Abstract
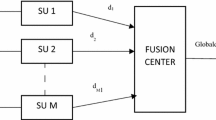
One primary function in a cognitive radio network (CRN) is spectrum sensing. In an infrastructure-based CRN, instead of individual nodes independently sensing the presence of the incumbent signal and taking decisions thereon, a fusion center (FC) aggregates the sensing reports from the individual nodes and makes the final decision. Such collaborative spectrum sensing (CSS) is known to result in better sensing accuracy. On the other hand, CSS is vulnerable to Spectrum Sensing Data Falsification (SSDF) attack (a.k.a. Byzantine attack) wherein a node maliciously falsifies the sensing report prior to sending it to the FC, with the intention of disrupting the spectrum sensing process. This paper investigates the use of machine learning techniques, viz., SVM, Neural Network, Naive Bayes and Ensemble classifiers for detection of SSDF attacks in a CRN where the sensing reports are binary (i.e., either 1 or 0). The learning techniques are studied under two experimental scenarios: (a) when the training and test data are drawn from the same data-set, and (b) when separate data-sets are used for training and testing. Under the first scenario, of all the techniques, NN and Ensemble are the most robust showing consistently very good performance across varying presence of attackers in the system. Moreover performance comparison with an existing non-machine learning technique shows that the learning techniques are generally more robust than the existing algorithm under high presence of attackers. Under the second scenario, in a limited environment, Ensemble is the most robust method showing good overall performance.























Similar content being viewed by others
References
Kakalou, I., Psannis, K. E., Krawiec, P., & Badea, R. (2017). Cognitive radio network and network service chaining toward 5G: Challenges and requirements. IEEE Communications Magazine, 55(11), 145–151.
Zhang, L., Ding, G., Wu, Q., Zou, Y., Han, Z., & Wang, J. (2015). Byzantine attack and defense in cognitive radio networks: A survey. IEEE Communications Surveys and Tutorials, 17(3), 1342–1363.
Attar, A., Tang, H., Vasilakos, A. V., Yu, F. R., & Leung, V. C. M. (2012). A survey of security challenges in cognitive radio networks: Solutions and future research directions. Proceedings of the IEEE, 100(12), 3172–3186.
Cheng, Z., Song, T., Zhang, J., Hu, J., Hu, Y., Shen, L., Li, X., & Wu, J. (2017). Self-organizing map-based scheme against probabilistic SSDF attack in cognitive radio networks. In Proceedings of IEEE WCSP, 978-1-5386-2062-5.
Marchang, N., Taggu, A., & Patra, A. K. (2018). Detecting Byzantine attack in cognitive radio networks by exploiting frequency and ordering properties. IEEE Transactions on Coginitive Communications and Networking, 4(4), 816–824.
Li, H., & Han, Z. (2010). Catch me if you can: An abnormality detection approach for collaborative spectrum sensing in cognitive radio networks. IEEE Transactions on Wireless Communications, 9(11), 3554–3565.
Duan, L., Min, A. W., Huang, J., & Shin, K. G. (2012). Attack prevention for collaborative spectrum sensing in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 30(9), 1658–1665.
Wang, W., Chen, L., Shin, K. G., & Duan, L. (2015). Thwarting intelligent malicious behaviors in cooperative spectrum sensing. IEEE Transactions on Mobile Computing, 14(11), 2392–2405.
He, X., Dai, H., & Ning, P. (2013). HMM-based malicious user detection for robust collaborative spectrum sensing. IEEE Journal on Selected Areas in Communications, 31(11), 2196–2208.
Zhu, F., & Seo, S. (2009). Enhanced robust cooperative spectrum sensing in cognitive radio. Journal of Communications and Networks, 11, 122–133.
Patnaik, M., et al. (2019). PROLEMus: A proactive learning-based MAC protocol against PUEA and SSDF attacks in energy constrained cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 5(2), 400–412.
Le, T. N., Chin, W., & Kao, W. (2015). Cross-layer design for primary user emulation attacks detection in mobile cognitive radio networks. IEEE Communications Letters, 19(5), 799–802.
Alahmadi, A., Fang, Z., Song, T., & Li, T. (2015). Subband PUEA detection and mitigation in OFDM-based cognitive radio networks. IEEE Transactions on Information Forensics and Security, 10(10), 2131–2142.
Lin, S., Wen, C., & Sethares, W. A. (2018). Two-tier device-based authentication protocol against PUEA attacks for IoT applications. IEEE Transactions on Signal and Information Processing over Networks, 4(1), 33–47.
Karimi, M., & Sadough, S. M. S. (2018). Efficient transmission strategy for cognitive radio systems under primary user emulation attack. IEEE Systems Journal, 12(4), 3767–3774.
Gao, N., Jing, X., Huang, H., & Mu, J. (2017). Robust collaborative spectrum sensing using PHY-layer fingerprints in mobile cognitive radio networks. IEEE Communications Letters, 21(5), 1063–1066.
Ghaznavi, M., & Jamshidi, A. (2017). Defence against primary user emulation attack using statistical properties of the cognitive radio received power. IET Communications, 11(9), 1535–1542.
Alahmadi, A., Abdelhakim, M., Ren, J., & Li, T. (2014). Defense against primary user emulation attacks in cognitive radio networks using advanced encryption standard. IEEE Transactions on Information Forensics and Security, 9(5), 772–781.
Chen, C., Cheng, H., & Yao, Y. (2011). Cooperative spectrum sensing in cognitive radio networks in the presence of the primary user emulation attack. IEEE Transactions on Wireless Communications, 10(7), 2135–2141.
Zhu, H., Song, T., Wu, J., Li, X., & Hu, J. (2018) Cooperative spectrum sensing algorithm based on support vector machine against SSDF attack. In Proceedings IEEE ICC workshops (pp. 1–6).
Farmani, F., Jannat-Abad, M. A., & Berangi, R. (2011). Detection of SSDF attack using SVDD algorithm in cognitive radio networks. In Proceedings of third international conference in computational intelligence, communication systems and networks (pp. 201–204).
Huo, Y., Wang, Y., Lin, W., & Sun, R. Three-layer Bayesian model based spectrum sensing to detect malicious attacks in cognitive radio networks. In Proceedings of IEEE ICCW (pp. 1640–1645).
Nie, G., Ding, G., Zhang, Li, & Wu, Q. (2017). Byzantine defense in collaborative spectrum sensing via Bayesian learning. IEEE Access, 5, 20089–20098.
Fragkiadakis, A. G., Tragos, E. Z., & Askoxylakis, I. G. (2013). A survey on security threats and detection techniques in cognitive radio networks. IEEE Communications Surveys and Tutorials, 15(1), 428–445.
Hlavacek, D., & Chang, J. M. (2014). A layered approach to cognitive radio network security: A survey. Computer Networks, 75(Part A), 414–436.
Rina, K., Nath, S., Marchang, N., & Taggu, A. (2018). Can clustering be used to detect intrusion during spectrum sensing in cognitive radio networks? IEEE Systems Journal, 12(1), 938–947.
Zhao, F., Li, S., & Feng, J. (2019). Securing cooperative spectrum sensing against DC-SSDF attack using trust fluctuation clustering analysis in cognitive radio networks. Hindawi Wireless Communications and Mobile Computing Volume 2019. Article ID, 3174304.
Ahmed, M. E., Song, J. B., & Han, Z. (2014). Mitigating malicious attacks using bayesian non-parametric clustering in collaborative cognitive radio networks. In Proceedings of IEEE Globecom—Cognitive radio and networks symposium (pp. 999–1004)
Penna, F., Sun, Y., Dolecek, L., & Cabric, D. (2011). Joint spectrum sensing and detection of malicious nodes via belief propagation. Proceedings of IEEE Globecom, 2011, 1–5.
Akbari, K., & Abouei, J. (2018). Signal classification for detecting primary user emulation attack in centralized cognitive radio networks. In Proceedings of 26th Iranian conference on electrical engineering (pp. 342–347).
Zhou, M., Shen, J., Chen, H., & Xie, L. (2013). A cooperative spectrum sensing scheme based on the Bayesian reputation model in cognitive radio networks. In Proceedings of IEEE wireless communications and networking conference(WCNC):MAC (pp. 614–619).
Penna, F., Sun, Y., Dolecek, L., & Cabric, D. (2012). Detecting and counteracting statistical attacks in cooperative spectrum sensing. IEEE Transactions on Signal Processing, 60(4), 1806–1822.
Jaglan, R. R., Mustafa, R., & Agrawal, S. (2018). Scalable and robust ANN based cooperative spectrum sensing for cognitive radio networks. Wireless Personal Communications, 99(3), 1141–1157.
Ye, N., Emran, S. M., Chen, Q., & Vilbert, S. (2002). Multivariate statistical analysis of audit trials for host-based intrusion detection. IEEE Transactions on Computers, 51(7), 810–820.
Panchal, G., Ganatra, A., Kosta, Y. P., & Panchal, D. (2011). Behaviour analysis of multilayer perceptrons with multiple hidden neurons and hidden layers. International Journal of Computer Theory and Engineering, 3(2), 332–337.
GnanaSheela, K., & Deepa, S. N. (2013). Review on methods to fix number of hidden neurons in neural networks. Hindawi Publishing Corporation: Mathematical Problems in Engineering, Volume 2013. ArticleID, 425740.
Spectrum Policy Task Force, Fed. Commun. Comm., ET Docket No. 02-135 Tech. Rep., Nov (2002)
Acknowlegements
This work is partially supported by Information Technology Research Academy (ITRA), Government of India under, ITRAMobile grant [ITRA/15(63)/Mobile/MBSSCRN/02/2015].
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Sarmah, R., Taggu, A. & Marchang, N. Detecting Byzantine attack in cognitive radio networks using machine learning. Wireless Netw 26, 5939–5950 (2020). https://doi.org/10.1007/s11276-020-02398-w
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-020-02398-w