Abstract
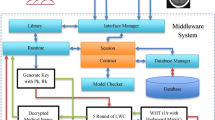
At present times, medical image security becomes a hot research topic in the healthcare sector. This paper presents an efficient lightweight image encryption model based on the Dynamic key generating Attribute based encryption (ABE) method with Opposition based joint Grey Wolf-Whale Optimization Algorithm (OjGW-WOA). The proposed encryption method undergoes certain pre-encryption steps like rotation and random column addition steps. Once the pre-encryption steps are done, ABE with OjGW-WOA is incorporated, where the optimal key is generated based on entropy value. In addition, the oppositional based learning concept is introduced to enhance the convergence rate and searching process of GWO and WOA algorithms. Next, the proposed encryption method is designed with a dynamic key generating model that generates updated keys during every time period. Therefore, during decryption, two-level key verification is done. At the first decryption stage, the key corresponding to that particular time period is required, then the original key is generated from that key and then employed for decrypting the original data. The proposed method is simulated using MATLAB tool and a detailed comparative results analysis is carried out. The performance of the proposed work is validated with the aid of performance metrics like Peak Signal to Noise Ratio (PSNR), number of changing pixel rate (NPCR) and unified averaged changed intensity (UACI). The experimental results stated that the presented model has resulted to a higher PSNR of 62.29 dB, NPCR of 99.23%, and UACI of 23.67%.










Similar content being viewed by others
Availability of Data and Material
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
Code Availability
Custom code.
Change history
02 April 2021
A Correction to this paper has been published: https://doi.org/10.1007/s11277-021-08444-w
References
Tan, Y., Xue, Y., Liang, C., Zheng, J., Zhang, Q., Zheng, J., & Li, Y. (2018). A root privilege management scheme with revocable authorization for android devices. Journal of Network and Computer Applications, 107, 69–82.
Cao, Y., Zhou, Z., Sun, X., & Gao, C. (2018). Coverless information hiding based on the molecular structure images of material. Computers, Materials and Continua, 54(2), 197–207.
Deng, X., Chen, Z., Zeng, F., Zhang, Y., & Mao, Y. (2013). Authentication and recovery of medical diagnostic image using dual reversible digital watermarking. Journal of Nanoscience and Nanotechnology, 13(3), 2099–2107.
Das, S., & Kundu, M. K. (2012). Effective management of medical information through a novel blind watermarking technique. Journal of Medical Systems, 36(5), 3339–3351.
Kanso, A., & Ghebleh, M. (2015). An efficient and robust image encryption scheme for medical applications. Communications in Nonlinear Science and Numerical Simulation, 24, 98–116.
Lima, J. B., Madeiro, F., & Sales, F. J. R. (2015). Encryption of medical images based on the cosine number transform. Signal Processing: Image Communication, 35, 1–8.
Mukhedkar, M., Powar, P., Gaikwad, P. (2015). Secure nonreal time image encryption algorithm development using cryptography & Steganography. In India conference (INDICON), 2015 annual IEEE (pp. 1–6). IEEE.
Daniel, R. M., Rajsingh, E. B., & Silas, S. A. (2018). Forward secure signcryption scheme with ciphertext authentication for e-payment systems using conic curve cryptography. Journal of King Saud University-Computer and Information Sciences. https://doi.org/10.1016/j.jksuci.2018.02.004
Nabil, E. (2016). A modified flower pollination algorithm for global optimization. Expert Systems with Applications, 57, 192–203.
Abdel-Basset, M., Manogaran, G., & Mohamed, M. (2018). Internet of Things (IoT) and its impact on supply chain: A framework for building smart, secure and efficient systems. Future Generation Computer Systems., 86, 614–628.
Abdel-Basset, M., Manogaran, G., El-Shahat, D., & Mirjalili, S. (2018). A hybrid whale optimization algorithm based on local search strategy for the permutation flow shop scheduling problem. Future Generation Computer Systems, 85, 129–145.
Song, Y., Wang, H., Wei, X., & Wu, L. (2019). Efficient attribute-based encryption with privacy-preserving key generation and its application in industrial cloud. Security and Communication Networks, 2019, 1–9.
Avudaiappan, T., Balasubramanian, R., Pandiyan, S. S., Saravanan, M., Lakshmanaprabu, S. K., & Shankar, K. (2018). Medical image security using dual encryption with oppositional based optimization algorithm. Journal of Medical Systems, 42(11), 208.
Sivaram, M., Lydia, E. L., Pustokhina, I. V., Pustokhin, D. A., Elhoseny, M., Joshi, G. P., & Shankar, K. (2020). An optimal least square support vector machine based earnings prediction of blockchain financial products. IEEE Access, 8, 120321–120330.
Shankar, K., Lakshmanaprabu, S. K., Gupta, D., Khanna, A., & de Albuquerque, V. H. C. (2020). Adaptive optimal multi key based encryption for digital image security. Concurrency and Computation: Practice and Experience, 32(4), e5122.
Funding
The author(s) received no specific funding for this study.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest. The manuscript was written through contributions of all authors. All authors have given approval to the final version of the manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original version of this article has been revised: The authors’ affiliation has been corrected.
Rights and permissions
About this article
Cite this article
Raja, M., Dhanasekaran, S. & Vasudevan, V. Opposition Based Joint Grey Wolf-Whale Optimization Algorithm Based Attribute Based Encryption in Secure Wireless Communication. Wireless Pers Commun 127, 635–655 (2022). https://doi.org/10.1007/s11277-021-08357-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08357-8