Abstract
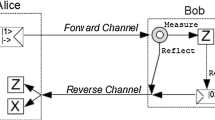
Semi-quantum key distribution (SQKD) protocols attempt to establish a shared secret key between users, secure against computationally unbounded adversaries. Unlike standard quantum key distribution protocols, SQKD protocols contain at least one user who is limited in their quantum abilities and is almost “classical” in nature. In this paper, we revisit a mediated semi-quantum key distribution protocol, introduced by Massa et al. (Experimental quantum cryptography with classical users, 2019. arXiv preprint arXiv:1908.01780), where users need only the ability to detect a qubit, or reflect a qubit; they do not need to perform any other basis measurement; nor do they need to prepare quantum signals. Users require the services of a quantum server which may be controlled by the adversary. In this paper, we show how this protocol may be extended to improve its efficiency and also its noise tolerance. We discuss an extension which allows more communication rounds to be directly usable; we analyze the key-rate of this extension in the asymptotic scenario for a particular class of attacks and compare with prior work. Finally, we evaluate the protocol’s performance in a variety of lossy and noisy channels.






Similar content being viewed by others
Data availability statement
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
References
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical Bob. Phys. Rev. Lett. 99, 140501 (2007)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A 79, 032341 (2009)
Zou, X., Qiu, D., Li, L., Wu, L., Li, L.: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79(5), 052312 (2009)
He, J., Li, Q., Wu, C., Chan, W.H., Zhang, S.: Measurement-device-independent semiquantum key distribution. Int. J. Quantum Inf. 16(02), 1850012 (2018)
Amer, O., Krawec, W.O.: Semiquantum key distribution with high quantum noise tolerance. Phys. Rev. A 100(2), 022319 (2019)
Vlachou, C., Krawec, W., Mateus, P., Paunković, N., Souto, A.: Quantum key distribution with quantum walks. Quantum Inf. Process. 17(11), 1–37 (2018)
Iqbal, H., Krawec, W.O.: High-dimensional semiquantum cryptography. IEEE Trans. Quantum Eng. 1, 1–17 (2020)
Boyer, M., Katz, M., Liss, R., Mor, T.: Experimentally feasible protocol for semiquantum key distribution. Phys. Rev. A 96(6), 062335 (2017)
Krawec, W.O.: Practical security of semi-quantum key distribution. In: Quantum Information Science, Sensing, and Computation X, vol. 10660, pp. 1066009. International Society for Optics and Photonics (2018)
Silva, M., Faleiro, R., Mateus, P.: Semi-device-independent quantum key distribution based on a coherence equality (2021). arXiv preprint arXiv:2103.06829
Chongqiang, Y., Jian, L., Xiubo, C., Yuan, T., Yanyan, H.: An efficient semi-quantum key distribution protocol and its security proof. IEEE Commun. Lett. 26, 1226–1230 (2022)
Li, Q., Chan, W.H., Long, D.-Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Lin, J., Yang, C.-W., Tsai, C.-W., Hwang, T.: Intercept-resend attacks on semi-quantum secret sharing and the improvements. Int. J. Theor. Phys. 52(1), 156–162 (2013)
Wang, J., Zhang, S., Zhang, Q., Tang, C.-J.: Semiquantum secret sharing using two-particle entangled state. Int. J. Quantum Inf. 10(05), 1250050 (2012)
Zou, X.F., Qiu, D.W.: Three-step semiquantum secure direct communication protocol. Sci. China Phys. Mech. Astron. 57(9), 1696–1702 (2014)
Gu, J., Lin, P., Hwang, T.: Double C-NOT attack and counterattack on ‘three-step semi-quantum secure direct communication protocol’. Quantum Inf. Process. 17(7), 1–8 (2018)
Xie, C., Li, L., Situ, H., He, J.: Semi-quantum secure direct communication scheme based on bell states. Int. J. Theor. Phys. 57(6), 1881–1887 (2018)
Sun, Y., Yan, L., Chang, Y., Zhang, S., Shao, T., Zhang, Y.: Two semi-quantum secure direct communication protocols based on bell states. Mod. Phys. Lett. A 34(01), 1950004 (2019)
Rong, Z., Qiu, D., Mateus, P., Zou, X.: Mediated semi-quantum secure direct communication. Quantum Inf. Process. 20(2), 1–13 (2021)
Thapliyal, K., Sharma, R.D., Pathak, A.: Orthogonal-state-based and semi-quantum protocols for quantum private comparison in noisy environment. Int. J. Quantum Inf. 16(05), 1850047 (2018)
Chongqiang, Y., Jian, L., Xiubo, C., Yuan, T.: Efficient semi-quantum private comparison without using entanglement resource and pre-shared key. Quantum Inf. Process. 20(8), 1–19 (2021)
Wen, X.-J., Zhao, X.-Q., Gong, L.-H., Zhou, N.-R.: A semi-quantum authentication protocol for message and identity. Laser Phys. Lett. 16(7), 075206 (2019)
Zhou, N.-R., Zhu, K.-N., Bi, W., Gong, L.-H.: Semi-quantum identification. Quantum Inf. Process. 18(6), 1–17 (2019)
Massa, F., Yadav, P., Moqanaki, A., Krawec, W.O., Mateus, P., Paunković, N., Souto, A., Walther, P.: Experimental quantum cryptography with classical users (2019). arXiv preprint arXiv:1908.01780
Gurevich, P., Orenstein, M., Mor, T.: Experimental Quantum Key Distribution with Clasical Alice. PhD thesis, Computer Science Department, Technion (2013)
Iqbal, H., Krawec, W.O.: Semi-quantum cryptography. Quantum Inf. Process. 19(3), 1–52 (2020)
Pirandola, S., Andersen, U.L., Banchi, L., Berta, M., Bunandar, D., Colbeck, R., Englund, D., Gehring, T., Lupo, C., Ottaviani, C., et al.: Advances in quantum cryptography. Adv. Opt. Photon. 12(4), 1012–1236 (2020)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009)
Amer, O., Garg, V., Krawec, W.O.: An introduction to practical quantum key distribution. IEEE Aerosp. Electron. Syst. Mag. 36(3), 30–55 (2021)
Krawec, W.O.: Mediated semiquantum key distribution. Phys. Rev. A 91(3), 032323 (2015)
Devetak, I., Winter, A.: Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A Math. Phys. Eng. Sci. 461(2053), 207–235 (2005)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72, 012332 (2005)
Krawec, W.O.: Quantum key distribution with mismatched measurements over arbitrary channels. Quantum Inf. Comput. 17(3 and 4), 209–241 (2017)
Krawec, W.O.: Multi-mediated semi-quantum key distribution. In: 2019 IEEE Globecom Workshops (GC Wkshps), pp. 1–6. IEEE (2019)
Davies, E.B., Lewis, J.T.: An operational approach to quantum probability. Commun. Math. Phys. 17(3), 239–260 (1970)
Wilde, M.M.: From classical to quantum Shannon theory (2011). arXiv preprint arXiv:1106.1445
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441 (2000)
Hwang, W.-Y.: Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003)
Lo, H.-K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Wang, X.-B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005)
Lim, C.C.W., Curty, M., Walenta, N., Xu, F., Zbinden, H.: Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89(2), 022307 (2014)
Guskind, J., Krawec, W.O.: Mediated semi-quantum key distribution with improved efficiency (2021). arXiv preprint arXiv:2111.01627
Maurer, U.M.: Secret key agreement by public discussion from common information. IEEE Trans. Inf. Theory 39(3), 733–742 (1993)
Bae, J., Acín, A.: Key distillation from quantum channels using two-way communication protocols. Phys. Rev. A 75(1), 012334 (2007)
Chau, H.F.: Practical scheme to share a secret key through a quantum channel with a 27.6% bit error rate. Phys. Rev. A 66(6), 060302 (2002)
Acknowledgements
WOK would like to acknowledge support from the National Science Foundation under Grant Number 1812070. SM would like to acknowledge the support of National Science Foundation grant number CNS-1950600, which supported her during a summer REU at the University of Connecticut.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix
A.1 Parameter estimation
In this appendix, we determine bounds on the needed inner products (required to evaluate Eq. 14) by considering various, observable, events such as the probability of the server sending the message “1” given that both parties choose \(\texttt {Reflect}\) (this should be small for instance). This can be done for arbitrary channels; however as discussed in the text, we derive expressions for a symmetric depolarization attack, a common approach in QKD security proofs. Note that our security proof does not require this as an assumption—it is only done in order to evaluate the performance on a standard channel scenario. Our steps below, however, may be followed for any observed channel. Under these evaluation conditions, we may parameterize the channel statistics as follows: \(\phi \) will be the phase error of the channel; \(p_l\) is the probability of loss in one direction (the server to users and the users to the server); and \(p_d\) is the dark count rate of the server’s detectors.
Recall the density operator describing one round of the protocol (Eq. 9) which we copy here:
We begin by considering \({\mathrm{Pr}}(C = 1 \text { }|\text { }A=B=\texttt {Reflect}) = P_{1|RR}\) which is the probability that conditioning on both Alice and Bob choosing \(\texttt {Reflect}\), the server sends the message 1. It is clear, from the analysis in Sect. 4 and the state \(\rho _{ABE}\), that this is \(P_{1|RR} = {\langle r_1|r_1\rangle }\). Under our symmetric attack scenario, we set this to \(P_{1|RR} = \frac{p_lp_d}{2} + (1-p_l)\left( \frac{p_lp_d}{2} + (1-p_l)\phi \right) \). Similarly, we find the following:
Note that, in the above, we are defining \(P_{i|RM}=P_{i|MR}\) to be the probability of the server sending message i and the measuring party not detecting the photon. These let us easily compute N using Eq. 10 and the above.
It is also clear that the values of \(\alpha \), \(\beta \), and \(\gamma \) may be observed based on Alice and Bob’s measurements. Namely, \(|\alpha |^2\) is the probability that conditioning on both parties choosing \(\texttt {Measure}\) that Alice detects the photon. Similar observations may be made for \(|\beta |^2\), while \(|\gamma |^2\) is the probability that neither party detects a photon. Thus, these are:
Next, we bound \(|{\langle s_1|t_1\rangle }|\) and \(|{\langle s_0|t_0\rangle }|\). From Eq. 8, we have:
Thus,
Now, we can write \({\mathrm{Re}}{\langle s_1|t_1\rangle }\) as:
By substituting in Eq. 16 and noting that \({\mathrm{Re}}{\langle e_1|f_1\rangle } = {\mathrm{Re}}{\langle f_1|e_1\rangle }\), we have:
Next we may find an expression for \(\alpha ^2{\langle e_1|e_1\rangle }\) by looking at \({\langle t_1|t_1\rangle }\) (which is an observable quantity as discussed above, namely \(P_{1|RM}\)):
Of course \({\langle t_1 |t_1\rangle }\) is an observable probability for Alice and Bob and, later, we may use Cauchy–Schwarz to bound \(|{\langle e_1|g_1\rangle }|\) thus allowing them to bound \(\alpha ^2{\langle e_1|e_1\rangle }\) used in the expansion of \({\langle s_1|t_1\rangle }\). Similarly, we find:
Combining this into Eq. 17 and using the (reverse) triangle inequality yields:
where, for the last inequality, we used the fact that \(|{\langle e_1|g_1\rangle }| \le \sqrt{{\langle e_1|e_1\rangle }{\langle g_1|g_1\rangle }} \le \sqrt{{\langle g_1|g_1\rangle }}\). (Similarly for \({\langle f_1|g_1\rangle }\).) Similarly we may bound:
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mutreja, S., Krawec, W.O. Improved semi-quantum key distribution with two almost-classical users. Quantum Inf Process 21, 319 (2022). https://doi.org/10.1007/s11128-022-03663-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03663-x