Abstract
In this paper, the occurrence of ghost attractor is verified in three cases of a proposed fractional order Rössler blinking system. Firstly, the dynamical behaviors of the short memory fractional order prototype-4 Rössler system with Chua’s diode are explored via bifurcation diagrams and Lyapunov exponents. It is depicted that this system exhibits a variety of dynamics including limit cycles, period doubling and chaos. Then, a proposed non-autonomous fractional order Rössler blinking system is introduced. Numerical simulations are employed to confirm the existence of ghost attractors at specific cases which involve very fast switching time between two composing autonomous fractional subsystems. It is found that the presented fractional order blinking system is very sensitive to system parameters, initial conditions, and stochastic process parameters. Thus, the induced chaotic ghost attractor is utilized in a suggested ghost attractor-based chaotic image encryption scheme for first time. Finally, a detailed security analysis is carried out and reveals that the proposed image cryptosystem is immune against different types of attacks such as differential attacks, brute force attacks, cropping and statistical attacks.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
In recent decades, the applications of fractional calculus in the area of dynamical systems have attracted great interest. Indeed, many theoretical and experimental studies indicated that fractional order derivatives have many advantages in modeling intricate systems in contrast to conventional treatment using integer order calculus [1]. The essential reason is that fractional derivative possesses hereditary properties and can mimic memory effects in some nonlinear systems [2]. So, fractional order differential equations have successfully modeled many real applications, such as neural networks [3, 4], biological systems [5, 6], financial systems [7, 8], secure communications [9], electronic circuit models [10,11,12], nonlinear mechanical problems [13, 14] and many more. The fractional order differential equations with chaotic behaviors can be physically realized using op-amp-based approximations of fractional-order integrators or embedded circuits uses FPGAs or DSPs [15,16,17,18]. Fractional order switched system which includes switching parameter based on logical rule has recently drawn the attention of several researchers [19, 20].
Switched system is a hybrid dynamical system that is composed of a number of dynamical subsystems and has a specific rule to control the switching between its subsystems with time [21, 22]. Stochastic processes are usually employed to externally drive these blinking non-autonomous systems at the specified values of switching time scales. More specifically, there is a predetermined fixed period of time \( \tau \) through which the dynamics of blinking system is determined by one of its composing subsystems then a random switching to another subsystem is done for the same time interval \( \tau \) and the process continues in this way as long as the blinking system is running. The blinking systems have appeared in many realistic models in biology, the internet networks, and circuits like power converters where the connections are randomly switched on and off in time. Assuming that the blinking system has n subsystems, the coupling between subsystems in each time interval of duration \( \tau \) is done stochastically with probability \( p_i, i=1,2,...,n \).
In blinking systems, there are two time-scales belonging to the stochastic process and the blinking system itself. In fast-switching blinking systems, the time scale of stochastic process is much faster than intrinsic time scale of the dynamical subsystems of the blinking system. This means that the switching is considered to be fast according to its value in comparison with intrinsic time scale of the blinking system [23]. The switching occurs randomly and independently for different time intervals and connections in the system. It is found that the blinking systems can exhibit non-trivial and unexpected nonlinear behaviors which surprisingly do not exist in each of the composing subsystems [24]. The averaged systems associated to the blinking systems which are given by the expectation of stochastic variables have attractors called ghost attractors of the blinking systems if they are different from the set of attractors in the composing subsystems [25].
Up to now, the study and investigation of blinking systems have been reported in few works. For example, Belykh et al. [26] showed an example of a blinking system and the corresponding synchronization in small-world networks. Barabash and Belykh [24] proved the existence of ghost attractors for certain parameter ranges in the blinking piecewise-linear Lorenz-type system being unexpectedly different with respect to the attractors of composing systems. Levanova et al. [25] obtained a ghost attractor in blinking Lorenz and Hindmarsh-Rose systems in spite of the trivial dynamics of the associated subsystems at selected values of parameters which is defined by stable equilibrium points. Hasler et al. [27], investigated the dynamics, finite time properties and asymptotic properties of a stochastically blinking system. The authors proven that any trajectory of the blinking system closely follows the trajectory of the averaged system, starting from the same initial condition, during a certain interval of time T when the switching is fast enough. They reported an explicit relation between the distance between the two trajectories, the switching time, and the length of the time interval T. Hasler et al. [28], discussed the relation between the trajectories of the averaged and blinking systems when time goes to infinity. They demonstrated that two trajectories usually cannot stay together, but they may converge to the same attractor. The work in [27, 28] can be extended to fractional order in separate paper as a future work.
In recent years, because of the rapid development of multimedia technologies and the increased exchange of multimedia data over the internet, the need to devise effective tools to make the transmitted multimedia secured and well preserved is becoming increasingly important [29]. Images have main features such as redundancy, a strong correlation between adjacent pixels, and a large amount of data. According to these features, the need to encryption schemes suitable for image encryption rather than traditional encryption algorithms such as DES, AES and RSA [30] for text encryption is required. In the last decades, researchers have developed algorithms based on chaos theory that are suitable for images encryption [31,32,33]. Chaotic systems are extremely sensitive to control parameters and initial values. In additions, inherent characteristics such as unpredictability, pseudo-randomness and ergodicity are employed for keystream generation [34, 35]. The required cryptographic characteristics through image diffusion and confusion can be achieved through the fascinating features of the image encryption techniques relying on chaotic systems [36]. The applicability of the fractional order chaotic systems and fractional order chaotic maps to image encryption are investigated to further enhance the security of the cryptosystem and increase key-space in several articles [37,38,39,40]. Chaos based encryption algorithms can be used in authentication systems for safely storing vital images in database [41].
It is worth mentioning that all the aforementioned works are only concerned with blinking systems in integer order forms. Inspired by the above discussion, the main contribution of this paper is to study fractional order blinking system composed of two fractional order Rössler prototype-4 autonomous continuous time subsystems based on Chua’s diode nonlinearity. Random switching between internal parameters of the proposed system occurs stochastically and evolves over time. To the best of authors knowledge, this first time to explore of the ghost attractor in fractional order blinking systems. This work is organized such that firstly, the short memory fractional order Rössler system is studied using Lyapunov spectrum, bifurcation diagrams. Secondly, a fractional order blinking system is presented in three cases involving different values of intrinsic parameters of the fractional order Rössler system. The randomly and rapidly switching time between two values of fractional blinking system parameter is verified to yield a chaotic attractor which goes near the chaotic ghost attractor of the associated fractional order averaged system. Detailed numerical simulations are utilized to explore chaotic ghost attractors. Thirdly, fractional order blinking system is considered for the first time to present an image encryption scheme to improve cryptosystem security and further increase the secret key space. Finally, the proposed scheme is analyzed by several security tests to show the immunity against different attacks.
The layout of this paper is structure as follows: The mathematical preliminaries and definitions are summarized in Sect. 2. The fractional order blinking Rössler system is introduced in Sect. 3 along with its detailed numerical investigation. In Sect. 4, the chaotic image encryption scheme based on fractional order blinking system is proposed and the security analysis is conducted. The discussion and future work are concluded in Sect. 5.
2 Mathematical preliminaries
This section addresses the definition of fractional order Caputo derivative, the definition of short memory fractional differential equation, the definition of fractional blinking system and the associate fractional order averaged system.
Recently, many definitions for fractional order derivatives have been well-established. We focus on the Caputo fractional derivative [1]. The Caputo fractional derivative of order \(\alpha \) of function f(t) is defined as follows
where \( \Gamma (.) \) is the Gamma function.
The standard fractional order system in Caputo sense is defined as follows [42]
where \( t_{0} \) is a fixed starting point of the fractional derivative.
2.1 Definition of short memory fractional order system
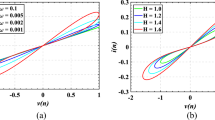
The standard fractional order system (2) holds the memory from \( t = t_{0} \). The weight coefficients of \( x(t_{0}) \) become smaller as the time t increases. The meaning of short memory is summarized in Fig. 1 [43].
Let the interval \( [t_{0}, T] \) is divided to m subinterval with length nh and n is an integer number such that \( [T - t_{0}] = [t_{0}, t_{l}] \cup [t_{l}, t_{2}] \cup ... \cup [t_{(m-1)}, t_{m}], h = (T - t_{0})/N \). In the first subinterval \( t \in [t_{0},t_{1}] \), the fractional order system is described as \( ^{C}_{t_{0}}D_{t}^{\alpha } x(t) = f(t,x) \), then in the second subinterval \( t \in [t_{1},t_{2}] \), the fractional order system is described as \( ^{C}_{t_{1}}D_{t}^{\alpha } x(t) = f(t,x) \) so, the intial point is updated to \( t_{1} \) and so on until the last subinterval.
Subsequently, the short memory fractional order system which holds short memory effect is defined as follows [43]
The Eq. (3) has different initial points \( t_{*} \) in the Caputo fractional derivative (1). This provides more freedom degrees in real-world applications.
2.2 Definition of the fractional order blinking system
The blinking system is presented in [27, 28] and it is defined in the form of time dependent ordinary differential equations. Here, we generalize the concept to the fractional order blinking system by defining it as
where \( ^{C}_{t_{*}}D_{t}^{\alpha } \) is a short memory derivative and the function s(t) is a binary random constant discrete scalar value such that \( s^{i} = (s_{1}^{i},..., s_{M}^{i}) \) with the probability \( p_{i} \) at each \( i^{th} \) time piecewise constant in the time interval \( [i\tau , (i+1)\tau ]\) and \( \tau \) is a constant switching period. All variables \( s_{j}^{i} \) are random variables and independent and they take the value 1 with probability p and the value 0 with probability \( 1-p \). So, the switching sequence of the stochastic process is determined according to s(t) . Hence this system is considered as a special case of random dynamical systems and its solution also is a stochastic process. The signal \( s_{i} \) can be viewed as a closing and opening eye lid therefore, the system (4) is called a blinking system. The trajectories of M autonomous systems are blinded together at \( t = i \tau \) to consist the trajectories of system (4). In this type of system, there are two-time scales which are the one associated with the dynamical system itself and the other of the switching process. In this work, the switching process is considered to be much faster than the dynamical subsystems.
2.3 Definition of the fractional order averaged system
The fractional order averaged system associated with the fractional order blinking system (4) reads as
where
and E(f(x, s)) denotes the average or expected value of f(x, s) .
3 Proposed fractional order blinking systems
3.1 Fractional order prototype-4 Rössler system with short memory
We propose the following fractional order version of the prototype-4 Rössler system with short memory [44] as follows
where \( q, \beta \) and \( \gamma \) have positive values and g(y) is a piecewise-linear function with definition as
where \( m_{0} \) and \( m_{1} \) are constants. Nonlinearity in (7) is known as a nonlinear component which called the Chua’s diode [45]. We call (7) a short memory fractional differential equation since the fractional derivative is defined from \( t_{*} \) not from the fixed \( t_{0} \) or 0.
3.1.1 Stability analysis
For the fractional order model (7), the phase space S can be divided into three linear subsets as follow:
Let \(D^{\alpha }_{t} x = D^{\alpha }_{t} y = D^{\alpha }_{t} z = 0\). The equilibrium points are studied so, the system Eq. (7) has three equilibrium points as \(E_{\mp } =(0 , \mp q \upsilon , \pm \upsilon ) \) and \( E_{0} = (0,0,0) \), where \( \upsilon = \frac{m_{1} - m_{0}}{q m_{1} + \gamma } \) with condition \( \gamma \ne - q m_{1} \) to avoid infinite coordinates. The system has the next Jacobian matrix:
with \( m _{i} = m _{0} \) in \( S _{0} \) and \( m _{i} = m _{1} \) in \( S _{\mp } \). The Jacobian matrix has a characteristic equation as follow
Based on the stability criterion of fractional Routh Hurwitz [46], if the system (7) has \( |arg (\lambda _{i}(J))|> \dfrac{\alpha \pi }{2} , \forall \lambda _{i} , i = 1,2,3\) where \( \lambda _{i} \) is an eigenvalue of matrix J then the system is locally asymptotically stable at the associated equilibrium point.
To get the stability region for system (7) depending on its parameter, we solve characteristic equation (9) and based on the stability condition \( |arg (\lambda _{i}(J))|> \dfrac{\alpha \pi }{2} , \forall \lambda _{i} , i = 1,2,3\). The stability region for the system in the phase space \( S_{0} \) and their dependance on different parameters are depicted in Fig. (2) and in the phase space \( S_{\mp } \) is displayed in Fig. 3.
Phase portrait for the system (7) with different parameter values. a \( m_0 = -1.4, \gamma =2.2 \), b \( m_0 = -1.4, \gamma =0.65 \), c \( q= 0.2 , \gamma = 0.8 \), d \( q =4.2 , \gamma = 0.8 \), e \( m_1 = 0.3, \gamma =2.5\), (f) \( m_1 = 0.3, \gamma =0.5 \)
To solve (7) numerically, starting from initial conditions at \( t =0 \) and updating initial conditions at each stage. We can get each subsystem as follows. For \( t \in ( 0,t_{1}) \) and the initial conditions \((x_{0},y_{0},z_{0})\) are known, we solve the following subsystem
Then, for \( t \in [ t_{k}, t_{k+1}]\) with \( (x_{k},y_{k},z_{k})\) is known from the system on \([ t_{k-1}, t_{k}]\) and we get the subsystem
We solve the system (7) numerically with some parameters values to confirm the stability region. In Fig. 2, the stability region based parameters on \( m_0 \) and \( \gamma \) is verified by phase portrait with \( m_0 = -1.4, \gamma =2.2 \) and \( m_0 = -1.4, \gamma =0.65 \) as displayed in Fig. 4a and b, respectively. Also, the stability region based on parameters q and \( \gamma \) is confirmed by phase portrait with \( q= 0.2 , \gamma = 0.8 \) and \( q =4.2 , \gamma = 0.8 \) as shown in Fig. 4c and d, respectively. In Fig. 3, the stability region based on parameters \( m_1 \) and \( \gamma \) is verified by phase portrait with \( m_1 = 0.3 ,\gamma =2.5\) and \( m_1 = 0.3, \gamma =0.5 \) as plotted in Fig. 4e and f, respectively.
We study the effect of varying parameter q in the interval [0, 4.5] as displayed in Fig. 7a and b. The system is stable in the interval [0, 0.7] then goes to 2- period doubling and 4- period doubling in the range [0.7, 1.9] after that the system exhibits chaotic behavior.
3.1.2 Influence of system parameters
The bifurcation strategies have been successfully deployed to handle nonlinear properties of complex systems. Different bifurcation parameters have been explored in this section to investigate the dynamical behaviors of the system (7). Firstly, all the system parameters are fixed at values \( \alpha =0.98 , \gamma = 1 , m_{0} =-1.5 , m_{1} = 0.3 , q =3 \) and we start analyzing the sensitivity of system by varying each parameter individually. Figure 5a and b show the bifurcation diagram and Lyapunov exponents spectrum, respectively, for bifurcation parameter \(\beta \) in the range [0.2, 3]. For \( 0.4\le \beta \le 0.85 \) there is 6- period doubling and \( 0.85\le \beta \le 3 \) the system goes to chaos. By fixing \( \beta = 1\) and varying parameter \(\gamma \) in range [0.6, 3.6] , the bifurcation diagram and Lyapunov exponents plots are illustrated in Fig. 5c and d, respectively. In range [0.6, 1.3] the system exhibits chaotic behavior and goes to 4-period doubling then 2-period doubling in the range [1.3, 3.6] .
a and b bifurcation diagram of the proposed fractional-order system and Lyapunov exponents, respectively, versus \( \beta \) for \(\beta \in [0.2,3]\). c and d bifurcation diagram of the proposed fractional-order system and Lyapunov exponents, respectively, versus \( \gamma \) for \( \gamma \in [0.6,3.6] \)
a and b bifurcation diagram of the proposed fractional-order system and Lyapunov exponents, respectively, versus \( m_{0} \) for \(m_{0} \in [-2,-0.5]\). c and d bifurcation diagram of the proposed fractional-order system and Lyapunov exponents, respectively, versus \( m_{1} \) for \( m_{1} \in [0,0.36] \)
Then, we fix \(\gamma = 1\) and explore the parameter \( m_{0} \) within range \( -2 \le m_{0} \le -0.5 \). It is noticed that from \( m_{0} = -2 \) to \( m_{0} = -1.8 \) and from \( m_{0} = -1.6 \) to \( m_{0} = -0.75 \) the system has chaotic behavior soon after that it tends to period doubling in two ranges \( [-1.8,-1.6] \) and \( [-0.75,-0.5] \) as displayed in Fig. 6a and b. In addition, the value of parameter \( m_{0} = -1.5 \) is fixed to analyze the effect of changing the value of parameter \( m_{1} \) in range \(0 \le m_{1} \le 0.36 \). It can be seen from Fig. 6c and d that the system is stable in the interval [0, 0.01] then it undergoes period doubling within the interval [0.01, 0.07] until it reaches the chaos behavior in the interval \( m_{1} \in [0.07, 0.36] \).
The fractional order \( \alpha \) is now considered as the bifurcation parameter to show its effects on the dynamics of the proposed system (7). The dynamics of the system with varying fractional order \( \alpha \) in the range 0.5 to 1 . We fix \( q = 3 \) and varying fractional order \( \alpha \), the bifurcation diagram and Lyapunov exponents plots are obtained in Fig. 8a and b, respectively.
It is shown that from \( \alpha = 0.5 \) to \( \alpha = 0.68 \) it is a stable region. A cascade of period doublings in ranges [0.68, 0.78] and [0.875, 0.91] are observed. Then the system (7) shows chaotic dynamics over the ranges of \( 0.78 \le \alpha \le 0.875 \) and \( 0.91 \le \alpha \le 1 \).
In spite of the simplicity of system (7), the dynamical behaviors of this system are complex depending on the value of the bifurcation parameters. Firstly, unlike the case of limit cycle presence in integer order systems, the limit set of a solution trajectory of fractional order system cannot be a constant periodic solution of the system. In additions, the nonexistence of periodic solutions was proved in time-invariant fractional order systems in [47]. However, some examples were given where the solutions of the fractional order system are not periodic, but they asymptotically converge to periodic signals [48]. Summarizing these results, the limit cycle that appears in phase portrait of the fractional order system is not a solution of the system, but it attracts nearby solutions. Secondly, the fractional order blinking system and some aspects of nonlinear dynamics of the model will be investigated in the following subsections.
3.2 Fractional order blinking system
We propose fractional order blinking Rössler system R(q) with Chua’s diode non-linearity as follows
with time-varying parameter \( q(t) = (q_{1}- q_{2}) s(t) + q_{2} \). Based on random sequence, the parameter s(t) switches in the non-autonomous system (12) between two subsystem \( R_{1}(q_{1}) \) for \( s =1 \) with probability \( p_{1} \) and subsystem \( R_{2}(q_{2}) \) for \( s = 0 \) with probability \( p_{2} \).
For sufficiently fast switching time, it is expected that the fractional order blinking system follows the corresponding fractional order averaged system as the case of integer order systems studied previously in literature. The emerging attractor of fractional order averaged system is referred to as ghost attractor if it is different from the set of attractors in the subsystems of corresponding fractional order blinking system. The careful numerical simulation will indicate that when the switching is very fast, the trajectory of the fractional order blinking system evolves rapidly towards the neighborhood of the ghost attractor and then stays most of the time close to ghost attractor.
3.3 Numerical simulation for fractional order blinking system
In this subsection, the numerical simulations have been presented via phase portraits for three cases of fractional order blinking system based on different values for parameter q as follows
3.3.1 Case 1
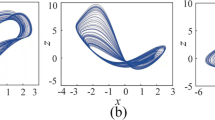
In first case, the solution trajectory of the system (7) is attracted to periodic orbit in phase space at \( q = 0.75\) as shown in Fig. 9 and at \( q = 3.83 \) as shown in Fig. 10 with other parameters values \( \beta = 1,\gamma =1, m_{0} = -1.5 , m_{1} = 0.3, \alpha =0.98 \) and \( T= 500 \), using a unit step \( h =0.005 \). Accordingly, the blinking system (12) switches in random between first subsystem \(R_{1}(q_{1} = 0.75) \) with probability \( p_{1} = \frac{22}{100}\) and second subsystem \(R_{2}(q_{2} = 3.83)\) with probability \( p_{2} = \frac{78}{100}\). The fractional order averaged autonomous system associated with the fractional order blinking system (12) where E(R(q, s(t))) is the expected value of R(q, s(t)) is \( R_{a}( q_{avg} = 3.1524) \) where \( q_{avg} = p_{1}*q_{1} + p_{2}*q_{2} \). The induced interesting ghost attractor is shown in Fig. 11. It is noticed that the trajectory of blinking system moves around the ghost attractor and after sufficient time remains close to the ghost attractor which means that it reaches a small neighborhood of the ghost attractor with appropriate fast switching. Indeed, the chaotic attractor of the fractional order averaged system represents the ghost attractor for the fractional order blinking system as shown in Fig. 12. Time series from the systems for first subsystem, second subsystem, averaged system and switching system are all depicted in Fig. 13.
3.3.2 Case 2
In second case, the system (7) has like a periodic behavior at \( q = 1.8 \) as shown in Fig. 14 and at \( q = 3.34 \) as shown in Fig. 15 with other parameters values as in Case 1 except \( m_{1} =0.35\). Thus, the blinking system (12) randomly switches between first subsystem \(R_{1}(q_{1} = 1.8) \) with probability \( p_{1} = \frac{30}{100}\) and second subsystem \(R_{2}(q_{2} = 3.34) \) with probability \( p_{2} = \frac{70}{100}\). The fractional order averaged system associated with the fractional order blinking system (12) where E(R(q, s(t))) is the expected value of R(q, s(t)) as \( R_{a}(q_{avg} = 2.878)\) where \( q_{avg} = p_{1}*q_{1} + p_{2}*q_{2} \). The ghost attractor of fractional order averaged system is shown in Fig. 16. For fast switching time, Fig. 17 displays the trajectory of fractional order blinking system reaches a small neighborhood of the ghost attractor and remains there. Time series of the solutions of first subsystem, second subsystem, averaged system and blinking system are depicted in Fig. 18.
3.3.3 Case 3
In third case, the system (7) has a stable equilibrium point at \( q = 0.8 , \gamma _{1} = 2.4 \) as shown in Fig. 19 and the solution trajectory of the system is attracted to periodic orbit in phase space at \(q = 2.58 , \gamma _{2} = 0.8\) as shown in Fig. 20 with other parameters values \( \beta = 1,\gamma =1, m_{0} = -1.5 , m_{1} = 0.3, \alpha =0.98 \) and \( T= 700 \), using a unit step \( h =0.005 \). Thus, the blinking system (12) randomly switches between first subsystem \(R_{1}(q_{1} = 0.8, \gamma _{1} = 2.4) \) with probability \( p_{1} = \frac{6.5}{100}\) and second subsystem \(R_{2}(q_{2} = 2.58, \gamma _{2} = 0.8)\) with probability \( p_{2} = \frac{93.5}{100}\). The fractional order averaged autonomous system associated with the fractional order blinking system (12) where E(R(q, s(t))) is the expected value of R(q, s(t)) as \( R_{a}(q_{avg} = 2.4643 ,\gamma _{avg} = 0.904)\) where \( q_{avg} = p_{1}*q_{1} + p_{2}*q_{2} \) and \( \gamma _{avg} = p_{1}*\gamma _{1} + p_{2}*\gamma _{2} \). The behavior of the averaged system is shown in Fig. 21. The trajectory of blinking system remains in a small neighborhood of the ghost attractor as shown in Fig. 22. Time series solutions of the first subsystem, second subsystem, averaged system and switching system are depicted in Fig. 23.
3.3.4 Euclidean distance
In this part, we calculate the Euclidean distance between the attractor of the blinking system and the ghost attractor. The Euclidean distance approximates the distance between invariant measures of the blinking system attractor and the ghost attractor. It is defined as [25]
where \( h_{j}^{\tau } = \dfrac{h_{1}^{\tau }}{T_{s}}, \dfrac{h_{2}^{\tau }}{T_{s}},..., \dfrac{h_{N}^{\tau }}{T_{s}} \) represents a distribution of \( T_{s} \) calculated phase points which is taken from the attractor of blinking system after neglecting the sufficient transient interval at chosen value of switching period \( \tau \). Similarly, \( h_{j}^{a} = {\dfrac{h_{1}^{a}}{T_{s}}, \dfrac{h_{2}^{a}}{T_{s}},..., \dfrac{h_{N}^{a}}{T_{s}}} \) is a distribution which is taken from the ghost attractor of fractional averaged system from these \( T_{s} \) points to the box \( D_j, \, j = 1,...,\,N\). These calculations are considered in the selected domain defined as \( D : {x_{i}^{-}< x_{i} <x_{i}^{+}, i = 1,2 , 3} \) which contains both two attractors of the blinking system and the averaged system. The two boundaries in each \( i^{th} \) direction of domain D are denoted by \( x_{i}^{-} \) and \( x_{i}^{+} \). The D region is divided into \( N = \prod _{i}^{n} N_{i} \) small boxes. The value of \(h_j\) represents the number of times that the solution trajectory hits the boundaries of box j after the initial transient time is ignored.
The Euclidean distance \( \delta (\tau ) \) has been used to quantify the closeness of the attractors of blinking system with those of the averaged system when the value of switching time is varied. In numerical simulations, the Euclidean distance is evaluated in the domain \( D: x\in [ -11, 13], y\in [-13 ,13 ], z\in [ -5.5, 5.5] \) and divide it into \( N = N_{x} \times N_{y} \times N_{z} \). For simplicty, we take \( N_{x} = N_{y} = N_{z} \) i.e. equal number of boxes in each direction such that \( N = 10^{6} \). We select interval length \( T = 500 \) and \( T = 700\) as it is used in the previous numerical simulation with the integration step 0.005 after neglecting \( 2*10^{4}\) iterations of the transition interval. For the switching period \( \tau \in [0.005, 1] \), the Euclidean distance \( \delta (\tau ) \) is evaluated and displayed in Fig. 24. It is noticed that the distance \(\delta (\tau ) \) rapidly increases for very small values of \(\tau \) then undergoes slight changes for further values till \(\tau =0.1\). This means that the attractor of system (12) changes under fast switching time \( \tau <1 \) in a slight way. The attractors of the fractional blinking system (12) for the three presented cases are shown in Figs. 12, (17) and 22. Accordingly, it is highly probable that the ghost attractor and the attractor of fractional order blinking system sufficiently remain close to each other with the advance of time.
3.3.5 Hardware implementation
Hardware experiment is realized using Arduino Uno board which is a board based on ATmega-328 microcontroller as illustrated in Fig. 25. The implementation consists of Arduino Uno platform which pulse width modulated signals are applied to resistor - capacitor low pass filter to generate chaotic outputs across capacitor terminals. All the used components are mentioned in Table (1). Through a fractional Euler discretization, the program is coded in C / Arduino language to validate the averaged system in case 2. The chaotic behavior is monitored through 500 ms Oscilloscope for the presented system.
4 Image encryption algorithm
In this section, we are motivated by the characteristics of the proposed system (12) as its high sensitivity to initial conditions, parameter values of chaotic system and the stochastic process to propose an image encryption scheme that utilizes this system.
4.1 Algorithm steps
The algorithm is mainly composed of two parts: plain image pixel shuffling without changing the pixels values and image diffusion. The block diagram to demonstrate the steps of encryption algorithm is given in Fig. 26.
The steps of the encryption strategy are detailed as follows
- Step 1:
-
Read the plain image \( I_{M\times N} \) as a matrix with dimensions \( M\times N \), where M is the length and M is the width.
- Step 2:
-
Evaluate a constant \(img_{c}\) as a perturbation value which depends only on the image to be ciphered, and it is defined as
$$\begin{aligned}&img_{c} = \frac{1}{(M\times N)^{2} }\sum _{i=1}^{M}\sum _{j=1}^{N} I(i,j), \end{aligned}$$(14)where i and j are the pixel positions of original image I. The image constant \(img_{c}\) is added to one of the system parameters as a perturbation value to make the original image contributes to evaluate the secret key. We choose to add \(img_{c}\) to the fractional derivative \( \alpha \) in the three examples that are used in our procedure.
- Step 3:
-
To get the chaotic time series as x(i), y(i), z(i), \( i = 1,2,...,n \), \( n= M \times N \), we first eliminate the transient values, then we take the time series with the required size where x, y, z are the solutions of fractional order blinking system.
- Step 4:
-
Standardize the values of the state variables as follows
$$\begin{aligned}&key_{i} = mod(floor(x_{i}\times 10^{15}),256),\,\,\quad \nonumber \\&row_{i} = mod(floor(y_{i}\times 10^{15}),512)+1,\,\, \nonumber \\&col_{i} = mod(floor(z_{i}\times 10^{15}),512)+1.\nonumber \\ \end{aligned}$$(15)We get \( x_{i}, y_{i}, z_{i} \) from solving fractional order blinking system (7) as the state variables. To obtain the value of the secret key \( key_{i}\) value within range [0, 256] as image pixels value, we use mod operation among the state variable \( x_{i} \) and 256. Also, we use mod operation between the state variables \( y_{i} , z_{i} \) and 512 to get a new position for pixels value image matrix I as shuffling process.
- Step 5:
-
Rearrange the pixels position as shuffle process as follows
$$\begin{aligned}&I_{sh}(i,j) = I(RW(i),CL(j)), \end{aligned}$$(16)where \( I_{sh} \) and I are the matrix for shuffle and plain images, respectively, where \( i= 1,2,...,M \) and \( j= 1,2,...,N\) are the image matrix dimensions. We set a simple scheme from three steps to get the shuffled matrix \( I_{sh} \) as follows S1 We used the generated values row and col to select from them first 512 different values as RW and CL. S2 Use the first value RW(1) in RW(j) in ascending order with all values in CL(j) where the pixels position in the plain image matrix are reposition in the shuffled image matrix and \( j=1,2,...,512 \). S3 To fit all the position of matrix I, repeat the second step 511 times where the pixels value remains unchanged.
- Step 6:
-
To set the secret key in matrix form the reshape function is used as follows
$$\begin{aligned}&Key_{s} = reshape(key,M,N). \end{aligned}$$(17) - Step 7:
-
Apply bitwise XOR operation between \( Key_{s}\) and \( I_{sh} \) to establish the encrypted image \( I_{en} \) as follows
$$\begin{aligned}&I_{en}(i,j) = I_{sh}(i,j) \oplus Key_{s}(i,j). \end{aligned}$$(18)To reconstruct the original image, the encryption steps are reversed. So, the decryption procedure is presented as
- Step 1:
-
Apply the bitwise XOR operation between \( I_{en} \) and \( Key_{s} \) to attain decrypted image \( I_{de} \) as follows
$$\begin{aligned}&I_{de}(i,j) = I_{en}(i,j) \oplus K_{s}(i,j). \end{aligned}$$(19) - Step 2:
-
The image pixel positions are reversed to obtain the original image \( I_{dsh} \) as
$$\begin{aligned}&I_{dsh}(RW(i),CL(j)) = I_{de}(i,j). \end{aligned}$$(20)
The proposed encryption scheme is applied on three different images as shown in Fig. 27 which depicts the original, shuffled, encrypted and decrypted images for the presented algorithm.
4.2 Security analysis
A good encryption scheme should defend against all sorts of known and common attacks such as differential attack, the brute force attacks and statistical attacks. Various security tests have been used on encrypted images to assess the proposed image cryptosystem. These tests include histogram, information entropy, pixel correlation, differential attack, key space and cropping attack. We have chosen three images: Pepper, Man and Baboon image of size \( 512 \times 512 \) to explore the security of the proposed encryption scheme. The chaotic time series from the third case of fractional order blinking system has been used to generate new row, column image pixel positions and the secret key. In addition, the perturbation values \(img_{c}\) for Pepper, Man and Baboon are \( 4.5710 \times 10^{-4}\) , \( 2.9686 \times 10^{-4} \) and \( 4.9284 \times 10^{-4} \), respectively are used to make the system solutions depend on the plain image and increase the robust the encryption scheme.
4.2.1 Histogram analysis
Image histogram is an important criterion to measure the performance of encryption algorithm. It can describe the intensity distribution of image gray-scale level. In order to protect the information of the plain image to stand up against the statistical attacks, the statistical characteristics of pixel values in plain image should be eliminated to bear no statistical similarity to the original image. The good image encryption algorithm will lead to a flat or uniform histogram of encrypted image. Figure 28 depicts the results of histogram analysis which is evaluated to Pepper, Man and Baboon images. It is shown that the encrypted image histogram is uniform and is different from the original image so, it is effectively resisting the statistical attacks.
The variance related to histograms is evaluated using [49]
where \( G_{L} = 256 \) is the grey level and \( h = [h_{1},h_{2},...,h_{256}] \) where \( h_{i} \) and \( h_{j} \) are the numbers of pixels. The histogram variances for original and ciphered images are depicted in Table 2. The reduction for Pepper, Man and Baboon images is verified with values approximate \( 99.8\% \).
4.2.2 Information entropy
In this subsubsection, we explore one of main features of randomness which is the information entropy. The greater information entropy means image pixels are less feasible to show information for the encryption scheme. The information entropy calculated by the following formula
where X is an input symbol, \( p_{i} \) is probability value of symbol X and H(X) is the entropy in bits. Image pixels are more invisible when \( H(X) \simeq 8 \) for an encrypted image. The entropy values for Pepper, Man and Baboon images for the proposed algorithm have been compared with other algorithms in Refs. [9, 36, 50] are shown in Table 3. Consequently, the calculated entropy is approximately 8 therefore, the proposed scheme is equivalent to the existing algorithms and has a good property of information entropy and decoding encrypted image is less possible from attackers.
4.2.3 Correlation analysis
The characteristic of image data is inherited by high correlation of adjacent pixels. Therefore, the correlation of adjacent pixels in the encrypted images should be as small as possible. To test the correlation coefficient \( r_{uv} \) between u, v as the gray-scale values of two adjacent pixels, the \( r_{uv} \) formula is defined as
where cov(u, v) is the covariance function, \( E(u) = \frac{1}{N} \sum _{i=1}^{N}u_{i}\) and \( \sigma _{u} = \frac{1}{N} \sum _{i=1}^{N}(u_{i}-E(u))^{2} \). In vertical, horizontal, and diagonal directions of the plain image and encrypted image, the value of correlation between two adjacent pixels are calculated for Pepper, Man and Baboon images of the proposed algorithm is shown in Table 4 with the comparison of our proposed algorithm with other methods mentioned in Refs. [9, 36, 50] and it is cleared that the superiority of the proposed algorithm to other algorithms. Through the obtained results, we noticed that the correlations in the plain image are strong since the correlation coefficients are all around to 0.8 and 0.97. And the correlation coefficients of the ciphered image are smaller and all around zero in the presented scheme, which demonstrates the insignificant correlation between adjacent pixels.
4.2.4 Differential attack
The cryptosystem should be kept safe from the different types of attacks. For a robust cryptosystem, an essential feature as differential attack is needed to analyze. To reflect the differences in the ciphers due to the changes in the encrypting keys which means that a slight change of secret key will cause an obvious distinction in the cipher-image. In order to test this feature, there are two benchmark values (NPCR) and (UACI) as in [51]. These evaluate the difference among the encrypted images obtained from an original image and its slightly modified copy. NPCR is used to calculate the total number of different pixels in the original cipher and modified ciphers. It is defined as
where \( C_{i} \) is the ciphered image and sign() is the sign function. The UACI is used to obtain average difference in the pixel intensity in the original cipher \( C_{1} \) and the modified cipher \( C_{2} \). It is calculated by
The ideal results to NPCR and UACI tests for encryption schemes should be near to \( 100\% \) and \( 33.33\% \), respectively as ideal results. Results of these two tests and the comparison with different algorithms is reported in Refs. [36, 50] are introduced in Tables 5 and 6. It is obvious that proposed encryption algorithm achieves equal or higher performance by comparing the other algorithms. The calculated NPCR and UACI for the proposed encryption algorithm are very close to the ideal value and is highly sensitive to image pixel change and mismatched keys.
4.2.5 Key space
The robust image encryption algorithm should have key space with value greater than \( 2^{100} \) at least [52] to withstand brute-force attacks. In the presented scheme, the secret key is composed of the double precision based on the parameters of the chaotic systems, \( q_{1}, q_{2}, \gamma _{1}, \gamma _{2},p_{1}, p_{2}, m_{0},\) \( m_{1} , \alpha , (x_{0}, y_{0}, z_{0}), img_{c}\). The digits number are to be at least \( 10^{-15} \) in each parameter. The key space of the presented scheme is \( 10^{195} \) and it is effectively enough to stand up against violent attack.
4.2.6 Cropping attack
The cropping attacks are used to examine the immunity of encryption scheme to information loss. To study the robustness in defend the cropping attack [53], we replaced an internal block of the ciphered image with size \( 512 \times 100 \) into black with left, middle, and right positions. The black blocks inside the ciphered image and the decrypted images are displayed in Fig. 29. It is noticed that recovered images are all recognizable despite the significant information loss.
5 Conclusion
Over the past twenty years, the study of integer order blinking systems has been considered in few works. In this work, we have presented a blinking system in fractional order model for first time. We have shown through thorough numerical simulation that the attractor of fractional order blinking system follows the ghost attractor of the corresponding fractional order averaged system when the switching time is sufficiently fast. We utilized the chaotic time series of resulting ghost attractor in a novel encryption scheme. The presented image encryption scheme successfully stands against different types of attacks with a high level of security. Nevertheless, the achieved results prove that the proposed image encryption algorithm preserves good encryption performance while comparing with existing algorithms. The theoretical work of fractional order blinking system with more numerical simulation can be reported in our subsequent studies. In addition, for independent navigation of a differential drive mobile robot, the chaotic signals that are generated from fractional blinking system can be utilized which could be used for search, firefighting, or patrol activities.
Data availability
All data generated or analyzed during this study are included in this article.
References
Kilbas, A., Srivastava, H., Trujillo, J.: Theory and Application of Fractional Differential Equations. Elsevier, New York (2006)
Elsadany, A., Matouk, A.: Dynamical behaviors of fractional-order lotka-volterra predator-prey model and its discretization. J. Appl. Math. Comput. 49, 269–283 (2015)
Xiong, P., Jahanshahi, H., Alcaraz, R., Chu, Y., Gómez-Aguilar, J., Alsaadi, F.: Spectral entropy analysis and synchronization of a multi-stable fractional-order chaotic system using a novel neural network-based chattering-free sliding mode technique. Chaos Solitons Fract. 144, 110576 (2021)
Xu, C., Liao, M., Li, P., Yuan, S.: Impact of leakage delay on bifurcation in fractional-order complex-valued neural networks. Chaos Solitons Fract. 142, 110535 (2021)
Yuana, J., Zhao, L., Huangb, C., Xiao, M.: Stability and bifurcation analysis of a fractional predator-prey model involving two nonidentical delays. Math. Comput. Simul. 181, 562–580 (2021)
Trikha, P., Mahmoud, E., Jahanzaib, L., Matoog, R., Abdel-Aty, M.: Fractional order biological snap oscillator: analysis and control. Chaos Solitons Fract. 145, 110763 (2021)
Xin, B., Zhang, J.: Finite-time stabilizing a fractional-order chaotic financial system with market confidence. Nonlinear Dyn. 79(2), 1399–1409 (2015)
Li, Y., Sun, C., Ling, H., Lu, A., Liu, Y.: Oligopolies price game in fractional order system. Chaos Solitons Fract. 132, 109583 (2020)
Yang, Y., Guan, B., Li, J., Zhou, Y., Shi, W.: Image compression-encryption scheme based on fractional order hyperchaotic systems combined with 2d compressed sensing and dna encoding. Opt. Laser Technol. 119, 105661 (2019)
El-Sayed, A., Nour, H., Elsaid, A., Matouk, A., Elsonbaty, A.: Dynamical behaviors, circuit realization, chaos control, and synchronization of a new fractional order hyperchaotic system. Appl. Math. Model. 40, 3516–3534 (2016)
El-Sayed, A., Elsonbaty, A., Elsadany, A., Matouk, A.: Dynamical analysis and circuit simulation of a new fractional-order hyperchaotic system and its discretization. Int. J. Bifurc. Chaos 26, 1650222 (2016)
Bansal, R.: Stochastic filtering in fractional-order circuits. Nonlinear Dyn. 103(1), 1117–1138 (2021)
Sun, Y., Gao, Y., Song, S.: Effect of integrating memory on the performance of the fractional plasticity model for geomaterials. Acta Mech. Sinica 34, 896–901 (2018)
Liu, R., Niu, J., Shen, Y., Yang, S.: Stability and bifurcation analysis o f two-degrees-of-freedom vibro-impact system with fractional-order derivative. Int. J. Non-Linear Mech. 126, 103570 (2020)
Munoz-Pacheco, J., Lujano-Hernández, L., Muñiz-Montero, C., Akgül, A., Sánchez-Gaspariano, L., Li, C.-B. C., Kutlu, M. Ç.: Active realization of fractional-order integrators and their application in multiscroll chaotic systems, Complexity (2021)
Hammouch, Z., Mekkaoui, T.: Circuit design and simulation for the fractional-order chaotic behavior in a new dynamical system. Complex Intell. Syst. 4(4), 251–260 (2018)
Ávalos-Ruiz, L., Zúñiga-Aguilar, C., Gómez-Aguilar, J., Escobar-Jiménez, R., Romero-Ugalde, H.: Fpga implementation and control of chaotic systems involving the variable-order fractional operator with mittag-leffler law. Chaos Solitons Fract. 115, 177–189 (2018)
Han, X., Mou, J., Xiong, L., Ma, C., Liu, T., Cao, Y.: Coexistence of infinite attractors in a fractional-order chaotic system with two nonlinear functions and its dsp implementation. Integration 81, 43–55 (2021)
Kaczorek, T.: Stability of positive fractional switched continuous-time linear systems. Tech. Sci. 61, 0033 (2013)
Feng, T., Guo, L., Wu, B., Chen, Y.: Stability analysis of switched fractional-order continuous-time systems. Nonlinear Dyn. 102, 2467–2478 (2020)
Lin, A., Antsaklis, P.: Stability and stabilizability of switched linear systems: a survey of recent results. IEEE Trans. Autom. Control 54(2), 308–322 (2009)
Yu, Q., Zhao, X.: Stability analysis of discrete-time switched linear systems with unstable subsystems. Appl. Math. Comput. 273, 718–725 (2016)
Belykh, I., Belykh, V., Jeter, R., Hasler, M.: Multistable randomly switching oscillators: the odds of meeting a ghost. Eur. Phys. J. Spec. Topics 222, 2497–2507 (2013)
Barabash, N., Belykh, V.: Non-stationary attractors in the blinking systems: ghost attractor of lorenz type. Cybern. Phys. 8, 209–214 (2016)
Barabash, N., Levanova, T., Belykh, V.: Ghost attractors in blinking lorenz and hindmarsh-rose systems. Chaos 30, 081105 (2020)
Belykh, I., Belykh, V., Hasler, M.: Blinking model and synchronization in small-world networks with a time-varying coupling. Phys. D 195, 188–206 (2004)
Hasler, M., Belykh, V., Belykh, I.: Dynamics of stochastically blinking systems. Part i: finite time properties. SIAM J. Appl. Dyn. Syst. 12, 1031–1084 (2013)
Hasler, M., Belykh, V., Belykh, I.: Dynamics of stochastically blinking systems. Part ii: asymptotic properties. SIAM J. Appl. Dyn. Syst. 12, 1031–1084 (2013)
Li, C., Li, Z., Feng, Y.T.W., Du, J., Wei, D.: Dynamical behavior and image encryption application of a memristor-based circuit system. Int. J. Electron. Commun. (AEÜ) 110, 152861 (2019)
Belazi, A., El-Latif, A., Rhouma, R., Belghith, S.: Selective image encryption scheme based on dwt, aes s-box and chaotic permutation. In International Wireless Communications and Mobile Computing Conference (IWCMC), IEEE pp. 606-610 (2015)
Shaukat, S., Arshid, A., Eleyan, A., Shah, S., Ahmad, J.: Chaos theory and its application: an essential framework for image encryption. Chaos Theory Appl. 2(1), 17–22 (2020)
Wang, X., Li, Y., Jin, J.: A new one-dimensional chaotic system with applications in image encryption. Chaos Solitons Fract. 139, 110102 (2020)
Kaur, G., Agarwal, R., Patidar, V.: Chaos based multiple order optical transform for 2d image encryption. Eng. Sci. Technol. 23, 998–1014 (2020)
Musanna, S.K.F.: A novel image encryption algorithm using chaotic compressive sensing and nonlinear exponential function. J. Inf. Secur. Appl. 54, 102560 (2020)
Askar, S., Al-khedhairi, A., Elsonbaty, A., Elsadany, A.: Chaotic discrete fractional-frder food chain model and hybrid image encryption scheme application. Symmetry 13, 161 (2021)
Zhou, M., Wang, C.: A novel image encryption scheme based on conservative hyperchaotic system and closed-loop diffusion between blocks. Signal Process. 171, 107484 (2020)
Yang, F., Mou, J., Ma, C., Cao, Y.: Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt. Lasers Eng. 129, 106031 (2020)
Sun, Y., Zhang, H., Wang, X.Y., Wang, X.Q., Yan, P.: 2d non-adjacent coupled map lattice with q and its applications in image encryption. Appl. Math. Comput. 373, 125039 (2020)
Talhaoui, M., Wang, X.: A new fractional one dimensional chaotic map and its application in high-speed image encryption. Inf. Sci. 550, 13–26 (2021)
Ismail, S., Said, L., Radwan, A., Madian, A., Abu-ElYazeed, M.: A novel image encryption system merging fractional-order edge detection and generalized chaotic maps. Signal Process. 167, 107280 (2020)
Boyraz, F., Çimen, M., Güleryüz, E., Yıldız, M.: A chaos-based encryption application for wrist vein images. Chaos Theory Appl. 3(1), 3–10
Lia, Y., Chen, Y., Podlubny, I.: Stability of fractional-order nonlinear dynamic systems: Lyapunov direct method and generalized Mittag-Leffler stability. Comput. Math. Appl. 59, 1810–1821 (2010)
Wu, G., Deng, Z., Baleanu, D., Zeng, D.: New variable-order fractional chaotic systems for fast image encryption. Chaos 29, 083103 (2019)
Kuate, P., Tchendjeu, A., Fotsin, H.: A modified rössler prototype-4 system based on chua’s diode nonlinearity: dynamics, multistability, multiscroll generation and fpga implementation. Chaos Solitons Fract. 140, 110213 (2020)
Chua, L., Komuro, M., Matsumoto, T.: The double scroll family. Parts I and II. IEEE Trans. Circuits. Syst. 33(1986), 1073–1118 (1986)
Ahmed, E., El-Sayed, A., El-Saka, H.: On some Routh-Hurwitz conditions for fractional order differential equations and their applications in Lorenz, Rössler, Chua and Chen systems. Phys. Lett. A 358, 1–4 (2006)
Tavazoei, M., Haeri, M.: A proof for non existence of periodic solutions in time invariant fractional order systems. Automatica 45, 1886–1890 (2009)
Tavazoei, M.: A note on fractional-order derivatives of periodic functions. Automatica 46, 945–948 (2010)
Lahdir, M., Hamiche, H., Kassim, S., Tahanout, M., Kemih, K., Addouche, S.: A novel robust compression-encryption of images based on spiht coding and fractional-order discrete-time chaotic system. Opt. Laser Technol. 109, 534–546 (2019)
Yadollahi, M., Enayatifar, R., Nematzadeh, H., Lee, M., Choi, J.: A novel image security technique based on nucleic acid concepts. J. Inf. Secur. Appl. 53, 102505 (2020)
Wu, Y., Noonan, J., Agaian, S.: Npcr and uaci randomness tests for image encryption. Cyber J. Multidiscip. J. Sci. Technol. 1(2), 31–38 (2011)
Barker, E., Roginsky, A.: Transitions, recommendation for transitioning the use of cryptographic algorithms and key lengths[j]. NIST Spec. Publ. 131A, 800 (2011)
Ullah, A., Jamal, S., Shah, T.: A novel scheme for image encryption using substitution box and chaotic system. Nonlinear Dyn. 91, 359–370 (2018)
Acknowledgements
The authors would like to thank the anonymous reviewers and the editor for providing their helpful comments and suggestions which further improved the scientific contents, readability, and clarity of this paper.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Kamal, F.M., Elsaid, A. & Elsonbaty, A. Ghost attractor in fractional order blinking system and its application. Nonlinear Dyn 108, 4471–4497 (2022). https://doi.org/10.1007/s11071-022-07391-w
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-022-07391-w