Abstract
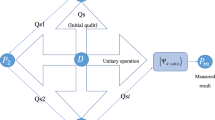
Secret sharing plays a fundamental role in both secure multi-party computation and modern cryptography. We present a new quantum secret sharing scheme based on quantum Fourier transform. This scheme enjoys the property that each share of a secret is disguised with true randomness, rather than classical pseudorandomness. Moreover, under the only assumption that a top priority for all participants (secret sharers and recovers) is to obtain the right result, our scheme is able to achieve provable security against a computationally unbounded attacker.
Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Blakley, G.R.: Safeguarding cryptographic keys. In: AFIPS, p. 313. IEEE Computer Society (1979)
Scherpelz, P., Resch, R., Berryrieser, D., Lynn, T.W.: Entanglement-secured single-qubit quantum secret sharing. Phys. Rev. A 84(3), 032303 (2011)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1999 (1829)
Gottesman, D.: Theory of quantum secret sharing. Phys. Rev. A 61(4), 042311 (2000)
Nascimento, A.C.A., Mueller-Quade, J., Imai, H.: Improving quantum secret-sharing schemes. Phys. Rev. A 64(4), 042311 (2001)
Tyc, T., Sanders, B.C.: How to share a continuous-variable quantum secret by optical interferometry. Phys. Rev. A 65(4), 042310 (2002)
Crépeau, C., Gottesman, D., Smith, A.: Secure multi-party quantum computation. In: Proceedings of the Thiry-Fourth Annual ACM Symposium on Theory of Computing, pp. 643–652. ACM (2002)
Hsu, L.Y.: Quantum secret-sharing protocol based on grovers algorithm. Phys. Rev. A 68(2), 022306 (2003)
Lance, A.M., Symul, T., Bowen, W.P., Sanders, B.C., Lam, P.K.: Tripartite quantum state sharing. Phys. Rev. Lett. 92(17), 177903 (2004)
Tokunaga, Y., Okamoto, T., Imoto, N.: Threshold quantum cryptography. Phys. Rev. A 71(1), 012314 (2005)
Markham, D., Sanders, B.C.: Graph states for quantum secret sharing. Phys. Rev. A 78(4), 042309 (2008)
Li, Q., Chan, W.H., Long, D.Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Dolev, S., Pitowsky I., Tamir, B.: A Quantum Secret Ballot. arXiv, preprint quant-ph/0602087 (2006)
Katz, J., Lindell, Y.: Introduction to Modern Cryptography. Chapman & Hall, Boca Raton (2008)
Goldreich, O.: Secure Multi-Party Computation. Working Draft. Version 1.3 (2001)
Nielsen, M.A., Chuang, I., Grover, L.K.: Quantum computation and quantum information. Am. J. Phys. 70, 558 (2002)
Weinstein, Y.S., Pravia, M.A., Fortunato, E.M., Lloyd, S., Cory, D.G.: Implementation of the quantum fourier transform. Phys. Rev. Lett. 86(9), 1889–1891 (2001)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM (JACM) 48(3), 351–406 (2001)
Lo, H.K., Chau, H.F., Ardehali, M.: Efficient quantum key distribution scheme and a proof of its unconditional security. J. Cryptol. 18(2), 133–165 (2005)
Holevo, A.S.: Bounds for the quantity of information transmitted by a quantum communication channel. Probl. Pered. Inform. 9(3), 3–11 (1973)
Csirmaz, L.: The size of a share must be large. J. Cryptol. 10(4), 223–231 (1997)
Jeffrey, A., Dai, H.H.: Handbook of Mathematical Formulas and Integrals. Academic Press, London (2008)
Acknowledgments
We would like to thank the anonymous reviewer for helpful suggestions. This work was supported by the National Natural Science Foundation of China (No. 60903217), the Fundamental Research Funds for the Central Universities (No. WK0110000027), and the Natural Science Foundation of Jiangsu Province of China (No. BK2011357).
Author information
Authors and Affiliations
Corresponding author
Appendix: Proof of Equation (8)
Appendix: Proof of Equation (8)
The case that \(\zeta =N\) if \(K = 0\) mod \(N\) is obvious, thus we only focus on the proof of \(\zeta =0\) if \(K \ne 0\) mod \(N\). When \(K \ne 0\) mod \(N\), we know that
Let \(\frac{2\pi K}{N}=t\), then Eq. (11) can be rewritten as
It is not hard to verify and prove the following two Lagrange’s trigonometric identities [25]:
and
Now we consider the first item of the right side of Eq. (12) using (13):
The last step of (15) holds iff \(K \ne 0\) mod \(N\).
Similarly, we can get that \(\sum _{j=0}^{N-1} \sin {jt}=0\) using (14) with \(K \ne 0\) mod \(N\).
So far, we can safely reach the conclusion that \(\zeta =0\) iff \(K \ne 0\) mod \(N\) and thus Eq. (8) follows.
Rights and permissions
About this article
Cite this article
Yang, W., Huang, L., Shi, R. et al. Secret sharing based on quantum Fourier transform. Quantum Inf Process 12, 2465–2474 (2013). https://doi.org/10.1007/s11128-013-0534-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0534-8