Abstract
In cryptosystems, the generation of random keys is crucial. The random number generator is required to have a sufficiently fast generation speed to ensure the size of the keyspace. At the same time, the randomness of the key is an important indicator to ensure the security of the encryption system. The chaotic random number generator has been widely used in cryptosystems due to the uncertainty, non-repeatability, and unpredictability of chaotic systems. However, chaotic systems, especially high-dimensional chaotic systems, have slow calculation speed and long iteration time. This caused a conflict between the number of random keys and the speed of generation. In this paper, we introduce the Least Squares Generative Adversarial Networks(LSGAN)into random number generation. Using LSGAN’s powerful learning ability, a novel learning random number generator is constructed. Six chaotic systems with different structures and different dimensions are used as training sets to realize the rapid and efficient generation of random numbers. Experimental results prove that the encryption key generated by this scheme can pass all randomness tests of the National Institute of Standards and Technology (NIST). Hence, our result shows that LSGAN has the potential to improve the quality of the random number generators. Finally, the results are successfully applied to the image encryption scheme based on selective scrambling and overlay diffusion, and good results are achieved.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
With the rapid development of network communication and multimedia technology, more and more digital images are stored, copied, and transmitted through various types of third-party platforms or unsecured channels [5]. Therefore, image security has become a hot topic [44]. There are a variety of means to protect image security (such as steganography [1, 2], watermark [4, 43], encryption [11, 12, 45, 54, 55]. etc.), among which image encryption is a more common and effective tool. Image encryption is usually divided into two stages: the scrambling stage and the diffusion stage. The scrambling stage is to change the relative position of pixels in the image, while the diffusion phase is to change the specific value of pixels in the image. Both scrambling and diffusion need to be controlled by the key. Considering the importance of an encryption key, it is a difficult task to generate encryption key with good randomness [44].
In recent years, many schemes of generating random numbers based on chaos have been proposed, but they have little help to improve the security of encryption algorithms [20, 46, 52, 53, 59]. Chai x et al. proposed an image encryption algorithm based on DNA sequence operation and chaotic system. This paper mainly uses a two-dimensional logistic adjusted sine map (2D-LASM) to generate encryption key [6]. Hua Z et al. proposed a cosine-transform-based chaotic system (CTBCS). Two chaotic maps were used as seed maps to make the CTBCS have more complex dynamic behaviors and then generate encryption keys with better randomness [18]. Gong l et al. proposed an effective image compression and encryption algorithm based on chaotic systems and compressed sensing. In this scheme, the logistic map and 1D cascade map are used as key generators [14]. The commonness of these algorithms is that they all use low dimensional chaotic systems as key generators, which may lead to the possibility that the generated keys are not random enough, so that attackers can take advantage of them. In contrast, the key generated by our scheme can make the encryption key completely random. In fact, many encryption schemes based on chaos have disadvantages [9, 14, 16, 22, 23, 42]. Short cycle length is one of the important problems of chaotic keystream generators, which results from the finite precision of computers [24, 35]. To solve the problem of randomness and insufficient security of keystream generated by the chaotic system, many scholars have developed several effective encryption algorithms by combining chaotic systems with other methods [10, 25, 37, 47, 57], such as breadth-first search [57], DAN coding [25, 47], edge password [37], elliptic curve [10] and so on.
After an in-depth study, we have found that the image encryption algorithm also has a promoted requirement of random numbers. According to the definition in [3, 36], three attributes can be considered to evaluate the randomness of the sequence [26]:
-
1.
It appears to be random, which means that it can pass all statistical tests of randomness.
-
2.
Unpredictability, even if the corresponding algorithm and hardware are given, it is still unable to predict the next random bit by calculation.
-
3.
It is impossible to replicate reliably. Even if the generator runs twice with exactly the same input, two completely unrelated random sequences can be obtained.
For the first time, we combine LSGAN with the chaotic system as a random number generator. The random numbers generated by this scheme satisfy the above three conditions at the same time. Therefore, the encryption key we use is completely random.
The basic idea of GAN comes from a two person zero-sum game in game theory. It consists of a generator and a discriminator and is trained through confrontation learning. Its purpose is to estimate the potential distribution of data samples and generate new data samples [30]. Since its first launch in 2014 [27], GAN has become a hot topic in the field of computer vision [48], natural language processing [28], malicious attack detection [8], and data generation [58]. We are very happy to see it introduced into the field of security [19, 21, 32, 60]. Because of the randomness and difference of GAN training results, we take the chaotic sequence as real data, so that the generator can produce data samples similar to and different from the chaotic sequence distribution to meet our need. Then, through NIST, histogram, and entropy analysis, we further prove the effectiveness of the random number generator. Finally, the generated random number is mapped to the image encryption key. Through the analysis of the ciphertext image, we can find that security has been significantly improved.
For an excellent image encryption algorithm, security and efficiency are equally important. Many existing encryption schemes are difficult to achieve a good balance between security performance and encryption efficiency [13, 29, 50, 54]. The main factor affecting the efficiency is that there will be some repeated pixel displacements during scrambling (for example, two identical pixel values are exchanged), which increases the time cost [31]. To improve the security of the algorithm, researchers have proposed a dynamic diffusion algorithm [53] and adaptive diffusion algorithm [7, 17], but they all traverse all pixels in turn to change the size of their values, so the encryption efficiency is not ideal. Therefore, we draw lessons from this mode and design a selective scrambling method and a superposition diffusion method.
To solve the above problems, we design a new random number generator to solve the problem of insufficient security and randomness of the encryption key. Firstly, we take the chaotic sequences generated by six chaotic systems as the training set of GAN in turn. By adjusting the parameters and training time of the GAN system, we finally generate random numbers that meet our needs. Secondly, to improve the scrambling effect, a selective scrambling method is designed, which scrambles the pixel regions with important information and the edge pixels in the image. Finally, a superposition diffusion method is proposed. Compared with the traditional dynamic diffusion method, each pixel block is used as the diffusion unit in the coverage diffusion method, while each pixel is used as the diffusion unit in the traditional method, so the coverage diffusion can improve the efficiency of the diffusion operation. Simulation results and security analysis show that the random number generated by this scheme can pass all the tests in NIST, and the efficiency of key generation is improved. The encryption system can effectively resist the common violent attacks, differential attacks, and shear attacks. In the performance test of pixel correlation and information entropy, compared with other literature, each index has certain advantages.
The rest of this paper is structured as follows. Section 2 briefly introduces the related work and the method of generating the security key. Section 3 introduces the randomness and security analysis of generating random numbers in detail. Section 4 introduces the encryption algorithm. Section 5 analyses the performance of the proposed algorithm through various security tests. Section 6 winds up the paper.
2 Random numbers generator with LSGAN
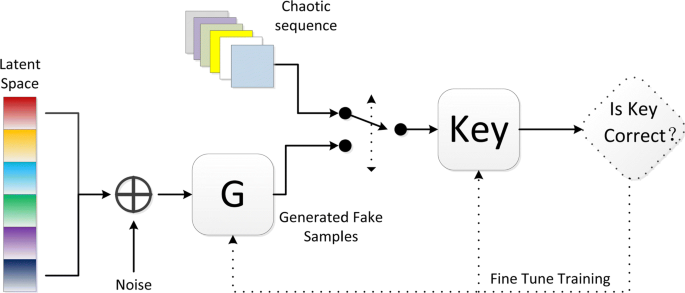
We propose a random number generator that combines LSGAN and chaotic systems as shown in Fig. 1. LSGAN is closer to real data than Generative Adversarial Networks(GAN) (The random number generated by LSGAN is used as the encryption key in the encryption algorithm). We choose six chaotic systems, including low dimensions and high dimensions. The chaotic sequence generated by a chaotic system is used as the training set. We try to make the data generated by the generator infinitely close to the chaotic sequence, and then test the randomness of the generated data. Through performance analysis, we can prove that our idea is correct. At the same time, we can test the randomness of the generated data. When a large number of random numbers are needed, the efficiency of LSGAN is much better than that of a chaotic system.
2.1 LSGAN
GAN is a deep learning model and is one of the most promising methods for unsupervised learning on complex distributions in recent years. The model produces good output through the mutual game learning of two modules in the framework: the generative model and the discriminant model.
In the formula, \(E_{x{\sim }Pdata}\) is the distribution of the real input data, \(\log {D(x)}\) is the judgment value of the discriminator, \(\log {[(1-D(z))]}\) is the judgment value of the generated data. Through the continuous game of the maximum and minimum values, the G-Network model and D-Network model are circularly and alternately optimized until the two models reach the Nash equilibrium; x is the training set, G(z) is the data generated by the G-Network model, and D(x) is the D-Network model for determining whether the real data and the training z is the noise of input G network model,\(E_{Z{\sim }P_{Z^{(Z)}}}\) is the distribution of noise data.
Conventional GAN uses S-type cross entropy loss function. As described in reference 1, when updating the generator, this loss function will cause the problem of vanishing gradients for the samples that are on the correct side of the decision boundary, but are still far from the real data, Therefore, the least square method (LSGAN) is proposed. Suppose A-B coding scheme is used for the identifier, where A and B are labels of pseudo data and real data, respectively. Then, the objective function of LSGAN can be defined as following:
where c denotes the value that G wants D to believe for fake data. The benefits of LSGAN can be drawn from two aspects [38]. First of all, unlike conventional GAN, LSGAN does minor damage to long samples located on the right side of the decision boundary. Even if they are correctly classified, LSGAN will punish those samples. When the generator is updated, the discriminator’s parameters are fixed, that is, the decision boundary is set. As a result, the penalty causes the generator to generate samples toward the decision boundary. On the other hand, the decision boundary should span all aspects of the real data for successful GAN learning. Otherwise, the learning process will be saturated. Therefore, moving the generated samples to the decision boundary will make them closer to the real data. Second, penalizing the samples that are far from the decision boundary can generate more gradients when up-dating the generator, which in turn reduces the problem of vanishing gradients. This allows LSGAN to perform more stable during the learning process.
2.2 Data set preparation
Six chaotic systems are selected, and the generated pseudo-random number is used as the training set of GAN.
-
(1)
QCNN [39]:
$$ \begin{cases}{\dot{g}}_{1}=-2a_{1}\sqrt{1-{g_{1}}^{2}}\sin h_{1} \\ {\dot{h}}_{1}=(-b_{1}(g_{1}-g_{2})+2a_{1}\cos h_{1})/(\sqrt{1-{g_{1}}^{2}}) \\ {\dot{g}}_{2}=-2a_{2}\sqrt{1-{g_{2}}^{2}}\sin h_{2} \\ {\dot{h}}_{2}=(-b_{2}(g_{2}-g_{1})+2a_{2}g_{2}\cos h_{2})/(\sqrt{1-{g_{2}}^{2}})\end{cases} $$(3)Where: g1, g2 is the polarizability; h1, h2 is the quantum phase; a1, a2 is the proportional coefficient of the energy between the points in each cell; b1, b2 is the weighted influence factor for the difference between the polarizability of adjacent cells. When a1 = a2 = 0.28, b1 = 0.7, and b2 = 0.3, the system is in a chaotic state.
-
(2)
4D hyperchaotic system [16]:
$$ \begin{cases}{\dot{x}}_{1}=\delta_{1}(x_{2}-x_{1})\\{\dot{x}}_{2}=\delta_{2}x_{1}+\delta_{3}x_{2}-x_{1}x_{3}+x_{4} \\ {\dot{x}}_{3}={x_{2}^{2}}-\delta_{4}x_{3} \\ {\dot{x}}_{4}=-\delta_{5}x_{1}\end{cases} $$(4)Let x = [x1;x2;x3;x4] represent the state vector of the system. When δ1 = 27.5, δ2 = 3, δ3 = 19.3, δ4 = 2.9, δ5 = 3, the system is hyperchaotic. Lyapunov exponents are λ1 = 1.6170, λ2 = 0.1123, λ3 = 0, λ4 = − 12.8245. The system has two positive Lyapunov exponents, indicating that it is a hyperchaotic system at this time.
-
(3)
Fractional Chen hyperchaotic system [33]:
$$ \begin{cases}{\frac{d^{\alpha}}{dt^{\alpha}}}y_{1}=\omega_{1}(y_{2}-y_{1})+y_{4}\\{\frac{d^{\alpha}}{dt^{\alpha}}}y_{2}=\omega_{2}y_{1}-y_{1}y_{3}+\omega_{3}y_{2} \\ {\frac{d^{\alpha}}{dt^{\alpha}}}y_{3}=y_{1}y_{2}-\omega_{3}y_{4} \\ {\frac{d^{\alpha}}{dt^{\alpha}}}y_{4}=y_{2}y_{3}+\omega_{5}y_{4}\end{cases} $$(5)Where ω1, ω2, ω3, ω4, and ω5are positive parameters. When ω1 = 35, ω2 = 3, ω3 = 12, ω4 = 7 and ω5 = 0.58, two positive Lyapunov exponents of hyper-chaotic systems are given by λ1 = 0.2104 and λ2 = 0.126. The prediction time of hyperchaotic systems is usually shorter than that of chaotic systems, so the security of hyperchaotic systems is higher.
-
(4)
3D hyperchaotic system [34]:
$$ \begin{cases}{\dot{z}}_{1}=-\beta_{1}z_{1}+z_{2}z_{3}\\{\dot{z}}_{2}=\beta_{2}z_{2}-z_{1}z_{3}-z_{3} \\ {\dot{z}}_{3}=-\beta_{3}z_{3} +{z_{2}^{3}} \end{cases} $$(6)Parameters β1, β2 and β3 are real constants, when β1 = 3, β2 = 5 and β3 = 10, the system is chaotic. Lyapunov exponents are λ1 = 0.03, λ2 = − 0.01 and λ3 = − 7.78. There are positive exponents in Lyapunov exponent, so the system has chaotic characteristics.
-
(5)
Lorenz chaotic system [31]:
$$ \begin{cases}{\frac{dq}{dt}}=-\varphi_{1}(q-w)\\{\frac{dw}{dt}}=-qr+\varphi_{2}q-w \\ {\frac{dr}{dt}}=-qw-\varphi_{3}r\end{cases} $$(7)where φ1, φ2 and φ3 are the parameters of the system. When φ1 = 10 and φ3 = 8/3, the system turns into the chaotic state if φ2 > 24.74. When φ2 = 28, the system turns into the best chaotic state.
-
(6)
Henon chaotic system [51]:
$$ \begin{cases}x_{n+1}=1-a{x_{n}^{2}}+y_{n}\\y_{n+1}=bx_{n} \end{cases} $$(8)where, n = 2,3,, w, a > 0, b > 0, and x, y ∈ Rw; w refers to the dimension, and a and b refer to the control parameters. When w = 2, the system becomes the famous Henon map.
2.3 Generation of random numbers
Firstly, the six chaotic systems are used to generate six sets of 400 × 100 normalized chaotic sequences HD1, HD2, HD3, HD4, HD5 and HD6, which are the training set of the LSGANs.
Secondly, LSGAN is iterated t times to generate 6 groups of random numbers G1, G2, G3, G4, G5, G6 with a size of 800 × 100. The encryption keys KG1, KG2, KG3, KG4, KG5 and KG6 are obtained after conversion.
3 Security analysis of random number generation scheme
3.1 Entropy analysis
It can be seen from Fig. 2a that the random numbers are evenly distributed and have good randomness. After the random number is converted into a key, it can be seen in Fig. 2b that the data distribution is relatively flat, and the entropy of the image is directly related to the histogram of the image, so the smoother histogram has a higher entropy. The entropy H (m) can be calculated as follows:
Where N = 256, R(si) is the probability of si. Ideally, entropy should be 8, which indicates that information is uncertain. Through the measurement, we get an entropy value of 7.9986 that is very close to the ideal value, which proves the feasibility of the scheme.
3.2 Randomness analysis
A test suite is a collection of statistical randomness test that is designed to test the randomness properties of sequences. NIST test suite [14] has been used in this study to assess randomness. Table 1 shows the results of NIST test when the chaotic sequences generated by different chaotic systems are used as real data. It can be seen from the data in Table 1 that the training results of high-dimensional chaotic system or low-dimensional chaotic system can pass NIST test when the chaotic sequence is used as the training set. Table 2 also lists the situation of using chaotic system to generate random number, using other software generated random number as training set and using chaotic sequence as training set. As can be seen from the data in Table 2, only our proposed scheme can pass all NIST tests.
3.3 Efficiency analysis
In order to test the efficiency of random numbers generation by LSGAN and chaotic system, we tested the time of generating 80000, 160000, 320000 and 1600000 random numbers respectively. As shown in Table 3, the time of random numbers generated by LSGAN is obviously better than that of the random numbers generated by the chaotic system. With the increasing amount of random number data, the advantage of LSGAN is more obvious. It shows that the random numbers generated by our method can improve encryption efficiency. At the same time, we find that the random numbers generated by QCNN, 4D hyperchaotic system and Lorenz chaotic system iterating 100 times in LSGAN can pass all NIST tests, while fractional Chen hyperchaotic system, 3D chaotic system and Henon chaotic system need to iterate 500 times in LSGAN. It shows that when the chaotic sequence generated by different chaotic systems are used as training sets, different iteration times are needed to pass all NIST tests.
4 Encryption algorithm
We propose an image encryption scheme based on LSGAN and a chaotic system to generate secure keys. The scheme uses LSGAN to generate the key of image encryption, and encrypts the image through the designed selective scrambling method and superposition diffusion method to obtain the cipher-image with good security. The scheme solves the problems of key randomness and low key generation efficiency. The overall block diagram of the encryption scheme is shown in Fig. 3, and the encryption flow chart is shown in Fig. 4.
Step 1. The input is an original image P in which M and N express its the width and height of the image, respectively.
Step 2. Four groups of security keys K1, K2, K3 and K4 with the size of 256×256 are generated using the method described in Part 2.
Step 3. Divide P into 16 equal-sized blocks, Bi(i = 1, 2, 3, 16). As shown in Fig. 5, there are 12 inter-block exchanges, so 12 pairs of coordinate blocks Indi(x, y) are generated by using the security keys K1 and K2 to control the inter-block pixel exchange.
Step 4. Design a selectieve scrambling rule.\(B_{1}\leftrightarrow B_{11}\), \(B_{2}\leftrightarrow B_{10},B_{3}\leftrightarrow B_{11}\), \(B_{4}\leftrightarrow B_{10},B_{5}\leftrightarrow B_{7}\), \(B_{6}\leftrightarrow B_{8},B_{6}\leftrightarrow B_{14}\), \(B_{6}\leftrightarrow B_{16},B_{7}\leftrightarrow B_{13}\), \(B_{7}\leftrightarrow B_{15},B_{9}\leftrightarrow B_{11}\), \(B_{10}\leftrightarrow B_{12}\). The principle of pixel exchange between blocks is controlled by random coordinate blocks Indi(x, y). The scrambled image is \(P^{\prime }\).
Step 5. Use K1 and K2 to construct a global coordinate Qx and Qy, by which the whole \(P^{\prime }\) is scrambled and the pixel correlation is further reduced.
Step 6. Dynamic overlay diffusion: Firstly, K3, K4 and the scrambled image \(P^{\prime }\) are transformed into a matrix of 16 × 4096 size, and the 16 × 16 pixel block is taken as an overlay block. Then K3 and K4 are used alternatively to do XOR operation with \(P^{\prime }\), as shown in the Fig. 6, and the cipher-image Cp is finally obtained.
Where i denotes the location of the current block, i = 1,2,3,...256.
5 Experimental simulation and performance analysis
In this section, to prove the security of our scheme, the 256 × 256 traditional 8-bit grayscale images are used as the original images. Common security analyses, including statistical data and common attacks and so on, are also made and compared. Figure 7a, d and g are plain-images, (b) (e) (h) are cipher-images, (c) (f) (i) are decrypted images.
5.1 Key space
It is important for an image encryption algorithm to have a large enough security key space to resist the brute force attacks. Taking a 4-D hyperchaotic system as an example, only the initial value and parameters of the chaotic system are considered, if the length of every subkey is set to 16 decimals, the key space of our algorithm will be 1016×4 = 2192 > 2100 [40]. As a result, it is large enough to resist brute force attacks.
5.2 Information Entropy
In many image processing processes, information entropy is often used to measure the randomness of a noise map. Its entropy value H(m) can be calculated by the following equation [49]:
Where N is the gray level, p(mi) is the probability of mi. The entropy should ideally be 8 for a cipher-image with 256 gray levels, which indicates that the information is uncertain. Therefore, the information entropy of the encrypted image with high security should be close to 8. Table 4 lists the results of the information entropy of the cipher-image. Compared with the algorithms in reference [10,11,12], we can see that in terms of information entropy, the proposed scheme is better, and the pixel distribution of the encrypted image is more random.
5.3 Histogram analysis
The histogram is one of the important criteria for measuring the performance of an image encryption algorithm. It can describe the number of pixels corresponding to the gray level and the frequency of occurrence of each gray level, showing the distribution law of image pixels. As can be seen from Fig. 8, the histograms of all cipher-images are uniformly distributed, so the strong regularity of the pixels of plain-images is not brought into the cipher-images. This means that the attacker can’t get any useful statistical information from the cipher-image to attack the algorithm. The scheme can provide a good confusion effect for encrypted images.
5.4 Correlation of two adjacent pixels
Because of the characteristics of digital images, plain-images usually show a certain degree of correlation between two adjacent pixels. In order to assess the correlation between adjacent pixels,4000 pairs of adjacent pixels (xi, yi) are randomly selected from the plain-image and cipher-image, and their correlation coefficients are calculated.
Where x and y represent the gray value of two adjacent pixels, Correlation coefficient performances of the proposed scheme have been presented in Fig. 9 and Table 5, from which we can see that the correlation coefficients of the secret image have been reduced dramatically, while the correlation coefficients of the plain image are close to 1. Literature [45, 54, 55] provide a comparative algorithm. It is obvious that adjacent pixels of plain-image has strong correlation, while those of cipher-image have low correlation. This further proves that the scheme can effectively resist statistical attacks.
The correlation plots of ‘baboon’ image: a horizontal correlation of plain-image, b horizontal correlation of cipher-image, c horizontal correlation of decrypted image, d vertical correlation of plain-image, e vertical correlation of cipher-image, f vertical correlation of decrypted image, g diagonal correlation of plain-image, h diagonal correlation of cipher- image, i diagonal correlation of decrypted image
5.5 Peak signal-to-noise ratio
The difference between plain-image and cipher-image is measured by mean square error (MSE). MSE is defined as:
T represents the number of pixels in an encrypted image. The larger the value of MSE, the greater the difference between the encrypted image and the original image, and the better the image encryption effect.
Peak signal-to-noise ratio (PSNR) is a ratio between plain-image and cipher-image. PSNR is defined as:
max is the maximum pixel value of plain-image. In a good encryption algorithm, PSNR should be as low as possible, which indicates that the encrypted image are more randomness [41]. The MSE and PSNR values of the cipher-image are shown in Table 6, and references [10, 46, 51] are used for comparison.
5.6 Differential attack
Sometimes, attackers make a tiny change in the original plain image, and then encrypts both the original plain image and the changed plain image by the same encryption scheme, and try to find out the relationship between plain image and its cipher image by comparing the two encrypted images. The number of pixels change rate (NPCR) [26] and the unified average changing intensity (UACI) [15] are two criteria for analyzing differential attacks.
Where C1(i, j) and C2(i, j) are the two encrypted images mentioned above and D(i, j) is computed as
The ideal NPCR value and UACI value of the cipher-image are 99.6093% and 33.4653% respectively [56]. Table 7 lists the calculations of NPCR and UACI and compares them with those of other algorithms [10, 52, 53]. A conclusion can be drawn that the proposed algorithm has good property in resisting differential attacks.
5.7 Speed analysis
Speed of the encryption algorithm is also considered as a crucial factor. The proposed GAN key generation scheme reduces the time of key generation greatly, and the designed scrambling and diffusion algorithm also improves the encryption efficiency. Compared with other encryption schemes [51,52,53] in Table 8, our algorithm shows some advantages in speed. At the same time, due to the symmetric structure, the time cost of encryption and decryption are the same. Therefore, the proposed algorithm shows that it can can be used for real-time transportation.
5.8 Robustness against noise
Practically, some noise may be added through the transmission of encrypted images from the transmitter to the receiver. This can lead to an inevitable error, causing difficulties in decryption. A good encryption algorithm should be able to resist noise attacks. Salt and Pepper noise is added to the ciphered image of Boat, with different densities. The decrypted image of each case is shown in Fig. 10, which validates the efficiency of the system against noise attacks. Therefore, our algorithm has good robustness and can efficiently resist noise attacks.
5.9 Robustness against cropping
An effective cryptosystem must take information loss into account. To evaluate its robustness of resisting cropping attacks, parts with 64 × 64, 64 × 128 and 128 × 128, are deleted from the cipher-image ’boat’. As shown in Fig. 11a-d, the decrypted plain images continue to be meaningful. Hence, our method is robust against this kind of attacks.
Through a series of performance analysis and anti-attack detection, it can be seen from the key space, information entropy, histogram, adjacent pixel correlation, peak signal-to-noise ratio and speed test results that its security is considerable. From the test results of differential attack, cropping attack and noise attack, it has been found that its anti-attack ability has certain advantages over the similar literature.
6 Conclusion
This paper innovatively introduces LSGAN into image encryption. The good learning ability of LSGAN model is used to obtain the encryption key. Through NIST test, efficiency test, entropy and histogram analysis, it is proved that the random number generation scheme proposed in this paper can provide strong guarantee for image security, and expand the new idea of image security research. In order to improve the security of encrypted image, a scrambling method and a coverage diffusion algorithm are designed. The experimental results show that the scheme has a large key space and an average entropy of 7.9976. The anti-attack ability of the scheme is also verified by differential attack, cut attack and noise attack. In the future, we will improve the current model and other shortcomings, try to make the encrypting and decrypting parties generate keys synchronously, and reduce the number of keys transmitted on the network.
References
Abdulla AA (2015) Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography. University of Buckingham
Abdulla AA, Sellahewa H, Jassim SA (2014) Stego quality enhancement by message size reduction and fibonacci bit-plane mapping. in International Conference on Research in Security Standardisation. Springer
Babbage S et al (2009) ECRYPT yearly report on algorithms and keysizes
Brunk H, Rogers E, Hannigan BT (2002) Adjusting an electronic camera to acquire a watermarked image. Google Patents
Cao W, Mao Y, Zhou Y (2020) Designing a 2D infinite collapse map for image encryption. Signal Processing, pp 107457
Chai X et al (2019) A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput Appl 31(1):219–237
Chen J et al (2018) Exploiting self-adaptive permutation–diffusion and DNA random encoding for secure and efficient image encryption. Signal Process 142:340–353
De Bernardi M, Khouzani M, Malacaria P (2018) Pseudo-Random Number Generation Using Generative Adversarial Networks. in Joint European Conference on Machine Learning and Knowledge Discovery in Databases. Springer
Di X et al (2017) A semi-symmetric image encryption scheme based on the function projective synchronization of two hyperchaotic systems. PloS one 12(9):e0184586
El-Latif AAA, Niu X (2013) A hybrid chaotic system and cyclic elliptic curve for image encryption. AEU-Int J Electron Commun 67(2):136–143
Fathi-Vajargah B, Kanafchian M, Alexandrov V (2018) Image encryption based on permutation and substitution using Clifford Chaotic System and logistic map. J Comput 13(3):309–326
Farwa S et al (2019) Fresnelet approach for image encryption in the algebraic frame (Retraction of Vol 334, Pg 343, 2018). ELSEVIER SCIENCE INC 360 PARK AVE SOUTH, NEW YORK, NY 10010-1710 USA
Fouda JAE et al (2014) A fast chaotic block cipher for image encryption. Commun Nonlinear Sci Numer Simul 19(3):578–588
Gong L et al (2019) An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt Laser Technol 115:257–267
Ghebleh M, Kanso A, Noura H (2014) An image encryption scheme based on irregularly decimated chaotic maps. Signal Process Image Commun 29 (5):618–627
Hao-Xiang W et al (2010) Nonlinear feedback control of a novel hyperchaotic system and its circuit implementation. Chin Phys B 19(3):030509
Hua Z, Yi S, Zhou Y (2018) Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process 144:134–144
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Inf Sci 480:403–419
Huang C et al (2017) Context-aware generative adversarial privacy. Entropy 19(12):656
Jin C, Liu H (2017) A color image encryption scheme based on arnold scrambling and quantum chaotic. IJ Netw Secur 19(3):347–357
Ke Y et al (2019) Generative steganography with Kerckhoffs’ principle. Multimed Tools Appl 78(10):13805–13818
Liu Y, Tong X, Ma J (2016) Image encryption algorithm based on hyper-chaotic system and dynamic S-box. Multimed Tools Appl 75(13):7739–7759
Lin J et al (2020) An image encryption method based on logistic chaotic mapping and DNA coding. In: MIPPR 2019, Remote Sensing Image Processing, Geographic Information Systems, and Other Applications. International Society for Optics and Photonics
Liu H, Wang X (2010) Color image encryption based on one-time keys and robust chaotic maps. Comput Math Appl 59(10):3320–3327
Li X, Zhou C, Xu N (2018) A secure and efficient image encryption algorithm based on DNA coding and spatiotemporal chaos. IJ Netw Secur 20(1):110–120
Liu H, Kadir A, Sun X (2017) Chaos-based fast colour image encryption scheme with true random number keys from environmental noise. IET Image Process 11(5):324–332
Liang X et al (2017) Dual motion gan for future-flow embedded video prediction. In: Proceedings of the IEEE International Conference on Computer Vision
Liu J et al (2020) Recent advances of image steganography with generative adversarial networks. IEEE Access 8:60575–60597
Liu H et al (2018) Chaos based adaptive double-image encryption scheme using hash function and S-boxes. Multimedia Tools and Applications 77(1):1391–1407
Mahajan P (2020) Recent Advances in Generative Adversarial Networks: An Analysis along with its outlook. in 2020 10th International Conference on Cloud Computing. Data Science & Engineering, Confluence. IEEE
Mao Y, Chen G, Lian S (2004) A novel fast image encryption scheme based on 3D chaotic baker maps. Int J Bifurcat Chaos 14(10):3613–3624
Parker AT, Short KM (2001) Reconstructing the keystream from a chaotic encryption scheme. IEEE Trans Circ Syst I: Fund Theory Appl 48 (5):624–630
Peng J et al (2020) Image Encryption Based on Fractional-order Chen Hyperchaotic System. In: 2020 15th IEEE Conference on Industrial Electronics and Applications (ICIEA). IEEE
Qi-Ling HE et al (2017) A New Chaotic System and its Linear Feedback Synchronization. Journal of Chengdu University of Information Technology
Stinson DR, Paterson M (2018) Cryptography: theory and practice. CRC press
Schneier B (2007) Applied cryptography: protocols, algorithms, and source code in C. Wiley
Sreelaja N, Sreeja N (2016) An image edge based approach for image password encryption. Secur Commun Netw 9(18):5733–5745
Sun D et al (2017) A New Mimicking Attack by LSGAN. In: 2017 IEEE 29th International Conference on Tools with Artificial Intelligence (ICTAI). IEEE
Sen W et al (2007) Chaotic phenomena in Josephson circuits coupled quantum cellular neural networks. Chin Phys 16(9):2631
Seyedzadeh SM, Mirzakuchaki S (2012) A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process 92(5):1202–1215
SK NK, HS SK, Panduranga H (2012) Encryption approach for images using bits rotation reversal and extended hill cipher techniques. Int J Comput Appl 59(16)
Taiyong L et al (2017) A novel image encryption algorithm based on a Fractional-Order hyperchaotic system and DNA computing. Complexity 2017:1–13
Venkatesan R, Jakubowski M, Jayram TS (2003) Technique for watermarking an image and a resulting watermarked image. Google Patents
Wang X-Y, Li Z-M (2019) A color image encryption algorithm based on Hopfield chaotic neural network. Opt Lasers Eng 115:107–118
Wang X-Y, Gu S-X, Zhang Y-Q (2015) Novel image encryption algorithm based on cycle shift and chaotic system. Opt Lasers Eng 68:126–134
Wang X, Zhu X, Zhang Y (2018) An image encryption algorithm based on Josephus traversing and mixed chaotic map. IEEE Access 6:23733–23746
Wang X-Y et al (2018) A novel color image encryption scheme using DNA permutation based on the Lorenz system. Multimed Tools Appl 77 (5):6243–6265
Wang X et al (2018) KDGAN: Knowledge distillation with generative adversarial networks in Advances in Neural Information Processing Systems
Wang X, Gao S (2020) Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf Sci 539:195–214
Wang X, Wang Q, Zhang Y (2015) A fast image algorithm based on rows and columns switch. Nonlinear Dyn 79(2):1141–1149
Wei-Bin C, Xin Z (2009) Image encryption algorithm based on Henon chaotic system in 2009, International Conference on Image Analysis and Signal Processing. IEEE
Wu X et al (2017) A novel color image encryption scheme using rectangular transform-enhanced chaotic tent maps. IEEE Access 5:6429–6436
Xu L et al (2017) A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt Lasers Eng 91:41–52
Yang H et al (2010) A fast image encryption and authentication scheme based on chaotic maps. Commun Nonlinear Sci Numer Simul 15(11):3507–3517
Ye G, Huang X (2016) A secure image encryption algorithm based on chaotic maps and SHA-3. Secur Commun Netw 9(13):2015–2023
Ye G et al (2018) A Chaotic Image Encryption Algorithm Based on Information Entropy. Int J Bifurcat Chaos 28(01):1850010
Yin Q, Wang C (2018) A new chaotic image encryption scheme using breadth-first search and dynamic diffusion. Int J Bifurcat Chaos 28(04):1850047
Yin D, Yang Q (2018) GANS based density distribution privacy-preservation on mobility data. Security and Communication Networks 2018
Zhang M, Tong X (2015) A new algorithm of image compression and encryption based on spatiotemporal cross chaotic system. Multimed Tools Applx 74 (24):11255–11279
Zhang R, Dong S, Liu J (2019) Invisible steganography via generative adversarial networks. Multimed Tools Appl 78(7):8559–8575
Acknowledgements
This work was supported in part by China’s Natural Science Foundation Project(20190201188JC) of the Science and Technology Department of Jilin Province and China’s Science and Technology Project (JJKH20181137KJ) for the 13th Five-Year Plan of the Education Department of Jilin Province.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Man, Z., Li, J., Di, X. et al. A novel image encryption algorithm based on least squares generative adversarial network random number generator. Multimed Tools Appl 80, 27445–27469 (2021). https://doi.org/10.1007/s11042-021-10979-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10979-w