Abstract
This paper presents a robust color image steganography approach for image communication over wireless communication systems. The objective of this approach is to hide three color images in one color cover image to increase the capacity of hiding as most previously published steganography approaches suffer from a capacity problem. Moreover, the investigation of wireless communication of steganography images is presented in this paper to study the sensitivity of extraction of hidden images to the channel degradation effects, which is not studied appropriately in the literature. The proposed approach depends on the Discrete Cosine and Discrete Wavelet transform. The cover image is first transformed to luminance and chrominance components for embedding the images to be hidden. The secret images are encrypted by chaotic Baker map, which is a good representative of the family of permutation-based algorithms, which tolerate the channel degradations better. The investigated wireless communication system is the Orthogonal Frequency Division Multiplexing system with channel equalization. The simulation results reveal the success of the proposed work for robust image communication.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The idea of image steganography is hiding image in another cover image. The objective of any image steganography scheme is to secure some secret images from intruders. Both secret images and the cover image need to be saved from deteriorations. The cover image quality and hidden image secrecy are main targets [1].
Although last image steganography approaches are widely used for securing secret data, they have problems such as capacity or the quality of steganography image or security or noise. Different approaches have been presented for image steganography based on spatial and transformed domains such as Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) [2]. Hussain et al. presented a survey on spatial domain techniques implementing Least Significant Bit (LSB) approaches [3]. Sandoval et al. presented a spatial domain image steganography method by embedding data in pixel values directly [4]. This method is subjected to removal of the secret image through simple manipulations such as filters. Sheidaee et al. presented DCT steganography approach, whose basic idea is to embed data in DCT lowest and medium coefficients [5]. Kim et al. performed image steganography based on block matching in DWT [6]. Steganography approaches have been studied in the literature without consideration of the wireless communication segment. With the modern advances in communication systems and the bad need to secure images through the communication process, there is a necessity to investigate the robustness of the steganography process in the presence of communication channel degradations. OFDM is the most widely used wireless communication technology. OFDM doesn’t need complex equalization filters. It uses many slowly modulated narrowband signals rather than the rapidly modulated wideband signal. Therefore, the channel equalization is simplified so that they are considered as the advantages of OFDM. OFDM presents low symbol rate, which makes a guard interval between symbols, and also it has the capability to eliminate Inter-Symbol Interference (ISI), echoes, and time-spreading [7,8,9]. This work is divided into two parts, The objective of the first part is performing steganography approach, which achieves high security and high capacity with keeping the quality of steganography image. The objective of the second part is studying the effect of channels through OFDM on this proposed approach.
2 Related Work
Most of the researches carried out in the area of image steganography depend on DCT, DWT, and the LSB. This part offers the latest methods for hiding data in a cover image. In [10], the researchers used Advanced Encryption Standard (AES) encryption algorithm on a secret image in order to increase safety. In order to embed secret image, IWT, and LSB are used after dividing the host image into blocks. Due to using blocks, there is a little distortion in the steganography image. If there is an increase in the size of the data, the distortion will be clear in the steganography image. In [11], the proposed method depends on DCT. At the first,the authors used filter to determine the position of the edges of color image, so they used limited size of data. After that performing DCT on (Red, Green, Blue) channels of the image. The half difference of coefficients of (Red, Blue) represents 0 and a half average of coefficients of (Red, Blue) represents 1 from embedded data. After that, they put them in an equal position of green coefficients. If there is noise, the positions of edges will be changed and the extracted data will be deformed.
In [12], the authors used an image scrambling in order to preserve the privacy of image contents, after that it’s converted to an un correlated color space HSV. On the other hand, an Iterative Magic Matrix Encryption Algorithm (IMMEA) encrypts the secret data. In order to embed data into V plane of HSV color model, LSB method is used. This way gives high quality for steganography images with low capacity because it used one plane of HSV color model. In [13], the researchers implemented image steganography by embedding message to LSB of quantized DCT coefficients which is performed on YCbCr components of cover image. In [14], the authors used fuzzy edge detection in order to detect the edges of image for embedding secret data in it by LSB method. this method gives high quality. The idea of the technique in [15] is embedding encrypted secret text into 2D Haar Discrete Wavelet Transform coefficients of YCbCr model channels. Despite getting high PSNR, the size of secret data is small. The method in [16] allows embedding of three secret images in the RGB color coordinate system using DWT. Secret images and cover image are divided into four bands by DWT and embeds LL bands of color plans of secret images into three color plans of cover image.
The previously mentioned approaches and some others used spatial domain and frequency domain with properties of the cover image. The enhancement of data security maintains the quality of the steganography and secret images. In this study, image steganography used an uncorrelated color space, DWT, DCT, and chaotic Baker map encryption are adopted to achieve security. The second part of this paper presents transmitting steganography image through OFDM over wireless channels and study their effects on the reconstructed images.
3 The Proposed Algorithm of Image Steganography
The first part of this research proposes a new technique. The proposed technique is divided into two algorithms (Embedding and Extracting). We have used encryption, DCT and DWT inorder to make it more secure.
3.1 Embedding of Secret Images
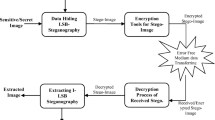
It illustrates how to hide three secret images in the cover image as shown in Fig. 1. The cover image size is chosen to be (512 × 512). The payload images have equal size (256 × 256) because the size of each band from DWT on the cover image is (256 × 256), It is necessary to perform encryption to increase security. This proposed algorithm used high frequency bands (LH, HL, HH),so we can embed three secret images with size (256 × 256) in these bands.
Step 1 Chaotic Backer map encryption is used for changing the order of pixels of secret images with a key. It’s used with DCT to prevent any attacker from knowing secret data.
Step 2 The red, blue, and green components of both the cover and encrypted secret images are separated.
Step 3 The red, blue and green components are normalized to a maximum of 1.
Step 4 Normalized components (Rn,Gn,Bn) are converted to Y,Db,Dr components in order to increase the security.
Step 5 DWT is performed on each of the normalized components of the cover image and DCT performed on each of the RGB normalized component of the secret images.
Step 6 Gain coefficient (α1) is multiplied by DCT coefficients of each normalized channel of RGB model for each secret image. DWT coefficients in (LH,HL,HH) bands for each channel of YDbDr color model of the cover image are combined with DCT coefficients of the normalized channels of RGB model of each secret image. \(M(x,y) = C(x,y) + \alpha_{1} P(x,y)\),where M is considered to be DWT coefficients of each component of YDbDr color model of modified cover image, C is DWT coefficients of (LH “Vertical details”, HL” horizontal details “,HH “diagonal details”) bands for every channel YDbDr of original cover image, P is DCT of normalized channels of RGB model for each payload image, α1 is chosen in such a way that the payload images are not visible in the steganography image.
Step 7 Inverse DWT is performed on each channel resulting from the combination.
Step 8 “YDbDr” is converted to RGB on results from step 7 to get a steganography image.
3.2 Extracting of Secret Images
The extracting algorithm explains how to extract three secret images from steganography image by knowing the cover image at the receiver as shown in Fig. 2.
Step 1 Red, Blue and Green components of both the steganography and cover images are separated.
Step 2 All the three components in both cases are normalized.
Step 3 The normalized channels are converted to “YDbDr” channels.
Step 4 2-D DWT is performed on components resulting from step 3 on cover and steganography images using DWT.
Step 5 The difference between high coefficients bands of DWT(LH “Vertical details”, HL” horizontal details “,HH “diagonal details”) for each channel of steganography and cover images is performed. Inverse DCT is computed for difference components for each channel coefficients.
Step 6 RGB components resulting from step 5 are combined inorder to get the extracted encrypted secret images.
Step 7 The chaotic Backer map decryption with the key is performed to get the extracted images.
3.3 Analysis to Get Values of α 1
By obtaining the relation between α1 and PSNR for all reconstructed images as shown in the curve found in Fig. 3. The Peak Signal to Noise Ratio (PSNR (dB)) is one of the public matrices for evaluating the quality of images. It’s clear from the curve, 0.08 is the best value of α1 inorder to get the best PSNR for all reconstructed image.
3.4 Stego Image with an Additive White Gaussian Noise
If we add white Gaussian noise to the stego image, where the range of SNR from (1 to 100). It’s observed that the curve in Fig. 4 has a good PSNR at α1 = 0.08 for all reconstructed image. Stego image has a good quality at noise as shown in Fig. 5. Figure 6 shows the reconstructed images at SNR = 30 dB.
4 Transmitting Steganography Image in OFDM with Gaussian and Rayleigh Fading Channels
4.1 Transmitting Steganography Image Through OFDM
-
Figure 7 illustrates OFDM system where the input is steganography image obtained from the embedding algorithm.
-
In OFDM modulation block, we used Quadrature Amplitude Modulation QAM with order 2. High efficiency is resulted from utilizing QAM obtained by setting a suitable constellation size in order to match the noise level of the communications channel.
-
The pilot symbol is transmitted with the received signal to detect the OFDM symbol start. It can also be used for channel estimation. Sam in [17] used pilot symbols for analysing and implementation of channel estimation in OFDM system, where the pilot symbol has a special symmetry so that the pilot symbol doesn’t need to be known at the receiver.
-
The IFFT block computes Inverse Fast Fourier Transform for high-efficiency signal processing.
-
One of the solutions to overcome the Rayleigh channel effect is using OFDM with a Guard Interval (GI) [18], because it resists propagation delays, and reduces interference to the next user.
4.2 Transmitting Steganography Image in OFDM with Modification
Figure 8 illustrates the modified OFDM system, it utilizes Least Square estimation channel (LSE). These fading profiles introduce inter-symbol interference, it must be compensated by using channel estimation to enhance the quality of steganography image. After that, guided image filter has been used. The content of a guidance image is utilized by the guided filter to make filtering on a specific image, which can be the input image itself or another different image. The guided filter is based on an edge preserving smoothing operator. The guided filter is widely performed in a great variety of computer vision and computer graphics applications because of its noise reduction, detail smoothing/enhancement [19]. The modification in the receiving side of OFDM has been introduced in order to enhance the performance of OFDM system on transmitted image over wireless channels.
5 Results and Discussion
Table 1 shows results at Rayleigh fading and AWGN channels at delays = [0,1e09], Gain = [0,0], SNR = 30 dB, and size of steganography _color image is 512 × 512. It’s clear that the AWGN and Multipath Fading channels have a very bad effect on transmitting steganography image through OFDM system. Due to these channels, the steganography image will have noise and the value of pixels will be changed, then the steganography and the secret image will be destroied. The correlation coefficient represents the performance of steganography image through OFDM, where a higher correlation coefficient means that the reconstructed images have a high quality. As a result of bad outputs, the OFDM system must be modified to get better results and enhances the quality of reconstructed images. So, channel estimation and filter are used to compensate the errors resulting from wireless channels. Correlation coefficients for reconstructed images obtained from the modified OFDM are listed in Table 2. The correlation coefficient equals 1 when there is no change in the image. From Fig. 9, it is clear that using LS channel estimation gives a good quality for reconstructed images. And also Table 3 shows the Doppler Effect on reconstructed images through OFDM with modification. Despite the noise generated by AWGN and Rayleigh channels, the quality of reconstructed images is good at different Doppler shift values at SNR = 30 dB. The algorithm that’s found in [10] embeds data in LSB of high coefficients of IWT of the blocked cover image, The quality deteriorates if the size of the secret image further increases, The algorithm in [12],when the percentage of secret data becomes 72,74% the PSNR of stego image will be 21.96. The idea of this algorithm is embedding data in LSB of V plane of HSV conversion of an encrypted cover image. Despite the highest PSNR, the capacity of secret data is low. The algorithm found in [13] depends on the properties of cover image YCbCr, the embedding process based on LSB technique with DCT transform. The capacity is low with small PSNR.In this proposed approach the capacity percentage of secret data is 75% compared with the latest algorithms found in Table 4. The proposed approach of steganography enables us to embed the highest capacity of secret data, where the capacity is the number of bits that can be embedded in cover media. Additionally using color space YDbDr gives high quality and high security compared to others color spaces models as shown in Table 5. From Fig. 10,it’s clear that BER gotten from OFDM system modification is satisfied compared with transmitting the image over AWGN channel in methods [10]. As shown in Fig. 11, it’s clear that OFDM with modification gives the lowest BER compared with OFDM without modification over AWGN and Rayleigh channels.
6 Conclusion
This paper has introduced an efficient approach for embedding and extracting steganography data, and also the proposed approach enables us to hide three images in one cover image. It also achieves more security because of using a gain coefficient (α1), merging two different types of image transforms and encryption. In this paper, the effect of AWGN and multipath fading channels on the steganography image and the extracted data through OFDM system has been studied. In order to reduce the distortion resulted from wireless channels, the modification on OFDM system has been performed. Simulation results are promising towards a more efficient colour steganography scheme.
References
Tripathi, D., & Sharma, S. (2016). A robust 3-SWT multiple image steganography and contrast enhancement technique. In 2016 International conference on inventive computation technologies (ICICT), Coimbatore, 2016 (pp. 1–6).
Malathi, P., & Gireeshkumar, T. (2016). Relating the embedding efficiency of LSB steganography techniques in spatial and transform domains. Procedia Computer Science,93, 878–885.
Hussain, M., Wahab, A. W. A., Idris, Y. I. B., Ho, A. T. S., & Jung, K.-H. (2018). Image steganography in spatial domain: A survey. Signal Processing: Image Communication,65, 46–66.
Sandoval, O. J., Hernandez, M. C., Miyatake, M. N., Meana, H. P., & Toscano, K. (2016). MedinaImageadaptive steganalysis for LSB matching steganography. In 2016 39th international conference on telecommunications and signal processing (TSP) (pp. 478–483).
Sheidaee, A., & Farzinvash, L. (2017). A novel image steganography method based on DCT and LSB. In 2017 9th International conference on Information and Knowledge Technology (IKT), Tehran (pp. 116–123).
Kim, J., Park, H., & Park, J. (2017). Image steganography based on block matching in DWT domain. In 2017 IEEE international symposium on broadband multimedia systems and broadcasting (BMSB), Cagliari (pp. 1–4).
Tiwari, R., Pathak, A., & Mishra, R. (2014). A study on steganography image. Journal of Science, Engineering and Technology Research (IJSETR), 3(10).
Hariprasad, N., & Sundari, G. (2015). Comparative analysis of the BER performance of DWT OFDM over that of FFT OFDM in presence of phase noise. In 2015 International conference on robotics, automation, control and embedded systems (RACE), Chennai (pp. 1–4).
Wang, Zhongpeng, Chen, Fangni, Qiu, Weiwei, Chen, Shoufa, & Ren, Dongxiao. (2018). A two layer chaotic encryption scheme of secure image transmission for DCT precoded OFDM-VLC transmission. Optics Communications,410, 94–101.
Seethalakshmi, K. S., Usha, B. A., & Sangeetha, K. N. (2016). Security enhancement in image steganography using neural networks and visual cryptography. In 2016 International conference on computation system and information technology for sustainable solutions (CSITSS), IEEE conference publications (pp. 396–403).
Lahiri, S., Paul, P., Banerjee, S., Mitra, S., Mukhopadhyay, A., & Gangopadhyaya, M. (2016). Image steganography on coloured images using edge based Data Hiding in DCT domain. In 2016 IEEE 7th annual information technology, electronics and mobile communication conference (IEMCON) (pp. 1–8).
Muhammad, K., Sajjad, M., Mehmood, I., Rho, S., & Baik, S. W. (2016). Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Future Generation Computer Systems (in press, Corrected Proof, Available online 27 November 2016).
El Rahman, S. A. (2016). A comparative analysis of image steganography based on DCT algorithm and steganography tool to hide nuclear reactors confidential information. Computers and Electrical Engineering (Available online 19 September 2016).
Dadgostar, H., & Afsari, F. (2016). Image steganography based on interval-valued intuitionistic fuzzy edge detection and modified LSB. Journal of Information Security and Applications,30, 94–104.
Broda, M., Hajduk, V., & Levický, D. (2015). Image steganography based on combination of YCbCrcolor model and DWT. In 2015 57th international symposium ELMAR (ELMAR), Zadar (pp. 201–204).
Baby, D., Thomas, J., Augustine, G., George, E., & Michael, N. R. (2015). A novel DWT based image securing method using steganography. In International conference on information and communication technologies (ICICT 2014).
Sam, J. A., & Nair, A. K. (2016). Analysis and implementation of channel estimation in OFDM system using pilot symbols. In 2016 International conference on control, instrumentation, communication and computational technologies (ICCICCT), Kumaracoil (pp. 725–728).
Odarchenko, R., Tkalich, O., Shevchuk, Z., & Lukin, S. (2015). OFDM signal formation with adaptive guard interval duration change. In 2015 Second international scientific-practical conference problems of infocommunications science and technology (PIC S&T), Kharkiv (pp. 216–219).
Jia, Y., Rong, C., Wu, C., & Yang, Y. (2017). Research on the decomposition and fusion method for the infrared and visible images based on the guided image filtering and Gaussian filter. In 2017 3rd IEEE international conference on computer and communications (ICCC), Chengdu (pp. 1797–1802).
Mannan, A., & Habib, A. (2017). Adaptive processing of image using DWT and FFT OFDM in AWGN and Rayleigh channel. In 2017 International conference on communication, computing and digital systems (C-CODE), Islamabad (pp. 346–350).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Eyssa, A.A., Abdelsamie, F.E. & Abdelnaiem, A.E. An Efficient Image Steganography Approach over Wireless Communication System. Wireless Pers Commun 110, 321–337 (2020). https://doi.org/10.1007/s11277-019-06730-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06730-2