Abstract
I consider a technology holder that has to decide whether to file for a patent or rely on secrecy, and a competing firm that can enter the market through technology transfer or imitation. Acknowledging that imitation is uncertain, imperfect, and takes time to materialise, as well as that intellectual property protection is not absolute, I find that technology transfer will always occur if the technological efficiency to imitate is sufficiently low. This will happen regardless of the protection choice of the inventor. Conversely, highly efficient imitation technologies will lead to imitation instead of licensing. I also consider that a trade secret might accidentally leak and thus lose its economic value, thereby rendering secrecy less preferable to patenting. Additionally, the risk of leakage might also lead to more imitation than licensing. Finally, considering that, in practice, the probability of leakage might increase with the number of firms practising a secret, I suggest an increase in the attractiveness of the patent system.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
I explore the licensing behaviour of an innovating firm that has developed a new technology and should decide the type of intellectual property protection upon which it can rely. I focus on the most common means of protection, enforceable in a court of law, namely patenting and secrecy. Patents and trade secrets, have become increasingly crucial to businesses and the market economy over the last decades.Footnote 1 The existing literature suggests that, in some technology areas, patents provide better protection than secrets, while, in the other areas, firms favour secrecy over patents to protect their inventions.Footnote 2 However, firms often use a combination of patent rights and trade secrets, particularly when inventions are complex (Cohen et al., 2000; Ottoz & Cugno, 2011). The dissemination of new technology has an impact on market structure and on the appropriability and the incentives of firms to invest in innovation.Footnote 3 Moreover, technology licensing can also lead to collusion between competing firms, less market competition, hold-up problems on cumulative innovation in certain markets such as telecommunications, and thus welfare concerns (Bogers et al., 2012). The aforementioned factors have led policymakers, practitioners, and scholars to take a strong interest in developing, monitoring, and studying the licensing behaviour of innovating firms. Acknowledging that patenting and secrecy are imperfect means of protection, as well as that trade secrets might leak and lose their economic value, I analyse how imitation and the strength of intellectual property protection affect technology transfer.
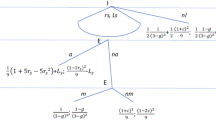
Consider a hypothetical two-stage duopoly game. In the first stage, Firm 1 has developed a technology and should decide whether to patent it or keep it a secret.Footnote 4 While the patent system is generally considered both complementary and a substitute to secrecy (Arora, 1997; Erkal, 2005; Belleflamme & Bloch, 2013), I assume that patenting is a mutually exclusive protection strategy to secrecy (Denicolo & Franzoni, 2003, 2004).Footnote 5 This assumption stems from that, under the patent act, inventors initially protecting a new technology under secrecy, forfeit their right to patent the invention after a grace period, which is not even granted in Europe. This prevents inventors from keeping the innovation secret and applying for patent protection only under the threat of imitation, encouraging the disclosure of information. Hence, I assume that an inventor can rely on either patents or secrecy, as discussed by Denicolo and Franzoni (2008). The patent term is set to be finite, whereas the length of secrecy protection is meant to be indefinite. I also discuss the scenario where secrets might accidentally leak, as revealed through a Poisson process. In the second stage, after the type of intellectual property protection has been chosen, Firm 1 and a single potential entrant, Firm 2, should decide whether to enter a licensing agreement regarding the use of the new technology. If technology transfer does not occur, Firm 2 can opt for imitation, regardless of the type of proprietary protection adopted in the first stage of the game.Footnote 6 Imitation is uncertain, imperfect, and takes time to materialise. Additionally, the probability of successful imitation depends on the cost spent to imitate chosen by Firm 2, which like Firm 1 aims at maximising its expected profit. Finally, I consider that the ease and time to imitate are dependent on the type of protection employed by the inventor. Evidently, the profit of each firm does not depend only on its individual decisions but also on the actions of the other firm, and thus the equilibrium of the game is determined from the strategic interactions between the two competing firms. This is achieved by comparing the profit of a firm that has a patented technology with that of the profits earned when the same technology is protected by secrecy.
On the one hand, patenting a technological improvement or a process invention enables the public to freely observe and study the protected technology during the patent term without wasting time and effort to discover it. Additionally, the patent act permits the public, and, particularly, competitors, to freely use the protected technology after expiration. Furthermore, patent rights are imperfect means of protection, in that others can invent around patented innovative efforts. Prior empirical literature focused on the imperfections of intellectual property protection for successful process inventions, has found that an invention is typically imitated with a probability of 34 per cent within the first year after its introduction (Levin et al., 1987) and with a probability of almost 60 per cent within the fourth year (Mansfield et al., 1981).Footnote 7 On the other hand, a trade secret derives its economic value from not being publicly available. A trade secret is attractive and valuable because it prevents information disclosure and has an indefinite economic life in the absence of an accidental disclosure and independent discovery. However, a trade secret typically changes hands among various locations and employees, thereby giving rise to a positive probability of the public disclosure of the secret (Epstein, 2003). This might lead to a loss of the secret’s status and its commercial value. Other causes that might diminish the value of a trade secret are weak enforcement of property rights and misappropriation or theft.Footnote 8
The main findings of the analysis are as follows. First, I demonstrate that the equilibrium protection choice depends on the efficiency of the imitation technology and the strength of intellectual property protection. Furthermore, patent protection might be more or less preferable to secrecy depending on whether certain conditions are satisfied. Second, a technology transfer always occurs if the efficiency to imitate a patented technology and to imitate a secret are sufficiently low. Conversely, if both the imitation technologies are highly efficient, then the imitation would dominate. Third, I show that the risk of accidental leakage lessens the attractiveness of trade secret protection, whereas it might encourage imitation. Additionally, the incentives to patent are fostered in a real-world scenario in which the probability of leakage might increase with the number of firms practising a trade secret.
Section 2 reviews the literature that analyses the effects of imitation and the strength of intellectual property protection on the licensing behaviour of innovating firms. In Sect. 3, I present a model of technology licensing through patenting and secrecy under the threat of imitation and imperfect intellectual property protection. In Sect. 4, I characterise the equilibrium outcomes of the game and apply Nash bargaining to determine the licensing fees in equilibrium. I also explore the random event of leakage of the trade secret. In Sect. 5, I discuss the main economic implication of the analysis and conclude.
2 Literature review
This section reviews the literature on technology licensing that emphasised the imperfect protection and weak enforcement of intellectual property rights (IPRs). Particularly, the review focuses on the theoretical research that analyses the factors that determine the optimal licensing behaviour of innovating firms and, in turn, the effects of licensing on the diffusion of technology, incentives to innovate, investment in imitation, and social welfare.
Friedman et al. (1991) analysed the loss of secrecy by accidental leakage and discovery considering the lack of protection that characterises the trade secret law. The authors suggested that relying on secrecy might reflect the fact that patenting is unified instead of technology-specific, and thus secrecy might be more beneficial in terms of economic reward and protection time. Likewise, I show that the strength of intellectual property protection affects the strategic behaviour of innovating firms and the type of technological advances licensed in equilibrium. Gallini (1992) also analysed the protection choices of firms by incorporating in the analysis optimal patent design and costly endogenous (imperfect) imitation. The author suggested that short-term patents are socially optimal when the patent length is the only available policy instrument, while broad patents with an adjusted patent length become optimal with an option to choose the patent breadth (scope).Footnote 9 Following Gallini (1992), I also determine imitation endogenously and consider that it is uncertain and takes time to occur. Takalo (1998) extended Gallini (1992)’s model by accounting for the spillover of research and development (R&D) that arises due to a rational imitation by a competitor. Takalo (1998) confirmed Gallini (1992)’s social optimality of short patents; however, Takalo (1998) argued that broad patents are not always optimal when imitation is costly, especially when associated with large spillovers. In an effort to determine optimal licensing when a technology holder has protection choices, I assume that both innovation and imitation determine the diffusion of new technology in an industry, similar to the consideration in Takalo (1998).
Maurer and Scotchmer (2002) suggested that licensing can serve as a managerial tool to deter duplication (perfect imitation) even when independent invention serves as a defence against infringement. The authors found that the threat of duplication by an unlimited number of entrants induces the diffusion of new technology because it lowers licensing fees and reduces entry to patent races, which, in turn, mitigates wasteful, duplicative effort. Additionally, Maurer and Scotchmer (2002) demonstrated that a new entry does not undermine investment in innovation when discovery does not lead to infringement and is not less than half the cost of invention. Ottoz and Cugno (2004) extended Maurer and Scotchmer (2002)’s analysis to consider the case of a single potential entry in the face of legal restriction on licensing contracts, that is, no negative fixed licensing fees. Building on the earlier literature described above, Anton and Yao (2004) examined the problem of how much knowledge should an innovating firm disclose, and how much it should conceal. The authors assumed Cournot competition characterised by asymmetric information about the extent of innovation and limited protection of property rights from imitation. They suggested that, in equilibrium, small inventions are patented free of imitation threat, larger inventions are protected through both patents and secrets in the face of imitation, and large inventions are protected by trade secrecy. The main reflection that comes from these findings is that when property rights are weak, technological information about smaller inventions is typically disclosed, whereas information about larger inventions is mostly concealed. Although I do not consider innovation size and a specific industry structure in my analysis, I find that technology licensing is optimal for inefficient or small imitations, but not for sufficiently large imitations.
Denicolo and Franzoni (2003), while also analysing imitation and market size of innovation, explored the contract theory of patents assuming that patenting is a substitute to secrecy.Footnote 10 The authors suggested that secrecy is typically the least socially preferable choice. Additionally, Denicolo and Franzoni (2003) showed that an inventor’s defence against infringement strengthens incentives to innovate, but lessens patenting and social welfare. In a companion paper, Denicolo and Franzoni (2004) analysed how changes in the scope of patent rights granted to the first and second inventors affect the first inventor’s propensity to patent and incentives to innovate. The authors assumed a game of complete information in which patent protection is perfect, but secrecy does not prevent imitation and leakage. Additionally, Denicolo and Franzoni (2004) compared the main policy options about the first and second inventors’ patent rights.Footnote 11 They found that the introduction of prior-user rights stimulates investment in innovation, reduces first inventor’s propensity to patent, and produces an uncertain effect on social welfare, which depends on whether or not the patent term is set optimally.Footnote 12 Extending their previous work on the contract theory of patents, Denicolo and Franzoni (2008) considered duplication with and without licensing, as well as preemptive licensing. The authors also regarded patents as an alternative to secrets, emphasising the fundamental difference that patents disclose information and encourage investment in innovation, while secrets conceal information. Additionally, they highlighted that under the patent act, inventors cannot file for formerly secret inventions to be patented after a grace period, and often, only complex inventions are protected by both patents and secrets. In line with Denicolo and Franzoni (2003, 2004, 2008), I also consider patenting as an alternative to secrecy. Specifically, I compare patents versus secrets incorporating imperfect intellectual property protection and assuming that the ease to imitate depends on the type of protection adopted by the first inventor.
Kultti et al. (2006) compared the choice of an inventor between patenting and secrecy when innovation is simultaneous, that is, a patent race. The authors suggested that the first inventor typically patents to prevent others from patenting even when secrecy offers better protection. Particularly, the first inventor’s propensity to patent increases with the likelihood of the second inventor to successfully innovate. In Kultti et al. (2007), the authors extended their previous work to a more comprehensive model that included a continuum of inventors and inventions. Kultti et al. (2007) found similar results, thereby suggesting that an effective patent system is more important for disclosing information than for rewarding innovative effort. Particularly, firms engage in costly patenting to prevent others from patenting the same invention; in this case, the first inventor risks both infringement and return appropriation. Being the first inventor is not always a defence against infringement. Unlike Kultti et al. (2007), which considered patents and trade secrets to be mutually exclusive protection choices, Ottoz and Cugno (2011) developed a model where both patents and secrets can be used to protect different aspects of the same invention (see, also, Garvey and Baluch, 2007). The authors assumed that only the component of the technology that relies on secrecy can be duplicated with a success probability; this probability depends on the duplication effort and scope of the trade secret law, that is, the level of concealed information that is spilled out. The authors determined conditions wherein secrecy can enable the society to save on wasteful imitation expenditure, and thereby become socially beneficial; this analysis was supported by prior empirical evidence, such as Cohen et al. (2000) and Arundel (2001), but opposed by Denicolo and Franzoni (2004) and several other studies. Yeh (2016) provided a more recent overview of the purpose, enforcement, limitation, and misappropriation of the trade secret law.Footnote 13
The available empirical evidence about the means of appropriating returns from investment in R &D shows that firms rely more on secrecy and lead time than on the patent system (see, for example, Levin et al., 1987; Anton and Yao, 2004; Hall et al., 2014). For example, Cohen et al. (2000) suggested that, although patent protection is among the main protection mechanisms in numerous industries, firms benefit from patenting in ways other than the protection of property rights. For instance, patent rights can be used to prevent new entry, block competitors, mitigate infringement risk, and increase bargaining power in technology transfer. Arundel (2001), analysed which protection choice is more effective as an appropriation mechanism. The author found that secrecy prevails as an effective appropriation method for both process and product inventions, which confirmed Cohen et al. (2000). Another interesting result of Arundel (2001) is the relevance of firm size on the effectiveness of intellectual property protection choice. Particularly, Arundel (2001) showed that the value of secrecy increases with firm size; however, the relative value of secrecy, when compared to patents, declines with firm size. Arora and Ceccagnoli (2006) and Arora et al. (2008) found that licensing through trade secrets occurs less often than licensing through patent rights. Most of this evidence is based on surveys that focus on the firm size and innovation size to determine the protection choice in equilibrium. Although I do not take into account firm size in my analysis, extending the analysis to the case with small and big types of firms might lead to useful insights about current problems with the patent act and trade secret law.
Horstmann et al. (1985) developed a model of patenting behaviour in which the disclosure of technical information might lead to imitation. The authors aimed to explain the decision of firms to patent only a proportion of their intellectual property.Footnote 14 They argued that patent disclosing makes imitation easier, which reduces firms’ propensity to patent and, in turn, increases firms’ reliance on trade secrecy. Hussinger (2006) examined the influence of patents and secrecy on a firm’s profits as indexed by sale figures. The author pointed out that firms tend to apply for both protection mechanisms; however, there are prominent industry preferences for the use of one mode over the other. In other words, patent effectiveness varies significantly across industries and judicial systems. Moreover, other industry-related features and employed innovation strategies have a limited impact on the propensity to file for a patent or opt for secrecy. Conversely, firm size, but not R &D intensity, has a strong positive impact on patent desirability. Additionally, Layne-Farrar (2014) showed that, generally, patents that are a part of standards are more valuable than patents that are not included in standards. In turn, Layne-Farrar (2016) demonstrated a strong impact of intellectual property protection on firms’ competitive advantage. The trade-off among available protection choices is thus a challenging problem in theoretical and empirical economics. Particularly, economists have sought to measure the value of patents and licences and their implications in firms’ strategic behaviour, and although much progress has been achieved, a conclusive answer remains to be seen.Footnote 15
3 The model
Let Firm i for \(i=\{1, 2\}\) denote the firms in a single market of a homogeneous (identical) good. Assume that Firm 1, which invested in innovation in the past, has developed a new technology for the production of a specific product. Let the initial investment of Firm 1 to develop the new technology be a sunk cost, and thus be irrelevant for decision making purposes. Additionally, consider that a single potential rival, Firm 2, can enter the market through licensing or imitation.
In the first stage of the game, Firm 1 should choose the type of intellectual property protection upon which it can rely. Particularly, Firm 1 should decide whether to patent the new technology or rely on secrecy to protect it. In the second stage, the two competing firms should decide whether to enter into a licensing agreement on the rights to use the new technology. By licensing, Firm 1 transfers the new technology to Firm 2 in return for a fixed licence fee and the firms compete in quantities, according to Cournot competition (Cournot, 1838). This yields a symmetric duopoly payoff \(\pi ^{d}\) for each firm.
Alternatively, Firm 2 can try to imitate the new technology. I assume that patenting and secrecy are imperfect means of protection. Additionally, the ease and time involved in imitating differ under each protection choice, which implies that the expected profits in equilibrium are dependent on the type of protection that is adopted in the first stage of the game. If imitation is successful, then the firms will engage again in a Cournot competition and each firm will earn \(\pi ^{d}\); otherwise, Firm 1 will earn the monopoly rent \(\pi ^{m}\) where \(\pi ^{m}>\pi ^{d}\), while Firm 2 will earn no profit.Footnote 16 Each firm aims at maximising its profit, and the game involves perfect information, thus I employ the Nash equilibrium solution (Nash, 1950). Principally, each firm anticipates the sequence of actions and the optimal actions of the other firm and includes this information in its decision making to maximise its profit.
In games of imperfect information, where firms are unaware of the actions chosen by other firms, an equilibrium cannot be reached by firms playing optimal deterministic strategies. Moreover, a subgame perfect Nash equilibrium is not even self-enforcing (Selten, 1975), thus requiring a refinement notion of equilibrium, including a belief system at all information sets of a game. In this case, the most commonly applied refinement is the solution concept sequential equilibrium developed by Kreps and Wilson (1982). In our context, this would complicate the analysis, as inefficient license contracts could occur, resulting in dead-weight loss. A potential solution to this would be applying strategies that are sequentially rational with respect to some conditional belief system and that this is consistent with Bayes’ rule applied to the strategy profile on each selected path, i.e., a weak perfect Bayesian equilibrium (Ritzberger, 2002).
3.1 The decision to patent
Consider that Firm 1 relies on patent protection in the first stage of the game. Patenting involves information disclosure and it does not prevent imitation. Additionally, upon expiry, which is assumed to be in time T, the technology becomes freely available to the public. When patent protection expires, the profits of the technology holders are driven to zero. Once the decision about the protection choice has been made, Firm 1 should decide whether to transfer the technology in return for an upfront fixed payment \(F_{p}\), where \(F_{p}>0\). In fact, technology transfer is an agreement that must be accepted by both parties; licensing occurs if each firm is better off accepting the agreement than rejecting it. When a licensing agreement occurs, each firm begins production at time 0 and receives a symmetric duopoly payoff \(\pi ^{d}\) from time 0 to time T. Additionally, Firm 2 pays a fixed fee \(F_{p}\) to Firm 1 at time 0 in return for the technology transfer. Let an ordered pair of entries denote the distribution of payoffs for each outcome of the game, where the first entry corresponds to the payoff of Firm 1 and the second entry to the payoff of Firm 2. Then, the payoff outcome of this case, without discounting, is \((\pi ^{d}+F_{p},\pi ^{d}-F_{p})\).Footnote 17
If technology transfer does not occur, then Firm 2 would opt for an uncertain and costly imitation. Let Firm 2 incur an imitation cost \(C_{p}=\frac{1}{2}\alpha _{p}x^2\) at time zero, where \(\alpha _{p}\) represents the exogenous efficiency of the technology in imitating a patent, and x denotes the endogenously determined probability of successful imitation, as discussed in Takalo (1998). Additionally, let \(\alpha _{p}\) be a sufficiently large positive number to ensure that \(x \le 1\). The underlying rationale for adopting this functional form for the imitation cost is that the higher the efficiency of the existing technology to imitate, the higher the cost incurred by the firm opting to imitate. It is evident that Firm 2 successfully imitates the new technology with a probability x and fails to imitate with a probability \(1-x\).
Imitation is not instantaneous; therefore, let \(t_{p}\) denote the time required to imitate the patented technology. Considering that the technology becomes freely available to the public when the patent expires, it implies that imitation is valuable only if it occurs earlier than the patent expiration, that is, \(t_{p}<T\). If imitation is successful, then each firm would earn the duopoly payoff \(\pi ^{d}\) from the time \(t_{p}\) that Firm 2 enters the market until time T that the patent expires. In this case, the payoff outcome without discounting will be \((\pi ^{d},\pi ^{d})\). If imitation is unsuccessful, then Firm 1 would earn the monopoly rent \(\pi ^{m}\) until time T, while Firm 1 will not enter the market, and thus receive nothing. As a result, the payoff outcome of this event, without discounting, will be \((\pi ^{m},0)\).
I will now determine the equilibrium when Firm 1 relies on patent protection in the first stage of the game. Assume that all profits are discounted at a continuously compounded common rate r, where \(r>0\). Additionally, it is helpful to define the discounted value of a unit flow earned from time \(t_{1}\) to time \(t_{2}\), where \(t_{1}<t_{2}\):
The measure \(\delta _{t_{1}}^{t_{2}}\) is convenient for computational purposes and can also be seen as a discounted-adjusted protection length (see, for example, Aoki and Hu, 2003; Denicolo and Franzoni, 2004).
First, consider that Firm 1 patents and offers a licence to transfer the technology. Clearly, licensing occurs if each firm is better off with the agreement than without it. Let \(\pi ^{L}_{i}\) for \(i=\{1, 2\}\) be the profit of Firm i when the technology is patented, and a licensing agreement is established. Then, the profits of Firms 1 and 2 are:
Second, consider that technology transfer does not occur. In this case, Firm 2 opts for imitation incurring a cost equal to \(C_{p}=\frac{1}{2}\alpha _{p}x^2\). Imitation occurs with probability x, which is chosen by Firm 2 that aims at maximising its expected profit. Let \(\pi ^{I}_{i}\) for \(i=\{1, 2\}\) be the profit of Firm i when Firm 2 tries to imitate the patented technology. Then, the expected profits of Firms 1 and 2 are:
It follows that the optimal probability of imitation can be determined from the first order condition of the following maximisation problem:
Let the superscript (\(*\)) denote the value of a variable in equilibrium, then the optimal probability of imitation is equal to \(x^{*}=\frac{1}{\alpha _{p}}\pi ^{d}\delta _{t_{p}}^{T}\).Footnote 18 This shows that as the exogenous efficiency of the imitation technology \(\alpha _{p}\) increases, the optimal imitation success probability decreases. This is because the imitation cost for Firm 2 is already significantly high for large values of \(\alpha _{p}\), and the addition of an extra unit of effort, i.e., an increase in x, becomes prohibitively costly. Consequently, the expected profits in equilibrium of Firms 1 and 2 are:
A licensing agreement occurs if \(\pi ^{L}_{1}+\pi ^{L}_{2} \ge \pi ^{I}_{1}(x^{*})+\pi ^{I}_{2}(x^{*})\), which is equivalent to \((\pi ^{m}-2\pi ^{d})\delta _{0}^{T} \le \frac{1}{\alpha _{p}}\pi ^{d}(\pi ^{m}-\pi ^{d}){(\delta _{t_{p}}^{T})}^{2}-\frac{1}{2\alpha _{p}}{(\pi ^{d}\delta _{t_{p}}^{T})}^{2}\). Rearranging this condition with respect to \(\alpha _{p}\), I establish the following result:
Proposition 1
A transfer of a patented technology, between Firms 1 and 2, occurs if and only if \(\alpha _{p} \le \hat{\alpha }_{p}\), where the licensing threshold \(\hat{\alpha }_{p}\) is defined to be:
Proposition 1 suggests that the technology transfer depends primarily on the relative magnitudes of the difference between monopoly profit and firms’ joint profit under imitation, and the difference between monopoly profit and firms’ joint profit under licensing. Specifically, the profit difference in the numerator of the expression in brackets in Eq. 6 represents the difference between monopoly profit (no imitation) and the aggregate profits of the firms under imitation from the time of imitation occurrence \(t_{p}\) until the maturity of the patent. Meanwhile, the denominator of that expression signifies the difference in profits between monopoly profit (no licensing) and the aggregate profits of the firms under licensing, capturing the efficiency gain. Moreover, the longer the patent term, the greater the licensing interval in support of a technology transfer, and thus the greater the attractiveness of patent licensing.Footnote 19 This is because the duopoly profit can be earned for a more extended time period compared to a shorter patent expiration time, resulting in less future profits.
Consider the optimal fee to transfer the new technology. This scenario represents a common bargaining problem, characterised by a conflict of interest between two firms striving for a mutually beneficial outcome. In general, such problems raise question about the distribution of profits from a potential agreement. Let the bargaining power of Firm 1 be \(\beta\), and that of Firm 2 be \(1-\beta\), where \(0 \le \beta \le 1\). I can now solve this game by employing Nash bargaining to determine the equilibrium fixed fee at which a licensing contract can be subscribed to transfer the new technology. The bargaining problem is \(\displaystyle \max _{F_{p} \ge 0} \big (\pi ^{L}_{1}-\pi ^{I}_{1}(x^{*})\big )^{\beta }\big (\pi ^{L}_{2}-\pi ^{I}_{2}(x^{*})\big )^{1-\beta }\); by substituting the profit functions, this becomes equivalent toFootnote 20
Let \(F_{p}^{*}\) be the optimal licensing fee determined using Nash bargaining at which a transfer of the patented technology occurs. Then, the first order condition of Eq. 7 yields (see Appendix A):
According to Eq. 8, the optimal licensing fee rises with the bargaining power of the patent holder \(\beta\), the cost to acquire a highly efficient imitation technology represented by \(\alpha _{p}\), and the time required to achieve imitation \(t_{p}\) (see Appendix B).
Consider now the equilibrium licensing fee for different efficiency levels of the imitation technology. In theory, as \(\alpha _{p}\) tends to zero, imitation becomes costless. Consequently, the optimal probability of imitation tends to unity, and the licensing fee in equilibrium falls to zero, leading to nearly certain imitation. Thus, both firms begin production simultaneously, and only a trivial licensing fee makes Firm 2 indifferent between technology transfer and imitation.Footnote 21 Conversely, as \(\alpha _{p}\) tends to infinity, the cost of imitation becomes prohibitively large, making imitation unlikely. Consequently, Firm 1 charges the maximum possible licensing fee that would facilitate technology transfer. However, in this case, technology transfer does not occur because the profit of Firm 1 as a monopolist exceeds its profit as a licensor.
An interesting scenario to consider is when Firm 1 has a maximum contractual advantage over Firm 2, i.e., \(\beta =1\). In this scenario, Firm 1 extracts the entire surplus from a potential licensing agreement. It is common in patent licensing agreements for the licensor to establish a break-even fee, making the competing firm indifferent between becoming a licensee or not (Kamien & Tauman, 1986). Specifically, substituting \(\beta\) equal to 1 in Eq. 8 yields a licensing fee equal to \(\pi ^{d}\delta _{0}^{T}-\frac{1}{2\alpha _{p}}{(\pi ^{d}\delta _{t_{p}}^{T})}^{2}\). Similarly, if Firm 2 has maximum bargaining power, i.e., \(\beta =0\), the equilibrium licensing fee is equal to \((\pi ^{m}-\pi ^{d})\delta _{0}^{T}-\frac{1}{\alpha _{p}}\pi ^{d}(\pi ^{m}-\pi ^{d}){(\delta _{t_{p}}^{T})}^{2}\). Finally, consider the scenario when both firms have equal bargaining shares, i.e., \(\beta =\frac{1}{2}\), which aligns closely with the real world conflict of interest situation. In this scenario, the equilibrium licensing fee is equal to \(\frac{1}{2}[\pi ^{m}\delta _{0}^{T}-\frac{1}{\alpha _{p}}\pi ^{d}(\pi ^{m}-\frac{1}{2}\pi ^{d}){(\delta _{t_{p}}^{T})}^{2}]\). This fee is larger than the equilibrium licensing fee when Firm 1 has minimum bargaining power (\(\beta =0\)) but smaller than the equilibrium fee when Firm 1 has maximum bargain power (\(\beta =1\)). All these scenarios correspond to specific cases of the Nash bargaining solution defined in Eq. 8.
3.2 The decision to rely on secrecy
Consider that Firm 1 keeps the new technology secret in the first stage of the game. A trade secret presumes that reasonable measures have been taken to maintain the secrecy of the scientifically and commercially valuable information by its rightful holder. This information concealment might, in turn, render imitation more difficult than when valuable information is publicly disclosed. However, it cannot prevent independent discovery or accidental disclosure. Particularly, the protection of a trade secret can last for an unlimited period of time unless the secret is independently discovered, legally acquired by others, or unintentionally leaked to the public. When the information becomes freely available to the public, a trade secret loses its commercial value, and thus the profits of the technology holders are driven to zero. I will first set the probability that the confidential information might accidentally leak out equal to zero.
In the second stage of the game, Firm 1 should decide whether to transfer the rights of the trade secret to Firm 2 in return for a fixed licensing fee \(F_{s}\), where \(F_{s}>0\). Secrecy is characterised from the perspective of an indefinite term and the transmission of less valuable information to Firm 2 when compared to a patent system, which might potentially lessen the incentives of Firm 2 to imitate. If technology transfer occurs, then each firm will earn \(\pi ^{d}\) from time 0 to perpetuity, unless the secret leaks to the public. Although I am considering a duopoly case, leakage here has the same effect as patent expiration. Other firms that can exploit this information and commercialise it will adopt the new technology and enter the market, leading to competitive profits prevailing in the market. Additionally, Firm 2 transfers a fixed fee \(F_{s}\) to Firm 1 at time 0 to legally use the technology. In this case, the payoff outcome, without discounting, is \((\pi ^{d}+F_{s},\pi ^{d}-F_{s})\).
However, if technology transfer does not occur, then Firm 2 will opt for imitation and incur a cost \(C_{s}=\frac{1}{2}\alpha _{s}y^2\) at time zero, where \(\alpha _{s}\) reflects the exogenous efficiency of the technology in imitating a secret, and y can be seen as the likelihood of a successful imitation. Similar to the patent protection case, \(\alpha _{s}\) is assumed to be sufficiently large to ensure that \(y \le 1\). If imitation is successful, which occurs with a probability y, then each firm would receive \(\pi ^{d}\) from time \(t_{s}\) to an unlimited period of time. As a result, the payoff outcome of this event, without discounting, is \((\pi ^{d},\pi ^{d})\). If Firm 2 fails to imitate, which has a probability \(1-y\) to occur, then Firm 1 would get the monopoly profit \(\pi ^{m}\) forever, while Firm 2 would not earn any profit. The payoff outcome is (\(\pi ^{m},0\)).
I will now determine the equilibrium when Firm 1 chooses secrecy as its protection mechanism. Let all profits be discounted at the continuously compounded common rate r, and \(v_{i}^{L}\) be the profit of Firm i for \(i=\{1, 2\}\), when Firm 1 keeps the technology secret and a licensing agreement occurs. The profits of Firms 1 and 2 are:
where \(\delta _{0}^{\infty }\) is equal to \(\frac{1}{r}\). However, in order to be consistent throughout the analysis, I use the \(\delta _{t_{1}}^{t_{2}}\) measure, which is defined in Eq. 1. Next, consider that technology transfer does not occur, and thus Firm 2 aims at independent discovery or imitation of the new technology. Similar to when the technology is patented, y is chosen by Firm 2 that aims to maximise its expected profit. Let \(v_{i}^{I}\) for \(i=\{1, 2\}\) be the profit of Firm i when Firm 2 tries to imitate the concealed invention. Then, the expected profits of Firms 1 and 2 are:
Similar to the patent licensing case, the optimal probability of imitation can be determined as follows:
This gives an optimal probability of imitation equal to \(y^{*}=\frac{1}{\alpha _{s}}\pi ^{d}\delta _{t_{s}}^{\infty }\).Footnote 22 As a result, the expected profits in equilibrium of Firms 1 and 2 are:
Equations 9 and 12 indicate that technology transfer occurs if \((\pi ^{m}-2\pi ^{d})\delta _{0}^{\infty } \le \frac{1}{\alpha _{s}}\pi ^{d}(\pi ^{m}-2\pi ^{d}){(\delta _{t_{s}}^{\infty })}^{2}-\frac{1}{2\alpha _{s}}{(\pi ^{d}\delta _{t_{s}}^{\infty })}^{2}\). Similar to the patent licensing condition, I establish the following result:
Proposition 2
A transfer of a technology protected by secrecy, between Firms 1 and 2, occurs if and only if \(\alpha _{s} \le \hat{\alpha }_{s}\), where the licensing threshold \(\hat{\alpha }_{s}\) is defined to be:
Proposition 2 suggests that the transfer of a trade secret, similar to that of a patent, depends on the relative magnitudes of the monopoly and duopoly profits.
Consider the optimal licensing fee when Firm 1 resorts to secrecy. The bargaining problem is \(\displaystyle \max _{F_{s}\ge 0} \big (v^{L}_{1}-v^{I}_{1}(x^{*})\big )^{\beta }\big (v^{L}_{2}-v^{I}_{2}(x^{*})\big )^{1-\beta }\) or, equivalently:
Let \(F^{*}_{s}\) denote the optimal licensing fee of a secret determined using Nash bargaining. Then, the first order condition of Eq. 14 gives:
Similar to the optimal licensing fee \(F^{*}_{p}\) defined in Eq. 8, the optimal licensing fee of a secret rises with the bargaining power of the technology holder \(\beta\), the cost to acquire a highly efficiency imitation technology represented by \(\alpha _{s}\), and the time required to achieve imitation \(t_{s}\). These similar results are expected due to the symmetric nature of the bargaining problem. Moreover, if \(\alpha _{s}\) is sufficiently low, the cost of imitation becomes negligible, and the success probability of imitation tends to one. As a result, only a sufficiently small licensing fee triggers a technology transfer. On the contrary, if \(\alpha _{s}\) is sufficiently large, the success probability tends to zero. In this case, the licensing fee required to facilitate a technology transfer becomes larger than the maximum fee that Firm 2 is willing to pay to acquire a licence. Consequently, a technology transfer does not occur, and Firm 1 becomes a monopoly.
Consider now the specific cases of the Nash bargaining solution when the new technology is protected through secrecy. When Firm 2 has maximum bargaining power, i.e., \(\beta =0\), the equilibrium licensing fee is equal to \((\pi ^{m}-\pi ^{d})\delta _{0}^{\infty }-\frac{1}{\alpha _{s}}\pi ^{d}(\pi ^{m}-\pi ^{d}){(\delta _{t_{s}}^{\infty })}^{2}\). If \(\beta =1\), then the equilibrium fee is equal to \(\pi ^{d}\delta _{0}^{\infty }-\frac{1}{2 \alpha _{s}}{(\pi ^{d}\delta _{t_{s}}^{\infty })}^{2}\). When \(\beta =1/2\), the equilibrium fee is \(\frac{1}{2}[\pi ^{m}\delta _{0}^{\infty }-\frac{1}{\alpha _{s}}\pi ^{d}(\pi ^{m}-\frac{1}{2}\pi ^{d}){(\delta _{t_{s}}^{\infty })}^{2}]\). These results are similar to those under patent licensing, with the difference being that the efficiency of the imitation technology and the protection lifetime correspond to a trade secret instead of a patent.
4 The equilibrium
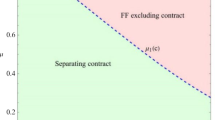
Propositions 1 and 2 define a licensing threshold for each of the available protection choices of Firm 1, namely \(\hat{\alpha }_{p}\) for patent protection and \(\hat{\alpha }_{s}\) for secrecy protection. This suggests that a technology transfer occurs if the efficiency of the imitation technology does not exceed the corresponding licensing threshold. Therefore, the strategic interaction between the firms depends on the efficiency of the imitation technology. Essentially, the protection choice is, in turn, dependent on the probabilistic outcome of imitation. Now, I will compare the two protection choices to determine the equilibrium outcomes of the game.
First, suppose that the efficiency of the technology to imitate a patent and to imitate a secret are both sufficiently low, that is, \(\alpha _{p} \le \hat{\alpha }_{p}\) and \(\alpha _{s} \le \hat{\alpha }_{s}\). According to Eqs. 6 and 13, a technology transfer occurs, regardless of the protection decision of Firm 1 in the first stage of the game. Essentially, the profit of Firm 1 with a patented technology is \(\pi _{1}^{L}(F^{*}_{p})=\pi ^{d}\delta _{0}^{T}+F^{*}_{p}\) and that with a technology protected by secrecy is \(v_{1}^{L}(F^{*}_{s})=\pi ^{d}\delta _{0}^{\infty }+F^{*}_{s}\). The new technology is thus patented if \(\pi _{1}^{L}(F^{*}_{p}) \ge v_{1}^{L}(F^{*}_{s})\), and this condition is equivalent to:
This condition shows that patent protection is optimal for Firm 1 when the threshold M is equal to or higher than one.Footnote 23 Similar to the case described above, when only the technological efficiency to imitate a patent is sufficiently low, while that for a secret is sufficiently high, that is, \(\alpha _{p} \le \hat{\alpha }_{p}\) and \(\alpha _{s} > \hat{\alpha }_{s}\), patenting is optimal if \(M \ge 1\). In other words, if the condition given by Eq. 16 holds, then the profit of Firm 1 with a patent would be at least as large as the profit of Firm 1 with a secret, that is, \(\pi _{1}^{L}(F^{*}_{p}) \ge v^{I}_{1}(y^{*})\). Note that the patenting threshold is consistent because of the weak preferences assumed when determining the optimal licensing fees. It is important to also note that the incentives to patent increase with the technological efficiency and time to imitate a patent, that is, \(\partial M / \partial \alpha _{p}>0\) and \(\partial M / \partial t_{p}>0\), unlike with the efficiency and time to imitate a trade secret, that is, \(\partial M / \partial \alpha _{s}<0\) and \(\partial M / \partial t_{s}<0\) (see Appendix C).Footnote 24
Second, let both the efficiency of the imitation technology of a patent and that of a secret be sufficiently high, that is, \(\alpha _{p} > \hat{\alpha }_{p}\) and \(\alpha _{s} > \hat{\alpha }_{s}\). Then, Eqs. 6 and 13 imply that a technology transfer does not occur, regardless of whether Firm 1 chooses to patent the new technology or keep it a secret. If Firm 1 chooses to patent the technology, then it would receive \(\pi ^{I}_{1}(x^{*})\); however, if it chooses to conceal the technology, then it would get \(v^{I}_{1}(y^{*})\). Evidently, patenting occurs if \(\pi ^{I}_{1}(x^{*}) \ge v^{I}_{1}(y^{*})\), which can also be written asFootnote 25:
This means that patenting prevails in equilibrium when the threshold N is equal to or larger than one. Finally, consider the case when the efficiency of the technology to imitate a patent is sufficiently high, while to imitate a trade secret is sufficiently low, that is, \(\alpha _{p} > \hat{\alpha }_{p}\) and \(\alpha _{s} \le \hat{\alpha }_{s}\). If Firm 1 relies on patent protection in the first stage of the game, it would earn \(\pi ^{I}_{1}(x^{*})\), while if Firm 1 keeps the technology a secret, it would earn \(v_{1}^{L}(F^{*}_{s})\). A comparison of these profits shows that if the condition given by Eq. 17 holds, then the profit of Firm 1 with a patent would be at least as large as the profit of Firm 1 with a secret. In other words, Firm 1 is indifferent between accepting and rejecting an agreement to transfer a secret at an optimal licensing fee, and hence the threshold is consistent. The properties of N are the same as those of M, that is, N increases with the technological efficiency and time to imitate a patent, while it decreases with the technological efficiency and time to imitate a secret. Ultimately, I establish the following result about the equilibrium outcomes of the game:
Proposition 3
Consider that the patenting thresholds M and N are defined by Eqs. 16 and 17, respectively. Then, Firm 1 relies on the patent system to protect a new technology if and only if \(M \ge 1\) or \(N \ge 1\); otherwise, secrecy characterises the equilibrium of the game. Additionally, when \(M \ge 1\), a technology transfer through patent licensing occurs; otherwise, licensing of a technology protected by secrecy occurs in equilibrium.
Proposition 3 suggests that both patenting and secrecy can characterise the equilibrium of the game if certain conditions hold. Additionally, it suggests that a technology transfer always occurs in equilibrium, regardless of the protection decision of Firm 1, if both the technological efficiency to imitate a patent and to imitate a secret are sufficiently low. However, if both the imitation technologies are sufficiently efficient, then imitation would always prevail in equilibrium.
Patenting and secrecy also characterise the equilibrium of a game with more competing firms, where only one firm has a new technology (i.e., Firm 1). However, the outcomes will depend on the licensing mode and the imitation cost (or cost of entry). For example, in a hypothetical setup with three firms, if the two firms with the inferior technology are identical, and technology licensing occurs via a fixed fee, it can be shown that it is optimal for Firm 1 to license only to one of the firms, considering a sufficiently high imitation cost. This implies that technology licensing can be used to prevent entry. If, however, technology licensing occurs through per unit royalties, then it is optimal for the patentee to license to both competing firms. Moreover, if the two firms with the inferior technology have different unit production costs, then the analysis becomes more complex. Technology licensing can be used to select competition. Specifically, the patentee might find it optimal to license only to the firm with the highest unit production cost. This will lead to a decrease in the market share of its nearest competitor, if the patentee is unsuccessful in driving this firm out of the market.Footnote 26
In conclusion, I will explore the scenario where there is a chance of the trade secret being publicly disclosed, leading to its legal and economic devaluation. In the duopoly setup considered here, this means that Firm 2 can freely utilise the new technology, eliminating the need for independent discovery efforts. Considering that only two firms can benefit from this, they will share the industry profit in this case. In a real-world scenario, this implies that all firms capable of employing the new technology and generating a positive profit will do so. Once the technology becomes public, other competing firms that were previously unable to enter this market due to high entry costs can now enter freely and drive profits to a competitive level. Consider a constant probability of leakage that is independent of whether only Firm 1 or both firms adopt the secret. Specifically, assume that leakage occurs according to a Poisson distribution with a parameter \(\lambda\), where \(\lambda >0\). If Firm 1 keeps the technology secret, the discounted-adjusted protection length defined by Eq. 1 becomes:
Acknowledging that only the discounted-adjusted protection duration of the trade secret differs from the existing equilibrium analysis, I can apply exactly the same analysis and determine the equilibrium outcomes in this case (see Appendix D). The key difference lies in the decreased discounted-adjusted parameter (increased discount rate) due to a positive probability of leakage. This increases the incentives to imitate, as leakage is a factor determining the strength of secrecy. For example, the easier the secret leaks to the public, the weaker is the protection under secrecy, making secrecy less preferable than patenting.Footnote 27 Moreover, considering a probability of leakage that depends on the number of firms practising the new technology, i.e., assuming a higher probability of leakage when both firms adopt the trade secret, the same analysis will show increased patent attractiveness. In practice, the probability of accidental leakage rises with more firms practicing the secret, weakening trade secret protection, potentially encouraging imitation over trade secret transfer, but reinforcing incentives for patenting.
5 Conclusions
I analyse the behaviour of innovating firms by comparing the effects of patenting and secrecy on the incentives to license and imitate. I determine the equilibrium actions and outcomes of a two-stage game. In the first stage of the game, an inventor endowed with a new technology, along with filing for patent protection, also has the option of keeping the technology secret. In the second stage, a single potential entrant can enter the market through technology transfer or imitation.
I find that both patent protection and secrecy might prevail in equilibrium. Particularly, the equilibrium outcomes of the game depend on the ease and time required to achieve imitation, and the type of property protection employed by the technology holder. I show that, if both the technological efficiency to imitate a patented technology and to imitate a secret are sufficiently low, then, in equilibrium, technology transfer would always be better than imitation, regardless of the protection type employed by the inventor. Conversely, highly efficient imitation technologies result in imitation. I also prove that trade secret protection weakens in the presence of a positive probability of accidental leakage, thereby increasing the attractiveness of the patent protection. Although imitation might be more or less attractive than licensing under secrecy, often the risk of leakage tends to make it preferable.
It is evident that the results described above come from a simple model, which needs to be refined along several lines. For instance, the model could be expanded to comprehensively analyze the implications of a higher number of potential licensees or entrants, employing advanced game theoretic analysis. Additionally, it can be extended to analyse how the enforcement efficiency of IPRs and the size of the firms affect the incentives to license, imitate, and even litigate. Furthermore, considering that licensing and imitation are more frequent in specific industries and geographical locations, it is essential to enrich the model to enable the analysis of industry-specific effects of patenting and secrecy on technology diffusion and imitation. Finally, the empirical analysis of the relevance of the propositions established in this study and their testable welfare considerations is left for future research.
Data availability
This paper has no data generated or analysed.
Notes
Ocean Tomo, a firm providing an industry leading array of financial products and services related to intangible assets, estimates that intangibles have emerged as the leading asset class, growing from around 17 per cent of the entire market value of the S &P 500 in 1975 to approximately 87 per cent in 2015. For more information regarding the growth of intangible assets, see www.oceantomo.com.
Arundel (2001) studied innovative manufacturing firms in the US and showed that secrecy is potentially a more effective means of appropriation than patents. Hall et al. (2014) conducted a survey of the economic literature on intellectual property protection and showed that only 10 per cent of a sample of innovating firms in the UK rate patent protection as important, around 15 per cent rate secrecy as important, and more than half of them do not use intellectual property protection.
The appropriability concern occurs when firms investing in innovation have difficulty securing returns on that investment due to imitation by competing firms.
For additional information about patents, refer to Hall (2007); this study surveyed the theoretical and empirical literature on the effectiveness of patent protection and its incentives to spur innovation. However, for a thorough review of the theory of trade secrets, refer to Dreyfuss and Strandburg (2011) and the literature cited therein.
In order for confidential information to be considered a trade secret, it must comply with certain conditions and general standards, which are specified in the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS Agreement).
I assume that imitation does not lead to potential infringement of patent rights or misappropriation of trade secrecy and that property rights of the new technology cannot be invalidated in a court of law.
One example of trade secret theft is the illegal transfer of Ford Motor Company's documents, which contained trade secrets about design specifications of engines and electric power supply systems, from an ex-Ford project engineer to China, particularly to Ford's rival Foxconn PCE Industry (Almeling, 2012).
The contract theory of patents states that the aim of patents is to diffuse technological advances.
In Europe, being the first inventor is a defence against infringement, whereas, in the United States, second inventors can exclude first inventors from the invention.
For a cost benefit analysis of prior-user rights, refer to Shapiro (2006).
The following literature is also useful to understand intellectual property protection and its implications. Schwartz (2004) addressed the question of patent valuation by implementing a simulation approach based on real options. Bulut and Moschini (2006) studied the strategic interaction between innovative firms that have a protection choice. The authors suggested that the availability of multiple protection mechanisms might lead to the selection of R &D projects that are closer to the socially desirable magnitude of correlation. Bessen and Maskin (2009) showed that, in a static setup, patents help inventors to cover the R &D costs and encourage innovative activity, but, in a sequential setting, the importance of patents is undermined. Baldi and Trigeorgis (2014) valued optimal intellectual property licensing in the light of a real options lens, by focusing in a case study from biotechnology.
I relax this assumption later in the analysis by discounting all payoffs at the time zero with a positive rate.
The optimal probability of imitation is more accurately given by the following equation:
$$\begin{aligned} x^{*}= & {} \left\{ \begin{array}{cl} \frac{1}{\alpha _{p}}\pi ^{d}\delta _{t_{p}}^{T} &{} \text{ for } \frac{1}{\alpha _{p}}\pi ^{d}\delta _{t_{p}}^{T} \le 1,\\ \\ 1 &{} \text{ for } \frac{1}{\alpha _{p}}\pi ^{d}\delta _{t_{p}}^{T} > 1. \end{array}\right. \end{aligned}$$However, I have already assumed that the parameter \(\alpha _{p}\) is large enough to ensure that \(x \le 1\); in this case, I need to consider only the first line of the above system of equations.
That is, \(\dfrac{\partial \hat{\alpha }_{p}}{\partial T} = \dfrac{2\big (\pi ^{m}-\frac{3}{2}\pi ^{d}\big )\delta _{t_{p}}^{T}\pi ^{d}e^{-rT}}{(\pi ^{m}-2\pi ^{d})\delta _{0}^{T}}-\dfrac{\big (\pi ^{m}-\frac{3}{2}\pi ^{d}\big ){(\delta _{t_{p}}^{T})}^{2}\pi ^{d}e^{-rT}}{(\pi ^{m}-2\pi ^{d}){(\delta _{0}^{T})}^{2}}>0.\)
It is important to note that the maximisation problem is subject to certain conditions, such as \(\pi ^{L}:_{1} \ge \pi ^{I}_{1}(x^{*})\) and \(\pi ^{L}_{2} \ge \pi ^{I}_{2}(x^{*})\). These two conditions, together, are equivalent to the licensing condition in Proposition 1, which is considered to determine the optimal licensing fee.
In an alternative scenario, many factors may deter firms from choosing imitation, such as the probabilistic nature of imitation, the rapid progress of technology, the enforcement of property rights, or a substantial time lag in the imitation process.
The optimal probability of imitation, similar to the effort when the technology is patented, can be more accurately given by the following equation:
$$\begin{aligned} y= & {} \left\{ \begin{array}{cl} \frac{1}{\alpha _{s}}\pi ^{d}\delta _{t_{s}}^{\infty } &{} \text{ for } \frac{1}{\alpha _{s}}\pi ^{d}\delta _{t_{s}}^{\infty } \le 1,\\ \\ 1 &{} \text{ for } \frac{1}{\alpha _{s}}\pi ^{d}\delta _{t_{s}}^{\infty } > 1. \end{array}\right. \end{aligned}$$However, given the assumption that \(\alpha _{s}\) is sufficiently large to ensure that \(y \le 1\); in this case, I need to consider only the first line of the above system of equations.
Assume that patenting prevails when Firm 1 is indifferent between the two available protection choices.
The partial derivatives of M with respect to the other variables cannot be determined unless further assumptions are made, particularly, regarding the relative magnitudes of \(\alpha _{p}\) and \(\alpha _{s}\). For example, it can be assumed that the difficulty to imitate a technology protected by secrecy is not less than the difficulty to imitate a patented technology. This might, in turn, imply that the length of time required to achieve imitation of a concealed technology is not shorter than the length of time required to imitate a patented technology; for instance, the information disclosed when patenting might facilitate the process of imitation. Additionally, the measures taken by the technology holder to protect a trade secret might decelerate the process of reverse engineering.
Note that substituting for \(\beta =0\) in M gives N, which is expected, as this represent a case where technology transfer does not occur. Thus, there is no distribution of profits from a potential licensing agreement to be determined by the bargaining power \(\beta\).
Proofs can also be provided through numerical results for a general case of \(n>2\) firms.
It can also be interesting and closer to the real-world to analyse the trade-off between certain and finite patent protection and infinite, but uncertain, trade secret protection.
References
Almeling, D. (2012). Seven reasons why trade secrets are increasingly important. Berkeley Technology Law Journal, 27(2), 1091–1117.
Anton, J., & Yao, D. (2004). Little patents and big secrets: Managing intellectual property. The Rand Journal of Economics, 35(1), 1–22.
Aoki, R., & Hu, J. L. (2003). Time factors of patent litigation and licensing. Journal of Institutional and Theoretical Economics, 159(2), 280–301.
Arora, A. (1997). Patents, licensing, and market structure in the chemical industry. Research Policy, 26(4–5), 391–403.
Arora, A., & Ceccagnoli, M. (2006). Patent protection, complementary assets, and firms’ incentives for technology licensing. Management Science, 52(2), 293–308.
Arora, A., Ceccagnoli, M., & Cohen, W. (2008). R &D and the patent premium. International Journal of Industrial Organization, 26(5), 1153–1179.
Arundel, A. (2001). The relative effectiveness of patents and secrecy for appropriation. Research Policy, 30(4), 611–624.
Baldi, F., & Trigeorgis, L. (2014). IP licensing: How to structure a good deal. Sinergie, Rivista di Studi e Ricerche, 93, 55–78.
Belleflamme, P. & Bloch,F. (2013). Dynamic protection of innovations through patents and trade secrets. Available at SSRN 2537248.
Bessen, J., & Maskin, E. (2009). Sequential innovation, patents, and imitation. The Rand Journal of Economics, 40(4), 611–635.
Bogers, M., Bekkers, R., & Granstrand, O. (2012). Intellectual property and licensing strategies in open collaborative innovation. In C. de Pablos Heredero and D. L. Berzosa (Eds.), Open innovation in firms and public administrations: Technologies for value creation, Chapter 3, pp. 37–58. IGI Global, Hershey, PA.
Bulut, H., & Moschini, G. (2006). Patents, trade secrets and the correlation among R &D projects. Economics Letters, 91(1), 131–137.
Cohen, W., Nelson, R., & Walsh, J. (2000). Protecting their intellectual assets: Appropriability conditions and why U.S. manufacturing firms patent (or not). NBER Working Paper (7552).
Cournot, A. A. (1838). Recherches sur les principes mathématiques de la théorie des richesses. L. Hachette.
Denicolo, V. (2007). Do patents over-compensate innovators? Economic Policy, 22(52), 679–729.
Denicolo, V., & Franzoni, L. (2003). The contract theory of patents. International Review of Law and Economics, 23(4), 365–380.
Denicolo, V., & Franzoni, L. (2004). Patents, secrets, and the first-inventor defense. Journal of Economics and Management Strategy, 13(3), 517–538.
Denicolo, V., & Franzoni, L. (2008). Innovation, duplication, and the contract theory of patents. In R. Cellini & L. Lambertini (Eds.), The economics of innovation, Volume 286 of Contribution to economic analysis, Chapter 2 (pp. 15–32). Emerald Group Publishing Limited.
Denicolo, V., & Zanchettin, P. (2002). How should forward patent protection be provided? International Journal of Industrial Organization, 20(6), 801–827.
Dreyfuss, R. & Strandburg, K. (Eds.) (2011). The law and theory of trade secrecy: A handbook of contemporary research. Edward Elgar.
Epstein, R. (2003). Trade secrets as private property: Their constitutional protection. University of Chicago Law and Economics, Olin working paper (190).
Erkal, N. (2005). Optimal licensing in differentiated industries. Economic Record, 81(252), 51–60.
Friedman, D., Landes, W., & Posner, R. (1991). Some economics of trade secret law. The Journal of Economic Perspectives, 5(1), 61–72.
Gallini, N. (1984). Deterrence by market sharing: A strategic incentive for licensing. The American Economic Review, 74(5), 931–941.
Gallini, N. (1992). Patent policy and costly imitation. The Rand Journal of Economics, 23(1), 52–63.
Gallini, N., & Scotchmer, S. (2002). Intellectual property: When is it the best incentive system? In Innovation policy and the economy, Volume 2, pp. 51–78. MIT Press.
Garvey, J., & Baluch, A. (2007). Intellectual property: Patent or padlock: Patents and trade secrets form the heart of an effective IP strategy. BioPharm International, 20(2), 1–5.
Gilbert, R., & Newbery, D. (1982). Preemptive patenting and the persistence of monopoly. The American Economic Review, 72(3), 514–526.
Hall, B. (2007). Patents and patent policy. Oxford Review of Economic Policy, 23(4), 568–587.
Hall, B., Helmers, C., Rogers, M., & Sena, V. (2014). The choice between formal and informal intellectual property: A review. Journal of Economic Literature, 52(2), 375–423.
Horstmann, I., MacDonald, G., & Slivinski, A. (1985). Patents as information transfer mechanisms: To patent or (maybe) not to patent. Journal of Political Economy, 93(5), 837–858.
Hussinger, K. (2006). Is silence golden? Patents versus secrecy at the firm level. Economics of Innovation and New Technology, 15(8), 735–752.
Kamien, M. (1992). Patent licensing. In R. Aumann & S. Hart (Eds.), Handbook of Game Theory (Vol. 1, pp. 331–354). Elsevier.
Kamien, M., Oren, S., & Tauman, Y. (1992). Optimal licensing of cost-reducing innovation. Journal of Mathematical Economics, 21(5), 483–508.
Kamien, M., & Tauman, Y. (1984). The private value of a patent: A game theoretic analysis. Journal of Economics, 4, 93–118.
Kamien, M., & Tauman, Y. (1986). Fees versus royalties and the private value of a patent. The Quarterly Journal of Economics, 101(3), 471–491.
Kamien, M., Tauman, Y., & Zang, I. (1988). Optimal license fees for a new product. Mathematical Social Sciences, 16(1), 77–106.
Katz, M., & Shapiro, C. (1985). On the licensing of innovations. The Rand Journal of Economics, 16(4), 504–520.
Katz, M., & Shapiro, C. (1986). How to license intangible property. The Quarterly Journal of Economics, 101(3), 567–589.
Katz, M., & Shapiro, C. (1987). R and D rivalry with licensing or imitation. The American Economic Review, 77(3), 402–420.
Kreps, D. M., & Wilson, R. (1982). Sequential equilibria. Econometrica, 50(4), 863–894.
Kultti, K., Takalo, T., & Toikka, J. (2006). Simultaneous model of innovation, secrecy, and patent policy. The American Economic Review, 96(2), 82–86.
Kultti, K., Takalo, T., & Toikka, J. (2007). Secrecy versus patenting. The Rand Journal of Economics, 38(1), 22–42.
Layne-Farrar, A. (2016). Antitrust intellectual property and high tech handbook. Chapter The Economics of FRAND: University of Cambridge Press.
Layne-Farrar, A. (2014). Moving past the SEP FRAND obsession: Some thoughts on the economic implications of unilateral commitments and the complexities of patent licensing. George Mason Law Review, 21(4), 1093–1110.
Lemley, M., & Shapiro, C. (2005). Probabilistic patents. The Journal of Economic Perspectives, 19(2), 75–98.
Lemley, M., & Shapiro, C. (2007). Patent holdup and royalty stacking. Texas Law Review, 85(7), 1991–2049.
Lemley, M., & Shapiro, C. (2013). A simple approach to setting reasonable royalties for standard-essential patents. Berkeley Technology Law Journal, 28(2), 1135–1166.
Levin, R., Klevorick, A., Nelson, R., Winter, S., Gilbert, R., & Griliches, Z. (1987). Appropriating the returns from industrial research and development. Brookings Papers on Economic Activity, 1987(3), 783–831.
Mansfield, E., Schwartz, M., & Wagner, S. (1981). Imitation costs and patents: An empirical study. The Economic Journal, 91(364), 907–918.
Maurer, S., & Scotchmer, S. (2002). The independent invention defence in intellectual property. Economica, 69(276), 535–547.
Nash, J. (1950). Equilibrium points in n-person games. Proceedings of the National Academy of Sciences, 36(1), 48–49.
Ottoz, E., & Cugno, F. (2004). The independent invention defence in a Cournot duopoly model. Economics Bulletin, 12(5), 1–7.
Ottoz, E., & Cugno, F. (2011). Choosing the scope of trade secret law when secrets complement patents. International Review of Law and Economics, 31(4), 219–227.
Pakes, A. (1985). On patents, R &D, and the stock market rate of return. Journal of Political Economy, 93(2), 390–409.
Pakes, A. (1986). Patents as options: Some estimates of the value of holding European patent stocks. Econometrica, 54(4), 755–784.
Reinganum, J. (1983). Uncertain innovation and the persistence of monopoly. The American Economic Review, 73(4), 741–748.
Ritzberger, K. (2002). Foundations of non-cooperative game theory. Oxford University Press.
Rostoker, M. (1983). PTC research report: A survey of corporate licensing. Idea, 24(2), 59–92.
Scherer, F. (1967). Research and development resource allocation under rivalry. The Quarterly Journal of Economics, 81(3), 359–394.
Scherer, F. (1983). The propensity to patent. International Journal of Industrial Organization, 1(1), 107–128.
Schwartz, E. (2004). Patents and R &D as real options. Economic Notes, 33(1), 23–54.
Selten, R. (1975). Reexamination of the perfectness concept for equilibrium points in extensive games. International Journal of Game Theory, 4(1), 25–55.
Shapiro, C. (2006). Prior user rights. The American Economic Review, 96(2), 92–96.
Takalo, T. (1998). Innovation and imitation under imperfect patent protection. Journal of Economics, 67(3), 229–241.
Yeh, B. (2016). Protection of trade secrets: Overview of current law and legislation. Congressional Research Service Report (7-5700).
Acknowledgements
The author has no acknowledgements to state.
Funding
Open access funding provided by University of Gothenburg. The author has no relevant financial or non-financial interests to disclose.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Consent for publication
The author gives his consent for publication.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Appendix A: proof of the optimal licensing fees
To determine the optimal licensing fee under patent protection, I utilize the chain rule of differentiation. Specifically, the first order condition for the bargaining problem, as defined in Eq. 7, with respect to \(F_{p}\) is:
which can be reformulated as follows:
This expression can be further simplified to:
Solving this expression for the licensing fee yields \(F_{p}^{*}\), as defined in Eq. 8. Furthermore, due to the symmetric nature of the bargaining problem, the derivation for the optimal licensing fee under secrecy \(F_{s}^{*}\), follows a similar rationale, with the distinction being that the efficiency of the imitation technology and the protection lifetime correspond to a trade secret instead of a patent.
Appendix B: proof of the partial derivatives of the optimal licensing fees
It is important to note that when \(\alpha _{p}\) is sufficiently large to ensure that \(x \le 1\), and also that \(t_{p}<<T\), representing a common real-world bargaining problem, applying numerical analysis shows that \(\frac{\partial F_{p}^{*}}{\partial \beta } >0\). Because of the symmetric nature of the bargaining problem, these results are also consistent for the partial derivatives of the optimal licensing fee under secrecy, \(F_{s}^{*}\).
Appendix C: proofs of the partial derivatives of the patenting thresholds
Considering that the licensing threshold N is a specific case of M for \(\beta =0\), these results are also consistent for the partial derivatives of N.
Appendix D: leakage of the secret
Assume that accidental leakage occurs according to a Poisson distribution with a parameter \(\lambda >0\). As discussed in Section 4, the discounted-adjusted protection length of the trade secret in the existing analysis, defined in Eq. 1, is now \(\tilde{\delta }_{t_{1}}^{t_{2}}\) as defined in Eq. 18. If the transfer of the trade secret occurs, the profits of Firms 1 and 2 are given by:
If a technology transfer does not occur in the second stage of the game, then Firm 2 will opt for imitation, in which case the profits are given by:
It is immediate that \(\tilde{y}^{*}=\frac{1}{\alpha _{s}}\pi ^{d}\tilde{\delta }_{t_{s}}^{\infty }\) and the equilibrium licensing fee is:
As usual, a transfer of the secret occurs if \(\alpha _{s} \le \tilde{\alpha }_{s}\), where the threshold \(\tilde{\alpha }_{s}\) is defined as:
It is important to note that \(\partial \tilde{\alpha }_{s} / \partial \lambda <0\), implying that an increase in the probability of the accidental leakage, such as due to misappropriation or for a variety of other reasons, discourages transferring a trade secret. Additionally, \(\tilde{\alpha }_{s}<\hat{\alpha }_{s}\) suggests that acknowledging the risk of leakage increases the incentives to imitate. I can now determine the equilibrium outcomes of the game by comparing the two protection choices.
To begin with, suppose that \(\alpha _{p}\le \hat{\alpha }_{p}\) and \(\alpha _{s}\le \tilde{\alpha }_{s}\); in this case, a technology transfer always occurs. However, patenting occurs in equilibrium if the following condition holds:
Similar to the existing analysis in Sect. 4, this threshold also characterises the case when \(\alpha _{p} \le \hat{\alpha }_{p}\) and \(\alpha _{s}>\tilde{\alpha }_{s}\). Moreover, if \(\hat{\alpha }_{s}>\alpha _{s}>\tilde{\alpha }_{s}\), then only the risk of leakage would cause imitation (i.e., adapting the secret without the need for a licensing agreement).
Next, suppose that \(\alpha _{p} > \hat{\alpha }_{p}\) and \(\alpha _{s} >\tilde{\alpha }_{s}\), implying that a technology transfer is never optimal, regardless of the protection choice of Firm 1 in the first stage of the game. In this case, and also when \(\alpha _{p} > \hat{\alpha }_{p}\) and \(\alpha _{s} \le \tilde{\alpha }_{s}\), patenting is preferable in equilibrium if the following condition is satisfied:
It is evident that both patenting thresholds \(\tilde{M}\) and \(\tilde{N}\) are higher than the existing patenting thresholds M and N, respectively. This result indicates that a positive probability of leakage weakens the strength of trade secret protection, consequently reducing the incentives of firms to rely on secrecy. This, in turn, increases the attractiveness of patent protection.
In conclusion, consider a higher probability of accidental leakage denoted by \(\Lambda\), where \(\Lambda > \lambda\). For example, this is the probability of leakage when Firm 2 also possesses the trade secret through technology transfer or imitation. Assume that \(\Lambda\) is an increasing function of the number of firms n using the secret (that is, \(n \ge 1\)), which is equal to \(\lambda\) for \(n=1\). In this case, the discounted-adjusted protection length becomes:
Establishing the model with a probability of leakage independent of the number of firms using the new technology makes it evident that, only the analysis of secrecy protection runs into alternations. The key distinction in this scenario is that a duopoly profit implies that both firms practise the secret, corresponding to a high-risk leakage possibility (that is, a duopoly profit will now be discounted using \(\tilde{\tilde{\delta }}_{t_{1}}^{t_{2}}\)). This is in contrast to a monopoly profit, which corresponds to a low-risk leakage possibility (that is, a monopoly profit will be discounted using \(\tilde{\delta }_{t_{1}}^{t_{2}}\)). Following the same reasoning as above, it can be shown that both patenting thresholds are higher than the related thresholds corresponding to the case when the probability of leakage is independent of the number of firms using the secret (that is, \(\tilde{\tilde{M}}>\tilde{M}\) and \(\tilde{\tilde{N}}>\tilde{N}\)). This implies that a probability of leakage increasing with the number of firms using the secret weakens the firms’ incentives to rely on secrecy, thus increases their incentives to patent. Consequently, this might encourage imitation relatively more than technology licensing.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Mallios, A.K. Licensing and secrecy under imperfect intellectual property protection. Theory Decis (2024). https://doi.org/10.1007/s11238-024-09984-w
Accepted:
Published:
DOI: https://doi.org/10.1007/s11238-024-09984-w