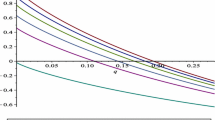
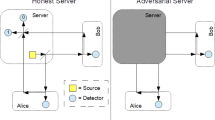
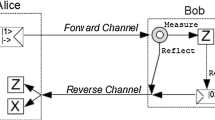
Abstract
In this paper, we investigate single-state, semi-quantum key distribution protocols. These are protocols whereby one party is limited to measuring only in the computational basis, while the other, though capable of measuring in both computational and Hadamard bases, is limited to preparing and sending only a single, publicly known qubit state. Such protocols rely necessarily on a two-way quantum communication channel making their security analysis difficult. However, we will show that, for single-state protocols, we need only consider a restricted attack operation by Eve. We will also describe a new single-state protocol that permits “reflections” to carry information and use our results concerning restricted attacks to show its robustness.

Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, vol. 175. New York (1984)
Acin, A., Gisin, N., Scarani, V.: Coherent-pulse implementations of quantum cryptography protocols resistant to photon-number-splitting attacks. Phys. Rev. A 69, 012309 (2004)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical bob. In: First International Conference on Quantum, Nano, and Micro Technologies, 2007. ICQNM ’07, pp. 10–10 (2007)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A 79, 032341 (2009)
Lu, H., Fung, C.-H.F., Ma, X., Cai, Q.-Y.: Unconditional security proof of a deterministic quantum key distribution with a two-way quantum channel. Phys. Rev. A 84, 042344 (2011)
Beaudry, N.J., Lucamarini, M., Mancini, S., Renner, R.: Security of two-way quantum key distribution. arXiv preprint arXiv:1301.3138 (2013)
Lu, H., Cai, Q.-Y.: Quantum key distribution with classical Alice. Int. J. Quantum Inf. 6(06), 1195–1202 (2008)
Jian, W., Sheng, Z., Quan, Z., Chao-Jing, T.: Semiquantum key distribution using entangled states. Chin. Phys. Lett. 28(10), 100301 (2011)
Sun, Z.-W., Du, R.-G., Long, D.-Y.: Quantum key distribution with limited classical bob. Int. J. Quantum Inf. 11(01), 1350005 (2013)
Yu, K.-F., Yang, C.-W., Liao, C.-H., Hwang, T.: Authenticated semi-quantum key distribution protocol using bell states. Quantum Inf. Process. 13(6), 1457–1465 (2014)
Xian-Zhou, Z., Wei-Gui, G., Yong-Gang, T., Zhen-Zhong, R., Xiao-Tian, G.: Quantum key distribution series network protocol with m-classical bobs. Chin. Phys. B 18(6), 2143 (2009)
Li, Q., Chan, W.H., Long, D.-Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82, 022303 (2010)
Li, L., Qiu, D., Mateus, P.: Quantum secret sharing with classical bobs. J. Phys. A Math. Theor. 46(4), 045304 (2013)
Wang, J., Zhang, S., Zhang, Q., Tang, C.-J.: Semiquantum secret sharing using two-particle entangled state. Int. J. Quantum Inf. 10(05), 1250050 (2012)
Yang, C-W, Hwang, T: Efficient key construction on semi-quantum secret sharing protocols. Int. J. Quantum Inf. 11(05), 1350052 (2013)
Zou, X., Qiu, D., Li, L., Li, L.: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79, 052312 (2009)
Boyer, M., Mor, T.: Comment on semiquantum-key distribution using less than four quantum states. Phys. Rev. A 83(4), 046301 (2011)
Miyadera, T.: Relation between information and disturbance in quantum key distribution protocol with classical alice. Int. J. Quantum Inf. 9(6), 1427–1435 (2011)
Kraus, B., Gisin, N., Renner, R.: Lower and upper bounds on the secret-key rate for quantum key distribution protocols using one-way classical communication. Phys. Rev. Lett. 95, 080501 (2005)
Tan, Y., Lu, H.: Comment on quantum key distribution with classical bob. Phys. Rev. Lett. 102, 098901 (2009)
Boyer, M., Kenigsberg, D., Mor, T.: Boyer, Kenigsberg, and Mor reply. Phys. Rev. Lett. 102, 098902 (2009)
Maitra, A., Paul, G.: Eavesdropping in semiquantum key distribution protocol. Inf. Process. Lett. 113(12), 418–422 (2013)
Christandl, M., Konig, R., Renner, R.: Postselection technique for quantum channels with applications to quantum cryptography. Phys. Rev. Lett. 102, 020504 (2009)
Renner, R.: Symmetry of large physical systems implies independence of subsystems. Nat. Phys. 3(9), 645–649 (2007)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72, 012332 (2005)
Acknowledgments
The author would like to thank Antonio R. Nicolosi and the anonymous reviewers for their valuable comments, all of which greatly improved the quality of this paper.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Krawec, W.O. Restricted attacks on semi-quantum key distribution protocols. Quantum Inf Process 13, 2417–2436 (2014). https://doi.org/10.1007/s11128-014-0802-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-014-0802-2