Abstract
The fairness of a secure multi-party quantum key agreement (MQKA) protocol requires that all involved parties are entirely peer entities and can equally influence the outcome of the protocol to establish a shared key wherein no one can decide the shared key alone. However, it is found that parts of the existing MQKA protocols are sensitive to collusion attacks, i.e., some of the dishonest participants can collaborate to predetermine the final key without being detected. In this paper, a multi-party QKA protocol resisting collusion attacks is proposed. Different from previous QKA protocol resisting \(N-1\) coconspirators or resisting 1 coconspirators, we investigate the general circle-type MQKA protocol which can be secure against t dishonest participants’ cooperation. Here, \(t < N\). We hope the results of the presented paper will be helpful for further research on fair MQKA protocols.

Similar content being viewed by others
Notes
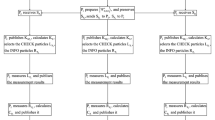
For the single state, it can be considered as the entangled states where parts of them \(R_{i}\) have already been measured.
For the single state, it can be considered as the entangled states where parts of them have already been measured.
References
Shor, P.W.: Algorithms for quantum computation: discrete logarithms and factoring. In: Proceedings of 35th Annual Symposium on the Foundations of Computer Science, pp. 124–134 (1994)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829 (1999)
Du, R.G., Sun, Z.W., Wang, B.H., Long, D.Y.: Quantum secret sharing of secure direct communication using one-time pad. Int. J. Theor. Phys. 51, 2727–2736 (2012)
Sun, Z.W., Du, R.G., Long, D.Y.: Quantum secure direct communication with quantum identification. Int. J. Quantum Inf. 10, 1250008 (2012)
Sun, Z.W., Du, R.G., Long, D.Y.: Quantum secure direct communication with two-photon four-qubit cluster state. Int. J. Theor. Phys. 51, 1946–1952 (2012)
Liu, W.J., Liu, C., Liu, Z.H., Liu, J.F., Geng, H.T.: Same initial states attack in Yang et al’s quantum private comparison protocol and the improvement. Int. J. Theor. Phys. 53(1), 271–276 (2014)
Liu, W.-J., Liu, C., Chen, H.-W., Liu, Z.-H., Yuan, M.-X., Lu, J.-S.: Improvement on “an efficient protocol for the quantum private comparison of equality with W state”. Int. J. Quantum. Inf. 12(01), 1450001 (2014)
Liu, W.J., Liu, C., Chen, H.W., Li, Z.Q.: Cryptanalysis and improvement of quantum private comparison protocol based on Bell entangled states. Commun. Theor. Phys. 62(2), 210–214 (2014)
Sun, Z.W., Long, D.Y.: Quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 52, 212–218 (2013)
Sun, Z.W., Yu, J.P., Wang, P., Xu, L.L., Wu, C.H.: Quantum private comparison with a malicious third party. Quantum Inf. Process. 14(6), 2125–2133 (2015)
Sun, Z., Jianping, Y., Wang, P., Lingling, X.: Symmetrically private information retrieval based on blind quantum computing. Phys. Rev. A 91, 052303 (2015)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40(18), 1149 (2004)
Tsai, C., Hwang, T.: On quantum key agreement protocol. Technical Report, C-S-I-E, NCKU, Taiwan, R.O.C (2009)
Chong, S.K., Tsai, C.W., Hwang, T.: Improvement on quantum key agreement protocol with maximally entangled states. Int. J. Theor. Phys. 50(6), 1793–1802 (2011)
Chong, S.K., Hwang, T.: Quantum key agreement protocol based on BB84. Opt. Commun. 283(6), 1192–1195 (2010)
Huang, W., Wen, Q.Y., Liu, B., Gao, F., Sun, Y.: Quantum key agreement with EPR pairs and single particle measurements. Quantum Inf. Process. 13(3), 649–663 (2014)
Dongsu, S., Wenping, M., Lili, W.: Two-party quantum key agreement with four-qubit cluster states. Quantum Inf. Process. 13, 2313 (2014)
He, Y.F., Ma, W.P.: Quantum key agreement protocols with four-qubit cluster states. Quantum Inf. Process. 14(9), 3483–3498 (2015)
Shi, R.H., Zhong, H.: Multi-party quantum key agreement with Bell states and Bell measurements. Quantum Inf. Process. 12(2), 921–932 (2013)
Liu, B., Gao, F., Huang, W., Wen, Qy: Multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(4), 1797–1805 (2013)
Sun, Z., Wang, B., Li, Q., Long, D.: Improvements on multiparty quantum key agreement with single particles. Quantum Inf. Process. 12, 3411 (2013)
Yin, X.R., Ma, W.P., Liu, W.Y.: Three-party quantum key agreement with two-photon entanglement. Int. J. Theor. Phys. 52, 3915–3921 (2013)
Yin, X.R., Wen, W.P., Shen, D.S., et al.: Three-party quantum key agreement with Bell states. Acta Phys. Sin. 62(17), 170304 (2013)
Chitra, S., Nasir, A., Anirban, P.: Protocols of quantum key agreement solely using Bell states and Bell measurement. Quantum Inf. Process. 13, 2391–2405 (2014)
Zhu, Z.C., Hu, A.Q., Fu, A.M.: Improving the security of protocols of quantum key agreement solely using Bell measurement. Quantum Inf. Process. 14(11), 4245–4254 (2015)
Sun, Z., Jianping, Y., Wang, P.: Efficient multiparty quantum key agreement by cluster states. Quantum Inf. Process. 15(1), 373–384 (2016)
Sun, Z., Zhang, C., Wang, P., Yu, J., Zhang, Y., Long, D.: Multi-party quantum key agreement by an entanglement six-qubit state. Int. J. Theor. Phys. 55(3), 1920–1929 (2015)
Sun, Z., Huang, J., Wang, P.: Efficient multiparty quantum key agreement protocol based on commutative encryption. Quantum Inf. Process. 15(5), 2101–2111 (2016)
Huang, W., Wen, Q.Y., Liu, B., et al.: Cryptanalysis of a multi-party quantum key agreement protocol with single particles. Quantum Inf. Process. 13(7), 1651–1657 (2014)
Liu, B., Di, X., Heng-Yue, J., Run-Zong, L.: Collusive attacks to circle-type multi-party quantum key agreement protocols. Quantum Inf. Process. 15(5), 2113–2124 (2016)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85, 5633–5638 (2000)
Acknowledgements
This work is funded by the National Natural Science Foundation of China (No. 61602316, 61402293), the Science and Technology Innovation Projects of Shenzhen (No. JCYJ20150324141711665 and No. JCYJ20150324141711694), Natural Science Foundation of SZU (No. 201435), and China Postdoctoral Science Foundation (No. 2015M572360).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, P., Sun, Z. & Sun, X. Multi-party quantum key agreement protocol secure against collusion attacks. Quantum Inf Process 16, 170 (2017). https://doi.org/10.1007/s11128-017-1621-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-017-1621-z