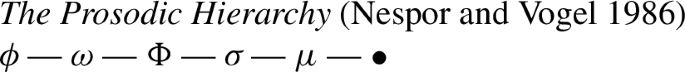Abstract
This paper offers a phonological account of various ways in which reduplication interacts with independent processes in Lakota: transparent application in the case of cluster simplification, overapplication in the case of palatalization, and underapplication in the case of vowel mutation. I argue that all three patterns follow from phonological optimization rather than morpheme-specific constraints on the reduplicant or on other morphemes, and that the co-existence of divergent patterns is compatible with such a phonological analysis. Local application is the default pattern, while overapplication receives a cyclic explanation. For underapplication, which is the most recalcitrant pattern in Lakota, I offer an account in terms of Trigger Poverty, a concept which denotes an imbalance between the number of triggers and the number of potential targets created by copying. Trigger Poverty is likely to be a more general abstract source of underapplication beyond Lakota. This paper thus contributes to the discussion of modularity in phonology by presenting evidence that identity effects in reduplication can be epiphenomenal.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
When a reduplicated form is targeted by some independent process, the interaction space between these two processes is delineated by three scenarios: transparent application, overapplication, and underapplication. In the first case, a process applies locally and affects a reduplicated form the same way it affects nonreduplicated forms. In the case of overapplication, a process applies to both the base and the reduplicant(s) even though only a single application would be expected. In underapplication, a process is exceptionally inhibited from applying to a reduplicated form.
In Lakota, all three scenarios are attested at various places in the grammar.Footnote 1 Transparent application occurs with cluster simplification, which is pervasive in Lakota and makes no distinction between reduplicated and non-reduplicated forms (1-a). Overapplication is observed with palatalization induced by certain prefixes which palatalize both a base and a reduplicant velar stop even though only the base form is preceded by a palatalizing vowel (1-b). Underapplication occurs in certain reduplicated vowel-final verb roots before suffixes that normally trigger vowel mutation (1-c).
-
(1)

The last pattern in particular presents a puzzle, as it is not obvious how it could be motivated and does not lend itself to a straightforward account in terms of base-reduplicant faithfulness (see Sect. 5.3). In what follows, I will argue that all three patterns follow purely from the optimization of incomplete and/or imbalanced phonological structures.
1.1 Problems and solutions
1.1.1 Controlling BR-identity
In Base-Reduplicant Correspondence Theory (BRCT, McCarthy and Prince 1995), reduplication is triggered by a RED morpheme coupled with a family of faithfulness constraints overseeing identity between base and reduplicant. A different approach is advocated by Morphological Doubling Theory (MDT, Inkelas and Zoll 2005), in which reduplicated constituents are special constructions with specific cophonologies. Indexed faithfulness constraints can straightforwardly compel identity relations between base and copied material, and cophonologies can achieve the same goal with the exception of phonological backcopying, albeit with a very different mechanism. Common to both BRCT and MDT is the strong emphasis on morphology, either by virtue of morpheme-specific constraints or distinct reduplicative constructions.
Strictly phonological theories of reduplication such as Minimal Reduplication (Saba Kirchner 2010) do not have either of these devices at their disposal, which prompts the question if they are still capable of deriving identity effects as described above. What I will propose here is that in the case of Lakota, overapplication emerges as a consequence of the feed-forward architecture of grammar (Kiparsky 1982; Bermúdez-Otero 2018): when a process such as overwriting applies at an earlier level than reduplication, the result of that process will be copied as is, creating the impression of double or overapplication (2).
-
(2)

On the other hand, underapplication may arise when a process that normally has exactly one target is confronted with more than one potential target because of the presence of copied segments. This may create a dilemma if the grammar independently restricts the freedom of associating certain nodes from one tier with multiple nodes from another tier. I argue that mutation underapplication in Lakota is an instantiation of this dilemma, which I dub Trigger Poverty (3). TP in most general terms can be understood as a lack of sufficient triggers that prevents a process from applying.
-
(3)
Trigger Poverty (TP)
Let F be a feature that triggers an alternation A and let T be a potential target for A. When N(F) = N(T), application of A is optimal. When N(F) < N(T), not applying A is optimal.
TP effects may arise when constraints against multiple linking conspire with constraints against line insertion, rendering featural epenthesis optimal. One such configuration is sketched in the tableau in (4) below, where one floating feature  faces two empty root nodes (•), both of which are potential targets for association. How can non-integration of the floater be optimal in such a scenario? The structure in (4-a) fatally violates high-ranked •→F (“Root nodes need to be linked to a feature F”), and also lower-ranked F→• (“No floating F”). Multiple linking of
faces two empty root nodes (•), both of which are potential targets for association. How can non-integration of the floater be optimal in such a scenario? The structure in (4-a) fatally violates high-ranked •→F (“Root nodes need to be linked to a feature F”), and also lower-ranked F→• (“No floating F”). Multiple linking of  would satisfy both constraints but is ruled out by a high-ranked constraint against multiple association of [-F], *[-F]2• (4-b). Single linking of [-F] and insertion of an epenthetic feature
would satisfy both constraints but is ruled out by a high-ranked constraint against multiple association of [-F], *[-F]2• (4-b). Single linking of [-F] and insertion of an epenthetic feature  is not optimal, either, because it fatally violates Dep(•–[-F]), a constraint against linking a root node to a [-F] feature (4-c). The optimal repair for (4-a) is thus epenthesis and multiple linking of
is not optimal, either, because it fatally violates Dep(•–[-F]), a constraint against linking a root node to a [-F] feature (4-c). The optimal repair for (4-a) is thus epenthesis and multiple linking of  while leaving
while leaving  floating (4-d). While this violates Dep([+F]) and F→•, it satisfies Dep(•–[-F]). Under the grammar with the constraint ranking indicated in (4), it is impossible to satisfy both •→F and F→• when there are two potential targets but only a single trigger, but it is possible to F→• without integration of the floating feature. In other words, the optimal response to a configuration with one trigger and two targets is to leave the trigger feature
floating (4-d). While this violates Dep([+F]) and F→•, it satisfies Dep(•–[-F]). Under the grammar with the constraint ranking indicated in (4), it is impossible to satisfy both •→F and F→• when there are two potential targets but only a single trigger, but it is possible to F→• without integration of the floating feature. In other words, the optimal response to a configuration with one trigger and two targets is to leave the trigger feature  floating.
floating.
-
(4)
TP: Non-integration of floater with two targets

A cyclic architecture of grammar, coupled with basic constraints on the association of phonological nodes, will prove to be sufficiently powerful to account for both over- and underapplication in Lakota reduplication.
1.1.2 Morpheme-specific phonology
Base-reduplicant identity effects are one example of a larger group of seemingly morpheme-sensitive phonological processes that have been referred to as “morphologically conditioned phonology” (Anttila 2002) or “morphological indexation” (Pater 2009). This group of processes have inspired accounts in which morphology either directly or indirectly governs phonological processes, including Output-Output Correspondence (Benua 1997), Realize Morpheme (Kurisu 2001), Cophonology Theory (Inkelas and Zoll 2007), and lexically indexed constraints (Pater 2009).
Zimmermann (2017a) and Trommer (2020), among others, have argued that all of the above mentioned accounts suffer from undergeneration and overgeneration, and that morpheme-specific effects instead follow from the basic tenets of featural affixation (Akinlabi 1996) constrained by Optimality Theory (Prince and Smolensky 1993/2004). This is exactly the standpoint that I will adopt here with respect to the seemingly opaque reduplication patterns in Lakota.
1.1.3 The coexistence of divergent interaction patterns
A third non-trivial problem is presented by the coexistence of divergent interaction patterns within a single language. If a phonological explanation can be defended for one particular misapplication pattern, the existence of the opposite pattern in the same grammar raises the question how those patterns can co-exist. The solution lies within the phonological properties of the respective processes. When different phonological features or nodes are involved, their behavior is governed by different sets of constraints. This is illustrated in (5), where a base and a reduplicant with a feature α are overwritten by a prefixed feature  but a reduplicated form with two γ features resists overwriting by a prefixed
but a reduplicated form with two γ features resists overwriting by a prefixed  . If α, β, γ and δ are different features, the divergent behavior of (5-a) and (5-b) may follow from a constraint ranking under which only overwriting of α by β is optimal.Footnote 2
. If α, β, γ and δ are different features, the divergent behavior of (5-a) and (5-b) may follow from a constraint ranking under which only overwriting of α by β is optimal.Footnote 2
-
(5)

Modeling different application patterns in terms of differences in phonological features, rather than morphological provenance, also allows for broader generalizations about the processes in question.
1.2 Roadmap
The remainder of this paper is structured as follows. Section 2 lays out the main theoretical assumptions and introduces the relevant formal concepts. Section 3 offers the relevant phonological and morphological background on Lakota. Section 4 presents in-depth analyses of the three interaction types (transparent, over- and underapplication) in Lakota. Section 5 provides further discussion, considers additional evidence and scrutinizes alternative accounts. Section 6 concludes the paper.
2 Theoretical assumptions
In this paper, I follow the research program of Generalized Non-linear Affixation (GNLA, Bermúdez-Otero 2012), which aims to derive productive non-concatenative processes from the concatenation of phonologically defective structures (see also Trommer and Zimmermann 2014). In this spirit, I assume that both reduplication and stem mutation follow from the same basic mechanism, viz. the affixation of defective phonological material: empty prosodic nodes in the case of reduplication, and sub-segmental features in the case of mutation. The central innovation proposed here is that over- and underapplication in reduplication likewise emerge from non-linear affixation and instantiate the same descriptive generalizations as obtain in nonreduplicative contexts.
2.1 Extended Stratal Containment
The theoretical framework that my analysis of Lakota is couched in is Extended Stratal Containment (ESC; Trommer 2011), with slight modifications regarding the copying mechanism. Extended Stratal Containment combines the insights of two strands of Optimality Theory (Prince and Smolensky 1993/2004): Stratal OT and Containment Theory.
2.1.1 Stratal OT
Similar to Lexical Phonology (Pesetsky 1979; Mohanan 1982; Kiparsky 1985; Pulleyblank 1986) and Derivational Optimality Theory (Rubach 2000, 2003, 2008), Stratal Optimality Theory postulates a modular feed-forward architecture of grammar in which morphological structure building and subsequent phonological optimization are distributed over multiple strata with independent grammars (Kiparsky 2000; Bermúdez-Otero 2012). While there is some debate about the number of strata that languages must minimally and may maximally have (see Kiparsky 2015 for discussion), in this paper, I am only concerned with two basic strata: the stem level and the word level. I also assume with Kiparsky (2000) that the stem stratum is a cyclic domain, i.e. optimization for the stem level phonology applies recursively after each morphological operation.Footnote 3
2.1.2 Containment Theory
The hallmark of Containment Theory (Prince and Smolensky 1993/2004; van Oostendorp 2006, 2007; Trommer 2015a; Zimmermann 2017a), and an important difference from Correspondence Theory (McCarthy and Prince 1995; Kager 2004), is a rather restrictive Gen module, most notably its inability to delete phonological material. The generative power of Gen is limited to adding new nodes and modifying association lines between nodes. A list of operations available to Gen is stated in (6), based on definitions in Trommer (2011:30), Trommer and Zimmermann (2014:472), and Zimmermann (2017a:78).Footnote 4 The exact details of the copy mechanism (6-d) will be discussed further below.
-
(6)
Possible operations of Gen
-
a.
Mark association lines present in the input as phonetically invisible.
-
b.
Insert epenthetic association lines.
-
c.
Insert epenthetic (= colorless) nodes.
-
d.
Copy a continuous string of phonological elements of the same tier from the input.Footnote 5
-
a.
Apart from the classic OT constraints, I will be making use of designated constraints on node association that are formulated according to the scheme in (7).
-
(7)

Moreover, ESC distinguished between different levels of representations. Reference to the phonological content of morphemes irrespective of phonetic visibility (“M-Structure”) is the default interpretation of constraints; such constraints do not receive extra marking, e.g. *CCC. Constraints referring to the actually pronounced form (“P-Structure”) evaluate the phonetic output and are indicated by underlining, e.g. *CCC.
There are independent reasons for assuming rather divergent stem and word level phonologies in Lakota (Shaw 1980), which welcomes an analysis couched in a stratal framework. Containment, on the other hand, allows us to specify whether a constraint is sensitive to phonetically visible or visible and invisible structure. This becomes relevant for the analysis of Lakota reduplication at various points. Phonotactic constraints, for instance, evaluate only pronounced structure (otherwise, repairs would have no effect) while the structure constraints against multiple linking (7-cd), which play a crucial part in Trigger Poverty, do not require the lines to be phonetically visible.
2.2 Morphological colors
The theory of morphological colors (van Oostendorp 2006) and its translation into Containment Theory, Colored Containment (van Oostendorp 2007; Trommer 2011, 2015a), heavily restricts the amount of morphological information accessible to the phonological component. Phonological constraints can identify whether phonological entities have the same or a different morphological affiliation but they cannot refer to specific lexical entries. This crucially excludes indexed constraints (Pater 2009) and, by logical extension, BR-faith constraints, which are specific to the red morpheme (McCarthy and Prince 1995; Mc Laughlin 2000).
One family of constraints that assigns violations based on color is Alt(ernate) (8). Alt penalizes linking two nodes of the same color and thus provides a natural explanation for non-derived environment blocking (Kiparsky 1993; Kula 2008).
-
(8)

Another process where color plays a vital role is line epenthesis. The constraint in (9) is only sensitive to non-epenthetic nodes. Nodes that are inserted by the phonology have no color, with the exception of copied nodes (see below). Alt and Dep are thus in a Paninian relationship: whenever the former is violated, the latter is violated as well.
-
(9)

The table in (10) provides an overview of the violation profiles for different line insertion scenarios. Following Trommer (2011), colorless material is visualized by  shading.
shading.
-
(10)

Morphological colors are merged at the end of each stratum such that affix material can only be distinguished from stem material at the level where the respective affix is added. At later stages, the morphological allegiance of segments is no longer visible to the phonology.
ESC with morphological colors seeks to derive apparent morpheme-specific exceptionality not from constraints hard-wired to specific morphemes but from a specific set of underlying representations and independently motivated processes in the grammar. In the context of the present analysis of Lakota, morphological colors provide an elegant way to distinguish between underlying and epenthetic nodes. As hinted at in Sect. 1.1.1, the crucial idea for deriving underapplication is that insertion of an epenthetic (colorless) feature allows for free linking of that feature without incurring a violation of (9). Colors are thus a crucial technical prerequisite for the Trigger Poverty solution.
2.3 Defective representations
The fundamental assumption underlying GNLA is that morphological exponence is inherently item-based and not procedural (Bye and Svenonius 2012). In accordance with Richness of the Base (ROTB; Smolensky 1996), there are no a priori restrictions on the composition of these phonological items: they can contain any combination of phonological nodes and be fully specified on all levels, underspecified for certain features, or consist of only a single node. The inventory of phonological nodes contains prosodic nodes (see below), place and constriction nodes, and root nodes (McCarthy 1988; Clements and Hume 1995).
For prosodic structure, this means that any subsets of the Prosodic Hierarchy (11) qualify as triggers for non-concatenative morphology. Davis and Ueda (2002) show how allomorphy in Japanese emphatic adjectives results from affixation of a single μ. Saba Kirchner (2010) argues that reduplicative allomorphy in Kwak’wala also receives a unified explanation under a μ-affixation account, an insight that will become relevant later on. Zimmermann (2017a) identifies prosodically defective morphemes as the source of a whole battery of non-concatenative processes, including segmental lengthening, shortening, deletion, epenthesis, stress shift, reduplication, and blocking.
-
(11)
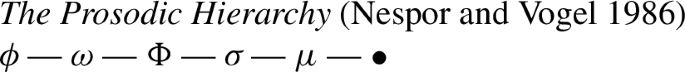
-
(12)
Overwriting

Affixation of non-segmental material is also what gives rise to segmental mutation by overwriting underlying features (12). Morphemes that trigger mutation contain a certain marked structure, viz. defective features or subsegments, that interact with underlying phonological material and induce segmental alternations (see Akinlabi 1996; Mc Laughlin 1994; Wolf 2007; Trommer 2020 for a variety of applications). In Lakota, vowel mutation is triggered by affixation of morphemes containing a floating [-l(ow)] feature.
Assuming defective representations means that there is a much more open and less restricted space of potential input forms to Eval. One may worry that this unnecessarily inflates the machinery required to eliminate unattested forms (see also Booij 2011). The standard response to this in ESC is the assumption that before any cycles instantiated by affixation, a root level evaluation takes place that optimizes roots and stem-level affixes and thus provides a “cleaner” input to the stem level phonology (Trommer 2011:72–76). It is important to note that the outcome of this stratal pre-processing may differ succinctly across languages. In Lakota, permittable deficient structures at the root level include a final empty root vowel, an empty root vowel and a floating [+l(ow)] that are linked at the root level (see Sect. 4.3.3), as well as empty moras. In languages such as English or Ngalakan, the root level optimization puts different restriction on input forms (ibid.).
2.4 Phonological copying
2.4.1 Minimal Reduplication
My theory of phonological copying, which I dub Bidirectional Minimal Reduplication (BMR), is an extension of Kirchner’s Minimal Reduplication (MR; Saba Kirchner 2010, 2013; see also Bye and Svenonius 2012). Kirchner’s main insight is that reduplication is the result of prosodic affixation, which may also trigger other non-concatenative processes depending on the grammar. This brings with it two advantages over the RED morpheme in BRCT. First, it allows for a unified analysis of reduplicative allomorphy, which has no straightforward solutions in BRCT (see also Zimmermann 2013). Second, it makes red-specific size constraints obsolete, because the size of the reduplicant follows from the size of the prosodic affix and independent markedness constraints. Since each copied segment incurs a violation of Integrity (McCarthy and Prince 1995), MR predicts that Gen will only copy the smallest number of segments necessary to satisfy markedness. This naturally derives The Emergence of The Unmarked (TETU, McCarthy and Prince 1994).
2.4.2 Bidirectional Minimal Reduplication
My theory of BMR builds upon the main insights of MR, with two crucial differences:Footnote 6
-
(13)
Copying in BMR
-
a.
Bidirectionality: A defective node may trigger copying of either lower-level nodes (segments) or higher-level nodes (syllables, feet, phonological words, …).
-
b.
Pied-piping: Copying of a node N on tier Tn entails recursive copying of all nodes on lower tiers (Tier\(_{n-1}\), Tier\(_{n-2}\) etc.) which are linked to N via an uninterrupted path of association lines below Tn.
-
a.
Pied-piping (13-b) is already an implicit assumption in Kirchner’s original model, as copying of a segment in MR implies copying of a • with all features associated to it.Footnote 7 Pied-piping obeys the same transitivity principle as phonetic spell-out: if a node N on tier Tn is phonetically invisible, nodes dominated by N on lower tiers are also invisible unless they are dominated by some other visible node. Bidirectionality (13-a) entails that next to copying of lower nodes, Gen can also copy structures headed by a higher node if the respective Int constraint is outranked by markedness.
-
(14)
Int(egrity)
Assign * to each node on the highest tier of a copied structure.
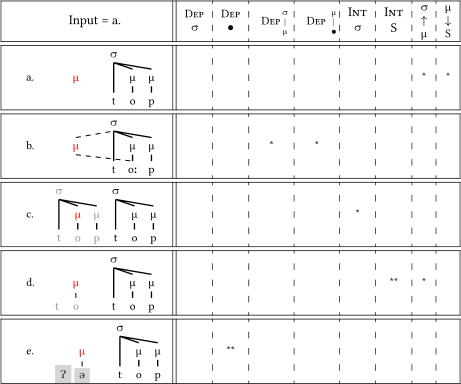
In (15), various responses to prosodic affixation are exercised. Candidate b. integrates the floating  into an existing structure and violates the relevant Dep| constraints. Candidate c. bidirectionally copies the syllable with all nodes associated to it, violating Int(σ) (14) but not Dep| as the lines are part of the copied structure. Candidate d. copies individual segments, violating Int(S) and Dep|. Candidate e. inserts epenthetic nodes, violating Dep but satisfying Dep| as that constraint is only sensitive to lines between colored nodes.
into an existing structure and violates the relevant Dep| constraints. Candidate c. bidirectionally copies the syllable with all nodes associated to it, violating Int(σ) (14) but not Dep| as the lines are part of the copied structure. Candidate d. copies individual segments, violating Int(S) and Dep|. Candidate e. inserts epenthetic nodes, violating Dep but satisfying Dep| as that constraint is only sensitive to lines between colored nodes.
-
(15)
Violation profiles for various repairs of an empty μ
As opposed to BRCT, BMR lacks constraints that evaluate identity or other faithfulness relations between base and copy material. On the one hand, this guarantees full compatibility with the modular architecture of ESC and the broader research program of GNLA. On the other hand, this raises the obvious question how identity effects can be accounted for, especially when they involve opacity between independent processes. In the next section, I will discuss two notorious cases of apparent base-reduplicant faithfulness in Lakota.
3 Lakota phonology and morphology
This section presents some background on Lakota phonology and morphology that will be relevant for the discussion of reduplication and the processes interacting with it.
3.1 Segment inventory
The vowel inventory of Lakota comprises five oral and three nasal vowels with three distinctive heights made up of [±h(igh)] and [±l(ow)] features (16). The low vowels do not contrast for backness and therefore lack a place feature, indicated by “Ø”. The Lakota consonant system is characterized by a ternary distinction between plain, aspirated and ejective plosives, as well as the presence of glottalized fricatives and the absence of rhotics (17).Footnote 8
-
(16)
Vowel phonemes
cor
Ø
lab
[+h, -l]
i ĩ
u ũ
[-h, -l]
e
o
[-h, +l]
a ã
-
(17)

Stems ending in a low vowel show a phonologically unpredictable allomorphy in that some vowels undergo vowel mutation (raising to /e/) while others do not.Footnote 9 Thus, the verb stem aphA ‘to strike’ changes to aphe before a trigger suffix such as -ʃni ‘neg’ while nija ‘to breathe’ does not change. As a notational convention, I follow Shaw (1980, 1985) and Ullrich (2011) in indicating low vowels that can undergo vowel mutation with the capital letters /A/ and /Ã/ throughout this paper.
3.2 Verbal morphology
Lakota is a highly synthetic language with complex verbal morphology. The verbal complex comprises the stem and the word layers, each with a set of designated affix slots (18). The stem domain comprises the root, all prefixes, infixes, the reduplicative suffix, and the verbal marker v (henceforth referred to as f(inal) v(owel)). The latter has two allomorphs depending on the shape of the stem: after C-final forms, it is an empty •, otherwise it has zero exponence (19) (for another example of affixes containing empty root nodes, see Trommer 2015b). The reduplicative morpheme is analyzed as a suffix because it copies the full syllable of monosyllabic and the final syllable of polysyllabic roots, cf. the examples in (20), (22), and (24).
-
(18)
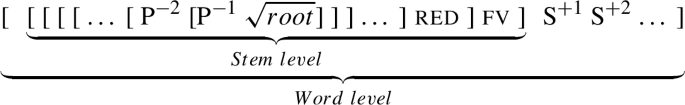
All other suffixes belong to the word-level domain. Evidence for this basic divide into stem- and word-level affixes comes from accentuation (word-level affixes never affect stress); see Shaw (1980) for further discussion. In terms of morphosemantics, prefixes are associated with agreement marking, valency modulation, and locative meanings. Suffixes are employed to form adverbials, to express various TAM meanings, and for nominalization.
-
(19)
[v]
↔
•
/
C)stem
Ø
/
V)stem
Both prefixes and suffixes may lack full segmental status and contain only single features or empty nodes (see Sect. 2.3). Apart from fv, the stem-level reduplicative suffix (μ) and the word-level terminative suffix ([-l]) are notable examples of non-segmental affixes in Lakota. The latter is obligatory in the absence of other word-level suffixes (as in most singular forms) and only manifests itself by inducing mutation.
3.3 Root shape
Lexical roots in Lakota are either C-final or V-final (Shaw 1980). The tables in (20) and (21) highlight the principal differences between C-final and V-final roots across various contexts. V-final roots may end in any of the eight Lakota vowels. The root-final vowel is also the stem-final vowel in simple verb stems (see Sect. 3.2) and is usually stressed, following the default peninitial stress pattern of the language (Shaw 1980).Footnote 10 Reduplication copies the final open root syllable including the final vowel. In nominal compounds and incorporated nouns, the final vowel is retained.
-
(20)

C-final roots, on the other hand, add a final vowel in simple stems. This vowel is never stressed and always takes the shape of /a/ or /A/. Reduplication does not copy the final vowel but applies to the final root syllable. The final V is also absent when the root appears as the first member of a lexical compound or in incorporation constructions.
-
(21)
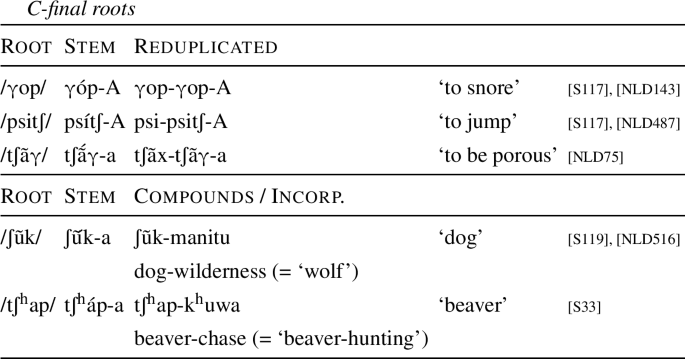
3.4 Reduplication
Lakota has fully productive verbal reduplication that conveys a wide range of grammatical and semantic meanings, including plurality of inanimate subjects, iterative and distributive aspect, and intensification.Footnote 11 The shape of the reduplicant is always a single syllable copying the final syllable of the stem that it attaches to (22)–(24).
-
(22)

-
(23)

-
(24)

The reduplicative suffix in Lakota attaches to the verbal root before the stem-final vowel (23) and before word-level agreement suffixes (24). The reduplicant is an exact copy of the root-final syllable, with a lack of common TETU modifications such as complex onset simplification. Reduplication in Lakota thus combines two typologically unusual traits: (i) the presence of productive partial reduplication without total reduplication (see discussion in Rubino 2013 and Stolz et al. 2011, 2015), and (ii) full syllable copying that does not obey a fixed segmental template (Moravcsik 1978; Marantz 1982; Downing 2000; Haugen 2005; Picanço 2005; Gordon 2016).
Under the assumption that the reduplicative morpheme contains an empty μ, both properties are straightforwardly accounted for by BMR. First, a floating μ may induce copying of an adjacent σ node with all segments associated to it, preserving even highly marked syllable structure. Second, the absence of total reduplication is simply due to the lack of morphemes containing higher-tier nodes such as Φ or ω that could induce total reduplication.
4 Analysis
4.1 Pattern I: Transparent application
The first scenario is local application: a phonological process affects a reduplicated form in the same way it would affect a non-reduplicated form. In Lakota, (at least) three processes exhibit transparent application: deletion, devoicing, and lenition.Footnote 12 All of these processes are driven by phonotactic restrictions holding both within and across morphemes. The table in (25) presents the relevant segmental alternations, and (26) – (28) contain the phonotactic constraints responsible for each of them.Footnote 13 All these constraints are undominated at the stem level.Footnote 14
-
(25)

The tableaux in (29) – (31) show how the three repair processes are optimal responses to markedness violations: deletion of a coda C to avoid a cluster of three or more consonants (29); devoicing to avoid a marked voiced coda C (30); and syllable-final coronal lenition (31). All three alternations are general processes that apply across the board and are not restricted to specific lexical items or constructions.
-
(26)
*CCC
Assign * for each phonetically visible sequence of three consonants.
-
(27)
*VcdCod
Assign * for each voiced obstruent in a coda of a monochrome syllable.
-
(28)
*FortisFinal
Assign * for each coronal non-continuant obstruent in a coda of a monochrome syllable.
Note that in the following tableaux, Max(N) constraints are to be read as shorthand for “Assign * for every N that is linked via an uninterrupted path of phonetically visible association lines to the highest node in the input but not in the output.” As stated before, different colors indicate morphological affiliation, and a black background marks phonetically invisible structures.
-
(29)
Deletion in triconsonantal clusters
-
(30)
Voiced coda devoicing

-
(31)
Coronal stop lenition

When reduplication creates a sequence of segments that violates any of these general phonotactic constraints, the final base consonant undergoes the same segmental alternations as outside of reduplication (32). This means that reduplicated forms obey the same constraints as any other forms at the stem level.
-
(32)

As mentioned earlier, the various reduplicative morphemes in Lakota contain an empty μ (33). This defective prosodic node is repaired by copying of the rightmost stem σ, with additional segmental modifications of the base syllable when necessary.
-
(33)

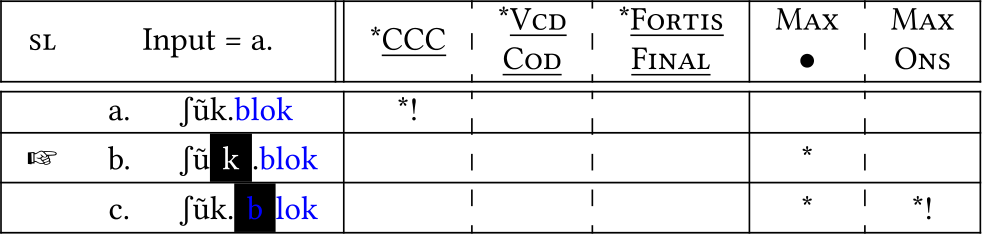
The tableau in (34) illustrates why full syllable reduplication is optimal upon μ-affixation. Integrating the  from the reduplicative morpheme (colored in red) into the underlying σ structure is ruled out by Dep(•→μ) and Dep(μ→σ) and would also violate an undominated constraint against long vowels in Lakota (34-b). Copying of individual segments (marked by a light gray color) does not satisfy μ→σ (34-c). Full-syllable copying creates an illicit CCC sequence (34-d). Therefore, deletion of the base coda C is optimal (34-e); the base modification is not backcopied to the reduplicant because Gen can only select material present in the input for copying.
from the reduplicative morpheme (colored in red) into the underlying σ structure is ruled out by Dep(•→μ) and Dep(μ→σ) and would also violate an undominated constraint against long vowels in Lakota (34-b). Copying of individual segments (marked by a light gray color) does not satisfy μ→σ (34-c). Full-syllable copying creates an illicit CCC sequence (34-d). Therefore, deletion of the base coda C is optimal (34-e); the base modification is not backcopied to the reduplicant because Gen can only select material present in the input for copying.
4.2 Pattern II: Overapplication
While BMR does not predict phonological backcopying, it can account for morphological overapplication because it operates under a derivational architecture of grammar. In any cyclic theory, whenever some process affects a string of segments at an earlier level than reduplication, reduplication will copy the outcome of that process, rendering the resulting output form non-surface-apparent (Mester 1986; Kiparsky 2010). In light of this, overapplication of palatalization in Lakota, briefly touched upon in Sect. 1, lends itself to a very basic analysis in terms of temporal ordering.
-
(34)
μ affixation triggers full syllable copying

Palatalization turns a prevocalic velar stop (/k/, /k’/, /kh/) into a postalveolar affricate (/tʃ/, /tʃ’/, /tʃh/) after the front-high oral vowel /i/ (35). Lexical roots and affixes can both trigger and undergo palatalization at the same time (cf. ki- ‘ben’ in (35-a)), and palatalization is strictly local (35-d).Footnote 15
-
(35)

Palatalization is enforced to obey the markedness constraint in ((36-a)), which penalizes occurrences of velar stops after the front vowel /i/ and is undominated at the stem level (37).Footnote 16 This constraint outranks the relevant faithfulness constraints Dep(•–cor) and Max(•–dor).
-
(36)
-
a.
*ikV Assign * for every pronounced [ikV] sequence. (McCarthy 2007:25)
-
b.
*ekV Assign * for every pronounced [ekV] sequence.
-
a.
-
(37)
Palatalization by underlying /i/

Underlying /e/ does not act as a trigger of palatalization (38). The reason for this is that the constraint *ekV (36-b) is outranked by the relevant faithfulness constraints (39).
-
(38)

-
(39)
Dep blocking palatalization after underlying /e/

When palatalization and reduplication apply in the same complex verb form, both the initial base and the initial copy C contain a palatalized segment (40). Note that ki-tʃos-tʃoz-e displays both palatalization overapplication and local application of devoicing.
-
(40)

This overapplication pattern is motivated by stem-level recursivity, in particular the fact that palatalization-inducing prefixes belong to an inner stem domain whereas reduplicative suffixes belong to an outer stem domain (see Sect. 3.2). Since palatalization applies before reduplication, the input for reduplication already contains a palatalized segment that is then copied (41). In fact, for the given grammar, overapplication is the only possible pattern in the reduplicated verb form.
-
(41)

4.3 Pattern III: Underapplication
The most intriguing and recalcitrant of the three interaction types examined here is underapplication of vowel mutation. Vowel mutation, which will be discussed in detail in Sect. 4.3.1, unexpectedly fails to apply to verb stems that normally do undergo mutation. However, this failure is observed only with V-final stems but not with C-final stems, which behave fully transparently (42). An account of vowel mutation thus has to reconcile the underapplication pattern of V-final stems with the transparent application pattern of C-final stems.
-
(42)

4.3.1 Vowel mutation
As mentioned earlier, Lakota has a process of vowel mutation that raises a low vowel /A/ or /Ã/ to /e/ before certain suffixes. Morphemes can either be undergoers or non-undergoers and, independently of that, triggers or non-triggers. Mutation applies only if a vowel belonging to an undergoer morpheme is followed by a trigger suffix, and fails to apply if one or both of these conditions are not met (43). While the present discussion mostly revolves around stem-final vowels, suffix vowels can also mutate, and certain suffixes such as -jA ‘caus’ are both triggers and undergoers at the same time. As mentioned before, I indicate mutable vowels with the capital letters /A/ and /Ã/ to distinguish them from the invariant /a/ and /ã/.
-
(43)

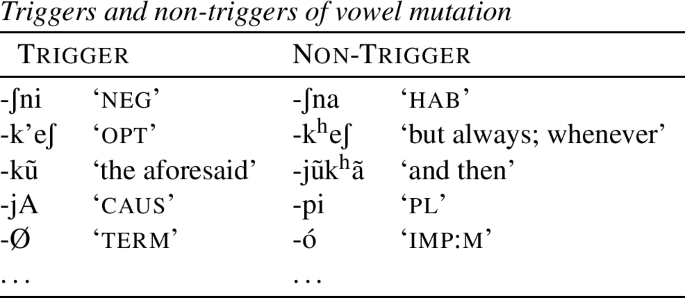
The status of being a trigger cannot be inferred from the phonological shape or the morphosemantics of the suffix. Table (44) presents a few examples of triggers and non-triggers (Shaw 1980:129–135).
-
(44)
To derive the basic mutation pattern, I make two critical assumptions. First, I assume trigger affixes carry a floating [-l(ow)] feature that may associate to a vocalic root node, thus affecting its quality. This is in line with a long tradition of research that has identified floating features as triggers of various types of segmental and tonal mutation (Akinlabi 1996; Wolf 2007; Trommer 2011; Paschen and Staroverov 2016). Second, I represent undergoer vowels as being underspecified for [±l(ow)], making them susceptible to mutation in the presence of a floating  feature. In the absence of a
feature. In the absence of a  feature, a
feature, a  feature is inserted epenthetically to resolve the missing [l] specification. The figures in (45) illustrate the behavior of the two types of V-final stems upon suffixation of the non-trigger suffix -pi ‘pl’ and the trigger suffix -ʃni ‘neg’.
feature is inserted epenthetically to resolve the missing [l] specification. The figures in (45) illustrate the behavior of the two types of V-final stems upon suffixation of the non-trigger suffix -pi ‘pl’ and the trigger suffix -ʃni ‘neg’.
-
(45)
V-final stems, word level

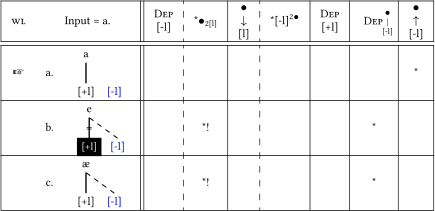
The immunity of fully specified vowels in Lakota follows from simple markedness constraints on association lines (46). Lakota has a high-ranked constraint *•2[l] against linking more than one [±l] feature to a single root node (see (7-c) for a definition). Since this constraint evaluates M-Structure, i.e. all lines independent of their phonetic visibility, it militates against both overwriting (46-b) and oversaturation, represented here as a near-open vowel /æ/ (46-c). The fully faithful candidate (46-a), which leaves  floating, is optimal.
floating, is optimal.
-
(46)
V-final non-undergoers
-
(47)
V-final undergoers

Successful mutation with undergoers is shown in (47). The underspecified • in (47-a) fatally violates high-ranked •→[l]. Candidates (47-b) and (47-d) are eliminated because they both incur fatal violations of Dep constraints. This makes candidate (47-c), which integrates the floating  , the winner.
, the winner.
Note that there are two constraints which are undominated on all strata in Lakota: alt, which militates against epenthetic lines between nodes of the same color (van Oostendorp 2007), and *Mix, which penalizes spreading. On these grounds, candidates violating either of these constraints are not shown in the tableaux.
4.3.2 Underapplication
The previous section has argued that mutation in Lakota is a combination of an underspecified • and a floating  feature. The crucial data for the curious underapplication pattern in reduplicated forms are presented in (48). The descriptive generalizations are as follows. Vowels that are unmutable in non-reduplicated forms remain unmutable in reduplication. Vowels that normally do undergo mutation, i.e. /A/ and /Ã/, resist mutation in reduplicated forms: instead of expected *aphe-phe-ʃni, the correct form for ‘does not strike’ is apha-pha-ʃni.
feature. The crucial data for the curious underapplication pattern in reduplicated forms are presented in (48). The descriptive generalizations are as follows. Vowels that are unmutable in non-reduplicated forms remain unmutable in reduplication. Vowels that normally do undergo mutation, i.e. /A/ and /Ã/, resist mutation in reduplicated forms: instead of expected *aphe-phe-ʃni, the correct form for ‘does not strike’ is apha-pha-ʃni.
-
(48)

I argue that underapplication reflects a ban on multiple linking of [-l] nodes. When a single [-l] faces two potential target •, it cannot link to both of them at the same time. Inserting a  feature is the next best repair option. Underapplication is thus a result of having too many targets for too few triggers, i.e., Trigger Poverty (3).
feature is the next best repair option. Underapplication is thus a result of having too many targets for too few triggers, i.e., Trigger Poverty (3).
The tableau in (50) shows how the underapplication pattern is derived (note that Alt is undominated in Lakota, and candidates violating Alt are not shown). The word-level phonology of Lakota has a general ban on [-l] features associated to more than one •, as formalized in (49-a). Reduplicated undergoer stems have two vowels underspecified for [l] which could potentially serve as targets for a floating  . Due to this constraint,
. Due to this constraint,  cannot associate to both Vs at the same time (candidate b.). The obvious alternative is local mutation of the final V and default insertion of [+l] to fill the base V, as shown in candidate c. (recall that •→[l] is undominated at wl). This violates both Dep([+l]) and Dep(•–[-l]). Recall from Sect. 4.3.1 that Dep([-l]) is undominated at the word level, and so it is never the case that two underspecified root nodes are accidentally filled with two distinct [-l] features, one belonging to a trigger suffix and the other one being epenthetic.
cannot associate to both Vs at the same time (candidate b.). The obvious alternative is local mutation of the final V and default insertion of [+l] to fill the base V, as shown in candidate c. (recall that •→[l] is undominated at wl). This violates both Dep([+l]) and Dep(•–[-l]). Recall from Sect. 4.3.1 that Dep([-l]) is undominated at the word level, and so it is never the case that two underspecified root nodes are accidentally filled with two distinct [-l] features, one belonging to a trigger suffix and the other one being epenthetic.
-
(49)
-
a.
*[-l]2•
Assign * for each [-l] feature associated to more than one root node.
-
b.
*[+l]2•
Assign * for each [+l] feature associated to more than one root node.
-
a.
There is, however, one candidate which satisfies the constraint against line insertion and which does not incur violations of any higher-ranked constraints: candidate d. This candidate leaves the  floating and fills the two underspecified Vs with a single inserted
floating and fills the two underspecified Vs with a single inserted  node. This is possible because the constraint against multiple linking of [+l] and the constraint penalizing floating
node. This is possible because the constraint against multiple linking of [+l] and the constraint penalizing floating  are ranked rather low. Inserting a
are ranked rather low. Inserting a  that hooks to two root nodes—in other words, double failure or underapplication of vowel mutation—is thus optimal compared to applying mutation once and inserting a
that hooks to two root nodes—in other words, double failure or underapplication of vowel mutation—is thus optimal compared to applying mutation once and inserting a  once. The fact that one target is in a base and the other target is in a reduplicant is purely accidental because mutation applies at the word level, after all stem level colors (including the copy color or the reduplicant) have been merged.
once. The fact that one target is in a base and the other target is in a reduplicant is purely accidental because mutation applies at the word level, after all stem level colors (including the copy color or the reduplicant) have been merged.
-
(50)
Reduplicated V-final undergoers resist mutation

There is one vexing prediction made by the constraint ranking in (50) that needs further consideration. The current grammar would predict that whenever two (or more) undergoer Vs are present, mutation will automatically be blocked, even when one of the undergoer Vs is affiliated with the trigger suffix. This is evidently wrong, as mutation applies locally irrespective of the number of undergoer vowels outside of reduplication (51).
-
(51)

The crucial difference between forms such as ijájejA and apháphaʃni is that in the latter, the two • share the same color (by virtue of color merging at the end of the stem stratum) whereas in the former, the two • have different colors. Since the word domain is non-cyclic, all suffixes are added and evaluated in parallel, which means their distinct morphological affiliations are visible to the word-level phonology (recall that the causative is a word-level affix and the reduplicating suffix is a stem-level affix). This allows us to make reference to those different colors in the form of a modified version of the NoSpread constraint penalizing spreading across morpheme boundaries (52).Footnote 17 Thus, (52), which outranks •→[-l], penalizes linking a  node to root nodes of different colors, and therefore favors local application of mutation. In other words, the grammar of Lakota allows insertion of
node to root nodes of different colors, and therefore favors local application of mutation. In other words, the grammar of Lakota allows insertion of  and also multiple linking, but only within the same morphological (color) domain.
and also multiple linking, but only within the same morphological (color) domain.
-
(52)

-
(53)
No underapplication with • of different colors

The violation profiles for the candidates in (53) are minimally different from those in (50) (note that candidate b. also violates Alt, as would a candidate where  links only to the final root node). The crucial point is that candidate d. is no longer optimal with respect to candidate c. because it incurs an additional violation of
links only to the final root node). The crucial point is that candidate d. is no longer optimal with respect to candidate c. because it incurs an additional violation of  . Data like (51) offer additional support for the different stratal specifications of reduplication and mutation and color merging between phonological strata.
. Data like (51) offer additional support for the different stratal specifications of reduplication and mutation and color merging between phonological strata.
4.3.3 C-final roots
The cases discussed so far have dealt with V-final roots. C-final roots behave differently from V-final roots in that mutation transparently affects the stem-final vowel in reduplicated undergoer stems (54).
-
(54)

Under the current approach, the reason for the “anomaly” of C-final roots, i.e. the fact that reduplication does not interfere with their mutability, is that they do not fall under Trigger Poverty. Stems built around C-final roots have only one underspecified final vowel, regardless of whether they are internally reduplicated. With one stem • and one suffix  , there is a perfect equilibrium between targets and triggers, and insertion of a default feature is not necessary (55).
, there is a perfect equilibrium between targets and triggers, and insertion of a default feature is not necessary (55).
-
(55)
Reduplicated C-final undergoers do not resist mutation

-
(56)
Reduplicated C-final non-undergoers resist mutation

The fact that some C-final roots act as non-undergoers follows from the assumption that their lexical entry contains a floating [+l] which docks to the • of the fv at the word level, obstructing realization of the affix  (56).Footnote 18 The verb form tʃãγa ‘be gristly’, for instance, is underlyingly /tʃãγ[+l]/ and donates its [+l] to the fv root node. This may be considered a rather marked configuration, admittedly; and in fact, the vast majority of C-final verbs in Lakota are undergoers, with C-final non-undergoers being the least common.Footnote 19 Regardless of their frequencies, the crucial difference between V-final and C-final stems is that the former copies an underspecified • and instantiates Trigger Poverty, while the latter does not.
(56).Footnote 18 The verb form tʃãγa ‘be gristly’, for instance, is underlyingly /tʃãγ[+l]/ and donates its [+l] to the fv root node. This may be considered a rather marked configuration, admittedly; and in fact, the vast majority of C-final verbs in Lakota are undergoers, with C-final non-undergoers being the least common.Footnote 19 Regardless of their frequencies, the crucial difference between V-final and C-final stems is that the former copies an underspecified • and instantiates Trigger Poverty, while the latter does not.
5 Discussion
5.1 Additional evidence: Mutated vowels as triggers of palatalization
Additional evidence for treating vowel mutation as a phonological process involving an underspecified • and a floating [-l] comes from the seemingly orthogonal process of palatalization. Recall from Sect. 4.2 that palatalization changes prevocalic /k, kh, k’/ into postalveolar affricates after /i/. Until the mid 20th century, palatalization was regularly triggered not only by /i/ but also by /e/ derived from /A, Ã/ (57). Underlying /e/, however, was never a trigger of palatalization (Boas and Deloria 1941, Ullrich 2011; cf. (38)).
-
(57)

Under a phonological approach, the ability of mutated Vs to affect velar stops in pre-1950 Lakota can be accounted for given just one additional stipulation: coronal unmarkedness. In the preceding sections, it was tacitly assumed that raising of a low vowel will automatically yield a front vowel /e/ instead of a back vowel /o/. Since low vowels are not contrastively specified for place in Lakota, there have to be constraints at work to ensure that a raised vowel will indeed acquire a front (coronal) place of articulation. These constraints are Dep(Place) constraints, and their ranking follows the universal place hierarchy (58), which states that cor is by default the least marked place of articulation (Avery and Rice 1989; Prince and Smolensky 1993/2004; Kang 2000; Lombardi 2002; Hirayama 2005; de Lacy 2006). Insertion of cor is thus cheaper than insertion of dor or lab, which results in mutated low vowels adopting a front place of articulation in addition to [-l].
-
(58)
Universal Place Markedness Hierarchy
cor ≺ {dor, lab}
The word level phonology of both contemporary and pre-1950 Lakota demotes *ikV and *ekV below Dep(•–cor), preventing palatalization by underlying front vowels. While a colored cor cannot spread, an epenthetic  may freely associate to a • because association lines between an epenthetic and some other node do not incur violations of the designated Dep| constraints (see Sect. 2). In modern-day Lakota, this is prevented by Max(•–dor), but in pre-1950 Lakota, that constraint was outranked by *ekV on wl, making overwriting possible. Therefore, derived /e/ triggered palatalization by virtue of the fact that it involves insertion of a colorless
may freely associate to a • because association lines between an epenthetic and some other node do not incur violations of the designated Dep| constraints (see Sect. 2). In modern-day Lakota, this is prevented by Max(•–dor), but in pre-1950 Lakota, that constraint was outranked by *ekV on wl, making overwriting possible. Therefore, derived /e/ triggered palatalization by virtue of the fact that it involves insertion of a colorless  node, with the relevant faithfulness constraint outranked by markedness (59).
node, with the relevant faithfulness constraint outranked by markedness (59).
-
(59)
Palatalization by derived /e/ (pre-1950 Lakota)

This reasoning can be extended to the demonstratives hé ‘that near you’, lé ‘this near me’, and é ‘the aforementioned’, which in pre-1950 Lakota also acted as exceptional triggers of palatalization (Shaw 1980:199–201). If we assume that the vowels in these words lack a place feature to begin with—a configuration independently predicted by ROTB—insertion of  will have the same catalyzing effect as in the case of mutated low Vs.
will have the same catalyzing effect as in the case of mutated low Vs.
The recent loss of palatalizability in present-day Lakota follows from a simple demotion of *ekV. Once *ekV no longer outranks Max(•–dor), there is no incentive for  to overwrite an underlying affix feature.
to overwrite an underlying affix feature.
5.2 Generality
In the previous section, I have treated local application as a default that is to be expected i) when no special order relation between reduplication and some other process holds leading to gratuitous copying (overapplication), and ii) when no imbalance between triggers and targets is given (underapplication). One may object that the solutions to presented to over- and underapplication here are particularly tailored to the idiosyncratic reduplication patterns of Lakota.
Two remarks are due here. First, timing of reduplication has long been identified as a source of overapplication in various theoretical frameworks, including Lexical Phonology (Wilbur 1973; Shaw 1980; Mester 1986; Steriade 1988), Stratal OT (Kiparsky 2010), and string-based theories of copying (Raimy 2000b).Footnote 20 The general insight that the order of reduplication relative to other operations can derive misapplication is thus not novel, and draws on a body of empirical evidence from outside reduplication as well.
Second, while the approach to underapplication outlined in this paper appears to require a very special configuration of features, root nodes and constraints, the core idea—Trigger Poverty inhibiting a certain process—is a very basic and general one.Footnote 21 Briefly consider the data from Kulina, an Arawan language of Brazil and Peru. Kulina has a mutation process whereby some suffixes (such as the directional -na but not the homophonous 1fut marker -na) raise a preceding /a/ to /e/ (60).Footnote 22
-
(60)

Reduplication copies a final stem syllable and can apply recursively to create an iconic meaning. When the reduplicated portion is a trigger suffix, the copies of that suffix do not induce mutation on their own bases (61).
-
(61)

The fact that copied triggers fail to act as triggers themselves is surprising under any account that assumes morphological identity between b and r, but is expected under a floating feature approach. If, as in Lakota, mutation is brought along by a floating [-l], and copying is a repair to fill empty prosodic nodes, Gen will only ever copy segments to fill empty nodes, but never unassociated features. Kulina thus presents a special kind of underapplication, one that does not directly fall under the definition of TP, but which nevertheless follows the same basic logic: When there are more targets than triggers, mutation is blocked where it might otherwise be expected.
On a final note, Trigger Poverty cannot be extended to languages where there is evidence against underspecification or default features. Languages with chain shift mutation such as /a/ → /e/ and /e/ → /i/, for instance, do not lend themselves to an account in terms of default features. If such a language were to show an underapplication pattern similar to that in Lakota, a Trigger Poverty analysis would not be viable because it relies on default features.
5.3 Alternative accounts
The main contestant for the analysis presented in the previous section is obviously BRCT. At first glance, the case of Lakota seems to make a paradigm case for br-faith constraints as proposed by BRCT, as these are by design supposed to easily capture both over- and underapplication.Footnote 23 Upon closer inspection, however, underapplication in Lakota proves highly problematic for standard BRCT. The reason is that any constraint that triggers mutation (e.g. MaxFloat) has to outrank io-faith, but by doing so, underapplication will inevitably lose against local or overapplication, regardless of br-faith (62).
-
(62)
Underapplication in BRCT

This problem is also acknowledged by Saba Kirchner (2009), who suggests that some morphemes, including the reduplicative morpheme, are lexically specified as [-ABL], i.e. as non-undergoers (morphemes without a [-ABL] features are undergoers by default). For this analysis to work, Kirchner has to make two additional assumptions. First, the crucial id constraint is multiply indexed, namely to red and to [-ABL]. Second, the final vowel added to C-final roots takes on the morphological affiliation of the stem (violating Consistency of Exponence, Prince and Smolensky 1993/2004). This causes the [-ABL] feature of the root and not that of red to be checked against id due to adjacency, which explains retention of lexical control over mutation in C-final roots.
Apart from the complications that each of these assumptions bring with them, and notwithstanding the introduction of an arbitrary diacritic [-ABL] feature, Kirchner’s approach crucially misses the generalization that C-final reduplicated undergoers behave just like V-final non-reduplicated ones. Kirchner’s analysis needs to resort to inconsistent exponency to derive what seems to be an exceptional pattern, where the same pattern falls out naturally in an underspecification account.
The divergent behavior of V-final and C-final roots pose a challenge for theories that assume morphological identity. In MDT (Inkelas and Zoll 2005; Inkelas 2008), reduplication is formalized as a construction with two daughter nodes with identical morphological content but potentially different cophonologies. The Lakota data thus prove challenging for MDT, albeit one that is not quite as serious as for BRCT. In fact, the sign-based framework underlying MDT equips it with a powerful artillery of iterative subcategorization.Footnote 24 For Lakota, one could thus imagine two red-stem constructions, one specified as an undergoer and the other as a non-undergoer depending on the properties of the daughters nodes. Mutation in extended stem or word constructions would then simply be determined by which red-stem is present, with cophonologies tailored to favor mutation in some stems but not in others.
A final alternative account that deserves mention is the one offered in Sande (2020). Sande proposes an analysis of doubly conditioned phonology within the theory of Cophonologies by Phase (CBP), combined with Harmonic Grammar (HG, Smolensky and Legendre 2006). The argument goes as follows: Morphemes are lexically specified for phonological content, subcategorization frames, and constraint weights. Weights can be positive or negative. When two morphemes are combined in a phase, they are evaluated based on the added weights of the individual morphemes. Doubly conditioned allomorphy then results from a configuration where both triggers and undergoers contribute negative weights to faithfulness constraints and/or positive weights to markedness constraints. Doubly conditioned allomorphy is thus analyzed as a threshold effect where a process is blocked by default but can become optimal when the weights are shifted in its favor. Sande (2020) also briefly discusses vowel mutation in Lakota, and sketches an analysis in terms of CBP & HG.Footnote 25 While such an approach is elegant and certainly capable of deriving the V mutation, it is questionable if it can extend to the underapplication pattern. Since reduplication is computed before mutation, the RED morpheme cannot contribute whatever weights would be required to block mutation upon affixation of a trigger suffix. Unless a “reduplicative stem” vocabulary item is stipulated that could perform this task, a CBP & HG approach appears to struggle with the underapplication data.
5.4 Other sources of misapplication
The previous sections have identified cyclicity and Trigger Poverty as causes of over- and underapplication in Lakota. Misapplication can also arise from other grammatical features and processes, however.
In the morphology, underapplication has been argued to result from blocking (Kiparsky 1973; Aronoff 1976), impoverishment (Halle and Marantz 1993), or allomorphy involving trigger and non-trigger variants of a morpheme. In the phonology, counterfeeding opacity is a classical example of underapplication in cyclic theories.
Another source of overapplication that is entirely unrelated to strata or cycles is copying of larger prosodic domains. Irie (2001) convincingly argues that overapplication of word-initial vowel raising in Fox is the result of copying a prosodic word, with raising applying transparently in both base and reduplicant (see Dahlstrom 1997 for a similar argument, and Burkhardt 2001 for an account using BRCT). Recently, Zimmermann (2020) has argued for an account of overapplication that makes use of Gradient Representations (Smolensky and Goldrick 2016; Rosen 2016) and features the notion of fission as shared activity: the gradual loss of activation in both base and reduplicant with each copy operation. Loss of activity makes copied segments weaker and less resistant to changes, which may induce overapplication.
5.5 Towards a typology of interactions
Table (63) summarizes the predictions made by stratal Bidirectional Minimal Reduplication and BRCT with regards to the interaction of reduplication and mutation. It is important to note that this typology outlines the way reduplication interacts with independent processes induced by a separate morpheme, but not with general phonological processes (be they dependent on the reduplicant or not). Such a typology will differ in several aspects. For instance, underapplication would be amenable to an analysis as counterfeeding opacity by ordering the respective phonological process before reduplication if reduplication creates the context for its application. Plausible candidates for such an account of underapplication are Akan palatalization (McCarthy and Prince 1995; Raimy 2000a; Dolphyne 2006) and Southern Paiute w-nasalization (Sapir 1930; Raimy 2000a).
-
(63)

As demonstrated in Sect. 5.3 above, underapplication of independent morphological processes are not predicted by standard BRCT without the addition of other indexed constraints. Also, as pointed out in Sect. 5.4, there may be additional ways to derive transparent and misapplication, e.g. by copying of non-minimal domains.
6 Conclusion
In this paper, I have argued for a phonological account of over- and underapplication in Lakota that is based on the idea of non-segmental affixation. I have shown how transparent application is the default scenario when reduplication applies simultaneously with (as in the case of Lakota cluster simplification) or is ordered before some independent process. Overapplication is the expected outcome when reduplication applies after some other process (here, palatalization). Underapplication, which at first glance seems highly problematic for item-based approaches, is derived with the help of Trigger Poverty, a configuration whereby a shortage of triggers against an overabundance of potential targets blocks a certain process altogether. At the same time, I have shown that this particular type of opacity is not derivable with standard BRCT.
The Lakota reduplication data has several important consequences. First, they exemplify the versatility of item-based accounts of non-concatenative morphology, particularly in cases where several processes are intertwined in a non-trivial way. At the expense of a greater representational freedom, item-based approaches secure a tight modulation of grammar such that the phonology is blind to lexical information of morphemes. Second, it strengthens the general argument for a modular and feed-forward architecture of grammar and a phonology organized around broad strata such as the word and stem levels. Third, it demonstrates that identity effects in over- and underapplication, which were at the heart of the original arguments for br-correspondence, can in fact be accounted for without the notion of a red morpheme and BR-faithfulness.
Notes
Lakota data discussed in this paper come from two sources: Shaw’s 1980 monograph, which is largely built on the original descriptive grammar by Boas and Deloria (1941), and the New Lakota Dictionary (NLD; Ullrich 2011). The NLD was compiled with the help of over 300 consultants from 1982 to 2008 (ibid., ix). Shaw (1980) and Ullrich (2011) will be abbreviated as [S] and [NLD] with the appropriate page numbers throughout the paper.
Colors are visible in the online version of this article.
The observation that stem-level phonology is different from word-level phonology in that each stem-level affix appears to constitute its own domain of cyclic evaluation dates back to Lexical Phonology, and is integrated into Kiparsky’s version of Stratal OT. Bermúdez-Otero (2012, 2013) takes a different stance on what he calls the stem-level syndrome, arguing instead that all outputs of stem-level affixation are stored as separate units in the lexicon. The predictions for Lakota would be the same under both frameworks: if palatalized stem forms are retrieved as such from the lexicon before reduplication applies, the result will again be overapplication.
Trommer (2011) and Trommer and Zimmermann (2014) do not include the copy operation. Zimmermann (2017a) discussses fusing of color indices with nodes on the same tier as a fifth option. This operation is not relevant here because, following Yu (2007), I assume that pivotal positions for infixes are directly encoded in the lexical representations of morphemes.
The idea that copying involves selection of a continuous substring from an underlying representation is conceptually similar to the notion of string-based selection in Frampton (2009).
Zimmermann (2017b) proposes a family of faithfulness constraints (e.g. Faithσ-S: “Given σ1 dominating segment Sx in the input. Assign * for every output syllable σ1 not dominating Sx in the output.”) which have a similar effect as (13-b) to derive what she dubs “maximal copying”. The important difference to BMR is that Zimmermann’s constraints are violable. The empirical implications of this still remain to be explored.
The plosives [b] and [g] only occur before vowels and /l/ or as the result of voicing in certain environments (S17, NLD755; see also Rood 2016. The phonemic status of the glottal stop is debatable because its distribution is limited to word-initial and intervocalic positions (NLD749). The velar fricative series is phonetically more accurately described as uvular (Ingham 2001:2).
Before a small number of suffixes, mutable vowels are raised to /ĩ/ instead of /e/ (NLD755). Besides their different target vowel, these suffixes behave the same way as the regular mutation triggers (S355). The present analysis of mutation and underapplication can readily be extended to /ĩ/-mutation if the special triggers are additionally specified for floating [+high] and [nas] features, and no constraint militates against multiple linking of those features.
Other functions of verbal reduplication include attenuation, formation of deverbal adverbs, and subject agreement with possessed body parts in the plural. Less productive examples of reduplication are found with adverbs, cf. lig-lila very-red ‘an awful lot’, affixes, as in nija-ʃni-ʃni breathe-neg-red ‘all out of breath’ (S324f), and agent nouns, cf. wa-wĩjã-jã-ka ‘a man who runs after women, a womanizer’ < wĩjã ‘woman’ (NLD807).
Other phonotactically driven processes showing local application are coronal dissimilation (S214) and deglottalization (S333, NLD101). Since the former is restricted in its usage and the latter is limited to a few lexical items due to the rarity of roots with final glottalized segments, they are not considered here.
Lenition is sometimes obscured by dissimilation when the stem contains another coronal sound, see Shaw (1980:335–338) for examples and further discussion.
*VcdCod is obviously demoted on a later stratum, cf. ainab (variant ainãm) ‘on the farther side of sth.’, derived by intervocalic voicing and final V deletion from a-inaph-A [NLD34]. Word- and phrase-level phonologies are generally more permissive in terms of phonotactics.
I am not aware of any verbal root in Lakota ending in a sequence of a velar stop and /i/. The prediction from my analysis of palatalization and reduplication as stem-level processes would be that such a base should palatalize the initial C of its reduplicant, e.g. /ki/ → /ki-tʃi/. Note that khi- in (35-d) is a verbal prefix that cannot be reduplicated.
The need for segment-specific constraints rather than constraints on, say, a coronal feature arises from the fact that /ĩ/ never triggers palatalization, and /e/ only does in special environments.
Following the conventions in Trommer (2011:63), each box refers to a unique color in the notation of this constraint.
I further assume that Dep([+l]) is undominated at sl, which is why the empty root node survives the stem-level evaluation and gets fully specified only at wl.
An anonymous reviewer pointed out the conceptual similarity of Trigger Poverty to the “sour grapes” syndrome. And indeed, both cases have in common that a process that could apply is blocked in a certain environment, even though there is a crucial technical difference in that Trigger Poverty implies applying another process (default feature insertion) instead of the one that is blocked.
Unlike Lakota, there is no distinction between undergoers and non-undergoers in Kulina, i.e. trigger suffixes always induce mutation when they are adjacent to a low vowel. There is a minor complication in that for some morphemes, vowels are raised to /i/ instead of /e/, but this is not relevant for the present discussion.
It is worth noting that underapplication does not always foster identity. For instance, Palauan (Austronesian) has a process of unstressed vowel reduction that exceptionally fails to apply to fixed /e/ in monosyllabic reduplicants while it regularly applies to base vowels (Flora 1974). For that reason, underapplication of vowel reduction gives rise to surface non-identity between base and reduplicant.
See Zukoff (2020) for a discussion of data from Ponaponean which could possibly prove problematic for MDT.
Sande follows Albright (2002) and reports /-e/-final stems that alternate with -/a/ in Lakota. This representation is somewhat misleading and likely conditioned on strict adherence to surface paradigms. Under an underspecification account, the cited example ʧhepe (p. 478) would be analyzed as a mutable C-final verb root with regular mutation in the singular: /ʧhep-A-[-l]/ be.fat-fv-term ‘(s)he is fat’; cf. ʧhepapi be.fat-fv-pl ‘they are fat’ without a trigger in the plural suffix (NLD94).
References
Akinlabi, Akinbiyi. 1996. Featural affixation. Journal of Linguistics 32: 239–289.
Albright, Adam. 2002. A restricted model of UR discovery. Unpublished Ms., University of California at Santa Cruz.
Anttila, Arto. 2002. Morphologically conditioned phonological alternations. Natural Language and Linguistic Theory 20: 1–42.
Aronoff, Mark. 1976. Word formation in generative grammar. Cambridge: MIT Press.
Avery, Peter, and Keren Rice. 1989. Segmental structure and coronal underspecification. Phonology 6(2): 179–200.
Benua, Laura. 1997. Transderivational identity: Phonological relations between words. PhD diss., UMass, Amherst.
Bermúdez-Otero, Ricardo. 2012. The architecture of grammar and the division of labour in exponence. In The morphology and phonology of exponence, ed. Jochen Trommer, 8–83. Oxford: University Press.
Bermúdez-Otero, Ricardo. 2013. The stem-level syndrome. Paper presented at the Speaker Series of the University of Pennsylvania Linguistics Department, Philadelphia, 11 Apr 2013.
Bermúdez-Otero, Ricardo. 2018. Stratal phonology. In The Routledge handbook of phonological theory, eds. S. J. Hannahs and Anna R. K. Bosch, 100–134. Abingdon: Routledge.
Boas, Franz, and Ella Deloria. 1941. Dakota grammar. Vol. 23 of Memoirs of the national academy of sciences. Washington: United States Government Printing Office.
Booij, Gert. 2011. Morpheme structure constraints. In The Blackwell companion to phonology, eds. Marc van Oostendorp, Colin J. Ewen, Elizabeth Hume, and Keren Rice. Vol. 4 of Blackwell companions to linguistics series, 2049–2069. Oxford: Wiley-Blackwell.
Burkhardt, Petra. 2001. Multiple faithfulness relations in Fox (Central Algonquian) reduplication. In ConSOLE X, Leiden, 33–48.
Bye, Patrick, and Peter Svenonius. 2012. Non-concatenative morphology as epiphenomenon. In The morphology and phonology of exponence, ed. Jochen Trommer, 426–495. Oxford: University Press.
Clements, G. Nick, and Elizabeth V. Hume. 1995. The internal organization of speech sounds. In The handbook of phonological theory, ed. John Anton Goldsmith. Blackwell handbooks in linguistics, 245–306. Oxford: Blackwell.
Dahlstrom, Amy. 1997. Fox (Mesquakie) reduplication. International Journal of American Linguistics 63(2): 205–226.
Davis, Stuart, and Isao Ueda. 2002. Mora augmentation processes in Japanese. Journal of Japanese Linguistics 18(1): 1–24.
de Lacy, Paul. 2006. Markedness. Cambridge: University Press.
Dienst, Stefan. 2014. A grammar of Kulina. Vol. 66 of Mouton grammar library. Berlin/Boston: de Gruyter.
Dolphyne, Florence Abenda. 2006. The Akan (Twi-Fante) language. Accra: Woeli Publishing Services.
Downing, Laura J. 2000. Morphological and prosodic constraints on Kinande verbal reduplication. Phonology 17(1): 1–38.
Flora, Marie Jo-Ann. 1974. Palauan phonology and morphology. PhD diss., University of California, San Diego.
Frampton, John. 2009. Distributed reduplication. Linguistic inquiry monographs. Cambridge: MIT Press.
Gordon, Matthew K. 2016. Phonological typology. Oxford: University Press.
Halle, Morris, and Alec Marantz. 1993. Distributed Morphology and the pieces of inflection. In The view from building 20, eds. Kenneth Locke Hale and Samuel Jay Keyser, 111–176. Cambridge: MIT Press.
Haugen, Jason D. 2005. Reduplicative allomorphy and language prehistory in Uto-Aztecan, ed. Bernhard Hurch. Vol. 28 of Empirical approaches to language typology, 315–349. Berlin: Mouton de Gruyter.
Hirayama, Manami. 2005. Place asymmetry and markedness of labials in Japanese. In ConSOLE XIII, eds. Marie K. Huffman and Rena A. Krakow, 121–133. Leiden.
Ingham, Bruce. 2001. English-Lakota dictionary. Richmond: Curzon Press.
Inkelas, Sharon. 2008. The dual theory of reduplication. Linguistics 46(2): 351–401.
Inkelas, Sharon. 2012. Reduplication. In The morphology and phonology of exponence, ed. Jochen Trommer, 355–378. Oxford: University Press.
Inkelas, Sharon, and Cheryl Zoll. 2005. Reduplication: Doubling in morphology. Cambridge studies in linguistics. Cambridge: University Press.
Inkelas, Sharon, and Cheryl Zoll. 2007. Is grammar dependence real? A comparison between cophonological and indexed constraint approaches to morphologically conditioned phonology. Linguistics 45(1): 133–171.
Irie, Maki. 2001. On reduplication in Fox. Unpublished Ms., University of California, Irvine.
Kager, René. 2004. Optimality Theory. Cambridge: University Press.
Kang, Yoonjung. 2000. The phonetics and phonology of coronal markedness and unmarkedness. PhD diss., MIT.
Kiparsky, Paul. 1973. ‘Elsewhere’ in phonology. In A festschrift for Morris Halle, eds. S. R. Anderson and Paul Kiparsky, 93–106. New York: Holt, Rinehart and Winston.
Kiparsky, Paul. 1982. Lexical Morphology and Phonology. In Linguistics in the morning calm: selected papers from SICOL-1981, ed. In-Seok Yang, 3–91. Seoul: Hanshin Publishing Company.
Kiparsky, Paul. 1985. Some consequences of Lexical Phonology. Phonology 2(1): 85–138.
Kiparsky, Paul. 1993. Blocking in nonderived environments. In Studies in lexical phonology, eds. Sharon Hargus and Ellen Kaisse, 277–313. San Diego: Academic Press.
Kiparsky, Paul. 2000. Opacity and cyclicity. The Linguistic Review 17: 351–367.
Kiparsky, Paul. 2010. Reduplication in Stratal OT. In Reality exploration and discovery: Pattern interaction in language & life. (Festschrift for K.P. Mohanan), eds. Linda Ann Uyechi and Lian-Hee Wee, 125–141. Stanford: CSLI Publications.
Kiparsky, Paul. 2015. Stratal OT. In Capturing phonological shades within and across languages, eds. Yuchau E. Hsiao and Lian-Hee Wee, 2–44. Newcastle upon Tyne: Cambridge Scholars Publishing.
Kula, Nancy C. 2008. Derived environment effects. Lingua 118: 1328–1343.
Kurisu, Kazutaka. 2001. The phonology of morpheme realization. PhD diss., University of California, Santa Cruz.
Lombardi, Linda. 2002. Coronal epenthesis and markedness. Phonology 19(2): 219–251.
Marantz, Alec. 1982. Re reduplication. Linguistic Inquiry 13: 483–545.
Mc Laughlin, Fiona. 1994. Consonant mutation in Seereer-Siin. Studies in African Linguistics 23(3): 279–313.
Mc Laughlin, Fiona. 2000. Consonant mutation and reduplication in Seereer-Siin. Phonology 17: 333–363.
McCarthy, John J. 1988. Feature geometry and dependency. Phonetica 43: 84–108.
McCarthy, John J. 2007. Hidden generalizations. London: Equinox.
McCarthy, John J., and Alan S. Prince. 1994. The emergence of the unmarked. In North East Linguistic Society (NELS) 24, ed. Mercé González, 333–379. Amherst: GLSA.
McCarthy, John J., and Alan S. Prince. 1995. Faithfulness and reduplicative identity. In University of Massachusetts occasional papers in linguistics 18: Papers in optimality theory, eds. Jill Beckman, Laura Dickey, and Suzanne Urbanczyk, 249–384. Amherst: GLSA.
Mester, Armin. 1986. Studies in tier structure. PhD diss., University of Massachusetts, Amherst.
Mirzayan, Armik. 2010. Lakota intonation and prosody. PhD diss., University of Colorado.
Mohanan, Karuvannur Puthanveettil. 1982. Lexical phonology. PhD diss., MIT.
Moravcsik, Edith A. 1978. Reduplicative constructions. In Universals of human language, ed. Joseph H. Greenberg, 297–334. Stanford: University Press.
Nespor, Marina, and Irene Vogel. 1986. Prosodic phonology. Dordrecht: Foris.
Paschen, Ludger, and Peter Staroverov. 2016. Floating, but ordered: An account of Sye verb root alternations. In North East Linguistic Society (NELS) 46, eds. Christopher Hammerly and Brandon Pricket, Vol. 3, 123–132.
Pater, Joe. 2009. Morpheme-specific phonology. In Phonological argumentation: Essays on evidence and motivation, ed. Steve Parker, 123–154. London: Equinox.
Pesetsky, David. 1979. Russian morphology and lexical theory. Unpublished Ms., MIT.
Picanço, Gessiane Lobato. 2005. Mundurukú: Phonetics, phonology, synchrony, diachrony. PhD diss., University of British Columbia.
Prince, Alan, and Paul Smolensky. 1993/2004. Optimality theory. Oxford: Blackwell.
Pulleyblank, Douglas. 1986. Tone in lexical phonology. Dordrecht: Reidel.
Raimy, Eric. 2000a. The phonology and morphology of reduplication. Vol. 52 of Studies in generative grammar. Berlin: deGruyter.
Raimy, Eric. 2000b. Remarks on backcopying. Linguistic Inquiry 31(3): 541–552.
Rood, David. 2016. The phonology of Lakota voiced stops. In Advances in the study of Siouan languages and linguistics, eds. Catherine Rudin and Bryan J. Gordon, 233–255. Berlin: Language Science Press.
Rosen, Eric. 2016. Predicting the unpredictable. In Berkeley Linguistic Society 42, eds. Emily Clem, Virginia Dawson, Alice Shen, Amalia Horan Skilton, Geoff Bacon, Aandrew Cheng, and Erik Hans Maier, 235–249. Berkeley: Berkeley Linguistic Society.
Rubach, Jerzy. 2000. Glide and glottal stop insertion in Slavic languages. Linguistic Inquiry 31: 271–317.
Rubach, Jerzy. 2003. Polish palatalization in derivational optimality theory. Lingua 113: 197–237.
Rubach, Jerzy. 2008. An overview of lexical phonology. Language and Linguistics Compass 2: 456–477.
Rubino, Carl. 2013. Reduplication. In The world atlas of language structures online, eds. Matthew S. Dryer and Martin Haspelmath. Leipzig: Max Planck Institute for Evolutionary Anthropology. http://wals.info/chapter/27, last accessed 13 August 2021.
Saba Kirchner, Jesse. 2009. Ablaut and reduplication in Dakota. In 12th annual workshop on American indigenous languages, eds. Daisy Rosenblum and Carrie Meeker. Vol. 20 of Santa Barbara papers in linguistics.
Saba Kirchner, Jesse. 2010. Minimal reduplication. PhD diss., University of California at Santa Cruz.
Saba Kirchner, Jesse. 2013. Minimal reduplication and reduplicative exponence. Morphology 23: 227–243.
Sande, Hannah. 2020. Morphologically conditioned phonology with two triggers. Phonology 37(3): 453–493. https://doi.org/10.1017/S0952675720000238.
Sapir, Edward. 1930. Southern Paiute: A Shoshonean language. Proceedings of the American Society of Arts and Sciences 65: 1–3.
Shaw, Patricia A. 1980. Theoretical issues in Dakota phonology and morphology. Outstanding dissertations in linguistics. New York: Garland.
Shaw, Patricia A. 1985. Modularism and substantive constraints in Dakota lexical phonology. Phonology Yearbook 2: 173–202.
Smolensky, Paul. 1996. The initial state and richness of the base in optimality theory. Technical report JHU-CogSci-96-4.
Smolensky, Paul, and Matthew Goldrick. 2016. Gradient symbolic representations in grammar: The case of French liaison. Unpublished Ms. [ROA 1286], Microsoft Research AI/Johns Hopkins and Northwestern.
Smolensky, Paul, and Geraldine Legendre. 2006. The harmonic mind. Cambridge: MIT Press.
Steriade, Donca. 1988. Reduplication and syllable transfer in Sanskrit and elsewhere. Phonology 5: 73–155.
Stolz, Thomas, Cornelia Stroh, and Ania Urdze. 2011. Total reduplication. Vol. 8 of Studia typologica. Bremen: Akademie Verlag.
Stolz, Thomas, Ania Urdze, Julia Nintemann, and Marina Tsareva. 2015. When some dots turn a different color …. Studies in Languages 39(4): 795–834.
Trommer, Jochen. 2011. Phonological aspects of Western Nilotic mutation morphology. Habilitation, Leipzig University.
Trommer, Jochen. 2015a. Moraic affixes and morphological colors in Dinka. Linguistic Inquiry 46(1): 77–112.
Trommer, Jochen. 2015b. Pari consonant mutation as defective root node affixation. In The segment in phonetics and phonology, eds. Eric Raimy and Charles E. Cairns, 283–313. Oxford: Wiley Blackwell. ISBN 978-1-118-55540-8.
Trommer, Jochen. 2020. Cumulativity in German umlaut. Natural Language & Linguistic Theory. https://doi.org/10.1007/s11049-020-09479-7.
Trommer, Jochen, and Eva Zimmermann. 2014. Generalised mora affixation and quantity-manipulating morphology. Phonology 31: 463–510.
Ullrich, Jan. 2011. New Lakota dictionary [NLD], 2nd edn. Bloomington: Lakota Language Consortium. [NLD].
van Oostendorp, Marc. 2006. A theory of morphosyntactic colours. Unpublished Ms., Meertens Institute.
van Oostendorp, Marc. 2007. Derived environment effects and consistency of exponence. In Freedom of analysis?, eds. Sylvia Blaho, Patrik Bye, and Martin Krämer, 123–148. Berlin: Mouton de Gruyter.
Wilbur, Ronnie Bring. 1973. The phonology of reduplication. PhD diss., University of Illinois at Urbana-Champaign.
Wolf, Matthew. 2007. For an autosegmental theory of mutation. In Papers in optimality theory 3, eds. Leah Bateman, Michael O’Keefe, Ehren Reilly, and Adam Werle. Vol. 32 of University of Massachusetts occasional papers in linguistics (UMOP), 315–404. Amherst: GLSA.
Yu, Alan C. L. 2007. A natural history of infixation. Vol. 15 of Oxford studies in theoretical linguistics. Oxford: University Press.
Zimmermann, Eva. 2013. Non-concatenative allomorphy is generalized prosodic affixation. Lingua 134: 1–26.
Zimmermann, Eva. 2017a. Morphological length and prosodically defective morphemes. Vol. 1 of Oxford studies in phonology and phonetics. Oxford: University Press.
Zimmermann, Eva. 2017b. Multiple reduplication as non-segmental affixation: A case study from Nuuchahnulth. In North East Linguistic Society (NELS) 47, eds. Andrew Lamont and Katerina Tetzloff, 285–294. Amherst: GLSA.
Zimmermann, Eva. 2020. Reduplication as weakening: Explaining the overapplication of reductions. Paper presented at LSA 2020, New Orleans.
Zukoff, Sam. 2020. Reduplicant shape alternations in Ponapean. Paper presented at LSA 2020, New Orleans.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Paschen, L. Trigger poverty and reduplicative identity in Lakota. Nat Lang Linguist Theory 40, 837–873 (2022). https://doi.org/10.1007/s11049-021-09525-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11049-021-09525-y