Abstract
This research work analyzes economic alternatives for the provision of ultra-reliable low latency communication (URLLC) and enhanced mobile broadband (eMBB) services by mobile network operators over the same fifth-generation (5G) network. Two business models are proposed to provide the two services to end users. Concretely, a monopoly is a single operator who offers both services, and a duopoly is two different operators that share network resources and offer one service each. In addition, two types of network scenarios for resource sharing are studied. Specifically, a shared network (SN) is a type of network scenario allowing resources to be shared between the two services without priority. A differentiated network (DN) is a type of network scenario that allows resources to be shared between the two services with a priority to URLLC service using network slicing (NS). Regarding the economic aspects, the incentive is modeled through the user’s utility and the operator’s benefit. At the same time, game theory is used to model the strategic interaction between users and operators, and queuing theory is used to model the interaction between the two services. We conclude that the monopoly social welfare (SW) is closer to the SW of the social optimum than the duopoly SW. In addition, the DN scenario to offer the services through NS is more suitable than the SN scenario since the point of view of service prices, user utilities, and operator benefit.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In recent years, the fifth-generation (5G) networks have reinvented the telecommunications industry with new use cases, business models, and organizations emerging in response to technological and business changes further driven by the deployment of Cloud Computing services, the growth of the Internet of Things (IoT) and artificial intelligence supporting the digital transformation of enterprises and industries [1,2,3].
The 5G network differs from previous wireless generations because it connects things to people, the Internet, and other things; previous generations were designed to connect people to the Internet, as described in [4]. In this context, the International Telecommunication Union (ITU) defines that 5G supports three broad categories of applications to enable the use cases described above: massive Machine-Type Communication (mMTC), URLLC, and eMBB [5, 6]. Specifically, as described in [7], URLLC is a key feature of 5G networks that enables the delivering extraordinarily reliable and low latency communication services. It is designed to support applications that require extremely high reliability and low latency, such as autonomous vehicles, industrial automation, and virtual reality [8,9,10]. Likewise, an essential technology to support some 5G network services is eMBB. eMBB enables high data rate communication and supports various applications, including video streaming, online gaming, and virtual reality [5]. To support URLLC and eMBB, 5G networks use various technologies and techniques, including advanced coding and modulation schemes, highly efficient resource allocation algorithms, and advanced multiple-input multiple-output (MIMO) techniques. In addition, 5G networks use NS to provide a high degree of flexibility and customization, allowing different applications and services to be supported on the same network [11]. Overall, the combination of URLLC and eMBB enables 5G networks to support a wide range of applications and services with different requirements for reliability, latency, and data rate.
This makes 5G networks highly versatile and able to support a wide range of use cases, applications, and business models. This work focuses on two business models called monopoly and duopoly, i.e., in the monopoly business model, a single operator offers URLLC and eMBB services. In the duopoly business model, two different operators offer one service each. Two network scenarios are analyzed for both business models. Firstly is the SN scenario, where URLLC and eMBB services share network resources without priority per service. Secondly is the DN scenario, where URLLC and eMBB services share network resources with a priority per service using NS.
In this regard, the provision of services through a shared network infrastructure enabled by the 5G network is analyzed in the first model without NS, and the second model is considered NS. Our hypothesis focuses on the strategic interaction between users and operators based on two business models: monopoly and duopoly. In particular, we characterize the conditions to determine which business models benefit users and the operator offering URLLC and eMBB services. We propose two business models to test the above described and analyze the proposal using a strategic game. These models capture the user utilities, the operators’ revenues, and the strategic interaction between the users’ subscription decisions and the operators’ pricing decisions. Finally, we compare the business models with the social optimum. The main contributions of this paper are the following:
-
Two business models are proposed to provide URLLC and eMBB services over the same network.
-
In the business models proposed, the strategic interaction between users and each operator is analyzed through Game Theory.
-
The equilibrium outcome of each business model is analyzed in terms of the most relevant parameters: delay sensitivity, packet transmission, service priority, and the pay-per-user price of a service.
-
We demonstrate that differentiated use of network resources is economically viable, allowing operators to coexist and interaction between URLLC and eMBB services to proceed normally.
-
The conditions are established under which the business models are feasible.
In the analysis, we apply queue theory and microeconomics concepts in formulating business models and modeling user-perceived quality of service (QoS). Game theory is used in the paper to compare monopoly and duopoly models. One branch of economic theory is game theory, which aims to help understand decision-makers’ interactions [12]. It is widely used in telecom business models to determine the economic incentives of agents, whether users or providers [13, 14], in telecom and computer networks to optimize routing and resource allocation [15, 16] and resource sharing [16, 17]. Our work analyzes business models proposed based on game theory, and optimization schemes that are part of the NS taxonomy described in [18, 19]. Moreover, our work contributes to the key points and main open questions related to NS and 5G services research [20, 21], so it belongs to a latter trend and shares this characteristic with some of the works referred to in the following sub0.
1.1 Related Work
This work is inspired by the different use cases developed in 5G networks to support the growing demand for high-speed data transfer, low-latency communication, and the massive number of connected devices (URLLC, eMBB, and mMTC), as described [5, 6]. In this context, some novel business models based on 5G use cases and supported by NS have been developed and addressed in several studies.
Specifically, many recent works study business models for URLLC, eMBB and mMTC and classify them into three main categories. The first category, Monetization, and Pricing, described in [22], focuses on understanding how service providers can monetize URLLC, eMBB, and mMTC services, including pricing strategies such as pay-per-use and subscription-based models. They also explore revenue-sharing models, such as shared spectrum and NS. For example, the authors in [23] analyze the monetization question to the residential user’s segment and address the use of 5G NS capability and appropriate pricing strategies. References [22, 24] analyze price and service competition under certain cost modeling assumptions, server capacity, and competition prices where firms compete regarding their prices under service levels. Previous studies have shown the economic feasibility of URLLC, eMBB, and mMTC-based service provisioning. In our paper, we analyze URLLC and eMBB-based service provisioning from a technical and economic point of view.
The second category, Network Deployment, and Optimization, described in [25], focuses on understanding the optimal deployment of networks to support URLLC, eMBB, and mMTC services, including edge computing and NS. They also explore the challenges and solutions for deploying and optimizing networks to support these services. For example, the authors in [26, 27] analyze the resources division and resource division mechanism of the 5G communication network to support different business models. Finally, Security and Interoperability, described in [28], focuses on understanding the security challenges and solutions for URLLC, eMBB, and mMTC services, including blockchain and other secure communications technologies. They also examine the issues related to interoperability and standardization for URLLC, eMBB, and mMTC services. For example, the authors in [29] analyze the blockchain-enabled SDN framework for securing transactions that use Software Defined Network (SDN) and Network Function Virtualization (NFV) to support different model business issues. The above studies have shown the technical feasibility of deploying business models based on URLLC, eMBB, and mMTC. At the same time, in our paper, we analyze the technical and economic feasibility of the business models based on URLLC and eMBB.
The requirements described above to be met by the 5G network are based on its leading enabler: NS [30]. Specifically, NS refers to partitioning a physical network into multiple virtual networks, each designed and optimized for a specific application/service [31]. In this regard, the authors in [32] indicate that network fragmentation enables value creation for verticals, application providers, and third parties that lack physical network infrastructure by offering radio, network, and cloud resources, allowing for customized network operation and true service differentiation. The framework of queuing theory in [33], studies the effects of queuing delay and offers a pricing methodology that considers the value of the user’s time. Also, in [33], the authors study the effects of queuing delays and related costs on the management and control of IT resources. Besides, in [34, 35], the authors analyze the application of priority queuing (PQ) to pricing to maximize network operators’ revenues. In the game theory framework, in [34], the problem of maximizing operator revenue, Nash equilibrium, was considered the solution. In [36, 37], the authors propose the game theory to solve the profit maximization problem of a set of independent mobile virtual network operators (MVNO) that request slices from a mobile network operator (MNO).
Concerning described above, in previous studies, we have carried out several investigations in the line of research on the network economy. In [38], we have used priority queuing to establish a differentiation between services; to do so, we have considered the Discriminatory Processor Sharing (DPS) discipline for two service models with different QoS and determine the prices that maximize the provider’s profit. As discussed in this study, the above studies represent an association between price and QoS to obtain user benefits. However, in this paper, we analyze pricing through a non-priority queue where URLLC and eMBB services with different QoS are served with the same priority and a two-priority queue where the URLLC service has a high priority. While the eMBB service has a low priority, depending on the delay dependency. In the game theory framework, in [39], we have analyzed service provision to a homogeneous traffic profile through a priority queue where a primary operator owns the resources. A second operator can alternatively access said resources; they use the Nash equilibrium to solve that. While in this paper, two types of traffic profiles are analyzed through a two-priority queue; the priority assignment is based on the QoS characteristics of each service, and the process is solved using also Nash equilibrium. In the same way, in some of our previous studies, such as [40,41,42], game theory to solve different scenarios is analyzed. These works apply game theory to the analysis of service provision in a competitive environment within the context of telecommunications. However, this paper differs significantly from our previous studies, as we propose two network scenarios. The first is the SN scenario, in which URLLC and eMBB services share resources. The second is the DN scenario, where resources are allocated to URLLC and eMBB services using NS.
Additionally, in [3], the authors discussed a detailed overview of the 5G network, especially business models. In this paper, we address a new business model not considered in [3], which is part of the different business models that can be proposed from 5G networks.
This paper is closely linked to the content discussed in reference [41], where the provision of services for machine-type communications (MTC) and human-type communications (HTC) is presented using a two-priority queue model. The previous work employs game theory to characterize two distinct games. The first game involves sensors deciding to subscribe to the network operator for uploading sensing data, considering a utility function related to average service time and the operator’s price. The second game focuses on users subscribing to the service based on provider sensor data. Reference [41] explicitly explores game theory models to analyze the strategic interaction between users’ subscriptions and the network capacities decision of the Mobile Network Operator (MNO). In this paper, our analysis considers 5G network concepts such as NS for resource sharing. It is different from the analysis in [41]. Specifically, in this paper, we study two business models, monopoly and duopoly. In each business model, two scenarios and their characteristics are considered. That is, whether a single operator offers the two services or two different operators each offer one service, or whether we use a network that allows resource sharing between the two services or another type of network that allocates resources per service using NS. In addition, our analysis considers URLLC and eMBB services defined in 5G networks that have very different QoS requirements.
The remainder of this paper is organized as follows. In Sect. 2, we describe in detail the network, the business model, the game model, the social optimum model, as well as the utility of each player and the pricing scheme. In Sect. 3, we analyze and solve the subscription and pricing strategies of the different models. In Sect. 4, we show and discuss the results. Finally, in Sect. 5, we present the conclusions.
2 Model Description
In this section, we describe the business models and the network models proposed.
The two business models are denominated as monopoly, where a single operator offers URLLC and eMBB services, and duopoly, where two operators offer one service each (URLLC or eMBB).
The two network models are a 5G network model without NS, where network resources are shared between both services without NS, and a 5G network model with NS, where network resources are shared between services but assigned a higher priority to the URLLC service.
We refer to the first network model as the shared network (SN) scenario and the second as the differentiated network (DN) scenario. Both scenarios are analyzed in each business model, as shown in Fig. 1.
On the other hand, to determine whether the monopoly or duopoly is better or worse, we contrast their results with the results of the model of the social optimum from the point of view of social welfare. This model, which constitutes a benchmark, is developed in Sect. 2.4.
Finally, in Fig. 2, we present a specific notation to identify the business model, scenery, and type of service analyzed in this article. In addition, we analyze the strategic interaction between users and operators. Simultaneous provision of URLLC and eMBB services is studied, allowing operators to coexist and interaction between services to take place, usually using concepts from queuing theory [43], game theory [44], and microeconomics in telecommunications.
A summary of the notation we use in this article is shown in Table 1.
2.1 System Model
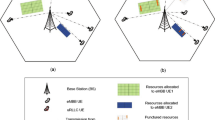
We model the entire network as an M/M/1/\(\infty\) queue. This type of modeling is a simplification justified by the need to obtain manageable expressions for the utility of the network users. The URLLC and eMBB user services are modeled as independent Poisson packet sources with an individual packet generation rate \(\lambda _{u}\) and, \(\lambda _{ej}\) respectively. As shown in Fig. 3, we define the aggregate URLLC rate as \(\Lambda _{uj}=n_{uj}\lambda _u\) (where \(n_{uj}\) is the number of URLLC service subscribers) and the aggregate eMBB rate as \(\Lambda _{ej}=N_{e}\lambda _{ej}\) (where \(N_{e}\) is the number of eMBB service subscribers, which for this analysis is considered a parameter). The mean service times of the packets are assumed to be exponentially distributed with a mean of \(\frac{1}{\mu }\), where \(\mu\) represents the capacity of the network. For stability reasons, it is assumed that \(\lambda <\mu\). Additionally, for the analysis of the SN scenario, we choose an M/M/1 queue without priority where the arriving packets are generated by the URLLC and eMBB users, which are served with the same priority. For the DN scenario, we choose an M/M/1 queue with two priorities, a high priority for the URLLC service due to the delay sensitivity and a low priority for the eMBB service because this service does not depend on delay sensitivity.
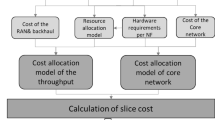
2.2 Economic Model
The users are interested in receiving the services that an operator provides. Each URLLC user pays a subscription price, \(p_{uj}\), for the URLLC service to an operator and receives one QoS, while each eMBB user pays a price per eMBB packet, \(\pi _{ej}\), to an operator and receives a QoS. Therefore, the subscription price for an eMBB user will be \(p_{ej}\), where \(p_{ej} \triangleq \pi _{ej} \lambda _{ej}\). Users will observe the prices set by the operator and decide whether or not to subscribe to the service. For SN and DN scenarios, the QoS expressions for URLLC and eMBB services are proposed in (1)–(3) based on queuing theory [43], where:
-
with (1), we model the QoS of the eMBB service for the SN and DN scenarios. The eMBB service does not offer delay requirements and the QoS is dependent on the rate that the network allocates to each user. \(Q_{ej}\) is an increasing function, then in (1), with a higher \(\lambda _{ej}\), the QoS user perceived in eMBB service increases. Moreover, it has a logarithmic dependence. \(Q_{ej}\) is a concave function whose slope decreases as \(Q_{ej}\) increases, so an increase of \(\lambda _{ej}\) in \(Q_{ej}\) with low values is perceived as a larger increase in \(Q_{ej}\), while an increase of \(\lambda _{ej}\) in \(Q_{ej}\) with very high values is perceived as a smaller increase in \(Q_{ej}\). In (1), add 1 to \(\lambda _{ej}\) so that when \(\lambda _{ej}=0\) then \(ln(1)= 0\). This is because the eMBB user values a high transmission of packets more than a delay in the transmission time, so \(Q_{ej}\) depends only on the \(\lambda _{ej}\) it achieves.
-
with (2) and (3), we model the QoS of the URLLC service. A queue model is a best fit for the modeling of the quality of service for the users of URLLC, where the delay is a key performance indicator. Furthermore, URLLC latency requirements are related not to the average delay, but to a maximum delay. That is the motivation of using the M/M/1 delay distribution \(P[t>\epsilon ]\) in the expression \(Q_{uj}=\frac{k_u}{P[t>\epsilon ]}\). Given a parameter \(\epsilon\), the higher the probability that the URLLC packets are delayed more that \(\epsilon\), the lower the QoS \(Q_{uj}\). Therefore, the greater the delay, the less \(Q_{uj}\) a URLLC user perceives.
-
with (2), we model the QoS of the URLLC service for the SN scenario, also, \(Q_{us}\) has a delay dependency and is under the First Input First Output (FIFO) scheduling discipline with no priority.
The rate of the eMBB service generates a delay in the URLLC service because both services are served with the same priority.
-
and, with (3), we model the QoS of the URLLC service for the DN scenario. Specifically, (3) allows assigning a high priority to the URLLC service due to its delay sensitivity and a low priority to the eMBB service due to its non-delay dependency. The speed of the eMBB service does not delay the URLLC service because the URLLC user packets are served first, while the eMBB user packets are served later.
-
The URLLC and eMBB users utility, \(U_{uj}\) and \(U_{ej}\), is the difference between the QoS perceived by users in monetary units minus the price charged by the operator [40]. We assume that URLLC and eMBB user utility is equal to zero when users do not subscribe to the corresponding service. The utility function can be related to the quasilinear function used in the telecommunications, and microeconomic analysis described in [44]. Therefore, the eMBB user utility for the SN and DN scenarios will be (4), while the URLLC user utility for the SN scenario will be (5) and for the DN scenario, it will be (6):
The profit obtained by the URLLC service is defined in (7) and by the eMBB service, it is defined in (8). In addition, to determine the total benefit in a model, the benefits obtained by the URLLC and eMBB services are defined in (9).
The operator profit should have decreased due to investment costs and operating costs. However, the operating costs have not been considered because it does not depend on the price of the service, this makes the expression of the benefit less explicit, nor the investment costs because we can affirm that it is a constant value.
2.3 Strategic Game
Strategic interactions over the two business models can be identified between the user’s subscription and pricing decisions for URLLC and eMBB services as follows:
-
The subscription decision of the URLLC users is influenced by the pricing decision for the URLLC service. Likewise, the subscription decision of the eMBB users is influenced by the pricing decision for the eMBB service.
-
The subscription decision of the URLLC users depends on the subscription decision of the eMBB users through its QoS. Likewise, the subscription decision of the eMBB users depends on the subscription decision of the URLLC users through its QoS.
-
\(\Pi _{uj}\) depends on the subscription decision of the URLLC users. Likewise, \(\Pi _{ej}\) depends on the subscription decision of the eMBB users.
-
\(\Pi _{uj}\) is influenced by the pricing for the eMBB service, indirectly through the eMBB users’ subscription decision.
Based on (7) and (9), in the monopoly, the operator’s profit is \(\Pi _{j}\). In contrast, in the duopoly, the URLLC operator’s profit is \(\Pi _{uj}\), and the eMBB operator’s profit is \(\Pi _{ej}\). These strategic interactions are amenable to analysis by means of Game Theory, where there are two user bases in the monopoly and duopoly. The incentives are the utilities for each user base and the profits for each operator. The proposed game model is a two-stage game as depicted in Fig. 4, with a different structure for each model:
-
Monopoly
-
Stage I comprises a single player (monopoly operator) who sets the price of the two services.
-
-
Duopoly
-
Stage I comprises two players (URLLC operator and eMBB operator) who set the service price.
-
In both the monopoly and the duopoly models, stage II comprises the URLLC and eMBB user bases, within which each user chooses whether to subscribe or not to its operator.
The game’s solution is an equilibrium decision or strategy for each player. The equilibrium used is the Nash equilibrium, where no player intends to change his equilibrium decision as long as the other players are playing with the equilibrium decision. This two-stage game is solved using backward induction [45], which means that at stage I, players proceed to anticipate the solution of stage II. Since stage II players choose their action knowing the choice of stage I players, in equilibrium, in the equilibrium stage I, players anticipate the choice of stage II players. This justifies solving the two-stage game by first solving the stage II equilibrium for the known actions of the stage I players, and then proceeding back to solve the stage I equilibrium with the knowledge of the stage I best response. The equilibrium calculation is then presented in the following order: first, stage II; and second, stage I.
2.3.1 STAGE II: Users Subscription
In stage II, each URLLC user pays a subscription price, \(p_{uj}\), for the URLLC service to an operator and receives one \(U_{uj}\), while each eMBB user pays a price per eMBB packet, \(\pi _{ej }\), to an operator and receives a \(U_{ej}\). Therefore, the subscription price for an eMBB user will be \(p_{ej} \triangleq \pi _{ej} \lambda _{ej}\).
Regarding the analysis of the eMBB service, \(U_{ej}\) is such that it is not affected by the subscription decisions of other eMBB users. The determination of \(\lambda _{ej}\) that is individual is solved as a classical consumer theory problem, where there are no externalities between consumers. In the eMBB service, there is no game, and it is solved as a maximization problem of \(U_{ej}\) by the Karush-Kuhn-Tucker theorem (KKT) defined in (10) and (11), obtaining \(\lambda _{ej}\) in (12) as the solution to the maximization problem, i.e., there are two solutions \(\lambda _{ej} \ge 0\) and \(\lambda _{ej} = 0\).
where \(\lambda _{ej}\) is the rate that an eMBB user will generate according to a price to maximize his utility.
In the analysis of the URLLC service, \(U_{uj}\) depends on the delay experienced by the M/M/1 queue, and the delay depends on the individual decisions of all the URLLC users because the more URLLC users decide to enter more delay there will be, hence the externality. In this sense, users must decide whether to subscribe or not (obtaining \(U_{uj}<0\)). A strategic interaction exists between each user decision through the congestion effect in the utility \(U_{uj}\). Under these conditions, the equilibrium reached is based on Wardrop’s 1952 principle. Specifically, we consider the first principle, Wardrop’s, stating that the journey times on all utilized routes should be equal and lower than the time required by a single vehicle on any new route. Essentially, a Wardrop equilibrium guarantees that all users receive the same level of utility from the selected alternatives. In this analysis, that means: (1) \(U_{uj} = 0\) (the utility of subscribing and not subscribing are equal), and some subscribe and some do not subscribe (\(n_{uj} \ge 0\)); (2) \(U_{uj} < 0\) (no user subscribes (\(n_{uj} = 0\)) because the utility they get is less than zero). On the other hand, we have \(\Lambda _{uj}= n_{uj} \,\, \lambda _{u}\) where \(n_{uj}\) is the number of URLLC users in the balance that subscribe and \(\lambda _{u}\) is the mean packet arrival rate of URLLC users to the network; therefore, \(n_{uj}\) is endogenous. For the eMBB service, what is endogenous is the individual rate \(\lambda _{ej}\) and \(N_{e}\) is a parameter. To ensure the stability of the network, the restriction \(n_{uj}\lambda _{u} + N_{e} \,\, \lambda _{ej} \le \alpha \mu\) is applied and based on the conditions of Wardrop and the solution of the maximization problem in (12), that is, (\(\lambda _{ej} \ge 0\)) and (\(\lambda _{ej} = 0\)), We describe four cases in (13)–(16).
where \(n_{uj}\) and \(\lambda _{ej}\) are expressed as a function of \(p_{uj}\) and \(\pi _{ej}\), i.e., \(n_{uj}(p_{uj},\pi _{ej})\) and \(\lambda _{ej}(p_{uj},\pi _{ej})\). The development is described in Sect. 3.
2.3.2 STAGE I: Operator Pricing
In the monopoly, the operator sets the URLLC and eMBB services prices to maximize its profit in the SN and DN scenarios. The operator anticipates that the subscription of the users will be consolidated within the equilibrium described in (13)–(16), where the Wardrop equilibrium regions have been found. The operator benefit will depend on the prices.
In the duopoly, each operator sets its service price instantly and independently in the SN and DN scenarios. Each operator is not only aware of the subscription decision in stage II and its profit, but also of the rational behavior of the other operator. The price that maximizes the benefit for each operator will also depend on the decision of the other operator, i.e., it will be given by the Best Response function (BR), as follows:
Finally, the price pair, (\(p_{uj}^{d},\pi _{ej}^{d}\)), is a Nash equilibrium provided that the choice of the URLLC operator is optimal given the choice of the eMBB operator and the choice of eMBB operator is optimal given the choice of URLLC operator [46].
The Nash equilibrium in stage I will be \(p_{uj}^{d}\) and \(\pi _{ej}^{d}\) such that each operator is fixing a price of the BR to the price of the other operator, anticipating the equilibrium of stage II. The solution is given by the following system of equations [44].
2.4 Social Optimum
The social optimum introduces a regulator to the market that seeks to maximize social welfare (\(SW_{j}\)) based on \(n_{uj}\) and \(\lambda _{ej}\). In this sense, \(SW_{j}\) is the sum of the utilities of all actors considered, i.e., \(SW_{j}\) is the sum of the consumer surplus (\(CS_{j}\)) and \(\Pi _{j}\), in the SN and DN scenarios, then the optimum social welfare is the maximum, \(SW_{j}^{o}\); we can use it as a reference to compare the \(SW_{j}\) of the monopoly and the duopoly. Therefore, we have the following.
Likewise, \(CS_{j} = CS_{uj} + CS_{ej}\), where \(CS_{uj}\) is the sum of the utility of all URLLC users and \(CS_{ej}\) is the sum of the utility of all eMBB users. Therefore, \(CS_{ej}~=~N_{e} (Q_{ej}~ -~\lambda _{ej} \pi _{ej})\) and \(CS_{uj} = n_{uj}(Q_{uj}-p_ {uj})\). On the other hand, in the user equilibrium, \(U_{uj}\) is zero (\(Q_{uj}=p_{uj}\)), consequently, \(CS_{uj}\) will be zero because \(CS_{uj}\) does not depend on the business model but of the balance of users, resulting in \(CS_{j}= CS_{ej}\). Based on what was described above, \(SW_{j} = n_{uj} \,\, Q_{uj} + N_{e} \,\, Q_{ej}\).
Obtaining \(SW_{j}^{o}\) and the pair of endogenous variables (\(n_{uj}^{o},\lambda _{ej}^{o}\)) is done through the maximization problem of social welfare, \(SW_{j}\).
In the social optimum, since it is not an operator who sets a price to maximize its profit but rather a regulator who seeks to maximize social welfare through the distribution of resources, prices are no longer necessary; therefore, although maximizing social welfare only has sense from the point of view of distributing resources, the variables that maximize \(SW_{j}\) are \(n_{uj}\) and \(\lambda _{ej}\); therefore, there is a correspondence between these variables with the prices, i.e., for each \(n_{uj}^{o }\) and \(\lambda _{ej}^{o}\) are matched to a price.
In addition, when maximizing \(SW_{j}\) there are no regions because they are a function of \(n_{uj}^{o}\) and \(\lambda _{ej}^{o}\), but a calculation is made based on equilibrium expressions of subscription (13)–(16) obtaining the prices induced by \(n_{uj}^{o}\) and \(\lambda _{ej}^{o}\) in Table 2 for SN and Table 3 for DN scenario.
Finally, based on (7), (9), and the prices of Tables 2 and 3, we determine the expression of the profit of each operator and the total profit in the social optimum for SN and DN, i.e., \(\Pi _{uj}^{o}\), \(\Pi _{ej}^{o}\), and \(\Pi _{j}^{o}\).
3 Analysis
This section first analytically obtains the Wardrop equilibrium for SN and DN scenarios in stage II for the monopoly and duopoly models. And then, we present the stage I solution for business models.
3.1 Stage II
3.1.1 SN Scenario
The analysis for the SN scenario in the monopoly and duopoly is carried out based on (12)–(16). The result we get is four regions.
Region a:
Region b:
Region c:
Region d:
Figure 5 shows the graphical representation of the regions in equilibrium on the plane \(p_{us}\)-\(\pi _{es}\) for a specific assignment of values of the parameters described in Table 4.
3.1.2 DN Scenario
In the same way, the analysis for the DN scenario in the monopoly and duopoly is carried out based on (12)–(16). The result we get is four regions.
Region a:
Region b:
Region c:
Region d:
Figure 6 shows the graphic representation of the regions in equilibrium on the plane \(p_{ud}\)-\(\pi _{ed}\) for a specific assignment of values of the parameters described in Table 4.
3.2 Stage I
3.2.1 The Monopoly SN and DN Scenarios
The solution of stage I for the monopoly is not analyzable. Therefore, the stage I solution for this model will be performed numerically in Sect. 4, based on the maximization problem in (17) defined in Sect. 2.3.2.
3.2.2 The Duopoly SN Scenario
The solution of stage I for the duopoly is to get the BRs based on the restrictions and regions analyzed in Sect. 3.1.1, obtaining the following:
Figure 7 shows the graphical representation of \(BR_{e}(p_{us})\) and \(BR_{u}(\pi _{es})\). On the other hand, we observe that the prices set by the operators reach equilibrium at the initial point where the BRs diverge. Therefore, the Nash Equilibrium is:
3.2.3 The Duopoly DN Scenario
The solution of stage I for the duopoly is to get the BRs based on the restrictions and regions analyzed in Sect. 3.1.2, obtaining the following:
Figure 8 shows the graphic representation of \(BR_{e}(p_{ud})\), \(BR_{u}(\pi _{ed})\), and the points crossed between them on the plane \(p_{ud}\)-\(\pi _{ed}\) for the DN scenario with a specific assignment of the parameter values described in Table 4.
As a result of the parameters, we observe that in Fig. 8, the prices set by the operators reach equilibrium within a range of values. This range of values comprises the different price pairs, \(p_{ud}\), and \(\pi _{ed}\). These prices are within a corresponding interval, that is, \(p_{uj} \subset \left[ k_u \,\, e^{\epsilon \mu - 1}, k_u e^{\epsilon \mu } \right]\), while \(\pi _{ej} \subset \left[ \frac{k_e}{\frac{\alpha \mu }{N_{e}}+1}, \frac{k_e}{\frac{1}{N_{e}}\left( \alpha \mu -\frac{1}{\epsilon }\right) +1} \right]\).
However, \((p_{ud},\pi _{ed})\) vertically at the upper extreme point is, \(\left( k_u e^{\epsilon \mu }, \frac{k_e}{\frac{\alpha \mu }{N_{e}}+1}\right)\) while at the lower extreme point it is \(\left( k_u \,\, e^{\epsilon \mu - 1}, \frac{k_e}{\frac{1}{N_{e}}\left( \alpha \mu -\frac{1}{\epsilon }\right) +1} \right)\). Based on this, it is found that the URLLC operator profit is much lower at the high point than at the low point for the price pair, while the eMBB operator profit is higher at the high point than at the low point. The midpoint of the interval of values of \(\pi _{ed}^{d}\) and its corresponding \(p_{ud}^{d}\) is taken as the solution for both operators, shown below:
4 Results and Discussion
In this section, we will present the numerical results for the proposed model, where we calculate the prices, the number of subscribers, and the operators’ profits in the monopoly in the monopolistic (Sect. 4.1), duopolistic (Sect. 4.2) business model, and monopoly and duopoly are compared with the social optimum (Sect. 4.3). Two scenarios are analyzed for each business model: SN and DN. Likewise, based on Sect. 4.2 we have \(p_{ej}^{i}\) and \(p_{uj}^{i}\) where \(p_{ej} \triangleq \pi _{ej} \lambda _ {ej}\). In the same sense, for the aggregate rates per service, \(\Lambda _{ej}^{i}\), \(\Lambda _{uj}^{i}\), we have defined as \(\Lambda _{uj}^{i} \triangleq n_{uj}^{i} \lambda _{u}\) and \(\Lambda _{ej}^{i} \triangleq N_{e} \lambda _{ej}^{i}\). Finally, we have conducted a series of numerical experiments to obtain a better understanding of the scenario from the economic interactions. The values for the parameters, if not stated otherwise, are shown in Table 4 are used.
4.1 Monopoly
Figure 9 shows the effect of \(\mu\) on the aggregate rates. In the SN scenario, \(\Lambda _{us}^{m}\) holds its value and \(\Lambda _{es}^{m}\) is zero as \(\mu\) increases, while in the DN scenario, \(\Lambda _{ud}^{m}\) and \(\Lambda _{ed}^{m}\) increase as \(\mu\) increases. As a result, in the SN scenario, the operator is not interested in providing the eMBB service because it harms the QoS of the URLLC service. Therefore, it makes sense that \(\Lambda _{es}^{m}=0\) and there is only \(\Lambda _{us}^{m}\). While in the DN scenario, the same does not occur as in the SN scenario, i.e., as shown in Fig. 9, when \(\mu\) increases, \(\Lambda _{ed}^{m}\) and \(\Lambda _{ud}^{m}\) increase; hence, there is provision of the eMBB service because it does not impair the QoS of the URLLC service.Therefore, there is provision of both services. Finally, the operator is interested in providing the URLLC service at a price higher than the eMBB service price due to the characteristics of the service from the point of view of maximizing the operator’s benefit, resulting in a higher \(\Lambda _{uj}^{i}\).
Figure 10 shows the effect of \(\mu\) on the prices of services. We observe that in the SN scenario, \(p_{us}^{m}\) increases and \(p_{es}^{m}\) is zero as \(\mu\) increases, while in the DN scenario, \(p_{ud}^{ m}\) increases more than \(p_{ed}^{m}\) increases as \(\mu\) increases. The described behavior is consistent with the analysis performed in the previous section on aggregate rates. On the other hand, we observe that URLLC users have a higher price than eMBB users in the SN and DN scenarios. The described behavior leads us to conclude that paying more for the URLLC service makes sense because it depends on the sensitivity \(\epsilon\), while the eMBB service does not depend on \(\epsilon\); this is in line with the approach of equations (1)–(3).
Figure 11 shows the total benefit as a function of \(\mu\) in the SN and DN scenarios. We observe that \(\Pi _{d}^{m}\) and \(\Pi _{s}^{m}\) increase as \(\mu\) increases. In the same sense, \(\Pi _{d}^{m} > \Pi _{s}^{m}\), this behavior is consistent because, in the SN scenario, the total profit depends only on the profit obtained by the URLLC service and not by the eMBB service as shown in (9), while in the DN scenario, the total profit depends on the profit obtained by the URLLC service and by the eMBB service as shown in (9).
Figure 12 shows social welfare as a function of \(\mu\). When \(\mu\) increases also \(SW_{d}^{m}\) and \(SW_{s}^{m}\) increase, i.e., the network supports a higher user number (\(n_{uj}\) and \(N_{e}\)). The described behavior is consistent because the increase in users influences both in (22), the increase \(\Pi _j\) (where \(\Pi _j= n_{uj} \,\, p_{uj} + N_e \lambda _{ej} \pi _{ej}\)) and the increase \(CS_{j}\) ( where \(CS_{j} = N_{e} (Q_{ej} - \lambda _{ej} \pi _{ej}) + n_{uj}(Q_{uj}-p_ {uj})\). Likewise, SW in the DN scenario is greater than the SN scenario because \(\Pi _{d}^{m} > \Pi _{s}^ {m}\) and \(CS_{ej}^{m} > CS_{uj}^{m}\), then from (22) it follows that \(SW_{d}^{m} > SW_{s}^{m}\).
The conclusion is that the DN scenario is the most favorable network configuration for the operators and users in the monopoly business model because the prices, operators’ benefits, user utilities, and social welfare are better than the SN scenario, i.e., the DN scenario through the NS permits allows to provide a better service to the users of the URLLC and eMBB services.
4.2 Duopoly
Figure 13 shows the effect of \(\mu\) on the aggregate rates. We can see that in the SN scenario, \(\Lambda _{es}^{d}\) increases and \(\Lambda _{us}^{d}\) is zero as \(\mu\) increases, while in the DN scenario, \(\Lambda _{ed}^{d}\) increases and \(\Lambda _{ud}^{d}\) decreases as \(\mu\) increases. We expected that, in the DN scenario, \(\Lambda _{ud}^{d}\) would increase. However, we found the opposite. One reason for this is that in the SN scenario, \(p_{es}^{d}\), \(p_{us}^{d}\) reach the equilibrium where only the eMBB service generates traffic, i.e., \(\Lambda _{us}^{d}=0\), while in the DN scenario, \(p_{ed}^{d}\) and \(p_{ud}^{d}\) reach equilibrium generating traffic for both services.
Figure 14 shows the effect of \(\mu\) on the prices of services. We observe that in the SN scenario, \(p_{us}^{d}\) and \(p_{es}^{d}\) increase slightly as \(\mu\) increases, while in the DN scnario, \(p_{ud}^{d}\) increases significantly and \(p_{ed}^{d}\) increases slightly as \(\mu\) increases. On the other hand, we observe that the price of the URLLC service is higher than the price of the eMBB service in the SN and DN scenarios. The described behavior leads us to conclude that paying more for the URLLC service makes sense because it depends on the sensitivity \(\epsilon\), while the eMBB service does not depend on \(\epsilon\); this is in line with the approach of equations (1)–(3).
Figure 15 shows the total benefit as a function of \(\mu\) for the SN and DN scenarios. We can observe that \(\Pi _{s}^{d}\) and \(\Pi _{d}^{d}\) increase as \(\mu\) increases. In the same sense, \(\Pi _{d}^{d} > \Pi _{s}^{d}\), this behavior is consistent because, the total benefit is the sum of the benefits obtained per service defined in (9) and profits are in function of prices, hence, as \(p_{ud}^{d}\) is much larger than \(p_{us}^{d}\), \(p_{ed}^{d}\) and \(p_{es}^{d}\), furthermore, \(\Pi _{us} = 0\); it makes sense that the total benefit in the DN scenario is greater than in the SN scenario.
Figure 16 shows social welfare as a function of \(\mu\). When \(\mu\) increases, \(SW_{d}^{d}\) and \(SW_{s}^{d}\) increase, i.e., the network supports a higher user number (\(n_{uj}\) and \(N_{e}\)). The described behavior is consistent because the increase in users influences both in (22), the increase \(\Pi _j\) (where \(\Pi _j= n_{uj} \,\, p_{uj} + N_e \lambda _{ej} \pi _{ej})\) and the increase \(CS_{j}\) ( where \(CS_{j} = N_{e} (Q_{ej} - \lambda _{ej} \pi _{ej}) + n_{uj}(Q_{uj}-p_ {uj}))\).
Likewise, SW in the DN scenario is greater than the SN scenario because \(\Pi _{d}^{d} > \Pi _{s}^ {d}\) and \(CS_{ej}^{d} > CS_{uj}^{d}\), then from (22) it follows that \(SW_{d}^{d} > SW_{s}^{d}\).
The conclusion is that the DN scenario is the most favorable network configuration for the operators and users in the duopoly because the prices, operators’ benefits, user utilities, and social welfare are better than the SN scenario, i.e., the DN scenario through of the NS permits allows to provide a better service to the users of the URLLC and eMBB services.
4.3 Comparison of Business Models with the Social Optimum
The business models are compared as follows. From the point of view of social welfare, Fig. 17 shows that \(SW_{d}^{o} > SW_{d}^{d}\), while \(SW_{d}^{m}\) is closer to \(SW_{d}^{o}\); therefore, the best way to offer eMBB and URLLC services in the DN scenario is the monopoly. The described behavior is consistent because since the monopoly in the DN scenario serves all customers of URLLC and eMBB services separately using NS, it can exploit the QoS characteristics and capacity of the network, which enables the SW to be achieved through the benefits obtained by a single operator (see Figs. 11 and 15).
Figure 18 shows that \(\Lambda _{ed}^{m}\) and \(\Lambda _{ud}^{m}\) are closer and crossed each other, while \(\Lambda _{ed}^{d}\) and \(\Lambda _{ud}^{d}\) are crossed but further apart from each other. On the other hand, the aggregate rates in the monopoly show behavior of proximity to each other similar to the behavior of the aggregate rates in the social optimum, while the behavior of the aggregate rates in the duopoly is more different. Therefore, the results obtained for the DN scenario in the monopoly are considered the most optimal.
\(\Lambda _{ed}^{m}\), \(\Lambda _{ud}^{m}\), \(\Lambda _{ed}^{d}\), \(\Lambda _{ud}^{d}\), \(\Lambda _{ed}^{o}\), and \(\Lambda _{ud}^{o}\) as functions of \(\mu\) for \(k_{u} = 1\), \(k_{e} = 1.1\), \(\alpha =0.8\), \(\epsilon = 0.0003 \,\hbox {s}\), \(\lambda _{u} = 1\, \hbox {packet/s}\), \(N_{e} = 7000 \,\hbox {eMBB}\) users
The business models are compared as follows. From the point of view of the prices, Fig. 19 shows that \(p_{ud}^{d}\) reaches a higher value compared to the rest of the prices of both services, while \(p_{ud}^{m}\) is the lowest for the URLLC service when \(\mu\) reaches a maximum value, in other words, \(p_{ud}^{d}> p_{ud}^{o} > p_{ud}^{m}\). Furthermore, we note that \(p_{ed}^{m}\), \(p_{ed}^{d}\) and \(p_{ed}^{o}\) are close to each other. This result is associated with the result of the comparison of social welfare, that is, since the monopoly prices are the lowest value, they are the most appropriate from the point of view of users.
The business models are compared as follows. From the point of view of the operator’s benefits, Fig. 20 shows that \(\Pi _{d}^{m}\) reaches a higher value compared to the other two benefits, while \(\Pi _{d}^{d}\) is the smallest of them, that is, \(\Pi _{d}^{m}> \Pi _{d}^{o} > \Pi _{d}^{d}\) as \(\mu\) increases. This result is also associated with the result of social welfare, since the total benefit in the monopoly is the closest to the total benefit achieved in the social optimum and with a value greater than the total benefit in the duopoly.
The conclusion is that the price, operator profit, and user utility results obtained in the monopoly are closer to the results of the optimum social than the duopoly results in the DN scenario. Therefore, the best way to offer eMBB and URLLC services is through a 5G network with NS and by a single operator.
5 Conclusions
Two business models have been proposed for providing services URLLC and eMBB over a 5G network, denominated Monopoly and Duopoly. In Monopoly, a single operator offers URLLC and eMBB services. While in a duopoly, two operators offer one service each. In addition, two network models are proposed. A 5G network model without NS, where network resources are shared between both services without NS, and a 5G network model with NS, where network resources are shared between both services but assigned a higher priority to the URLLC service. The first network model is referred to as the SN scenario, and the second is referred to as the DN scenario. Also, we studied the feasibility of the model from a positive-profit point of view for all the actors.
Our main results suggest that, in both business models, the DN scenario is feasible from a pricing and operator profit point of view because its results are closer to those of the social optimum, i.e., using a 5G network NS technology to share resources for each service is better than not using an NS. Also, the monopoly results are better than the duopoly results for the DN scenario, as these results are closer to the social optimum results. Therefore, the best way to offer URLLC and eMBB services over a 5G network is with NS and provided by a single operator.
Finally, our conclusions make sense because the monopolist covers the entire service provision, and there is no social welfare loss due to resource sharing between the two services using NS.
As regards the future lines of work, two open issues are worth mentioning. First, realize a comparative analysis of the quality of URLLC and mMTC services provided by different network operators, using the results obtained in this study as a benchmark. Secondly, analyze the economic viability of the provision of eMBB, URLLC, and mMTC services offered by network operators, and compare the results obtained in this research with current market data.
Data Availability
No data was used to support this study.
References
Banda, L., Mzyece, M., Mekuria, F.: 5G business models for mobile network operators: a survey. IEEE Access (2022)
Yang, W., Li, C.-P., Fakoorian, A., Hosseini, K., Chen, W.: Dynamic URLLC and eMBB multiplexing design in 5G new radio. In: 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), pp. 1–5. IEEE (2020)
Aranda, J., Sacoto Cabrera, E.J., Haro Mendoza, D., Astudillo Salinas, F.: 5G networks: a review from the perspectives of architecture, business models, cybersecurity, and research developments. Novasinergia 4, 6–41 (2021)
Miladić-Tešić, S., Marković, G., Peraković, D., Cvitić, I.: A review of optical networking technologies supporting 5G communication infrastructure. Wirel. Netw. 28(1), 459–467 (2022)
Popovski, P., Trillingsgaard, K.F., Simeone, O., Durisi, G.: 5G wireless network slicing for eMBB, URLLC, and mMTC: a communication-theoretic view. Ieee Access 6, 55765–55779 (2018)
Xiang, W., Zheng, K., Shen, X.S.: 5G Mobile Communications. Springer, London (2016)
Le, T.-K., Salim, U., Kaltenberger, F.: An overview of physical layer design for Ultra-Reliable Low-Latency Communications in 3GPP Releases 15, 16, and 17. IEEE Access 9, 433–444 (2020)
Li, Z., Uusitalo, M.A., Shariatmadari, H., Singh, B.: 5G URLLC: Design challenges and system concepts. In: 2018 15th International Symposium on Wireless Communication Systems (ISWCS), pp. 1–6. IEEE (2018)
Nwakanma, C.I., Anantha, A.P., Islam, F.B., Lee, J.-M., Kim, D.-S.: 3GPP release-16 for industrial internet of things and mission critical communications. In: 2020 International Conference on Information and Communication Technology Convergence (ICTC), pp. 403–406. IEEE (2020)
Nwadiugwu, W.-P., Nwakanma, C.I., Lee, J.-M., Kim, D.-S.: Achieving reliable URLLC-based network in industrial and military embedded systems. In: 2019 International Conference on Information and Communication Technology Convergence (ICTC), pp. 642–645. IEEE (2019)
Foukas, X., Patounas, G., Elmokashfi, A., Marina, M.K.: Network slicing in 5G: Survey and challenges. IEEE Commun. Mag. 55(5), 94–100 (2017)
Osborne, M.J., et al.: An Introduction to Game Theory, vol. 3. Oxford University Press, New York (2004)
Antoniou, J.: Game Theory, the Internet of Things and 5G Networks. Springer, London (2020)
Guijarro, L., Pla, V., Vidal, J.R., Naldi, M.: Competition in data-based service provision: nash equilibrium characterization. Future Gener. Comput. Syst. 96, 35–50 (2019)
Dhanare, R., Nagwanshi, K.K., Varma, S.: A study to enhance the route optimization algorithm for the internet of vehicle. Wirel. Commun. Mobile Comput. 2022, 1–20 (2022)
Yan, X., Huang, C., Gan, J., Wu, X.: Game theory-based energy-efficient clustering algorithm for wireless sensor networks. Sensors 22(2), 478 (2022)
Sadreddini, Z., Masek, P., Cavdar, T., Ometov, A., Hosek, J., Gudkova, I., Andreev, S.: Dynamic resource sharing in 5G with LSA: criteria-based management framework. Wirel. Commun. Mobile Comput. 2018, 1–12 (2018)
Khan, L.U., Yaqoob, I., Tran, N.H., Han, Z., Hong, C.S.: Network slicing: recent advances, taxonomy, requirements, and open research challenges. IEEE Access 8, 36009–36028 (2020)
Wong, S., Han, B., Schotten, H.D.: 5G network slice isolation. Network 2(1), 153–167 (2022)
Alliance, N.: 5G mobile network sharing security (2022)
Samdanis, K., Costa-Perez, X., Sciancalepore, V.: From network sharing to multi-tenancy: the 5G network slice broker. IEEE Commun. Mag. 54(7), 32–39 (2016)
Smail, G., Weijia, J.: Techno-economic analysis and prediction for the deployment of 5G mobile network. In: 2017 20th Conference on Innovations in Clouds, Internet and Networks (ICIN), pp. 9–16. IEEE (2017)
Stojanović, M.: Monetization and pricing of the 5G-enabled smart residential services. In: E-business Technologies Conference Proceedings, vol. 2, pp. 70–73 (2022)
Allon, G., Federgruen, A.: Service competition with general queueing facilities. Oper. Res. 56(4), 827–849 (2008)
Yrjölä, S., Ahokangas, P., Matinmikko-Blue, M.: Novel context and platform driven business models via 5G networks. In: 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), pp. 1–7. IEEE (2018)
Arulappan, A., Raja, G., Passi, K., Mahanti, A.: Optimization of 5G/6G telecommunication infrastructure through an NFV-based element management system. Symmetry 14(5), 978 (2022)
Liu, H.: Research on Resource Allocation and Optimization Technology in 5G Communication Network. In: 2022 2nd International Conference on Consumer Electronics and Computer Engineering (ICCECE), pp. 209–212. IEEE (2022)
Wong, S., Han, B., Schotten, H.D.: 5G network slice isolation. Network 2(1), 153–167 (2022). https://doi.org/10.3390/network2010011
Das, D., Banerjee, S., Dasgupta, K., Chatterjee, P., Ghosh, U., Biswas, U.: Blockchain Enabled SDN Framework for Security Management in 5G Applications. In: 24th International Conference on Distributed Computing and Networking, pp. 414–419 (2023)
Santos, E.J., Souza, R.D., Rebelatto, J.L., Alves, H.: Network slicing for URLLC and eMBB with max-matching diversity channel allocation. IEEE Commun. Lett. 24(3), 658–661 (2019)
Li, X., Samaka, M., Chan, H.A., Bhamare, D., Gupta, L., Guo, C., Jain, R.: Network slicing for 5G: challenges and opportunities. IEEE Internet Comput. 21(5), 20–27 (2017)
Zhang, S.: An overview of network slicing for 5G. IEEE Wirel. Commun. 26(3), 111–117 (2019)
Mendelson, H.: Pricing computer services: queueing effects. Commun. ACM 28(3), 312–321 (1985)
Hayel, Y., Ros, D., Tuffin, B.: Less-than-best-effort services: pricing and scheduling. In: IEEE INFOCOM 2004, vol. 1. IEEE (2004)
Hayel, Y., Tuffin, B.: Pricing for heterogeneous services at a discriminatory processor sharing queue. In: NETWORKING 2005. Networking Technologies, Services, and Protocols; Performance of Computer and Communication Networks; Mobile and Wireless Communications Systems: 4th International IFIP-TC6 Networking Conference, Waterloo, Canada, May 2-6, 2005. Proceedings 4, pp. 816–827. Springer (2005)
Han, B., Tayade, S., Schotten, H.D.: Modeling profit of sliced 5G networks for advanced network resource management and slice implementation. In: 2017 IEEE Symposium on Computers and Communications (ISCC), pp. 576–581. IEEE (2017)
Han, B., Feng, D., Ji, L., Schotten, H.D.: A profit-maximizing strategy of network resource management for 5G tenant slices (2017). arXiv preprint arXiv:1709.09229
Sacoto Cabrera, E.J., Guijarro, L., Maillé, P.: Game theoretical analysis of a multi-MNO MVNO business model in 5G networks. Electronics (2020). https://doi.org/10.3390/electronics9060933
Guijarro, L., Pla, V., Tuffin, B.: Entry game under opportunistic access in cognitive radio networks: A priority queue model. In: 2013 IFIP Wireless Days (WD), pp. 1–6. IEEE (2013)
Sacoto-Cabrera, E.J., Sanchis-Cano, A., Guijarro, L., Vidal, J.R., Pla, V.: Strategic interaction between operators in the context of spectrum sharing for 5G networks. Wirel. Commun. Mobile Comput. 2018, 1–10 (2018)
Sanchis-Cano, A., Guijarro, L., Pla, V., Vidal, J.R.: Economic viability of HTC and MTC service provision on a common network infrastructure. In: 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), pp. 1044–1050. IEEE (2017)
Sacoto-Cabrera, E.J., Guijarro, L., Vidal, J.R., Pla, V.: Economic feasibility of virtual operators in 5G via network slicing. Future Gener. Comput. Syst. 109, 172–187 (2020)
Hassin, R., Haviv, M.: To Queue or Not to Queue: Equilibrium Behavior in Queueing Systems, vol. 59. Springer, Luxemburgo (2003)
Maillé, P., Tuffin, B.: Telecommunication Network Economics: From Theory to Applications. Cambridge University Press, Cambridge (2014)
Maschler, M., Zamir, S., Solan, E.: Game Theory. Cambridge University Press, Cambridge (2020)
Varian, H.: Intermediate Microeconomics: A Modern Approach: Ninth International, Student WW Norton & Company, New York (2014)
Funding
Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature. This work was supported through Grants PGC2018-094151B-I00 and PID2021-123168NB-I00, funded by MCIN/AEI, Spain/10.13039/501100011033 and the European Union A way of making Europe/ERDF, and Grant TED2021-131387B-I00, funded by MCIN/AEI, Spain /10.13039/501100011033 and the European Union NextGenerationEU/RTRP and partially financed by the Government of Peru through the Bicentennial Generation Scholarship granted to the first author.
Author information
Authors and Affiliations
Contributions
Conceptualization, E.M.; Validation, L.G.; Formal analysis, E.M. and L.G; Investigation, E.M. AND E.J.S.C; Writing-original draft, E.M. AND E.J.S.C; Writing-review and editing, L.G. and E.J.S.C. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Moreno-Cardenas, E., Sacoto-Cabrera, E.J. & Guijarro, L. Economic Alternatives for the Provision of URLLC and eMBB Services Over a 5G Network. J Netw Syst Manage 32, 50 (2024). https://doi.org/10.1007/s10922-024-09826-8
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10922-024-09826-8