Abstract
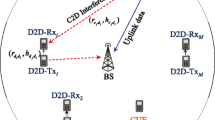
This paper studies the interference graph construction problem for device-to-device (D2D) communications underlaying cellular networks. Firstly, an improved interference graph construction method compared to the previous work in Zhang et al. (IEEE Trans Vehicular Technol 66(4):3293–3305, 2017) is proposed. The difference is mainly that, in this work the BS allocates resources for transmitting probe packets for links in a centralized manner; while in the previous work the links select resources for transmitting probe packets in a random and autonomous manner. With this “BS-allocation” method, the BS can obtain more useful information about the interference graph than the previous “random allocating” method. Secondly, this work proposes a new theoretical analysis metric, i.e., the missing rate; while previous work analyzed the traditional convergence time. This difference is caused by that this work considers the dynamic scenario in which cellular and D2D links arrive to and leave the cell dynamically, while the previous work considered the static scenario. When considering dynamic scenario, it is possible that the interference graph has changed before the BS completes the graph construction. Hence, we must evaluate the accuracy of the constructed interference graph, i.e., the missing rate, for dynamic scenario. Simulation results validate the theoretical analysis and show that the proposed method outperforms existing methods. The impact of parameters on the missing rate is also investigated.









Similar content being viewed by others
References
Alnoman, A., & Anpalagan, A. (2017). Towards the fulfillment of 5G network requirements: Technologies and challenges. Telecommunication Systems, 65(1), 101–116.
Jameel, F., Hamid, Z., Jabeen, F., Zeadally, S., & Javed, M. (2018). A survey of device-to-device communications: research issues and challenges. IEEE Communications Surveys & Tutorials, 20(3), 2133–2168.
Ali, S., & Ahmad, A. (2017). Resource allocation, interference management and mode selection in device-to-device communication: a survey. Transactions on Emerging Telecommunications Technologies, 28(7), 1–36.
Yu, C., Doppler, K., Ribeiro, C., & Tirkkonen, O. (2011). Resource sharing optimization for device-to-device communication underlaying cellular networks. IEEE Transactions on Wireless Communications, 10(8), 2752–2763.
Min, H., Lee, J., Park, S., & Hong, D. (2011). Capacity enhancement using an interference limited area for device-to-device uplink underlaying cellular networks. IEEE Transactions on Wireless Communications, 10(12), 3995–4000.
Lee, N., Lin, X., Andrews, J., & Heath, R. (2015). Power control for D2D underlaid cellular networks: Modeling, algorithms, and analysis. IEEE Journal on Selected Areas in Communications, 33(1), 1–13.
Banagar, M., Maham, B., Popovski, P., & Pantisano, F. (2016). Power distribution of device-to-device communications in underlaid cellular networks. IEEE Wireless Communications Letters, 5(2), 204–207.
Orakzai, F., Iqbal, M., Naeem, M., & Ahmad, A. (2018). Energy efficient joint radio resource management in D2D assisted cellular communication. Telecommunication Systems, 69(4), 505–517.
Abdallah, A., Mansour, M., & Chehab, A. (2018). Power control and channel allocation for D2D underlaid cellular networks. IEEE Transactions on Communications, 66(7), 3217–3234.
Sun, J., Zhang, Z., Xiao, H., & Xing, C. (2018). Uplink interference coordination management with power control for D2D underlaying cellular networks: Modeling, algorithms, and analysis. IEEE Transactions on Vehicular Technology, 67(9), 8582–8594.
Zhang, Z., Wu, Y., Chu, X., & Zhang, J. (2019). Resource allocation and power control for D2D communications to prolong the overall system survival time of mobile cells. IEEE Access, 7, 17111–17124.
Tanbourgi, R., Jakel, H., & Jondral, F. K. (2014). Cooperative interference cancellation using device-to-device communications. IEEE Communications Magazine, 52(6), 118–124.
Jayasinghe, K., Jayasinghe, P., Rajatheva, N., & Latva-aho, M. (2014). Linear precoder-decoder design of MIMO device-to-device communication underlaying cellular communication. IEEE Transactions on Communications, 62(12), 4304–4319.
Lin, X., Heath, R., & Andrews, J. (2015). The interplay between massive MIMO and underlaid D2D networking. IEEE Transactions on Wireless Communications, 14(6), 3337–3351.
Pratas, N., & Popovski, P. (2015). Zero-outage cellular downlink with fixed-rate D2D underlay. IEEE Transactions on Wireless Communications, 14(7), 3533–3543.
Ni, Y., Jin, S., Xu, W., Wang, Y., Matthaiou, M., & Zhu, H. (2016). Beamforming and interference cancellation for D2D communication underlaying cellular networks. IEEE Transactions on Communications, 64(2), 832–846.
Pan, Y., Pan, C., Yang, Z., & Chen, M. (2018). Resource allocation for D2D communications underlaying a NOMA-based cellular network. IEEE Wireless Communications Letters, 7(1), 130–133.
Wang, H., Zhao, B., & Zheng, T. (2019). Adaptive full-duplex jamming receiver for secure D2D links in random networks. IEEE Transactions on Communications, 67(2), 1254–1267.
Bjornson, E., Carvalho, E., Sorensen, J., Larsson, E., & Popovski, P. (2017). A random access protocol for pilot allocation in crowded massive MIMO systems. IEEE Transactions on Wireless Communications, 16(4), 2220–2234.
Han, H., Guo, X., & Li, Y. (2017). A high throughput pilot allocation for M2M communication in crowded massive MIMO systems. IEEE Transactions on Vehicular Technology, 66(10), 9572–9576.
Zhang, R., Cheng, X., Yang, L., & Jiao, B. (2015). Interference graph based resource allocation (InGRA) for D2D communications underlaying cellular networks. IEEE Transactions on Vehicular Technology, 64(8), 3844–3850.
Zhang, R., Cheng, X., Yang, L., & Jiao, B. (2013). Interference-aware graph based resource sharing for device-to-device communications underlaying cellular networks. In The 2013 IEEE wireless communications and networking conference (WCNC 2013). China: Shanghai.
Hoang, T., Le, L., & Le-Ngoc, T. (2016). Resource allocation for D2D communication underlaid cellular networks using graph-based approach. IEEE Transactions on Wireless Communications, 15(10), 7099–7113.
Uykan, Z., & Jantti, R. (2016). Transmission-order optimization for bidirectional device-to-device (D2D) communications underlaying cellular TDD networks: a graph theoretic approach. IEEE Journal on Selected Areas in Communications, 34(1), 1–14.
Gu, J., Bae, S., Hasan, S., & Chung, M. (2016). Heuristic algorithm for proportional fair scheduling in D2D-cellular systems. IEEE Transactions on Wireless Communications, 15(1), 769–780.
Ban, T., & Jung, B. (2016). On the link scheduling for cellular-aided device-to-device networks. IEEE Transactions on Vehicular Technology, 65(11), 9404–9409.
Kim, J., Caire, G., & Molisch, A. (2016). Quality-aware streaming and scheduling for device-to-device video delivery. IEEE/ACM Transactions on Networking, 24(4), 2319–2331.
Yang, T., Zhang, R., Cheng, X., & Yang, L. (2017). Graph coloring based resource sharing (GCRS) scheme for D2D communications underlaying full-duplex cellular networks. IEEE Transactions on Vehicular Technology, 66(8), 7506–7517.
Zhao, L., Wang, H., & Zhong, X. (2018). Interference graph based channel assignment algorithm for D2D cellular networks. IEEE Access, 6, 3270–3279.
Du, P., & Zhang, Y. (2016). Performance analysis of graph based scheduling for device-to-device communications overlaying cellular networks. Journal of Southeast University (English Edition), 32(3), 272–277.
Jain, K., Padhye, J., Padmanabhan, V., & Qiu, L. (2003). Impact of interference on multi-hop wireless network performance. In ACM MobiCom, pp. 66–80.
Chen, L., Low, S., Chiang, M., & Doyle, J. (2006). Cross-layer congestion control, routing and scheduling design in ad hoc wireless networks. In IEEE Infocom, pp. 1–13.
Zhang, R., Cheng, X., Yao, Q., Wang, C., Yang, Y., & Jiao, B. (2013). Interference graph-based resource-sharing schemes for vehicular networks. IEEE Transactions on Vehicular Technology, 62(8), 4028–4039.
Meng, Y., Li, J., Li, H., & Pan, M. (2015). A transformed conflict graph-based resource-allocation scheme combining interference alignment in OFDMA femtocell networks. IEEE Transactions on Vehicular Technology, 64(10), 4728–4737.
Du, Z., Wu, Q., Jiang, B., Xu, Y., & Qin, Z. (2018). Interference-aware spectrum access self-organization: a weighted graph game perspective. IEEE Systems Journal, 12(4), 3250–3259.
Zhang, R., Cheng, X., Cheng, X., & Yang, L. (2018). Interference-free graph based TDMA protocol for underwater acoustic sensor networks. IEEE Transactions on Vehicular Technology, 67(5), 4008–4019.
Zhou, X., Zhang, Z., Wang, G., Yu, X., Zhao, B., & Zheng, H. (2015). Practical conflict graphs in the wild. IEEE/ACM Transactions on Networking, 23(3), 824–835.
Niculescu, D. (2007). Interference map for 802.11 networks. In Proc. 7th ACM SIGCOMM conf. internet meas., pp. 339–350.
Ahmed, N., & Keshav, S. (2006). Smarta: a self-managing architecture for thin access points. In Proc. ACM CoNEXT conf., pp. 1–12.
Shrivastava, V., Rayanchu, S., Banerjee, S., & Papagiannaki, K. (2011). PIE in the sky: Online passive interference estimation for enterpriseWLANs. In Proc. 8th USENIX conf. netw. syst. des. implementation, pp. 337–350.
Yang, J., Draper, S., & Nowak, R. (2017). Learning the interference graph of a wireless network. IEEE Transactions on Signal and Information Processing Over Networks, 3(3), 631–646.
Haddadi, H., Rio, M., Iannaccone, G., Moore, A., & Mortier, R. (2008). Network topologies: Inference, modeling, and generation. IEEE Communications Surveys & Tutorials, 10(2), 48–69.
Sardellitti, S., Barbarossa, S., & Lorenzo, P. (2019). Graph topology inference based on sparsifying transform learning. IEEE Transactions on Signal Processing, 67(7), 1712–1727.
Bouchoucha, T., Chuah, C., & Ding, Z. (2019). Topology inference of unknown networks based on robust virtual coordinate systems. IEEE/ACM Transactions on Networking, 27(1), 405–418.
Zhang, Y., Zheng, J., Lu, P., & Sun, C. (2017). Interference graph construction for cellular D2D communications. IEEE Transactions on Vehicular Technology, 66(4), 3293–3305.
Wu, Z., Park, V., & Li, J. (2016). Enabling device to device broadcast for LTE cellular networks. IEEE Journal on Selected Areas in Communications, 34(1), 58–70.
Cai, X., Zheng, J., & Zhang, Y. (2015). A graph-coloring based resource allocation algorithm for D2D communication in cellular networks. In The 2015 IEEE international conference on communications (ICC 2015), London UK.
Acknowledgements
Y. Zhang would like to thank K. Lin for his input. This work was supported by the National Key Research and Development Program of China under Grant 2018YFB1800800. The author thanks reviewers for pointing out future research directions.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The author declares that there is no conflict of interests regarding the publication of this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Derivation of Eq. (6)
Assume the system is in the equilibrium state and recall that \(\mu _{{\mathrm{cell}}, h}\) denote the average number of cellular links of priority h at the beginning of each frame. For these cellular links, some leave the cell during the tth frame. Then the average number of cellular links of priority h during the tth frame can be written as \(\mu _{{\mathrm{cell}}, h} \cdot q_{{\mathrm{cell}}}\), where \(q_{{\mathrm{cell}}}\) is the probability that a cellular link does not leave during one frame. On the other hand, some new cellular links arrive during the tth frame. According to the method, all newly arriving cellular links are assigned priority \(H_{\max }\). Then the average number of cellular links of priority \(H_{\max }\) during the tth frame can be written as \(\mu _{{\mathrm{cell}}, H_{\max }} \cdot q_{{\mathrm{cell}}} + \Delta _{{\mathrm{cell}}}\). For convenience, let \(\tilde{\mu }_{{\mathrm{cell}}, h}\) denote
Then begins the FU allocation procedure as specified in Step 1a. For the proposed method, the BS sorts cellular links according to the priorities and selects the first \(2 N_{{\mathrm{cell}}}\) cellular links to which FUs are allocated. Then we know there exists a \(h_0\) so that for \(h_0 + 1 \le h \le H_{\max }\) all \({{\tilde{\mu }}}_{{\mathrm{cell}}, h}\) cellular links are selected and allocated while for \(0 \le h \le h_0 - 1\) no cellular link is selected and allocated. After FU allocation, the BS updates the priority according to the rule that, for cellular link which has been selected, its priority is cleared as 0; for cellular link which has not been selected, its priority is increased by 1 until reaching \(H_{\max }\). Therefore, we can know
Iteratively executing Eqs. (30) and (29), we can have
There is still \(\mu _{{\mathrm{cell}}, h_0 + 1}\) not determined. Actually, recalling that the average number of cellular links at the beginning of each frame is \(\mu _{{\mathrm{cell}}}\), we have \(\sum \nolimits _{h = 0}^{H_{\max } } {\mu _{{\mathrm{cell}},h} } = \mu _{{\mathrm{cell}}}\). Substituting Eq. (31), we can have
Finally, there still \(h_0\) not determined. We propose to determine the value of \(h_0\) as the solution to the following inequality
where x is an integer. Additionally, if \(2 N_{{\mathrm{cell}}} \ge \mu _{{\mathrm{cell}}}\), there is no solution to the above inequality and we simply have
Combining Eqs. (31) and (32), we can obtain the expression in Eq. (6).
Appendix B: Derivation of Eq. (14)
Let \(B_j\) denote the number of D2D neighbors of a D2D link j. It can be approximately calculated as
Therefore, we can approximately calculate
where \({\mathrm{E}}\left[ {\cdot } \right] \) represents the expectation of a random variable. It can be calculated that
where \(f_{r_j}(x)\) is the the probability distribution function of random variable \(r_j\). Assume all D2D links are uniformly distributed in the cell and then \(d_j\) is uniformly distributed from 0 to and \(d_{{\mathrm{max}}}\) where \(d_{{\mathrm{max}}}\) is the maximum distance of D2D links. Since \(r_j = w \cdot d_j\), we know \(r_j\) is uniformly distributed from 0 to and \(w \cdot d_{{\mathrm{max}}}\) and can write the probability distribution function of \(r_j\) as
Substituting this equality and we can have the expression in Eq. (14).
Appendix C: Other methods
1.1 The raw method
For this method, the following procedures are used to determine the three types of edges.
1.1.1 Type 1 edges
For fair comparison, we also use the same procedure of the proposed method as presented in Section III-A to determine Type 1 edges.
1.1.2 Type 2 and 3 edges
In each frame, each D2D transmitter randomly select a FU in \({{\mathbb {N}}}_{{\mathrm{D2D}}}\) to broadcast a message. The information carried by the message is the identification of the D2D link. Simultaneously, the receiver of each D2D or cellular link k monitors each FU in \({{\mathbb {N}}}_{{\mathrm{D2D}}}\) to see whether there are messages being transmitted by the transmitters of other D2D links. For each FU, if the message transmitted on this FU is correctly decoded, then the BS knows there is an edge from g to k, where g is the decoded D2D link identification.
1.2 The method in [45]
The method proposed in [45] is a “random allocating” method, in which the D2D links select resources for transmitting probe packets in a random and autonomous manner. The following procedures are used by this method to determine the three types of edges.
1.2.1 Type 1 edges
For Type 1 edges, we use the same procedure of the proposed method as presented in Section III-A. Here is the reason. The work in [45] focused on the D2D overlay case. Thus, Type 1 edge is not considered by the method in [45]. For fair comparison, we use the same procedure of the proposed method to determine Type 1 edges.
1.2.2 Type 2 and 3 edges
In each frame, each D2D transmitter randomly select a FU in \({{\mathbb {N}}}_{{\mathrm{D2D}}}\) to broadcast a message. The information carried by the message is the identification of the D2D link. Let \(n_j\) denote the FU selected by link j. Simultaneously, the BS monitors each FU in \({{\mathbb {N}}}_{{\mathrm{D2D}}}\) to see whether there are messages being transmitted by D2D links. For each FU, if the message transmitted on this FU is correctly decoded, the BS knows there is an edge from g to cellular links, where g is the decoded D2D link identification. The receiver of each D2D link l also monitors each FU in \({{\mathbb {N}}}_{{\mathrm{D2D}}}\). For each FU, there are two cases.
-
Case 1: the message transmitted on this FU is correctly decoded. Let g denote the decoded D2D link identification, which is reported to the BS. Then the BS knows there is an edge from g to l.
-
Case 2: a collision is detected on this FU. Let \(U_l\) denote the set of all such FUs observed by link l.
Then, the receiver of each D2D link l broadcasts a message on each FU in \(U_l\). The information carried by the message is also the identification of the D2D link. Simultaneously, transmitter of D2D link j monitors the FU \(n_j\) to see whether there are messages being transmitted by other D2D links. If the message transmitted on this FU is correctly decoded, then the BS knows there is an edge between g and j, where g is the decoded D2D link identification.
Rights and permissions
About this article
Cite this article
Zhang, Y. Interference graph construction for D2D underlaying cellular networks and missing rate analysis. Telecommun Syst 75, 383–399 (2020). https://doi.org/10.1007/s11235-020-00693-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-020-00693-7