Abstract
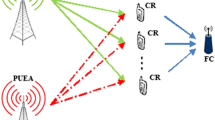
The nature of cognitive radio (CR) technology creates a lot of opportunities for attackers. When an attack occurs, the function of the primary network is affected and thus the overall system performance will be reduced. In the present paper, we introduce and simulate a novel method for identifying spectral sensing data falsification (SSDF) attack and recognizing the malicious users (MU), which we refer to as “Recognition and Elimination of SSDF Attackers”. Our proposed scheme uses the generalized likelihood ratio test (GLRT) approach for solving the MUs detection problem. In this method, we do not need previous information about the network and number of the MUs and secondary users (SUs). In addition to detecting the occurrence of an attack, our method can recognize attackers. By recognizing the MUs, their negative effect will be eliminated and the cognitive radio network (CRN) performance will return to normal condition. Consequently, our scheme can save resources by identifying the strategy of the known attackers. Simulation results reveal that our detection and recognition scheme is better than some of methods available.









Similar content being viewed by others
References
F. S. P. T. Force. (2002). Report of the spectrum efficiency working group. http://www.fcc.gov/sptf/files/SEWGFinalReport_1.pdf
Latif, S., Akraam, S., Karamat, T., Khan, M. A., Altrjman, C., Mey, S., & Nam, Y. (2022). An efficient pareto optimal resource allocation scheme in cognitive radio-based internet of things networks. Sensors, 22(2), 451.
Kakalou, I., Psannis, K. E., Krawiec, P., & Badea, R. (2017). Cognitive radio network and network service chaining toward 5G: Challenges and requirements. IEEE Communications Magazine, 55(11), 145–151.
Min, A. W., Kim, K.-H., & Shin, K. G. (2011). Robust cooperative sensing via state estimation in cognitive radio networks. In 2011 IEEE international symposium on dynamic spectrum access networks (DySPAN) (pp. 185–196). IEEE.
Wu, J., Song, T., Yu, Y., Wang, C., & Hu, J. (2018). Sequential cooperative spectrum sensing in the presence of dynamic byzantine attack for mobile networks. PloS One, 13(7), e0199546.
Axell, E., Leus, G., Larsson, E. G., & Poor, H. V. (2012). Spectrum sensing for cognitive radio: State-of-the-art and recent advances. IEEE Signal Processing Magazine, 29(3), 101–116.
Arora, N., & Mahajan, R. (2014). Cooperative spectrum sensing using hard decision fusion scheme. International Journal of Engineering Research and General Science, 2(4), 36–43.
Feng, J., Du, X., Zhang, G., & Shi, W. (2017). Securing multi-channel selection using distributed trust in cognitive radio ad hoc networks. Ad Hoc Networks, 61, 85–94.
Cheng, Z., Song, T., Zhang, J., Hu, J., Hu, Y., Shen, L., Li, X., & Wu, J. (2017). Self-organizing map-based scheme against probabilistic SSDF attack in cognitive radio networks. In 2017 9th International conference on wireless communications and signal processing (WCSP) (pp. 1–6). IEEE.
Muñoz, E. C., Rodriguez-Colina, E., Pedraza, L. F., & Paez, I. P. (2020). Detection of dynamic location primary user emulation on mobile cognitive radio networks using USRP. EURASIP Journal on Wireless Communications and Networking, 2020(1), 1–19.
Liagkou, V., Kavvadas, V., Chronopoulos, S. K., Tafiadis, D., Christofilakis, V., & Peppas, K. P. (2019). Attack detection for healthcare monitoring systems using mechanical learning in virtual private networks over optical transport layer architecture. Computation, 7(2), 24.
Sohu, I. A., Rahimoon, A. A., Junejo, A. A., Sohu, A. A., & Junejo, S. H. (2019). Analogous study of security threats in cognitive radio. In 2019 2nd International conference on computing, mathematics and engineering technologies (iCoMET) (pp. 1–4). IEEE.
Sheng, X., & Wang, S. (2021). Online primary user emulation attacks in cognitive radio networks using Thompson sampling. IEEE Transactions on Wireless Communications, 20(12), 8264–8273.
Ghaznavi, M., & Jamshidi, A. (2017). Defence against primary user emulation attack using statistical properties of the cognitive radio received power. IET Communications, 11(9), 1535–1542.
Sawant, S., Hanawal, M. K., Darak, S., & Kumar, R. (2018). Distributed learning algorithms for coordination in a cognitive network in presence of jammers. In 2018 16th International symposium on modeling and optimization in mobile, ad hoc, and wireless networks (WiOpt) (pp. 1–8) IEEE.
Chatterjee, P. S., & Roy, M. (2018). Lightweight cloned-node detection algorithm for efficiently handling SSDF attacks and facilitating secure spectrum allocation in CWSNs. IET Wireless Sensor Systems, 8(3), 121–128.
Zamanipour, M. (2022). Adversarial robustness in cognitive radio networks. arXiv preprint arXiv:2201.01842
Jaglan, R. R., Mustafa, R., & Agrawal, S. (2018). Scalable and robust ANN based cooperative spectrum sensing for cognitive radio networks. Wireless Personal Communications, 99(3), 1141–1157.
Fu, Y., & He, Z. (2019). Bayesian-inference-based sliding window trust model against probabilistic SSDF attack in cognitive radio networks. IEEE Systems Journal, 14(2), 1764–1775.
Ji, C., & Zhu, Q. (2021). Smart contract-based secure cooperative spectrum sensing algorithm. International Journal of Distributed Sensor Networks, 17(12), 15501477211058672.
Hu, Z., Bai, Y., Cao, L., Huang, M., & Xie, M. (2018). A sequential compressed spectrum sensing algorithm against SSDH attack in cognitive radio networks. Journal of Electrical and Computer Engineering, 2018, 4782718. https://doi.org/10.1155/2018/4782718
Wan, R., Ding, L., Xiong, N., & Zhou, X. (2019). Mitigation strategy against spectrum-sensing data falsification attack in cognitive radio sensor networks. International Journal of Distributed Sensor Networks, 15(9), 1550147719870645.
Tephillah, S., & Martin Leo Manickam, J. (2020). An SETM algorithm for combating SSDF attack in cognitive radio networks. Wireless Communications and Mobile Computing, 2020, 9047809. https://doi.org/10.1155/2020/9047809
Cheng, Z., Zhang, J., Song, T., Hu, J., & Bao, X. (2020). Detection strategy against restricted SSDF attack with potential interaction assistance. IEEE Transactions on Cognitive Communications and Networking, 7(2), 553–566.
Ghaznavi, M., & Jamshidi, A. (2019). A low complexity cluster based data fusion to defense against SSDF attack in cognitive radio networks. Computer Communications, 138, 106–114.
Zhao, F., Li, S., & Feng, J. (2019). Securing cooperative spectrum sensing against DC-SSDF attack using trust fluctuation clustering analysis in cognitive radio networks. Wireless Communications and Mobile Computing, 2019, 3174304. https://doi.org/10.1155/2019/3174304
Taggu, A., & Marchang, N. (2021). Detecting byzantine attacks in cognitive radio networks: A two-layered approach using hidden Markov model and machine learning. Pervasive and Mobile Computing, 77, 101461.
Zhu, H., Song, T., Wu, J., Li, X., & Hu, J. (2018) Cooperative spectrum sensing algorithm based on support vector machine against SSDF attack. In 2018 IEEE international conference on communications workshops (ICC workshops) (pp. 1–6). IEEE.
Sarmah, R., Taggu, A., & Marchang, N. (2020). Detecting Byzantine attack in cognitive radio networks using machine learning. Wireless Networks, 26(8), 5939–5950.
Chen, H., Zhou, M., Xie, L., & Li, J. (2017). Cooperative spectrum sensing with M-ary quantized data in cognitive radio networks under SSDF attacks. IEEE Transactions on Wireless Communications, 16(8), 5244–5257.
Ghaznavi, M., & Jamshidi, A. (2014). A reliable spectrum sensing method in the presence of malicious sensors in distributed cognitive radio network. IEEE Sensors Journal, 15(3), 1810–1816.
Lin, F., Hu, Z., Hou, S., Yu, J., Zhang, C., Guo, N., Wicks, M., Qiu, R. C., & Currie, K. (2011)Cognitive radio network as wireless sensor network (ii): Security consideration. In Proceedings of the 2011 IEEE national aerospace and electronics conference (NAECON) (pp. 324–328). IEEE.
Goldsmith, A. (2005). Wireless communications. Cambridge University Press.
Derakhtian, M., Tadaion, A., Gazor, S., & Nayebi, M. M. (2009). Invariant activity detection of a constant magnitude signal with unknown parameters in White Gaussian noise. IET Communications, 3(8), 1420–1431.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A
By giving \({\hat{X}}\), the pdf of observation signals under \(H_1^{1}\) can be written as follows:
By replacing \({\hat{X}}\) from Eq. (19) into Eq. (37) and simplifying, we have
Where \(P_G^ \bot \) is defined as follows:
We can derive the MLE of \(\varDelta _i\) by solving Eq. (40)
Equation (38) can be replaced into Eq. (40) and simplified as follows:
Equation (41) can be solved as follows:
By replacing Eq. (42) into Eq. (41) and simplifying, The \(\hat{\varDelta }_i\) can be obtained as:
Appendix B
By giving \(\hat{\varDelta }_i\), the pdf of observation signals under \(H_1^{1}\), can be written as follows:
Equation (44) can be simplified as follows:
By replacing Eq. (43) into Eq. (45) and simplifying, the pdf of observation signals under \(H_1^{1}\) can be written as follows:
The pdf of observation signals under \(H_0^{1}\) can be written as follows:
Similarly the pdf of observation signals under \(H_1^{1}\), Eq. (47) can be simplified as follows:
Rights and permissions
About this article
Cite this article
Zardosht, F., Derakhtian, M., Jamshidi, A. et al. Recognition and elimination of SSDF attackers in cognitive radio networks. Telecommun Syst 81, 53–66 (2022). https://doi.org/10.1007/s11235-022-00935-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-022-00935-w