Abstract
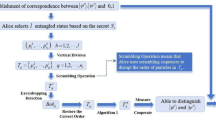
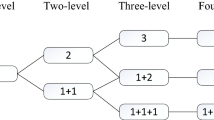
Quantum secret sharing plays a crucial role in quantum cryptography. In this paper, we present a rational hierarchical (t,n)-threshold quantum secret sharing scheme based on Lagrange interpolation. In our scheme, participants possess rational and hierarchical properties, and the secret can be reconstructed when the number of rational participants satisfies the hierarchical (t,n)-threshold structure proposed in this paper. The reconstructed secret can encompass both classical information and quantum state information, enhancing the practicality and flexibility of our scheme compared to existing ones. Additionally, we redefine the utility of participants based on their roles in the secret recovery process. This newly defined utility allows for a more precise analysis of the correctness, fairness, and equilibrium of our scheme. Finally, our scheme not only resists a typical set of external attacks but also incorporates mechanisms to detect forgery and collusion among participants.
Similar content being viewed by others
Data availability
All data generated or analyzed during this study are included in this published article.
References
Shamir, A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Halpern, J., Teague, V.: Rational secret sharing and multiparty computation. In: Proceedings of the 36th Annual ACM Symposium on Theory of Computing. ACM, pp. 623-632 (2004)
Abraham, I., Dolev, D., Gonen, R.: Distributed computing meets game theory. In: Proceedings of the 25th Annual ACM Symposium on Principles of Distributed Computing. ACM, pp. 53-62 (2006)
Nojoumian, M., Stinson, D.R.: Brief announcement: secret sharing based on the social behaviors of players. In: Proceedings of the 29th Annual ACM Symposium on Principles of Distributed Computing. ACM, pp. 239-240 (2012)
Harn, L., Lin, C., Yong, L.: Fair secret reconstruction in (t, n)-secret sharing. J. Inf. Sesur. Appl. 23, 1–7 (2015)
Shor, P.W.: Algorithms for quantum computation: discrete logarithms and factoring. In: Proceedings of 35th Annual Symposium on the Foundations of Computer Science. ACM, pp. 124-134 (1994)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Proceedings of the 28 Annual ACM Symposium Computing. ACM, pp. 212-219 (1996)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299, 802–803 (1982)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050–2056 (1999)
Mayers, D.: Unconditional security in quantum cryptography. ACM 48, 351–406 (2001)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
Li, Y., Zhang, K., Peng, K.: Multiparty secret sharing of quantum information based on entanglement swapping. Phys. Lett. A 324, 420–424 (2004)
Katz, J.: Theory of Cryptography, pp. 251–272. Springer-Verlag, Berlin (2008)
Lau, H.K., Weedbrook, C.: Quantum secret sharing with continuous-variable cluster states. Phys. Rev. A 88, 042313 (2013)
Rahaman, R., Parker, M.G.: Quantum scheme for secret sharing based on local distinguish ability. Phys. Rev. A 91, 022330 (2015)
Fu, Y., Yin, H.L., Chen, T.Y., Chen, Z.B.: Long-distance measurement-device-independent multiparty quantum communication. Rhys. Rev. Lett. 114, 090501 (2015)
Brian, P.W., Joseph, M.L., Nicholas, A.P., Bing, Q., Warren, P.G.: Quantum secret sharing with polarization-entangled photon pairs. Rhys. Rev. A 99, 062311 (2019)
Ju, X.X., Zhong, W., Sheng, Y.B., Zhou, L.: Measurement-device-independent quantum secret sharing with hyper-encoding. Chinese Phys. B 31, 100302 (2022)
Li, C.L., Fu, Y., Liu, W.B., Xie, Y.M., Li, B.H.: Breaking rate-distance limitation of measurement-device-independent quantum secret sharing. Rhys. Rev. Res. 5, 033077 (2023)
Gu, J., Cao, X.Y., Yin, H.L., Chen, Z.B.: Differential phase shift quantum secret sharing using twin field. Opt. Express 29, 9165 (2021)
Shen, A., Cao, X.Y., Wang, Y., Fu, Y., Gu, Jie: Experimental quantum secret sharing based on phase encoding of coherent states. Sci. China-Phys. Mech. Astron. 66, 260311 (2023)
Yin, H.L., Fu, Y., Li, C.L., Weng, C.X., Li, B.H.: Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 10, nwac228 (2023)
Qin, H., Tang, W.K.S., Tso, R.: Rational quantum secret sharing. Sci. Rep. 8(1), 11115 (2018)
Dou, Z., Xu, G., Chen, X.B.: A secure rational quantum state sharing protocol. Sci. China. Inf. Sci. 61(2), 022501 (2018)
Maitra, A., Joyee, D.S., Paul, G.: Proposal for quantum rational secret sharing. Phys. Rev. A 92, 022305 (2015)
Simmon, G.J.: How to (really) share a secret. In: Proceedings of Advances in Cryptology-CRYPTO’ 88. Springer, pp. 390-448 (1990)
Basit, A., Kumar, N.C., Venkaiah, V.C.: Multi-stage multi-secret sharing scheme for hierarchical access structure. In: Proceedings of International Conference on Computing, Communication and Automation. IEEE, pp. 557-563 (2017)
Zhang, J., Lin, C.L., Huang, K.K.: Polynomial interpolation based hierarchical secret sharing schemes. J. Cryptol. Res. 9(4), 743–754 (2022)
Shukla, C., Pathak, A.: Hierarchical quantum communication. Phys. Lett. A 377, 1337 (2013)
Xu, G., Wang, C., Yang, Y.X.: Hierarchical quantum information splitting of an arbitrary two-qubit state via the cluster state. Quantum Inf. Process. 13(1), 43–57 (2014)
Venugopalan, A., Shukla: Protocol, an integrated hierarchical dynamic quantum secret sharing. Int. J. Theor. Phys. 54, 3143–3154 (2015)
Xu, G., Shan, R.T., Chen, X.B.: Probabilistic and hierarchical quantum information splitting based on the non-maximally entangled cluster state. CMC-Comput. Mat. Contin. 69(1), 339–349 (2021)
Qin, H., Tang, W., Tso, R.L.: Hierarchical quantum secret sharing based on special high-dimensional entangled state. IEEE. J. Sel. Top. Quant. 26, 1–1 (2020)
Zha, X.W., Miao, N., Wang, H.F.: Hierarchical quantum information splitting of an arbitrary two-qubit using a single quantum resource. Int. J. Theor. Phys. 58, 2428–2434 (2019)
Nielsen, M.A., Chuang, I.L.: Quantum computation and quantum information. Math. Struct. Comp. Sci. 17(6), 1115–1115 (2002)
Stefanov, A., Gisin, N., Guinnard, O.: Optical quantum random number generator. J. Mod. Opt. 47, 595–598 (2000)
Qin, H., Zhu, X., Dai, Y.: (t, n) Threshold quantum secret sharing using the phase shift operation. Quantum Inf. Process. 14(8), 2997–3004 (2015)
Zhang, X.L.: One-way quantum identity authentication based on public key. Chinese. Sci. Bull. 54, 2018–2021 (2009)
Makarov, V., Anisimov, A., Skaar, J.: Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74, 022313 (2006)
Qi, B., Fung, C.H.F., Lo, H.K.: Time-shift attack in practical quantum cryptosystems. Quantum Inf. Comput. 7, 73–824 (2007)
Zhang, H.L., Che, B.C., Dou, Z.: A rational quantum state sharing protocol with semi-off-line dealer. Chinese Phys. B 31(5), 050309 (2022)
Tsai, C.W., Hsieh, C.R., Hwang, T.: Dense coding using cluster states and its application on deterministic secure quantum communication. Eur. Phys. J. D 61, 779 (2011)
Daryanoosh, S., Slussarenko, S., Berry, D.W.: Experimental optical phase measurement approaching the exact Heisenberg limit. Nat. Commun. 9, 4606 (2018)
Acknowledgements
This research was supported by the National Natural Science Foundation of China (No.U21A20428, No.61972126, No.12171134).
Author information
Authors and Affiliations
Contributions
FL, ZL and SZ have written this paper and have done the research which supports it. FL and ZL have collaborated in the conception, research and design of the paper. SZ and LL have collaborated in the language polishment and the typesetting. Above all authors have tried best to review the manuscript carefully.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest regarding the publication of this manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This research was supported by the National Natural Science Foundation of China (Nos. U21A20428, 61972126, 12171134).
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Li, F., Liu, Z., Liu, L. et al. A rational hierarchical (t,n)-threshold quantum secret sharing scheme. Quantum Inf Process 23, 60 (2024). https://doi.org/10.1007/s11128-024-04269-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-024-04269-1