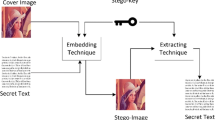
Abstract
Steganography is the method of hiding secret message information in various cover media like text, image, audio, video and others without raising suspicion to intruders about the existence of any such information. Exploiting Modification Direction (EMD) based image steganography is a steganographic technique designed by Zhang and Wang in 2006 that yields minute distortion of the cover image. In this paper, an Extended EMD based steganography using Hashed-Weightage Array abbreviated as EEMDHW has been proposed. 2KN-ary numbers are embedded in every K pixels of the cover image, where N denotes the number of bits embedded in each pixel. Thus, the payload is purely variable in this technique. Embedding is performed using dynamic weightage array. This array is made pseudo random by applying eliminative hashing technique on the message pixels. Experimental results show that the technique is superior to other state-of-the-art techniques in terms of embedding capacity (payload) and has reduced quality distortion of cover image. Steganalysis using RS attack shows that the embedding done by the proposed method cannot be detected upto 3 bits per pixel (bpp) embedding rate.








Similar content being viewed by others
References
N. Hamid, A. Yahya, R. B. Ahmad, and O. M. Al-Qershi, “Image steganography techniques: an overview,” Int. J. Comput. Sci. Secur., 2012.
W. Bender, D. Gruhl, N. Morimoto, and A. Lu, “Techniques for data hiding,” IBM Syst. J., 1996, doi: https://doi.org/10.1147/sj.353.0313, Techniques for data hiding.
R. Z. Wang, C. F. Lin, and J. C. Lin, “Image hiding by optimal LSB substitution and genetic algorithm,” Pattern Recognit., 2001, doi: https://doi.org/10.1016/S0031-3203(00)00015-7, Image hiding by optimal LSB substitution and genetic algorithm.
C. C. Chang, P. Tsai, and M. H. Lin, “An adaptive steganography for index-based images using codeword grouping,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), 2004, doi: https://doi.org/10.1007/978-3-540-30543-9_91.
Zhang X, Wang S (2006) Efficient Steganographic embedding by exploiting modification direction. IEEE Commun Lett 10(11):781–783. https://doi.org/10.1109/LCOMM.2006.060863
S. K. Ghosal and J. K. Mandal, “On the use of the Stirling transform in image steganography,” J. Inf. Secur. Appl., 2019, doi: https://doi.org/10.1016/j.jisa.2018.04.003, On the use of the Stirling Transform in image steganography.
S. Saha, S. K. Ghosal, A. Chakraborty, S. Dhargupta, R. Sarkar, and J. K. Mandal, “Improved exploiting modification direction-based steganography using dynamic weightage array,” Electron. Lett., 2018, doi: https://doi.org/10.1049/el.2017.3336, Improved exploiting modification direction-based steganography using dynamic weightage array.
M. Hussain, A. W. Abdul Wahab, A. T. S. Ho, N. Javed, and K. H. Jung, “A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement,” Signal Process. Image Commun., 2017, doi: https://doi.org/10.1016/j.image.2016.10.005, A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement.
Y. Liu, C. C. Chang, P. C. Huang, and C. Y. Hsu, “Efficient Information Hiding Based on Theory of Numbers,” Symmetry (Basel)., vol. 10, no. 1, p. 19, Jan. 2018, doi: https://doi.org/10.3390/sym10010019.
C. K. Chan and L. M. Cheng, “Hiding data in images by simple LSB substitution,” Pattern Recognit., 2004, doi: https://doi.org/10.1016/j.patcog.2003.08.007, Hiding data in images by simple LSB substitution.
J. Bai, C. C. Chang, T. S. Nguyen, C. Zhu, and Y. Liu, “A high payload steganographic algorithm based on edge detection,” Displays, 2017, doi: https://doi.org/10.1016/j.displa.2016.12.004, A high payload steganographic algorithm based on edge detection.
D. Chaudhary, S. Gupta, and S. Deswal, “Origin of Hybrid Security Mechanisms and Ways of Improvement,” Int. J. Big Data Secur. Intell., 2015, doi: https://doi.org/10.21742/ijbdsi.2015.2.2.01.
T. Rabie, “Digital image steganography: an FFT approach,” in Communications in Computer and Information Science, 2012, doi: https://doi.org/10.1007/978-3-642-30567-2_18.
A. A. Al-Ataby and F. M. Al-Naima Fiete, “High capacity image steganography based on curvelet transform,” in Proceedings - 4th International Conference on Developments in eSystems Engineering, DeSE 2011, 2011, doi: https://doi.org/10.1109/DeSE.2011.13.
E. Ghasemi, J. Shanbehzadeh, and N. Fassihi, “High capacity image steganography using wavelet transform and genetic algorithm,” in IMECS 2011 - international MultiConference of engineers and computer scientists 2011, 2011.
Z. Pan, X. Ma, and X. Deng, “New reversible full-embeddable information hiding method for vector quantisation indices based on locally adaptive complete coding list,” IET Image Process., 2015, doi: https://doi.org/10.1049/iet-ipr.2014.0310, New reversible full-embeddable information hiding method for vector quantisation indices based on locally adaptive complete coding list.
M. A. Alia and A. A. Yahya, “Public-key steganography based on matching method,” Eur. J. Sci. Res., 2010.
M. R. Islam, A. Siddiqa, M. P. Uddin, A. K. Mandal, and M. D. Hossain, “An efficient filtering based approach improving LSB image steganography using status bit along with AES cryptography,” in 2014 International conference on informatics, Electronics and Vision, ICIEV 2014, 2014, doi: https://doi.org/10.1109/ICIEV.2014.6850714.
A. Chatterjee, S. K. Ghosal, and R. Sarkar, “LSB based steganography with OCR: an intelligent amalgamation,” Multimed. Tools Appl., 2020, doi: https://doi.org/10.1007/s11042-019-08472-6, LSB based steganography with OCR: an intelligent amalgamation.
N. Tayal, R. Bansal, S. Dhal, and S. Gupta, “A novel hybrid security mechanism for data communication networks,” Multimed. Tools Appl., 2017, doi: https://doi.org/10.1007/s11042-016-4111-x, A novel hybrid security mechanism for data communication networks.
R. Bansal, S. Gupta, and G. Sharma, “An innovative image encryption scheme based on chaotic map and Vigenère scheme,” Multimed. Tools Appl., 2017, doi: https://doi.org/10.1007/s11042-016-3926-9, An innovative image encryption scheme based on chaotic map and Vigenère scheme.
C. C. Chang, Y. C. Chou, and D. Kieu, “An information hiding scheme using Sudoku,” in 3rd International Conference on Innovative Computing Information and Control, ICICIC’08, 2008, doi: https://doi.org/10.1109/ICICIC.2008.149.
Q. Mao, K. Bharanitharan, and C. C. Chang, “Multi-round dynamic swap optimisation for table-based steganography,” IET Image Process., 2015, doi: https://doi.org/10.1049/iet-ipr.2015.0065, Multi-round dynamic swap optimisation for table-based steganography.
Z. X. Yin, C. C. Chang, Q. Xu, and B. Luo, “Second-order steganographic method based on adaptive reference matrix,” IET Image Process., 2015, doi: https://doi.org/10.1049/iet-ipr.2014.0159, Second-order steganographic method based on adaptive reference matrix.
C. C. Chang, W. L. Tai, and K. N. Chen, “Improvements of EMD embedding for large payloads,” in Proceedings - 3rd International Conference on Intelligent Information Hiding and Multimedia Signal Processing, IIHMSP 2007., 2007, doi: https://doi.org/10.1109/IIHMSP.2007.4457590.
K. H. Jung, “Improved Exploiting Modification Direction Method by Modulus Operation,” vol. 2, no. 1, pp. 79–88, 2009.
N. T. Huynh, K. Bharanitharan, and H. S. Hsueh, “Efficient Combinatorial Optimization Algorithm for Exploiting Modification Direction in Data Embedding,” Indian J. Sci. Technol., 2016, doi: https://doi.org/10.17485/ijst/2016/v9i28/92733.
A. A. Abdulla, H. Sellahewa, and S. A. Jassim, “Stego quality enhancement by message size reduction and fibonacci bit-plane mapping,” in Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), 2014, doi: https://doi.org/10.1007/978-3-319-14054-4_10.
Rehman A, Saba T, Mahmood T, Mehmood Z, Shah M, Anjum A (Dec. 2019) Data hiding technique in steganography for information security using number theory. J Inf Sci 45(6):767–778. https://doi.org/10.1177/0165551518816303
D. R. I. M. Setiadi, “Payload enhancement on least significant bit image steganography using edge area dilation,” Int. J. Electron. Telecommun., 2019, doi: https://doi.org/10.24425/ijet.2019.126312.
Z. F. Yaseen and A. A. Kareem, “Image steganography based on hybrid edge detector to Hide encrypted image using Vernam algorithm,” in SCCS 2019–2019 2nd Scientific Conference of Computer Sciences, 2019, doi: https://doi.org/10.1109/SCCS.2019.8852625.
H. S. Leng and H. W. Tseng, “Generalize the EMD scheme on an n-dimensional hypercube with maximum payload,” Multimed. Tools Appl., 2019, doi: https://doi.org/10.1007/s11042-019-7228-x, Generalize the EMD scheme on an n-dimensional hypercube with maximum payload.
A. A. Abd EL-Latif, B. Abd-El-Atty, and S. E. Venegas-Andraca, “A novel image steganography technique based on quantum substitution boxes,” Opt. Laser Technol., 2019, doi: https://doi.org/10.1016/j.optlastec.2019.03.005, A novel image steganography technique based on quantum substitution boxes.
S. Dhargupta, A. Chakraborty, S. K. Ghosal, S. Saha, and R. Sarkar, “Fuzzy edge detection based steganography using modified Gaussian distribution,” Multimed. Tools Appl., Jan. 2019, doi: https://doi.org/10.1007/s11042-018-7123-x, Fuzzy edge detection based steganography using modified Gaussian distribution.
X. Liao, Y. Yu, B. Li, Z. Li, and Z. Qin, “A new payload partition strategy in color image steganography,” IEEE Trans. Circuits Syst. Video Technol., 2019, doi: https://doi.org/10.1109/tcsvt.2019.2896270, A New Payload Partition Strategy in Color Image Steganography.
B. Carpentieri, A. Castiglione, A. De Santis, F. Palmieri, and R. Pizzolante, “Compression-based steganography,” in Concurrency computation , 2019, doi: https://doi.org/10.1002/cpe.5322, 32.
A. A. Abdulla, “Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography,” 2015.
J. Fridrich, M. Goljan, and R. Du, “Detecting LSB steganography in color and gray-scale images,” IEEE Multimed., 2001, doi: https://doi.org/10.1109/93.959097, Detecting LSB steganography in color, and gray-scale images.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Saha, S., Chakraborty, A., Chatterjee, A. et al. Extended exploiting modification direction based steganography using hashed-weightage Array. Multimed Tools Appl 79, 20973–20993 (2020). https://doi.org/10.1007/s11042-020-08951-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-08951-1