Abstract
In this paper, the secrecy performance of cooperative heterogeneous networks with unreliable backhaul over Nakagami-m fading channels is investigated. To secure the proposed system, a friendly jammer is considered to confuse eavesdroppers. To transmit the signals from the source to the destination, a two-phase transmitter/relay selection scheme is proposed. The best transmitter is selected when the signal-to-noise ratio at the relays is maximized. In the second phase, the best relay is chosen when the jamming signal-to-interference-plus-noise ratio of the eavesdroppers is minimized. To investigate the system performance, closed -form expressions are derived for the secrecy outage probability, ergodic capacity and non-zero achievable secrecy rate. In order to gain an insight into the system, asymptotic analysis is also provided. The results show that the degree of cooperative transmission and backhaul reliability are key parameters in the system and these parameters determine the secrecy performance.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Due to the increasing wireless data traffic demand, future networks will become more dense and heterogeneous. In heterogeneous networks (HetNets), macro cells and small cells will be used to increase the capacity needed for this rise in traffic demand and to offload traffic. A backhaul link will connect these small cells with the core network. The traditional backhaul is wired and can ensure the connection. However, the cost of the deployment and maintenance is high, especially when a large number of small cells is needed to cover dense scenarios. Moreover, small cells may not need such a highly reliable backhaul as traditional macro cells do [27]. This is because small cells serve a lower traffic capacity than macro cells. In this way, wireless backhaul has emerged as an alternative and attractive approach due to its low cost and flexibility. However, wireless backhaul is not as reliable as its wired backhaul counterpart due to wireless channel impairments such as non-line-of-sight (nLOS) propagation and channel fading [10].
The reliability of the backhaul is an important factor in HetNets and research has been undertaken to investigate how the backhaul reliability can affect the system performance [2, 10,11,12,13,14,15, 19,20,21,22, 31]. In [2], the authors considered co-channel inter-cell interference (ICI) in HetNets with unreliable backhaul and coordinated multi-point (CoMP) transmission was considered to reduce the interference. In [12,13,14,15, 22, 31], the impact of unreliable backhaul on cooperative relay systems was investigated. The outage probability of finite-sized selective relaying systems with unreliable backhaul was studied in [15]. A cognitive network with unreliable backhaul was investigated in [21], and asymptotic analysis showed that performance was mainly decided by backhaul reliability. For all the research mentioned on unreliable backhaul connections, backhaul reliability is a key factor in the system performance. Therefore, in a HetNet context it is essential for us to investigate backhaul reliability.
Another aspect that cannot be ignored is security [5]. For a complete study in HetNets system, security needs to be considered. The traditional way to enhance security is deploying cryptographic techniques across upper layers. However, it consumes significant power to encrypt and decrypt data [25]. In addition, with the development of quantum computing, key schemes can be broken and the key infrastructure become insecure [30]. In recent years, physical layer security (PLS) has become increasingly popular to secure wireless communications [9, 26, 28]. The main idea of PLS is that the wireless channels are random and unpredictable, thus this can be exploited to keep the information confidential from eavesdroppers. Wyner proposed that when the main channel has better propagation conditions than the eavesdroppers’, the communication between legitimate users could be secure [29]. However, when the wiretap channel is better, the secrecy rate can even drop to zero [7]. Various PLS techniques have been investigated to tackle this problem and enhance the security of the main channel; one of the main techniques is using cooperative jamming to generate artificial noise to confuse eavesdroppers [1, 4, 6, 7, 16, 17, 23, 32]. In [6, 32], the authors considered PLS and energy harvesting with a friendly jammer, and the authors in [6] also proposed joint jammer and relay selection schemes. In related work [16], a jammer is assumed to be an energy constrained node with no power of its own and can harvest power from the source node, but cooperative relaying was not considered in this work. However, all of the research above ignored the reliability of the backhaul. As discussed an unreliable wireless backhaul results in poor performance. It is essential to consider backhaul reliability when studying PLS in a small cell HetNet contexts.
Research in [13, 14, 22, 31] has taken into account PLS in relay systems with unreliable backhaul. In [31], the authors studied PLS and energy harvesting. In [14], the authors studied PLS in full-duplex cooperative relay systems. In [13], multiple eavesdroppers that can wiretap information from relay and transmitters are considered in a finite-sized cooperative system. In [22], a friendly jammer was used to confuse eavesdroppers in single carrier systems.
Cooperative jamming in the presence of wireless backhaul over Nakagami-m fading channels has not been studied yet. In this research, we investigate the cooperative jamming in a small cells HetNet context with unreliable backhaul over Nakagami-m fading channel. In our system model, an outage occurs when the system is either not reliable or not secure, hence we assess the secrecy outage probability as a performance parameter. Our main contributions are summarized as below:
-
We investigate the secrecy performance of cooperative systems by exploiting cooperative relay and jamming signals in the presence of unreliable backhaul links between macro-cells and small-cells over Nakagami-m fading channels.
-
A two-phase transmitter/relay selection scheme is proposed. The achievable SNR at the relays is maximized by applying the best small cell transmitter selection in the first phase. The relay selection scheme is deployed in the second phase to minimize the instantaneous signal-to-interference-plus-noise ratio (SINR) at the eavesdroppers.
-
Analytical expressions to evaluate the secrecy outage probability, non-zero achievable secrecy rate, and ergodic capacity are derived in closed-form. The asymptotic secrecy expressions are also attained to gain full insights into the impact of backhaul reliability on the network secrecy performance in the high SNR regime.
-
The effect of the number of small-cell transmitters, relays, eavesdroppers and backhaul reliability on the system performance is investigated.
The remainder of the paper is organized as follows. System and channel models are described in Section 2. Derivation of the SNR distributions in the proposed system is obtained in Section 3. The closed-form expressions for outage probability, ergodic capacity and symbol error rate as well as the asymptotic analysis are carried out in Section 4, while numerical results are presented in Section 5. Finally, the paper is concluded in Section 6.
Notation:P[⋅] is the probability of occurrence of an event. For a random variable X, FX(⋅) denotes its cumulative distribution function (CDF) and fX(⋅) denotes the corresponding probability density function (PDF). max(⋅) and min(⋅) denote the maximum and minimum of their arguments, respectively.
2 System model
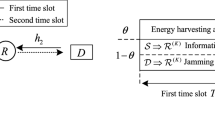
We consider a HetNet system with a macro base station, S, K small cells, T{1,⋯ ,K}, M relays, R{1,⋯ ,M}, a jammer, J, N eavesdroppers, E{1,⋯ ,N} and a destination, D, as shown in Fig. 1. S is connected to Tk via wireless backhaul. We assume that there is no direct link between Tk and D because of the poor channel condition. Tk sends information to D with the help of Rm. A single J transmits jamming signals in the system, and we assume that the jamming signals can be nulled out at D [6]. En wiretaps the information transmitted from Rm. All of the nodes are equipped with single antenna and operate in half-duplex. We assume that all the channels are Nakagami-m fading, and the channel power gains are gamma distributed. The cumulative distribution function (CDF) and probability density function (PDF) of the random variable X can be written as
Where Γ(⋅,⋅) is the incomplete gamma function [8, Eq. (8.352.6)].
Backhaul reliability is modeled as a Bernoulli process \(\mathbb {I}_k\) with success probability sk where \(\mathbb {P}(\mathbb {I}_{k^{*}}= 1)=s_{k}\) and \(\mathbb {P}(\mathbb {I}_{k^{*}}= 0)= 1-s_{k}\). This indicates that Tk is participating in the transmission if the message is successfully delivered over its dedicated backhaul with probability sk whereas it defers its transmission with probability 1 − sk.
We assume the global channel state information (CSI) is available, which is a common assumption in PLS [22]. The CSI of the eavesdroppers can be known when eavesdroppers are active in the network and their status can be monitored [3].
In the first hop, the received signals at Rm are of the form
where \(\mathcal {P}_{t}\) is the transmit power at Tk and \(h_{T_k R_m}\) is the channel coefficient of the link Tk − Rm, x is the unit power transmitted symbol and z is the complex additive white Gaussian noise (AWGN) with zero mean and variance σ, i.e., z ∼ CN(0,σ). The path loss component corresponding to \(h_{T_{k} R_{m}}\) is denoted as \(\alpha _T^{k,m}\), respectively.
In the second hop, the received signals at D are of the form
where \(\mathcal {P}_{r}\) is the transmit power at relays and \(h_{R_m D}\) is the channel coefficient of the link Rm − D. The path loss component corresponding to \(h_{R_m D} \) is represented by \(\alpha _D^{m}\), respectively.
Similarly, the received signals at E are of the form
where \(\mathcal {P}_{j}\) is the transmit power at the jammer, \(h_{R_m E_n}\) is the channel coefficient of the link Rm − En and \(h_{J E_n}\) is the channel coefficient of the link J − En. The path loss component corresponding to \(h_{R_m E_n}\) and \(h_{J E_n}\) are denoted as \(\alpha _E^{m,n}\) and \(\alpha _J^{n}\), respectively.
We assume that the unreliable backhaul links are independent from the indices of the K transmitters, i.e., sk = s,∀k.
3 SNR distributions
In this section, SNR distributions are derived firstly which are necessary for system secrecy performance analysis in the next section.
From Eq. 3, the SNR from Tk and Rm can be given as
where \(\widetilde {\alpha }_R = \frac {\mathcal {P}_{t} \alpha _T^{k,m}} {\sigma _n^2}\). λk,m ∼Ga(mR,𝜃R).
Similarly, according to Eqs. 4 and 5, the SNR between Rm and D and the SINR between Rm and En can be obtained as
where \(\widetilde {\alpha }_D=\frac {\mathcal {P}_{r} \alpha _D^{m}} {\sigma _n^2}\), \(\widetilde {\alpha }_E = \frac {\mathcal {P}_{r} \alpha _E^{m,n}}{\sigma _n^2}\) and \(\widetilde {\alpha }_J = \frac {\mathcal {P}_{j} \alpha _J^{n}}{\sigma _n^2}\). \({\lambda _{D}^{m}} \sim \text {Ga}(m_{D},\theta _{D})\), λm,n ∼Ga(mE,𝜃E) and \({\lambda _{J}^{n}} \sim \text {Ga}(m_{J},\theta _{J})\).
In order to achieve a high performance of the considered system, our selection scheme is to maximize the performance at the relays and destination and minimize the performance at the eavesdroppers.
3.1 Distribution of the link \(T_{k^{*}}-R_{m}\)
In the first hop, each relay selects a small cell that can achieve the best performance of the link Tk − Rm. In this way, the best small cell is selected as
Corresponding CDF of \(SNR_{T_{K^{*}} R_{m}}\) is given as
The proof is given in Appendix A.
3.2 Distribution of the link \(R_{m} -E_{n^{*}}\)
In the second hop, the eavesdropper is selected when the SINR between Rm and En is maximum to enhance its performance,
Corresponding CDF of \(SINR_{R_{m} E_{n^{*}}}\) can be derived according to Appendix B.
3.3 Distribution of the link \(R_{m^{*}}-E_{n^{*}}\)
The relay is selected when the SNR of the link \(R_{m}-E_{n^{*}}\) is minimized. It can be formulated as
corresponding PDF of \(SINR_{R_{m^{*}} E_{n^{*}}}\) can be derived according to Appendix C and corresponding CDF of \(SINR_{R_{m^{*}} E_{n^{*}}}\) can be obtained as
3.4 Distribution of the end-to-end SNR
The relays use decode-and-forward (DF) protocol for its high system performance. This is because the interference is lower in DF protocol compared with amplify-and-forward (AF) protocol [31]. In this way, the end-to-end SNR of the considered system at the destination is given by
where \(SNR_{T_{k^{*}} R_{m^{*}}}\) is the SNR from the selected small cell transmitter to the selected relay, and \(SNR_{R_{m^{*}} D}\) is the SNR from the selected relay to the destination.
Corresponding CDF of the end-to-end SNRDF can be obtained as
According to Eq. 15 and by applying binomial and multinomial theorems, the CDF of the end-to-end SNR obtained at D can be given as
4 Secrecy performance analysis
This section derives the performances of secrecy outage probability, non-zero achievable secrecy rate and ergodic capacity utilizing the SNR distributions obtained in the previous section. Towards deriving these performances, secrecy rate is required to be defined first. Secrecy capacity is equal to the difference between main channel and the wiretap channel, which is given by [31]
where [x]+ = max(x,0). In addition, log2(1 + SNRDF) is the instantaneous capacity obtained at D from selected relay and \(\log _{2} (1+ SNR_{R_{m^{*}} E_{n^{*}}})\) is the instantaneous capacity of the channel from selected relay to the selected eavesdropper.
4.1 Secrecy outage probability
The secrecy outage probability is introduced to evaluate the system security and it is defined as the probability that the instantaneous secrecy capacity is less than a positive target secrecy rate 𝜃 [31], i.e.,
Substitute (15) and (32) into (18), and with the help of [24, Eq. (2.3.6.9)], [8, Eq. (9.211.4)], the expression for secrecy outage probability can be given as (19).
where
______________________________________________________________________________________________
and \(\beta = {\sum }_{t = 0}^{m_{R}-1}t \), Υ = 22𝜃, \( \epsilon = \frac {\theta _E}{\theta _J}\)\(J = \frac {M N}{(\theta _J)^{m_{J}} (m_{J}-1)!}\).
In addition, \(\widehat {\sum \limits _{N,n,m_{E}}}\), \(\widetilde {\sum \limits _{E}}\), \(\widetilde {\sum \limits _{D}}\) are the shorthand notations of
______________________________________________________________________________________________
To provide full insights into the impact of unreliable backhaul connections, the asymptotic expression for the secrecy outage probability can be obtained as Eq. 20.
______________________________________________________________________________________________where
______________________________________________________________________________________________
and \(\tilde {\beta } = {\sum }_{t = 0}^{m_{R}-1}t \omega _{t + 1}\), \(\tilde {\Phi } = \frac {k}{\theta _R}\), \( \widetilde {\sum \limits _{D^{\infty }}} ={\sum }_{k = 1}^{K} {\sum }_{\omega _{1},...,\omega _{m_{R}}}^{k}\)\(\binom {K}{k} \left (\frac {k!}{\omega _{1}!...\omega _{m_{R}}!} \right ) \frac { (-1)^{k-1} s^{k}} {{\prod }_{t = 0}^{m_{R}-1} \left (t!(\theta _R)^{t} \right )^{\omega _{t + 1}}}\)
4.2 Probability of non-zero secrecy rate
The probability of non-zero secrecy rate is the probability that secrecy rate is more than zero, or another way \(SNR_{T_{k^{*}}D}\) is higher than \(SINR_{R_{m^{*}} E_{n^{*}}}\). The probability of none-zero secrecy rate can be obtained as [31]
Using Eqs. 15 and 32 and with the help of [24, Eq. (2.3.6.9)]. The closed-form expression for the probability of non-zero achievable secrecy rate is given as, Eq. 22.
where
______________________________________________________________________________________________
To investigate the asymptotic behavior of the probability of non-zero achievable secrecy rate in high SNR regime, the asymptotic expression is given as Eq. 23.
where
______________________________________________________________________________________________
4.3 Ergodic capacity
The ergodic capacity is defined as the average secrecy rate averaged over all the SNR distributions.
Ergodic capacity (nat/s/Hz) is expressed as [31]
Substitute (13) and (15) into (24), and with the help of [24, Eq. (2.3.6.9)], [18, Eq. (1.1.1)], [18, Eq. (2.6.2)], [18, Appendix A7], ergodic capacity can be evaluated as Eq. 25.
______________________________________________________________________________________________
To gain the full insights of the system, the asymptotic ergodic capacity is given as Eq. 26.
______________________________________________________________________________________________
where \(H_{p q}^{m n} \left [ . \right ]\) denotes the Fox H-function [18, Eq. (1.1.1)].
5 Numerical results
In this section, numerical results along with simulations are shown for the analysis carried out on the proposed system. The threshold of secrecy outage probability is fixed at 𝜃 = 1 bits/s/Hz. The binary phase-shift keying (BPSK) modulation is adopted in the simulations with transmission block size S = 64 symbols. In figures, “Sim” represents the simulation results, “Ana” represents the analytical results and “Asy” represents the asymptotic analysis results. We investigate the network performance with various parameters to examine the effects of the degrees of cooperative transmission and backhaul reliability.
5.1 Secrecy outage probability
Fig. 2 investigates the secrecy outage probability for various M and N. The network parameters are set as K = 3,s = 0.998,{mR,mE,mJ,mD} = {2,2,2,3}, and {𝜃R,𝜃E,𝜃J} = {10,10,10} dB. We can observe that the number of relays and eavesdroppers strongly affects the secrecy outage probability. Specifically, when N = 1, the secrecy outage probability decreases when the number of relay increases, thus achieving a better system performance. By contrast, when M = 1, the secrecy outage probability increases when the number of eavesdropper increases. We can also observe that our results approach asymptotic results in the high SNR regime.
Figure 3 plots the secrecy outage probability with various K and s. We set the parameters as M = 2,N = 1,{mR,mE,mJ,mD} = {2,2,3,2}, and {𝜃R,𝜃E,𝜃J} = {10,10,10} dB. We can observe from the figures that when K = 1, the secrecy outage probability decreases when the backhaul reliability gets higher. If the system has more reliable backhaul, it performs better.
In addition, when s = 0.95 and the number of small-cell transmitters increases from K = 1 to K = 3, the secrecy outage probability decreases due to the increased received signal power at D.
Figure 4 shows the effects of dense networks on secrecy outage probability versus number of relays M with K = 10,s = 0.998,{mR,mE,mJ,mD} = {2,2,2,3},and {𝜃R,𝜃E,𝜃J,𝜃D} = {10,10,10,10} dB. We can observe that for all N = {1,5,10}, secrecy outage probability decreases when there are more relays due to the cooperative communication. In addition, with the increase of N from N = 1 to N = 10, the secrecy outage probability increases. This is because the achievable capacity in the wiretap channels gets higher.
5.2 Ergodic capacity
Figures 5 and 6 depict the effect of the number of small-cell transmitters, the number of relays and eavesdroppers and backhaul reliability on the ergodic capacity. Parameters are the same in the corresponding figures of the ergodic capacity and secrecy outage probability. Effects of the degree of cooperative transmission and reliability of backhaul are complementary on ergodic secrecy rate and secrecy outage probability. When secrecy outage probability decreases, the ergodic secrecy rate would increase. We can observe in the figures that when N = 1, the ergodic capacity increases when the number of relay grows. Also, when M = 1, ergodic capacity decreases when the number of eavesdroppers increases. In addition, when K = 1, the ergodic capacity increases when the backhaul is more reliable, and when s = 0.95, the ergodic capacity increases when the number of small-cell transmitters increases.
5.3 Non-zero achievable secrecy rate
Figures 7 and 8 show the same performances as of secrecy outage probability and ergodic secrecy rate with the same parameters, correspondingly. The observations are similar in all the cases.
In the figure, simulation results match well with the numerical results, thus, validating the analysis presented in the paper.
6 Conclusions
This paper investigates the secrecy performance of cooperative heterogeneous networks with unreliable backhaul links. A two phase transmitter/relay selection scheme was proposed to maximize the SNR at the relays and minimize the SINR at the eavesdroppers. Closed-form expressions are derived and asymptotic expressions are also provided. Results show that when the number of small-cell transmitters and relays increases, the system can achieve a better performance. However, the increase of eavesdroppers can significantly degrade the system performance. Moreover, backhaul reliability is a key parameter for the improvement of secrecy performance.
References
Akitaya T, Asano S, Saba T (2014) Time-domain artificial noise generation technique using time-domain and frequency-domain processing for physical layer security in mimo-ofdm systems. In: 2014 IEEE international conference on Communications workshops (ICC). IEEE, pp 807–812
Ali MS, Synthia M (2015) Performance analysis of jt-comp transmission in heterogeneous network over unreliable backhaul. In: 2015 international conference on Electrical engineering and information communication technology (ICEEICT). IEEE, pp. 1–5
Dong L, Han Z, Petropulu AP, Poor HV (2010) Improving wireless physical layer security via cooperating relays. IEEE Trans Signal Process 58(3):1875–1888
El Shafie A, Mabrouk A, Tourki K, Al-Dhahir N, Hamila R (2018) A secret-key-aided scheme to secure transmissions from single-antenna rf-eh source nodes. IEEE Wirel Commun Lett 7(2):238–241
Hieu TD, Duy TT, Kim BS (2018) Performance enhancement for multihop harvest-to-transmit wsns with path-selection methods in presence of eavesdroppers and hardware noises. IEEE Sensors J 18(12):5173–5186
Hoang TM, Duong TQ, Vo NS, Kundu C (2017) Physical layer security in cooperative energy harvesting networks with a friendly jammer. IEEE Wirel Commun Lett 6(2):174–177
Hui H, Swindlehurst AL, Li G, Liang J (2015) Secure relay and jammer selection for physical layer security. IEEE Signal Process Lett 22(8):1147–1151
Jeffrey A, Zwillinger D (2007) Table of integrals, series, and products. Academic Press, New York
Jiang X, Zhong C, Chen X, Duong TQ, Tsiftsis TA, Zhang Z (2016) Secrecy performance of wirelessly powered wiretap channels. IEEE Trans Commun 64(9):3858–3871
Khan TA, Orlik P, Kim KJ, Heath RW (2015) Performance analysis of cooperative wireless networks with unreliable backhaul links. IEEE Commun Lett 19(8):1386–1389
Kim KJ, Khan TA, Orlik PV (2017) Performance analysis of cooperative systems with unreliable backhauls and selection combining. IEEE Trans Veh Technol 66(3):2448–2461
Kim KJ, Orlik PV, Khan TA (2016) Performance analysis of finite-sized co-operative systems with unreliable backhauls. IEEE Trans Wirel Commun 15(7):5001–5015
Kim KJ, Yeoh PL, Orlik PV, Poor HV (2016) Secrecy performance of finite-sized cooperative single carrier systems with unreliable backhaul connections. IEEE Trans Signal Process 64(17): 4403–4416
Liu H, Kim KJ, Tsiftsis TA, Kwak KS, Poor HV (2017) Secrecy performance of finite-sized cooperative full-duplex relay systems with unreliable backhauls. IEEE Trans Signal Process 65(23):6185–6200
Liu H, Kwak KS (2017) Outage probability of finite-sized selective relaying systems with unreliable backhauls. In: 2017 international conference on Information and communication technology convergence (ICTC). IEEE, pp 1232–1237
Liu W, Zhou X, Durrani S, Popovski P (2016) Secure communication with a wireless-powered friendly jammer. IEEE Trans Wirel Commun 15(1):401–415
Liu Y, Wang L, Duy TT, Elkashlan M, Duong TQ (2015) Relay selection for security enhancement in cognitive relay networks. IEEE Wirel Commun Lett 4(1):46–49
Mathai AM, Saxena RK (1978) The h function with applications in statistics and other disciplines
Nguyen HT, Duong TQ, Dobre OA, Hwang WJ (2017) Cognitive heterogeneous networks with best relay selection over unreliable backhaul connections. In: 2017 IEEE 86th Vehicular technology conference (VTC-fall). IEEE, pp 1–5
Nguyen HT, Duong TQ, Hwang WJ (2017) Multiuser relay networks over unreliable backhaul links under spectrum sharing environment. IEEE Commun Lett 21(10):2314–2317
Nguyen HT, Ha DB, Nguyen SQ, Hwang WJ (2017) Cognitive heterogeneous networks with unreliable backhaul connections. Mobile Networks and Applications:1–14
Nguyen HT, Zhang J, Yang N, Duong TQ, Hwang WJ (2017) Secure cooperative single carrier systems under unreliable backhaul and dense networks impact. IEEE Access 5:18310–18324
Nguyen VD, Duong TQ, Shin OS, Nallanathan A, Karagiannidis GK (2017) Enhancing phy security of cooperative cognitive radio multicast communications. IEEE Trans Cogn Commun Netw 3(4):599–613
Prudnikov A, Brychkov I, Marichev O (1998) Integrals and Series, vol. 1: Elementary functions. Gordon and Breach Science Publishers, New York
Rodríguez LJ, Tran NH, Duong TQ, Le-Ngoc T, Elkashlan M, Shetty S (2015) Physical layer security in wireless cooperative relay networks: State of the art and beyond. IEEE Commun Mag 53(12):32–39
Sheng Z, Tuan HD, Nasir AA, Duong TQ, Poor HV (2018) Power allocation for energy efficiency and secrecy of wireless interference networks. IEEE Transactions on Wireless Communications
Siddique U, Tabassum H, Hossain E, Kim DI (2015) Wireless backhauling of 5g small cells: challenges and solution approaches. IEEE Wirel Commun 22(5):22–31
Wang L, Kim KJ, Duong TQ, Elkashlan M, Poor HV (2015) Security enhancement of cooperative single carrier systems. IEEE Trans Inf Forensic Secur 10(1):90–103
Wyner AD (1975) The wire-tap channel. Bell Labs Techn J 54(8):1355–1387
Yang M, Guo D, Huang Y, Duong TQ, Zhang B (2016) Physical layer security with threshold-based multiuser scheduling in multi-antenna wireless networks. IEEE Trans Commun 64(12):5189–5202
Yin C, Nguyen HT, Kundu C, Kaleem Z, Garcia-Palacios E, Duong TQ (2018) Secure energy harvesting relay networks with unreliable backhaul connections. IEEE Access 6:12074– 12084
Zhou X, McKay MR (2010) Secure transmission with artificial noise over fading channels: Achievable rate and optimal power allocation. IEEE Trans Veh Technol 59(8):3831–3842
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A
Since all the channels follow Nakagami-m fading, and the CDF and PDF can be found in Eqs. 1 and 2. The CDF and PDF of \(SNR_{T_{k} R_{m}}\) can be written as
where δ(.) denotes the Dirac delta function. Since the best transmitter T\(_{k^{*}}\) is selected, the CDF of \(SNR_{T_{k^{*}} R_{m}}\) can be given as
After some simple manipulations, we can derive (10).
Appendix B
The CDF of \(SINR_{R_{m} E_{n}}\) can be obtained as
Since the frequency selective fading channels between the particular relay to the eavesdroppers are independent and identically distributed, the CDF of the \(SINR_{E_{n^{*}}}\) is given as
Appendix C
We first derive the PDF of \(SINR_{R_{m} E_{n^{*}}}\),
Since (12), we derive the PDF of \({SINR_{R_{m^{*}} E_{n^{*}}}}\),
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Yin, C., Garcia-Palacios, E. Performance Analysis for Secure Cooperative Systems Under Unreliable Backhaul Over Nakagami-m Channels. Mobile Netw Appl 24, 480–490 (2019). https://doi.org/10.1007/s11036-018-1159-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1159-z