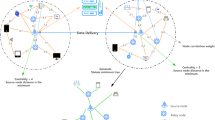
Abstract
Opportunistic social network enables users to form an instant network for information sharing, which is a type of multi-hop wireless network in nature, thus relies on cooperation between nodes to complete message transmission. At present, most traditional routing algorithms require relay nodes to unconditionally forward received data. However, due to the limited of network resources, not all nodes are willing to forward data for other nodes, which is manifested as refusing to accept or even discarding messages, leading to deterioration of network performance. In this regard, this paper proposes an effective positive transmission routing algorithm (EPTR) based on social relationships in opportunistic social networks. This technology optimizes the method of community division by modularity, which not only considers the tightness of networks, but also discusses the social attributes of nodes. In this scheme, nodes with high relationship strength are selected to participate in data forwarding process, which makes packets are transmitted in the direction of increasing forwarding capability of nodes to the destination community. Simulation results show that the proposed algorithm can discover most abnormal nodes including malicious nodes and selfish nodes. Besides, compared with EIMCT algorithm, ITPCM algorithm and Spray and Wait algorithm, the proposed scheme has the highest transmission success rate and the lowest network load.





















Similar content being viewed by others
References
Dede J, Förster A, Hernández-Orallo E, Herrera-Tapia J, Kuladinithi K, Kuppusamy V, Manzoni P, bin Muslim A, Udugama A, Vatandas Z (2018) Simulating opportunistic networks: survey and future directions. IEEE Commun Surv Tutor 20:1547– 1573
Trifunovic S, Kouyoumdjieva ST, Distl B, Pajevic L, Karlsson G, Plattner B (2017) Decade of research in opportunistic networks: challenges, relevance, and future directions. IEEE Commun Mag 55:168–173
Roy A, Deb T (2018) Performance comparison of routing protocols in mobile ad hoc networks. Int J Eng Sci Technol 2: 279
Wang Y, Liu Y, Zhang J, Ye H, Tan Z (2017) Cooperative store-carry-forward scheme for intermittently connected vehicular networks. IEEE Trans Veh Technol 66:777–784
Yan Y, Chen Z, Wu J, Wang L, Liu K, Wu Y (2019) Effective data transmission strategy based on node socialization in opportunistic social networks. In: IEEE Access, vol 7, pp 22144–22160
Lenando H, Alrfaay M (2826) Epsoc: Social-based epidemic-based routing protocol in opportunistic mobile social network. Mob Inf Syst 2018(646):2018
Tuncer D, Sourlas V, Charalambides M, et al. (2016) Scalable cache management for ISP-operated content delivery services. IEEE J Sel Areas Commun 34(8):2063–2076
Talipov E, Chon Y, Cha H (2015) User context-based data delivery in opportunistic smartphone networks. Pervasive Mob Comput 17:122–138
Wu J, Chen Z (2017) Human activity optimal cooperation objects selection routing scheme in opportunistic networks communication. Wirel Pers Commun 95:3357–3375
Kumiawan ZH, Yovita LV, Wibowo TA (2017) Performance analysis of dLife routing in a delay tolerant networks. In: Proceedings of the 2016 international conference on international conference on control, electronics, renewable energy and communications, Bandung, Indonesia, pp 41–46
Wu J, Chen Z, Zhao M (2017) Effective information transmission based on socialization nodes in opportunistic networks. Comput Net 129, Part 1:297–305
Tao J, Wu H, Shi S, Hu J, Gao Y (2018) Contacts-aware opportunistic forwarding in mobile social networks: a community perspective. IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, pp 1–6. https://doi.org/10.1109/WCNC.2018.8377216
Bocquillon R, Jouglet A (2018) Robust routing in deterministic delay-tolerant networks. Comput Oper Res 92:77–86
Zhu H, Dong M, Chang S, Zhu Y, Li M, Sherman Shen X (2013) ZOOM: scaling the mobility for fast opportunistic forwarding in vehicular networks. In: 2013 Proceedings IEEE INFOCOM, Turin, pp 2832–2840
Daly EM, Haahr M (2007) Social network analysis for routing in disconnected delay-tolerant MANETs. In: Proceedings of the 8th ACM international symposium on mobile ad hoc networking and computing. Montreal, Quebec, Canada
Hui P, Crowcroft J, Yoneki E (2008) Bubble rap: social-based forwarding in delay tolerant networks. In: Proceedings of the 9th ACM international symposium on mobile ad hoc networking and computing, May 26-30, Hong Kong, Hong Kong, China
Zhu H, Chang S, Li M, Naik K, Shen S (2011) Exploiting temporal dependency for opportunistic forwarding in urban vehicular networks. In: 2011 Proceedings IEEE INFOCOM, Shanghai, pp 2192–2200
Wu J, Chen Z, Zhao M (2018) Information transmission probability and cache management method in opportunistic networks, wireless communications and mobile computing, volume 2018
Qin J, Zhu H, Zhu Y, Lu L, Xue G, Li M (2016) POST: exploiting dynamic sociality for mobile advertising in vehicular networks. IEEE Trans Parallel Distrib Syst 27(6):1770–1782
Neena VV, Rajam VMA (2013) Performance analysis of epidemic routing protocol for opportunistic networks in different mobility patterns. In: Proceedings of the 2013 international conference on international conference on computer communication and informatics, Coimbatore, India, 4–6 January, pp. 1–5
Kim JB, Lee IH (2015) Non-orthogonal multiple access in coordinated direct and relay transmission. IEEE Commun Lett 19:2037–2040
Spyropoulos T, Psounis K, Raghavendra CS (2005) Wait spray: an efficient routing scheme for intermittently connected mobile networks. In: Proceedings of the ACM workshop on delaytolerant networking, Philadelphia, PA, USA, pp 252–259
Borah SJ, Dhurandher SK, Tibarewala S, Woungang I, Obaidat MS (2017) Energy-efficient prophet-PRowait-EDR protocols for opportunistic networks. In: Proceedings of the GLOBECOM 2017—2017 IEEE global communications conference, Singapore, pp 4–8
Mir MY, Chih-Lin-Hu, Huang S (2018) Data forwarding with finite buffer capacity in opportunistic networks. In: 2018 27th wireless and optical communication conference (WOCC), Hualien, pp 1–5. https://doi.org/10.1109/WOCC.2018.8372708
Qin X, Wang X, Wang L, Lin Y, Wang X (2019) An efficient probabilistic routing scheme based on game theory in opportunistic networks. Comput Net 149:144–153
Sati S, Ippisch A, Graffi K (2017) Replication probability-based routing scheme for opportunistic networks[C]// International Conference on Networked Systems
Jinie P, Song YT (2016) Health capability maturity model: person-centered approach in personal health record system. In: Proceedings of the Americas Conference on Information Systems, San Diego, CA, USA, pp 11–14
Author information
Authors and Affiliations
Contributions
Conceptualization, P.Z. and Y.Y.; Methodology, P.Z.; Software, Y.Y.; Validation, P.Z.; Formal Analysis, P.Z. and Y.Y.; Investigation, P.Z. and Y.Y.; Resources, P.Z.; Data Curation, P.Z. and Y.Y.; Writing—Original Draft Preparation, P.Z.; Writing—Review & Editing, P.Z.; Visualization, Y.Y.; Supervision, H.F.; Project Administration, H.F.; Funding Acquisition, H.F.
Corresponding author
Ethics declarations
Conflict of interests
The authors declare no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Peng Zheng, Hongxiao Fei and Yeqing Yan contributed equally to this work.
Rights and permissions
About this article
Cite this article
Zheng, P., Fei, H. & Yan, Y. An effective positive transmission routing algorithm based on social relationships in opportunistic social networks. Peer-to-Peer Netw. Appl. 13, 269–286 (2020). https://doi.org/10.1007/s12083-019-00767-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00767-7