Abstract
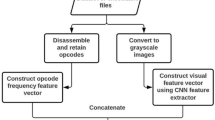
In recent years, malware authors have had significant developments in offering new generations of malware and have tried to use different methods to make malware detection hard, so detecting malware has become one of the most important challenges for the security of computer systems. These developments have made detection of malware using conventional methods rather difficult and in many cases impossible. Thus, inventing new methods for detecting malware is critical. In this paper, a new method is proposed to detect unknown malware based on micro-patterns within the executable files. In the proposed method, for extracting required micro-patterns, one of the well-known methods in machine vision field is used. The proposed method works as follows: first executable files are converted into digital images; second, these images are used to extract visual features of the executable files; finally, machine learning methods are used to detect malware. The main idea of the proposed method is based on differences in the behavior and functionality of malware and benign files, where different behavior results in different micro-patterns which can be used to distinguish between malware and benign files. Accordingly, in this paper a textural image classification method is used which aims to extract micro-patterns of digital textural images, to detect and extract micro-patterns of executable files and use them to detect malware.
















Similar content being viewed by others
References
Bazrafshan, Z., Hashemi, H., Fard, S.M.H., Hamzeh, A.: A survey on heuristic malware detection techniques. In: IKT 2013—2013 5th Conference on Information and Knowledge Technology, pp. 113–120 (2013)
Harrington, P.: Machine Learning in Action, vol. 5. Greenwich, CT: Manning (2012)
Yang, Y., Newsam, S.: Comparing sift descriptors and gabor texture features for classification of remote sensed imagery. In: Proceedings of International Conference on Image Processing, ICIP, pp. 1852–1855 (2008)
Ding, Y., Dai, W., Yan, S., Zhang, Y.: Control flow-based opcode behavior analysis for Malware detection. Comput. Secur. 44(2007), 65–74 (2014)
Santos, I., Devesa, J., Brezo, F., Nieves, J., Bringas, P.G.: OPEM: a static-dynamic approach for machine-learning-based malware detection. Adv. Intell. Syst. Comput. (AISC) 189, 271–280 (2013)
Santos, I., Brezo, F., Ugarte-Pedrero, X., Bringas, P.G.: Opcode sequences as representation of executables for data-mining-based unknown malware detection. Inf. Sci. (Ny) 231, 64–82 (2013)
Devesa, J., Santos, I., Cantero, X., Penya, Y.K., Bringas, P.G.: Automatic behaviour-based analysis and classification system for malware detection. Computer (Long. Beach. Calif) 2, 395–399 (2010)
Khorsand, Z., Hamzeh, A.: A novel compression-based approach for malware detection using PE header. In: IKT 2013—2013 5th Conference on Information and Knowledge Technology, pp. 127–133 (2013)
Zhou, Y., Inge, W.M.: Malware detection using adaptive data compression. In: Proceedings of the 1st ACM Work. Work. AISec, pp. 53–60 (2008)
Hashemi, H., Azmoodeh, A., Hamzeh, A., Hashemi, S.: Graph embedding as a new approach for unknown malware detection. J. Comput. Virol. Hacking Tech. 13(3), 153–166 (2017)
Lin, F., Cohen, W.W.: Power iteration clustering. In: Proceedings of 27th International Conference on Machine Learning, pp. 655–662 (2010)
Farrokhmanesh, M., Hamzeh, A.: A novel method for malware detection using audio signal processing techniques. In: 2016 Artificial Intelligence and Robotics (IRANOPEN), pp. 85–91 (2016)
Conti, G., Dean, E., Sinda, M., Sangster, B.: Visual reverse engineering of binary and data files. Vis. Comput. Secur. 1–17 (2008)
Conti, G., et al.: A Visual Study of Primitive Binary Fragment Types. Black Hat USA, pp. 1–17 (2010)
Yoo, I.: Visualizing windows executable viruses using self-organizing maps. In: Proceedings of the 2004 ACM Workshop on Visualization and Data Mining for Computer Security—VizSEC/DMSEC ’04, p. 82 (2004)
Kohonen, T.: Self-organizing maps. Springer Ser. Inf. Sci. 30, 1–45 (2001)
Han, K., Lim, J. H., Im, E. G.: Malware analysis method using visualization of binary files. In: Proceedings of the 2013 Research in Adaptive and Convergent Systems, pp. 317–321 (2013)
Datar, M., Immorlica, N., Indyk, P., Mirrokni, V. S.: Locality-sensitive hashing scheme based on p-stable distributions. In: Proceedings of the Twentieth Annual Symposium on Computational Geometry—SCG ’04. p. 253 (2004)
Ojala, S., Member, T., Ma, T.: Multiresolution gray-scale and rotation invariant texture classification with local binary patterns. IEEE Trans. Pattern Anal. Mach. Intell. 24(7), 971–987 (2002)
Kirschen, R.H., O’Higgins, E.A., Lee, R.T.: The Royal London Space Planning: an integration of space analysis and treatment planning part I: assessing the space required to meet treatment objectives. Am. J. Orthod. Dentofac. Orthop. 118(4), 448–455 (2000)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hashemi, H., Hamzeh, A. Visual malware detection using local malicious pattern. J Comput Virol Hack Tech 15, 1–14 (2019). https://doi.org/10.1007/s11416-018-0314-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11416-018-0314-1