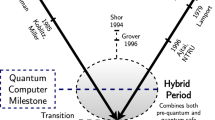
Abstract
This article describes the current situation with incorporating hybrid post-quantum key exchange into the internet security protocols taking TLS 1.3 and IKEv2 as examples.
Similar content being viewed by others
Notes
The diagram below follows the convention from [9]. In addition, protocol field that contains combined public keys is underlined.
Two diagrams below follow the conventions from [11]. In addition, bold typeface is used to depict protected messages, italic font is used to depict newly introduced exchanges and public keys of additional key exchanges are underlined.
Two diagrams below follow the conventions from [11]. In addition, shared keys from additional key exchanges are underlined.
References
Grover, L. K.: A fast quantum mechanical algorithm for database search, 1996, https://arxiv.org/abs/quant-ph/9605043
Shor, P. W.: Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer, 1996, https://arxiv.org/abs/quant-ph/9508027
Bernstein, D. J.: Introduction to post-quantum cryptography, 2009, https://pqcrypto.org/www.springer.com/cda/content/document/cda_downloaddocument/9783540887010-c1.pdf
S. Fluhrer, Cryptanalysis of ring-LWE based key exchange with key share reuse, 2016, https://eprint.iacr.org/2016/085
Krawczyk H.: SIGMA: the ‘SIGn-and-MAc’ Approach to Authenticated Diffie-Hellman and its Use in the IKE Protocols, (2003)
Driscoll, F.: Terminology for Post-Quantum Traditional Hybrid Schemes, draft-ietf-pquip-pqt-hybrid-terminology (work in progress), https://datatracker.ietf.org/doc/draft-ietf-pquip-pqt-hybrid-terminology/
Bernstein, D. J.: (djb@cr.yp.to), e-mail message to the CFRG mailing list (cfrg@irtf.org) with subject “NSA vs. hybrid”, Fri, 12 Nov 2021 09:28:11UTC, https://mailarchive.ietf.org/arch/msg/cfrg/T3XgKeJr4-PvmPrS5TwVNfW9t_w/
Ounsworth, M., Wussler, A., Kousidis, S.: Combiner function for hybrid key encapsulation mechanisms (Hybrid KEMs), draft-ounsworth-cfrg-kem-combiners (work in progress), https://datatracker.ietf.org/doc/draft-ounsworth-cfrg-kem-combiners/
Rescorla, E.: The Transport Layer Security (TLS) Protocol Version 1.3, RFC 8446, August 2018, https://www.rfc-editor.org/rfc/rfc8446.html
Stebila, D., Fluhrer, S., Gueron, S.: Hybrid key exchange in TLS 1.3, draft-ietf-tls-hybrid-design (work in progress), https://datatracker.ietf.org/doc/draft-ietf-tls-hybrid-design/
Kaufman, C., Hoffman, P., Nir, Y., Eronen, P., Kivinen, T.: Internet Key Exchange Protocol Version 2 (IKEv2), RFC 7296, October 2014, https://www.rfc-editor.org/rfc/rfc7296.html
Tjhai, C. J., Tomlinson, M., Bartlett, G., Fluhrer, S., Van Geest, D., Garcia-Morchon, O., Smyslov, V.: Multiple Key Exchanges in the Internet Key Exchange Protocol Version 2 (IKEv2), RFC 9370, May 2023, https://www.rfc-editor.org/rfc/rfc9370.html
Funding
No funding was received for conducting this study.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Smyslov, V. Use of hybrid post-quantum key exchange in internet protocols. J Comput Virol Hack Tech (2024). https://doi.org/10.1007/s11416-024-00515-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11416-024-00515-3