Abstract
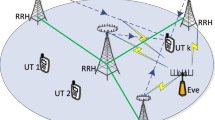
In this paper, we investigate the secrecy performance of a massive MIMO NOMA network. Specifically, we demonstrate a detailed training process in the network and derive downlink ergodic secrecy rates of legitimate users. In order to gain system’s insights, discussions on secrecy performance of the network in two special cases, i.e., large number of antennas and high transmit power at the BS, are provided. Furthermore, from the analysis, an optimization to maximize the users’ minimum secrecy rate in each NOMA cluster is proposed to aid the weak users’ secrecy performance. The correctness of our analysis and the efficiency of the proposed are confirmed through computer simulations.







Similar content being viewed by others
Notes
The reason for choosing EPA as a benchmark is that an optimization algorithm for users’ minimum secrecy rate of the exact system model has not been developed in the literature yet. Therefore, in this situation, in the literature, equal power allocation is often preferred as in [7], [11] and the references therein. Besides, although the idea of this scheme is straightforward, it still provides secrecy transmissions for weakest users of the proposed system, i.e., non-zero ergodic secrecy rate, as seen in Figs. 5, 6, and 7. As a result, EPA is a decent benchmark of the proposed optimization algorithm.
References
Barros, J., Rodrigues, D., & M.R. ‘Secrecy capacity of wireless channels’. (2006). IEEE International Symposium on Information Theory, 2006, 356–360.
Hochwald, B. M., Marzetta, T. L., & Tarokh, V. (2004). Multiple-antenna channel hardening and its implications for rate feedback and scheduling. IEEE Transaction on Information Theory, 50(9), 1893–1909.
Islam, S. M. R., Avazov, N., Dobre, O. A., & Kwak, K. (2017). Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges. IEEE Communications Surveys and Tutorials, 19(2), 721–742.
Kay, S.M. (1997) ‘Fundamentals of statistical signal processing: Estimation theory’,
Kudathanthirige, D., & Baduge, G.A.A. (2019) ‘NOMA-aided multicell downlink massive MIMO’, IEEE Journal of Selected Topics in Signal Processing , 13, (3), pp. 612–627
Lu, L., Li, G. Y., Swindlehurst, A. L., Ashikhmin, A., & Zhang, R. (2014). An overview of massive MIMO: Benefits and challenges. IEEE Journal of Selected Topics in Signal Processing, 8(5), 742–758.
Marzetta, T.L., Larsson, E.G., Yang, H., & Ngo, H.Q. (2016) ‘Fundamentals of Massive MIMO’,
Mukherjee, A., Fakoorian, S. A. A., Huang, J., & Swindlehurst, A. L. (2014). Principles of physical layer security in multiuser wireless networks: A survey. IEEE Communication Survey Tutorials, 16(3), 1550–1573.
Nguyen, N., Dobre, O. A., Nguyen, L. D., Nguyen, C. T., Poor, H. V., & ‘Secure downlink massive MIMO-NOMA network in the presence of a multiple-antenna eavesdropper’. (2019). IEEE International Conference on Communications, 2019, 1–6.
Nguyen, H. T., Nguyen, N., Pham, A. T., Nguyen, C. T., & ‘Performance analysis of ergodic secrecy rates in massive MIMO-NOMA networks with zero-forcing precoding’. (2019). International Conference on Advanced Technologies for Communications, 2019, 204–209.
Nguyen, N., Ngo, H. Q., Duong, T. Q., Tuan, H. D., & Tourki, K. (2018). Secure massive MIMO with the artificial noise-aided downlink training. IEEE Journal on Selected Areas in Communications, 36(4), 802–816.
Saito, Y., Kishiyama, Y., Benjebbour, A., Nakamura, T., Li, A., Higuchi, K., & ‘Non-orthogonal multiple access (NOMA) for cellular future radio access’. (2013). IEEE 77th Vehicular Technology Conference, 2013, 1–5.
Sheng, Z., Tuan, H. D., Nasir, A. A., Duong, T. Q., & Poor, H. V. (2018). Power allocation for energy efficiency and secrecy of wireless interference networks. IEEE Transaction on Wireless Communication, 17(6), 3737–3751.
Zeng, M., Nguyen, N., Dobre, O. A., & Poor, H. V. (2019). Securing downlink massive MIMO-NOMA networks with artificial noise. IEEE Journal of Selected Topics in Signal Processing, 13(3), 685–699.
Acknowledgements
This research is funded by the Hanoi University of Science and Technology (HUST) under project number T2020-SAHEP-017.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This paper was presented in part at the 2019 International Conference on Advanced Technologies for Communications (ATC) in Hanoi, Vietnam [10]
Appendices
Appendices
where X follows Chi-squared distribution with \(2(M- C + 1)\) degrees of freedom as described in [2]. Step (a) of (39) can be achieved when \(M\) is large [10].
Rights and permissions
About this article
Cite this article
Nguyen, NP., Nguyen, L.D., Nguyen, H.T. et al. Performance analysis and optimization of ergodic secrecy rates for downlink data transmission in massive MIMO-NOMA networks. Wireless Netw 28, 355–365 (2022). https://doi.org/10.1007/s11276-021-02867-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02867-w