Abstract
Due to the increased number of cyberattacks, numerous researchers are motivated towards the design of such schemes that can hide digital information in a signal. Watermarking is one of the promising technologies that can protect digital information. However, traditional watermarking schemes are either slow or less secure. In this paper, a dynamic S-Box based efficient watermarking scheme is presented. The original image was extracted at the receiver’s end without any loss of sensitive information. Firstly, the Secure Hash Algorithm is applied to the original image for the generation of the initial condition. Piece Wise Linear Chaotic Map is then used to generate 16 \(\times\) 16 dynamic Substitution Box (S-Box). As an additional security feature, the watermark is substituted through dynamic S-Box. Hence, it is hard for the eavesdroppers to attack the proposed scheme due to the dynamic nature of S-Box. Lastly, lifting wavelet transform is applied to the host image and the High Low and High High blocks of host image are replaced with least significant bits and most significant bits of the substituted watermark, respectively. Robustness, efficiency and security of the proposed scheme is verified using Structure Similarity Index, Structure Dissimilarity Index, Structure Content, Mutual Information, energy, entropy, correlation tests and classical attacks analysis.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Transmission of multimedia data such as images, videos and audios has significantly increased in the last decade. However, such a massive usage of the Internet also provided some opportunities for the eavesdropper. Eavesdropper apply different attacks and can access private and secret information. Therefore, to secure the information from illegal access and distribution, information hiding has recently become a major area of research. Intruders apply various attacks such as changing meaningful information through modifying the content or decipher the actual information. Steganography, cryptography, and watermarking have one thing in common: they all transmit secret information in such a way that only the receiver can decrypt. Steganography and cryptography are two separate approaches for keeping data secure. The goal of steganography is to conceal hidden messages in media files in such a way that no one can detect the existence of a secret message. A watermark is a type of marking that is hidden within a noise-tolerant signal like audio, video, or image data. It is commonly used to determine who owns the copyright to a signal with the main purpose of watermarking is to ensure proof of ownership. In watermarking, secret data is embedded in the original image in the form of text or image to shield the ownership of original image against unlawful copies. Watermarking can be mainly classified into blind, semi-blind and non-blind watermarking. Blind watermarking extracts the watermark without any knowledge of the original and watermarked images. The semi-blind watermarking extracts the original image knowing the watermarked image while the non-blind watermarking extracts the original image knowing original image, watermarked image and watermark [5, 20].
Over the last decade, various watermarking schemes have been proposed [6, 7, 9, 11, 12, 21, 23, 25, 28, 31, 32, 34, 35, 37]. For instance, a secure and Singular Value Decomposition (SVD) based watermarking method was proposed in [7, 25]. However, due to greater complexity and higher computational complexity, SVD based watermarking schemes are not suitable for hardware implementation. In [11, 23, 28], authors modified Discrete Cosine Transform (DCT) coefficients to embed the watermark. In 2012, Vahedi et al. improved the performance of some existing schemes by utilizing genetic algorithm optimization principles and proposed a new watermarking scheme for colour images [37]. Das et al. utilized the correlation among DCT adjacent coefficients and designed a blind efficient image watermarking scheme in the transform domain [12]. Authors in [8, 22] found that using 8 \(\times\) 8 block-wise DCT based watermarking schemes can decrease real-time hardware implementation problem. In [26, 27], Moulin et al. and Mukherjee et al. designed secure watermarking schemes, respectively. Authors in [24], presented sub-sampling and Discrete Wavelet Transform (DWT) based watermarking scheme in the frequency domain. The proposed scheme in [24] resist geometric distortions. Zhou et al. inserted watermark in mid frequencies of Fourier Mellin Transform (FMT) for the minimization of the geometric deformation caused by lawful printing and scanning processes [41].
Since the last decade, a close relationship between chaos and cryptography has been proved. Due to the initial key sensitivity, non-periodicity, deterministic pseudo randomness, and larger keyspace, chaos-based watermarking schemes have received a lot of attention from the research community. In literature, a number of chaos-based watermarking schemes are available [13,14,15,16, 18, 19, 29, 36, 40]. The most commonly used chaotic maps are Henon map, Logistic map, Arnold map, Lorenz equations, Skew Tent map, Standard map and Baker map. Dawei et al. designed a chaos-based watermarking scheme for still images by transforming the image into the frequency domain. Dawei et al. applied wavelet transformation locally and inserted the chaos-based watermark into sub-band coefficients [13]. Authors in [40] presented a new watermarking scheme using two chaotic maps. Embedded indexes of the host images were encrypted by one chaotic map while the second chaotic map was used to locate the pixel bit of the host image. Fan et al. proposed a novel watermarking scheme for speech data copyright protection via Discrete Fractional Sine Transform (DFRST) [14]. The security of the watermarking scheme [14] was improved through adopting chaotic sequences. In [29], a novel chaos-based fragile watermarking scheme for image authentication and tamper detection was presented. This watermarking scheme can identify the modification in an image and can also detect the exact location that has been modified. For security enhancement, two chaotic maps were employed in the presented algorithm [29].
Self-recovery and tamper detection fragile watermarking scheme were presented by Tong et al. [36]. Blocks of the original image were confused by using the cross chaotic map. The recovery after tampering was improved through a novel method known as sister block embedding scheme [36]. Ghebleh et al. proposed blind frequency domain watermarking scheme using Logistic and Arnold chaotic maps [15]. According to [15], the proposed wavelet transform based algorithm inserts a white and black watermark logo in the mid-band component of the host image. Two copies of watermark were embedded in two distinct subbands of the host image. The computational complexity was reduced by using only the least significant bits of the image [18]. Furthermore, Khan et al. [19] utilized classes of finite chain rings for designing of substitution Box (S-Box). The authors developed image encryption and watermarking schemes using the aforementioned S-Box. Jamal et al. embedded watermark in the frequency domain of the original image [16]. The embedded indexes were generated through random numbers that were obtained from Chaotic Fractional Rössler System [16]. Su et al. [33] utilized Hessenberg transform and designed a blind colour image watermarking algorithm. The security of the proposed watermarking scheme was increased via Arnold transform and MD5 hashing. Roy et al. developed a DCT-based blind colour watermarking scheme for inserting multiple watermarks simultaneously [30].
1.1 Contributions
Following are the main contributions of this paper.
-
1.
For higher security, SHA-256 is applied on the original image and initial condition is generated for PWLCM chaotic map.
-
2.
A dynamic \(16 \times 16\) S-Box is generated from the random data obtained using PWLCM. Due to the dynamic nature of substitution, the presented scheme resist a number of statistical attacks.
-
3.
The final watermark image is obtained using dynamic S-Box and the HH and HL block of the lifting wavelet transformed image.
The rest of paper is structured as follows: Sect. 2 presents the fundamental knowledge. Section 3 discusses the proposed scheme. Sections 4 and 5 presents simulation results and conclusion, respectively.
2 Fundamental Knowledge
2.1 PWLCM
Due to the random-like nature and sensitivity to initial conditions, a number of researchers have used PWLCM map in image encryption schemes [10]. From previous research [3, 38], it is evident that PWLCM has good dynamical behavior, uniform invariant density, and ergodicity. Mathematically, PWLCM map can be written as [39]:
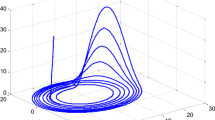
where \(\alpha \in (0,0.5)\) is the control parameter and \(z_{0} \in (0,1)\) is initial condition. These two parameters serve as a secret key in the proposed watermarking scheme. Figure 1 shows the key sensitivity of PWLCM for a small change in initial condition. In Fig. 2, 5000 random numbers are generated for \(z_{0}=0.4999\) and \(\alpha = 0.2120\). From these figures, one can conclude that PWLCM is highly sensitive to initial conditions and all random numbers are different.
2.2 Substitution Box (S-Box)
S-Box is used to induce non-linearity in a cryptosystem. In order to develop an efficient and robust watermarking scheme, S-Box should be part of it. S-Box decreases correlation between original/plaintext data. High non-linearity in a cryptosystem is always of great interest. S-Box is fundamentally vector boolean function that maps n input bits to m output bits which means \(n \times m\) S-Box always produces m bits for a given number of n bits. In cryptographic theory, S-Box is a function of the form [2]:
Where \(B = {0, 1}\). As \(S-Boxes\) are nonlinear components, therefore, it determines security strength against differential and linear attacks.
3 The Proposed Scheme
Flowchart of the proposed image watermarking scheme is shown in Fig. 3. The presented scheme consists of two main steps: (1) dynamic S-Box generation using PWLCM chaotic map (2) embedding watermark in the original image. Detail steps of the proposed image watermarking scheme are as follows:
\(\mathbf {Step 1}\): Apply \(SHA-256\) on the original image P and generate the initial condition \(z_{0}\) for the PWLCM.
\(\mathbf {Step 2}\): Convert 256 bit (64 byte hexadecimal) hash value to decimal format.
\(\mathbf {Step 3}\): Divide decimal hash value \(H_{decimal}\) by \(2^{48}\) to ensure that the value of initial condition \(z_{0}\) is between 0 and 1.
\(\mathbf {Step 4}\): Set maximum number of iterations i.e., 356 for PWLCM. To avoid the transient effect, the first 100 random numbers were ignored and the remaining 256 random numbers were considered. \(\mathbf {Step 5}\): Multiply random numbers vector z with \(10^{14}\) and apply modulus 256 operation.
\(\mathbf {Step 6}\): Arrange decimal random numbers in \(16 \times 16\) matrix form and obtain dynamic S-Box.
\(\mathbf {Step 7}\): To get a substituted watermark \(W'\), substitute each pixel of the watermark with the value of dynamic S-Box. \(\mathbf {Step 8}\): Convert each decimal pixel of substituted watermark \(W'\) to binary 8 bits at index i and j.
\(\mathbf {Step 9}\): Split the 8 bit binary pixel values into 4 LSBs and 4 MSBs.
\(\mathbf {Step 10}\): Apply LWT on the original image P.
\(\mathbf {Step 11}\): Replace HL and HH blocks of the host image with the LSBs and MSBs of the substituted watermark.
\(\mathbf {Step 12}\): Apply inverse lifting wavelet transform on the new blocks of host image to get the final watermarked image W.
To obtain the watermark and original image P from the watermarked image W, all the above steps are applied in reverse order. The step-wise flowchart of the watermark extraction algorithm is illustrated in Fig. 4. As the initial condition, \(z_{0}\) serve as a secret key in the proposed scheme, therefore, at the receiver end, the receiver must know this key. Due to this reason, the flow chart in Fig. 4 does not have key generation steps.
Visual results of proposed watermarking scheme for Baboon image a Original Baboon image. b Watermark imagem. c Substitute watermark image. d Histogram of original Baboon image. e Histogram of watermark image. f Histogram of substitute watermark image. g Watermarked Baboon image. h Extracted watermark image. i Recovered original Baboon image. j Histogram of watermarked Baboon image. k Histogram of extracted watermark image. l Histogram of recovered original Baboon image
Visual results of proposed watermarking scheme for Pepper image a Original Pepper image. b Watermark image. c Substitute watermark image. d Histogram of original Pepper image. e Histogram of watermark image. f Histogram of substitute watermark image. g Watermarked Pepper image. h Extracted watermark image. i Recovered original Pepper image. j Histogram of watermarked Pepper image. k Histogram of extracted watermark image. l Histogram of recovered original Pepper image
4 Simulation Results and Evaluation
Original Baboon image, watermark image, ciphered watermarked image, watermarked Baboon image, recovered watermark and recovered Baboon image are illustrated in Fig. 5a, b, c, g, h and i, respectively. Similarly, original Pepper image, watermark image, ciphered watermarked image, watermarked Pepper, recovered watermark and recovered Pepper image are shown in Fig. 6a, b, c, g, h and i, respectively. To prove the robustness and efficiency of the designed watermarking scheme, Structure Similarity Index (SSI), Structure Dissimilarity Index (SDI), Structure Content (SC), Mutual Information (MI), energy, entropy, correlation, histogram tests, and classical attacks analysis are carried out for the proposed scheme. All these parameters are discussed in the following subsections along with obtained results.
4.1 Structure Similarity Index (SSI)
SSI test is used to compute similarity between two variables or (in our case) two images. The results of SSI primarily reveals pixel inter dependency relationship. Mathematically, it is computed as [1]:
where W represent watermarked image and R represents recovered image, respectively. The variables \(\mu _{W}\) and \(\mu _{R}\) compute the average values of W and R, respectively. The parameters \(\sigma _{W}\) and \(\sigma _{R}\) calculate variance of W and R, respectively. Similarly, the parameters \(\sigma _{WR}\) quantifies the covariance of image W and R. Likewise, the parameters \(C1 = (K1L)^{2}\) and \(C2 = (K2L)^{2}\) are utilized to stabilize the division with weak denominator, where \(L = 2^{\#bitsperpixel} - 1\), \(K1 = 0.01\) and \(K2 = 0.03\). The resultant SSI is 1 if two images are identical, otherwise it is between 0 and 1. From Table 1, SSI value of the proposed image watermarking is near to the ideal value 1. Hence, SSI test confirms that the watermarked image is closer to the original image.
4.2 Structure Dissimilarity Index (SDI)
SDI computes dissimilarities between two images i.e., host and watermarked image. Mathematically it is calculated as [4]:
From Table 1, one can see that the SDI value of the proposed image watermarking scheme is considerably small, which again confirms that the watermarked image is closer to the original image.
4.3 Structure Contents (SC)
SC is the measure of information content in an image. Mathematically, it is written as the ratio of the structural information contents of the original and watermarked images. SC is calculated as [4]:
In the above equation, O(i; j) represents original image and W(i; j) represents the watermarked image at index i and j while a and b illustrates the number of rows and columns, respectively. From Table 1, one can see that the values of SC is close to 1 for the proposed watermarking scheme that confirms the robustness of the proposed scheme.
4.4 Mutual Information (MI)
The statistical dependence between two random variables is determined by MI test. MI can also be used to quantify robustness efficiency against various image degradation [4]. Mathematically, MI can be computed as follows [4]:
where p(O, W) computes the joint probability distribution function of original and watermarked images while p(O) and p(W) computes the probability density functions in the individual images, respectively. The lower values of MI in Table 1 is a proof of good watermarking.
4.5 Energy
The disorder in texture can be computed via energy of an image. Energy of an image determines the information in an image in terms of the sum of squared values [4].
where E(i, j) is pixel value at position i and j. Low energy means that the entries in Gray Level Co-occurrence Matrix (GLCM) are almost equal while higher energy means that some entries in the GLCM have higher magnitudes. A lower value of energy is required in image watermarking. The computed value in Table 2 proves that the proposed watermarking scheme has small value of energy.
4.6 Entropy
Entropy test is used to calculate the degree of randomness of digital images. In watermarking, entropy is of great interest to approximate whether the watermarked image is similar to the original image or not. By assuming that an algorithm which output \(2^{8}\) symbols, its ideal entropy should be 8 bits. For a good watermarking scheme, entropy value of the watermarked image should be near to the original image entropy value. Mathematically entropy can be calculated as [17]:
In the above equation, \(p(x_{i})\) represents the probability of random variable x at \(i^{th}\) position. The calculated entropy for the proposed watermarking scheme is shown in Table 2. From Table 2, one can see that entropy values for watermarked and host images are approximately equal. Thus the proposed watermarking scheme can resist entropy attacks.
4.7 Correlation Analysis
Correlation coefficient determine similarity between variables. Mathematically, the correlation coefficient is written as [17]:
where
The variable Cov(O, W) represents the covariance of adjacent pixels between original image O and watermarked image W, respectively. Correlation coefficient values in horizontal, vertical and diagonal directions are highlighted in Table 2. From Table 2, one can see that the correlation coefficient values in all direction are almost same which confirms the similarity between watermarked and original images.
4.8 Histogram Analysis
The histogram shows the pixel distribution of a digital image. From Figs. 5d, e, f, j, k and l and 6d, e, f, j, k and l, it is evident that the histogram of the watermarked image is similar to the original image histogram. Furthermore, the histograms of the recovered watermark and recovered plaintext original images are also exactly similar to the original watermark and original plaintext images histograms. Hence, the histogram plot confirms that an intruder cannot detect any differences between original and watermarked images.
4.9 Classical Attacks Analysis
SHA-256 and plaintext image are utilized to produce the initial values of PWLCM chaotic maps \((z_{0})\). This makes the proposed watermarking dependable on the plaintext image. For a single pixel change in the original plaintext image, the proposed scheme will produce a totally different random number. Therefore, during extraction and inverse substitution of the watermark image, instead of generating the original watermark image, the algorithm will produce a totally different cipher watermark. As a result, the proposed watermarking scheme can resist ciphertext-only, chosen-plaintext and known-plaintext attack.
5 Conclusion
In this paper, a dynamic S-Box based efficient watermarking scheme is presented and statistically evaluated. The dynamic S-Box and PWLCM strengthen the security of the proposed scheme due to the dynamic nature. The initial condition for PWLCM was generated from the \(SHA-256\). The watermark is substituted with the values of dynamic S-Box. Due to the dynamic nature of S-Box, it is hard for the eavesdroppers to launch an attack on the proposed scheme. Lastly, LWT is applied on the host image and HL and HH blocks of host image were replaced with Least Significant Bits (LSBs) and Most Significant Bits (MSBs) of the substituted watermark. The efficiency and robustness of the presented watermarking scheme are tested against numerous security parameters which confirmed that the scheme is highly secure. Furthermore, at the receiver’s end, the proposed scheme can recover the original image without loss of any sensitive information. In future, we intend to optimize the proposed scheme by targeting the colored images rather than only gray-scale ones and we will also evaluate the scheme under numerous types of attacks.
Data Availability
Enquiries about data availability should be directed to the authors.
References
Abbas, N. A. (2015). Image watermark detection techniques using quadtrees. Applied Computing and Informatics, 11(2), 102–115.
Ahmad, J., & Hwang, S. O. (2015). Chaos-based diffusion for highly autocorrelated data in encryption algorithms. Nonlinear Dynamics, 82(4), 1–12 .
Baranovsky, A., & Daems, D. (1995). Design of one-dimensional chaotic maps with prescribed statistical properties. International Journal of Bifurcation and Chaos, 5(06), 1585–1598.
Batool, S. I., Shah, T., & Khan, M. (2014). A color image watermarking scheme based on affine transformation and s 4 permutation. Neural Computing and Applications, 25(7), 2037–2045.
Benhocine, A., Laouamer, L., Nana, L., & Pascu, A. C. (2013). New images watermarking scheme based on singular value decomposition. Journal of Information Hiding and Multimedia Signal Processing, 4(1), 9–18.
Chamlawi, R., Khan, A., & Usman, I. (2010). Authentication and recovery of images using multiple watermarks. Computers and Electrical Engineering, 36(3), 578–584.
Chang, C. C., Tsai, P., & Lin, C. C. (2005). Svd-based digital image watermarking scheme. Pattern Recognition Letters, 26(10), 1577–1586.
Chau, L. P., & Siu, W. C. (2003). Efficient multiplier structure for realization of the discrete cosine transform. Signal Processing: Image Communication, 18(7), 527–536.
Chen, L., Chen, J., Zhao, G., & Wang, S. (2019). Cryptanalysis and improvement of a chaos-based watermarking scheme. IEEE Access, 7, 97549–97565.
Chen, Y., Tang, C., & Yi, Z. (2020). A novel image encryption scheme based on pwlcm and standard map. Complexity, 2020, 3026972. https://doi.org/10.1155/2020/3026972.
Chu, W. C. (2003). Dct-based image watermarking using subsampling. IEEE Transactions on Multimedia, 5(1), 34–38.
Das, C., Panigrahi, S., Sharma, V. K., & Mahapatra, K. (2014). A novel blind robust image watermarking in dct domain using inter-block coefficient correlation. AEU-International Journal of Electronics and Communications, 68(3), 244–253.
Dawei, Z., Guanrong, C., & Wenbo, L. (2004). A chaos-based robust wavelet-domain watermarking algorithm. Chaos, Solitons and Fractals, 22(1), 47–54.
Fan, M., & Wang, H. (2009). Chaos-based discrete fractional sine transform domain audio watermarking scheme. Computers and Electrical Engineering, 35(3), 506–516.
Ghebleh, M., Kanso, A., & Own, H. S. (2014). A blind chaos-based watermarking technique. Security and Communication Networks, 7(4), 800–811.
Jamal, S. S., Khan, M. U., & Shah, T. (2016). A watermarking technique with chaotic fractional s-box transformation. Wireless Personal Communications, 90(4), 2033–2049.
Khan, J. S., Ahmad, J., Ahmed, S. S., Siddiqa, H. A., Abbasi, S. F., & Kayhan, S. K. (2019). Dna key based visual chaotic image encryption. Journal of Intelligent and Fuzzy Systems, 37(2), 2549–2561.
Khan, M., & Shah, T. (2015). A copyright protection using watermarking scheme based on nonlinear permutation and its quality metrics. Neural Computing and Applications, 26(4), 845–855.
Khan, M., Shah, T., & Batool, S. I. (2016). A new approach for image encryption and watermarking based on substitution box over the classes of chain rings. Multimedia Tools and Applications, 76(22), 24027–24062.
Wang, R., Shaocheng, H., Zhang, P., Yue, M., Cheng, Z., & Zhang, Y. (2020). A novel zero-watermarking scheme based on variable parameter chaotic mapping in NSPD-DCT domain. In IEEE Access, 8, 182391–182411. https://doi.org/10.1109/ACCESS.2020.3004841.
Lian, S., Chen, X., & Wang, J. (2012). Content distribution and copyright authentication based on combined indexing and watermarking. Multimedia Tools and Applications, 57(1), 49–66.
Liang, J., & Tran, T. D. (2001). Fast multiplierless approximations of the dct with the lifting scheme. IEEE Transactions on Signal Processing, 49(12), 3032–3044.
Lin, S. D., & Chen, C. F. (2000). A robust dct-based watermarking for copyright protection. IEEE Transactions on Consumer Electronics, 46(3), 415–421.
Lu, W., Sun, W., & Lu, H. (2012). Novel robust image watermarking based on subsampling and dwt. Multimedia Tools and Applications, 60(1), 31–46.
Lu, Z. M., Zheng, H. Y., & Huang, J. W. (2007). A digital watermarking scheme based on dct and svd. In Intelligent Information Hiding and Multimedia Signal Processing, 2007. IIHMSP 2007. Third International Conference on (Vol. 1, pp. 241–244). IEEE.
Moulin, P., & Mihcak, M. K. (2002). A framework for evaluating the data-hiding capacity of image sources. IEEE Transactions on Image Processing, 11(9), 1029–1042.
Mukherjee, D. P., Maitra, S., & Acton, S. T. (2004). Spatial domain digital watermarking of multimedia objects for buyer authentication. IEEE Transactions on Multimedia, 6(1), 1–15.
Patra, J. C., Phua, J. E., & Bornand, C. (2010). A novel dct domain crt-based watermarking scheme for image authentication surviving jpeg compression. Digital Signal Processing, 20(6), 1597–1611.
Rawat, S., & Raman, B. (2011). A chaotic system based fragile watermarking scheme for image tamper detection. AEU-International Journal of Electronics and Communications, 65(10), 840–847.
Roy, S., & Pal, A. K. (2017). A blind dct based color watermarking algorithm for embedding multiple watermarks. AEU-International Journal of Electronics and Communications, 72, 149–161.
Seo, J. S., & Yoo, C. D. (2006). Image watermarking based on invariant regions of scale-space representation. IEEE Transactions on Signal Processing, 54(4), 1537–1549.
Singhal, N., Lee, Y. Y., Kim, C. S., & Lee, S. U. (2009). Robust image watermarking using local zernike moments. Journal of Visual Communication and Image Representation, 20(6), 408–419.
Su, Q., & Chen, B. (2017). A novel blind color image watermarking using upper hessenberg matrix. AEU-International Journal of Electronics and Communications, 78, 64–71.
Thakur, S., Singh, A. K., Ghrera, S. P., & Elhoseny, M. (2019). Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimedia Tools and Applications, 78(3), 3457–3470.
Thakur, S., Singh, A. K., Ghrera, S. P., & Mohan, A. (2020). Chaotic based secure watermarking approach for medical images. Multimedia Tools and Applications, 79(7), 4263–4276.
Tong, X., Liu, Y., Zhang, M., & Chen, Y. (2013). A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Processing: Image Communication, 28(3), 301–308.
Vahedi, E., Zoroofi, R. A., & Shiva, M. (2012). Toward a new wavelet-based watermarking approach for color images using bio-inspired optimization principles. Digital Signal Processing, 22(1), 153–162.
Wang, X., & Jin, C. (2012). Image encryption using game of life permutation and pwlcm chaotic system. Optics Communications, 285(4), 412–417.
Wang, X., & Xu, D. (2014). A novel image encryption scheme based on brownian motion and pwlcm chaotic system. Nonlinear Dynamics, 75(1–2), 345–353.
Wu, X., & Guan, Z. H. (2007). A novel digital watermark algorithm based on chaotic maps. Physics Letters A, 365(5), 403–406.
Zhou, J., & Pang, M. (2010). Digital watermark for printed materials. In 2010 2nd IEEE international conference on network infrastructure and digital content (pp. 758–762). IEEE.
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Khan, J.S., Kayhan, S.K., Ahmed, S.S. et al. Dynamic S-Box and PWLCM-Based Robust Watermarking Scheme. Wireless Pers Commun 125, 513–530 (2022). https://doi.org/10.1007/s11277-022-09562-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09562-9