Abstract
Images are a crucial component in contemporary data transmission. Numerous images are transmitted daily through the open-source network. This paper presents a multi-image encryption scheme that utilises flip-shift-rotate synchronous-permutation-diffusion (FSR-SPD) processes to ensure the security of multiple images in a single encryption operation. The proposed encryption technique distinguishes itself from current multi-image encryption methods by utilising SPD operation and rapid FSR-based pixel-shuffling and diffusion operation. The SPD is a cryptographic technique that involves the simultaneous application of permutation and diffusion methods. The FSR-based process involves the manipulation of pixels through three different operations, namely flipping, shifting, and rotating. In the process of encryption, the image components of red, green, and blue colours are merged into a single composite image. The large image is partitioned into non-overlapping blocks of uniform size. The SPD technique is employed to tackle each specific block. The encryption method is efficient and expeditious as it exhibits high performance with both FSR and SPD procedures. The method employs a single, fixed-type, one-dimensional, piecewise linear chaotic map (PWLCM) for both the permutation and diffusion phases, resulting in high efficiency in both software and hardware. The proposed method is assessed using key space, histogram variance, neighbouring pixel correlation, information entropy, and computational complexity. The proposed method has a much bigger key space than the comparative method. Compared to comparison approaches, the suggested solution reduces encrypted picture histogram variance by 6.22% and neighbouring pixel correlations by 77.78%. Compared to the comparison technique, the proposed scheme has a slightly higher information entropy of 0.0025%. Other multiple-color image encryption methods are more computationally intensive than the suggested method. Computer simulations, security analysis, and comparison analysis evaluated the proposed methodology. The results show it outperforms multiple images encrypting methods.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The utilisation of the internet for media transmission, particularly images, has significantly increased due to technological advancements and the availability of efficient and time-saving service-based Android applications [1]. Images include the vast bulk of important information, such as government documents, satellite reports, military secrets, etc. The transfer of digital images has raised security concerns. There are two primary approaches to ensuring the security of digital images. The first involves identifying and detecting viruses within the systems responsible for storing and transmitting these images. The second approach centres on preventing viruses from infecting these systems in the first place. Continuous capture, analysis, and reporting of daily network activities and events are essential functions of detection systems. Various techniques are employed in the process of capturing, analysing, and reporting. These techniques include virus detection, vulnerability scanning, intrusion detection, and other ad hoc methods. Wani et al. [2] have developed a Software Defined Network (SDN)-based intrusion detection system, which is one of the most effective intrusion detection systems available. The system employs a deep learning classifier to identify anomalies in Internet of Things (IoT) devices. The prediction of network security situational awareness has gained increasing attention for intrusion detection [3]. To detect viruses, it is necessary to implement a 24-h monitoring system that can promptly notify security personnel. Therefore, implementing a prevention-focused system security policy is likely to be the most effective approach. There are two primary approaches for preventing unauthorised access to images: data hiding and data encryption. The data hiding approach is employed to mitigate the risk of volatile data being compromised or misused by concealing it from unauthorised access. Hassan and Gutub devised a data hiding technique in [4] that minimises image distortion and maximises embedding capacity during data hiding. The authors suggest two high payload embedding techniques for data concealment: hue-based embedding (HBE) and three-planes embedding (TPE). Gutub [5] developed a method for improving the authentication of images by securing the watermarking of concealed data with shares derived from counting-based secret sharing. The data hiding method is particularly appropriate when the objective is to embed information within images without emphasising strong encryption or security features.
So, encryption is considered one of the most effective prevention approaches for protecting images. Various encryption techniques are available for securing images, such as Data Encryption Standard (DES), Triple-DES (3DES), Advanced Encryption Standard (AES), and more [6,7,8]. The encryption of images using conventional techniques is ineffective due to the large volume of data and significant pixel correlation present in images [9, 10]. Verma et al. [11] devised a conventional image encryption technique that employs an improved version of Caesar cipher and modular arithmetic to transform plaintext into ciphertext. Several keyless techniques have been developed for encrypting images, as documented in references [12, 13]. However, these algorithms are inadequate for secure image encryption in situations where maintaining confidentiality and resiliency is crucial. Implementing a robust encryption method is therefore of the utmost significance. Machine Learning (ML) algorithms are currently utilised in the security industry. The ML algorithms provide mathematical model-based algorithms that develop automatically through experience [14]. Data-driven machine learning algorithms make decisions without being explicitly programmed to do so. Nevertheless, there are several disadvantages and difficulties associated with the use of machine learning for image encryption, such as computational overhead, key management, susceptibility to adversarial assaults, etc. Another author Wang et al. [15] developed a block switching approach to provide deep learning security. It is a defense strategy against adversarial attacks based on stochasticity. However, the block switching approach has certain disadvantages such as reduced determinism, performance variability, increased computational overhead, tuning complexity, etc. Combining chaos-based encryption methods with image encryption is effective. Kumar et al. [16] developed a medical image encryption method that combines chaotic maps and deep learning. The advantages of combining chaotic systems and deep learning for image encryption are accompanied by several disadvantages and difficulties. High Computational Complexity because the deep learning neural networks are computationally intensive and require substantial processing power, Key Management because it requires multiple key parameters, etc., are potential disadvantages. To achieve a balance between speed and security, it is preferable to utilise exclusively image encryption techniques based on chaotic maps.
Chaotic systems make great candidates for an effective and powerful encryption method because they display extraordinarily complicated behaviour, are sensitive to chaotic factors, have mixed features, and are ergodic [17]. Numerous single-image encryption (SIE) systems employ chaotic techniques to generate robust and secure cipher images [18,19,20,21,22]. SIE methods use chaotic “high-dimensional” (HD) and “one-dimensional” (1D) systems [23]. The 1D chaotic map seems favourable because of its simple design, which enables it to make better use of resources, yet it has a small key space. HD chaotic maps are resource-intensive and complex, yet they have a lot of key spaces [24, 25]. To give the technique a vast key space, high efficiency, and resource efficiency, some researchers have used multi-type chaotic 1D maps in image encryptions [26,27,28,29,30]. The key space is expanded, efficiency is increased, security is enhanced, but software-hardware efficiency is decreased when different chaotic 1D maps are used in image encryptions. The proposed method makes extensive use of the single Piece-wise Linear Chaotic Map (PWLCM) to improve security, key space, encryption, and software-hardware efficiency. In addition, and without using trigonometric functions, the PWLCM system lowers computation by requiring only one division and a maximum of two additions in a single iteration.
In this big data era, a significant number of images are transmitted across the communications network. When SIE techniques are consistently employed to secure many images, the encryption process’ efficiency suffers [31]. To strengthen the security of the encryption, many authors use multiple image encryption (MIE) algorithms for multi-image encryption. MIE algorithms have been created in a variety of domains during the past few years, including transform, chaotic, and a mix of transform and chaotic domains. The encryption efficacy of the transform domain-based MIE algorithms [32,33,34,35] is lower. This is due to the requirement of information translation between the spatial and transform domains in these techniques. The encryption effectiveness of the algorithm is increased using chaotic domain MIE techniques. Bit-plane operation was used by Tang et al. [36] to create a chaotic domain-based MIE algorithm. In this method, the chaotic map is used to carry out the encryption process; nevertheless, the algorithm’s encryption efficacy is decreased because of the challenge, that means complex bit-plane operation. Zhang et al. suggested a method for improving encryption effectiveness in [37]. Although this approach increases the effectiveness of the encryption, the security is still inferior to [36]. This is so because the algorithm in [36] processes block positions as well as content, but the method in [37] just processes block ordering. As a result, the algorithm in [37] is less reliable. Furthermore, the secret keys for the algorithm in [37] are unrelated to the actual images. This may be due to the possibility of targeted chosen-plaintext and chosen-ciphertext attacks. The same author put up a different MIE method in [31] to address all the previously listed issues. By using a diffusion process, this technology increases the effectiveness of encryption while maintaining security. With this method, the pixel blocks are scrambled but not the contents insides of the pixels. In theory, this means that the pixels in this method are not entirely mixed up. To address the issues with [31], the same author Zhang and Wang developed a MIE technique based on DNA and chaos in [38]. The DNA strand technology has two important features: a lot of storage space and exact parallelism. In contrast to earlier MIE techniques, this method’s permutation and diffusion are managed by a three-dimensional DNA matrix. However, the algorithm’s computational complexity is increased by the additional DNA operations, such as encoding and decoding. The algorithm becomes slower as a result. The suggested multi-image encryption solution does not incorporate DNA operations with chaos to address the issues, indicating that the suggested method simply employs 1D chaotic maps for encryption. To speed up the method, a chaotic map-based encryption technique is employed. Additionally, the proposed method employs four permutation operations: block-selection, which permutes the blocks, and flipping, shifting, and rotating operations, which entirely randomises the locations of the pixels in each block.
In today’s digital environment, several colour images are produced, and the MIE algorithms in [31, 36,37,38] are less effective at encrypting colour images. The previous steps must be repeated three times to encrypt colour images because they have three different parts (Red, Green, and Blue). This causes the technique to run more slowly and adds to its computational complexity. Patro et al. [39] developed a multiple colour image encryption method based on 1D chaotic maps to address this issue. The method in [39] effectively encrypts multiple colour images, however the computational complexity of the technique is raised by the challenging multiple permutation step. In addition, the algorithm’s computing complexity is increased by the independent permutation and diffusion processes. The suggested method addresses this issue by accelerating pixel shifting in colour images using relatively simple and negligible computational complexity flipping, shifting, and rotating approaches. Furthermore, the encryption of several colour images is expedited by the synchronous-permutation-diffusion method.
To solve all the issues, this work proposes a speedy and effective multi-image encryption method based on synchronous-permutation-diffusion (SPD) operations and flip-shift-rotate (FSR) based procedures. The suggested system consists of two steps. In the first stage of encryption, all the colour image components are combined into a single huge image, and after that, a block division operation of size \(\left(3\times Number of colour images\right)\) is carried out. The second stage produces cipher images by simultaneously permuting and diffusing all the blocks. The blocks are initially selected from the array of blocks using the PWLCM-1 system, and in the second stage of the synchronous permutation and diffusion operation, the contents (pixels) of each of the selected blocks are permuted utilising flipping and shifting operations. The PWLCM-2, PWLCM-3, and PWLCM-4 chaotic systems regulate the flipping and shifting operations in each block. Following the permutation, the same block is exposed to diffusion utilising two different PWLCM systems, PWLCM-5, and PWLCM-6, together with key image rotation operation. As a result, each block is concurrently permuted and diffused until each block has been analysed. The blocks are finally combined to create the cipher images.
The major contributions of this paper are as follows:
-
The permutation phases are implemented with FSR-based operations such as flipping, shifting, and rotations to assure the quickest pixel scrambling operations. Because FSR-based operations do not require constant time, they are among the shortest on modern CPU architectures.
-
The permutation and diffusion operations are executed using SPD-based operations, which stands for synchronous-permutation-diffusion, to speed up the permutation and diffusion operations.
-
The permutation and diffusion operations are performed using a single type of 1D chaotic map-PWLCM system, rendering the algorithm’s software and hardware theoretically efficient. In addition, the PWLCM chaotic system is implemented at each stage of the permutation and diffusion operation, which increases the algorithm’s security and expands the key space.
-
The hash-based key generation operation ensures that the algorithm is resistant to chosen-plaintext and chosen-ciphertext attacks.
The subsequent sections of this document are structured in the following manner. Section 2 provides an overview of the foundational concepts and terminology utilised in this methodology. Section 3 provides an overview of the methodology outlined in this section. In Sect. 4, the security analysis of the algorithm is presented along with the results of the simulation. In Sect. 5, an analysis of the algorithm’s performance is presented. Section 6 serves as the concluding section of the paper.
2 Preliminaries
2.1 PWLCM system
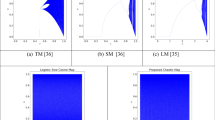
“Simplicity” and “ergodicity”, two crucial qualities of chaotic maps, must be considered while choosing a chaotic map for image encryption. PWLCM is the map that provides both “simplicity” and “ergodicity”. The Logistic map is a preferred chaotic map for “simplicity”, but since it lacks wider “ergodicity”. The greatest option for generating excellent pseudorandom chaotic sequences is the PWLCM system. It is generated by the Eq. (1) as [40, 41],
where, \(a\in \left(\mathrm{0,0.5}\right)\) is the system parameter and \(s\in \left(\mathrm{0,1}\right)\) is the initial value. Because just one division and a maximum of two additions are required in a single iteration, the PWLCM approach, like the Logistic map, offers “simplicity”. The PWLCM system iterates without employing trigonometric functions. However, when comparing the “ergodicity” of the two systems, the PWLCM system outperforms the Logistic map. The bifurcation of a Logistic map and a PWLCM system, respectively, in Figs. 1 and 2, serve as indicators of this. Figures 1 and 2 demonstrate that “ergodicity” happens in the Logistic map when \(\mathrm{^{\prime}}a\mathrm{^{\prime}}\) approaches 4 and for every PWLCM system parameter in the range of \(\left(\mathrm{0,1}\right)\). Other essential qualities of PWLCM system are uniform invariant distribution, powerful dynamical behaviour, and efficient implementation, in addition to “simplicity” and “ergodicity”. These qualities make the PWLCM system a reliable pseudo-random sequence generator [40, 41].
2.2 Secure Hash Algorithm
The Secure Hash Algorithms, which include SHA-0, SHA-1, SHA-2, and SHA-3, are a set of cryptographic hash functions formally recognised as a U.S. Federal Information Processing Standard (FIPS) by NIST. The most well-known of them is Secure Hash Algorithm 2 (SHA-2). There are two related hash functions in the SHA-2 family, both called SHA-256, and one called SHA-512, which differ only in their block sizes. SHA-256 operates with 32-bit words, while SHA-512 operates with 64-bit words. Each hashing standard also has shorter “truncated” variants: SHA-224, SHA-384, SHA-512/224, and SHA-512/256.
SHA-256 (Secure Hash Algorithm 256-bit) is a widely used cryptographic hash function with multiple essential applications in a variety of domains. Data integrity, digital signatures, password storage, digital forensics, certificate authority operations, etc., are some common applications of the SHA-256 hash algorithm. The proposed method employs the SHA-256 hashing algorithm to generate the hash values for image files, which are then used to generate the new key parameters. This protects the algorithm from the most prevalent attacks, such as chosen-plaintext and chosen-ciphertext attacks.
In addition, several lightweight algorithms, such as SPONGENT, QUARK, and PHOTON, are desired to employ electronic signatures that perform lightweight operations to reduce the server’s high overheads [42]. The SHA-256 algorithm has several advantages over SPONGENT, QUARK, and PHOTON:
-
Security: SHA-256 is a widely recognised and thoroughly analysed cryptographic hash function. It is intended to provide a high level of security against a variety of attacks, such as collision, preimage, and second preimage attacks. The cryptographic community has rigorously examined and validated SHA-256’s security properties.
-
Standardisation: SHA-256 is a standard algorithm that has been extensively adopted as a cryptographic hashing function. It is utilised in a variety of protocols and systems to ensure compatibility and interoperability across platforms and implementations. Its standardisation makes integration with existing cryptographic frameworks easier.
-
Established Track Record: SHA-256 has been in use for several years and has been rigorously evaluated by the cryptographic community. Its reputation as a trustworthy and secure hash function has been strengthened by its extensive adoption and analysis.
-
Broad Support: A variety of software libraries and hardware implementations support SHA-256. This extensive support makes it readily accessible and enables its efficient implementation on a variety of platforms and systems.
-
Performance: Even though SHA-256 was not intended specifically for lightweight operations, it benefits from optimisations and advances in hardware technology. Consequently, it can attain efficient performance in a variety of use cases, particularly on modern hardware.
Notably, the benefits of SHA-256 are predominantly applicable to cryptographic hash functions, which are designed for applications that rely on collision resistance and data integrity. In contrast, SPONGENT, QUARK, and PHOTON are lightweight encryption algorithms designed for devices with limited resources. The choice between SHA-256 and SPONGENT, QUARK, and PHOTON is determined by the application’s specific requirements and the trade-offs between security, performance, and resource constraints.
3 Proposed methodology
The proposed methodology consists of three main sections: key generation, encryption, and decryption. The utilisation of multiple attributes, such as key generation, encryption, and decryption, in encryption techniques can enhance performance and reduce the overhead associated with having a single authority [43]. The key generation section comprises two primary phases, namely: (i) The generation of hash values, and (ii) The generation of PWLCM-1 to PWLCM-6 based keys. The encryption and decryption section comprises six major phases, including: (i) The division of non-overlapping blocks, (ii) The selection of blocks, (iii) The flipping-based permutation operation, (iv) The shifting-based permutation operation, (v) The rotation-based permutation operation, and (vi) The block-based diffusion operation.
In the key generation section, the hash values are first generated from the concatenated multiple colour images then all the keys (both the initial values and system parameters of the PWLCM system) of the proposed algorithm are combined with these hash values of \(K\)-colour images to generate the keys of the algorithm. This protects the algorithm from well-known types of attacks such as Chosen-plaintext attack and Chosen-ciphertext attack. Since the generated hash value-based keys are entirely dependent on the images, the proposed algorithm generates unique keys for each image, thereby protecting it from the most common types of attacks.
In the encryption section, the Red \((R)\), Green \((G)\), and Blue \((B)\) components of all \(K\)-colour images are combined to create a large image. The large image is then divided into several blocks that undergo three main pixel shuffling operations, including rotation, shifting, and flipping. First, the flipping-based permutation operation is executed in each of the selected blocks followed by shifting operation on the same selected blocks. Then the rotation operation is executed in each of the key image blocks. The flipped and shifted blocks are subsequently diffused (XOR operation) by rotated key images generated by PWLCM systems. The execution of scrambling and diffusion operations simultaneously accelerates the algorithm. The synchronous-permutation-diffusion operations are carried out until all the blocks have been permuted and diffused. Finally, the permuted-diffused blocks are combined to create K-colour cipher images.
In the decryption section, which is essentially the opposite of the encryption section, the Red \((R)\), Green \((G)\), and Blue \((B)\) components of all \(K\)-colour cipher images are combined to form a large image. Each block is then synchronously-diffused-permuted to produce the final permutated blocks. The synchronous-diffusion-permutation operation is carried out until all blocks have been synchronously-diffusion-permuted. The permuted blocks are then combined to produce \(K\)-colour decrypted images that are identical to the original \(K\)-colour images. Therefore, the decryption process is the exact opposite of the encryption process.
Each of the three aspects, including key generation, encryption, and decryption, are described in detail below.
3.1 Process for key generation
-
Step-1. Input of colour images: Take a set of \(M\times N\times 3\)-dimensional \(K\)-colour images, such as \({A}_{1}, {A}_{2}, {A}_{3}, \cdots ,{A}_{K}\).
-
Step-2. Separation of colour image components: Separate the component of each \(K\)-colour image that are Red \((R)\), Green \((G)\), and Blue \((B)\). \({R}_{1},{R}_{2},{R}_{3},\cdots ,{R}_{K}\) stand for the \(R\) elements in \(K\)-colour images. The \(G\) and \(B\) component descriptors are \({G}_{1},{G}_{2},{G}_{3},\cdots ,{G}_{K}\) and \({B}_{1},{B}_{2},{B}_{3},\cdots ,{B}_{K}\), respectively. Red \((R)\), Green \((G)\), and Blue \((B)\) components of \(K\)-colour images are separated as shown below.
$$\begin{array}{c}{R}_{1}={A}_{1}\left(:,:,1\right)\\ {G}_{1}={A}_{1}\left(:,:,2\right)\\ {B}_{1}={A}_{1}\left(:,:,3\right)\\ {R}_{2}={A}_{2}\left(:,:,1\right)\\ {G}_{2}={A}_{2}\left(:,:,2\right)\\ {B}_{2}={A}_{2}\left(:,:,3\right)\\ \vdots \\ {R}_{K}={A}_{K}\left(:,:,1\right)\\ {G}_{K}={A}_{K}\left(:,:,2\right)\\ {B}_{K}={A}_{K}\left(:,:,3\right)\end{array}$$where \(\left({R}_{1},{R}_{2},{R}_{3},\cdots ,{R}_{K}\right)=R\) represents the red components of \(K\)-colour input images. Likewise, the arrays \(\left({G}_{1},{G}_{2},{G}_{3},\cdots ,{G}_{K}\right)=G\) and \(\left({B}_{1},{B}_{2},{B}_{3},\cdots ,{B}_{K}\right)=B\) represent, respectively, the green and blue components of \(K\)-colour input images.
-
Step-3. Horizontal and vertical concatenation of colour image components: Append horizontally and then vertically the \(R\), \(G\), and \(B\) components of \(K\)-colour images. The outputs of horizontal concatenation are denoted by \(HR,\;HG,\;and\;HB\), respectively. \(HVRGB\) denotes the vertically concatenated output. Below is the horizontal and vertical concatenation of \(R\), \(G\), and \(B\) components.
$$\begin{array}{c}HR=horzcat\left({R}_{1},{R}_{2},{R}_{3},\cdots ,{R}_{K}\right)\\ HG=horzcat\left({G}_{1},{G}_{2},{G}_{3},\cdots ,{G}_{K}\right)\\ \begin{array}{l}HB=horzcat\left({B}_{1},{B}_{2},{B}_{3},\cdots ,{B}_{K}\right)\\ HVRGB=vertcat\left(HR,HG,HB\right)\end{array}\end{array}$$ -
Step-4. Generation of hash values: Create a 64-hexadecimal hash value of \(HVRGB\) using the SHA-256 algorithm. It is portrayed by,
$$HS=\left(H{S}_{1},H{S}_{2},H{S}_{3},\cdots \cdots ,H{S}_{64}\right)$$where, the hash value array is referred to as \(HS\).
-
Step-5. Generation of PWLCM-1 to 6 based keys: Create the algorithm’s keys using Eqs. (2) through (7).
$$\left\{\begin{array}{l}x\left(1\right)=ax-\left(\left(\frac{H{S}_{1}+H{S}_{2}+\cdots +H{S}_{5}}{{10}^{15}}\right)-\lceil\frac{H{S}_{1}+H{S}_{2}+\cdots +H{S}_{5}}{{10}^{15}}\rceil\right)\times 0.01\\ xa=xx-\left(\left(\frac{H{S}_{6}+H{S}_{7}+\cdots +H{S}_{10}}{{10}^{15}}\right)-\lceil\frac{H{S}_{6}+H{S}_{7}+\cdots +H{S}_{10}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(2)$$\left\{\begin{array}{l}y\left(1\right)=ay-\left(\left(\frac{H{S}_{11}+H{S}_{12}+\cdots +H{S}_{15}}{{10}^{15}}\right)-\lceil\frac{H{S}_{11}+H{S}_{12}+\cdots +H{S}_{15}}{{10}^{15}}\rceil\right)\times 0.01\\ ya=yy-\left(\left(\frac{H{S}_{16}+H{S}_{17}+\cdots +H{S}_{20}}{{10}^{15}}\right)-\lceil\frac{H{S}_{16}+H{S}_{17}+\cdots +H{S}_{20}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(3)$$\left\{\begin{array}{l}z\left(1\right)=az-\left(\left(\frac{H{S}_{21}+H{S}_{22}+\cdots +H{S}_{25}}{{10}^{15}}\right)-\lceil\frac{H{S}_{21}+H{S}_{22}+\cdots +H{S}_{25}}{{10}^{15}}\rceil\right)\times 0.01\\ za=zz-\left(\left(\frac{H{S}_{26}+H{S}_{27}+\cdots +H{S}_{30}}{{10}^{15}}\right)-\lceil\frac{H{S}_{26}+H{S}_{27}+\cdots +H{S}_{30}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(4)$$\left\{\begin{array}{l}u\left(1\right)=au-\left(\left(\frac{H{S}_{31}+H{S}_{32}+\cdots +H{S}_{35}}{{10}^{15}}\right)-\lceil\frac{H{S}_{31}+H{S}_{32}+\cdots +H{S}_{35}}{{10}^{15}}\rceil\right)\times 0.01\\ ua=uu-\left(\left(\frac{H{S}_{36}+H{S}_{37}+\cdots +H{S}_{40}}{{10}^{15}}\right)-\lceil\frac{H{S}_{36}+H{S}_{37}+\cdots +H{S}_{40}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(5)$$\left\{\begin{array}{l}v\left(1\right)=av-\left(\left(\frac{H{S}_{41}+H{S}_{42}+\cdots +H{S}_{46}}{{10}^{15}}\right)-\lceil\frac{H{S}_{41}+H{S}_{42}+\cdots +H{S}_{46}}{{10}^{15}}\rceil\right)\times 0.01\\ va=vv-\left(\left(\frac{H{S}_{47}+H{S}_{48}+\cdots +H{S}_{52}}{{10}^{15}}\right)-\lceil\frac{H{S}_{47}+H{S}_{48}+\cdots +H{S}_{52}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(6)$$\left\{\begin{array}{l}w\left(1\right)=aw-\left(\left(\frac{H{S}_{53}+H{S}_{54}+\cdots +H{S}_{58}}{{10}^{15}}\right)-\lceil\frac{H{S}_{53}+H{S}_{54}+\cdots +H{S}_{58}}{{10}^{15}}\rceil\right)\times 0.01\\ wa=ww-\left(\left(\frac{H{S}_{59}+H{S}_{60}+\cdots +H{S}_{64}}{{10}^{15}}\right)-\lceil\frac{H{S}_{59}+H{S}_{60}+\cdots +H{S}_{64}}{{10}^{15}}\rceil\right)\times 0.01\end{array}\right.$$(7)
-
\(\left(H{S}_{1},H{S}_{2},H{S}_{3},\cdots \cdots ,H{S}_{64}\right)\) are the hash values generated by the SHA-256 hash algorithm from \(K\)-colour images. These hash values are distinct from each \(K\)-colour image input.
-
The original initial values for PWLCM-1 through PWLCM-6 are \(\left(ax,ay,az,au,av,aw\right)\). These values correspond to the initial six keys of the algorithm.
-
\(\left(xx,yy,zz,uu,vv,ww\right)\) are the original system parameters for PWLCM-1 through PWLCM-6. These six system parameters are also represented as the initial six keys of the algorithm. Therefore, the six original initial values and six original system parameters comprise the algorithm’s initial 12 keys.
-
\(\left(x\left(1\right),y\left(1\right),z\left(1\right),u\left(1\right),v\left(1\right),w\left(1\right)\right)\) are the initial values, and \(\left(xa,ya,za,ua,va,wa\right)\) are the system parameters for PWLCM-1 through PWLCM-6 that are generated by combining the original initial values and system parameters with the hash values of the images. The generated initial values and system parameters are the algorithm’s final keys, which are unique for each image input. The process of generating keys is resistant to the chosen-plaintext and chosen-ciphertext attacks on the algorithm.
In the preceding equations, the symbol \(\lceil.\rceil\) represents the ceiling operation. The \({''}ceil{''}\) function returns the smallest positive integer greater than or equal to the given number.
3.2 Process for encryption
A block diagram of the suggested encryption technique is shown in Fig. 3. The following are the steps in the encryption process.
-
Step-1. Input of colour images: As in Step-1 of Sect. 3.1, choose a set of \(K\)-coloured, \(M\times N\times 3\)-sized images such as \({A}_{1}, {A}_{2}, {A}_{3}, \cdots ,{A}_{K}\).
-
Step-2. Separation of colour image components: As in Step-2 of Sect. 3.1, split the \(K\)-colour image into their \(R\), \(G\), and \(B\) components such as \(({R}_{1},{R}_{2},\cdots ,{R}_{K})\), \(\left({G}_{1},{G}_{2},\cdots ,{G}_{K}\right),\) and \(({B}_{1},{B}_{2},\cdots ,{B}_{K})\). The size of each component is \(M\times N\).
-
Step-3. Horizontal concatenation of colour image components: As in Step-3 of Sect. 3.1, concatenate each of the \(R,G,\) and \(B\) parts horizontally. The components of \(R,G,\) and \(B\) that have been horizontally concatenated are referred to as \(R,\) \(HG\), and \(HB\), respectively. The dimensions of \(R,\) \(HG\), and \(HB\) are \(M\times \left(N\times K\right)\).
-
Step-4. Vertical concatenation of horizontally concatenated components: As in Step-3 of Sect. 3.1, concatenate \(,\) \(HG\), and \(HB\) vertically. Output that has been vertically concatenated is referred to as \(HVRGB\). The \(HVRGB\) dimension is \(\left(M\times 3\right)\times \left(N\times K\right)\).
-
Step-5. Division of non-overlapping blocks: Divide the image \(HVRGB\) into blocks of size \(3\times K\) and reshape them into a row vector \(RC\). The total number of blocks that have been generated is \(\frac{\left(M\times 3\right)\times \left(N\times K\right)}{3\times K}=M\times N\).
-
Step-6. Sorting and indexing of PWLCM-1 based iterated sequence: Generate the keys \(\left(x\left(1\right),xa\right)\) of PWLCM-1 by using Eq. (2). Then, execute the Eq. (1) \(M\times N-1\) times by utilizing the produced keys \(\left(x\left(1\right),xa\right)\). \(x\) denotes the iterated sequence. Finally, sorting and indexing the iterated sequence by,
$$\left[xsort,xindex\right]=sort\left(x\right)$$where, the sorted and indexed sequences are denoted as \(xsort\) and \(xindex\), respectively.
-
Step-7. Preprocessing of PWLCM-2 based iterated sequence: Generate the keys \(\left(y\left(1\right),ya\right)\) of PWLCM-2 using Eq. (3). Then, by using the keys \(\left(y\left(1\right),ya\right)\), iterate the Eq. (1) \(M\times N-1\) times. \(y\) is the generated sequence after iteration. Finally, preprocess the iterated sequence \(y\) by,
$$yn=mod\left(floor\left(y\times {10}^{6}\right),2\right)$$
In the above expression, the sequence \(yn\) generates either the value 0 or 1. The function \({''}mod{''}\) performs the modulus operation and the function \({''}floor{''}\) performs the round value operation towards minus infinity.
-
Step-8. Preprocessing of PWLCM-3 based iterated sequence: Generate the PWLCM-3 based keys \(\left(z\left(1\right),za\right)\) using Eq. (4). Then, iterate the Eq. (1) \(M\times N-1\) times by using the keys \(\left(z\left(1\right),za\right)\). The sequence that generated is denoted as \(z\). Finally, the iterated sequence \(z\) is preprocessed as,
$$zn=mod\left(floor\left(z\times {10}^{6}\right),3\right)+1$$where, \(zn\) is the preprocessed sequence whose values are either 1 or 2 or 3.
-
Step-9. Preprocessing of PWLCM-4 based iterated sequence: Generate the keys \(\left(u\left(1\right),ua\right)\) of PWLCM-4 system using Eq. (5). Then, \(M\times N-1\) times iterate the Eq. (1) by using the keys \(\left(u\left(1\right),ua\right)\), where \(u\) is the generated sequence after iteration. Finally, preprocess the iterated sequence \(u\) by,
$$un=mod\left(floor\left(u\times {10}^{6}\right),K\right)+1$$where, \(un\) is the preprocessed sequence whose values are in between \(\left(1,K\right)\).
-
Step-10. Preprocessing of PWLCM-5 based iterated sequence: Generate PWLCM-5 dependent keys \(\left(v\left(1\right),va\right)\) using Eq. (6). Then, iterate the Eq. (1) \(3\times K\) times using the keys \(\left(v\left(1\right),va\right)\). The generated sequence after iteration is \(v\). Finally, the iterated sequence \(v\) is preprocessed as,
$$vn=mod\left(floor\left(v\times {10}^{6}\right),256\right)$$
In the above expression, \(vn\) is the preprocessed sequence whose values are in the range of \(\left(\mathrm{0,255}\right)\).
-
Step-11. Generation of a key image: Generate a key image using the sequence values of \(vn\) by,
$$kimg=reshape(vn, \left[3,K\right])$$where, \(kimg\) is the generated key image whose dimension is \(3\times K\). The function \({''}reshape{''}\) shapes the array of values with a particular dimension.
-
Step-12. Preprocessing of PWLCM-6 based iterated sequence: Generate PWLCM-6 dependent keys \(\left(w\left(1\right),wa\right)\) using Eq. (7). Then, by using the keys \(\left(w\left(1\right),wa\right)\), iterate the Eq. (1) \(M\times N-1\) times. After iteration, the sequence that generated is denoted as \(w\). Finally, preprocess the iterated sequence \(w\) by,
$$wn=mod\left(floor\left(w\times {10}^{6}\right),2\right)$$where, \(wn\) is the new generated sequence, whose values are either 0 or 1.
-
Step-13. First phase of block-based permutation: Using the starting value of the indexing sequence \(xindex\), select the relevant block from the sequence \(RC\). The operation’s name is first phase permutation (block-permutation) operation.
-
Step-14. Second phase of flipping-based permutation: Perform flip operation on the block selected in Step-13. This algorithm uses two different flip operations, such as “flip up-down” and “flip left–right”. The sequence values of \(yn\) are used to carry out the flip operation. This is the second phase of permutation (pixel-permutation) operation in each block. The following procedure is used to accomplish the flip operation.
$$\left\{\begin{array}{l}flip\;up-down\leftarrow if\;\left(yn\left(i\right)==1\right)\\ flip\;left-right\leftarrow if\;\left(yn\left(i\right)==0\right)\end{array}\right.$$
In the above expression, the “flip up-down” operation is executed by using the function \(^{\prime}flipud^{\prime}\) and the “flip left–right” operation is executed by using the function \(^{\prime}fliplr^{\prime}\). The flipped output that is produced is denoted as \(ful\left\{1\right\}\).
-
Step-15. Third phase of shifting-based permutation: Perform circular shift operation on the flipped output \(ful\left\{1\right\}\) of Step-14. The sequence values of \(zn\) and \(un\) are used to perform the circular shift operation. This is the third phase of permutation (pixel-permutation) operation in each block. The following procedure is used to carry out the circular shift operation.
$$circ\left\{1\right\}=circshift\left(ful\left\{1\right\},[zn\left\{1\right\},un\left\{1\right\}]\right)$$where, \(circ\left\{1\right\}\) denotes the result of a circular shift. The Matlab built-in function \("circshift"\) shifts the position of the elements circularly.
-
Step-16. Fourth phase of rotation-based permutation: Perform rotation operation on the key image generated in Step-11. The values from the sequence \(wn\) are used to carry out the rotation operation. This is the fourth phase of permutation (pixel-permutation) operation in the key image. The following method is used to carry out the key image rotation operation.
$$\left\{\begin{array}{l}No\;rotation\leftarrow if \left(wn\left(i\right)==0\right)\\ Rotation\;of\;180^\circ \leftarrow if \left(wn\left(i\right)==1\right)\end{array}\right.$$
In the above expression, the rotation operation is executed by using the function \(^{\prime}rot90^{\prime}\). The rotated output that is produced is denoted as \(kro\left\{1\right\}\).
-
Step-17. First-time of block-based diffusion: Perform bit-XOR diffusion process among the permuted block \(circ\left\{1\right\}\) (output of Step-15) and the rotated key image \(kro\left\{1\right\}\) (output of Step-16).
-
Step-18. Second time of block-based permutation: Like Step-13, choose the relevant block from the sequence \(RC\) using the second value of the indexing sequence \(xindex\). Apply the flip operation, as in Step-14, to the block chosen in Step-18. The generated flipped output is designated as \(ful\left\{2\right\}\).
Like Step-15, perform circular shift operation on the flipped output \(ful\left\{2\right\}\) in the following way.
where, \(circ\left\{2\right\}\) is the output produced by a circular shift.
Like Step-16, perform rotation operation on the key image generated in Step-11. The key image rotation operation is performed in the following way.
The rotated output that is produced is denoted as \(kro\left\{2\right\}\).
-
Step-19. Second time of block-based diffusion: Perform two-time bit-XOR diffusion operation. First bit-XOR diffusion process is executed among the permuted block \(circ\left\{2\right\}\) (output of Step-20) and the rotated key image \(kro\left\{2\right\}\) (output of Step-21).
The second bit-XOR diffusion operation is performed among the output of the first bit-XOR diffusion process and the block diffused output of the Step-17.
-
Step-20. Permutation and diffusion of remaining blocks: For each consecutive block, repeat Steps-18 through 22 until every block has been synchronously permuted and diffused. The Cipher Block Chaining (CBC) mode of operation is used during the diffusion procedure. The array of diffused blocks is denoted as \(DRC\).
-
Step-21. Concatenation of diffused blocks: Concatenate all the diffused blocks of \(DRC\) to make a big image. The big image is denoted as \(BDRC\). The dimension of \(BDRC\) is \(\left(M\times 3\right)\times \left(N\times K\right)\).
-
Step-22. Generation of cipher images: Separate the R, G, and B components (opposite action of Step-4). Then, similarly, separate the individual R, G, and B components to make \(K\) colour cipher images (opposite action of Step-3). Combine the R, G, and B components to generate \(K\) colour cipher images (opposite action of Step-2). The \(K\) colour cipher images are denoted as \({C}_{1}, {C}_{2}, {C}_{3}, \cdots ,{C}_{K}\).
3.3 Process for decryption
-
Step-1. Collection of source elements: The receiver portion contains the encrypted images \({C}_{1}, {C}_{2}, {C}_{3}, \cdots ,{C}_{K}\). Additionally, the receiver receives key values for the PWLCM system \(\left(ax,ay,az,au, av,aw,xx,yy,zz,uu,vv,ww\right)\) and hash values \(\left(HS\right)\) for the multiple large image \(HVRGB\).
-
Step-2. Separation of cipher colour image components: Separate the Red \((CR)\), Green \((CG)\), and Blue \((CB)\) components of each \(K\)-colour cipher image. The red parts in \(K\)-colour cipher images are denoted by the symbols \(C{R}_{1},C{R}_{2},C{R}_{3},\cdots ,C{R}_{K}\). The descriptors for the green and blue components are \(C{G}_{1},C{G}_{2},C{G}_{3},\cdots ,C{G}_{K}\) and \(C{B}_{1},C{B}_{2},C{B}_{3},\cdots ,C{B}_{K}\), respectively. Each component has an \(M\times N\) size. The following describes the separation of the Red \((CR)\), Green \((CG)\), and Blue \((CB)\) components of each \(K\)-colour cipher images.
$$\begin{array}{c}{CR}_{1}={C}_{1}\left(:,:,1\right)\\ {CG}_{1}={C}_{1}\left(:,:,2\right)\\ {CB}_{1}={C}_{1}\left(:,:,3\right)\\ {CR}_{2}={C}_{2}\left(:,:,1\right)\\ {CG}_{2}={C}_{2}\left(:,:,2\right)\\ {CB}_{2}={C}_{2}\left(:,:,3\right)\\ \vdots \\ {CR}_{K}={C}_{K}\left(:,:,1\right)\\ {CG}_{K}={C}_{K}\left(:,:,2\right)\\ {CB}_{K}={C}_{K}\left(:,:,3\right)\end{array}$$where \(\left(C{R}_{1},C{R}_{2},C{R}_{3},\cdots ,C{R}_{K}\right)=CR\) are the red components of \(K\)-colour cipher images. Similarly, the arrays \(\left(C{G}_{1},C{G}_{2},C{G}_{3},\cdots ,C{G}_{K}\right)=CG\) and \(\left(C{B}_{1},C{B}_{2},C{B}_{3},\cdots ,C{B}_{K}\right)=CB\) represent the green and blue components of \(K\)-colour cipher images, respectively.
-
Step-3. Horizontal and vertical concatenation of colour image components: Follow Steps-3 and 4 of Sect. 3.2 to concatenate the red, green, and blue components to produce the big image designated as \(CHVRGB\).
-
Step-4. Division of non-overlapping blocks: Follow Step-5 in Sect. 3.2 to divide \(CHVRGB\) into several blocks of size \(3\times K\). The number of blocks generated are \(M\times N\).
-
Step-5. Sorting and indexing of PWLCM-1 based iterated sequence: Follow Steps-6 in Sect. 3.2, to generate the PWLCM-1 based iterated sequence and the sorted and indexed sequence. The iterated sequence is denoted as \(cx\), whereas the sorted and indexed sequences are denoted as \(cxsort\) and \(cxindex\), respectively.
-
Step-6. Preprocessing of PWLCM-2 to 4 based iterated sequences: Follow Steps-7 to 9 in Sect. 3.2 to generate PWLCM-2 to 4 based iterated sequences and its preprocessed sequences. Preprocessed sequences based on PWLCM-2 to 4 are designated as \(cyn\), \(czn\), and \(cun\), respectively, whereas iterated sequences based on PWLCM-2 to 4 are designated as \(cy\), \(cz\), and \(cu\), respectively.
-
Step-7. Generation of a key image: Generate the key image \(ckimg\) by following Steps-10 and 11 of Sect. 3.2.
-
Step-8. Preprocessing of PWLCM-6 based iterated sequence: Follow Steps-12 of Sect. 3.2, to generate PWLCM-6 based iterated sequence and its preprocessed sequence. The preprocessed sequence based on PWLCM-6 is designated as \(wn\), whereas the iterated sequence based on PWLCM-6 is designated as\(cw\).
-
Step-9. Reverse synchronous permutation and diffusion of blocks: Perform the reverse synchronous-permutation-diffusion operation, which is the same as the synchronous-diffusion-permutation operation, as described in Steps-13 to 20 of Sect. 3.2. Perform a bit-XOR based reverse diffusion operation first, then shifting and flipping operation in the synchronous-diffusion-permutation operation. The first bit-XOR operation is performed between the last ciphered block and the last rotated key image, followed by the bit-XOR diffusion operation between the output of the first bit-XOR operation and the prior ciphered block. The operation continues until all the ciphered blocks have been synchronously diffused and permuted.
-
Step-10. Concatenation of diffused blocks: Concatenate all the diffused and permuted blocks to create the big image by following Step-21 in Sect. 3.2.
-
Step-11. Generation of decrypted images: Separate and combine the red, green, and blue components as explained in Sect. 3.2Steps-22 to obtain \(K\) colour decrypted images that are identical to the \(K\) colour original images.
4 Simulation results and security analysis
In this paper, eight colour images, including “Splash”, “Tiffany”, “Baboon”, “Lena”, “Airplane”, “Lake”, “Peppers” and “House” are used to simulate the proposed method. Computer simulations are run on a system with a 2.80 GHz processor and 8.00 GB of RAM using MATLAB R2022a. The USC-SIPI image database has been used to acquire each of the \(512\times 512\) pixel images [44]. The keys of the proposed scheme are stated in Table 1. The rules for choosing the key values in Table 1 are as follows.
-
The initial values of PWLCM-1 to 4 should range from \(\left(\mathrm{0,1}\right)\).
-
The system parameters of PWLCM-1 to 4 should be between \(\left(\mathrm{0,0.5}\right)\).
-
All key values should be interpreted as having 15 decimal places to maximize the algorithm’s sensitivity to keys.
-
Any 15-decimal place random key value that falls within the appropriate range can be used as the key value.
Figure 4 displays the simulation findings. The encrypted images are seen to be extremely noisy in the simulation results, indicating that attackers would not be able to extract useful information about the original images. This demonstrates how effectively our method encrypts data. The simulation results also show that we can successfully decrypt the images if we use the right secret keys.
Simulation outcomes – (a) Original “Splash” image, (b) Encrypted “Splash” image, (c) Decrypted “Splash” image, (d) Original “Tiffany” image, (e) Encrypted “Tiffany” image, (f) Decrypted “Tiffany” image, (g) Original “Baboon” image, (h) Encrypted “Baboon” image, (i) Decrypted “Baboon” image, (j) Original “Lena” image, (k) Encrypted “Lena” image, (l) Decrypted “Lena” image, (m) Original “Airplane” image, (n) Encrypted “Airplane” image, (o) Decrypted “Airplane” image, (p) Original “Lake” image, (q) Encrypted “Lake” image, (r) Decrypted “Lake” image, (s) Original “Peppers” image, (t) Encrypted “Peppers” image, (u) Decrypted “Peppers” image, (v) Original “House” image, (w) Encrypted “House” image, (x) Decrypted “House” image
In the next part, the security of the suggested algorithm is evaluated.
4.1 Key space analysis
The key space is a representation of the total number of keys utilised in the encryption process. To resist a brute-force attack, it is necessary for a method’s key space to exceed \({2}^{100}\) [45]. The following is a list of keys utilised in the suggested technique.
-
PWLCM systems initial values \((ax,ay,az, au, av, aw)\) and control parameters \((xx,yy,zz, uu, vv, ww)\)
-
256-bit hash values in terms of 64-hexadecimals
Table 2 presents an illustration of the key space of the algorithm. As per the table, it can be observed that the key space utilised by all PWLCM system-based keys is \({10}^{15}\). The utilization of a 64-bit floating point standard in this method results in a value of \({10}^{15}\) as provided by IEEE [46]. The table presents the \({2}^{128}\) key space pertaining to the SHA-256 hash value. The SHA-256 hash algorithm is highly secure with a security level of \({2}^{128}\), making it capable of withstanding even the most powerful attacks. The proposed method employs a key space totaling \(1.9279\times {2}^{725}\), surpassing the \({2}^{100}\) threshold, to protect against brute-force attacks.
4.2 Histogram analysis
Histogram analysis is a graphical method for assessing statistical assaults. The following two elements are used to calculate histograms [47]:
-
The original and cipher images’ histograms ought to differ significantly more.
-
For encrypted images, the histogram’s pixel-grey values must all have an equal number of pixels.
Figures 5 depict the histograms of the R, G, and B components for both the original and encrypted versions of the “Splash” and “Tiffany” images. The histogram map displays the differentiation between the source and associated cipher images, along with the uniformity of the pixel grayscale values in the red, green, and blue components of the encoded images. The statement implies that the original images’ redundancy is concealed entirely after encryption, making it impossible to launch statistical attacks.
Histogram plots – (a) Original R component of “Splash” image, (b) Original G component of “Splash” image, (c) Original B component of “Splash” image, (d) Encrypted R component of “Splash” image, (e) Encrypted G component of “Splash” image, (f) Encrypted B component of “Splash” image, (g) Original R component of “Tiffany” image, (h) Original G component of “Tiffany” image, (i) Original B component of “Tiffany” image, (j) Encrypted R component of “Tiffany” image, (k) Encrypted G component of “Tiffany” image, (l) Encrypted B component of “Tiffany” image
4.3 Histogram variance analysis
To help with the impacts of visual inspection, the variance, a dispersion statistic, is used in image histograms. This method determines how frequently the components of a set of data vary from one another around the mean. The mean (average value) of two datasets can be the same, but their variances may differ substantially. Lowering the histogram’s variance increases grayscale homogeneity [48]. Calculated in the form of Eq. (8) as,
where, \(p\) is the frequency with which each pixel’s intensity appears in the histogram from 0–255 grey levels, \(\overline{p }\) is the mean, and \(V\) is the variance. Following is how the mean \(\overline{p }\) is calculated in terms of Eq. (9) as,
where \(M\times N\) is the size of the image. Table 3 displays the histogram variance of several colour images created using the suggested method. As shown in the table, the cipher image variance is significantly lower than the original image variance. This demonstrates the high level of grayscale constancy in pixel values in cipher images.
4.4 Chi-square test analysis
In encrypted image histograms, the chi-square test can be used to validate the consistency of grey scale values. A low chi-square value in encrypted image histograms indicates high consistency [49, 50]. It is expressed as follows in Eq. (10):
where \({of}_{i}\) represents the frequency that was observed, also known as the observed frequency, and \({ef}_{i}\) represents the frequency that was anticipated, also known as the expected frequency. The expected frequency, \({ef}_{i}\), is computed with the following formula (Eq. (11)).
where \(M\times N\) is the size of the image. Table 4 presents chi-square test results of the encrypted version of multiple colour images. As demonstrated in Table 4, the proposed method accepts the hypothesis at both the 5% and 1% significance levels. This indicates that the cipher image histograms generated by the suggested method are grayscale homogeneous.
4.5 Adjacent pixel correlation analysis
It defines the relationship between adjacent pixels in an image. There is a weak association between neighbouring pixels in encrypted images, whereas there is a strong correlation in the original images. When correlation is feeble, the correlation coefficient is much closer to zero, whereas when correlation is strong, it is closer to + 1 or -1. Equations (12) to (17) are utilised to calculate the correlation coefficient.
where,
In formulations (12) through (17), adjacent gray pixels are represented by \(u\) and \(v\), while neighboring pixel pairs are represented by \(P\). Table 5 displays the results of the suggested procedure for neighbouring pixel correlation. To establish neighbouring pixel correlation, the proposed method employs 10,000 randomly selected pairs of adjacent pixels. Table 5 demonstrates that while the correlation between neighbouring pixels in cipher images is comparatively close to 0, it is much closer to one in original images. This indicates how well the proposed strategy is protected against statistical assaults.
The correlation plots in the diagonal direction for the R, G, and B components of the “Splash” and “Tiffany” images are shown in Fig. 6. The adjacent pixels in the original images are linearly connected and exhibit significant adjacent pixel relationships, whereas in the encrypted images, adjacent pixels are dispersed across the entire image surface. This indicates that the proposed procedure is statistically secure against attacks.
Adjacent pixel correlation plots in diagonal direction—(a) R component of original “Splash” image, (b) G component of original “Splash” image, (c) B component of original “Splash” image, (d) R component of encrypted “Splash” image, (e) G component of encrypted “Splash” image, (f) B component of encrypted “Splash” image, (g) R component of original “Tiffany” image, (h) G component of original “Tiffany” image, (i) B component of original “Tiffany” image, (j) R component of encrypted “Tiffany” image, (k) G component of encrypted “Tiffany” image, (l) B component of encrypted “Tiffany” image
4.6 Information entropy analysis
It is a method for determining the randomness of the pixels in encrypted images [53]. Image entropy increases as the unpredictability of pixels increases. The greater the information’s entropy, the greater its entropy. Eight is the optimal entropy value for a 256-grayscale image. The closer we go to 8, the less data leakage there is. To compute entropy, the following formula (Eq. (18)) is used:
where \({P}_{CI}\left(i\right)\) represents the unpredictability of the \(i\) symbol and \({H}_{CI}\) represents the entropy of an image.
Table 6 depicts the entropy values of multiple-colour images. All the entropy values for colour images in the table are quite near to the ideal value. This indicates the effectiveness of the proposed method for preventing data leakage.
4.7 Differential attack analysis
Differential attack analysis is used to assess the sensitivity of the ciphertext image to the plaintext image. If the ciphertext is more sensitive to the plaintext, then the method is more resistant to differential attacks. Numbers of Pixel Changing Rate (NPCR) and Unified Average Changing Intensity (UACI) are two frequently employed security techniques for analysing differentiated attack studies [48].
NPCR determines the pixel change percentage in an encoded image. The NPCR can be calculated using the following mathematical Eq. (19):
\({D}_{{C}_{org},{C}_{mod}}\left(i,j\right)\) is defined by Eq. (20) as,
where \({C}_{org}\) represents the original version of the cipher image and \({C}_{mod}\) represents its modified variant. Optimally, the NPCR should be \(99.6094\%\) [48].
UACI calculates the difference in intensity level between the original image and the cipher. Using the formula in Eq. (21), the UACI is computed as follows:
In an optimal scenario, the UACI would be 33.4635% [48].
Table 7 displays the NPCR and UACI values for the suggested methodology. As shown in the table, the average NPCR and UACI values for each image are greater than their desired values. This demonstrates the effectiveness of the proposed technique in defending against differential attacks.
4.8 Key sensitivity analysis
The proposed method employs a total of six PWLCM system-based keys. To secure the system from brute-force attacks, all keys should be exceedingly sensitive. To accomplish this, one of the 12 keys can be modified at a time, and the two cipher images – the original cipher images and the modified key cipher images – can then be compared. As the difference between the two cipher images increases, so does the sensitivity of the key and the security of the algorithm. In addition, NPCR and UACI are used to determine the sensitivity of the key. If the NPCR and UACI values approach 99% and 33%, respectively, the key is more susceptible to the algorithm.
Figure 7 depict the key sensitivity results for PWLCM system-based key \(\left(ax\right)\) utilising multiple colour images. Two cipher image variations in Fig. 7 demonstrate that only one of twelve possible keys can substantially alter the cipher images. This demonstrates how sensitive the proposed method is to key input. Table 8 presents the key sensitivity information for all 12 keys, including \(ax,xx,ay,yy,az,zz,au,uu,av,vv,aw, \mathrm{and} ww\), in NPCR and UACI format. As shown in Table 8, the NPCR and UACI values for each image exceeded 99% and 33%, respectively. This demonstrates how sensitive the suggested strategy is to all keys.
Key sensitivity results by the changed key \(ax\) to \(ax+{10}^{-15}\)—(a, c, e, g, i, k, m, o) Key changed “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” cipher images, respectively, (b, d, f, h, j, l, n, p) Corresponding difference images of original cipher images of Fig. 4 and key changed cipher images
4.9 Noise attack analysis
The noise resistance of an encryption method is one of the most crucial factors in real communications [54]. The proposed algorithm is noise resistant. The algorithm’s efficacy is demonstrated using both Gaussian and salt-and-pepper noise. Both noise experiments were conducted by adding noise to the encrypted image and then recovering the decrypted version. The contrast between the original image and the decrypted images illustrates the method’s noise resistance. The difference between the original image and the decrypted image is determined by NPCR and UACI. As noise resistance increases, the NPCR and UACI values diminish.
Figure 8 depicts the results of the Gaussian noise attack analysis of multiple colour images with variance = 0.0001. The figures indicate the resistance of various colour images to Gaussian noise, with Mean = 0 and Variance = 0.0001. Table 9 displays the NPCR and UACI values for multiple colour images with Mean = 0 and Variance = 0.0001, 0.0003, and 0.0005 respectively. Table 10 compares the NPCR and UACI results of the proposed method with those of References [48, 50, 54]. In terms of NPCR and UACI values, Table 10 demonstrates that the proposed method outperforms the methodologies described in [48, 50, 54]. Consequently, it is evident that the proposed method is more resistant to Gaussian noise than the methods described in [48, 50, 54].
Figure 9 depicts the results of the Salt and Pepper noise attack analysis performed at a noise level of 5% on various colour images. These figures indicate that the proposed method is highly resistant to the Salt and Pepper noise attack. Multiple colour image NPCR and UACI results are shown in Table 11 for noise levels of 5%, 10%, and 25%. The results of Salt and Pepper’s noise assault assessments are compared in Table 12. In terms of NPCR and UACI values, Table 12 demonstrates that the proposed procedure outperforms the approach described in [50]. Consequently, it is evident that the proposed technique is more resistant to the Salt and Pepper noise assault than the methods in [50].
4.10 Cryptanalysis
Hackers frequently employ the chosen-plaintext attack and the chosen-ciphertext attack against encryption algorithms [55]. The proposed method takes into consideration these vulnerabilities.
4.10.1 Chosen-plaintext attack
In this type of attack, the attacker can choose which randomly generated plaintexts to encrypt and then obtain the corresponding ciphertexts. In a straightforward example, the attacker is in possession of the ciphertext \(C\) and is attempting to decrypt it with the unknown encryption key \(K\). Nonetheless, the adversary was able to access both the plaintext \({P}_{alz}\) and its encrypted counterpart \({C}_{alz}\), as both utilise the same secret encryption key. For pixel encryption, the following sub-key recovery technique (Eq. (22)) is employed by the adversary.
where \({P}_{alz}^{i,j}\) represents all-zero-pixel plaintext, \({C}_{alz}^{i,j}\) represents the associated ciphertext, and \({K}_{alz}^{i,j}\) represents the obtained key stream.
Consequently, the plaintext of \({P}^{i,j}\) can be obtained using Eq. (23) by,
Figure 10(a-h) depicts a chosen-plaintext attack utilising null images with all zero pixels on a variety of coloured images. Figure 11 depicts histograms for the images shown in Fig. 10(a-h). The proposed solution for encrypting multiple images has been shown to be resistant to the chosen-plaintext attack on multiple colour images and their accompanying histograms. This is the case because the key values generated by the proposed method are associated with both the provided key values and the hash values of the actual image data. Consequently, the chosen-plaintext attack is extremely unlikely to succeed against the proposed strategy.
a, b, c, d, e, f, g, & h Chosen-plaintext attack (All zero-pixel null-images) of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively, i, j, k, l, m, n, o, & p Chosen-ciphertext attack (All zero-pixel null-images) of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively
Histogram plots of chosen-plaintext attack (All zero-pixel null-images) images of Fig. 10(a-h)—(a, d, g, j, m, p, s, & v) R components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively; (b, e, h, k, n, q, t, & w) G components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively; (c, f, i, l, o, r, u, & x) B components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively
4.10.2 Chosen-ciphertext attack
In this type of attack, the attacker also does not have a key. \({P}_{alz}\), the decoded version of \({C}_{alz}\), an all-zero (or all-one) ciphertext, is accessible to the adversary. The intruder obtains the keystream \({K}_{alz}^{i,j}\) using the previously mentioned Eq. (22). Using Eq. (23), the plaintext \({P}^{i,j}\) is extracted from the ciphertext \({C}^{i,j}\). Figure 10(i-p) depicts a chosen-ciphertext attack on multiple colour images utilising null images with all zero pixels. Figure 12 depicts the histogram graphs for the images in Fig. 10(i-p). The proposed multiple image encryption method fails the chosen-ciphertext attack on multiple colour images and their corresponding histograms, as determined by an analysis of the attack.
Histogram plots of chosen-ciphertext attack (All zero-pixel null-images) images of Fig. 10(i-p)—(a, d, g, j, m, p, s, & v) R components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively; (b, e, h, k, n, q, t, & w) G components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively; (c, f, i, l, o, r, u, & x) B components of “Splash,” “Tiffany,” “Baboon,” “Lena,” “Airplane,” “Lake,” “Peppers,” “House” images, respectively
4.11 Randomness test
The National Institute of Standards and Technology (NIST) conducts a test to evaluate the performance of a random number generator. The test results are then used to determine the suitability of the chaotic system for the encryption scheme. The NIST test is comprised of 15 sub-tests. A sub-test result of \(p\ge 0.01\) signifies that the test sequence has successfully passed the sub-test. This indicates that the test sequence is unpredictable and random. If the value of \(p\) is less than 0.01, it can be concluded that the test sequence is non-random. According to the results presented in Table 13, the PWLCM system successfully passed all sub-tests, indicating that it possesses random and unpredictable characteristics [56,57,58].
4.12 Comparison analysis with respect to various security measures
The security analysis of the proposed multi-image encryption system is compared with the following essential measures. Tables 14 present a comparison of different security measures.
4.12.1 Comparison of key space analysis
For an encryption algorithm to be secure against brute-force attacks, its key space must exceed \({2}^{100}\). Table 14 displays the key space comparison findings. This table shows that all multi-image encryption algorithms have key spaces greater than \({2}^{100}\), which indicates that all the techniques effectively withstand brute-force attacks. The table also reveals that the suggested method has a larger key space value than the multi-image encryption methods in [31, 36,37,38,39]. This demonstrates that the suggested method outperforms the currently used multi-image encryption methods.
4.12.2 Comparison of histogram variance analysis
The analysis of histogram variance is a quantitative method that assesses the homogeneity of pixel values in grayscale histograms. Table 14 presents the outcomes of the comparison of histogram variances. The analysis of comparative data indicates that the proposed method exhibits a lower variance value in comparison to the other approaches cited in [31, 36]. The proposed method exhibits superior grayscale homogeneity compared to the presently employed encryption techniques. It can be asserted that our approach is superior to other techniques.
4.12.3 Comparison of adjacent pixel correlation analysis
Adjacent pixel correlation analysis measures the correlation of pixels in images. Table 14 compares the suggested strategy with the algorithms from [31, 36, 38, 39] for adjacent pixel correlation in encrypted images. Table 14 demonstrates that adjacent pixels in encrypted images are weakened when using the proposed method compared to the methods from [31, 36, 38, 39]. This demonstrates the effectiveness of the proposed strategy against the statistical assault.
4.12.4 Comparison of information entropy analysis
The concept of information entropy is utilised to quantify the level of randomness present in the pixels of images. Increasing the value of 8 in encrypted images results in stronger pixel randomness and reduced information leakage in the images. Table 14 presents a comparison of the average information entropy outcomes. The entropy of the proposed scheme is higher than that of the other systems listed in the table. The results indicate that the proposed method produces a greater number of random pixels when compared to other approaches.
4.12.5 Comparison of differential attack analysis
Differential attack analysis is a technique utilised to evaluate the susceptibility of a ciphertext image to the plaintext image. The security techniques commonly used to analyse differential attack are the Numbers of Pixel Changing Rate (NPCR) and Unified Average Changing Intensity (UACI). Table 14 compares the NPCR and UACI results of the proposed method to those of the methodologies described in [31, 38, 39]. According to the findings of the evaluation, the offered method has a higher average NPCR than the method in [31, 39] and a marginally lower average NPCR than the method in [38]. As shown in Table 14, the proposed strategy has a slightly lower average UACI than the techniques of [31], but a higher average UACI than the techniques of [38, 39]. When both NPCR and UACI comparison data are considered together, it is found that the proposed strategy produces superior NPCR and UACI results than the other suggested methods. This demonstrates that the proposed solution is more effective than the previously discussed image encryption techniques.
4.13 Comparison analysis with respect to various classical encryption algorithms
The proposed chaotic map-based multiple image encryption algorithm has several advantages over other recent encryption algorithms such as RC4 + . Here are some of the reasons they are deemed advantageous:
-
Enhanced Security: Inherent characteristics of chaotic maps include unpredictability, sensitivity to initial conditions, and randomness. These characteristics make them appropriate for generating encryption keys and shuffling image pixels, thereby enhancing the security of the encryption process. Using chaotic maps adds another layer of complexity, making it more difficult for an attacker to breach the encryption.
The proposed algorithm for encrypting multiple colour images employs six Piece-wise Linear Chaotic Maps (PWLCM-1 through PWLCM-6) to encrypt multiple colour images. Each of the six Piece-wise Linear Chaotic Maps has unique key parameters (initial values and system parameters) that make the algorithm more secure and robust.
-
Resistance to Cryptanalysis: When properly designed and implemented, chaotic maps demonstrate resistance to a variety of cryptographic attacks, including brute-force attacks, statistical attacks, and differential attacks. These maps can provide strong encryption that is difficult to crack without knowledge of the chaotic dynamics underlying them.
According to simulation results and security analysis, the proposed algorithm is designed and executed appropriately.
-
Increased Key Space: Chaotic maps produce encryption keys by utilising the enormous key space available within the chaotic system. This results in a larger key space than algorithms such as RC4 + . A larger key space makes it computationally impractical for adversaries to exhaustively search all possible keys, thereby enhancing the encryption process’s security.
The key space of the proposed algorithm is \(1.9279\times {2}^{725}\).
-
Nonlinear Encryption: Typically, chaotic map-based algorithms employ nonlinear operations, such as permutation and substitution, on the image data. The complexity introduced by these nonlinear transformations makes it more difficult for adversaries to analyse and decipher encrypted images.
The proposed chaotic map-based multiple colour image encryption algorithm performs all permutation, substitution, and diffusion operations that make it exceedingly difficult for adversaries to analyse and decipher encrypted images.
-
Enhanced Robustness: Chaotic map-based algorithms often incorporate techniques like image decomposition, diffusion, and mixing to disperse the pixel information across the entire image. This ensures that small changes in the input image result in significant changes throughout the encrypted image. As a result, the encrypted images exhibit robustness against data loss, noise, and other image processing operations.
The proposed chaotic map-based multiple colour image encryption algorithm resists noise attack and other security attacks efficiently.
-
Parallel Processing: Many chaotic map-based algorithms are amenable to parallel processing techniques, allowing for efficient encryption and decryption of multiple images simultaneously. This parallelization capability is particularly beneficial when dealing with large-scale image encryption tasks, providing faster encryption and decryption speeds.
The proposed chaotic map-based multiple colour image encryption algorithm performs synchronous-permutation-diffusion operation for the encryption of multiple colour images.
It is essential to remember that the RC4 and its variants, including RC4 + , have been shown to exhibit vulnerabilities and are no longer recommended for use in new cryptographic applications. RC4 + encryption algorithm is an enhanced version of the RC4 encryption algorithm which is recommended for stream cipher encryption algorithms. However, the proposed chaotic map-based multiple image encryption algorithm is recommended for block cipher encryption algorithms.
5 Performance analysis
5.1 Mean square error (MSE) and peak signal-to-noise ratio (PSNR) analysis
Using the MSE technique, both input and decrypted as well as input and encrypted images are compared. The high value of MSE indicates that the actual and cipher images differ significantly [51, 52]. The MSE between the input and decrypted images is 0 [51]. The MSE is defined by Eqs. (24) and (25) as follows:
where \(^{\prime}{OC}^{\prime}\) represents the “input image,” \(^{\prime}EC^{\prime}\) represents the “encrypted image,” and \(^{\prime}DC^{\prime}\) represents the “decrypted image.” \({MSE}_{OC-EC}\) is the “MSE between the input and the encrypted image”, whereas \({MSE}_{OC-DC}\) is the “MSE between the input and the decrypted image”.
PSNR compares the quality assessments of the encrypted image to those of the original image. A low PSNR value reveals significant disparities between the input and cipher images [51, 52]. Between the input image and the decoded image, the PSNR is infinite [51]. It is characterised by Eqs. (26) and (27) as
where \({I}_{maxC}\) is the maximum pixel value allowed in an image and \({PSNR}_{OC-EC}\) and \({PSNR}_{OC-DC}\) are the PSNRs between the input and the encrypted and unencrypted variants of the image, respectively.
Table 15 displays the MSE and PSNR of the original and encrypted images using the suggested method. In accordance with the table, the MSE has a higher value while the PSNR has a lower value. This demonstrates how the proposed algorithm distinguishes significantly between input and cipher images. The PSNR between the original and decrypted images is measured as infinite whereas the MSE is measured as zero. This demonstrates that the input and decryption images are identical.
5.2 Computational complexity analysis
The suggested technique’s computing complexity is significantly influenced by the diffusion, permutation, and creation of pseudo-random sequences. The following is a list of each item’s computational complexity.
-
i.
Pseudo-random sequence creation operation: The suggested method creates pseudo-random sequences by utilising the chaotic map—PWLCM system. Six PWLCM systems—PWLCM-1, PWLCM-2, PWLCM-3, PWLCM-4, PWLCM-5, and PWLCM-6 – are used in this method. The chaotic sequence based on the PWLCM-1, PWLCM-2, PWLCM-3, PWLCM-4, PWLCM-5, and PWLCM-6 requires \({f}_{1}\left(M,N,K\right)=M\times N\), \({f}_{2}\left(M,N,K\right)=M\times N\), \({f}_{3}\left(M,N,K\right)=M\times N\), \({f}_{4}\left(M,N,K\right)=M\times N\), \({f}_{5}\left(M,N,K\right)=3\times K\), and \({f}_{6}\left(M,N,K\right)=M\times N\) iterations, respectively. The total number of chaotic iterations needed from PWLCM-1 to PWLCM-6 is \({f}_{I}\left(M,N,K\right)={f}_{1}+{f}_{2}+{f}_{3}+{f}_{4}+{f}_{5}+{f}_{6}=5\times \left(M\times N\right)+ 3\times K\) and \({g}_{I}\left(M,N,K\right)=M\times N\) (\(\because K\ll M,N\)). According to the BIG-O notation principle, the total computing cost to create chaotic sequences is \({f}_{I}\left(M,N,K\right)=O\left({g}_{I}\left(M,N,K\right)\right)=O\left(M\times N\right)\) [59].
-
ii.
Permutation operation: The suggested approach carries out four permutation operations, including a one-time block permutation and three times of pixel shuffling in terms of flipping, shifting, and rotating. The first-time block permutation procedure, which is a block-selection operation, selects one block at a time from \(M\times N\). Although it is a block selection operation, this one behaves somewhat like a block permutation operation. Therefore, block permutation is \({f}_{1}\left(M,N,K\right)=1\). The flipping, shifting, and rotating operation are used in the second, third, and fourth-time block permutation approaches. Flipping, shifting, and rotation operations are finished in a few of clock cycles in modern CPU architectures. These processes are among the quickest ones available in today’s CPU architectures because they do not need constant time. The flipping, shifting, and rotating operations are carried out one block out of \(M\times N\) blocks at a time, much like the block selection function. As a result, just a little amount of computing is needed for flipping, shifting, and rotational operations. Therefore, the permutation of one block in synchronous-permutation-diffusion is \({f}_{P}\left(M,N,K\right)=1\) and \({g}_{P}\left(M,N,K\right)=1\). So, according to the BIG-O notation concept [59], the overall computing complexity of doing one block permutation in synchronous-permutation-diffusion is \({f}_{P}\left(M,N,K\right)=O\left({g}_{P}\left(M,N,K\right)\right)=O\left(1\right)\).
-
iii.
Diffusion operation: The recommended technique uses block-level diffusion that is bit-XOR based on each individual pixel. In this diffusion procedure, each of the permuted outputs is bit-XORed with the key image outputs and then bit-XORed with the previously diffused block. During a diffusion process, one block is diffused twice at once. First-time diffusion of the block is \({f}_{1}\left(M,N,K\right)=3\times K\times 8\) (The complexity of bit-XOR operation of two pixels with 8-bits is \(O\left(8\right)\). Hence, the complexity of a single \(3\times K\) block is \(O\left(3\times K\times 8\right)\)). Like this, the second time diffusion of the block is \({f}_{2}\left(M,N,K\right)=\left(3\times K\times 8\right)-1\). Therefore, the diffusion of one block in the synchronous-permutation-diffusion process is \({f}_{D}\left(M,N,K\right)={f}_{1}+{f}_{2}=2\times \left(3\times K\times 8\right)-1\) and \({g}_{D}\left(M,N,K\right)=3\times K\times 8\). According to the BIG-O notation principle, the total computation cost of conducting one block diffusion in synchronous-permutation-diffusion operation is \({f}_{D}\left(M,N,K\right)=O\left({g}_{D}\left(M,N,K\right)\right)=O\left(3\times K\times 8\right)\) [59].
\(f\left(M,\mathrm{N},\mathrm{K}\right)={f}_{P}+{f}_{D}=1+24\mathrm{K}\) and \(g\left(M,\mathrm{N},\mathrm{K}\right)=K\) are the combined permutation and diffusion of one block in synchronous-permutation-diffusion processes. Therefore, the overall computing complexity of doing one block permutation and diffusion in synchronous-permutation-diffusion operations is \(f\left(M,N,K\right)=O\left(g\left(M,N,K\right)\right)=O\left(K\right)\). The computational complexity of permuting and diffusing \(M\times N\) blocks in synchronous-permutation-diffusion is \(O\left(MN+MNK\right)\approx O\left(M\times N\times K\right)\). When using multiple-colour image encryption algorithms, an encryption process has a computational cost of about \(O\left(3\times {\left(M\times N\times K\right)}^{3}\right)\). The proposed approach, on the other hand, has a computational complexity of about \(O\left(M\times N\times K\right)\). This indicates that the suggested process is rapid and efficient when compared to earlier methods for encrypting multiple colour images.
The computing complexity of the suggested approach and the method from [31, 36,37,38,39] is compared in Table 16. According to Table 16, the proposed method is significantly less computationally complex than the methods described in [31, 36,37,38,39]. This demonstrates that the proposed approach outperforms currently used multi-image encryption methods. Table 16 also presents a comparison of the computational complexity between the proposed algorithm and several conventional algorithms. The results presented in the table indicate that the proposed algorithm outperforms and is more appropriate than the conventional algorithms. The following explanation is provided below.
-
Traditional algorithms are not so efficient for encrypting images because of the high correlation of adjacent pixels in images and the vast amount of data in images.
-
The encryption of multiple images using traditional algorithms is inefficient as the algorithms need to be executed as many times as the number of images being encrypted.
-
In addition, conventional algorithms are appropriate for encrypting grayscale images. To encrypt colour images, it is customary to execute the conventional algorithm thrice, once for each of the individual R, G, and B components. The algorithm’s efficiency is decreased. In the instance of a breach in one component, the remaining components will also be breached as there is no interdependence between them.
5.3 Simulation timing analysis
The proposed algorithm has been implemented on a set of eight colour images, namely “Splash”, “Tiffany”, “Baboon”, “Lena”, “Airplane”, “Lake”, “Peppers”, and “House”. The computer simulations are executed on a MATLAB R2022a platform, utilising a system equipped with an 8.00 GB RAM and a 2.80 GHz processor. The proposed algorithm can simulate eight colour images with encryption in 0.93 s and decryption in 0.81 s. The encryption and decryption process exhibits a notably low processing time, even though it involves the encryption of eight distinct colour images.
6 Conclusion
This paper proposes a new and efficient method for encrypting multiple colour images. In this method, the permutation and diffusion processes run concurrently. The colour image components are first linked together to generate a composite image, which is then used to build a huge, non-overlapping image. The synchronous-permutation-diffusion approach is applied to each block in order to create cipher images. The methodology outperforms existing multi-image encryption methods owing to the synchronous-permutation-diffusion operation and the flip-shift-rotate (FSR) based permutation operation. It also speeds up the encryption of a number of coloured images. Because the encryption technique only uses the one-dimensional chaotic map-PWLCM system, it is hardware and software efficient. The technique is also resistant to chosen-plaintext and chosen-ciphertext attacks when employing hash-based keys. The outcomes of the simulation demonstrate that the suggested approach is more efficient for encryption. According to the security review, the suggested solution successfully defends against all frequently used security attacks. The comparison study shows that the suggested method for multi-image encryption is more effective, quicker, and stronger than the currently used methods for multi-image encryption. One limitation of the proposed algorithm is that it requires all colour images to be of the same size. When working with colour images of varying sizes, it may be necessary to apply padding using either zeros or ones. The algorithm’s complexity is elevated by this. The algorithm’s future scope involves the development of encryption algorithms that can accommodate multiple sizes, types, and images.
Data availability
All data generated or analyzed during this study are included in this published article. [Usc-sipi image database for research in image processing, image analysis, and machine vision, http://sipi.usc.edu/database/].
References
Sarkar S, Saha K, Namasudra S, Roy P (2015) An efficient and time saving web service based android application. SSRG Int J Comput Sci Eng 2:18–21
Wani A, Khaliq R (2021) SDN-based intrusion detection system for IoT using deep learning classifier (IDSIoT-SDL). CAAI Trans Intell Technol 6:281–290. https://doi.org/10.1049/cit2.12003
Chen Z (2022) Research on internet security situation awareness prediction technology based on improved RBF neural network algorithm. J Comput Cogn Eng 1:103–108. https://doi.org/10.47852/bonviewJCCE149145205514
Hassan FS, Gutub A (2022) Improving data hiding within colour images using hue component of HSV colour space. CAAI Trans Intell Technol 7:56–68. https://doi.org/10.1049/cit2.12053
Gutub A (2023) Boosting image watermarking authenticity spreading secrecy from counting-based secret-sharing. CAAI Trans Intell Technol 8:440–452. https://doi.org/10.1049/cit2.12093
Wang J, Zhi X, Chai X, Lu Y (2021) Chaos-based image encryption strategy based on random number embedding and DNA-level self-adaptive permutation and diffusion. Multimed Tools Appl 80:16087–16122. https://doi.org/10.1007/s11042-020-10413-7
Coppersmith D (1994) The Data encryption standard (DES) and its strength against attacks. IBM J Res Dev 38:243–250. https://doi.org/10.1147/rd.383.0243
Pub NF (2001) 197: Advanced encryption standard (AES). Fed Inf Process Standards Publ 197:0311
Patro KA, Soni A, Netam PK, Acharya B (2020) Multiple grayscale image encryption using cross-coupled chaotic maps. J Inf Secur Appl 52:102470. https://doi.org/10.1016/j.jisa.2020.102470
Yavuz E (2021) A new parallel processing architecture for accelerating image encryption based on chaos. J Inf Secur Appl 63:103056. https://doi.org/10.1016/j.jisa.2021.103056
Verma R, Kumari A, Anand A, Yadavalli VS (2022) Revisiting shift cipher technique for amplified data security. J Comput Cogn Eng. https://doi.org/10.47852/bonviewJCCE2202261
Miss NA, Shaikh R (2016) A keyless approach for RDH in encrypted images using visual cryptography. Procedia Comput Sci 78:125–131. https://doi.org/10.1016/j.procs.2016.02.021
Inoue K, Cho M (2021) Amplitude based keyless optical encryption system using deep neural network. J Vis Commun Image Represent 79:103251. https://doi.org/10.1016/j.jvcir.2021.103251
Namasudra S, González-Crespo R, Kumar S (2022) Introduction to the special section on advances of machine learning in cybersecurity (VSI-mlsec). https://doi.org/10.1016/j.compeleceng.2022.108048
Wang X, Wang S, Chen PY, Lin X, Chin P (2020) Block switching: a stochastic approach for deep learning security. arXiv preprint arXiv:2002.07920. https://doi.org/10.48550/arXiv.2002.07920
Kumar P, Rahman M, Namasudra S, Moparthi NR (2023) Enhancing security of medical images using deep learning, chaotic map, and hash table. Mob Netw App l1–15. https://doi.org/10.1007/s11036-023-02158-y
Li H, Li T, Feng W, Zhang J, Zhang J, Gan L, Li C (2021) A novel image encryption scheme based on non-adjacent parallelable permutation and dynamic DNA-level two-way diffusion. J Inf Secur Appl 61:102844. https://doi.org/10.1016/j.jisa.2021.102844
Liu L, Jiang D, Wang X, Rong X, Zhang R (2021) 2D Logistic-Adjusted-Chebyshev map for visual color image encryption. J Inf Secur Appl 60:102854. https://doi.org/10.1016/j.jisa.2021.102854
Patro KAK, Prasanth Jagapathi Babu M, Pavan Kumar K, Acharya B (2020) Dual-Layer DNA-Encoding–Decoding Operation Based Image Encryption Using One-Dimensional Chaotic Map. In: Kolhe M, Tiwari S, Trivedi M, Mishra K (eds) Advances in Data and Information Sciences. Lecture Notes in Networks and Systems. Springer, Singapore, pp 67–80. https://doi.org/10.1007/978-981-15-0694-9_8
Sneha PS, Sankar S, Kumar AS (2020) A chaotic colour image encryption scheme combining Walsh-Hadamard transform and Arnold-Tent maps. J Ambient Intell Humaniz Comput 11:1289–1308. https://doi.org/10.1007/s12652-019-01385-0
Lu Q, Zhu C, Deng X (2020) An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 8:25664–25678. https://doi.org/10.1109/ACCESS.2020.2970806
Abdelfatah RI (2020) A new fast double-chaotic based Image encryption scheme. Multimed Tools Appl 79:1241–1259. https://doi.org/10.1007/s11042-019-08234-4
Liu W, Sun K, Zhu C (2016) A fast image encryption algorithm based on chaotic map. Opt Lasers Eng 84:26–36. https://doi.org/10.1016/j.optlaseng.2016.03.019
Wang X, Wang S, Zhang Y, Guo K (2017) A novel image encryption algorithm based on chaotic shuffling method. Inf Secur J 26:7–16. https://doi.org/10.1080/19393555.2016.1272725
Patro KA, Acharya B, Nath V (2020) Various dimensional colour image encryption based on non-overlapping block-level diffusion operation. Microsyst Technol 26:1437–1448. https://doi.org/10.1007/s00542-019-04676-w
Behnia S, Akhshani A, Mahmodi H, Akhavan AJ (2008) A novel algorithm for image encryption based on mixture of chaotic maps. Chaos Solit Fractals 35:408–419. https://doi.org/10.1016/j.chaos.2006.05.011
Abd El-Latif AA, Li L, Zhang T, Wang N, Song X, Niu X (2012) Digital image encryption scheme based on multiple chaotic systems. Sens Imaging 13:67–88. https://doi.org/10.1007/s11220-012-0071-z
Zhang TJ, El-Latif AAA, Amin M, Zaghloul A (2014) Diffusion-substitution mechanism for color image encryption based on multiple chaotic systems. Adv Mater Res, Trans Tech Pub Ltd 981:327–330. https://doi.org/10.4028/www.scientific.net/amr.981.327
Wu X, Kan H, Kurths J (2015) A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl Soft Comput 37:24–39. https://doi.org/10.1016/j.asoc.2015.08.008
Chen X, Hu CJ (2017) Medical image encryption based on multiple chaotic mapping and wavelet transform. Biomed Res 28:9001–9004
Zhang X, Wang X (2017) Multiple-image encryption algorithm based on mixed image element and permutation. Opt Lasers Eng 92:6–16. https://doi.org/10.1016/j.optlaseng.2016.12.005
Singh N, Sinha A (2010) Chaos based multiple image encryption using multiple canonical transforms. Opt Laser Technol 42:724–731. https://doi.org/10.1016/j.optlastec.2009.11.016
Kong D, Shen X, Xu Q, Xin W, Guo H (2013) Multiple-image encryption scheme based on cascaded fractional Fourier transform. Appl Opt 52:2619–2625. https://doi.org/10.1364/AO.52.002619
Kong D, Shen X (2014) Multiple-image encryption based on optical wavelet transform and multichannel fractional Fourier transform. Opt Laser Technol 57:343–349. https://doi.org/10.1016/j.optlastec.2013.08.013
Li CL, Li HM, Li FD, Wei DQ, Yang XB, Zhang J (2018) Multiple-image encryption by using robust chaotic map in wavelet transform domain. Optik 171:277–286. https://doi.org/10.1016/j.ijleo.2018.06.029
Tang Z, Song J, Zhang X, Sun R (2016) Multiple-image encryption with bit-plane decomposition and chaotic maps. Opt Lasers Eng 80:1–11. https://doi.org/10.1016/j.optlaseng.2015.12.004
Zhang X, Wang X (2017) Multiple-image encryption algorithm based on mixed image element and chaos. Comput Electr Eng 62:401–413. https://doi.org/10.1016/j.compeleceng.2016.12.025
Zhang X, Wang X (2019) Multiple-image encryption algorithm based on DNA encoding and chaotic system. Multimed Tools Appl 78:7841–7869. https://doi.org/10.1007/s11042-018-6496-1
Patro KA, Acharya B (2018) Secure multi–level permutation operation based multiple colour image encryption. J Inf Secur Appl 40:111–133. https://doi.org/10.1016/j.jisa.2018.03.006
Li S, Chen G, Mou X (2005) On the dynamical degradation of digital piecewise linear chaotic maps. Int J Bifur Chaos 15:3119–3151. https://doi.org/10.1142/S0218127405014052
Wang XY, Yang L (2012) Design of pseudo-random bit generator based on chaotic maps. Int J Mod Phy B 26:1250208. https://doi.org/10.1142/S0217979212502086
Al-Zubaidie M, Zhang Z, Zhang J (2019) RAMHU: A new robust lightweight scheme for mutual users authentication in healthcare applications. Secur Commun Netw 2019:3263902. https://doi.org/10.1155/2019/3263902
Das S, Namasudra S (2022) Multiauthority CP-ABE-based access control model for IoT-enabled healthcare infrastructure. IEEE Trans Industr Inform 19:821–829. https://doi.org/10.1109/TII.2022.3167842
(1977) USC-SIPI image database for research in image processing, image analysis, and machine vision. http://sipi.usc.edu/database/. Accessed July 2016
Lai Q, Hu G, Erkan U, Toktas A (2023) High-efficiency medical image encryption method based on 2D Logistic-Gaussian hyperchaotic map. Appl Math Comput 442:127738. https://doi.org/10.1016/j.amc.2022.127738
IEEE Computer Society Standards Committee (1985) Working group of the microprocessor standards subcommittee, & American National Standards Institute. In: IEEE standard for binary floating-point arithmetic, vol 754. IEEE.
Elkandoz MT, Alexan W (2022) Image encryption based on a combination of multiple chaotic maps. Multimed Tools Appl 81:25497–25518. https://doi.org/10.1007/s11042-022-12595-8
Wang T, Wang MH (2020) Hyperchaotic image encryption algorithm based on bit-level permutation and DNA encoding. Opt Laser Technol 132:106355. https://doi.org/10.1016/j.optlastec.2020.106355
Liao X, Hahsmi MA, Haider R (2018) An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using DNA and chaos. Optik (Stuttg) 153:117–134. https://doi.org/10.1016/j.ijleo.2017.09.099
Patro KA, Acharya B, Nath V (2020) Secure, lossless, and noise-resistive image encryption using chaos, hyper-chaos, and DNA sequence operation. IETE Tech Rev 37:223–245. https://doi.org/10.1080/02564602.2019.1595751
Norouzi B, Mirzakuchaki S, Seyedzadeh SM, Mosavi MR (2014) A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed Tools Appl 71:1469–1497. https://doi.org/10.1007/s11042-012-1292-9
Patro KA, Acharya B, Nath V (2019) Secure multilevel permutation-diffusion based image encryption using chaotic and hyper-chaotic maps. Microsyst Technol 25:4593–4607. https://doi.org/10.1007/s00542-019-04395-2
Samiullah M, Aslam W, Nazir H, Lali MI, Shahzad B, Mufti MR, Afzal H (2020) An image encryption scheme based on DNA computing and multiple chaotic systems. IEEE Access 8:25650–25663. https://doi.org/10.1109/ACCESS.2020.2970981
Liu H, Wang X (2012) Image encryption using DNA complementary rule and chaotic maps. Appl Soft Comput 12:1457–1466. https://doi.org/10.1016/j.asoc.2012.01.016
Nkandeu YP, Tiedeu A (2019) An image encryption algorithm based on substitution technique and chaos mixing. Multimed Tools Appl 78:10013–10034. https://doi.org/10.1007/s11042-018-6612-2
Bassham III LE, Rukhin AL, Soto J, Nechvatal JR, Smid ME, Barker EB, Leigh SD, Levenson M, Vangel M, Banks DL, Heckert NA (2010) Sp 800–22 rev. 1a. a statistical test suite for random and pseudorandom number generators for cryptographic applications. National Institute of Standards & Technology
Lai Q, Hu G, Erkan U, Toktas A (2023) A novel pixel-split image encryption scheme based on 2D Salomon map. Expert Syst Appl 213:118845. https://doi.org/10.1016/j.eswa.2022.118845
Li D, Li J, Di X, Li B (2023) Design of cross-plane colour image encryption based on a new 2D chaotic map and combination of ECIES framework. Nonlinear Dyn 111:2917–2942. https://doi.org/10.1007/s11071-022-07949-8
Arora S, Barak B (2009) Computational complexity: a modern approach. Cambridge University Press, United Kingdom
Funding
Open access funding provided by Manipal Academy of Higher Education, Manipal. There is no funding received by any funding agency.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Raghuvanshi, A., Budhia, M., Patro, K.A.K. et al. FSR-SPD: an efficient chaotic multi-image encryption system based on flip-shift-rotate synchronous-permutation-diffusion operation. Multimed Tools Appl 83, 57011–57057 (2024). https://doi.org/10.1007/s11042-023-17700-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-17700-z