Abstract
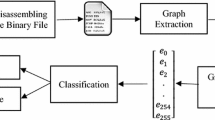
The development of cryptocurrency has led to an increase in a type of malware called ransomware. Ransomware is a family of malware that uses malicious techniques to prevent users from accessing their systems or data. Ransomware threatens all industries, from health and hospitals to banks, training centers, and manufacturers of goods. Therefore, early ransomware detection is critical. Most researchers try to identify ransomware by examining the behavior of the software at runtime. Therefore, these approaches are costly and require resources to run every software. In this paper, ransomware detection is conducted without running the software and without any special pre-processing, only using the headers of the executable file. In the proposed approach, a graph is created using the headers of executable files (specifically portable executable files) and then the graph is mapped in an eigenspace using the “Power Iteration” method. This mapping converts an executable file to a feature vector, which is eventually used to train a Random Forest classifier. Acceptable computational complexity in large datasets compared to previous methods and high detection rates are the main advantages of the proposed method.




Similar content being viewed by others
References
Alqahtani, H., Sarker, I.H., Kalim, A., Hossain, S.M.M., Ikhlaq, S., Hossain, S.: Cyber intrusion detection using machine learning classification techniques. In: International Conference on Computing Science, Communication and Security. pp. 121–131. Springer (2020)
Humayun, M., Niazi, M., Jhanjhi, N.Z., Alshayeb, M., Mahmood, S.: Cyber security threats and vulnerabilities: a systematic mapping study. Arab. J. Sci. Eng. 45, 3171–3189 (2020)
Usman, N., Usman, S., Khan, F., Jan, M.A., Sajid, A., Alazab, M., Watters, P.: Intelligent dynamic malware detection using machine learning in IP reputation for forensics data analytics. Futur. Gener. Comput. Syst. 118, 124–141 (2021)
Connolly, L.Y., Wall, D.S.: The rise of crypto-ransomware in a changing cybercrime landscape: Taxonomising countermeasures. Comput. Secur. 87, 101568 (2019)
Ghazi-Tehrani, A.K., Pontell, H.N.: Phishing evolves: analyzing the enduring cybercrime. Vict. Offender. 16, 316–342 (2021)
Damasevi ius, R., Ven kauskas, A., Toldinas, J., Grigali nas, sar nas: Ensemble-based classification using neural networks and machine learning models for windows PE malware detection. Electronics. 10, 485 (2021)
Zhang, Y., Li, H., Zheng, Y., Yao, S., Jiang, J.: Enhanced DNNs for malware classification with GAN-based adversarial training. J. Comput. Virol. Hacking Tech. 17, 153–163 (2021)
Egele, M., Scholte, T., Kirda, E., Kruegel, C.: A survey on automated dynamic malware-analysis techniques and tools. ACM Comput. Surv. 44, 1–42 (2008)
Homayoun, S., Dehghantanha, A., Ahmadzadeh, M., Hashemi, S., Khayami, R.: Know abnormal, find evil: frequent pattern mining for ransomware threat hunting and intelligence. IEEE Trans. Emerg. Top. Comput. (2017)
Richardson, R., North, M.M.: Ransomware: evolution, mitigation and prevention. Int. Manag. Rev. 13, 10 (2017)
Cabaj, K., Gregorczyk, M., Mazurczyk, W.: Software-defined networking-based crypto ransomware detection using HTTP traffic characteristics. Comput. Electr. Eng. 66, 353–368 (2018)
Kharraz, A., Robertson, W., Kirda, E.: Protecting against ransomware: a new line of research or restating classic ideas? IEEE Secur. Priv. 16, 103–107 (2018)
Azmoodeh, A., Dehghantanha, A., Conti, M., Choo, K.-K.R.: Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient Intell. Humaniz. Comput. 9, 1141–1152 (2018)
Davies, S.R., Macfarlane, R., Buchanan, W.J.: Differential area analysis for ransomware attack detection within mixed file datasets. Comput. Secur. 108, 102377 (2021)
Jimada, S., Nguyen, T.D.L., Sanda, J., Vududala, S.K.: Analysis of ransomware, methodologies used by attackers and mitigation techniques. In: Research in Intelligent and Computing in Engineering, pp. 379–387. Springer (2021)
Humayun, M., Jhanjhi, N.Z., Alsayat, A., Ponnusamy, V.: Internet of things and ransomware: evolution, mitigation and prevention. Egypt. Inform. J. 22, 105–117 (2020)
Conti, M., Gangwal, A., Ruj, S.: On the economic significance of ransomware campaigns: a Bitcoin transactions perspective. Comput. Secur. 79, 162–189 (2018)
O’Kane, P., Sezer, S., Carlin, D.: Evolution of ransomware. IET Netw. 7, 321–327 (2018)
Gomez-Hernandez, J Alvarez-Gonzalez, L., Garcia-Teodoro, P.: R-Locker: Thwarting ransomware action through a honeyfile-based approach. Comput. Secur. 73, 389–398 (2018)
Kolodenker, E., Koch, W., Stringhini, G., Egele, M.: Paybreak: Defense against cryptographic ransomware. In: Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, pp. 599–611 (2017)
Faghihi, F., Zulkernine, M.: RansomCare: Data-centric detection and mitigation against smartphone crypto-ransomware. Comput. Netw. 191, 108011 (2021)
Zavarsky, P., Lindskog, D.: Experimental analysis of ransomware on windows and android platforms: evolution and characterization. Proc. Comput. Sci. 94, 465–472 (2016)
Bhagwat, L.B., Patil, B.M.: Detection of ransomware attack: a review. In: Proceeding of International Conference on Computational Science and Applications, pp. 15–22. Springer (2020)
Moussaileb, R., Cuppens, N., Lanet, J.-L., Bouder, H.L.: A survey on windows-based ransomware taxonomy and detection mechanisms. ACM Comput. Surv. 54, 1–36 (2021)
Ahmed, Y.A., Kocer, B., Huda, S., Al-rimy, B.A.S., Hassan, M.M.: A system call refinement-based enhanced Minimum Redundancy Maximum Relevance method for ransomware early detection. J. Netw. Comput. Appl. 167, 102753 (2020)
Goyal, P.S., Kakkar, A., Vinod, G., Joseph, G.: Crypto-ransomware detection using behavioural analysis. In: Reliability, Safety and Hazard Assessment for Risk-Based Technologies, pp. 239–251. Springer (2020)
Ramesh, G., Menen, A.: Automated dynamic approach for detecting ransomware using finite-state machine. Decis. Support Syst. 138, 113400 (2020)
Mercaldo, F.: A framework for supporting ransomware detection and prevention based on hybrid analysis. J. Comput. Virol. Hacking Tech. 17, 221–227 (2021)
De Lorenzo, A., Martinelli, F., Medvet, E., Mercaldo, F., Santone, A.: Visualizing the outcome of dynamic analysis of Android malware with VizMal. J. Inf. Secur. Appl. 50, 102423 (2020)
Ye, Y., Li, T., Adjeroh, D., Iyengar, S.S.: A survey on malware detection using data mining techniques. ACM Comput. Surv. 50, 1–40 (2017)
Zhang, H., Xiao, X., Mercaldo, F., Ni, S., Martinelli, F., Sangaiah, A.K.: Classification of ransomware families with machine learning based on N-gram of opcodes. Futur. Gener. Comput. Syst. 90, 211–221 (2019)
Manavi, F., Hamzeh, A.: A new method for ransomware detection based on PE header using convolutional neural networks. In: 2020 17th International ISC Conference on Information Security and Cryptology (ISCISC), pp. 82–87. IEEE (2020)
Vidyarthi, D., Kumar, C.R.S., Rakshit, S., Chansarkar, S.: Static malware analysis to identify ransomware properties. Int. J. Comput. Sci. Issues. 16, 10–17 (2019)
Khammas, B.M.: Ransomware detection using random forest technique. ICT Express. 6, 325–331 (2020)
Baldwin, J., Dehghantanha, A.: Leveraging support vector machine for opcode density based detection of crypto-ransomware. In: Cyber Threat Intelligence, pp. 107–136. Springer (2018)
Zhang, B., Xiao, W., Xiao, X., Sangaiah, A.K., Zhang, W., Zhang, J.: Ransomware classification using patch-based CNN and self-attention network on embedded N-grams of opcodes. Futur. Gener. Comput. Syst. 110, 708–720 (2019)
Manavi, F., Hamzeh, A.: A new approach for malware detection based on evolutionary algorithm. In: Proceedings of the Genetic and Evolutionary Computation Conference Companion, pp. 1619–1624 (2019)
Hashemi, H., Hamzeh, A.: Visual malware detection using local malicious pattern. J. Comput. Virol. Hacking Tech. 15, 1–14 (2019)
Farrokhmanesh, M., Hamzeh, A.: Music classification as a new approach for malware detection. J. Comput. Virol. Hacking Tech. 15, 77–96 (2019)
Kim, S.: PE header analysis for malware detection. (2018)
Rezaei, T., Manavi, F., Hamzeh, A.: A PE header-based method for malware detection using clustering and deep embedding techniques. J. Inf. Secur. Appl. 60, 102876 (2021)
Vinayakumar, R., Soman, K.P., Velan, K.K.S., Ganorkar, S.: Evaluating shallow and deep networks for ransomware detection and classification. In: 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), pp. 259–265. IEEE (2017)
Takeuchi, Y., Sakai, K., Fukumoto, S.: Detecting ransomware using support vector machines. In: Proceedings of the 47th International Conference on Parallel Processing Companion, pp. 1–6 (2018)
Kumar, A., Kuppusamy, K.S., Aghila, G.: A learning model to detect maliciousness of portable executable using integrated feature set. J. King Saud Univ. Inf. Sci. 31, 252–265 (2019)
Raff, E., Sylvester, J., Nicholas, C.: Learning the PE header, malware detection with minimal domain knowledge. In: Proceedings of the 10th ACM Workshop on Artificial Intelligence and Security, pp. 121–132 (2017)
Ferrante, A., Malek, M., Martinelli, F., Mercaldo, F., Milosevic, J.: Extinguishing ransomware-a hybrid approach to android ransomware detection. In: International Symposium on Foundations and Practice of Security, pp. 242–258. Springer (2017)
Wilkinson, J.H.: The Algebraic Eigenvalue Problem. Oxford, Clarendon (1965)
Lin, F., Cohen, W.W.: Power iteration clustering. In: ICML (2010)
Hashemi, H., Azmoodeh, A., Hamzeh, A., Hashemi, S.: Graph embedding as a new approach for unknown malware detection. J. Comput. Virol. Hacking Tech. 13, 153–166 (2017)
Harrington, P.: Machine Learning in Action. Manning Publications Co. (2012)
Ho, T.K.: Random decision forests. In: Proceedings of 3rd International Conference on Document Analysis and Recognition, pp. 278–282. IEEE (1995)
Ao, Y., Li, H., Zhu, L., Ali, S., Yang, Z.: The linear random forest algorithm and its advantages in machine learning assisted logging regression modeling. J. Pet. Sci. Eng. 174, 776–789 (2019)
Kohavi, R.: A study of cross-validation and bootstrap for accuracy estimation and model selection. In: Ijcai, pp. 1137–1145. Montreal, Canada (1995)
Powers, D.M.: Evaluation: from precision, recall and F-measure to ROC, informedness, markedness and correlation. arXiv:2010.16061 (2011)
Pedregosa, F., Varoquaux, G., Gramfort, A., Michel, V., Thirion, B., Grisel, O., Blondel, M., Prettenhofer, P., Weiss, R., Dubourg, V.: Scikit-learn: machine learning in Python. J. Mach. Learn. Res. 12, 2825–2830 (2011)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Manavi, F., Hamzeh, A. A novel approach for ransomware detection based on PE header using graph embedding. J Comput Virol Hack Tech 18, 285–296 (2022). https://doi.org/10.1007/s11416-021-00414-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11416-021-00414-x