it will not be submitted until a decision has been made by “peer to peer networking and applications”.
b) This manuscript presents original material which has not been previously published, completely or in part, in another journal.
Consent to publish
The authors have consented to the submission of the case report to the journal.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on 2 - Track on Security and Privacy
Guest Editor: Rongxing Lu
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Marandi, S., Moazami, F. & Malekinezhad, A. A lightweight and anonymous mutual authentication and key agreement scheme for WBAN. Peer-to-Peer Netw. Appl. 17, 2555–2571 (2024). https://doi.org/10.1007/s12083-024-01686-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-024-01686-y