Abstract
The scarcity of bandwidth in the radio spectrum has become more vital since the demand for more and more wireless applications has increased. Most of the spectrum bands have been allocated although many studies have shown that these bands are significantly underutilized most of the time. The problem of unavailability of spectrum and inefficiency in its utilization has been smartly addressed by the cognitive radio (CR) technology which is an opportunistic network that senses the environment, observes the network changes, and then uses knowledge gained from the prior interaction with the network to make intelligent decisions by dynamically adapting their transmission characteristics. In this paper, some of the decentralized adaptive medium access control (MAC) protocols for CR networks have been critically analyzed, and a novel adaptive MAC protocol for CR networks, decentralized non-global MAC (DNG-MAC), has been proposed. The results show the DNG-MAC outperforms other CR-MAC protocols in terms of time and energy efficiency.
Similar content being viewed by others
1 Introduction
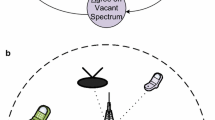
The development of new technologies such as Wi-Fi, cellular phones, bluetooth, TV broadcasts and satellite has created immense demand for radio spectrum which is a limited natural resource ranging from 30 KHz to 300 GHz[1]. For every wireless application, some portion of the radio spectrum needs to be purchased, and the Federal Communication Commission (FCC) allocates the spectrum for some fee for such services[2]. This static allocation of the radio spectrum has led to different problems such as saturation in some bands, scarcity, and lack of radio resources to new wireless applications. Most of the frequencies in the radio spectrum have been allocated although many studies have shown that the allocated bands are not efficiently being used[3]. Cognitive radio (CR) technology[4–7] is the solution to the shortage of spectrum and the inefficiency of its utilization. CR nodes are intelligent wireless devices that sense the environment, observe the network changes, and then use knowledge learnt from the previous interaction with the network and make intelligent decisions to seize the opportunities to transmit. This process of scanning the spectrum (S), exchanging control information (E), agreeing upon white space (A) and transmitting data (T) on the network is repeated continuously in a cycle called SEAT cycle. Fig. 1 shows how a cognitive radio learns from its environment and tunes its transceivers to adapt the network changes. CR can autonomously detect the unoccupied spectrum and exploit the opportunities to transmit with increased throughput. With its remembrance capability, it can arrange a new call by a different carrier for those locations where calls with existing services drop. The fundamental features of CR technology have been shown in Fig. 2. CR network serves as a framework in accessing the spectrum allocation dynamically, and spectrum opportunity[8] deals with the usage of a free channel that is part of radio spectrum and not currently being used by primary users (PUs). The licensed user or PU of the frequency band is the existing wireless system who purchases a portion of radio spectrum from FCC for fee, and those who utilize the unoccupied spectrum opportunistically for communication without interference to PU are called secondary users (SUs). Each CR device is equipped with sensors and transceivers that sense the spectrum and allow SUs to access licensed spectrum bands as long as SUs do not impose any interference to PUs.
2 Literature review
Different areas of CR networks are being explored by scientists and researchers. Some of the areas are architecture, medium access control (MAC) protocols, scheduling policy, spectrum sensing, quality of service (QoS), energy efficiency, and security for CR networks. In CR networks, channel availability can rapidly change, so synchronization in the CR network is a key challenge in MAC protocols to adapt the environment and quickly detect the free channels for subsequent transmission. Fig. 3 shows the spectrum usage by PUs and the formation of free channels (also called white spaces). These free channels are in fact the opportunities for SUs to transmit. MAC protocols deal with the exchange of this type of information in the form of free channel list (FCL) amongst CR nodes. MAC protocols for CR networks can be broadly classified as centralized and decentralized. The centralized MAC protocols use a central entity, usually called a base station, which is responsible for detection, coordination and communication of multiple cognitive devices in a cognitive radio network (IEEE 802.22)[9, 10].
The decentralized MAC protocols consider different aspects such as the number of transceivers, channel access mechanism, spectrum sensing techniques, and selection criteria for control channel[11, 12]. For example, the authors of [13, 14] make use of global common control channel (GCCC) for control information exchange while non-GCCC is used in [15, 16] to setup initial configuration dialog. Zhang and Su[17], and Song and Lin[18] do not address the design constraint of control channel and assume that a dedicated channel already exists for exchange of control information. Fig. 4 shows the classification of CR-MAC protocols.
3 Analysis of decentralized adaptive MAC protocols for cognitive radio networks
In this section of the paper, we critically analyze the decentralized MAC protocols of both the GCCC and non-GCCC.
3.1 Cognitive radio-enabled multichannel MAC (CREAM-MAC) protocol
CREAM-MAC[17] is a decentralized CR-MAC protocol which assumes that a CCC has been found and agreed upon by all CR nodes in the vicinity before the CREAM-MAC starts its operation. The sender initiates four-way dialog by exchanging four types of packets, namely request-to-send (RTS), clear-to-send (CTS), channel-state-transmitter (CST) and channel-state-receiver (CSR). The control information dialog contains the information about the number of channels available, reliability of channel and the length of transmission. After agreeing upon all the communication rules exchanged during the handshake, data is transmitted over one of the free channel common to both SUs. CREAM-MAC calculates the PU interference probability and the channel utilization by PU, and the aggregated throughput. CREAM-MAC assumes that a control channel is already available and always reliable. It is strongly believed that finding a common channel to exchange control information is the primary task of cognitive nodes. Subsequent operation could not take place if the existence of a control channel has not been addressed. So the unrealistic assumption of an available control channel is not a well-built justification.
3.2 Opportunistic cognitive MAC (OC-MAC) protocol
OC-MAC protocol[19] is a decentralized and connection-oriented MAC protocol over CR network. OC-MAC is different from CREAM-MAC due to its co-existence with wireless local area networks (WLAN). OC-MAC uses a dedicated channel for control information, on which CR nodes compete with one another for data channel reservation. Like WLAN IEEE802.11, CR nodes apply the distributed coordination function (DCF) mechanism[20,21], and the status of each channel is recorded with the execution of DCF. OC-MAC uses the typical exchange of RTS/CTS followed by confirm-RTS (CRTS). The protocol evaluates the throughput with and without the PU traffic. OC-MAC is a decentralized CR-MAC protocol that exchanges the information obtained from the spectrum sensors at the physical layer over the dedicated control channel. The specification about the nature of dedicated channel (GCCC or non-GCCC) has not been addressed in OC-MAC. The statistics of each channel is maintained in the channel state table, which every secondary user updates after each scan. OC-MAC maximizes the throughput of the network by exchanging the statistics among each secondary communicator in the cognitive radio network. It avoids collisions by using these statistics. However, there are some vital design flaws in OC-MAC which make it inappropriate for CR nodes. First of all, the operation of OC-MAC is started with the existence of dedicated control channel which will be used for exchange of RTS/CTS and CRTS, and no description of the dedicated control channel is provided. Secondly, CR nodes in OC-MAC predict the length of a spectrum hole. We strongly criticize this because a CR network is an opportunistic network and it is very hard to find the exact period during which the PU will not utilize the spectrum so that the time length of spectrum hole could be calculated. Lastly, the protocol claims to be co-existent with WLAN. However, the justification for this theory is not clearly presented in the paper. And we do not believe that CR nodes need to coexist with WLAN because WLAN uses the industrial, scientific and medical (ISM) band (e.g., 2.4 GHz) which is already freely available to any user. There is no need to seize the opportunity to transmit in the ISM band, and nodes only need to contend for the ISM band.
3.3 Statistical channel allocation MAC (SCA-MAC) protocol
SCA-MAC protocol[14] intelligently senses the spectrum and dynamically accesses the unused or underutilized spectrum with the minimum or no interference to PUs. Two basic control parameters are operating range and channel aggregation for SCA-MAC. This protocol also uses carrier sense multiple access/collision avoidance (CSMA/CA)[22] mechanism to achieve a higher spectrum utilization. To avoid interference with primary users, SCA-MAC evaluates its impact in real time by predicting the successful rate of each transmission. Spectrum sensing is performed continuously and rapidly. SCA-MAC uses the cyclostationery feature detection[23,24] for the continuous and rapid spectrum sensing. After exchange of control-channel-request-to-send (CRTS) and Control-channel-Clear-To-Send (CCTS) frames on GCCC, both sender and receiver tune their transceivers to the agreed data channel. This protocol can speed up transmission by using more than one channel for data transmission and can wait for some time for a channel with a higher bandwidth to become available. SCA-MAC is a global decentralized CR protocol which performs the 2-way handshake by sending CRTS and CCTS frames which contain the information of the best opportunity. SCA-MAC emphasizes on the data transmission, and ignores the pre-transmission overheads. Obviously, more number of frames exchanged as control information will not only add delay in QoS aware data but will also contribute towards inefficient use of energy as nodes will have to wait longer before the actual transmission starts.
3.4 Adaptive MAC (A-MAC) protocol
A-MAC protocol[16] is a decentralized MAC protocol for CR networks, which is distributed in nature and does not require any GCCC, and can utilize a backup data channel when higher throughput is required. The protocol considers different aspects such as bandwidth, channel reliability, channel condition, and rate adaption to perform channel indexing, create FCL and find the best channel. Indexed channel listing (ICL) is done according to the available bandwidth. The higher is the bandwidth of a channel, the higher will be the statistics of the channel. Other parameters that A-MAC uses to build a channel rank are signal-to-noise ratio (SNR), queue length, frame error rate and past history. The protocol starts its operation by sending the ICL in the RTS frame, and the receiver replies with its own ICL. Both the communication partners switch to the agreed data channel after exchanging channel reservation control packets which confirm the white space to be used as data channel.
A-MAC is different from the previously discussed protocols as it makes use of non-GCCC. However, the methodology used by CR nodes in the vicinity to converge on a non-GCCC is clearly missing. It is very important for nodes in the CR network to be well aware about the control channel because no subsequent transmission could occur without first finding the control channel. Also, more control frames and a heavier size of each control frame cause a higher pre-transmission time. Consequently, CR nodes will strive a lot to seize the rare opportunity to utilize the white spaces before a PU activity is sensed.
3.5 Fast and fair MAC (F2-MAC) protocol
F2-MAC protocol[25] presents an efficient channel sensing and access mechanism for an ad-hoc CR network. F2-MAC uses a five-way handshake to dialog control information. Two types of control frames, similar to traditional RTS and CTS frames, are delivered through a dedicated control channel. Three more control messages, data channel idle (DCI), DCIACK and ready-to-vacate (RTV), are delivered through data channels. The proactive channel vacating phenomenon presented in F2-MAC lets the CR users to be reactively aware of the presence of PUs and the nodes vacate the licensed channel before a PU reclaims. SUs in F2-MAC sense the data channel, and send the RTV frame, and then wait for certain time. This waiting time is long enough for PUs to be sure that their channels are unoccupied. So a PU can access the channel without having any interference from SUs. By transmitting multiple frames on a licensed channel, the throughput in a CR network is improved.
However, five control frames and certain waiting time before transmitting in the F2-MAC protocol impose the highest overheads. The maximum number of frames exchanged as control information is four for many CR-MAC protocols. Exchanging five control frames will not only consume more mobile energy, but also CR nodes will miss the rare opportunity to transmit. Moreover, F2-MAC does not specify whether the dedicated control channel is GCCC or non-GCCC.
4 Design and simulation of a novel CR-MAC protocol
4.1 A novel CR-MAC protocol
After analyzing different decentralized MAC protocols, we see that most of CR-MAC protocols cannot initiate the communication until a startup dialog or handshake, which can only be done on the control channel, is performed. The above discussed protocols avoid collision by CSMA/CA on the common control channel. However, having a dedicated control channel could be wasteful of resource. Also when one pair of SUs have occupied the common control channel, all the other SUs who are the candidates for the CCC set their network allocation vector (NAV) and wait for the CCC to become idle. Some of the other problems could be: 1) there is always a “first-come first-get” mechanism to access the common control channel, so the needy may suffer from long waiting time; 2) the computational cost of back-off algorithm gets too high when the common control channel gets saturated; 3) the secondary communication pair which did not end up the communication due to PU’s arrival must start the process of renegotiation on the control channel. Considering the drawbacks of GCCC, we propose a novel decentralized non-global MAC (DNG-MAC) protocol which is based on the fair allocation of control channel to all candidate SUs using the time division multiple access (TDMA) mechanism.
The first CR node in the DNG-MAC initiates the operation by selecting one of the best channels as the common control channel. The selection criterion for the best channel in this case is arbitrary in the beginning and would be refined after certain number of successful transmissions. The control channel is divided into time slots of fixed length. Each time slot has a listening period and a transceiving period. All CR nodes in the network are synchronized in the listening period of each time slot. DNG-MAC makes use of TDMA, and FCL is exchanged in the transceiving period between secondary user communication pair (SUCP). The duration of the time slot is carefully selected by calculating the average time required for each secondary pair to complete negotiation on the common control channel. Fig. 5 shows the TDMA based allocation of control channel and the occupancy of SUCPs in different white spaces. We strongly argue that due to the starving nature of cognitive radio networks, CR nodes are likely to always have data to transmit. So there would be no wastage of time slot and this will also give the other SUs a fair access to the common control channel. The timing diagram of the proposed multi-channel protocol is given in Fig. 6.
The DNG-MAC makes use of non-GCCC and divides the control channel in n time slots, where n represents the number of SUs in a CR network. Each time slot has a listening period where all CR nodes get synchronized and a transceiving period where the exchange of control infor-mation takes place. Two types of control frames, available channel list (ACL) and ACL acknowledgment (ACLACK), are exchanged in the respective time slots of each CR node.
After successful exchange of ACL and ACLACK, nodes eventually start transmitting data. The overall waiting time for the SUs to access CCC in DNG-MAC is shorter than the waiting time in any of other MAC protocols. Here, every SU is given the confidence that it is in the queue to access the CCC. In this way, more than one secondary communicating pair can access the CCC at the same time. The vacant channels on the spectrum can be simultaneously used by more than one communicating pair through having a shorter waiting time to access the CCC, thus improving overall throughput of the CR nodes.
4.2 Simulation model and results
The proposed protocol has been simulated in OPNET Modeler 14.5. An office scenario with span of 100 × 100m2 has been considered where CR nodes are in coalition with wireless LAN nodes. This ad-hoc based scenario contains 10 CR nodes. All the devices in the given scenario have capa-bility to transmit at 1 Mbps by consuming 0.005dB transmission power, and all pairs are using differential phase-shift keying (DPSK) modulation type. The size of control frames are set to 20 bytes keeping IEEE 802.11b as benchmark. The physical layer parameters of direct sequence spread spectrum (DSSS) have been deployed. The time slot has been set to 10 ms based on average negotiation time required by cognitive radio secondary users on the control channel.
DNG-MAC protocol, the simulation was run for 300s for each experiment, and 10 experiments have been performed to obtain the average results. The global statistics obtained between two CR nodes have been plotted in Fig.7. Due to burst traffic nature which increases exponentially, uneven curves have been generated. Since a CR node cannot transmit until a negotiation has taken place, and the opportunity to transmit has to be seized, the traffic sent remains approximately 40 Kbps in first 50 s and gradually increases in next 100s of the simulation time.
5 Comparative evaluation of CR-MAC protocols
Different CR-MAC protocols have been critically reviewed in the previous section. The generic behaviors of these protocols are presented in Fig. 8. The protocols discussed so far share some common features like the selection criteria for control channel and the access mechanism, etc. while other features are unique. Many of these protocols make use of multiple frames for control information exchange before transmitting data. If certain PU activity is sensed on the data channel, SUs switch on to CCC for renegotiation. These features of the adaptive MAC protocols have been summarized in Table 1.
6 Conclusions
Cognitive radio technology serves as a framework to address the spectrum scarcity issues. One of the important features of a CR network is the exchange of control information (e.g., FCL). Different protocols have been developed which exchange the FCL on either GCCC or non-GCCC for subsequent transmission. A novel MAC protocol has been proposed which fairly allocates the non-GCCC to all CR nodes. The simulation results have revealed the suitability of the proposed scheme where CR nodes co-exist with other wireless LAN nodes in the vicinity. Currently, DNG-MAC is under extensive simulation in which it will be compared with some other MAC protocols for performance comparison and evaluation.
References
The Radio Spectrum, [Online], Available: http://transition.fcc.gov/Bureaus/OPP/working papers/oppwp38chart. pdf.
P. Kolodzy. Spectrum Policy Task Force, Technical Report ET Docket, no. 02-135, Federal Communications Commission, Washington DC, USA, 2002.
Federal Communications Commission. Spectrum Policy Task Force Report, Technical Report ET Docket, no. 02-155, Federal Communications Commission, Washington DC, USA, 2002.
J. Mitola III, G. Q. Maguire Jr. Cognitive radio: Making software radios more personal. IEEE Personal Communications, vol. 6, no. 4, pp. 13–18, 1999.
S. Haykin. Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, vol. 23, no. 2, pp. 201–220, 2005.
I. F. Akyildiz, W. Y. Lee, M. C. Vuran, S. Mohanty. Next generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, vol. 50, no. 13, pp. 2127–2159, 2006.
J. Mitola III. Cognitive Radio Architecture, New York: John Wiley, 2006.
H. Kim, K. G. Shin. Efficient discovery of spectrum opportunities with MAC-layer sensing in cognitive radio networks. IEEE Transactions on Mobile Computing, vol. 7, no. 5, pp. 533–545, 2008.
C. Cordeiro, K. Challapali, D. Birru, N. Sai Shankar. IEEE 802.22: The first worldwide wireless standard based on cognitive radios. In Proceedings of the 1st IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, IEEE, Baltimore, MD, USA, pp. 328–337, 2005.
IEEE. 802 LAN/MAN Standards Committee 802.22 WG on WRANs, [Online], Available: http://www.ieee802.org/22/, 2009.
D. Gozupek, F. Alagoz. MAC protocols for multi-hop cognitive radio networks: A survey. Journal of Communications, vol. 11, no. 2, pp. 1–8, 2009.
C. Cormio, K. R. Chowdhury. A survey on MAC protocols for cognitive radio networks. Ad Hoc Networks, vol. 7, no. 7, pp. 1315–1329, 2009.
J. C. Jia, Q. Zhang, X. M. Shen. HC-MAC: A hardware-constrained cognitive MAC for efficient spectrum management. IEEE Journal on Selected Areas in Communications, vol. 26, no. 1, pp. 106–117, 2008.
A. C. C. Hsu, D. S. L. Wei, C. C. J. Kuo. A cognitive MAC protocol using statistical channel allocation for wireless Ad-Hoc networks. In Proceedings of 2007 IEEE Wireless Communications and Networking Conference, IEEE, Kowloon, pp. 105–110, 2007.
Y. R. Kondareddy, P. Agrawal. Synchronized MAC protocol for multi-hop cognitive radio networks. In Proceedings of 2008 IEEE International Conference on Communications, IEEE, Beijing, China, pp. 3198–3202, 2008.
G. P. Joshi, S. W. Kim, B. S. Kim. An efficient MAC protocol for improving the network throughput for cognitive radio networks. In Proceedings of the 3rd International Conference on Next Generation Mobile Applications, Services and Technologies, IEEE, Cardiff, Wales, pp. 271–275, 2009.
X. Zhang, H. Su. CREAM-MAC: Cognitive radio-enabled multi-channel MAC protocol over dynamic spectrum access networks. IEEE Journal of Selected Topics in Signal Processing, vol. 5, no. 1, pp. 110–123, 2011.
H. Song, X. L. Lin. A leasing oriented MAC protocol for high spectrum usage in cognitive radio networks. In Proceedings of 2009 IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, IEEE, Marrakech, Morocco, pp. 173–178, 2009.
S. Y. Hung, Y. C. Cheng, E. H. K. Wu, G. H. Chen. An opportunistic cognitive MAC protocol for coexistence with WLAN. In Proceedings of 2008 IEEE International Conference on Communications, IEEE, Beijing, China, pp. 4059–4063, 2008
C. A. Patel, S. Kumar. Enhancing throughput efficiency of Ad hoc wireless networks using cognitive radio approach. In Proceedings of 2011 International Conference on Devices and Communications (ICDeCom), IEEE, Mesra, Algeria, pp. 1–5, 2011.
K. Ghaboosi, M. Latva-aho, Y. Xiao, B. H. Khalaj. IEEE 802.11 distributed coordination function service time and queuing delay analysis using Parallel Space - Time Markov Chain. In Proceedings of the 19th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, IEEE, Cannes, France, pp. 1–5, 2008.
A. Zuquete. Improved CSMA/CA protocol for IEEE 802.11. In Proceedings of 2008 Next Generation Internet Networks, IEEE, Krakow, Poland, pp. 247–252, 2008.
D. Cabric, S. M. Mishra, R. W. Brodersen. Implementation issues in spectrum sensing for cognitive radios. In Proceedings of the 38th Asilomar Conference on Signals, Systems and Computers, IEEE, Pacific Grove, CA, USA, vol. 1, pp. 772–776, 2004.
H. Kim, K. G. Shin. In-band spectrum sensing in cognitive radio networks: Energy detection or feature detection? In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, ACM, New York, USA, pp.14–25, 2008.
H. L. Chao, T. C. Lou, S. H. Jiang. F2-MAC: An efficient channel sensing and access mechanism for cognitive radio networks. Wireless Networks, vol. 17, no. 5, pp. 1113–1126, 2011.
L. Ma, X. Han, C. C. Shen. Dynamic open spectrum sharing MAC protocol for wireless ad hoc networks. In Proceedings of the 1st IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, IEEE, Baltimore, MD, USA, pp. 203–213, 2005.
I. F. Akyildiz, W. Y. Lee, M. C. Vuran, S. Mohanty. A survey on spectrum management in cognitive radio networks. IEEE Communications Magazine, vol. 46, no. 4, pp. 40–48, 2008.
A. V. Adamis, K. N. Maliatsos, P. Constantinou. A new MAC protocol with control channel auto-discovery for self-deployed cognitive radio networks. In Proceedings of the 13th Program for European Wireless, pp. 1–7, 2007.
N. Bol var, J. L. Marzo, E. Rodr guez-Colina. Distributed control using cognitive pilot channels in a centralized cognitive radio network. In Proceedings of the 6th Advanced International Conference on Telecommunications, IEEE, Barcelona, Spain, pp. 30–34, 2010.
F. Wang, M. Krunz, S. G. Cui. Spectrum sharing in cognitive radio networks. In Proceedings of the 27th Conference on Computer Communications, IEEE, Phoenix, AZ, USA, pp. 1885–1893, 2008.
E. Hossain. Cognitive Wireless Communication Networks, Berlin, Heidelberg, Germany: Springer-Verlag, 2009.
Author information
Authors and Affiliations
Additional information
Munam Ali Shah received B. Sc. and M. Sc. degrees, both in computer science from University of Peshawar, Pakistan in 2001 and 2003, respectively. He completed his M. Sc. degree in security technologies and applications from University of Surrey, UK in 2010, and is currently a Ph. D. candidate at University of Bedfordshire, UK. Since July 2004, he has been a lecturer at the Department of Computer Science, COMSATS Institute of Information Technology, Islamabad, Pakistan. He received the Best Paper Award of the International Conference on Automation and Computing in 2012.
His research interests include MAC protocol design, QoS, security and performance optimization issues in wireless communication systems.
Sijing Zhang obtained his B. Sc. and M. Sc. degrees, both in computer science, from Jilin University, Changchun, China in 1982 and 1988, respectively. He earned a Ph. D. degree in computer science from the University of York, UK in 1996. He then joined the Network Technology Research Centre (NTRC) of Nanyang Technological University, Singapore as a post-doctoral fellow. In 1998, he returned to the UK to work as a research fellow with the Centre for Communications Systems Research (CCSR) of the University of Cambridge. He joined the School of Computing and Technology, University of Derby, UK, as a senior lecturer in 2000. Since October 2004, he has been working as a senior lecturer in the Department of Computer Science and Technology, University of Bedfordshire, UK.
His research interests include real-time scheduling algorithms, schedulability tests for hard real-time traffic, performance analysis and evaluation of real-time communication protocols, and wireless networks for real-time industrial applications.
Carsten Maple obtained his B. Sc. (Hons) degree at the University of Leicester, UK in 1994, and his Ph. D. degree in 1998. He joined the University of Luton, UK in 1998 as a lecturer in computer science before moving into senior lecturer role later the same year and a principal lecturer post by 2002. In 2004, he was appointed professor of applicable computing, and was promoted to head of the Department for Computer Science and Technology at the newly formed University of Bedfordshire, where he led the department from strength to strength before his promotion to pro-vice chancellor (Research and Enterprise) in 2010.
His research interests include network and computer security, cyberstalking, ethical hacking, information security, trust and authentication in distributed systems, and optimisation techniques.
An erratum to this article is available at http://dx.doi.org/10.1007/s11633-014-0773-x.
Rights and permissions
About this article
Cite this article
Ali Shah, M., Zhang, S. & Maple, C. An Analysis on Decentralized Adaptive MAC Protocols for Cognitive Radio Networks. Int. J. Autom. Comput. 10, 46–52 (2013). https://doi.org/10.1007/s11633-013-0695-z
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11633-013-0695-z