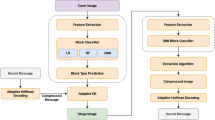
Abstract
Pixel Value Differencing (PVD) is one of the popular steganography methods and continues to be developed today. This method works based on differences in pixel values in the image. Each cover image has a different embedding capacity based on the difference in pixel values and their quantification range. PVD is superior in the aspects of capacity and imperceptibility based on the human visual system (HVS), which is widely measured using a structural similarity index (SSIM). By default, PVD has two quantization ranges. After further evaluation using SSIM in several types of cover images, the results do not always match due to differences in the characteristics of the cover image. PVD is mostly developed with adaptive quantization, which directly calculates the pixel value to optimize the trade-off of capacity and imperceptibility. This research proposes a different method to optimize this trade-off. The method is to learn the cover image characteristics with features extraction and machine learning (ML). This is done in the preprocessing before the embedding process to determine the ideal quantization for each cover image. The proposed method has been tested on the standard PVD method. It is proven to classify the cover image well and improve the quality of the stego image because the selected quantization range is more by the image characteristics. This method can later be developed and combined with the further PVD steganography method or other methods because the process is not integrated with the embedding process.




Similar content being viewed by others
References
Abdel Hameed M, Aly S, Hassaballah M (2018) An efficient data hiding method based on adaptive directional pixel value differencing (ADPVD). Multimed Tools Appl 77:14705–14723. https://doi.org/10.1007/s11042-017-5056-4
Alharan AFH, Fatlawi HK, Ali NS (2019) A cluster-based feature selection method for image texture classification. Indones J Electr Eng Comput Sci 14:1433–1442. https://doi.org/10.11591/ijeecs.v14.i3.pp1433-1442
Dias PA, Tabb A, Medeiros H (2018) Multispecies fruit flower detection using a refined semantic segmentation network. IEEE Robot Autom Lett 3:3003–3010. https://doi.org/10.1109/LRA.2018.2849498
Fridrich J, Goljan M, Du R (2001) Detecting LSB steganography in color and gray-scale images. IEEE Multimed 8:22–28. https://doi.org/10.1109/93.959097
Grover R, Yadav DK, Chauhan DK, Kamya S (2018) Adaptive steganography via image complexity analysis using 3D color texture feature. In: 3rd International Conference on Innovative Applications of Computational Intelligence on Power, Energy and Controls with their Impact on Humanity, CIPECH 2018. Institute of Electrical and Electronics Engineers Inc., Ghaziabad, pp 125–129
Hameed MA, Hassaballah M, Aly S, Awad AI (2019) An adaptive image steganography method based on histogram of oriented gradient and PVD-LSB techniques. IEEE Access 7:185189–185204. https://doi.org/10.1109/ACCESS.2019.2960254
Hussain M, Abdul Wahab AW, Ho ATS et al (2017) A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement. Signal Process Image Commun 50:44–57. https://doi.org/10.1016/j.image.2016.10.005
Images - Google Drive. https://drive.google.com/drive/u/0/folders/1JrRPz9ZVj54Pvo-sZMEX1CqgiAfibKjZ. Accessed 6 Apr 2022
Irawan C, Ardyastiti EN, Setiadi DRIM et al (2018) A Survey: Effect of the number of GLCM features on classification accuracy of Lasem Batik Images using K-Nearest Neighbor. International seminar on research of information technology and intelligent systems. IEEE, Yogyakarta, pp 33–38
Kaur G, Singh S, Rani R, Kumar R (2020) A comprehensive study of Reversible Data Hiding (RDH) schemes based on Pixel Value Ordering (PVO). Springer Netherlands
Kavzoglu T (2009) Increasing the accuracy of neural network classification using refined training data. Environ Model Softw 24:850–858. https://doi.org/10.1016/j.envsoft.2008.11.012
Krishna R, Kumar K (2020) P-MEC: Polynomial congruence based Multimedia Encryption technique over Cloud. IEEE Consum Electron Mag 2248:1–6. https://doi.org/10.1109/MCE.2020.3003127
Kumar R, Chand S, Singh S (2018) An Improved Histogram-Shifting-Imitated reversible data hiding based on HVS characteristics. Multimed Tools Appl 77:13445–13457. https://doi.org/10.1007/s11042-017-4960-y
Kumar R, Chand S, Singh S (2018) A reversible data hiding scheme using pixel location. Int Arab J Inf Technol 15:763–768
Kumar R, Kim DS, Jung KH (2019) Enhanced AMBTC based data hiding method using hamming distance and pixel value differencing. J Inf Secur Appl 47:94–103. https://doi.org/10.1016/j.jisa.2019.04.007
Lee YP, Lee JC, Chen WK et al (2012)High-payload image hiding with quality recovery using tri-way pixel-value differencing. Inf Sci (Ny) 191:214–225. https://doi.org/10.1016/j.ins.2012.01.002
Lee CF, Weng CY, Chen KC (2017) An efficient reversible data hiding with reduplicated exploiting modification direction using image interpolation and edge detection. Multimed Tools Appl 76:9993–10016. https://doi.org/10.1007/s11042-016-3591-z
Li Z, He Y (2018) Steganography with pixel-value differencing and modulus function based on PSO. J Inf Secur Appl 43:47–52. https://doi.org/10.1016/j.jisa.2018.10.006
Lorem Ipsum - All the facts - Lipsum generator. https://www.lipsum.com/. Accessed 16 Feb 2021
Luo W, Huang F, Huang J (2011) A more secure steganography based on adaptive pixel-value differencing scheme. Multimed Tools Appl 52:407–430. https://doi.org/10.1007/s11042-009-0440-3
Mader KS (2017) CT Medical Images | Kaggle. https://www.kaggle.com/datasets/kmader/siim-medical-images?select=tiff_images. Accessed 6 Apr 2022
Malik A, Singh S, Kumar R (2018) Recovery based high capacity reversible data hiding scheme using even-odd embedding. Multimed Tools Appl 77:15803–15827. https://doi.org/10.1007/s11042-017-5156-1
Mishra A, Kumar K, Kumar P, Mittal P (2020) A novel approach for handwritten character recognition using K-NN classifier. Advances in intelligent systems and computing. Springer, Berlin, pp 887–894
Mooney P (2018) Chest X-Ray Images (Pneumonia) | Kaggle. https://www.kaggle.com/datasets/paultimothymooney/chest-xray-pneumonia/metadata. Accessed 6 Apr 2022
Mukhopadhyay S, Hossain S, Ghosal SK, Sarkar R (2021) Secured image steganography based on Catalan transform. Multimed Tools Appl 1–26. https://doi.org/10.1007/s11042-020-10424-4
Negi A, Chauhan P, Kumar K, Rajput RS (2020) Face mask detection classifier and model pruning with Keras-Surgeon. In: 2020 5th IEEE International Conference on Recent Advances and Innovations in Engineering, ICRAIE 2020 - Proceeding. Institute of Electrical and Electronics Engineers Inc
Rehman TU, Mahmud MS, Chang YK et al (2019) Current and future applications of statistical machine learning algorithms for agricultural machine vision systems. Comput Electron Agric 156:585–605
Rustad S, Setiadi DRIM, Syukur A, Andono PN (2022) Inverted LSB image steganography using adaptive pattern to improve imperceptibility. J King Saud Univ - Comput Inf Sci 34:3559-3568. https://doi.org/10.1016/j.jksuci.2020.12.017
Saha S, Chakraborty A, Chatterjee A et al (2020) Extended exploiting modification direction based steganography using hashed-weightage Array. Multimed Tools Appl 79:20973–20993. https://doi.org/10.1007/s11042-020-08951-1
Sahu AK, Swain G (2019) An optimal information hiding approach based on pixel value differencing and modulus function. Wirel Pers Commun 108:159–174. https://doi.org/10.1007/s11277-019-06393-z
Setiadi DRIM (2019) Payload enhancement on least significant bit image steganography using edge area dilation. Intl J Electron Telecommun 65:295–300. https://doi.org/10.24425/ijet.2019.126313
Setiadi DRIM (2021) PSNR vs SSIM: imperceptibility quality assessment for image steganography. Multimed Tools Appl 80:8423–8444. https://doi.org/10.1007/s11042-020-10035-z
Setiadi DRIM (2022) Improved payload capacity in LSB image steganography uses dilated hybrid edge detection. J King Saud Univ - Comput Inf Sci 34:104–114. https://doi.org/10.1016/J.JKSUCI.2019.12.007
Shen S, Huang L, Tian Q (2015) A novel data hiding for color images based on pixel value difference and modulus function. Multimed Tools Appl 74:707–728. https://doi.org/10.1007/s11042-014-2016-0
Shukla AK, Singh A, Singh B, Kumar A (2018) A secure and high-capacity data-hiding method using compression, encryption and optimized pixel value differencing. IEEE Access 6:51130–51139. https://doi.org/10.1109/ACCESS.2018.2868192
Swain G (2016) Adaptive pixel value differencing steganography using both vertical and horizontal edges. Multimed Tools Appl 75:13541–13556. https://doi.org/10.1007/s11042-015-2937-2
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: From error visibility to structural similarity. IEEE Trans Image Process 13:600–612. https://doi.org/10.1109/TIP.2003.819861
Wang C-M, Wu N-I, Tsai C-S, Hwang M-S(2008) A high quality steganographic method with pixel-value differencing and modulus function. J Syst Softw 81:150–158. https://doi.org/10.1016/J.JSS.2007.01.049
Wu D-C, Tsai W-H(2003) A steganographic method for images by pixel-value differencing. Pattern Recognit Lett 24:1613–1626. https://doi.org/10.1016/S0167-8655(02)00402-6
Younus ZS, Hussain MK (2019) Image steganography using exploiting modification direction for compressed encrypted data. J King Saud Univ - Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2019.04.008
Zhang X, Wang S (2006) Efficient steganographic embedding by exploiting modification direction. IEEE Commun Lett 10:781–783. https://doi.org/10.1109/LCOMM.2006.060863
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have influenced the work reported in this paper.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix 1
Appendix 1
The following appendix lists abbreviations with their descriptions and/or terminology.
- BER:
-
Bit Error Ratio (image steganography measuring tool to determine the quality of the extraction results)
- BPP:
-
Bit Per Pixel (image steganography measuring tool for payload capacities aspects)
- CER:
-
Bit Error Ratio (image steganography measuring tool to determine the quality of the extraction results)
- EMD:
-
Exploiting Modification Direction (one of the steganographic methods in the spatial domain)
- GLCM:
-
Gray level co-occurrence matrix (one of feature extraction in the image)
- HVS:
-
Human Visual System
- KNN:
-
k-Nearest Neighbor (one of the classification methods in data mining, in this case, image classification)
- LSB:
-
Least Significant Bit (one of the steganographic methods in the spatial domain)
- ML:
-
Machine Learning (data mining method)
- NB:
-
Naïve Bayes (one of the classification methods in data mining)
- PSNR:
-
peak signal-to-noise ratio (image steganography measuring tool for imperceptibility aspects)
- PVD:
-
Pixel value Differencing (one of the steganographic methods in the spatial domain)
- RS:
-
Regular Singular (image steganography measuring tool for security aspects)
- SSIM:
-
structural similarity index (image steganography measuring tool for imperceptibility aspects)
- SVM:
-
Support Vector Machine
- Q1:
-
PVD quantization range ([8 8 16 32 64 128] excels in payload capacity)
- Q2:
-
PVD quantization range ([2 2 4 4 8 8 16 16 32 32 64 64] excels in imperceptibility)
Rights and permissions
About this article
Cite this article
Andono, P.N., Setiadi, D.R.I.M. Quantization selection based on characteristic of cover image for PVD Steganography to optimize imperceptibility and capacity. Multimed Tools Appl 82, 3561–3580 (2023). https://doi.org/10.1007/s11042-022-13393-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13393-y