Abstract
We numerically study a new hardware method for network authentication, using a pair of chaotic lasers subject to the same optical injection from a third chaotic laser, in a close-loop configuration. One laser is in the secure environment, the other is in the unsecure environment, and if their parameters are matched (i.e., they are ‘twins’), in suitable operating conditions they synchronize and generate the same pseudo-random amplitude modulation. Access to the secure environment is authorized only if the two responses are found equal. As in other schemes based on Physical Unclonable Functions (PUFs), security relies on unavoidable small differences between nominally identical but physically separate devices: due to the strong sensitivity of chaos to laser parameter dispersion, finding a suitable laser to synchronize is a very difficult task for the Adversary, while the laser of the Authorized user can be selected as a twin of the one in the secure environment.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Challenge-response authentication schemes based on Physical Unclonable Functions (PUFs) have been proposed and are being actively investigated as an alternative to standard authentication protocols, especially for the Internet of Things (IoT) applications (Shamsoshoara 2020, Velasquez 2018, Suh 2007, Babaei 2019, Idriss 2016, Mall 2022, Najafi 2009, Gao 2022, Zang 2014). With PUFs, authentication is based on secrets, which are produced in the unsecure environment from complex physical characteristics of integrated circuits or other electronic devices, and which are the response to a specific stimulus (challenge) sent from the secure environment. The main advantage of these methods is that they provide a good security level, without requiring neither to store the key in the unsecure environment nor extended computation capabilities, which is important especially on the user (unsecure) side.
In the optoelectronic domain, semiconductor lasers are interesting candidates for such hardware-based method of authentication, because of the dispersion of their parameters. Lasers in the chaotic regime are especially suitable to this scope, because of the strong sensitivity of chaos to parameter variations.
A semiconductor laser can be routed to chaos by delayed optical feedback provided by back-reflection from a local mirror, or by injection from another laser. Chaos in lasers has been extensively analyzed since the last 1990s, both theoretically and experimentally, finding bifurcation diagrams and attractors (Annovazzi-Lodi 1994, Annovazzi-Lodi 1998, Ohtsubo 1999, Ryan 1994, Masoller 1995, Kanno 2012). Applications of chaos to secure transmission of data have been investigated starting from the early 2000s (Donati 2002, Larger 2004, Argiris 2005). An important characteristic of the chaotic regime is that two lasers never produce the same chaotic waveform, (i.e., the same pseudo-random amplitude modulation, which, for telecommunication lasers, is typically in the GHz range), unless they are synchronized. Different schemes have been proposed to synchronize two lasers in the chaotic regime (Donati 2002, Larger 2004). A fundamental condition, to obtain a stable and robust synchronization, is that the lasers must be ‘twins’, i.e., they must have very well matched, almost identical, parameters. This can be obtained by selecting them from the same wafer, which is possible only for the Authorized user. For the Adversary, instead, it is very difficult to generate an identical chaotic waveform, because of the unavoidable differences between nominally identical but physically different devices.
This property has been already exploited in chaos-secured communication experiments (Donati 2002, Larger 2004). Different methods have been investigated to hide a message in chaos, and chaos-protected digital transmission on a metropolitan network (Argiris 2005) has been demonstrated years ago. Integrated optics cryptosystems have been also designed and manufactured (Syvridis 2009).
In a previous paper (Annovazzi-Lodi 2022), a challenge-response authentication scheme has been proposed, which is inspired by the so-called three-laser chaos-protected transmission scheme (Yamamoto 2007, Annovazzi-Lodi 2010, Annovazzi-Lodi 2011, Uchida 2003, Oowada 2009) in which synchronization is obtained by driving the two lasers (called Slaves, SL) by the common optical injection of a third chaotic laser (Driver, DRV).
In transmission applications, two main topologies have been considered so far in the literature (Donati 2002, Larger 2004): the close loop, when the isolated SL lasers are already chaotic, and the open loop, where they are chaotic only due to injection from DRV.
In (Annovazzi-Lodi 2022), only the basic open loop has been evaluated in detail for authentication. However, in transmission applications it has been demonstrated that the close loop offers a much better security level, because it has more parameters to be optimized and stricter tolerances to match (Donati 2002, Larger 2004, Annovazzi-Lodi 2011). In (Annovazzi-Lodi 2022) the close loop has been only preliminarily considered without sweeping parameters. In (Lombardi 2022), the close loop has been addressed by sweeping parameters, but only in selected cases.
Thus, we have now studied the close loop in detail, to check if the increased complexity of the scheme results into a better performance in terms of security also when applied to authentication.
A specific advantage of our approach is that both the challenge and the responses are generated on the fly in both environments, and thus they do not need to be stored, not even in the secure environment. Moreover, the challenge changes at every attempt in a virtually random way.
A preliminary numerical evaluation on the validity of this approach could open the route to a new PUF based authentication method, which could then be investigated in detail both theoretically and experimentally. This is the goal of our contribution.
2 The authentication scheme
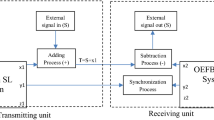
In Fig. 1 we show the proposed scheme of challenge-response authentication with chaotic lasers.
The driver laser DRV is routed to chaos by delayed optical feedback, provided by an external mirror M, and injects (this is the challenge) two Slave lasers: SL1, in the secure environment, and SL2 in the unsecure environment. Slave lasers also work in the chaotic regime, due to delayed optical feedback produced by local mirrors (M). If SL1, SL2 are twins, in suitable operating conditions they synchronize, i.e., they produce the same chaotic modulation. A bit sequence can be easily obtained from the chaotic waveform by photodetection and electronic processing. The response in the unsecure environment is the bit stream produced by Slave SL2. The reference response in the secure environment is the bit stream generated by SL1. Only if the responses match (as detected by the EXOR block), authorization is granted.
As usual with PUFs, a small number of errors in the response bit sequence must be tolerated, because synchronization is never perfect in practice. A threshold is to be defined, to offer a probability of success of (or next to) 100% to the Authorized user, while keeping the probability of success of the Adversary as low as possible.
This can really be obtained, in practice, not only because the Authorized user can own a SL2 laser which is twin to SL1, while getting a matched laser is a very difficult task for the Adversary; moreover, the Authorized user can train his system, by optimizing pump current and optical injection to minimize errors, before using it in the field (Annovazzi-Lodi 2022). This is not possible for the Adversary, who can only sweep his parameters, trying many different lasers and working points. As already observed, the responses need not to be stored, not even in the secure environment, but they are produced on the fly, which improves security.
3 Numerical model
The well-known Lang-Kobayashi model (Lang 1980) is used to describe the lasers. The set of equations for the driver and the two slave lasers of the setup of Fig. 1 is the same used for the three-laser chaos-protected transmission (Annovazzi-Lodi 2011), without, however, including a message. The different devices are described by varying index J in Eqs. 1–3:
For J = D, we have the equations describing the DRV dynamics, while for J = 1 and J = 2 we have the equations describing the SL1 and SL2 dynamics, respectively. Coefficient ΔD,J is zero for J = D, otherwise it is ΔD,J = 1.
In these equations, EJ(t) is the slowly varying, complex electric field, NJ(t) the carrier density, GJ(t) the linear gain coefficient, the pump current, e the electron charge and KJ, τ are the feedback parameter and the time of flight to the external mirrors. For J = T,R the terms KD,J/τin and TD,J represent the injection rate and the propagation time from the driver into transmitter and receiver, respectively. For simplicity, in the simulations we have taken TD,T = TD,R = 0. Other parameters are defined in Table 1.
The Langevin noise terms LEj(t) LEJ(t) and LNj(t) (Ju 2004), are given by:
where \(R_{sp} = {{\beta N_{J} \left( t \right)\Gamma } \mathord{\left/ {\vphantom {{\beta N_{J} \left( t \right)\Gamma } {\tau_{s} }}} \right. \kern-0pt} {\tau_{s} }}\) is the spontaneous emission rate.
The terms\(\chi_{e}\), \(\chi_{\phi}\) and \(\chi_{n}\) are time series with zero-mean, unit-variance Gaussian distribution, and Δt is the time resolution in the modeling of white noise.
It is worth noting that the equation set 1–3 differs from that of the open-loop scheme (Annovazzi-Lodi 2022) for the inclusion of a term describing the reflection from each laser mirror in the equations for the electric fields (second term in Eq. 1).
As usual, the electric fields are normalized in (m−3/2). The true value of each electric field (in [V/m]) is given by:
where \(\hbar\) is the Planck’s constant, Z0 = (1/ε0c) the vacuum impedance, ε0 the vacuum permittivity and c the speed of light. The photodetected currents of PD1, PD2 are obtained by computing \(I = \sigma AZ_{0}^{ - 1} \left| {E_{True} \left( t \right)} \right|^{2}\) for both SL1 and SL2.
In the next Section, we report the numerical results obtained with this model. In all simulations, in addition to the Langevin noise, the photodetector noise has been taken into account. This has been done by assuming Johnson noise and shot noise as white Gaussian processes of variance 4KBTB/R and 2e < I > B, respectively, where KB is the Boltzmann constant, T is the absolute temperature (T = 300 K), R is the load resistance (R = 50 Ω) and < I > is the mean detected current. For the simulations, time samples for each noise source have been obtained by a standard numerical routine.
In our previous paper (Annovazzi-Lodi 2022) the proposed authentication method was evaluated in the open loop (Kj = 0 for both SLs). The parameters of DRV and SL1,2, and the working point, were optimized to obtain a robust synchronization. Then, the main internal parameters, i.e., the linewidth enhancement factor α, the carrier lifetime τs, the photon lifetime τp, the gain coefficient \(\xi\) had been swept in numerical simulations from 1 to 10%, to test different levels of mismatch of SL2 with respect to SL1. For each combination of the internal parameters, the external parameters of the lasers, i.e., the supply current and the injection from the DRV, were also varied, on more that 16 million combinations.
In the present analysis, two more parameters have been added to describe the close loop, i.e., the reflectivity Kj of the mirrors in front of each slave laser, and the time of flight τ from each mirror to its laser. Figure 2 shows the chaotic waveforms generated by the DRV, SL1 and SL2 in a typical close loop simulation. The time series generated by the SLs are identical since the lasers are twins in this case. The time series generated by the DRV is significatively different, since this laser has been intentionally selected to be unmatched with respect to SL1,2. This is required to prevent the Adversary from recovering the bit stream directly from processing the DRV emission.
For the Authorized user, who can select the laser, we have assumed a parameter mismatch of 2%, while for the Adversary the assumed mismatch was from 3 to 10%. For each internal parameter combination, the external parameters of the lasers have been also varied, as for the open loop. For the Authorized user, who can train his system, the error number was minimized by properly selecting the external parameters, while, for the Adversary, these parameters were simply swept, and all combinations were added to the statistics.
In principle, all the parameters of the close loop should be swept in the numerical analysis, getting a total number of more than 56 million combinations for each single percentage of mismatch. Due to the large number of combinations, we have begun by assuming, as a reasonable starting point, a 2% mismatch for the Authorized user, and a 5% for the Adversary, as often done with chaos-protected transmission. For these two values, all parameter combinations have been tested. For the other cases, to reduce the machine time, we have first considered the results obtained with constant nominal values for the two new parameters. From them, we have selected the combinations giving the least number of errors, and only for these lasers we have swept the two new parameters, for approximately 7 million combinations per laser. In this way, we have been able to get the results for a mismatch of 3, 4, 7 and 10% in a relatively short time.
For 2% (Authorized) and 5% (Adversary) the number of detected errors is reported in Table 2, for a 128-bit sequence (2 ns bit time) obtained from the chaotic waveforms with a low-pass filter followed by a comparator to obtain a two-level signal (where the time of each level over the full sequence is approximately the same), which is then sampled by a clock. In Fig. 3 the reference response SL1, in the secure environment, is shown together with those of the Authorized user (SL2, in optimized condition), and of the Adversary (SL2, typical case).
The results for the open loop (Annovazzi-Lodi 2022) are also shown in Table 2, for comparison.
From Table 2, we would like to point out the difference in the performance of the Authorized user vs. the Adversary, which is large for both the open and the close loop. Even if for the Adversary the minimum error number is low, because sweeping parameters occasionally results in a well performing device, this event is very unlikely (Fig. 4). The mean error number is very small, instead, for the Authorized user.
Finally, we have calculated (Table 3) the authentication success rate, for different levels of mismatch.
As already observed, this implies to define a maximum acceptable error number. From Table 2, for 2% mismatch at least 7 errors should be tolerated, in order to obtain a success rate of 100%, for the Authorized user with the close loop. Even if we select a threshold of 9 errors, to get some margin, the success rate of the Adversary with 5% mismatch is only 0.0004%. In comparison, the open loop (Annovazzi-Lodi 2022) performs, with the same mismatch levels and a 6-error threshold, an authentication success of 0.004% (i.e., ten times lower) for the Adversary, while it is 100% for the Authorized user.
Similar results have been obtained with different mismatch levels for the Adversary, which are also shown in Table 3.
From these outcomes, we conclude that the proposed scheme is well performing in both versions, and thus it represents a new promising method of network authentication. Moreover, based on the new available data, the close loop is found to offer a significative improvement vs. the open loop. Thus, the close loop scheme should be considered for applications where the security improvement it offers overcompensates the increased complexity of the setup.
Following the numerical analysis, next step will be the experimental evaluation of the authentication scheme. We are confident that both versions can be successfully implemented, based on the experiments already performed on similar setups in chaos-secured transmission (Donati 2002, Larger 2004, Annovazzi-Lodi 2011). In these papers stable synchronization is demonstrated and since the time series of chaos are matched (they can be subtracted almost to zero), we expect that also bit sequences obtained from them should be equal, but for a small percentage of occurrences. As in (Syvridis 2009) a suitable photonic integration technology could be considered to produce a conveniently compact and stable system.
About the statistical properties of the authentication key obtained by our method, the digital sequence should reflect the characteristics of chaos, i.e., it should be pseudo-random. However, the exact statistics is expected to depend on the source characteristics and working point, as well as on the electronic processing (Li 2019, 2022, Aromataris and Annovazzi-Lodi 2012), and thus it should be evaluated in a real implementation.
4 Conclusions
In this paper we have proposed an authentication method based on twin chaotic lasers, synchronized by the common optical injection from a third chaotic laser. Our numerical analysis demonstrates the good performance of both the open and the close loop version of our scheme. However, the results for the close loop, where both lasers are chaotic even before injection, are far better than for the open loop, in spite of a somewhat more complex setup. Based on our findings, we conclude that the proposed scheme represents a promising approach for a new authentication method.
Data availability
All relevant data generated or analysed during this study are included in this published article.
Code availability
Custom code developed in Matlab is available on request.
References
Annovazzi-Lodi, V., Donati, S., Manna, M.: Chaos and locking in a semiconductor laser due to external injection. IEEE J. Quantum Electron. 30(7), 1537–1541 (1994)
Annovazzi-Lodi, V., Scirè, A., Sorel, M., Donati, S.: Dynamic behaviour and locking of a semiconductor laser subjected to external injection. IEEE J. Quantum Electron. 34(12), 2350–2357 (1998)
Annovazzi-Lodi, V., Aromataris, G., Benedetti, M., Merlo, S.: Private message transmission by common driving of two chaotic lasers. IEEE J. Quantum Electron. 46(2), 258–264 (2010)
Annovazzi-Lodi, V., et al.: Close-loop three-laser scheme for chaos-encrypted message transmission. Opt. Quantum Electron. 42(3), 143–156 (2011)
Annovazzi-Lodi, V., Lombardi, L., Aromataris, G.: Challemge-response authentication scheme with chaotic lasers. IEEE J. Quantum Electron. 58(1), 2000107 (2022)
Argyris, A., et al.: Chaos-based communications at high bit rates using commercial fiber-optic links. Nature 438, 343–346 (2005)
Aromataris, G., Annovazzi-Lodi, V.: Error analysis of a digital message impaired by optical chaos. IEEE Photonics Techn. Lett. 24(11), 903–905 (2012)
Babaei, A., Schiele, G.: Physical unclonable functions in the internet of things: state of the art and open challenges. Sensors 19, 3208 (2019)
Bin, G.B., et al.: Concealable physically unclonable function chip with a memristor array. Sci. Adv. 8, eabn7753 (2022)
Donati, S., Mirasso, C.R.: Feature section on optical chaos and applications to cryptography. IEEE J. Quantum Electron. 38(9), 1137–1196 (2002)
Idriss T., Idris H., Bayoumi M.: A PUF-based paradigm for IoT security. In: Proc. IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, 700–705 (2016)
Ju, R., Spencer, P.S., Shore, K.A.: The relative intensity noise of a semiconductor laser subject to strong coherent optical feedback. J. Opt. B Quantum Semiclassical Opt. 6(8), S775–S779 (2004)
Kanno, K., Uchida, A.: Consistency and complexity in coupled semiconductor lasers with time-delayed optical feedback. Phys. Rev. E 86, 066202 (2012)
Lang, R., Kobayashi, K.: external optical feedback effects on semiconductor injection laser properties. IEEE J. Quantum Electron. 16(3), 347–355 (1980)
Larger L., Goedgebuer J.P., (Editors): Special Number on Criptography using Optical Chaos. Comptes Rendus de l'Academie des Sciences-Dossier de Physique 6(5), 609–681 (2004)
Li, X.Z., Chan, S.C.: Detection dependencies of statistical properties for semiconductor laser chaos. IEEE J. Sel. Topics Quantum Electron. 25(6), 1501209 (2019)
Li, X.Z., Zhou, X., Gu, Y., Zhao, M.: Numerical study of statistical properties for semiconductor laser chaos by exploring the injection parameter space. IEEE J. Sel. Topics Quantum Electron. 28(1), 0600108 (2022)
Lombardi L., Annovazzi-Lodi V., Aromataris G.: Network authentication with synchronized chaotic lasers. In: Proc. NUSOD 2022, 22nd International Conference on Numerical Simulation of Optoelectronic Devices, IEEE, Torino, pp. 19–20 (2022)
Mall, P., Amin, R., Das, A.K., Leung, M.T., Choo, K.K.R.: PUF-based authentication and key agreement protocols for IoT, WSNs, and smart grids: a comprehensive survey. IEEE Int. Things J. 9(11), 8205–8228 (2022)
Masoller, C., Sicardi Schifino, A.C., Cabeza, C.: The nonlinear gain and the onset of chaos in a semiconductor laser with optical feedback chaos. Solit. Fract. 6, 347–356 (1995)
Najafi, F., Kaveh, M., Martín, D.: Deep PUF: a highly reliable DRAM PUF-based authentication for IoT networks using deep convolutional neural networks. Sensors 21(6), 2009 (2021)
Ohtsubo, J.: Feedback induced instability and chaos in semiconductor lasers and their applications. Opt. Rev. 6(1), 1–15 (1999)
Oowada, I., et al.: Synchronization by injection of common chaotic signal in semiconductor lasers with optical feedback. Opt. Express 17(12), 10025–10034 (2009)
Ryan, A.T., Agrawal, G.P., Gray, G.R., Gage, E.C.: Optical-feedback-induced chaos and its control in multimode semiconductor lasers. IEEE J. Quantum Elecron. 30(3), 668–679 (1994)
Shamsoshoara, A., Korenda, A., Afghah, F., Zeadally, S.: A survey on physical unclonable function (PUF)-based security solutions for Internet of Things. Comput. Netw. 183, 107593 (2020)
Suh G. E., Devadas S.: Physical Unclonable Functions for Device Authentication and Secret Key Generation. In: Proc. 44th ACM/IEEE Design Automation Conference, San Diego, CA, 2007, 9–14 (2007)
Syvridis, D., Argiris, A., Bogris, A., Hamacher, M., Giles, I.: integrated devices for optical chaos generation and communications applications. IEEE J. Quantum Electron. 45(11), 1421–1428 (2009)
Uchida, A., Davis, P., Itaya, S.: Generation of information theoretic secure keys using a chaotic semiconductor laser. Appl. Phys. Lett. 83, 3213–3215 (2003)
Velasquez, I., Caro, A., Rodriguez, A.: authentication schemes and methods: a systematic literature review. Inf. Softw. Technol. 94(1), 30–37 (2018)
Yamamoto, T., et al.: Common-chaotic-signal induced synchronization in semiconductor lasers. Opt. Express 15(7), 3974–3980 (2007)
Zhang, L., et al.: Exploiting process variations and programming sensitivity of phase change memory for reconfigurable physical unclonable functions. IEEE Trans. Inform. Forensic Security 9(6), 921–932 (2014)
Funding
Open access funding provided by Università degli Studi di Pavia within the CRUI-CARE Agreement. This work was funded by the Department of Electrical, Computer and Biomedical Engineering of the University of Pavia, Pavia, Italy.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Code preparation was performed by LL and GA. The first draft of the manuscript was written by VAL and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflicts of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Lombardi, L., Aromataris, G. & Annovazzi-Lodi, V. Network authentication by close-loop synchronized chaotic lasers. Opt Quant Electron 55, 326 (2023). https://doi.org/10.1007/s11082-023-04640-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11082-023-04640-z