Abstract
In this paper, we propose a tree-based time division multiple access (Tree TDMA) media access control (MAC) algorithm based on the IEEE 802.15.4 PHY standard. The method involves the simultaneous use of two algorithms, a time slot allocation algorithm (TSAA) and a frequency slot allocation algorithm (FSAA), at low power consumption to support voice and data communication to solve the problems afflicting prevalent MAC protocols in tree topology networks. The TSAA first generates routing paths through the control channel in a super frame prior to transmitting packets, and allocates time slots for each node to transmit packets. The FSAA then allocates frequencies to each path according to the routing paths generated following its application. The overhearing problem and the funneling effect in TDMA as well as carrier sense multiple access with collision avoidance (CSMA/CA) MACs are resolved by these two algorithms because a given node and its neighbors are orthogonal in terms of time and frequency. The problem of inter-node synchronization is addressed by periodically sending a beacon from higher to lower nodes, and the issue of low power is solved by leaving unsigned time slots in an idle state. To test the effectiveness of the proposed algorithm, we used a MATLAB simulation to compare its performance with that of contention-based CSMA MAC and non-contention-based TreeMAC in terms of network throughput, network delay, energy efficiency, and energy consumption. We also tested the performance of the algorithms for increasing number of nodes and transmission packets in the tree topology network.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Early wireless sensor networks (WSNs) were considerably limited in the provision of services such as voice or multimedia communication because the main function of media access control (MAC) at the time was to monitor sensor data from devices without guaranteeing successful or timely delivery. The representative MAC protocol featuring this characteristic is carrier sense multiple access with collision avoidance (CSMA/CA). It incurs a significant overhead according to the depth of the relevant tree topology network and the funneling effect. The funneling effect is typically generated when packets are transferred from a lower node to a higher one in a tree topology network. It leads to packet transmission delays and inefficient energy consumption, with the consequence that successful and timely delivery cannot be guaranteed. Time division multiple access (TDMA)-based MAC has recently been proposed to solve the above problem. However, it has not been widely used in WSNs because it can reduce packet transmission efficiency while trying to prevent packets from being overheard and adjusting inter-node synchronization according to the topology at hand.
Among WSNs using CSMA/CA MAC, ZigBee has been widely used. It is based on the IEEE802.15.4 physical layer (PHY) and the CSMA MAC. It exhibits poor performance in terms of data transmission efficiency unless the MAC of ZigBee dynamically manages the channel by designating active and inactive intervals to reduce energy consumption. Moreover, ZigBee struggles to support voice communication, and invariably incurs a delay because of limited bandwidth and the delay characteristics of sensor networks. Nonetheless, because it can be simply implemented using the IEEE 802.15.4 MAC, and it supports low energy consumption as well as the star, tree, and mesh topologies, it is among the most widely used sensor network protocols.
The ZigBee Alliance has recently begun distributing CSMA/CA network-based standards for automation, remote control, smart energy profiles, ZigBee healthcare, home automation, input devices, light links, retail services, and telecom services to expand ZigBee’s field of application in order to compensate for the limited service due to CSMA/CA. Of these, telecom only provides service between devices. However, research is underway on providing Voice over IP (VoIP) services that utilize codecs and the Session Initiation Protocol (SIP).
The commonly used tree topology sensor network is classified into a sink node and a general node. It is a widely used topology for data monitoring that requires variation from low to high speed owing to the generation of tree-form traffic while transmitting data from the general node to the sink node. Traditional MAC protocols, such as ALOHA and CSMA, that do not have traffic channel control at traffic generation create a funneling effect [1] that increases traffic congestion as packets approach the sink node in the tree sensor network by increasing the number of reattempts as well as the backoff time. This causes a sudden increase in network delay as well as traffic congestion and greater energy consumption at each node. Therefore, subsequent MAC protocol design aims at a short duty cycle in order to resolve these issues [2,4,5,6,6].
Unlike these contention-based MACs, non-contention-based time division multiple access (TDMA) MAC focuses on timely delivery when transmitting sensor data. Representative protocols include data gathering MAC (D-MAC) [2], Pattern MAC (PMAC) [3], Tree Search Resource Auction Multiple Access (TRAMA) [7], Tree MAC (TreeMAC) [8], Voice-over-sensor-network (VoSN) MAC [9], Sparse Topology Management Schemes (SETM) [10], and Modified T-MAC (MT-MAC) [11]. Of these, D-MAC and PMAC were designed to reduce transmission delays in data transmission due to operating time syncing between neighboring nodes. Nodes that collect data using Sensor MAC (S-MAC) [12] and Timeout MAC (T-MAC) [13] transmit them to the sink node with improved latency, throughput, efficiency, and node fairness using adaptive time slot scheduling according to traffic in neighbor nodes.
The distribution election technique [7] has recently been used in the TRAMA protocol. The technique uses the traffic information of each node to determine an appropriate time slot for it to transmit data in order to prevent collisions with unicast or broadcast transmission. The advantages and disadvantages of TDMA-based and CSMA-based protocols have also been studied, and a TDMA/CSMA Hybrid (Z-MAC) [14] that uses distributed randomized TDMA (DRAND) [15] has been proposed to determine the number of allocated slots for each node.
Z-MAC supports two modes: low contention level (LCL) and high contention level (HCL) in a node. Any node can compete for access to a transmission slot in the LCL mode, whereas the owners and the slots belonging to their one-hop neighbors that are used to transmit data can only compete for access to the transmitting slot channel in the HCL mode. In these modes, the slot owners have higher priority than non-owners. However, the funneling effect in the tree topology networks is not discussed in Z-MAC. This effect is caused by inefficient processing of concentrated data packets from distal nodes to those proximate to the sink node. Tree-based protocols have recently been proposed to solve these problems [1, 8, 16].
TreeMAC is a TDMA-based MAC that uses frame-slot schedule assignment (FSA) in tree topology networks. It involves the assignment of three time slots to each node in a frame to guarantee reliable transmission and simultaneously prevent the funneling effect that occurs when collecting data in the sink node. TreeMAC consists of three time slots with a frame, which is defined as the time cycle where all nodes attributed to a tree can transmit data to the sink node without interference. Each node assigns frames depending on the data transmitting demand of its child node, and a frame consists of three slots to send, receive, or sleep for conflict-free packet scheduling. As a result, this method can solve the problem of overhearing by blocking transmission interference among nodes over a two-hop distance using FSA. TreeMAC can help avoid collision during packet transmission using FSA, transmit packets without buffering, and provide high transmission efficiency for the sink node. Despite these advantages, TreeMAC makes it difficult to combine data packets and filter them, thus preventing balanced power consumption because the slot of each frame can be in any of the sleep, transmission, and receive modes. Further, it has a transmission issue whereby the lowest node only transmits data in the direction of the sink node.
The VoSN MAC, which is a TDMA-based MAC that uses RTP and SIP with the time division multiple access (TDMA)/time division duplex (TDD) method, has recently been proposed. It uses an SF of 20 ms to support voice, and provides a pilot channel to sync nodes, the paging and access channels for down-link and up-link control, respectively, and six voice traffic channels. However, because this MAC only supports star topology networks, it only consists of a coordinator and devices for channel distribution, and hence needs a gateway to work with the SIP network, which is a heterogeneous network that supports larger networks [9, 17, 18].
To resolve the issues in contention-based MAC and non-contention-based TDMA MAC, hybrid MACs comprising two MACs have been proposed in recent research. Representative protocols include Sparse Topology and Energy Management (STEM) [10], MT-MAC [11], Energy-efficient and QoS-aware MAC (EQ-MAC) [19], QoS-aware MAC (Q-MAC) [20], Z-MAC, TDMA based multichannel MAC (TMMAC) [21], Traffic-adaptive MAC (TRAMA) [7, 22], and self-organizing media access control for sensor networks (SMACS) [23, 24]. Although these hybrid MACs improve performance in terms of network throughput, delay, and so on, they exhibit limited effectiveness in addressing the funneling effect, overhearing problem, and energy consumption.
In this paper, we propose a Tree TDMA MAC consisting of a TSAA and an FSAA to compensate for the drawbacks of contention-based MACs, such as the traditional ALOHA and CSMA, as well as non-contention-based TDMA MACs, and simultaneously support voice and data using full duplex communication in a tree topology network. Tree TDMA MAC is a hybrid MAC where the control channel and the traffic channel use CSMA/CA and TDMA MAC, respectively. The control channel uses CSMA/CA MAC to generate a routing table for the Ad-hoc On-demand Distance Vector (AODV), and serves as a transmitting/receiving channel for the association of devices and dispatch-related commands. The traffic channel serves as a communication channel for the transmission and reception of voice and data using TDMA MAC.
The AODV routing algorithm operates by SF unit and determines the routing path for packet transmission from source to destination through the TDMA traffic channel. If a node is not included in the routing path, the SF of that node remains idle to minimize energy consumption. Once the routing table is updated by the AODV algorithm, the path for the transmission of packets from source to destination is determined and the slot for the node along the path is assigned by the TSAA. During this, the unassigned slots remain idle to minimize energy consumption. On the contrary, if multiple routing paths are required to transmit multiple packets, each frequency value is assigned by the FSA according to the routing path to prevent the overhearing problem in the same slot between an owner node and its neighbors beyond one hop.
Unlike traditional MACs that use only a single frequency, Tree TDMA MAC supports full-duplex communication multiplexing voice and data while minimizing the funneling effect and the overhearing problem, and ensuring low power consumption, and timely and guaranteed delivery because it uses multiple frequencies unlike other traditional MACs. Furthermore, it improves the efficiency of channels, the irregular data transmission delays in contention-based WSNs, and the overhearing problem in non-contention- and contention-based MACs without reducing channel capacity. In Tree TDMA MAC, a reason for having such properties is that it has characteristics such as frequency channel orthogonality and TDMA-based time channel orthogonality.
The proposed Tree TDMA MAC can be utilized in small-scale military communication networks or emergency disaster communication networks that require ultra-low power and a multi-hop environment. It can also be used in the Internet of Things (IoT), which will require real-time data monitoring in the near future using the characteristics of timely and guaranteed delivery in a sensor network environment. The remainder of this paper is organized as follows. In Sect. 2, we propose the protocol design and algorithm of the Tree TDMA MAC. In Sect. 3, we analyze the performance of our method through an experiment. Finally, we present our conclusions in Sect. 4.
2 Tree TDMA MAC: Principles and Design
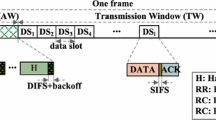
The SF structure and slot specification for full duplex transmission of voice and data in a tree-based topology using Tree TDMA MAC are shown in Fig. 1 and Table 1, respectively. In general, a transmission bandwidth of over 56 Kbps is required to support voice communication. However, it is difficult to accommodate more than four TDMA channels even without overhead, because the sensor network transmission bandwidth in IEEE 802.15.4 is limited to 250 Kbps and the protocol can only support one to three channels if overhead is considered. A voice codec such as G.729, G.711 and etc. [9, 17, 18] are typically used to overcome limited transmission bandwidth, and the design of Tree TDMA MAC in this paper is based on the G.729 voice codec.
As the G.729 codec processes input/output intervals of 20 ms with compression and decompression, the duration of the SF of the Tree TDMA MAC frame, aBaseSuperframeInterval, is set to 1250 in Table 1. This is because a symbol represents 16 \(\upmu \)s, and therefore, 20 ms is equivalent to 1250 symbols in IEEE 802.15.4 PHY. A traffic channel is designed to have a packet length of 40 bytes, consisting of a payload of 20 bytes, a header of 10 bytes, and 10 reserved bytes for symbol interference (SI) and redundancy in the future. The default value of aBaseTrafficDuration is set to 80 symbols, since 80 symbols are converted into 40 bytes, the default value of aBaseTrafficCount is set to 12 slots, and hence aTrafficInterval has a value of 960 symbols.
The duration of the beacon message, aBaseBeaconDuration, is set to be able to obtain information from the synchronization between a given node and neighboring nodes, and its default value is set to 10 symbols. aBaseControlDuration is the duration of the control channel, and its default value is set to 230 symbols because this channel is used for transmitting/receiving AODV routing messages, updating network associations, exchanging information between neighboring nodes, and transmitting short messages that do not require timely delivery. The guard time is used to correct SF synchronization between nodes in the tree topology network, and to consider propagation delay and multiple paths. Hence, the default value of aBaseGuardDuration is set to 50 symbols.
As shown in Fig. 1, controls the active and the inactive slot intervals of SFs to minimize energy consumption. If the difference in the values of the arithmetic sequence is d, the active slot of the SF is defined as \(SF^{d}_{a}\), and is represented by the following equation:
where,
Here, because we assume that the value of d as the distance between two SFs is \(1, 2,\ldots , d_{max}\), \(d_{max}\) as the maximum value of aBaseMaxSFDistance is set as 100, and the duration of a SF is 20 ms, we can know that the maximum period of an active SF is 2 s. A Personal Area Network (PAN) coordinator then receives the cumulative buffer size information for the packet transmitter from subordinate nodes every 2 s, and the value of d decreases by one until the maximum buffer size of a node among subordinate nodes in an active SF becomes 0. If the buffer size of the packet transmitter of this subordinate node becomes 0, the value of d increases by one until it becomes aBaseMAXSFDistance to manage QoS.
Figure 2 shows an example of tree topology network using Tree TDMA MAC, and Fig. 3 shows the channel structure of each node generated according to the topology in Fig. 2. In Fig. 3, transmit and receive slot are alternately generated in the traffic channel. If the depth value is odd, the generating order is the transmit slot followed by the receive slot. If the value is even, the alternately generated order begins with receive followed by transmit to generate the traffic channel. In general, the duration of the time slot increases in a tree topology network when approaching a higher sink node, and more time slots are required, especially for middle-level nodes where traffic tends to concentrate, as shown in Fig. 3. This may cause greater congestion and degraded throughput performance in a many-to-one tree TDMA MAC structures. Therefore, to maximize throughput performance and reduce congestion, the configuration of routing paths by SF unit should be prioritized, and it is important to optimally schedule time slots based on the routing paths. Table 2 shows the notation that will be used in this paper.
The topology in Fig. 2, which will be used in this paper, has a structure consisting of 10 nodes in a tree of depth 5. Here, node \(n_{1}\) is used as a PAN coordinator and nodes \(n_{2}\)–\(n_{10}\) as device nodes. The PAN coordinator provides a reference beacon for devices within the same PAN and synchronizes with other PAN coordinators through a protocol. The device node receives the beacon signals from the PAN coordinator to maintain SF synchronization, and transmits the beacon signal to the lower nodes, an example of TSAA can be expressed as the path set of each path element in Tree TDMA MAC:
When four routing paths to node \(n^{1}_{1}\)–\(n^{5}_{7}\), \(n^{5}_{7}\)–\(n^{1}_{1}\), \(n^{1}_{1}\)–\(n^{5}_{9}\), and \(n^{5}_{9}\)–\(n^{1}_{1}\), according to the path shown in the tree topology network of Fig. 2, are generated (and entered into the shortest path table) using the AODV algorithm. The set of paths is defined as \(l=\{l_{1}, l_{2}, l_{3}, l_{4}\}\). The path elements of \(l^{d}_{i}\) are converted into a time slot for each \(s^{j}_{ld}\) node according to the TSAA in the Tree TDMA MAC in Fig. 4, and the system creates a slot assignment table for the SF of each node.
In Fig. 1, the time slots in these SFs are in one of three states: transmit, receive, and sleep. Figure 3 shows the consequence of time slots assignment to each node during an SF by the TSAA of Tree TDMA MAC, when two full duplex voice and two data traffic loads are generated in this tree topology network. In this process, when an SF of the particular node in set \(l^{d}_{i}\), which is the set element of routing path l is active, the status of the time slot of the node that is not in path set \(l^{d}_{i}\) is changed to the sleep state, and that of the node in the path set \(l^{d}_{i}\) is changed to active. The transceiver is turned off to minimize energy consumption when the SF is inactive or the slot is in the sleep state even though the SF is active.
On the contrary, each node is assumed to have a buffer required to transmit/receive. For the case where data transmission occurs in the neighboring node of an owner node at any given time during packet transmission from source to destination, if the target neighboring node does not have more receiving slot resources within the same SF, the packet changes to pending status, as with slot \(R_{4}\) of \(n_{3}\) node in Fig. 3, and can be transmitted only in the time slot reassigned by the TSAA for the next SF.
Figure 3 shows the consequence of time slots assigned to each node during an SF by the TSAA of Tree TDMA MAC, when two full duplex voice and two data traffic loads are generated in this tree topology network. Figure 4 shows a flowchart of the TSAA in Tree TDMA MAC for the assignment of time slots to the SFs of nodes along a path when transmitting a packet from the sync node, which is the PAN coordinator in the tree topology network of Fig. 2, to the lowest node. The TSAA of Tree TDMA MAC generates the routing path set \(l=\{l_{1}, l_{2}, l_{3}, l_{4}\}\) using the AODV routing algorithm and assigns time slots in the following order:
-
1.
In an early stage shown in Fig. 4, all slot S sets assigned to each node are initialized to 0; their super frame index SF is set to 0 as well, whereas l and d is initialized to 1; L is the number of maximum paths of l and D is the number of maximum depths of d.
-
2.
It is assumed that the source and the destination are determined in the node that requires packet data transmission, and path l is generated, as shown in Fig. 3, by the shortest path AODV routing algorithm.
-
3.
If packets are not transmitted during an SF, they are saved in the buffer of the relevant node and transmitted at the next SF.
-
4.
As shown in Fig. 3, if the value of depth d is odd, time slots are generated to send and receive slot order, otherwise, d is even, time slots are generated to receive and send orders during an SF.
-
5.
As shown in Fig. 3, if a packet is transmitted from the sync node to a lower node, a time slot is assigned at path l = 1, depth d = 1, and slot number j = 0, and the slots for d and d + 1 are assigned following confirmation that the relevant slot and the d + 1-th slot are in use.
-
6.
Slots are assigned until the value of depth d becomes the maximum depth value D of the destination node, and Step 5 is repeated until path l becomes the maximum path L by increasing the value of l by one.
-
7.
In an early stage shown in Fig. 5, all slot sets S assigned to each node are initialized to 0; whereas l and d is initialized to 1; and L is the number of maximum paths of l and D is the number of maximum depths of d.
-
8.
It is assumed that the source and destination are determined in the node that requires packet data transmission, and that path l is generated, as shown in Fig. 3, by the shortest path AODV routing algorithm.
-
9.
If packets are not transmitted during an SF, they are saved in the buffer of the relevant node and transmitted at the next SF.
-
10.
As shown in Fig. 3, if the value of depth d is odd, time slots are generated to send and receive slot order, otherwise d is even, time slots are generated to receive and send orders during an SF.
-
11.
As shown in Fig. 3, if a packet is transmitted from the sync node to a lower node, the time slot is assigned path l = 1, depth d = D, slot number j = 0, and slots for d and d − 1 are assigned after confirming that the particular slot and d + 1-th slot are in use.
-
12.
Slots are assigned until d is 1, and Step 5 is repeated until path l becomes the maximum path L by increasing the value of l by one.
-
13.
Once time slot assignment is complete, as shown in Fig. 3, frequency is set as shown in Fig. 5 in the order \(F_{1}\), \(F_{2}\),...\(F_{max}\), according to the order of generation of packet transmission path l = {\(l_{1}\), \(l_{2}\), \(l_{3}\), \(l_{4}\),...\(l_{d}\)}. The PAN coordinator should send the frequency assignment information to all children nodes in the tree topology network once the routing path is determined, whereas the maximum value of \(F_{max}\) is 16.
-
14.
As shown in Fig. 6, Beacon, Control, and Guard time slot assign the \(F_{0}\) channel and set the unused time slot to the sleep state.
In general, the overhearing problem in a sensor network occurs when an owner node transmits packet data to a neighbor. In this process, not only is packet data transmitted from the owner node to its one-hop neighbor, but also to neighbor nodes more than one hop from it. In order to solve this problem, TreeMAC assigns three time slots to a frame and three other time slots, different from those for its own node, to its one-hop neighbor node. However, this method can cause throughput degradation by reducing the efficiency of the time slot. Therefore, we use a method whereby a different frequency is assigned to each path according to the AODV, as shown in Fig. 6.
In this paper, we propose two algorithms—TSAA and FSAA—sto solve the above problem. Although the TSAA supports time orthogonality between an owner node and each of its one-hop neighbors, it does not support this among neighbors beyond one hop from the owner. To solve this issue, we propose the FSAA shown in Fig. 6. It allocates each frequency value to a different routing path. As a result, frequency orthogonality is maintained between the owner node and its one-hop neighbors. Hence, using the two algorithms, overhearing is avoided during packet transmission. At the same time, the unallocated slots are kept in a sleep state to reduce energy consumption. Moreover, unlike TreeMAC, Tree TDMA MAC does not require the allocation of three time slots to an SF to prevent overhearing. Hence, it has superior transmission efficiency to TreeMAC.
By expanding the Tree TDMA MAC proposed in this paper, it is possible to exploit the tree topology network featuring multiple PAN coordinators, as shown in Fig. 7. If the multiple PAN coordinators are connected, they can be divided into a Master PAN coordinator and several PAN coordinators. The Master PAN coordinator manages information transmission to device nodes within the same PAN from other PAN coordinators and synchronizes with them. A PAN coordinator sends a beacon message to devices, gathers data, and acts as a transmission gateway for devices within the same PAN.
Assuming that a packet is delivered from node \(n_{7}\) of PAN coordinator #1 to node \(n_{9}\) of PAN coordinator 3 in a tree topology network of the sort shown in Fig. 7, the total number of hops is 13, and packet delay is generated by a minimum of 12 hops. In here, the Master PAN coordinator broadcasts a beacon message to synchronize with neighboring PAN coordinators or its PAN device. The minimum transmission period is decided by the hop value of the maximum depth minus one within the Master PAN topology in order to prevent overhearing of the beacon, as shown in Fig. 8. However, it is impossible for the Master PAN coordinator to know the maximum depth within each PAN coordinator at the outset. Thus, in order to solve this problem, the Master PAN coordinator needs to gather information regarding the maximum depth of the tree topology network from each PAN coordinator, it obtains information regarding the nodes from each device node following beacon transmission. The Master PAN coordinator should not broadcast the beacon message again until the sub-PAN coordinators of the Master coordinator provide information regarding the device depths in the tree topology network.
Figure 8 shows an example of broadcasting a beacon message when the period of the SF is \(SF^{1}_{a}\), as shown in Fig. 7. Since the maximum depth of the Master PAN coordinator is 5, the period of the beacon transmitted by the Master PAN coordinator to the overall network is an arithmetic progression with \(d=4\). While the PAN coordinators and devices maintain a receiving state at the beginning, they transmit the beacon message to the lower nodes if they receive it from the Master PAN coordinator. At this time, if the time slot of each node is not on its own beacon period, it should minimize standby power by changing these slots to idle because it does not need to transmit or receive a beacon message.
3 Experimental Method
The first objective of our simulation was to analyze the performance of our proposed method in terms of network throughput, network energy efficiency, network delay, and network energy consumption, and compare it with CSMA/CA and TreeMAC in a one-PAN topology environment, as shown in Fig. 2. The second objective was to analyze the performance of our Tree TDMA MAC in a multi-PAN topology, as shown in Fig. 7. The parameters of each MAC were set to be similar to those of the Tree TDMA MAC, as listed in Tables 3, 4, and 5.
We used MATLAB as simulation tool to analyze the performance of the MACs. In the case of one-PAN topology, we set the shortest routing path as the routing path, and assumed that the source and destination nodes–\(n_{7}\) and \(n_{9}\), respectively–intersected if the source and the destination nodes changed during packet transmission or reception. Furthermore, in the simulation process, we used the parameters listed in Tables 3, 4, and 5 to create the SF and the channel allocation algorithms. The tree topology network had 10 nodes, as shown in Fig. 2, for ease of implementation.
Since we assumed that the AODV routing algorithm is used in the simulation environment of MACs, the routing algorithm does not affect the performance of the MACs. Hence, we used pre-defined static routing paths instead of implementing the routing algorithm. Moreover, the BI, SD, and BP values of the CSMA/CA MAC were set to generate a frame structure similar to the slot length and cycle of the SF in TreeMAC, in order to compare its performance with that of Tree TDMA MAC.
Traffic was only generated in the nodes \(n_{7}\) and \(n_{9}\) as Fig. 7 and we increased the data rate. Since TreeMAC outperformed Funneling-MAC, Z-MAC, and B-MAC [1, 8, 25], we do not consider the simulation results of these MACs here. In order to calculate the average values of network throughput, network delay, energy efficiency, and energy consumption under the same network topology and identical traffic generation conditions, we performed the simulation 10 times for these items.
In case of multi-PAN topology, as shown in Fig. 7, the channel and the slot allocated algorithms were implemented by using the simulation parameters in Table 5 for Tree TDMA MAC. In order to make the simulation easier to implement, we did not implement AODV routing protocol, as it does not affect the performance of MACs. The simulation was carried out by increasing the number of hops from 4 to 48 between the specified source and destination nodes, and by increasing the data rate from 50 to 600 pps.
4 Simulation
4.1 Network Throughput in One-PAN Topology
An important feature of Tree TDMA MAC is that it can increase network throughput by improving the performance of MAC. In order to achieve this objective, we increased the data rate from the source to the destination nodes by one packet and calculated network throughput while counting successfully delivered packets within 120 ms without collision. Tree TDMA MAC generated 50–600 packets per second, which corresponded to 80 symbols, which was 40 bytes on a one-traffic channel. This means that packet transmission was attempted at a data speed of 16–192 Kbps, and this was reflected in the altered network throughput according to change in the data transmission rate in Fig. 9.
Figure 9 shows that Tree TDMA MAC outperformed other MACs in terms of network throughput. Since Tree TDMA MAC allocates slots per SF and transmits packets at the outset, network throughput increased linearly until the time slot resource of the relevant node was consumed. Following this, network throughput no longer increased because no more time slots could be allocated. However, in the case of TreeMAC, since it only allows half-duplex communication and has smaller slot capacity than Tree TDMA MAC, it yielded lower network throughput than Tree TDMA. In the case of CSMA/CA, as the number of packet collisions increased with increasing data rate and re-transmission, it exhibited the worst results in terms of network throughput.
4.2 Network Delay in One-PAN Topology
Network delay is defined as
where d is the average value of network delay, \(t^r_i\) is the time of receipt of the i-th packet, \(t^{s}_{i}\) is the transmission time of the i-th packet, and n is the number of packets. Figure 10 shows that CSMA/CA showed the worst performance in terms of network delay as data rate increased. This is because it involves contention-based packet transmission, unlike the time slot-based TreeMAC or Tree TDMA MAC.
The increase in the number of packets in CSMA/CA caused network load to increase exponentially as packet collision increased. TreeMAC has a tree slot structure consisting of sending, receiving, and idle states for an SF, with an SF = 3N structure for cycle N. It allocates different time slots between an owner node and each of its one-hop neighbors. Thus, TreeMAC has three slots–sending, receiving, and idle state–in an SF to prevent the overhearing problem. When a packet is eventually transmitted, the sending slot is used to transmit it and the receiving and two idle slots are left as redundancies. Thus, as shown in Fig. 10, the sharp network delay increment of TreeMAC is generated at lower data rate than Tree TDMA MAC using one time slot to transmit a packet.
4.3 Energy Efficiency in One-PAN Topology
In general, increasing energy efficiency is one of the main objectives of MAC protocol design. Energy efficiency is defined as the ratio of successfully transmitted data packets over all data transmitted in the tree topology network [17]. The transmitted data packets include retransmitted packets because no ACK message is received following initial transmission as well as dropped packets due to an excessive number of retries or pending packets. However, packet loss due to the loss of the radio path was not considered.
Figure 11 shows the simulation result for energy efficiency for Tree TDMA, TreeMAC, and CSMA/CA MAC. We see that packet loss did not occur in Tree TDMA MAC until the traffic channel slot of the middle tree node was expended all because it assigned time slots prior to packet transmission during an SF. Hence, it maintained 100% energy efficiency up to 300 pps, where the time slots of the middle tree node were full. Hereafter, when packet transmission exceeded the time slot capacity of the node where packets were concentrated, packet retransmission occurred, and hence energy efficiency began to drop drastically.
TreeMAC, like Tree TDMA MAC, is TDMA MAC. However, it has the structure of SF with three slots per SF to prevent packet collision between neighboring nodes. Therefore, in order to transmit one packet, two slots of three are invariably unusable. This reduces transmission and energy efficiency.
CSMA MAC checks whether there are empty channel when transmitting data between parent and child nodes. If the transmission channel is not empty, it stands by for a specified backoff time until the channel becomes empty. Increased data rate causes collision and retransmissions, hence increasing backoff time and reducing energy efficiency in comparison with TDMA MACs.
4.4 Energy Consumption in One-PAN Topology
As most sensor networks require very low power, the energy consumed by each node while transmitting or receiving packets is among the important elements when designing a new MAC in a sensor network. Figure 12 shows the simulation results of energy consumed by the network as number of packets increased in Tree TDMA, TreeMAC, and CSMA/CA MAC.
CSMA/CA MAC showed greater energy consumption than the TDMA MACs in the tree topology network with increasing number of packets. This was because it performs Clear Channel Assessment (CCA) and random backoff, and hence needs a higher data rate for packet transmission than other TDMA MACs, Since TreeMAC is a kind of TDMA MAC and uses time scheduling, it can be operated at lower energy than CSMA/CA. However, it reaches a point where time slot resources are consumed faster than in Tree TDMA MAC because it has fewer time slot resources. As a result, TreeMAC showed similar performance to Tree TDMA MAC at the beginning, but its energy consumption increased more rapidly than that of Tree TDMA MAC as packet transmission rate increased.
4.5 Network Throughput in Multi-PAN Topology
We saw that the value of L and the distance between source and destination nodes in multi-PAN topology was proportional to the number of hops. Figure 13 shows the simulation results for network throughput against data rate according to change in the value of L. It shows that increase in L caused a decline in network throughput, although it was not significant. On the contrary, Fig. 13 also shows the simulation result where network throughput could no longer be increased when it reached the saturation data rate of 200–300 pps and it became difficult to assign more time slot.
4.6 Network Delay in Multi-PAN Topology
Figure 7 shows that the increased value of l and the distance between source and destination nodes in the multi-PAN topology caused greater network delay than one-PAN topology. Figure 14 shows that an increment in the L value, which is the maximum path distance between the source and destination nodes, affects network delay. These results are typical characteristics of TDMA MACs.
4.7 Energy Efficiency in Multi-PAN Topology
In the multi-PAN topology of Fig. 7 that uses Tree TDMA MAC, when the distance between the source and destination was L, where L had its lowest value of 4, there was a sharp decline in network efficiency. The system maintained almost perfect network efficiency until the data rate reached 300 pps, following which it decreased drastically with increasing L, as shown in Fig. 15. These results indicate that the increase in L leads to more time slots and, hence, more unused time slots. However, if the source and destination nodes are selected as randomly as in real network environments, energy efficiency according to increasing L will be less affected than in the simulation.
4.8 Energy Consumption in Multi-PAN Topology
Figure 16 shows the simulation results for network consumption versus data rate in multi-PAN topology according to increasing values of L, where L is the distance between the source and destination nodes. The hop count depended on the value of L.
Figure 16 shows that an increase in the value of L led to greater energy consumption because it increased the number of required nodes for packet transmission, and the data rate led to energy consumption because it increased the number of packet transmissions in an SF. The results of the simulation showed that Tree TDMA MAC increased energy consumption at a slower rate than CSMA/CA MAC and other MACs.
5 Conclusion
In the past, CSMA/CA MACs have been typically used in wireless sensor networks because of the simplicity of the relevant algorithm and energy-efficient implementation. At the same time, their implementation leads to low throughput, high congestion, and high overhead. In particular, the overhead due to an increase in the number of packets proportional to the depths of nodes in tree topology networks renders CSMA/CA MACs unsuited for voice or real-time communication requiring timely and guaranteed delivery. TDMA-based MACs have been proposed to solve such problems, but suffer from similar issues during implementation in real environments because it is difficult to maintain synchronization with trees of increasing depth, and leads to overhearing between neighboring nodes. In this paper, we proposed Tree TDMA MAC with the TSAA and the FSAA to solve the above problems. The TSAA solves collision and congestion problems by allocating time slots before transmitting packets during an SF, and the FSAA provides frequency orthogonality for each path generated by the AODV algorithm prior to the transmission of each packet to prevent overhearing that is otherwise inevitable in TDMA MAC. Moreover, we proposed methods to control the active periods of SFs to implement internode synchronization while maintaining minimum energy consumption. We conducted network simulations to analyze the performance of our proposed Tree TDMA MAC and compare it with other MACs in one-PAN topology as well as multi-PAN topology. Our method outperformed CSMA/CA and TreeMAC in terms of throughput, network delay, energy efficiency, and energy consumption without incurring overhearing and the funneling effect. This also showed that the performance of our method does not degrade with increasing packet transmission path length in multi-PAN topology.
References
Ahn, G.-S., Hong, S. G., Miluzzo, E., Campbell, A. T., & Cuomo, F. (2006). Funneling MAC: A localized, sink-oriented MAC for boosting fidelity in sensor networks. In The 4th international conference on embedded networked sensor systems, Boulder, Colorado.
Lu, G., Krishnamachari, B., & Raghavendra, C. S. (2004). An adaptive energy-efficient and low-latency MAC for data gathering in wireless sensor networks. In The 18th international parallel and distributed processing symposium, p. 224.
Zheng, T., Radhakrishnan, S., & Sarangan, V. (2005). PMAC: An adaptive energy efficient MAC protocol for wireless sensor networks. In The 19th IEEE international parallel and distributed processing symposium, p. 8.
Heinzelman, W. R., Chandrakasan, A., & Balakrishnan, H. (2000). Energy-efficient communication protocol for wireless microsensor networks. In The 33rd annual Hawaii international conference on system sciences, 2, 10.
Timmons, N. F., & Saanlon, W. G. (2009). An adaptive energy-efficient MAC protocol for the medical body area network. In International conference on wireless communication, vehicular technology, information theory, and aerospace & electronic systems technology, 2009. Wireless VITAE, pp. 587–593.
Jung, E.-S., & Vaidya, N. F. (2002). An energy-efficient MAC protocol for wireless LANs. In The 21st annual joint conference of the IEEE computer and communications societies. INFOCOM. 3, pp. 1756–1764.
Chih-Lin, I., & Pollini, G. P. (1994). The tree-search resource auction multiple access (TRAMA) protocol for wireless personal communications. In 1994 IEEE 44th vehicular technology conference.
Song, W.-Z., Huang, R., Shirazi, B., & LaHusen, R. (2009). TreeMAC: Localized TDMA MAC protocol for real-time high-data-rate sensor networks. In PerCom 2009: IEEE international conference in pervasive computing and communications, pp. 1–10.
Kim, J., Yoo, J. H., Lee, J. H., & Cho, S. H. (2012). A design of the full-duplex voice mixer for multi-user voice over sensor networks (VoSN) systems. In: 3rd IEEE international conference on network infrastructure and digital content (IC-NIDC), pp. 102–105.
Schurgers, C., Tsiatsis, V., & Srivastava, M. B. (2002). STEM: Topology management for energy-efficient sensor networks. In Aerospace conference proceedings. IEEE, (Vol. 3, pp. 1099–1108).
Kim, S., Huang, D.-S., Zhang, X.-P., & Huang, G.-B. (2005). An adaptive energy-efficient and low-delay MAC protocol for wireless sensor networks. In Advances in intelligent computing (pp. 598–606). Berlin: Springer.
Wei, Y., Heidemann, J., & Estrin, D. (2002). An energy-efficient MAC protocol for wireless sensor networks. In Proceedings of twenty-first annual joint conference of the IEEE computer and communications societies (INFOCOM 2002). (Vol. 3, pp. 1567–1576).
Van Dam, T., & Langendoen, K. (2003). An adaptive energy-efficient MAC protocol for wireless sensor networks. In The 1st international conference on embedded networked sensor systems. Los Angeles, California.
Rhee, I., Warrier, A., Aia, M., Min, J., Sichitiu, M. L. (2008). Z-MAC: A hybrid MAC for wireless sensor networks. IEEE/ACM Transactions on Networking, 16, 511–524.
Rhee, I., Warrier, A., Min, J., & Xu, L. (2006). DRAND: Distributed randomized TDMA scheduling for wireless ad-hoc networks. In The 7th ACM international symposium on mobile ad hoc networking and computing. Florence.
Wan, C.-Y., et al. (2005). Siphon: Overload traffic management using multi-radio virtual sinks in sensor networks. In Proceedings of the 3rd international conference on embedded networked sensor systems. San Diego, California, ACM, pp. 116–129.
Jung, S. W., Lee, H. J., Lee, J. H., & Cho, S. H. (2012). Interworking of voice over sensor network (VoSN) using the TDMA/TDD MAC and VoIP-based SIP. In 2012 3rd IEEE international conference on network infrastructure and digital content (IC-NIDC), pp. 97–101.
Song, H. Y., & Cho, S.-H. (2011). Performances of IEEE 802.15.4 unslotted CSMA-CA for voice communications. In 2011 17th Asia–Pacific conference on communications (APCC), pp. 151–156.
Yahya, B., & Ben-Othman, J. (2010). Energy-efficient and QoS-aware medium access control for wireless sensor networks. Concurrency and Computation: Practice and Experience, 22, 1252–1266.
Yigitel, M. A., Incel, O. D., Ersoy, C. (2011). QoS-aware MAC protocols for wireless sensor networks: A survey. Computer Networks, 55, 1982–2004.
Zhang, J., Zhou, G., Huang, C., Son, S. H., & Stankovic, J. A. (2007). TMMAC: An energy efficient multi-channel MAC protocol for ad hoc networks. In ICC ‘07. IEEE international conference on communications, pp. 3554–3561.
Rajendran, V., Obraczka, K., & Garcia-Luna-Aceves, J. J. (2003). Energy-efficient collision-free medium access control for wireless sensor networks. In The 1st international conference on embedded networked sensor systems. Los Angeles, California.
Sohrabi, K., Gao, J., Ailawadhi, V., Pottie, G. J. (2000). Protocols for self-organization of a wireless sensor network. IEEE Personal Communications, 7(5), 16–27.
Balasubramanian, S., & Aksoy, D. (2006). Adaptive online scheduling for asymmetric wireless sensor networks. In 2006 international symposium on computer networks, pp. 73–78.
Rhee, I., Warrier, A., Aia, M., Jeongki, M., Sichitiu, M. L. (2008). Z-MAC: A hybrid MAC for wireless sensor networks. Transactions on Networking, IEEE/ACM 16, 511–524.
Acknowledgements
This work was supported by the ICT R&D Program of MSIP/IITP. [B0126-16-1018, The IoT Platform for Virtual Things, Distributed Autonomous Intellgence and Data Federation/Analysis]
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Lee, JH., Cho, S.H. Tree TDMA MAC Algorithm Using Time and Frequency Slot Allocations in Tree-Based WSNs. Wireless Pers Commun 95, 2575–2597 (2017). https://doi.org/10.1007/s11277-016-3938-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3938-9