Abstract
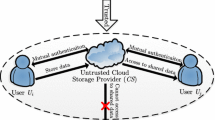
The ability of data owner in secure and efficient arbitrary data sharing with others is of great importance in the outsourced encrypted data on the cloud. To protect data confidentiality, data owner encrypts his files before storing information on the cloud. Data sharing schemes are used to share encrypted files with others. Guo et al.’s data sharing scheme in dynamic cloud storage is evaluated in this paper. We investigate its vulnerability against DoS and impersonation attacks. In this scheme, anyone can forge the authentication key and access any arbitrary set of files stored on the cloud. We present a new scheme to overcome the weaknesses. Moreover, we evaluate the security and efficiency of our scheme comparing to some related ones. The results indicate that the proposed scheme is suitable for data sharing in dynamic cloud storage.

Similar content being viewed by others
References
Akl SG, Taylor PD (1983) Cryptographic solution to a problem of access control in a hierarchy. ACM Trans Comput Syst (TOCS) 1(3):239–248
AlZain MA, Li AS, Soh B, Pardede E (2015) Multi-cloud data management using shamir’s secret sharing and quantum byzantine agreement schemes. Int J Cloud Appl Comput (IJCAC) 5(3):35–52
Atallah MJ, Blanton M, Fazio N, Frikken KB (2009) Dynamic and efficient key management for access hierarchies. ACM Trans Inform Syst Secur (TISSEC) 12 (3):18
Atawneh S, Almomani A, Al Bazar H, Sumari P, Gupta B (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in dwt domain. Multimed Tools Appl 76(18):18451–18472
Ateniese G, De Santis A, Ferrara AL, Masucci B (2012) Provably-secure time-bound hierarchical key assignment schemes. J Cryptol 25(2):243–270
Bayat M, Arkian HR, Aref MR (2015) A revocable attribute based data sharing scheme resilient to dos attacks in smart grid. Wirel Netw 21(3):871–881
Bayat M, Barmshoory M, Rahimi M, Aref MR (2015) A secure authentication scheme for vanets with batch verification. Wireless Netw 21(5):1733–1743
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: IEEE symposium on security and privacy, 2007. SP’07, IEEE, pp 321–334
Boneh D, Boyen X (2004) Short signatures without random oracles. In: International conference on the theory and applications of cryptographic techniques. Springer, pp 56–73
Boneh D, Lynn B, Shacham H (2004) Short signatures from the weil pairing. J Cryptol 17(4):297–319
Boneh D, Boyen X, Goh EJ (2005) Hierarchical identity based encryption with constant size ciphertext. In: Annual international conference on the theory and applications of cryptographic techniques. Springer, pp 440–456
Boneh D, Gentry C, Waters B (2005) Collusion resistant broadcast encryption with short ciphertexts and private keys. In: Annual international cryptology conference. Springer, pp 258–275
Boyen X, Waters B (2006) Anonymous hierarchical identity-based encryption (without random oracles). In: Annual international cryptology conference. Springer, pp 290–307
Chase M (2007) Multi-authority attribute based encryption. In: Theory of cryptography conference. Springer, pp 515–534
Chick GC, Tavares SE (1989) Flexible access control with master keys. In: Conference on the theory and application of cryptology. Springer, pp 316–322
Chu CK, Chow SS, Tzeng WG, Zhou J, Deng RH (2014) Key-aggregate cryptosystem for scalable data sharing in cloud storage. IEEE Trans Parallel Distributed Syst 25(2):468–477
Cui B, Liu Z, Wang L (2016) Key-aggregate searchable encryption (kase) for group data sharing via cloud storage. IEEE Trans Comput 65(8):2374–2385
Fan CI, Huang VSM, Ruan HM (2014) Arbitrary-state attribute-based encryption with dynamic membership. IEEE Trans Comput 63(8):1951–1961
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM conference on Computer and communications security. ACM, pp 89–98
Guo C, Zhuang R, Jie Y, Ren Y, Wu T, Choo KKR (2016) Fine-grained database field search using attribute-based encryption for e-healthcare clouds. Journal Med Syst 40(11):235
Guo C, Luo N, Bhuiyan MZA, Jie Y, Chen Y, Feng B, Alam M (2018) Key-aggregate authentication cryptosystem for data sharing in dynamic cloud storage. Futur Gener Comput Syst 84:190–199
Guo F, Mu Y, Chen Z (2007) Identity-based encryption: how to decrypt multiple ciphertexts using a single decryption key. In: International conference on pairing-based cryptography. Springer, pp 392–406
Guo F, Mu Y, Chen Z, Xu L (2007) Multi-identity single-key decryption without random oracles. In: International conference on information security and cryptology. Springer, pp 384–398
Gupta B, Agrawal DP, Yamaguchi S (2016) Handbook of research on modern cryptographic solutions for computer and cyber security. IGI global
Gupta S, Gupta BB (2018) Xss-secure as a service for the platforms of online social network-based multimedia web applications in cloud. Multimed Tools Appl 77 (4):4829–4861
Horwitz J, Lynn B (2002) Toward hierarchical identity-based encryption. In: International conference on the theory and applications of cryptographic techniques. Springer, pp 466–481
Jararweh Y, Al-Ayyoub M, Fakirah M, Alawneh L, Gupta BB (2017) Improving the performance of the needleman-wunsch algorithm using parallelization and vectorization techniques. Multimedia Tools Appl: 1–17
King WC, Hjelm B (2015) Centralized key management. US Patent 8,990,555
Li M, Yu S, Zheng Y, Ren K, Lou W (2013) Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans Parallel Distributed Syst 24(1):131–143
Li T, Liu Z, Li P, Jia C, Jiang ZL, Li J (2016) Verifiable searchable encryption with aggregate keys for data sharing in outsourcing storage. In: Australasian conference on information security and privacy. Springer, pp 153–169
Liu Z, Li T, Li P, Jia C, Li J (2018) Verifiable searchable encryption with aggregate keys for data sharing system. Futur Gener Comput Syst 78:778–788
Okamoto T, Takashima K (2015) Achieving short ciphertexts or short secret-keys for adaptively secure general inner-product encryption. Des Codes Crypt 77(2-3):725–771
Ometov A, Masek P, Malina L, Florea R, Hosek J, Andreev S, Hajny J, Niutanen J, Koucheryavy Y (2016) Feasibility characterization of cryptographic primitives for constrained (wearable) IoT devices. In: 2016 IEEE International conference on pervasive computing and communication workshops (PerCom Workshops). IEEE, pp 1–6
Patranabis S, Shrivastava Y, Mukhopadhyay D (2017) Provably secure key-aggregate cryptosystems with broadcast aggregate keys for online data sharing on the cloud. IEEE Trans Comput 66(5):891–904
Pournaghi SM, Zahednejad B, Bayat M, Farjami Y (2018) Necppa: a novel and efficient conditional privacy-preserving authentication scheme for vanet. Comput Netw 134:78–92
Sahai A, Waters B (2005) Fuzzy identity-based encryption. In: Annual international conference on the theory and applications of cryptographic techniques. Springer, pp 457–473
Sandhu RS (1988) Cryptographic implementation of a tree hierarchy for access control. Inf Process Lett 27(2):95–98
Sun Y, Liu KR (2004) Scalable hierarchical access control in secure group communications. In: INFOCOM 2004. Twenty-third annualjoint conference of the IEEE computer and communications societies, IEEE, vol 2, pp 1296–1306
Tong Y, Sun J, Chow SS, Li P (2014) Cloud-assisted mobile-access of health data with privacy and auditability. IEEE J Biomed Health Inform 18(2):419–429
Tzeng WG (2002) A time-bound cryptographic key assignment scheme for access control in a hierarchy. IEEE Trans Knowl Data Eng 14(1):182–188
Vahedi E, Bayat M, Pakravan MR, Aref MR (2017) A secure ecc-based privacy preserving data aggregation scheme for smart grids. Comput Netw 129:28–36
Wang S, Zhou J, Liu JK, Yu J, Chen J, Xie W (2016) An efficient file hierarchy attribute-based encryption scheme in cloud computing. IEEE Trans Inform Forensics Secur 11(6):1265–1277
Wang Z (2019) Provably secure key-aggregate cryptosystems with auxiliary inputs for data sharing on the cloud. Future Gen Comput Syst 93:770–776
Wang Z, Zhou L (2016) Leakage-resilient key-aggregate cryptosystem with auxiliary input. In: 2016 25th International conference on computer communication and networks (ICCCN), IEEE, pp 1–5
Waters B (2005) Efficient identity-based encryption without random oracles. In: Annual international conference on the theory and applications of cryptographic techniques. Springer, pp 114–127
Zhang Q, Wang Y (2004) A centralized key management scheme for hierarchical access control. In: IEEE global telecommunications conference, 2004. GLOBECOM’04., IEEE, vol 4, pp 2067–2071
Zhou R, Zhang X, Du X, Wang X, Yang G, Guizani M (2018) File-centric multi-key aggregate keyword searchable encryption for industrial internet of things. IEEE Trans Industrial Inform 14(8):3648–3658
Zhou Z, Huang D, Wang Z (2015) Efficient privacy-preserving ciphertext-policy attribute based-encryption and broadcast encryption. IEEE Trans Comput 64(1):126–138
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alimohammadi, K., Bayat, M. & Javadi, H.H.S. A secure key-aggregate authentication cryptosystem for data sharing in dynamic cloud storage. Multimed Tools Appl 79, 2855–2872 (2020). https://doi.org/10.1007/s11042-019-08292-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08292-8