Abstract
In this paper, we present an asymmetric “4+2” protocol for quantum key distribution with finite photon pulses. The main work of this paper focuses on the composable security proof for this protocol in a finite-key scenario. Based on the essence security basis of the original “4+2” protocol proposed by Huttner et al. (Phys Rev A 51(3):1863–1869, 1995), we first develop the squashing model for this protocol with the quantum non-demolition measure theory. From this model, against the collective photon-number-splitting attack, we then provide the security proof (formulas of finite-key security bounds) for this protocol. The expected performance of this protocol are also evaluated on a priori reasonable expected values of parameters. Our work shows that the performance we derived is the lower one and it can cover long distances in the lossy channel.


Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public-key distribution and coin tossing. In: Proceedings IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, pp. 175–179. IEEE, New York (1984)
Gottesman, D., Lo, H.K., Lütkenhaus, N., Preskill, J.: Security of quantum key distribution with imperfect devices. J. Quantum Inf. Comput. 5, 325–360 (2004)
Lo, H.K., Ma, X.F., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94(23), 230504–230507 (2005)
Ma, X.F., Qi, B., Zhao, Y., Lo, H.K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72(1), 012326–012340 (2005)
Ma, X.F., Fred Fung, C.H., Dupuis, F., Chen, K., Tamaki, K., Lo, H.-K.: Decoy state quantum key distribution with two-way classical post-processing. Phys. Rev. A 74(3), 032330–032345 (2006)
Wang, X.B.: Secure and efficient decoy-state quantum key distribution with inexact pulse intensities. arXiv.org:quant-ph, 0609081 (2006)
Wang, X.B., Peng, C.Z., Zhang, J., Y.L., Pan, J.W.: General theory of decoy-state quantum cryptography with source errors. Phys. Rev. A 77(4), 042311–042318 (2008)
Wang, X.B., Yang, L., Peng, C.Z., Pan, J.W.: Decoy-state quantum key distribution with both source errors and statistical fluctuations. arXiv.org:quant-ph, 09024660 (2009)
Xu, F.X., Zhang, Y., Zhou, Z., Chen, W., Han, Zf, Guo, G.C.: Experimental demonstration of counteracting imperfect sources in a practical one-way quantum-key-distribution system. Phys. Rev. A 80(6), 062309–062313 (2009)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time-pad. Phys. Rev. A 69(5), 052319–052322 (2004)
Deng, F.G., Long, G.L.: Bidirectional quantum key distribution protocol with practical faint laser pulses. Phys. Rev. A 70(1), 012311–012317 (2004)
Lu, H., Fung, C.-H., Ma, X., Cai, Q-y: Unconditional security proof of a deterministic quantum key distribution with a two-way quantum channel. Phys. Rev. A 84(6), 042344–042355 (2011)
Bennett, C.H.: Quantum cryptography using any two non-orthogonal states. Phys. Rev. Lett. 68(21), 3121–3124 (1992)
Koashi, M.: Unconditional security of coherent-state quantum key distribution with a strong phase-reference pulse. Phys. Rev. Lett. 93(12), 120501–120504 (2004)
Tamaki, K., Lütkenhaus, N., Koashi, M., Batuwantu-dawe, J.: Unconditional security of the Bennett 1992 quantum key-distribution scheme with strong reference pulse. Phys. Rev. A 80(3), 032302–032310 (2009)
Huttner, B., Imoto, N., Gisin, N., Mor, T.: Quantum cryptography with coherent states. Phys. Rev. A 51(3), 1863–1869 (1995)
Nielsen, M.A., Chuang, I.L.: Quantum computation and quantum information Cambridge. Cambridge University Press, UK (2000)
Carter, J.L., Wegman, M.N.: Universal classes of hash functions. J. Comput. Syst. Sci. 19, 143–154 (1979)
Wegman, M.N., Carter, J.L.: New hash functions and their use in authentication and set equality. Comput. Syst. Sci 22(3), 265–279 (1981)
Lo, H.K., Chau, H.F., Ardehali, M.: Efficient quantum key distribution. arXiv.org:quant -ph, 9803007 (1998)
Dusek, M., Läutkenhaus, N., Hendrych, M.: Quantum cryptography. Prog. Opt. 49, 381–454 (2006)
Derka, R., Buzk, V., Ekert, A.K.: Universal algorithm for optimal estimation of quantum states from finite ensembles via realizable generalized measurement. Phys. Rev. Lett. 80(8), 1571–1575 (1998)
Csiszar, I., KÄorner, J.: Broadcast channels with confidential messages. IEEE Trans. Inf. Theory. 24(3), 339–348 (1978)
Tsurumaru, T., Tamaki, K.: Security proof for quantum-key-distribution systems with threshold detectors. Phys. Rev. A 78(3), 032302–032309 (2008)
Beaudry, N.J., Moroder, T., Lutkenhaus, N.: Squashing models for optical measurements in quantum communication. Phys. Rev. Lett. 101(9), 093601–093604 (2008)
Mayers, D.: Advances in Cryptology-Proceedings of Crypto. Springer, Berlin (1996)
Inamori, H., Lütkenhaus, N., Mayers, D.: Unconditional security of practical quantum key distribution. Eur. J. Phys. D. 41(3), 599–627 (2007)
KÄonig, R., Renner, R., Bariska, A., Maurer, U.: Small accessible quantum information does not imply security. Phys. Rev. Lett. 98(14), 140502–140505 (2007)
Wang, X.B.: Quantum error correction in spatially correlated quantum noise. Phys. Rev. Lett. 95(23), 230503–230506 (2005)
Meyer, T., Kampermann, H., Kleinmann, M., Bru\(\beta \), D.: Finite key analysis for symmetric attacks in quantum key distribution. Phys. Rev. A 74(4), 042340–042348 (2006)
Hayashi, M.: Upper bounds of eavesdropper’s performances in finite-length code with the decoy method. Phys. Rev. A 76(1), 012329–012344 (2007)
Hasegawa, J., Hayashi, M., Hiroshima, T., Tanaka, A., Tomita, A.: Experimental decoy state quantum key distribution with unconditional security incorporating finite statistics. arXiv.org:quant-ph, 0705.3081 (2007)
Scarani, V., Renner, R.: Quantum cryptography with finite resources: Unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100(20), 200501–200504 (2008)
Scarani, V., Renner, R.: Security bounds for quantum cryptography with finite resources, arXiv.org:quant-ph, 0806.0120 (2008)
Renner, R.: Security of quantum key distribution, PhD thesis, Diss. ETH No. 16242, Int. J. Quant. Inf 61 (2008)
Raymond, Cai, Q.Y., Scarani, V.: Finite-key analysis for practical implementations of quantum key distribution. New. J. Phys. 11(4), 045024 (2009)
Kraus, B., Gisin, N., Renner, R.: Lower and upper bounds on the secret-key rate for quantum key distribution protocols using one-way classical communication. Phys. Rev. Lett. 95(8), 080501–080504 (2008)
Devetak, I., Winter, A.: Distillation of secret key and entanglement from quantum states. Proc. R. Soc. Lond. A. 461(2053), 207–235 (2005)
Cover, T.M., Thomas, J.A.: Elements of Information Theory, Wiley Series in Telecommunications. Wiley, New York (1991)
Gobby, C., Yuan, Z.L., Shields, A.J.: Quantum key distribution over 122km of standard telecom fiber. Appl. Phys. Lett. 84(19), 3762–3674 (2004)
Wang, X.B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94(23), 230503–230506 (2008)
Acknowledgments
The work was supported by the National Natural Science Foundation of China (No. 11374096), the Education Ministry of Hunan province (No. 11A096), the Doctor Foundation (No. jsdxrcyjkyxm201104) and the Foundation (No. jd12039).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
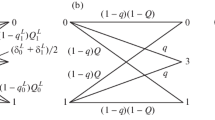
As shown in Fig. 1, the process of coherent pulses preparation (by Alice) and measurement (by Bob) states the following: The relatively strong coherent pulse \(\left| {\hbox {e}^{i\theta _0 }\sqrt{3\mu _1 }} \right\rangle \) in the path 0 is described by a field operator \(a_0^\dagger \). The transformation for \(a_0^\dagger \) in terms of the creation operators \(a_1^\dagger \) and \(a_2^\dagger \) of the upper and lower paths (labeled by 1 and 2, respectively) is
The transformation for \(a_2^\dagger \) in terms of the creation operators \(a_3^\dagger \) and \(a_4^\dagger \) (operators of BS\(_{2}\) for the paths 3 and 4) is
While the transformations for the operators \(a_1^\dagger \) and \(a_3^\dagger \) in terms of the creation operators \(a_5^\dagger \) and \(a_6^\dagger \) (operators of the BS3 for the paths 5 and 6) is, respectively, given by
Where \(\theta _1, \theta _2, \theta _3\) represent, respectively, the phase shift due to beam splitter reflection (for simplicity, another term of phase shift due to path length and the transmission in beam splitters are neglected). From the above discussion, we obtain the transformation operator of the QKD system:
where beam splitters are chosen such that the phase shift in the upper path compensates the phase shift in the lower path(\(\theta _1 +\theta _3 =\theta _2 )\). Then, if Alice prepares the state \(\left| {\hbox {e}^{i\theta _0 }\sqrt{3\mu _1 }} \right\rangle \) in the path 0, the outgoing state \(\left| {\psi _{lj}^{\prime } } \right\rangle \) in the paths 5 and 6 is given by
where \(\phi _{A_j }\) and \(\phi _{B_j}\) represents, respectively, the encoding phase modulation (used by Alice) and the decoding phase modulation (used by Bob). The outgoing state can also be written in the form
where \(\Delta \phi =\phi _{A_j } -\phi _{B_j }\) means the inner phase shift of two-beam interference. The state of the RP that enters D(2) is \(\left| {\hbox {e}^{i\theta _0 }\sqrt{\mu _1 }} \right\rangle \). It is easy to figure out that clicks will occur in detector D(0) if \(\phi _{A_j } =0, \phi _{B_j } =0\) or \(\phi _{A_j } =\pi /2, \phi _{B_j} =\pi /2\) and other results can be similarly obtained, while there will be random clicks in D(0) or D(1) with equal probability for the cases that unmatched phases for decoding are used by Bob and the corresponding bits will be discarded in key sifting procedures. From the above discussion, the specific form of the POVM elements for both the full optical measurement and the equivalent squashing model can be obtained.
Rights and permissions
About this article
Cite this article
Kang, G., Zhou, Q., Fang, M. et al. Asymmetric “4+2” protocol for quantum key distribution with finite resources. Quantum Inf Process 13, 5–20 (2014). https://doi.org/10.1007/s11128-013-0684-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0684-8