Abstract
With the fast growth of technologies like cloud computing, big data, the Internet of Things, artificial intelligence, and cyber-physical systems, the demand for data security and privacy in communication networks is growing by the day. Patient and doctor connect securely through the Internet utilizing the Internet of medical devices in cloud-healthcare infrastructure (CHI). In addition, the doctor offers to patients online treatment. Unfortunately, hackers are gaining access to data at an alarming pace. In 2019, 41.4 million times, healthcare systems were compromised by attackers. In this context, we provide a secure and lightweight authentication scheme (RAPCHI) for CHI employing Internet of medical Things (IoMT) during pandemic based on cryptographic primitives. The suggested framework is more secure than existing frameworks and is resistant to a wide range of security threats. The paper also explains the random oracle model (ROM) and uses two alternative approaches to validate the formal security analysis of RAPCHI. Further, the paper shows that RAPCHI is safe against man-in-the-middle and reply attacks using the simulation programme AVISPA. In addition, the paper compares RAPCHI to related frameworks and discovers that it is relatively light in terms of computation and communication. These findings demonstrate that the proposed paradigm is suitable for use in real-world scenarios.
Similar content being viewed by others
1 Introduction
People choose an applicable medical system for high perfection of healthcare due to the quick growth of the Internet and its technology [1, 2]. Health centres provide medical services in remote regions in order to support the development of medical institutions and the medical sectors. The medical structure not only offers the necessary facilities, but it also improves medical care while maintaining the protection of patient data. Hospitals are working to develop their assistance so that patients may receive care that is easily accessible. When a patient enters the hospital, medical personnel immediately creates a medical report detailing their care in order to prevent mistakes. However, because this is not feasible everywhere, internet medical care has become a need in today’s world. Blood pressure, heart rate, body temperature, ECG, electromyography, and other physiological data are all measured by the medical equipment. The employment of wireless-assisted technology has removed the bulk of physical, geographical, and organisational barriers, removing the need to pass over medical papers and information to the relevant authorities [3]. Patients save information in the cloud for secure retrieval in a cloud-based telecare medical information system (TMIS) in medical management. Because it is well recognised that the cloud environment is not completely secure, a robust authentication structure should be implemented to handle security risks [4]. Both the patient and the doctor can share information over the cloud via TMIS. Following that the doctor gathers medical information from patients and uploads a diagnosis report to the cloud as if they had specifically participated. The medical report is a very important aim in TMIS to maintain security and privacy. In a CHI, it is not possible to acknowledge it openly. In terms of security and privacy, data transmitted between the cloud, the patient, and the doctor are a major concern that must be addressed in this system. The medical report falls under the heading of “essential information” and is vulnerable to theft. It might be a delicate decline in one’s life [5], and therefore, it is an important to provide a secure authentication framework so that an attacker cannot look into patients’ medical records [6].
IoMT, Internet of Things, Internet of Service, Artificial Intelligence, Cyber-Physical Systems (CPS), and Multi-access Edge-based Cloud Computing are some of the technical contexts in which CHIs operate. Due to many advantages of cloud computing platform in an IoMT driven smart healthcare system and extensive information processing, such as the requirement of mobility support, heterogeneity distributed architecture, and other factors, data security and privacy, authentication, and key agreement protocols in cloud environments are no longer secure in IoMT healthcare systems. A user’s data security, privacy, and physical control over the communication system are all compromised under this paradigm. Illegal data and data breath actions such as copy, deletion, alteration, and distribution can pose a number of security risks in these systems [7,8,9]. Data integrity, authenticity, secrecy, and other aspects of the cloud system may be affected by an attacker. As a result, it is a critical to develop a new solution against malicious attackers in order to build a safe and efficient environment.
Smart CHI is a technology that enables for the transfer of patient data across two or more sites. During COVID-19 pandemic, there are many users using many application of CHI. Hackers are obtaining access to data at an alarming pace. In 2019, healthcare systems were hacked 41.4 million times. In July 2020, 640,000 patient records were hacked at Florida Orthopedic Institute. In June 2020, Elite Emergency Physicians will have served 550,000 patients. It is necessary to preserve the data integrity of a patient in this system. CHI is playing an important role in medical user care for preserving the required physical distance during the ongoing COVID-19 epidemic. To safeguard sensitive patient data, integrity, secrecy, authentication, and key agreement methods are required in the current situation [10].
IoMT is a new field of CPS that aims to create a ubiquitous patient monitoring system. The majority of CHI’s demands are met by this technology. It also allows for more consistent and definite essential treatment before the patient’s health worsens. It is a cutting-edge technology approach for saving human lives by lowering the cost of medical treatment while removing the need for physical contact between the doctor and the patient. It has benefited medical users during COVID-19, according to [11]. The authentication and key agreement protocol in CHI is designed to manage security and privacy, including computation, data hiding, message authentication, mutual authentication, integrity, confidentiality, anonymity, non-repudiation, session key security communication, watermarking, and presume property rights, among other things [12]. A CHI system based on IoMT is expected to deal with algorithms that are computationally efficient, content authentication and key agreement that is safe, and so on.
1.1 Related work
In cloud-medical system, user should have particular access of medical information and privilege. They store data in cloud and TMIS can be classified into several applications to client constraints and organized classifications. A cloud-based approach for healthcare systems was proposed by Padhy et al. [13]. Banerjee et al. [14] proposed a cloud-based emergency healthcare system that retrieves the patient’s data centrally before any medical treatment begins. Li et al. [15] suggested a privacy-preserving strategy for TMIS employing a cloud environment in order to offer security, privacy, and medical resource access. Chatterjee et al. [16] proposed a secure biometric authentication protocol for TMIS with proper user authentication. In this protocol, authors had not discussed the user linkability and users relationship. Islam et al. [17] created a framework for user authentication and key agreement that is highly suited to modern information systems. Wazid et al. [18] proposed user authentication and session key agreement schemes with client anonymity for TMIS. It is suggested the patient’s healthcare record should be secure from malicious attacks. RSA-based safe authentication mechanism with user anonymity was proposed by Sutrala et al. [19]. They also used a verification tool to assure the security of the medical communication system. Chen et al. developed a cloud-based TMIS authentication technique [20] in 2014. In 2015, Amin et al. offered design and investigation authentication work for a healthcare system [21], He et al proposed robust authentication work for TMIS [22], and Zhou et al suggested a security-preserving cloud-supported wireless body area network approach [23]. Castiglione et al. developed a Software-as-a-Service (SaaS)-assisted cloud heterogeneous equipments communication system for TMIS resources used by clients [24]. Chiou et al. [25] exhibited Chen et al. framework [20] in 2016, claiming that it fails to provide actual telemedicine, communication authentication, or patient anonymity. Then, in a similar situation, Chiou et al. devised a modification technique. In 2017, Mohit et al. [26] challenged that Chiou et al.’s protocol cannot support in mobile stolen verifier attack and patient anonymity. In addition to, Mohit et al. suggested authentication work for healthcare system. Kumar et al. [6] and Li et al. [27] shown the drawbacks of Mohit et al. scheme. Most recently, Kumar et al. [28] reviewed Li et al. scheme and discussed demerits of [27]. In 2019, Chandrakar et al. [29] presented cloud-based authenticated protocol for healthcare monitoring system which is not secure against patient anonymity, data confidentiality, impersonation attack and patient password change. For wireless body area network, Chen and Peng proposed analysing and improving a mutual authentication and key agreement mechanism [30]. Chen et al. [31] presented an authorization mechanism for smart device usage in cloud environments in the year 2020. For RFID-based healthcare systems, Zhu et al. [32] proposed a lightweight authentication technique. Arunkumar and Kousalya [33] suggested a decentralised and safe lightweight E-health system based on blockchain technology. For TMIS, Amintoosi and Nikooghadam suggested an ECC-based authentication and key management mechanism that is probably safe [33]. In this protocol, they claimed that Khatoon et al.’s [34] scheme is vulnerable to known-session-specific temporary information attacks as well as perfect forward secrecy. Deebak and Turjman [35] proposed a protocol for CHI using IoMT. It does not contain patient password change phase, high computation and communication cost. Chen et al. [36] a RFID authentication protocol for epidemic prevention and epidemic emergency management systems. They claimed that the designed scheme can aid in the realisation of the safety and traceability of epidemic prevention materials, as well as improving the automation and decision-making efficiency of epidemic prevention. Hathaliy and Tanwar presented an exhaustive survey on security and privacy issues in Healthcare 4.0 [37]. The authors claim that different taxonomies used in Healthcare 4.0 to investigate various security and privacy issues are also presented in a structured manner. The benefits and drawbacks of various security and privacy techniques are then discussed. Awotunde et al. proposed the big data analytics of IoT-based cloud system framework: smart healthcare monitoring systems [38]. They discussed Raj et al. published a work entitle issues and challenges related to privacy and security in healthcare using IoT, Fog, and cloud computing [39]. According to them, the published paper also includes some methodology used in various research papers to address security and privacy issues in the IoT, fog, and cloud computing environments. Singh et al. [40] proposed IoT for sustaining a smart and secure healthcare system. The performance of work [40] is measured in terms of latency, network utilisation, RAM utilisation, and energy consumption. On the other hand, the suggested classifier’s accuracy, precision, specificity, sensitivity, and F1 score are all evaluated. The results show that the proposed framework and classifier consistently outperform conventional frameworks and classifiers.
1.2 Motivation and contribution
Because of their increasing utility, dependability, autonomy, efficiency, and safety, various scopes of CHI in IoMT are currently opening as research and technology advance. By allowing users to obtain programmes on demand, cloud computing is excellent at reducing infrastructure expenses. However, impersonation, stolen-verifier attacks, data non-repudiation, data confidentiality, anonymity, known-key security, replay attack, message authentication, privileged-insider attacks, parallel session, and man-in-the-middle attacks are all vulnerable to communication across entities in CHI. CHI’s security and privacy were breached by hackers during the COVID-19 epidemic. As a result, in a cloud-based CHI environment, information, security, and privacy are top priorities. In recent years, protocols [20, 25,26,27, 29, 35, 41] have been proposed in healthcare communication systems. However, these are insufficient to address the system’s fundamental security and privacy issues. As a result, many procedures have significant omissions. A secure and efficient structure is required to safeguard CHI’s security and privacy at all times. In this paper, the authors introduce a novel RAPCHI: Robust authentication protocol method for IoMT-based CHI to assure the security and privacy of CHI. The proposed RAPCHI has a number of important characteristics, which are listed below:
-
To ensure the security of CHI as an IoMT application, an authentication and key agreement are formed among the patient, cloud server, and doctor.
-
Without keeping data in a cloud database system, a session key is formed between patient and doctor.
-
Further, RAPCHI is also resistant to a variety of security threats and meets a number of security requirements.
-
Based on the random oracle concept, we give two independent formal security analyses of RAPCHI.
-
We use the AVISPA tool to simulate RAPCHI.
-
The comparison study shows that during a pandemic, RAPCHI is more effective than other protocols in the same context.
1.3 Threat model for RAPCHI
We consider the Dolev-Yao (DY) [42] in RAPCHI. Any opponent E has the following assumptions and capabilities:
-
The public network system is open to E. In the network system, he/she can create new messages, retrieve, inject, edit, replay, and discard any information.
-
Intruders or public users of the underlying network infrastructure can both be E.
-
E knows the public keys of all the users in public channel.
1.4 The paper organization
The remaining paper is constructed as follows. In Section 2, we express the preliminaries. In Section 3, we proposed RAPCHI framework for CHI. Section 4 describes security analysis. Section 5 describes performance analysis. Lastly, we discuss conclusion of the paper. Furthermore, we have given notations in Table 1.
2 Preliminaries
2.1 One-way collision-resistant hash function
Definition
Hash function converts arbitrary string length \(x \in \{0, 1\}^*\) in finite length string \(h(x) \in \{0, 1\}^l\). \(H_i\) is the hash function then, \(H_{i}:\{0, 1\}^* \rightarrow \{0, 1\}^l\).
The following properties of best hash function as below [6]:
-
If inputs x then output the digest h(x).
-
One-way If output \(y= h (x)\). Then, it is hard to compute x.
-
Weak-collision resistance If x is the input and \(h(x)=h(y)\) is the output. Finding y is then computationally impossible..
-
Strong-collision resistance If \(h (x)=h(y)\) is the output. Finding pair (x, y) with \(x \ne y\) then becomes computationally impossible.
It is a deterministic method that takes any string as input and returns a fixed-length string as output. Let \(Adv^{HASH}_{E}(t_{1})\) denote any E’s benefices in obtaining collision. Then, we have \(Adv^{HASH}_{E}(t_{1}) =Prob[(\varphi , \psi )\Leftarrow _{R} E: \varphi \ne \psi ~and ~h(\varphi )= h(\psi )]\), where Prob[W] represents the probability of a random appearance W, and \((\varphi , \psi )\Leftarrow _{R}\) E expresses the pair \((\varphi , \psi )\) is elected randomly by E. Here, E is made probabilistic, and the probability in advantage is calculated using any E with a computing time of \(t_1\). The h(.) is called collision-resistant, if \(Adv^{HASH}_{E}(t_{1})\le \epsilon _{1}\), for any adequately slight \(\epsilon _{1}>0\) [43].
2.2 Elliptic curve cryptography
Classically, cryptographic protocols are used to ensure the security and privacy of communicated data. An emerging trend for security and privacy, authors are using two cryptographic techniques 1) symmetric key cryptography and 2) public key cryptography. In this paper, we use the concepts of elliptic curve cryptography (ECC) which is the branch of public key cryptography. The basic information of ECC is explained as below:
Let q be the large prime then \(F_{q}\) be the prime finite field of order q. An equation of elliptic curve (EC) is given by \(v^2=u^3+cu+d ~~ mod~~ q\) with \(c, d \in F_{q}\). The elliptic curve is said to be non-singular if \(4c^3+27d^2~~ mod~~q \ne 0\). Then, G define as \(G=\{(u, v):u, v \in F_{q}; (u, v) \in \mathcal {E}\} \bigcup \{ \varTheta \}\), where the point \(\varTheta\) is known as the identity element of G. ECC contains the following properties:
-
1.
If \(X= (u, v) \in G\) then \(-X=(v, -v)\) and \(X+(-X)= \varTheta .\)
-
2.
If \(X= (u, v) \in G\) then scalar multiplication: \(kX=X+X+X.................+X~(k-times)\).
-
3.
If \(X= (u_{1}, v_{1})\), \(Y=(u_{2}, v_{2}) \in G\). Then, \(X+Y=(u_{3}, v_{3})\), where \(u_{3}=\mu ^{2}-u_{1}-u_{2}~ ~ mod ~~q\), \(v_{3}=(\mu (u_{1} - u_{3})-v_{1})~~ mod ~~q\) and
$$\begin{aligned} \mu = \left\{ \begin{array}{ll} \frac{v_{2}-v_{1}}{u_{2}-u_{1}}~~ mod~~ q &{} ~if X \ne Y \\ \\ \frac{3u^2_{1}+c}{2v_{1}}~~ mod~~ q &{} if ~ X=Y\\ \end{array}\right. \end{aligned}$$
For more information of elliptic curve group and its properties, we refer [44]. The comparison of key size in ECC, DSA, RSA, and Diffie–Hellman given in Table 2.
2.3 ECC-based computational hard problems
The following computational hard problems which are based on ECC:
-
Elliptic curve Discrete Logarithms problem (ECDLP) The detail of ECDLP discussed in [6].
Remark The symbol \(x \Leftarrow _{R} T\) to express value x is taken randomly from T.
Input: (R, S, r) for some \(k, r \in _{R} Z^*_{q}\).
Output Yes, if \(S=rR\), means that, \(k= r\), and result No, otherwise.
Assume the following two handling:
\(D_{real}=\{ x \Leftarrow _{R} Z^*_{q}, L= R, M= S= kR, N= k:(L, M, N)\}\).
\(D_{rand}= \{ k, r \Leftarrow _{R} Z^*_{q}, L= R, M= S= kR, N= r: (L, M, N)\}.\)
The benefits of any probabilistic, polynomial-time 0/1-listed recognizer \(\mathbb {D}\) in solving ECDLP on \(\mathcal {E}(F_q)\) is explained as \(Adv^{ECDLP}_{\mathbb {D}, \mathcal {E}}= |Prob[(L, M, N)\leftarrow D_{real}:\mathbb {D}(L, M, N)=1]-Prob[(L, M, N)\leftarrow D_{rand}:\mathbb {D}(L, M, N)=1]|\), where the probability Prob(.) is take on the random values k and r. \(\mathbb {D}\) is called a \((t_{2}, \epsilon _{2})\)- ECDLP recognizer for \(\mathcal {E}\), if \(\mathbb {D}\) executes at most in time \(t_{2}\) such that \(Adv^{ECDLP}_{\mathbb {D}, \mathcal {E}}(t_{2})\ge \epsilon _{ 2}\).
-
ECDLP assumption There exits no \(t_{2}\ge \epsilon _{ 2}\)-ECDLP recognizer for \(\mathcal {E}\). On the otherhand, for every probabilistic, polynomial-time 0/1- listed recognizer \(\mathbb {D}\), we have \(Adv^{ECDLP}_{\mathbb {D}, \mathcal {E}} (t_{2})< \epsilon _{ 2}\), for any sufficient small \(\epsilon _{ 2}>0\) [47].
-
Elliptic curve computational Diffie–Hellman problem (ECCDHP) The detail of ECCDHP discussed in [6].
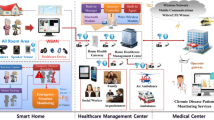
3 The RAPCHI framework
Figure 1 shows the proposed framework’s architecture.
There are four participants in CHI such as Patient, Doctor, Cloud server, and Body sensor RAPCHI framework having following phases:
3.1 Initialization
S selects security parameter l, the nonsingular elliptic curve \(\mathcal {E}(F_{q})\) over \(F_{q}\), elliptic curve additive group G with base point g, hash function \(h:\{0, 1\}^*\rightarrow Z^*_{q}\) and ECDLP which is intractable. S publishes public parameters \(\{F_{q}, \mathcal {E}(F_{q}), G, g, h(.), l\}\).
3.2 Patient registration in cloud server
With the help of medical device, P gets registration by S via secure channel as below:
- Step 1.:
-
To register with S, P inputs identity \(ID_{P}\) and password \(pw_{P}\). Then, P generates random value \(a_{P} \in Z^\star _{q}\) and selects as a secret key. Further, P executes \(PWP= pw_{P}\oplus h(pw_{P}\Vert ID_{P}\Vert a_{P})\) and \(P \Rightarrow S: M_{PR1}= \{ PWP, ID_{P}\}\).
- Step 2.:
-
On getting \(M_{PR1}\), S verifies \(ID_{P}\) and PWP in database. If, these are new, S computes \(A_{P}= h(h(ID_{P})\oplus h(PWP\Vert ID_{P}))\), generates random value \(b_{P} \in Z^\star _{q}\), computes \(P_1= h(ID_{P}\Vert A_{P}\Vert b_P)\), \(P_2= h(P_1\Vert ID_{P}\Vert A_P)\), \(B_{P}= h(ID_{P}\Vert s\Vert P_1\Vert A_P\Vert P_2)\), stores \(\{A_{P}, B_{P}, P_1, P_2, g, G\}\) in database and \(S \Rightarrow P: M_{RP2}= \{A_{P}, B_{P}, P_1, P_2,\) \(g, G\}\).
- Step 3.:
-
On collecting \(M_{RP2}\), P sets public key \(PK_{P}= a_{P}.g\) and stores parameters \(\{ A_{P}, B_{P}, P_1, P_2, g, G\}\) in database.
3.3 Doctor registration in cloud server
D gets registration via secure channel as below:
- Step 1.:
-
To register with S, D inputs identity \(ID_{D}\) and \(D \Rightarrow S: M_{RD1}= \{ID_{D}\}\).
- Step 2.:
-
On collecting \(\{ID_{D}\}\), S verifies \(ID_{D}\) in database. If, \(ID_D\) is new, S generates random number \(b_D \in Z^\star _{q}\), computes \(D_1=h(ID_D\Vert b_D)\), \(B_D= h(D_1\Vert s\Vert b_D)\), stores \(\{D_{1}, B_{D}, g, G\}\) in database and \(S \Rightarrow D: M_{RD2}= \{D_{1}, B_{D}, g, G\}\).
- Step 3.:
-
On getting \(M_{RD2}\), S generates \(a_D \in Z^\star _{q}\) and sets as a public key \(PK_{D}= a_{D}.g\). Further, D stores parameters \(\{D_{1}, B_{D}, g, G\}\) in database.
3.4 Patient login, authentication and key agreement phase
P uses the medical sensors device, forward regular medical record to S and get treatment by D via S. The process of this phase is explained as below:
- Step 1.:
-
P login with \(ID^\prime _{P}\) and \(pw^\prime _{P}\). Further, P computes \(PWP^\prime = pw^\prime _{P}\oplus h(pw^\prime _{P}\Vert ID^\prime _{P}\) \(\Vert a_{P})\), \(A^\prime _{P}= h(h(ID^\prime _{P})\oplus h(PWP^\prime \Vert ID^\prime _{P}))\) and verifies \(A^\prime _{P}\overset{?}{=} A_{P}\). After that P generates random number \(x \in Z^\star _{q}\), computes \(\alpha =x.g\), inserts medical data \(M_{P}=(ID_{P}, Data_{P})\), computes signature \(Sig_{P}= S_{SK_{P}}(h(M_{P}))\), computes \(H_{1}= h(ID_{P}\) \(\Vert PK_D\Vert (ID_{P}\oplus T_{1}))\), \(H_{2}= h(A_{P}\Vert B_D\Vert (ID_{P})\), encrypts \(E_{1}=E_{h(ID_P\Vert P_1\Vert P_2)}(H_{1},\) \(M_{P}, \alpha , Sig_{P}, T_1)\) by using key \(h(ID_P\Vert P_1\Vert P_2)\). Then, \(P \rightarrow S: M_{1}\)= \(\{E_{1}, H_{2}, T_{1}\}\).
- Step 2.:
-
On collecting \(M_1\), S verifies \(T_{2}- T_{1} \le \triangle T\) and \(H^*_{2}\overset{?}{=}h(P_{P}\Vert B_{P}\Vert ID_{D})\). Further, S computes \(ID_{P1}=ID_P \oplus h(ID_1\Vert ID_D\Vert B_D)\), \(H_3= h(ID_D\Vert B_D\Vert D_1\) \(\Vert T_{3})\), encrypts \(E_{2}=E_{h(ID_D\Vert B_D\Vert D_1)}( E_1, H_3, ID_{P1}, P_{1}, P_{2}, B_{P})\) by using key \(h(ID_D\Vert\) \(B_D\Vert D_1)\). Then, \(S \rightarrow D: M_{2}=\{ E_{2}, T_3\}\).
- Step 3.:
-
On getting \(M_{2}\), D verifies \(T_ {4}- T_{3} \le \triangle T\). Then, D decrypts \(( E_1, H_3, ID_{P1}, P_{1},\) \(P_{2}, B_{P})=D_{h(ID_D\Vert B_D\Vert D_1)}(E_2)\) by using key \(h(ID_D\Vert B_D\Vert\) \(D_1)\), verifies \(H^*_{3}\overset{?}{=} h(ID_D\Vert B_D\Vert D_1\Vert T_3)\), computes \(ID^*_P= ID_{P1} \oplus h(ID_1\Vert ID_D\Vert\) \(B_D)\), decrypts \((H_{1},\) \(M_{P}, \alpha , Sig_{P}, T_1)=D_{h(ID^*_P\Vert P_1\Vert P_2)}(E_1)\) by using key \((ID^*_P\Vert\) \(P_1\Vert P_2)\), verifies \(H^*_{1}\overset{?}{=} h(ID_{P}\Vert a_D.g\Vert (ID_{P}\oplus T_1))\) and \(V_{PK_{P}}(Sig_{P})\overset{?}{=} h(M_{P})\). Further, D generates medical report \(M_{D}= (ID_{D}, Data_{D})\), computes signature \(Sig_{D}= S_{SK_{D}}(h(M_{D}))\). Then, D generates random number \(y \in Z^\star _{q}\), computes \(\beta =y.g\), \(MAC_{D}= h(ID^*_{P}\Vert ID_{D}\) \(\Vert B_{P}\Vert B_{D}\Vert T_{5})\), session key \(SK_{DP}= h(ID^*_{P}\Vert ID_{D}\Vert Sig_{P}\Vert Sig_{D}\Vert MAC_{D}\Vert B_{D}\Vert B_{P}\) \(\Vert y.\alpha \Vert T_{5})\), \(ID_{D1}=ID_D\oplus h(Sig_P\Vert\) \(B_P\Vert H^*_1)\), encrypts \(E_{3}=E_{h(H^*_1\Vert B_P\Vert P_2)}( ID_{D1},\) \(MAC_{D}, Sig_{D}, M_{D}, B_D, \beta , T_5)\) by using key \(h(H^*_1\) \(\Vert B_P\Vert P_2)\) and \(D \rightarrow S: M_{3}=\{E_{3}, T_5\}\).
- Step 4.:
-
On collecting \(M_{3}\), S verifies \(T_{6}- T_{5} \le \triangle T\) and \(S \rightarrow P:M_{4}=\{E_{3}, T_5, T_7\}\).
- Step 5.:
-
Upon accepting \(M_{4}\), P verifies \(T_{8}- T_{7} \le \triangle T\). Then, P computes \(ID^*_{D}\) \(=ID_{D1}\oplus h(Sig_P\Vert B_P\Vert H_1)\), decrypts \(( ID_{D1}, MAC_{D}, Sig_{D}, M_{D}, B_{D},\beta , T_5)= D_{h(H_1\Vert B_P\Vert P_2)}(E_3)\) by using key \(h(H_1\Vert B_P\Vert P_2)\) and verifies \(V_{PK_{D}}(Sig_{D})\) \(\overset{?}{=} h(M_{D})\). Further, P computes \(MAC_{P}= h(ID_{P}\Vert ID^*_{D}\Vert B_{P}\Vert B_{D}\Vert T_{5})\) and verifies \(MAC_{P}\overset{?}{=} MAC_{D}\). Furthermore, P computes session key \(SK_{PD}= h(ID_{P}\Vert\) \(ID^*_{D}\Vert Sig_{P}\Vert Sig_{D}\) \(\Vert MAC_{P}\Vert B_{D}\Vert B_{P}\Vert x.\beta \Vert T_{5})\).
Thus, common session key between P and D is \(SK=SK_{PD}= SK_{PD}\). Hence, P gets treatment by authenticated D (Table 3).
3.5 Patient password change
The details of this phase is given as below:
- Step 1.:
-
P login with \(ID^\prime _{P}\) and \(pw^\prime _{P}\). P computes \(PWP^\prime =pw^\prime _P\oplus h(pw^\prime _{P}\) \(\Vert ID^\prime _{P}\Vert a_{P})\), \(A^\prime _{P}= h(h(ID^\prime _{P})\oplus h(PWP^\prime \Vert ID^\prime _{P}))\) and verifies whether holds \(A^\prime _{P}\overset{?}{=}A_{P}\) or not.
- Step 2.:
-
P verifies the validity of the condition \(A^\prime _{P}\overset{?}{=}A_{P}\). Then, P selects new password \(pw^{NEW}_{P}\). Further, P computes \(PWP^{NEW} = pw^{NEW}_P\oplus h(pw^{NEW}_{P}\Vert ID_{P}\Vert a_{P})\) and \(A^{NEW}_{P}= h(h(ID_{P})\oplus h(PWP^{NEW} \Vert ID_{P}))\) .
- Step 3.:
-
P replaces \(pw^{NEW}_P\) by \(pw_P\), \(PWP^{NEW}\) by PWP, and \(A^{NEW}_{P}\) by \(A _{P}\), respectively.
4 Security evaluation
In this session, we will look at RAPCHI’s security in the following ways:
4.1 Formal security analysis by method I
Here, we apply the formal method of security evaluation under the approach of ROM, we prove that RAPCHI is safe. We take the proof of this approach by the mechanism of contradiction as [48]. We apply same investigation as [49,50,51]. In RAPCHI, we implement this method under the generic group method of secure communication environment. Assume that there are two oracles for any E:
-
Reveal 1 Here, x is an arbitrary value, and \(y = h(x)\) is a fixed length value [52].
-
Reveal 2 Given \(X \in \mathcal {E}(F_q)\) and the public key \(Y =kX \in \mathcal {E}(F_q)\), this oracle will find as secret key k [52].

Theorem 1
Under ECDLP assumption, RAPCHI is safe against any E for determining \(ID_{P}\) and \(SK_{PD}\) between a patient and the doctor, if h(.) nearly acts such a random oracle.
Proof
Here, we want to compose E which has the capacity to determine both \(ID_{P}\) of P and \(SK_{PD}\) between P and D. Any E uses the random oracles Reveal 1 and Reveal 2 in order to test the algorithm, say \(EXP^{HASH, ECDLP}_{E, RAPCHI}\) prepared in Algorithm. For the proposed framework RAPCHI, define the success probability for \(EXP^{HASH, ECDLP}_{E, RAPCHI}\) as \(Succ= 2Prob[EXP^{HASH, ECDLP}_{E, RAPCHI}= 1]-1,\) where Prob[W] presents the probability on a game W. For the experiment, the benefit function becomes \(Adv(et, qR_{1}, qR_{2})= Max_{E}\{Succ\}\), where the maximal is seized overall E with queries \(qR_{1}\), \(qR_{2}\) done to Reveal 1 and Reveal 2 oracles and execution time et, respectively. RAPCHI is said to be provably safe against an E for determining \(ID_{P}\) and \(SK_{PD}\), if \(Adv(et, qR_{1}, qR_{2})< \epsilon\), for any adequately slight \(\epsilon >0\). As an experiment, if E has the capability to change h(.) and deals with ECDLP, she/he can simply determine both \(ID_{P}\) and \(SK_{PD}\) and achieve the game. However, by Subsect. 2.3, it is a findable computing unattainable issue to revert \(h(\Delta )\), means that, \(Adv^{HASH}_E(t_{1})\), for any adequately slight \(\epsilon > 0\). Also, in subsection 2.3, it is computationally unattainable to determine k from R and \(S = kR\) in \(\mathcal {E}(F_q)\), means that \(Adv^{ECDLP}_{\mathbb {D}, \mathcal {E}}(t_{2})< \epsilon _{ 2}\), for any sufficient slight \(\epsilon _{ 2}>0\). Hence, we contain \(Adv(et_{1}, qR_{1}, qR_{2})\le \epsilon\), as \(Adv(et_{1}, qR_{1}, qR_{2})\) depends into other advantages \(Adv^{HASH}_E\) \((t_{1})\) and \(Adv^{ECDLP}_{\mathbb {D}, \mathcal {E}}(t_{2})< \epsilon _{ 2}\). \(\square\)
Theorem 2
Under the assumption that h(.) nearly performs such an oracle, RAPCHI is provably safe against attacker E for acquire \(pw_P\) of a valid patient P, even if her/his registration phase is breakable.
Proof
This proof is also same as Theorem 1. We wish to make any E who will contain the capacity to rid the password \(pw_P\) of a valid P, even if her/his registration. By Threat model [42] and Sect. 2.1E can extract all information of P. Any E uses the Reveal oracle for Algorithm 2, say \(EXP2^{HASH}_{E, RAPCHI}\) for RAPCHI. The progressive probability for \(EXP2^{HASH}_{E, RAPCHI}\) as \(Succ2= 2Prob[EXP2^{HASH}_{E, RAPCHI}= 1]-1,\) and the experiment’s advantage \(Adv(et, qR_{1}, qR_{1})= Max_{E}\{Succ2\}\), where the maximal is seized overall E with the queries \(qR_{1}\), \(qR_{2}\) made to the Reveal 1 oracles and execution time \(et_1\), respectively. The RAPCHI is said to be provably safe against E for determining \(pw_{P}\), if \(Adv(et, qR_{1})< \epsilon _1\), for any adequately slight \(\epsilon >0\). As experiment 2, if E has the capability to change h(.) and achieve the game. However, by subsection 2.1, it is a possible for computing unattainable issue to invert \(h(\Delta )\), means that, \(Adv^{HASH}_E(t_{1})\), for any adequately slight \(\epsilon > 0\), means that \(Adv(et_{1}, qR_{1})\le \epsilon\), since \(Adv(et_{1}, qR_{1})\) depends on other advantages \(Adv^{HASH}_E(t_{1})\) \(< \epsilon _{ 1}\). \(\square\)

4.2 Formal security by method II
Here, we adopt the random oracle model II for RAPCHI from [53,54,55,56].
Theorem 3
The RAPCHI employees a group G under addition with a base point g of order q. According to the assumption of hash output digest of length l bit which performs an exact random oracle. Therefore, we have
For a probabilistic polynomial time-bounded technique,\(ADV^{RAPCHI}_{E,~succ}\) which is the probability of success. Any E is trying to hack the semantic security (SS) of RAPCHI and \(ADV^{ECCDHP}_{E,~succ}\) is denoted a chance of success for E to find the solution of the ECCDHP. The password dictionary is represented by \(\bigvee\), while the identity dictionary is represented by \(\bigwedge\) in this competition. Where \(q_{h}\) times H, \(q_{e}\) times Execute queries and \(q_{s}\) times Send queries for E to breach the communication of entities in RAPCHI.
Proof
We believe E is capable of cracking the RAPCHI mechanism. In addition, the ECCDHP may be used to find a polynomial time-bounded method \(\sum\) [57], i.e. from a random input (g, xg, yg), sum returns xyg within polynomial time bounds, where \(x, y \in Z^*_q\). Here, we consider a sequence of games \(G_{j} (0\le j \le 5)\) [55, 56], and in the simulation of the game \(G_j\), E can compute the exact attack against RAPCHI by computing \(G_0\), but E has no security. Further, we define the term game \(\eta _{j} (0\le j \le 5)\) where E defeats \(G_j\) in breaking into the RAPCHI’s communication system. Furthermore, we believe that the event \(\varPi\), which separates \(\eta _i\), may occur while E is being calculated, causing \(\sum\) to detect \(\varPi\). Unless \(\varPi\) is present, neither \(G_j\) nor \(G_{j+1}\) can be distinguished. As a result, we have
- \(G_{0}:\):
-
The execution of \(G_0\) is akin to the ROR model of a real-world security attack. As a result, in this oracle, all P and D outcomes are modelled as expected. When \(G_0\) is computed, E can guess which bit in the Test question is related to \(\tau\), which is the exact bit. Therefore, we have
$$\begin{aligned} ADV^{RAPCHI}_{E, succ}= ~\mid 2Pr [\eta _{0}]-1 \mid \end{aligned}$$(3) - \(G_{1}:\):
-
Here, \(G_{1}\) is similar to \(G_{0}\) without the hash oracle H is calculated by E by maintaining a list \(L^P_{H}\), which runs the (Hin, Hout). If E inputs \(Hin_{NEW}, \sum\) and find output \(Hout_{NEW}\). Then, a new list of tuple \(( Hin_{NEW},\) \(Hout_{NEW})\) in \(L^P_{H}\). Otherwise, \(\sum\) randomly prefers a number \(Hout_{NEW} \in F^\star _{q}\), returns to E and considers new tuples \(( Hin_{NEW}, Hout_{NEW})\) in \(L^P_{H}\). Here, Execute, Send, Corrupt, Reveal, and \(Test-queries\) are polished in the same way that genuine attacks are calculated. So that’s it.
$$\begin{aligned} Pr[\eta _{1}] = Pr [\eta _{0}] \end{aligned}$$(4) - \(G_{2}:\):
-
In this contest, \(G_{2}\) is similar to except if a collision occurs during the simulation of the values, \(G_1\) will be exited \(M_{1}= \{E_{1}, H_{}, T_1\}, M_{2}= \{E_{2}, T_{3}\},\) \(M_{3}= \{E_{3}, T_{5}\}\) and \(M_{2}= \{E_{3}, T_{5}, T_7\}\) which are based on the birthday attack. Probability of collisions of the simulated hash oracle is at most \(\frac{q^2_{h}}{2q}\). In the contents simulation, the possibility of collisions is \(\frac{(q_{s}+q_{e})^2}{2^{l+1}}\) . Thus, we have
$$\begin{aligned} \mid Pr [\eta _{2}] - Pr [\eta _{1}]\mid \le \frac{q^2_{h}}{2q}+ \frac{(q_{s}+q_{e})^2}{2^{l+1}} \end{aligned}$$(5) - \(G_{3}:\):
-
Here, suppose E is guessed attributes \(Sig_{P}, H_{1}, H_{2}\) without hash query. Further, \(G_{3}\) is similar to \(G_{2}\) with P and S occurrence refuses authenticated numbers. Thus, we have
$$\begin{aligned} \mid Pr [\eta _{3}] - Pr [\eta _{2}] \mid \le \frac{q_{s}}{2^l} \end{aligned}$$(6) - \(G_{4}:\):
-
In this contest, E accurately guessed attributes \(H^*_2, H_3, ID_{P1}\) without hash query. Further, \(G_{4}\) is similar to \(G_{3}\) with S and D occurrence refuses authenticated values. Thus, we have
$$\begin{aligned} \mid Pr [\eta _{4}] - Pr [\eta _{3}] \mid \le \frac{q_{s}}{2^l} \end{aligned}$$(7) - \(G_{5}:\):
-
In this game, E accurately guessed the authenticated attributes \(H^*_{3}, ID^*_{P}, H^*_{1}, V_{PK_{P}}(\) \(Sig_{P}), Sig_{D}= S_{SK_{D}}(h(M_{D})), MAC_{D}, SK_{DP}, ID_{D1}, MAC_{D}\) without hash query. Further, \(G_{5}\) is similar to \(G_{4}\) with S and D occurrence refuses authenticated values. Thus, we have
$$\begin{aligned} \mid Pr [\eta _{5}] - Pr [\eta _{4}] \mid \le \frac{q_{s}}{2^l} \end{aligned}$$(8) - \(G_{6}:\):
-
In this event, E accurately guessed attributes \(E_{3}, T_5, T_7\) without hash query. Further, \(G_{6}\) is similar to \(G_{5}\) with S and P occurrence refuses a legitimated values. Thus, we have
$$\begin{aligned} \mid Pr [\eta _{6}] - Pr [\eta _{5}] \mid \le \frac{q_{s}}{2^l} \end{aligned}$$(9) - \(G_{7}:\):
-
In this game, E is session key \(SK_{U}= SK_{S}= SK\) with find the values xyg. As a result, when using the ECCDHP’s random self-reducibility, \(G_6\) and \(G_6\) are comparable in execution. Thus E applied queries with random values (g, xg, yg) to compute \(ECCDHP(xg, yg) = xyg\), where \(x, y \in Z^\star _{q}\) .Therefore, we have
$$\begin{aligned} \mid Pr [\eta _{7}] - Pr [\eta _{6}]\mid \le q_{h} ADV^{ECCDHP}_{E,~ succ}(q) \end{aligned}$$(10) - \(G_{8}:\):
-
This game is identical to the previous game except for the addition of a \(Test-query\). If E asks a \(H-query\) with information \(\{ID_{P}, ID^*_{D}, Sig_{P}, Sig_{D}, MAC_{P}, B_{D}, B_{P}, x,\) \(\beta , T_{5}\}\), the game will end. By running the \(H-query\) with a probability at most \(\frac{q^2_{h}}{2l}\), E can obtain the session key \(SK=SK_U= SK_S\). Thus, we have
$$\begin{aligned} \mid Pr [\eta _{9}] - Pr [\eta _{8}]\mid \le \frac{q^2_{h}}{2q} \end{aligned}$$(11)
If E will not get a session key without perfect input which contains different parameters, thus \(Prob [\eta _{9}]= \frac{1}{2}\). Furthermore, it specifies that the password \(Corrupt-query(Corrupt(U, 1))\) has not been made in [53] if the Corrupt(U, 2)query has been made. The probability of applying off-line password guessing attack and identity guessing attacks are \(\frac{q_{s}}{\bigvee }\) and \(\frac{q_{s}}{\bigwedge }\) by E. Thus, from equations \((3) - (11)\), we obtained
Hence, the theorem is established. \(\square\)
4.3 Informal security analysis
The following security aspects and properties are discussed in this session for RAPCHI analysis:
4.3.1 Patient anonymity
We express P anonymity in RAPCHI which is given as below:
-
S computes P’ partial identity \(ID_{P1}=ID_P \oplus h(ID_1\Vert ID_D\Vert B_D)\), encrypts \(ID_{P1}\) by \(E_{2}=E_{h(ID_D\Vert B_D\Vert D_1)}( E_1, H_3,\) \(ID_{P1}, P_{1}, P_{2}, B_{P})\) with using key (h( \(ID_D\Vert B_D\Vert\) \(D_1)\) and sends to D. Further, D decrypts \(( E_1, H_3, ID_{P1}, P_{1}, P_{2},\) \(B_{P})=D_{h(ID_D\Vert B_D\Vert T_2)}\) \((E_2)\) using key \(h(ID_D\Vert B_D\Vert D_1)\) and computes anonymous identity of P as \(ID^*_{P}=ID_{P1} \oplus h(ID_1\Vert ID_D\Vert B_D)\). Furthermore, D uses \(ID^*_P\) in authentication phase of RAPCHI.
Thus, our protocol provides P anonymity.
4.3.2 Doctor anonymity
We describe D anonymity in RAPCHI as below:
-
D computes his/her partial identity \(ID_{D1}=ID_D\oplus h(Sig_P\Vert B_P\Vert H^*_1)\) and sends to P. Further, P computes D’s anonymous identity as \(ID^*_{D}=ID_{D1}\oplus h(Sig_P\Vert B_P\Vert H^*_1)\) and uses \(ID^*_P\) in RAPCHI.
Thus, our protocol provides D anonymity.
4.3.3 Man-in-the-middle attack
In RAPCHI, each step of authentication phase having time-stamp status \(T_{i}- T_{j} \le \triangle T\) and hash conditions \(H^*_{i}\overset{?}{=}H_{i}\). If possible, any E enters in authentication and key agreement phase after checks \(T_{i}- T_{j} \le \triangle T\) then, verifies \(H^\prime _{i}\overset{?}{=}H_{j}\). This condition is not achievable to verify by the definition of hash function which is secure. Further, E cannot verify P’s signature \(V_{PK_{P}}(Sig_{P})\overset{?}{=} h(M_{P})\) and D’s signature \(V_{PK_{D}}(Sig_{D})\overset{?}{=} h(M_{D})\). Thus, E will unsuccessful in authentication and key agreement phase. Therefore, RAPCHI secures against this attack.
4.3.4 Replay attack
Every time we utilise the time-stamp condition \(T_{i}- T_{j} \le \triangle T\) in RAPCHI, we use random values as a counter-measure. In RAPCHI, the valid time length is \(\triangle T\). Furthermore, the hash value, encryption, decryption, various keys, and session keys are all computed using the current time value and a random number. It is well known that in a network system, an ECC-based one-way hash function is secure. Hence, the replay attack is not possible in RAPCHI.
4.3.5 Known-key security property
The session keys are expressed in the following way by RAPCHI:
-
P executes session key \(SK_{PD}= h(ID_{P}\Vert ID^*_{D}\Vert Sig_{P}\Vert Sig_{D}\Vert MAC_{P}\Vert B_{D}\Vert B_{P}\Vert\) \(x.\beta \Vert T_{5})\).
-
D executes session key \(SK_{DP}= h(ID^*_{P}\Vert ID_{D}\Vert Sig_{P}\Vert Sig_{D}\Vert MAC_{D}\Vert B_{D}\Vert B_{P}\Vert\) \(y.\alpha \Vert T_{5})\).
RAPCHI presents session key in communication system. Even if E finds the past key, she/he cannot execute it. Thus, RAPCHI maintains this property.
4.3.6 Data confidentiality
It is a way to send secure data in communication system without E. In RAPCHI, the following are the details of encryption and description:
-
P encrypts \(E_{1}=E_{h(ID_P\Vert P_1\Vert P_2)}(H_{1}, M_{P}, \alpha , Sig_{P}, T_1)\) by using key \(h(ID_P\Vert\) \(P_1\Vert P_2)\) and uploads to S. Further, S encrypts \(E_{2}=E_{h(ID_D\Vert B_D\Vert D_1)}( E_1, H_3,\) \(ID_{P1}, P_{1}, P_{2},\) \(B_{P})\) by using key \(h(ID_D\Vert B_D\Vert D_1)\) and forwards to D. After that, D decrypts \(( E_1, H_3,\) \(ID_{P1},\) \(P_{1}, P_{2}, B_{P})=D_{h(ID_D\Vert B_D\Vert D_1)}(E_2)\) by using key \(h(ID_D\Vert B_D\Vert D_1)\) and \((H_{1}, M_{P}, \alpha ,\) \(Sig_{P}, T_1)=D_{h(ID^*_P\Vert P_1\Vert P_2)}(E_1)\) by using key \(ID^*_P\Vert P_1\Vert P_2)\). Furthermore, D encrypts \(E_{3}=E_{h(H^*_1\Vert B_P\Vert P_2)}( ID_{D1}, MAC_{D}, Sig_{D},\) \(M_{D}, B_D, \beta , T_5)\) by using key \(h(H^*_1\Vert B_P\Vert P_2)\) and uploads to S. In addition to, S sends \(E_{3}\) to P. Then, P decrypts \(( ID_{D1}, MAC_{D},\) \(Sig_{D}, M_{D}, B_{D}, \beta , T_5)= D_{h(H_1\Vert B_P\Vert P_2)}(E_3)\) by using key \(h(H_1\Vert\) \(B_P\Vert P_2)\).
Thus, if E tries to find communicated message at the time of communication, E encrypts information which cannot be decrypted without the hash value and generated key. By the definition of hash function, it assumed to be secure and one way. So that, it is hard to compute generated key and hash value. Therefore, RAPCHI maintains the confidentiality.
4.3.7 Data non-repudiation
The details of this attribute in RAPCHI are given as:
-
P makes digital signature \(Sig_{P}= S_{SK_{P}}(h(M_{P}))\) and verifies D’s digital signature \(V_{PK_{D}}(Sig_{D})\overset{?}{=} h(M_{D})\).
-
D verifies P’s digital signature by \(V_{PK_{D}}(Sig_{P})\overset{?}{=} h(M_{P})\). After that, D makes digital signature \(Sig_{D}\) \(= S_{SK_{D}}(h(M_{D}))\).
Thus, P checks the health information. If, the medical information is incorrect, the authenticated party cannot be denied. The non-repudiation arguments are saved in S. Therefore, RAPCHI protests data non-repudiation.
4.3.8 Message authentication
The details of it describe in RAPCHI as below:
-
S gets \(M_{2}\), verifies \(T_ {2}- T_{1} \le \triangle T\) and hash function \(H^*_{2}\overset{?}{=}h(P_{P}\Vert B_{P}\Vert\) \(ID_{D})\). Similarly, S accepts message \(M_{3}\) and checks the validity by confirming times-stamps condition \(T_{6}- T_{5} \le \triangle T\).
-
D receives message \(M_{2}\), verifies \(T_ {4}- T_{3} \le \triangle T\), \(H^*_{3}\overset{?}{=} h(ID_D\Vert B_D\Vert D_1\Vert T_3)\), \(H^*_{1}\overset{?}{=} h(ID_{P}\Vert a_D.g\Vert (ID_{P}\oplus T_1))\) and \(V_{PK_{P}}(Sig_{P})\overset{?}{=} h(M_{P})\).
-
P receives message \(M_{4}\), checks \(T_{8}- T_{7} \le \triangle T\), \(V_{PK_{D}}(Sig_{D})\overset{?}{=} h(M_{D})\) and \(MAC_{P}\overset{?}{=} MAC_{D}\).
If any E endeavours change any charge in data of P, S and D will recognize it. Therefore, RAPCHI protests against the message authentication attack.
4.3.9 Impersonation attack
The details of an impersonation attack describe in RAPCHI as below:
-
Any E attempts to masquerade as an authenticated P and tries to compute \(Sig_{P}= S_{SK_{P}}(h(M_{P}))\), \(H_{1}= h(ID_{P}\Vert PK_D\Vert (\) \(ID_{P}\oplus T_{1}))\), \(H_{2}= h(A_{P}\Vert B_D\Vert ID_{P})\), encrypts \(E_{1}=E_{h(ID_P\Vert P_1\Vert P_2)}(H_{1}, M_{P}, \alpha , Sig_{P}, T_1)\) by using key \(h(ID_P\) \(\Vert\) \(P_1\Vert P_2)\). Then, P sends \(M_{1}\)= \(\{E_{1}, H_{2}, T_{1}\}\) to S . E cannot compute \(Sig_{P}, H_{1}\), \(H_{2}\), and \(h(ID_P\) \(\Vert P_1\Vert P_2)\) by the definition explanation of hash function and digital signature. Thus, E cannot impersonate as authenticated P.
-
Any E attempts to masquerade as an authenticated D. On getting \(M_{2}\), D decrypts \(( E_1, H_3, ID_{P1}, P_{1}, P_{2}, B_{P})\) \(=D_{h(ID_D\Vert B_D\Vert D_1)}(E_2)\) by using key \(h(ID_D\Vert\) \(B_D\Vert D_1)\), computes \(ID^*_P= ID_{P1} \oplus h(ID_1\Vert ID_D\Vert B_D)\), decrypts \((H_{1}, M_{P}, \alpha ,\) \(Sig_{P}, T_1)=D_{h(ID^*_P\Vert P_1\Vert P_2)}(E_1)\) by using key \(ID^*_P\Vert P_1\Vert P_2)\). Further, D generates medical report \(M_{D}= (ID_{D}, Data_{D})\), computes signature \(Sig_{D}= S_{SK_{D}}(h\) \((M_{D}))\). Then, D generates random value \(y \in Z^\star _{q}\), computes \(\beta =y.g\), \(MAC_{D}\) \(= h(ID^*_{P}\Vert ID_{D}\Vert B_{P}\Vert B_{D}\Vert T_{5})\), session key \(SK_{DP}= h(ID^*_{P}\Vert ID_{D}\Vert Sig_{P}\Vert Sig_{D}\Vert\) \(MAC_{D}\Vert B_{D}\Vert B_{P}\Vert y.\alpha \Vert T_{5})\), \(ID_{D1}\) \(=h(Sig_P\Vert\) \(B_P\Vert H^*_1)\), encrypts \(E_{3}=E_{h(H^*_1\Vert B_P\Vert P_2)}( ID_{D1},\) \(MAC_{D}, Sig_{D}, M_{D}, B_D,\) \(\beta , T_5)\) by using key \(h(H^*_1\Vert B_P\Vert P_2)\) and D sends \(M_{3}=\{E_{3}, T_5\}\) to S. E cannot compute these parameters as discussed above. Thus, E cannot impersonate as an authenticated D.
-
Any adversary E attempts to masquerade as an authenticate S and eavesdrop the transmitted \(M_{2}\) and \(M_{4}\). Further, S \(ID_{P1}=ID_P \oplus h(ID_1\Vert ID_D\Vert B_D)\), \(H_3= h(ID_D\Vert B_D\) \(\Vert D_1\Vert T_{3})\), encrypts \(E_{2}=E_{h(ID_D\Vert B_D\Vert D_1)}( E_1, H_3,\) \(ID_{P1},\) \(P_{1}, P_{2}, B_{P})\) by using key \(h(ID_D\Vert B_D\Vert D_1)\). E cannot compute these parameters as discussed above. Thus E cannot impersonate as authenticated S.
Hence, RAPCHI is secured against this attack.
4.3.10 Session key security
RAPCHI contains two session keys which are computed between P and D. The details of session key are shown in RAPCHI as below:
-
D computes \(SK_{DP}= h(ID^*_{P}\Vert ID_{D}\Vert Sig_{P}\Vert Sig_{D}\) \(\Vert MAC_{D}\Vert B_{D}\Vert B_{P}\Vert y.\alpha \Vert T_{5})\) and P computes \(SK_{PD}= h(ID_{P}\Vert ID^*_{D}\) \(\Vert Sig_{P}\Vert Sig_{D}\Vert MAC_{P}\Vert B_{D}\Vert B_{P}\Vert x.\beta \Vert T_{5})\). E cannot execute \(SK_{DP}\) or \(SK_{PD}\), where \(MAC_{P}= MAC_D\). With the help of impersonation attack, \(MAC_{D}\) and \(MAC_{P}\) cannot be executed by E. Furthermore, for given \((g, \alpha , \beta )\), it is impossible for an attacker G to compute xyg using ECCDHP in ECC for \(x, y \in Z^*_q\) and g is the base point of G. As a result, the authenticated participant is the only one who can build SK.
Hence, RAPCHI could defend the session key.
5 Simulation study using AVISPA tool
AVISPA is a tool for evaluating the proposed protocols’ security against passive/active attacks, man-in-the-middle attacks, and reply assaults. AVISPA’s back-end servers, such as the On-the-Fly Modeler (OFMC), constraint-Logic (Cl-AtSe) attacker search, SAT-based Model-Checker (SATMC), and Tree Automata based on Automatic Approximations for the evaluation of security protocols, include an integrated automated validation security analysis (TA4SP) [45, 58]. It can examine the capability of the RAPCHI under security attacks. As a result, we decided to investigate RAPCHI’s security and confidentiality against active and passive attacks. The analysis results are depicted in Fig. 2. RAPCHI is secure in communication channel. AVISPA’s outcome is that one of the four back-ends is used: CL-AtSe, OFMC, TA4SP and SATMC. The results reveal that the private parameters between P and D are kept secret. It also protects against both passive and active attacks. In the execution of RAPCHI, the parameters cannot be determined by E in public channel.
It is worth noting that we did not use the TA4SP and SATMC simulation results because they do not support running bitwise XOR (\(\oplus\)) operations.
6 Performance analysis
In this part, we compare RAPCHI’s security and functionality aspects, as well as communication and computation costs, to other frameworks such Mohit et al.[26], Chen et al.[20], Li et al.[27], Chen et al. [41], Chiou et al. [25], Chandrakar et al. [29] and Deebak and Turjman [35]. The details of this phase following as:
6.1 Comparison of the security and functionality attributes
In Table 4, we compare security and functionality attributes of RAPCHI with related frameworks below as:
-
Chen et al.’s protocol [20] fails against \(\varGamma 2\), \(\varGamma 3\), \(\varGamma 5\), \(\varGamma 10\), \(\varGamma 12\), \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Mohit et al.’s protocol [26] fails against \(\varGamma 2\), \(\varGamma 3\), \(\varGamma 5\), \(\varGamma 9\),\(\varGamma 11\), \(\varGamma 12\) \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Chen et al’s. protocol [41] fails against \(\varGamma 2\), \(\varGamma 3\), \(\varGamma 8\), \(\varGamma 9\), \(\varGamma 11\), \(\varGamma 12\), \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Li et al.’s protocol [27] fails \(\varGamma 2\), \(\varGamma 3\), \(\varGamma 8\), \(\varGamma 9\), \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Chiou et al.’s protocol [25] fails against \(\varGamma 2\), \(\varGamma 3\), \(\varGamma 5\), \(\varGamma 9\),\(\varGamma 11\), \(\varGamma 12\), \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Chandrakar et al.’s protocols [29] fails against \(\varGamma 2\), \(\varGamma 6\), \(\varGamma 9\), \(\varGamma 13\), \(\varGamma 14\), \(\varGamma 15\) and \(\varGamma 16\).
-
Deebak and Turjman protocol [35] fails against \(\varGamma 12\), \(\varGamma 14\) and \(\varGamma 15\).
In this context, RAPCHI satisfies all above security attributes.
6.2 Comparison of the computation cost
We have taken several cryptographic operations those based on the information applicable in [6, 25, 26] to test the execution cost of the presented scheme which are related frameworks. The RAPCHI used time for computing to verify/execute a signature \((T_{Sign}\approx 0.3317~ Sec)\), asymmetric decryption/encryption \((T_{A}\approx 0.3057~Sec)\), multiplication \((T_{M}\approx 0.0503 ~Sec)\), bilinear pairing \((T_{P}\approx 0.0621~Sec)\), symmetric decryption/encryption \((T_{S}\approx 0.0087~ Sec)\) and hash function is \((T_{H}\approx 0.0005 ~Sec)\).
The communication overhead concatenation operation (\(\Vert\)) and XOR operation (\(\oplus\)) are generally known to be minimal. Table 5 shows the computation cost of the proposed framework and related frameworks as follows:
-
The computation cost Chen et al.’s protocol [20] is \(3T_{Sign}+3T_{M}+6T_{P}+15T_{S}+6T_{H}+10T_{A}\) which is \(\approx\) 4.7091 Sec.
-
The computation cost Mohit et al.’s protocol [26]is \(6T_{Sign}+9T_{S}+35T_{H}\) which is \(\approx\) 2.086 Sec.
-
The computation cost Chen et al.’s protocol [41] is \(6T_{Sign}+12T_{M}+15T_{P}+15T_{S}+22T_{H}+2T_{A}\) which is \(\approx\) 4.379 Sec.
-
The computation cost Li et al.’s protocol [27] is \(7T_{Sign}+15T_{S}+36T_{H}\) which is \(\approx\) 2.4704 Sec.
-
The computation cost Chiou et al.’s protocol [25]is \(5T_{Sign}+4T_{M}+13T_{P}+10T_{S}+33T_{H}\) which is \(\approx\) 2.7705 Sec.
-
The computation cost Chandrakar et al.’s protocol [29] is \(10T_{Sign}+18T_{S}+59T_{H}\) which is \(\approx\) 3.5031 Sec.
-
The computation cost of Deebak and Turjman protocol [35] is \(8T_{Sign}+17T_{S}+51T_{H}+T_{mul}\) which is \(\approx\) 2.9503 Sec.
-
The computation cost of RAPCHI is \(4T_{Sign}+6T_{S}+2T_{M}+24T_{H}\) which is \(\approx\) 1.4916 Sec.
Thus, RAPCHI is more efficient and secure in CHI. Figure 3 details of computation cost. As a result, as compared to other CHI protocols, RAPCHI is both secure and cost-effective in terms of computation cost.
6.3 Comparison of the communication cost
The communication cost of RAPCHI is compared to that of equivalent frameworks in this section. For this, we use the method of the Mohit et al. [26] protocol. There are several cryptographic components, including produced random numbers, time stamps, and a 48-bit identity length; 128-bit symmetric encryption/decryption, asymmetric encryption/decryption, and modular multiplication/inversion operations; length of cryptographic hash function and bilinear pairing to be 160-bits and length of executing/verifying a signature is 512-bits. Table 5 displays the communication cost of RAPCHI and other comparable related frameworks in details as below:
-
The communication cost Chen et al.’s protocol [20] is 2576 bits.
-
The communication cost Mohit et al.’s protocol [26]is 5312 bits.
-
The communication cost Chen et al.’s protocol [41] is 7952 bits.
-
The communication cost Li et al.’s protocol [27] is 3776 bits.
-
The communication cost Chiou et al.’s protocol [25]is 6528 bits.
-
The communication cost Chandrakar et al.’s protocol [29] is 9440 bits.
-
The communication cost of Deebak and Turjman protocol [35] is 7646 bits.
-
The communication cost of RAPCHI is 752 bits.
Figure 4 details of communication cost. As a result, RAPCHI has a lower communication cost than other protocols CHI.
7 Conclusions
In this work, we have proposed a secure and lightweight authentication mechanism for IoMT-based CHI. The study demonstrates formal security analysis using two distinct ROM-based techniques. We also used the simulation software AVISPA to demonstrate that RAPCHI is not vulnerable to replay and man-in-the-middle attacks. Furthermore, informal security analysis based on various security attributes and properties such as replay attack, data confidentiality, man-in-the-middle attack, patient anonymity, doctor anonymity, data non-repudiation, known-key property, patient unlinkability, impersonation attack, session key security, message authentication, and doctor unlinkability is demonstrated. Furthermore, we compared the proposed framework to existing frameworks in a similar environment, demonstrating that RAPCHI is more secure and efficient in terms of computation and communication cost. As a result, our proposed framework could be more useful in IoT-based cloud-healthcare infrastructure. It is also a real-world application that protects humans from attackers through online treatment.
References
Abor PA, Agrizzi D (2012) Healthcare Governance and Patients’ Perception of Service Quality. In: Annual Conference on Innovations in Business & Management, London, pp 21–23
Ramez WS (2012) Patients’ perception of health care quality, satisfaction and behavioral intention: an empirical study in bahrain. International Journal of Business and Social Science, Centre for Promoting Ideas, US, 3(18):
Wu J, Li H, Cheng S, Lin Z (2016) The promising future of healthcare services: when big data analytics meets wearable technology. Inform Manag 53(8):1020–1033
Li C-T, Lee C-C, Weng C-Y (2014) A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecare medicine information systems. J Med Syst 38(9):77
Tan Z et al (2013) An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2 2(3):200–204
Kumar V, Jangirala S, Ahmad M (2018) An efficient mutual authentication framework for healthcare system in cloud computing. J Med Syst 42(8):142
Habibzadeh H, Dinesh K, Shishvan OR, Boggio-Dandry A, Sharma G, Soyata T (2019) A survey of healthcare internet of things (hiot): a clinical perspective. IEEE Internet Things J 7(1):53–71
Dourado CM, da Silva S.P.P., da Nobrega RVM, Rebouças Filho PP., Muhammad K, de Albuquerque VHC (2020) An open ioht-based deep learning framework for online medical image recognition. IEEE J Sel Areas Commun 39(2):541–548
Tanveer M, Zahid AH, Ahmad M, Baz A, Alhakami H (2020) Lake-iod: lightweight authenticated key exchange protocol for the internet of drone environment. IEEE Access 8:155645–155659
Parah SA, Kaw JA, Bellavista P, Loan NA, Bhat G, Muhammad K, Victor A (2020) Efficient security and authentication for edge-based internet of medical things. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2020.3038009
Hayajneh T, Vasilakos AV, Almashaqbeh G, Mohd BJ, Imran MA, Shakir MZ, Qaraqe KA (2014) Public-Key Authentication for Cloud-Based wbans. In: Proceedings of the 9th International Conference on Body Area Networks, pp 286–292
Choo K-KR, Gritzalis S, Park JH (2018) Cryptographic solutions for industrial internet-of-things: research challenges and opportunities. IEEE Trans Industr Inf 14(8):3567–3569
Padhy RP, Patra MR, Satapathy SC (2012) Design and implementation of a cloud based rural healthcare information system model. Univ J Appl Comput Sci Technol 2(1):149–157
Banerjee A, Agrawal P, Rajkumar R (2013) Design of a cloud based emergency healthcare service model. Int J Appl Eng Res 8(19):2261–2264
Li C-T, Lee C-C, Wang C-C, Yang T-H, Chen S-J (2015) Design Flaws in a Secure Medical Data Exchange Protocol Based on Cloud Environments. In: International Conference on Algorithms and Architectures for Parallel Processing, Springer, pp 435–444
Chatterjee S, Roy S, Das AK, Chattopadhyay S, Kumar N, Reddy AG, Park K, Park Y (2017) On the design of fine grained access control with user authentication scheme for telecare medicine information systems. IEEE Access 5:7012–7030
Islam SH, Khan MK, Li X (2015) Security analysis and improvement of ‘a more secure anonymous user authentication scheme for the integrated epr information system’. PLoS ONE 10(8):e0131368
Wazid M, Das AK, Kumari S, Li X, Wu F (2016) Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for tmis. Sec Commun Netw 9(13):1983–2001
Sutrala AK, Das AK, Odelu V, Wazid M, Kumari S (2016) Secure anonymity-preserving password-based user authentication and session key agreement scheme for telecare medicine information systems. Comput Methods Prog Biomed 135:167–185
Chen C-L, Yang T-T, Chiang M-L, Shih T-F (2014) A privacy authentication scheme based on cloud for medical environment. J Med Syst 38(11):143
Amin R, Islam SH, Biswas G, Khan MK, Obaidat MS (2015) Design and analysis of an enhanced patient-server mutual authentication protocol for telecare medical information system. J Med Syst 39(11):137
He D, Kumar N, Chen J, Lee C-C, Chilamkurti N, Yeo S-S (2015) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Syst 21(1):49–60
Zhou J, Cao Z, Dong X, Xiong N, Vasilakos AV (2015) 4s: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inf Sci 314:255–276
Castiglione A, Pizzolante R, De Santis A, Carpentieri B, Castiglione A, Palmieri F (2015) Cloud-based adaptive compression and secure management services for 3d healthcare data. Futur Gener Comput Syst 43:120–134
Chiou S-Y, Ying Z, Liu J (2016) Improvement of a privacy authentication scheme based on cloud for medical environment. J Med Syst 40(4):101
Mohit P, Amin R, Karati A, Biswas G, Khan MK (2017) A standard mutual authentication protocol for cloud computing based health care system. J Med Syst 41(4):50
Li C-T, Shih D-H, Wang C-C (2018) Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput Methods Prog Biomed 157:191–203
Kumar V, Ahmad M, Kumari A (2019) A secure elliptic curve cryptography based mutual authentication protocol for cloud-assisted tmis. Telematics Inform 38:100–117
Chandrakar P, Sinha S, Ali R (2019) Cloud-based authenticated protocol for healthcare monitoring system. J Ambient Intell Human Comput, 1–17
Chen R, Peng D (2019) Analysis and improvement of a mutual authentication scheme for wireless body area networks. J Med Syst 43(2):19
Chen C-L, Huang P-T, Deng Y-Y, Chen H-C, Wang Y-C (2020) A secure electronic medical record authorization system for smart device application in cloud computing environments. HCIS 10:1–31
Zhu F, Li P, Xu H, Wang R (2020) A novel lightweight authentication scheme for rfid-based healthcare systems. Sensors 20(17):4846
Arunkumar B, Kousalya G (2020) Blockchain-based decentralized and secure lightweight e-health system for electronic health records. In: Intelligent Systems, Technologies and Applications, Springer, pp 273–289
Khatoon S, Rahman SMM, Alrubaian M, Alamri A (2019) Privacy-preserved, provable secure, mutually authenticated key agreement protocol for healthcare in a smart city environment. IEEE Access 7:47962–47971
Deebak BD, Al-Turjman F (2020) Smart mutual authentication protocol for cloud based medical healthcare systems using internet of medical things. IEEE J Sel Areas Commun 39(2):346–360
Chen X, Zhang X, Geng D, Zhou L, Chen J, Lu F (2021) A rfid authentication protocol for epidemic prevention and epidemic emergency management systems. J Healthcare Eng
Hathaliya JJ, Tanwar S (2020) An exhaustive survey on security and privacy issues in healthcare 4.0. Comput Commun 153:311–335
Awotunde JB, Jimoh RG, Ogundokun RO, Misra S, Abikoye OC (2022) Big data analytics of iot-based cloud system framework: Smart healthcare monitoring systems. In: Artificial Intelligence for Cloud and Edge Computing, Springer, pp 181–208
Raj H, Kumar M, Kumar P, Singh A, Verma OP (2022) Issues and challenges related to privacy and security in healthcare using iot, fog, and cloud computing. Empowering Physicians with IoT-Enabled Technologies, Advanced Healthcare Systems, pp 21–32
Singh PD, Dhiman G, Sharma R (2022) Internet of things for sustaining a smart and secure healthcare system. Sustain Comput Inform Syst 33:100622
Chen C-L, Yang T-T, Shih T-F (2014) A secure medical data exchange protocol based on cloud environment. J Med Syst 38(9):112
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Sarkar P (2010) A simple and generic construction of authenticated encryption with associated data. ACM Trans Inform Syst Sec (TISSEC) 13(4):33
Hankerson D, Menezes A.J., Vanstone S (2006) Guide to elliptic curve cryptography. Springer, New York
Kumar V, Ahmad M, Mishra D, Kumari S, Khan MK (2020) Rseap: Rfid based secure and efficient authentication protocol for vehicular cloud computing. Vehicul Commun 22:100213
Stallings W (2006) Cryptography and network security, 4/E. Pearson Education India, UK
Das AK, Paul NR, Tripathy L (2012) Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Inf Sci 209:80–92
Chuang Y-H, Tseng Y-M (2010) An efficient dynamic group key agreement protocol for imbalanced wireless networks. Int J Network Manage 20(4):167–180
Chatterjee S, Das AK, Sing JK (2014) An enhanced access control scheme in wireless sensor networks., Adhoc Sensor Wirel Netw, 21(1)
Das AK, Goswami A (2015) A robust anonymous biometric-based remote user authentication scheme using smart cards. J King Saud Univ-Comput Inform Sci 27(2):193–210
Odelu V, Das AK, Goswami A (2014) A secure effective key management scheme for dynamic access control in a large leaf class hierarchy. Inf Sci 269:270–285
Das AK (2015) A secure user anonymity-preserving three-factor remote user authentication scheme for the telecare medicine information systems. J Med Syst 39(3):30
Kumari A, Jangirala S, Abbasi MY, Kumar V, Alam M (2020) Eseap: Ecc based secure and efficient mutual authentication protocol using smart card. J Inform Sec Appl 51:102443
Bellare M, Rogaway P (1993) Random Oracles are Practical: A Paradigm for Designing Efficient protocols. In: Proceedings of the 1st ACM Conference on Computer and Communications Security, ACM, pp 62–73
Shoup V (2004) Sequences of games: a tool for taming complexity in security proofs. IACR Cryptology ePrint Archive 2004:332
Xu J, Zhu W-T, Feng D-G (2009) An improved smart card based password authentication scheme with provable security. Comput Stand Interfaces 31(4):723–728
Mishra D, Das AK, Mukhopadhyay S (2016) A secure and efficient ecc-based user anonymity-preserving session initiation authentication protocol using smart card. Peer-to-peer Netw Appl 9(1):171–192
Wazid M, Das AK, Odelu V, Kumar N, Conti M, Jo M (2017) Design of secure user authenticated key management protocol for generic iot networks. IEEE Internet Things J 5(1):269–282
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, V., Mahmoud, M.S., Alkhayyat, A. et al. RAPCHI: Robust authentication protocol for IoMT-based cloud-healthcare infrastructure. J Supercomput 78, 16167–16196 (2022). https://doi.org/10.1007/s11227-022-04513-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-022-04513-4