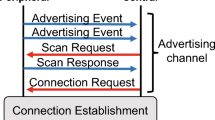
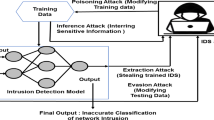
Abstract
The identification of the presence of primary user enhances the spectrum efficiency in cognitive radio (CR). The studies suggested that the existence of malicious user adversely affects the system performances; especially the primary user emulation attack (PUEA) has a greater influence in spectrum sensing on the CR network. Moreover, the detection of PUEA is a challenging and complex task and involves constructive design with sensing algorithm. In this study, a support vector machine (SVM) along with energy vectors is designed to improve the spectrum sensing mechanism. The presented approach integrates the SVM with the Bayesian optimization algorithm (BOA) in which SVM aims to detect the malicious user by randomly selecting the primary and secondary users. The BOA aims to optimize the hyperparameters of the SVM, thereby improving the detection performances and maximizes the algorithms convergence speed. The experimental analysis illustrate that the presented approach predicts the PUEA with 98% accuracy and reduces the average node power is 9.7. Moreover, the results demonstrated that the system performance does not vary on implementing it with the large-scale CR network. Finally, the system performances are compared and evaluated with existing techniques in terms of accuracy, and average noise power.















Similar content being viewed by others
Availability of data and materials
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
Code availability
Not applicable.
References
Ahmadfard, A., & Jamshidi, A. (2019). A channel hopping based defense method against primary user emulation attack in cognitive radio networks. Computer Communications, 148, 1–8.
Hei, Y., Li, W., Fu, W., & Li, X. (2015). Efficient parallel artificial bee colony algorithm for cooperative spectrum sensing optimization. Circuits, Systems, and Signal Processing, 34(11), 3611–3629.
Chen, H., & Vun, C. H. (2018). A novel matrix optimization for compressive sampling-based sub-Nyquist OFDM receiver in cognitive radio. Circuits, Systems, and Signal Processing, 37(11), 5069–5086.
Salahdine, F., & Kaabouch, N. (2020). Security threats, detection, and countermeasures for physical layer in cognitive radio networks: A survey. Physical Communication, 39, 101001.
Ghaznavi, M., & Jamshidi, A. (2019). A low complexity cluster based data fusion to defense against SSDF attack in cognitive radio networks. Computer Communications, 138, 106–114.
Fihri, W. F., El Ghazi, H., Abou El Majd, B., & El Bouanani, F. (2020). A machine learning approach for backoff manipulation attack detection in cognitive radio. IEEE Access, 8, 227349–227359.
Zhang, M., Cumanan, K., Thiyagalingam, J., Tang, Y., Wang, W., Ding, Z., & Dobre, O. A. (2021). Exploiting deep learning for secure transmission in an underlay cognitive radio network. IEEE Transactions on Vehicular Technology, 70(1), 726–741.
Ponnusamy, V., & Malarvihi, S. (2017). Hardware impairment detection and prewhitening on MIMO precoder for spectrum sharing. Wireless Personal Communications, 96(1), 1557–1576.
Ponnusamy, V., Kottursamy, K., Karthick, T., Mukeshkrishnan, M. B., Malathi, D., & Ahanger, T. A. (2020). Primary user emulation attack mitigation using neural network. Computers & Electrical Engineering, 88, 106849.
Mahmoudi, M., Faez, K., & Ghasemi, A. (2020). Defense against primary user emulation attackers based on adaptive Bayesian learning automata in cognitive radio networks. Ad Hoc Networks, 102, 102147.
Awin, F., Abdel-Raheem, E., & Tepe, K. (2018). Blind spectrum sensing approaches for interweaved cognitive radio system: A tutorial and short course. IEEE Communications Surveys & Tutorials, 21(1), 238–259.
Mahmoudi, M., Faez, K., & Ghasemi, A. (2019). Uncoordinated frequency hopping scheme for defense against primary user emulation attack in cognitive radio networks. Computer Networks, 163, 106884.
Elghamrawy, S. M. (2020). Security in cognitive radio network: Defense against primary user emulation attacks using genetic artificial bee colony (GABC) algorithm. Future generation computer systems, 109, 479–487.
Okegbile, S. D., & Ogunranti, O. I. (2020). Users emulation attack management in the massive internet of things enabled environment. ICT Express, 6(4), 353–356.
Clement, J. C., & Emmanuel, D. S. (2016). Sensing UHF-TV spectrum for narrowband cognitive radios in a malicious presence. Canadian Journal of Electrical and Computer Engineering, 39(2), 141–149.
Karimi, A., Taherpour, A., & Cabric, D. (2019). Smart traffic-aware primary user emulation attack and its impact on secondary user throughput under Rayleigh flat fading channel. IEEE Transactions on Information Forensics and Security, 15, 66–80.
Clement, J. C., & Emmanuel, D. S. (2016). Enhancing the throughput of cognitive radio networks through malevolent presence. Computers & Electrical Engineering, 52, 240–252.
Karimi, M., & Sadough, S. M. S. (2017). Efficient transmission strategy for cognitive radio systems under primary user emulation attack. IEEE Systems Journal, 12(4), 3767–3774.
Li, K., & Wang, J. (2019). Optimal joining strategies in cognitive radio networks under primary user emulation attacks. IEEE Access, 7, 183812–183822.
Patnaik, M., Kamakoti, V., Matyáš, V., & Řchák, V. (2019). PROLEMus: A proactive learning-based MAC protocol against PUEA and SSDF attacks in energy constrained cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 5(2), 400–412.
Zhang, Y., Wu, Q., & Shikh-Bahaei, M. R. (2020). On ensemble learning-based secure fusion strategy for robust cooperative sensing in full-duplex cognitive radio networks. IEEE Transactions on Communications, 68(10), 6086–6100.
Banerjee, A., & Maity, S. P. (2019). On residual energy maximization in cooperative spectrum sensing with PUEA. IEEE Wireless Communications Letters, 8(6), 1563–1566.
Tashman, D. H., & Hamouda, W. (2020). An overview and future directions on physical-layer security for cognitive radio networks. IEEE Network, 35(3), 205–211.
Nanjundaswamy, M. K., Babu, A. A., Shet, S., Selvaraj, N., & Kovelakuntla, J. (2022). Mitigation of spectrum sensing data falsification attack using multilayer perception in cognitive radio networks. Acta IMEKO, 11(1), 1–7.
Wang, Q., Sun, H., Hu, R. Q., & Bhuyan, A. (2022). When machine learning meets spectrum sharing security: Methodologies and challenges. IEEE Open Journal of the Communications Society, 3, 176–208.
Ayanoglu, E., Davaslioglu, K., & Sagduyu, Y. E. (2022). Machine learning in NextG networks via generative adversarial networks. IEEE Transactions on Cognitive Communications and Networking, 8(2), 480–501.
Lalouani, W., Younis, M., & Baroudi, U. (2021). Countering radiometric signature exploitation using adversarial machine learning based protocol switching. Computer Communications, 174, 109–121.
Zhang, X., Chen, Z., Zhang, Y., Liu, Y., Jin, M., & Qiu, T. (2024). Deep reinforcement learning-based distributed dynamic spectrum access in multi-user multi-channel cognitive radio internet of things networks. IEEE Internet of Things Journal.
Kongkham, D., & Sundararajan, M. (2022). Recurrent network based protocol design for spectrum sensing in cognitive users. Wireless Personal Communications. https://doi.org/10.1007/s11277-022-09847-z
Zheng, Q., Wang, H., Elhanashi, A., Saponara, S., & Zhang, D. (2022). An Intelligent Non-cooperative Spectrum Sensing Method Based on Convolutional Auto-encoder (CAE). In S. Saponara & A. De Gloria (Eds.), Applications in Electronics Pervading Industry, Environment and Society. ApplePies 2021. Lecture Notes in Electrical Engineering. (Vol. 866). Cham: Springer. https://doi.org/10.1007/978-3-030-95498-7_1
Zardosht, F., Derakhtian, M., Jamshidi, A., et al. (2022). Recognition and elimination of SSDF attackers in cognitive radio networks. Telecommunication Systems. https://doi.org/10.1007/s11235-022-00935-w
Ayanoglu, E., Davaslioglu. K., & Sagduyu. Y. E. (2022). Machine learning in NextG networks via generative adversarial networks. IEEE Transactions on Cognitive Communications and Networking.
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Informed consent
Informed consent does not apply as this was a retrospective review with no identifying patient information.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Derivation for mean and variance of Yj.
In this section, the derivation of mean and variance of Yj is presented
Assuming that the malicious user’s signal samples and noise samples are independent of each other.
The mean under hypothesis \({H}_{1}\) is obtained as
The variance in \({H}_{0}\) is.
The term \(E\left[{y}_{j}^{2}(n)\right]\) in (18) is
Substituting the above result in (18), gives
The variance in \({H}_{1}\) is
The term \(E\left[{y}_{j}^{2}(n)\right]\) in (19) is
Substituting in 19, gives
After Reducing, we get
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ambhika, C. Discrimination of primary user emulation attack on cognitive radio networks using machine learning based spectrum sensing scheme. Wireless Netw (2024). https://doi.org/10.1007/s11276-024-03720-6
Accepted:
Published:
DOI: https://doi.org/10.1007/s11276-024-03720-6