Abstract
Two players strike balances between allocating resources for defense and production of zero-day exploits. Production is further allocated into cyberattack or stockpiling. Applying the Cobb Douglas expected utility function for equivalent players, an analytical solution is determined where each player’s expected utility is inverse U shaped in each player’s unit defense cost. More generally, simulations illustrate the impact of varying nine parameter values relative to a benchmark. Increasing a player’s unit costs of defense or development of zero-days benefits the opposing player. Increasing the contest intensities over the two players’ assets causes the players to increase their efforts until their resources are fully exploited and they receive zero expected utility. Decreasing the Cobb Douglas output elasticity for a player’s stockpiling of zero-days causes its attack to increase and its expected utility to eventually reach a maximum, while the opposing player’s expected utility reaches a minimum. Altering the Cobb Douglas output elasticities for a player’s attack or defense contests towards their maxima or minima causes maximum expected utility for both players.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
1.1 Background
In 2010, the Natanz nuclear facility in Iran suffered a series of malfunctions causing significant damage to its nuclear program. The cause was a sophisticated cyber attack, a worm called Stuxnet, that is widely considered one of the first significant acts of cyber war, in large part, due to its use of zero-day vulnerabilities. The zero-day vulnerability gets its name from a vulnerability in a defender’s computer system being known to the defender for zero days before it was discovered through the attack or in some other way. That is, the zero-day was unknown to or unaddressed through public patches or a fix by the defender. Because they are unknown and unpatched, zero-day cyberattacks are highly effective. They are also hard to produce, often requiring a significant allocation of resources by the attacker. As a result, it was noteworthy that the cyberattack on the Natanz facility exploited not one but four zero-day vulnerabilities, a previously unobserved use of cyber firepower. In the new landscape of cyberwar, such zero-day attacks are well-researched and highly prized weapons of cyber armies. The catch? They can only be used once. Cyber armies therefore face the tradeoff between using weapons today or stockpiling them for tomorrow.
1.2 Contribution
The Natanz attack raised the awareness of zero-day vulnerabilities. A facility such as the Natanz nuclear facility is controlled by, or has interests aligned by, a player which in this case is the Iranian government. Such a player has resources to defend against zero-day attacks, and has resources to launch zero-day attacks against an opposing player. In this case the opposing player is widely understood to be the United States and Israel (Nakashima 2012). The research context in this article is zero-day vulnerabilities generally, i.e. whether to produce zero-day capabilities, stockpile the capabilities, launch the capabilities as an attack, and defend against zero-day attacks. The model in this article has applicability beyond zero-day vulnerabilities, assuming two players who attack and defend, and may stockpile their capabilities.
To analyze this research problem, we introduce a two-player game to elucidate potential strategies of cyber armies and the decision to stockpile or use zero-day capabilities to exploit zero-day vulnerabilities. More specifically, each player has cyber resources applicable to produce zero-day exploits or defend against the opposing player’s zero-day attacks. Production of zero-days includes discovery, reconnaissance (research into the opponent’s systems), and weaponization. We, therefore, specify that each player can have zero-day vulnerabilities, which can be attacked by the opposing player, and zero-day exploits, which are produced and are applicable to attack the opposing player. That is, each player’s zero-day exploits can either be used to attack the opposing player or be stockpiled for future use. Since the nature of a zero-day vulnerability is that it has limited or no value after a zero-day attack exploits it and the defender realizes the exploit, the attacker can be expected to have an incentive to use it immediately in some cases, and to stockpile it in other cases. The value of stockpiling is specified in a Cobb Douglas expected utility function. The attacker derives utility from stockpiling zero-day capabilities due to enhanced security, in the knowledge that various uncertain threats posed by the opposing player (and which the attacker may keep secret) can be immediately eliminated or ameliorated. Announcing that a player has zero-day capabilities may also constitute deterrence utility for the player. Hence each player faces a resource allocation decision about how to strike a balance between producing zero-days, storing zero-days, attacking with zero-days, and defense against zero-days, which is explored. The article is to our knowledge the first to assess how a player strikes such a balance. The literature, reviewed below, has a more specific focus not focusing on these balances.
1.3 Literature
No game-theoretic treatment of zero-days have been found in the literature to date. For cyber security more generally, Nagurney and Shukla (2017) compare three models for cybersecurity investment accounting for noncooperation, Nash bargaining theory to facilitate information sharing, and system-optimization through cooperation. Edwards et al. (2017) present a game-theoretic model of blame with an attacker and a defender exploring the asymmetric problem of attribution, the stability of peace, conditions for attack tolerance, and conditions that allow a mistake or third party attacker to undermine peace.
Baliga et al. (2020) expand the treatment of the imperfect attribution in a game-theoretic model with a single defender and multiple attackers in order to identify opportunities for cyber deterrence. They identify conditions for enhancing deterrence through detection while revealing the potential for enhanced attribution to undermine deterrence. Interestingly, Baliga et al. (2020) uncover an endogenous strategic complementarity where increased aggression by one attacker increases the aggression of the other attackers. Welburn et al. (2019) expand on the discussion of cyber deterrence by defining an attribution game between an attacker and a defender and introducing signaling. In their attribution game, following the attacker’s decision to attack or not, the defender receives a (possibly noisy) signal and choses to retaliate or not. Their signaling game randomly assigns the defender a capability to retaliate and allows the defender to signal this capability to the attacker before it decides to attack. While finding that it is never in the best interest of the defender to signal truthfully, they find that the defender can enhance deterrence through signaling and discuss implications for cyber deterrence policy. Trang and Brendel (2019) find through meta-analysis that deterrence theory involving sanctions to enforce information security policies better predicts deviant behavior in cultures with malice, power distance, and uncertainty avoidance.
Regarding strategy and timing of security investments, Xu et al. (2019) find through options theory that reactive investments to improve IT security and proactive investments to exploit commercial opportunities is beneficial. Miaoui and Boudriga (2019) find that optimal information security investment depends on the attitude towards security risk, and increases with the investment horizon for all types of vulnerabilities for located attacks, but not always for distributed attacks. Crossler et al. (2019) study 279 individuals’ computer security behaviors and three security threats, i.e. security related performance degradation, identify theft, and data loss. They find through expert interviews that response efficacy and response cost help explain chosen behaviors, and identify security threat-response pairs, which may aid to obtain multi-layered protection.
Further game theoretic research exists on information security to protect against attacks, accounting for returns on information security investment (Hausken 2006b, 2014), substitution and interdependence (Enders and Sandler 2003; Hausken 2006a; Lakdawalla and Zanjani 2002), data survivability versus security in information systems (Levitin et al. 2012), and information sharing to prevent attacks (Hausken 2007, 2015, 2017a, 2017b, 2018b). For recent reviews of the use of game theoretic models applied to cyber security, see Roy et al. (2010), Hausken and Levitin (2012), and Do et al. (2017).
2 Theoretical Background
Appendix 1 shows the nomenclature. Consider two players in a simultaneous move one-period game. Assume that player i, i = 1, 2, gets cyber resources Ri (capital, manpower, competence, etc.) from a national budget which is allocated to develop zero-day exploits (zero-days, for short) Zi (intended to exploit zero-day vulnerabilities) at unit cost bi, and defense with effort Fi at unit cost ai. Player i’s resource allocation is
Assume that player i uses zi of its zero-days, 0 ≤ zi ≤ Zi, to attack its opponent’s asset, and stockpiles the remaining Zi − zi. In order to enable independence between player i’s effort Zi to develop zero-day capabilities, and player i’s defense effort Fi, which is necessary for the model to be conceptually consistent, we assume that player i’s effort Zi confines attention to exploiting the opposing player j’s vulnerabilities, j ≠ i. i = 1, 2, not player i’s own vulnerabilities, which is a means of defense for player i, which we now proceed to elaborate upon.
When player i as a defender and player j as an attacker use the same or similar systems (e.g. produced by the same manufacturer), we assume that player i can defend itself by discovering its own vulnerabilities, and patching them, without informing player j about the patch. If player j discovers the patch (e.g. through leakage or spying), player i’s defense is still intact (since the patch is operational), and player j can be expected to apply the same or a similar patch which means that player i can not exploit this vulnerability to develop zero-day exploits against player j.
When the defending player i and the attacking player j apply different systems, discovering vulnerabilities in one system generally does not mean that the other system has the same vulnerabilities. This article assumes that all kinds of defense, including conventional defense against zero-day attacks, and discovering player i’s own vulnerabilities and patching them, have the same unit effort cost ai. To the extent different kinds of defense in practice may have different unit effort costs, we assume that some weighted average unit effort cost ai can be determined. Future research may model different kinds of defense effort which, e.g., may operate additively (Hausken 2020) or multiplicatively (Arbatskaya and Mialon 2010). Such generalization causes various complications. For example, if multiple defense efforts operate additively, player i generally chooses the effort with the lowest unit effort cost. Alternatively, if such multiple efforts operate multiplicatively, e.g. applying the Cobb Douglas function which Arbatskaya and Mialon (2010) do, player i needs to exert all its efforts to ensure impact. The latter is not realistic in the current model since we assume that any defense effort exerted by player i, whether exerted alone or in conjunction with other defense efforts, constitutes defense effort for player i. These considerations are such that we model player i’s defense effort as Fi with an average unit cost ai, which accounts for all kinds of defense including conventional defense and discovering and patching player i’s own vulnerabilities as a means of defense.
The players fight over two assets as shown in Fig. 1. We may think of player 1 as blue and player 2 as red. An asset has value, which can be, e.g., economic, human, or symbolic (Hausken 2018a). Two players owning one asset each usually value their assets differently, causing four different valuations. For example, the US may value the Statue of Liberty highly, whereas an opposing player may assign a lower value to it. As a second example, Fort Knox which contains the US Bullion Depository has high value to the US, but also has value to an opposing player (which may differ from the US’ value) since destroying it is a way of attacking the US. Player 1 values its own asset as V1 and player 2’s asset as W1. Player 2 values its own asset as W2 and player 1’s asset as V2. The players attack their opponents’ assets with zero-day attacks z1 and z2, and defend their own assets with defenses F1 and F2.
We first consider player 1’s asset valued as V1 by player 1 and V2 by player 2. Player 1 defends with effort F1, while player 2 attacks with its zero-days z2. We apply the ratio form contest success function (Tullock 1980), which is a plausible and widely used method for assessing two opposing players’ success. Player 1’s expected contest success is p1, and player 2’s expected contest success is q2, i.e.
where the parameter v is the contest intensity over player 1’s asset. In (2) the ratios have a sum of two efforts (each raised to v) in the denominator, and one of the efforts in the numerator. That gives a number between zero and one which specifies contest success. The contest success can express the probability of winning the contest, or the fraction that one receives. In (2), v = 0 means that the players’ efforts have equal impact on the contest success p1 and q2, 0 < v < 1 gives disproportional advantage of exerting less effort than one’s opponent. Assuming v = 1 gives proportional advantage, and v > 1 gives disproportional advantage of exerting more effort than one’s opponent. For further interpretations of the contest intensity v in risk analysis see Hausken and Levitin (2008).
We secondly consider player 2’s asset valued as W1 by player 1 and W2 by player 2. Player 1 attacks with its zero-days z1 while player 2 defends with effort F1. Player 1’s expected contest success is q1, and player 2’s expected contest success is p2, i.e.
where the parameter w is the contest intensity over player 2’s asset, with the same interpretation as v in (2).
Finally, we assume that player i earns a benefit from its stockpiled zero-days Zi − zi, which are produced but not used in the attack. Assuming a Cobb Douglas expected utility function with these three ingredients, with output elasticities αi, μi, 1 − αi − μi for player i’s stockpiled non-used zero-days Zi − zi, 0 ≤ αi, μi, 1−αi−μi≤ 1, player i’s contest success when defending its own asset, and player i’s contest success when attacking its opponent’s asset, respectively, player i’s expected utility is
where (2) and (3) have been inserted. Player 1’s free choice variables are Z1 and z1, where F1 is determined by (1). Player 2’s free choice variables are Z2 and z2, where F2 is determined by (1).
In (4) the term \( {\left({Z}_i-{z}_i\right)}^{\alpha_i} \) for player i’s stockpiled zero-days Zi − zi requires further interpretation. Especially, the expected utility of stockpiling comprises time discounting of the future expected utility of attack, since that is what stockpiling is for. The future expected utility of attack depends on the players’ time discounting, future available strategies, future cyber resources and budgets, and future asset valuations, contest intensities, and Cobb Douglas output elasticities. Equation (4) makes a first step towards modeling this complex phenomenon of stockpiling by abstracting away and compressing the time considerations and other considerations into one strategic choice and one parameter. The strategic choice is Zi − zi, i.e. how much to stockpile. Evidently, more stockpiling enables a larger attack at some future time. The parameter is αi, i.e. the Cobb Douglas output elasticity for player i’s stockpiled non-used zero-days Zi − zi, which contains ample information. First, αi weighs stockpiling relative to the two other ingredients, μi for defending its own asset and 1 − αi − μi for attacking the opponent’s asset, in the Cobb Douglas expected utility. Second, αi, 0 ≤ αi ≤ 1, specifies the degree of concavity imposed on Zi − zi which implicitly accounts for the plethora of phenomena mentioned above, including time discounting of the future expected utility of attack. Future research may model strategic interaction through time to account for the various aspects of stockpiling. This article confines attention to \( {\left({Z}_i-{z}_i\right)}^{\alpha_i} \) for stockpiling, which player i weighs against defending its own asset with defense effort Fi and attacking the opponent’s asset with zi.
3 Methodology
3.1 First Order Conditions
Differentiating player i’s expected utility in (4) with respect to its two free choice variables Zi and zi, and equating with zero, gives the first order conditions
3.2 Analytical Solution for Equivalent Players
Equation (5) is analytically solvable for v = w = 1 and equivalent players where Ri = R, ai = a, bi = b, αi = α, μi = μ, Zi = Z, zi = z, i = 1, 2, which is inserted into (5) to yield the two first order conditions
which are solved to yield the equilibrium strategies and expected utilities
where F1 and F2 are determined by (1).
3.3 Analytical Solution for Equivalent Players when α = μ = 1/3
Inserting α = μ = 1/3 into (6) gives
The Hessian matrix for player 1, inserting (8), is negative semi-definite, i.e.
The Hessian matrix for player 2 is equivalent to (9), except that V1 is replaced with W2, W1 is replaced with V2, Z1 is replaced with Z2, z1 is replaced with z2, U1 is replaced with U2, and H1 is replaced with H2.
3.4 Property for Equivalent Players when α = μ = 1/3
-
Property 1. For v = w = 1 and the symmetric event in (8) where Ri = R, ai = a, bi = b, αi = α, μi = μ, Zi = Z, zi = z, i = 1, 2, \( \frac{\partial {Z}_i}{\partial {a}_i}\le 0 \),\( \frac{\partial {Z}_i}{\partial {b}_i}\le 0 \), \( \frac{\partial {Z}_i}{\partial {R}_i}\ge 0 \), \( \frac{\partial {Z}_i}{\partial {V}_i}=0 \), \( \frac{\partial {Z}_i}{\partial {W}_i}=0 \), \( \frac{\partial {z}_i}{\partial {a}_i}\le 0 \),\( \frac{\partial {z}_i}{\partial {b}_i}\le 0 \), \( \frac{\partial {z}_i}{\partial {R}_i}\ge 0 \),\( \frac{\partial {z}_i}{\partial {V}_i}=0 \), \( \frac{\partial {z}_i}{\partial {W}_i}=0 \), \( \frac{\partial \left({Z}_i-{z}_i\right)}{\partial {a}_i}=0 \), \( \frac{\partial \left({Z}_i-{z}_i\right)}{\partial {b}_i}\le 0 \), \( \frac{\partial \left({Z}_i-{z}_i\right)}{\partial {R}_i}\ge 0 \), \( \frac{\partial \left({Z}_i-{z}_i\right)}{\partial {V}_i}=0 \), \( \frac{\partial \left({Z}_i-{z}_i\right)}{\partial {W}_i}=0 \), \( \frac{\partial {U}_i}{\partial {a}_i}\le 0 \) when a ≥ b, \( \frac{\partial {U}_i}{\partial {b}_i}\le 0 \), \( \frac{\partial {U}_i}{\partial {V}_i}\ge 0 \), \( \frac{\partial {U}_i}{\partial {W}_i}\ge 0 \).
-
Proof. Appendix 2. □.
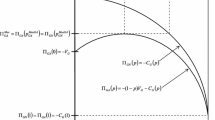
Property 1 states that for v = w = 1 and in the symmetric event in (8) where Ri = R, ai = a, bi = b, αi = α, μi = μ, Zi = Z, zi = z, i = 1, 2, each equivalent player i’s effort Zi to develop zero-day capabilities, and each player i’s part zi of zero-day capabilities used in the attack, decreases as each player’s unit effort cost ai of defense, and unit effort cost bi of developing zero-day capabilities, increase. Player i’s allocation Zi − zi to stockpiling decreases in bi and is independent of ai. Furthermore, Zi, zi, and Zi − zi increase as player i’s resources Ri increase, and are independent of the asset valuations Vi and Wi.
Player i’s expected utility Ui decreases as each player’s unit effort cost ai of defense increases, provided that ai ≥ bi, and increases when ai increases provided that ai < bi, i.e. is inverse U shaped as ai varies. This latter result follows since low ai < bi means that defense is cheap, which causes more resources Ri to be allocated to exert effort Zi to develop zero-day capabilities and more effort zi to attack. Such costly attacks cause low expected utility Ui which increases as ai increases to ai = bi. As ai increases above ai = bi, the opposite impact takes over. That is, although attacks zi decrease, defense Fi decrease even more, causing each player to suffer from the attacks and receive decreasing expected utility Ui as ai increases. Finally, player i’s expected utility Ui decreases as each player’s unit effort cost bi of developing zero-day capabilities increases, and increases as its resources Ri and asset valuations Vi and Wi increase.
4 Analysis and Discussion
Figure 2 illustrates the solution with the benchmark parameter values Ri = ai = bi = Vi= Wi = v = w = 1, αi = μi = 1/3, i = 1, 2, which causes the symmetric event in (8) with solution Z1 = Z2 = 3/4, z1 = z2 = F1 = F2 = 1/4, U1 = U2 = 1/2. Given that choices have to be made for the parameter values, we believe that e.g. V1 = V2 = W1= W2 = 1 are the most plausible choices for the four asset valuations. We have chosen unitary parameter values whenever possible. Hence at the benchmark each player i’s allocation Zi − zi = 1/2 of zero-day capabilities to stockpiling is twice as large as its allocation zi = 1/4 to attack. This follows since in (4) allocation Zi − zi to stockpiling appears as a proportional term, whereas allocations zi to attack and Fi to defense appear in the numerator and denominator of two ratio terms. In each of the nine panels one parameter value varies, while the other parameter values are kept at their benchmarks.
In Figure 2 panel a, as player 1’s cyber resources R1 increase from R1 = 0, intuitively, its effort Z1 to develop zero-day capabilities, its part z1 of zero-day capabilities used in the attack, its defense effort F1, and its expected utility U1, all increase, \( \underset{R_1\longrightarrow \infty }{\lim }{Z}_1=\underset{R_1\longrightarrow \infty }{\lim }{z}_1= \) \( \underset{R_1\longrightarrow \infty }{\lim }{F}_1= \) \( \underset{R_1\longrightarrow \infty }{\lim }{U}_1=\infty \). The limit values are determined numerically or, in rare instances, analytically. In contrast, player 2’s effort Z2 to develop zero-day capabilities decreases convexly from Z2 = 1 when R1 = 0, and asymptotically towards \( \underset{R_1\longrightarrow \infty }{\lim }{Z}_2=2/3 \). Player 2’s part z2 of zero-day capabilities used in the attack, and its defense effort F2, increase concavely from z2 = F2 = 0 when R1 = 0, and asymptotically towards \( \underset{R_1\longrightarrow \infty }{\lim }{z}_2=\underset{R_1\longrightarrow \infty }{\lim }{F}_2=1/3 \). When R1 is negligible, it is sufficient for the superior player 2 to allocate negligibly to defense F2 and attack z2. Player 2’s limit values reflect that player 2 allocates its resources R2 = 1 equally to stockpiling Z2 − z2 = 1/3, defense\( \underset{R_1\longrightarrow \infty }{\lim }{F}_2=1/3 \), and attack \( \underset{R_1\longrightarrow \infty }{\lim }{z}_2=1/3 \). Consequently, player 2’s expected utility U2 decreases from U2 = 1 when R1 = 0, and asymptotically towards \( \underset{R_1\longrightarrow \infty }{\lim }{U}_2=0 \), as it becomes increasingly inferior to player 1’s possession of superior cyber resources.
In Figure 2 panel b, as player 1’s unit defense effort a1 increases from a1 = 0, its defense effort F1 decreases convexly from infinity towards the limit \( \underset{a_1\longrightarrow \infty }{\lim }{F}_1=0 \), as defense becomes more costly. Interestingly, this makes player 2’s part z2 of zero-day capabilities used in the attack increasingly superior, causing z2 to decrease convexly from z2 = 0.389 when a1 = 0, and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{z}_2=0 \), as player 2 does not need to spend excessive resources on the attack. This remarkable de-escalating result for player 1’s asset has implications for external actors and technological and other factors which may somehow impact player 1’s unit defense effort a1 (which is a parameter in this article). That is, increasing a1 causes both F1 and z2 to decrease. Player 1’s F1 decreases most as it becomes more inferior. Player 2’s z2 decreases least as it becomes more superior. A consequence of decreasing z2 is that player 2’s effort Z2 to develop zero-day capabilities also decreases convexly from Z2 = 0.777 when a1 = 0, and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{Z}_2=0.701 \). Player 1’s effort Z1 to develop zero-day capabilities decreases convexly from Z1 = 1 when a1 = 0, and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{Z}_1=0.611 \), as it allocates more resources to defense F1. Similarly, its part z1 of zero-day capabilities used in the attack also decreases convexly, from z1 = 0.299 when a1 = 0, and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{z}_1=0.223 \). That is, player 1 attacks less when a1 increases since defense F1 becomes more costly. This also remarkable result means that higher a1 causes player not only to choose lower defense F1, but also to become so inferior that it attacks less. Player 2 takes advantage of the increasing a1. Its defense effort F2 increases slightly and concavely from F2 = 0.223 when a1 = 0, and towards \( \underset{a_1\longrightarrow \infty }{\lim }{F}_2=0.299 \). Hence, out of the four defense and attack variables F1, z2, z1, F2, increasing player 1’s unit defense effort a1 causes the three former to decrease, and the latter to increase slightly. Consequently, player 2’s expected utility U2 increases concavely from U2 = 0 when a1 = 0 (and player 1 is superior), and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{U}_2=0.738 \), as player 2 becomes increasingly superior to player 1. In contrast, player 1’s expected utility U1 decreases convexly from U1 = 0.738 when a1 = 0, and asymptotically towards \( \underset{a_1\longrightarrow \infty }{\lim }{U}_1=0 \), as it becomes increasingly inferior to player 2.
In Figure 2 panel c, as player 1’s unit effort cost b1 of developing zero-day capabilities increases from b1 = 0, its effort Z1 to develop zero-day capabilities decreases convexly from infinity towards \( \underset{b_1\longrightarrow \infty }{\lim }{Z}_1=0 \), as development becomes more costly. Concomitantly, its part z1 of zero-day capabilities used in the attack also decreases convexly from infinity towards the limit \( \underset{b_1\longrightarrow \infty }{\lim }{z}_1=0 \), as its attack becomes constrained from above by its decreasing Z1. This makes player 2’s defense F2 increasingly superior, causing F2 to decrease convexly from F2 = 0.388 when b1 = 0, and asymptotically towards \( \underset{b_1\longrightarrow \infty }{\lim }{F}_2=0 \), as player 2 does not need to spend excessive resources on the defense. Decreasing F2 for player 2 implies increasing Z2 according to (1). Accordingly, player 2’s effort Z2 to develop zero-day capabilities increases concavely from Z2 = 0.612 when b1 = 0, and asymptotically towards \( \underset{b_1\longrightarrow \infty }{\lim }{Z}_2=1 \). Concomitantly, its part z2 of zero-day capabilities used in the attack also increases slightly and concavely, from z2 = 0.223 when b1 = 0, towards the limit \( \underset{b_1\longrightarrow \infty }{\lim }{z}_2=0.299 \), as more zero-day capabilities Z2 become available. Player 1 does its best to counter the slightly increasing attack z2, but cannot overcome is inferiority, so that its defense F1 decreases slightly from F1 = 0.299 when b1 = 0, and towards \( \underset{b_1\longrightarrow \infty }{\lim }{F}_1=0.223 \). Consequently, player 2’s expected utility U2 increases concavely from U2 = 0 when b1 = 0 (and player 1 is superior), and asymptotically towards \( \underset{b_1\longrightarrow \infty }{\lim }{U}_2=0.734 \) as player 2 becomes increasingly superior to player 1. In contrast, player 1’s expected utility U1 decreases convexly from infinity, i.e. \( \underset{b_1\longrightarrow 0}{\lim }{U}_1=\infty \) when b1 → 0, and asymptotically towards \( \underset{b_1\longrightarrow \infty }{\lim }{U}_1=0 \), as it becomes increasingly inferior to player 2.
In Figure 2 panel d, increasing player 1’s valuation V1 of its own asset causes its own expected utility U1 to increase concavely from U1 = 0 when V1 = 0, towards infinity, \( \underset{V_1\longrightarrow \infty }{\lim }{U}_1=\infty \). The other seven variables remain at their benchmarks.
In Figure 2 panel e, increasing player 1’s valuation W1 of player 2’s asset causes its own expected utility U1 to increase concavely from U1 = 0 when W1 = 0, towards infinity, \( \underset{W_1\longrightarrow \infty }{\lim }{U}_1=\infty \). The other seven variables remain at their benchmarks.
In Figure 2 panel f, increasing the contest intensity v over player 1’s asset from zero makes the contest between player 1’s defense F1 and player 2’s attack z2 increasingly contested. At the benchmark v = 1, these variables are F1 = z2 = 1/4. As v increases above v = 1, the variables F1 and z2 increase above their benchmarks, as is commonly the case for increasing contest intensity. Furthermore, F1 and z2 increase equivalently since the players are equally advantaged at the benchmark, and also equally advantaged as v varies outside the benchmark. Consequently, \( \underset{v\longrightarrow \infty }{\lim }{F}_1=\underset{v\longrightarrow \infty }{\lim }{z}_2=1 \), which means that at the limit with infinitely large contest intensity v over player 1’s asset, player 1 allocates all its resources R1 = 1 to defense F1, while player 2 allocates all its resources R2 = 1 to attack z2. To furnish its attack z2, player 2 must allocate sufficient resources to its effort Z2 to develop zero-day capabilities. Hence increasing v causes Z2 to increase more rapidly than z2, \( \underset{v\longrightarrow \infty }{\lim }{Z}_2=1 \). Consequently, at the limit when v approaches infinity, player 1 allocates no resources R1 to develop zero-day capabilities, \( \underset{v\longrightarrow \infty }{\lim }{Z}_1=0 \), and player 2 allocates no resources R2 to defend its asset, \( \underset{v\longrightarrow \infty }{\lim }{F}_2=0 \). Hence also, \( \underset{v\longrightarrow \infty }{\lim }{z}_1=0 \), since player 1 at the limit when v approaches infinity cannot attack with zero-day capabilities z1 when it has not developed zero-day capabilities Z1. The dismal result at the limit when v approaches infinity is that both players receive zero expected utilities, \( \underset{v\longrightarrow \infty }{\lim }{U}_1=\underset{v\longrightarrow \infty }{\lim }{U}_2=0 \). This result is consistent with (1) since the results above imply that the first term on the right hand side of both expected utility equations approaches zero, \( \underset{v\longrightarrow \infty }{\lim }{\left({Z}_i-{z}_i\right)}^{\alpha_i}=0 \), i = 1, 2. As v approaches zero, the limits are different. First, decreasing contest intensity v over player 1’s asset makes that contest more egalitarian so that efforts matter less. Hence the players exert no efforts at the limit when v = 0, i.e. no defense \( \underset{v\longrightarrow 0}{\lim }{F}_1=0 \) for player 1 and no attack \( \underset{v\longrightarrow 0}{\lim }{z}_2=0 \) for player 2. In the beginning of this section we observed that at the benchmark when v = 1 each player i’s allocation Zi − zi = 1/2 of zero-day capabilities to stockpiling is twice as large as its allocation zi = 1/4 to attack and Fi = 1/4 to defense. This same ratio 2/1 also occurs when v = 0. Since \( \underset{v\longrightarrow 0}{\lim }{F}_1=0 \) for player 1, the ratio 2/1 between stockpiling and attack is preserved by allocating \( \underset{v\longrightarrow 0}{\lim }{Z}_1-{z}_1=2/3 \) to stockpiling and \( \underset{v\longrightarrow 0}{\lim }{z}_1=1/3 \) to attack, i.e. \( \underset{v\longrightarrow 0}{\lim }{Z}_1=1 \) since player 1 allocates all its resources R1 to develop zero-day capabilities. Since \( \underset{v\longrightarrow 0}{\lim }{z}_2=0 \) for player 2, the ratio 2/1 between stockpiling and defense is preserved by allocating \( \underset{v\longrightarrow 0}{\lim }{Z}_2-{z}_2=2/3 \) to stockpiling and \( \underset{v\longrightarrow 0}{\lim }{F}_2=1/3 \) to defense, i.e. \( \underset{v\longrightarrow 0}{\lim }{Z}_2=2/3 \). This asymmetry between player 1 and player 2 follows since the contest intensity is v = 0 for the asset player 1 defends and player 2 attacks, while w = 1 for the asset player 1 attacks and player 2 defends. The asymmetry does not cause different expected utilities for the players. Inserting the variables above into (4) when v = 0 gives \( \underset{v\longrightarrow 0}{\lim }{U}_1=\underset{v\longrightarrow 0}{\lim }{U}_2=1/\sqrt[3]{6}\approx 0.550 \). That is, the players’ expected utilities are highest with zero contest intensity v = 0 over player 1’s asset.
In Figure 2 panel g, the results are analogous to panel f, but with interchanged variables since the contest intensity that varies is w over player 2’s asset. Hence, interchanging \( \underset{w\longrightarrow \infty }{\lim }{F}_2=\underset{w\longrightarrow \infty }{\lim }{z}_1=\underset{w\longrightarrow \infty }{\lim }{Z}_1=1 \), \( \underset{w\longrightarrow \infty }{\lim }{Z}_2=\underset{w\longrightarrow \infty }{\lim }{F}_1=\underset{w\longrightarrow \infty }{\lim }{z}_2=\underset{w\longrightarrow \infty }{\lim }{U}_1=\underset{w\longrightarrow \infty }{\lim }{U}_2=\underset{w\longrightarrow \infty }{\lim }{\left({Z}_i-{z}_i\right)}^{\alpha_i}=0 \), i = 1, 2, \( \underset{w\longrightarrow 0}{\lim }{F}_2=\underset{w\longrightarrow 0}{\lim }{z}_1=0 \), \( \underset{w\longrightarrow 0}{\lim }{Z}_2=1 \), \( \underset{w\longrightarrow 0}{\lim }{z}_2= \) \( \underset{w\longrightarrow 0}{\lim }{F}_1=1/3 \), \( \underset{w\longrightarrow 0}{\lim }{Z}_1=\underset{w\longrightarrow 0}{\lim }{\left({Z}_i-{z}_i\right)}^{\alpha_i}=2/3,i=1,2 \), \( \underset{w\longrightarrow 0}{\lim }{U}_1=\underset{w\longrightarrow 0}{\lim }{U}_2=1/\sqrt[3]{6}\approx 0.550. \)
In Figure 2 panel h, decreasing the Cobb Douglas output elasticity α1 for player 1’s stockpiled non-used zero-days Z1 − z1 to zero gives \( \underset{\alpha_1\longrightarrow 0}{\lim }{Z}_1=\underset{\alpha_1\longrightarrow 0}{\lim }{z}_1=0.616 \). This result follows from the term \( {\left({Z}_1-{z}_1\right)}^{\alpha_1} \) in (4) which gives no value to player 1 of storing zero-days when α1 = 0. As α1 increases above α1 = 0, player 1 gets increasing expected utility U1 from stockpiling, accomplished by increasing its effort Z1 to develop zero-day capabilities, and decreasing its part z1 of zero-day capabilities used in the attack. This decrease continues until z1 = 0 when α1 = 2/3, which causes 1 − α1 − μ1 = 0 (since μ1 = 1/3), and hence an egalitarian contest over player 2’s asset which causes no need for the players to exert efforts z1 and F2 and hence \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{F}_2=\underset{\alpha_1\longrightarrow 2/3}{\lim }{z}_1=0 \), to the advantage of player 2 who wins the contest. Player 1 eventually earns increased expected utility U1 from stockpiling as α1 increases. Hence, as z1 decreases, player 1 increases its effort Z1 to develop zero-day capabilities moderately towards a maximum, and thereafter slightly decreases Z1 due to decreasing return on investment, finally causing \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{Z}_1=0.777 \). Consistently with concavely increasing (and eventually slightly decreasing) Z1 is convexly decreasing (and eventually slightly increasing) defense effort F1 for player 1 of its own asset, from \( \underset{\alpha_1\longrightarrow 0}{\lim }{F}_1=0.384 \) to \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{F}_1=0.223 \). The overall result for player 1 is U shaped expected utility U1 with minimum U1 = 0.499 for α1 = 0.294, a maximum \( \underset{\alpha_1\longrightarrow 0}{\lim }{U}_1=0.647 \) for α1 = 0, and a high value \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{U}_1=0.636 \) for α1 = 2/3. This interesting result means that when player 2 has the Cobb Douglas output elasticities α1 = μ1 = 1/3, and player 1 has Cobb Douglas output elasticity μ1 = 1/3 for when defending its own asset, then player 1 prefers to avoid intermediate Cobb Douglas output elasticity α1 = 0.294 for storing its zero-days Z1 − z1. Player 2’s prefers zero attack z1 = 0 by player 1, which occurs when α1 = 2/3. Then player 2 can choose \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{F}_2=0 \) due to being advantaged with respect to its own asset. That, in turn, enables player 2 to allocate all its resources R2 to exert effort Z2 to develop zero-day capabilities, i.e. \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{Z}_2=1 \), and to attack player 1 with \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{z}_2=0.299 \), which gives player 2 its highest expected utility \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{U}_2=0.738 \). That is, player 2 is advantaged with respect to its own asset, and strikes a balance between storing zero-days, Z2 − z2, and attacking player 1 with z2. As α1 decreases below α1 = 2/3, player 1’s attack z1 increases above zero, causing player 2’s defense F2 to increase above zero, eventually reaching \( \underset{\alpha_1\longrightarrow 0}{\lim }{F}_2=0.297 \). Consequently, player 2’s effort Z2 to develop zero-day capabilities decreases, eventually reaching \( \underset{\alpha_1\longrightarrow 0}{\lim }{Z}_2=0.703 \). Player 2’s attack z2 is relatively constant (has a very weak U shape), eventually reaching \( \underset{\alpha_1\longrightarrow 0}{\lim }{z}_2=0.262 \), since it still prefers to attack player 1, and accepts allocating less, Z2 − z2, to stockpiling. The overall result for player 2 is decreasing expected utility U1 as α1 decreases, eventually causing \( \underset{\alpha_1\longrightarrow 0}{\lim }{U}_2=0.388 \). In other words, when only α1 varies from the given benchmark, player 2 prefers not to be attacked, z1 = 0, which occurs for maximum α1 = 2/3. This maximum α1 = 2/3 is also relatively preferable for player 1 which then receives good expected utility U1 from storing all its produced zero-days, \( \underset{\alpha_1\longrightarrow 2/3}{\lim }{z}_1=0 \). However, player 1 receives slightly higher expected utility U1 when α1 = 0 when the attack \( \underset{\alpha_1\longrightarrow 0}{\lim }{Z}_1=\underset{\alpha_1\longrightarrow 0}{\lim }{z}_1=0.616 \) is substantial.
In Figure 2 panel i, increasing the Cobb Douglas output elasticity μ1 for player 1’s contest success when defending its own asset to its maximum μ1 = 2/3, which causes 1 − α1 − μ1 = 0 (since α1 = 1/3), causes an egalitarian contest over player 2’s asset (as in panel h) which causes no need for the players to exert efforts z1 and F2 and hence \( \underset{\mu_1\longrightarrow 2/3}{\lim }{F}_2=\underset{\mu_1\longrightarrow 2/3}{\lim }{z}_1=0 \), to the advantage of player 2 who wins the contest. Hence also (as in panel h), since player 2 allocates no resources R2 to defense F2 when μ1 = 2/3, it allocates all its resources R2 to exert effort Z2 to develop zero-day capabilities, i.e. \( \underset{\mu_1\longrightarrow 2/3}{\lim }{Z}_2=1 \), and to attack player 1 substantially with \( \underset{\mu_1\longrightarrow 2/3}{\lim }{z}_2=0.361 \), which gives player 2 its highest expected utility \( \underset{\mu_1\longrightarrow 2/3}{\lim }{U}_2=0.653 \). Player 1 responds by defending substantially, \( \underset{\mu_1\longrightarrow 2/3}{\lim }{F}_1=0.466 \). Hence player 1 can allocate less resources R1 to exert effort Z1 to develop zero-day capabilities, \( \underset{\mu_1\longrightarrow 2/3}{\lim }{Z}_1=0.534 \), receiving expected utility \( \underset{\mu_1\longrightarrow 2/3}{\lim }{U}_1=0.554 \). Decreasing μ1 below μ1 = 2/3 causes the contest over player 1’s asset to become more egalitarian so that effort z2 by player 2 to attack it and effort F1 by player 1 to defend it have less impact and eventually no impact, i.e. \( \underset{\mu_1\longrightarrow 0}{\lim }{z}_2=\underset{\mu_1\longrightarrow 0}{\lim }{F}_1=0 \). Thus player 2 also allocates less resources R2 to exert effort Z2 to develop zero-day capabilities, which decreases to \( \underset{\mu_1\longrightarrow 0}{\lim }{Z}_2=0.639 \). In contrast, player 1 increases its effort Z1 to develop zero-day capabilities, eventually allocating all its resources R1 to it, i.e. \( \underset{\mu_1\longrightarrow 0}{\lim }{Z}_1=1 \). Thus player 1 also allocates more resources R1 to attack player 2 with z1, which increases to \( \underset{\mu_1\longrightarrow 0}{\lim }{z}_1=0.466 \). Player 2 responds by defending its asset more with F2, which increases to \( \underset{\mu_1\longrightarrow 0}{\lim }{F}_2=0.361 \). Especially interesting in panel i is the symmetry around μ1 = 1/3 which did not arise around α1 = 1/3 in panel h for player 1’s stockpiled non-used zero-days Z1 − z1. The reason is that increasing (decreasing) the Cobb Douglas output elasticity μ1 for player 1’s contest success around μ1 = 1/3 causes equivalent decrease (increase) of the Cobb Douglas output elasticity μ1 for player 1’s contest success around 1 − α1 − μ1 = 0 when α1 = 1/3. Hence \( \underset{\mu_1\longrightarrow 0}{\lim }{z}_1=\underset{\mu_1\longrightarrow 2/3}{\lim }{F}_1=0.466 \) and \( \underset{\mu_1\longrightarrow 2/3}{\lim }{z}_2=\underset{\mu_1\longrightarrow 0}{\lim }{F}_2=0.361 \). The impact on the players’ expected utilities is also symmetric so that each player is indifferent regarding its preference for the extreme values μ1 = 0 and μ1 = 2/3, i.e. \( \underset{\mu_1\longrightarrow 0}{\lim }{U}_1=\underset{\mu_1\longrightarrow 2/3}{\lim }{U}_1=0.554 \) and \( \underset{\mu_1\longrightarrow 0}{\lim }{U}_2=\underset{\mu_1\longrightarrow 2/3}{\lim }{U}_2=0.653 \). Player 2’s expected utility U2 is larger than player 1’s expected utility U1 at μ1 = 0 and μ1 = 2/3 since player 1 exerts higher costly efforts \( \underset{\mu_1\longrightarrow 0}{\lim }{z}_1=\underset{\mu_1\longrightarrow 2/3}{\lim }{F}_1=0.466 \) than \( \underset{\mu_1\longrightarrow 2/3}{\lim }{z}_2=\underset{\mu_1\longrightarrow 0}{\lim }{F}_2=0.361 \) for player 2. At the midpoint benchmark value μ1 = 1/3, as we know from the first paragraph of this section, the players receive their equal minimum expected utilities U1 = U2 = 1/2.
5 Conclusion
A model is developed for two players (e.g. countries) which allocate resources to defend against zero-day attacks, and to produce zero-day exploits for attack and stockpiling. Each player also defends against zero-day cyber attacks. First, using one part of one’s resources to build up a defense infrastructure to handle attacks or potential attacks is useful. Second, using the remaining part of one’s resources to produce zero-day capabilities is useful. This illustrates a balance or tradeoff that has to be struck between defense and production. Third, the produced zero-day exploits can be stockpiled, or can be used in attacking the opposing player, both of which are useful. This article determines each player’s optimal strategy by applying the common Cobb Douglas expected utility function while accounting for three inputs; the production of zero-day exploits for stockpiling, production for attack, and defense.
For equivalent players an analytical solution is determined. When, additionally, production for attack and stockpiling, and defense, are valued equally in the Cobb Douglas expected utility function, a property is developed showing, for example, that each player’s expected utility is inverse U shaped in each player’s unit effort cost of defense.
For different players the solution is illustrated with simulations where each of nine parameters are varied for player 1, without loss of generality, relative to a plausible benchmark where production for stockpiling and the contests for attack and defense are valued one third each. First, increasing player 1’s resources causes all its efforts (production, attack, defense) and its expected utility to increase towards infinity. In contrast, player 2’s expected utility decreases towards zero, its production decreases convexly towards a constant, and its attack and defense increase concavely towards a constant.
Second, increasing player 1’s unit defense cost causes its defense and expected utility to decrease to zero due to inferiority, while its production and attack decrease towards constants. Player 2 decreases its production and attack somewhat due to superiority, defends marginally more, and receives increasing expected utility. Importantly, both players’ attacks decrease, due to inferiority and superiority, respectively. This counterintuitive result, that making defense more expensive could decrease overall attacks and potentially deescalate conflict, warrants future exploration. For example, it raises the issue of whether the players themselves, external players, or technological innovation, can influence the players’ unit defense costs.
Third, increasing player 1’s unit development cost of zero-day capabilities causes its production, attack, and expected utility to decrease to zero, while its defense increases marginally towards a constant. Player 2 decreases its defense to zero due to superiority, which enables it to increase its production and attack towards constants, causing increasing expected utility towards a constant. This more intuitive result means that increasing a player’s unit development cost causes that player to attack less and the opposing player to attack more.
Fourth and fifth, increasing player 1’s valuation of its own asset, or player 2’s asset, causes its expected utility to increase to infinity, while the other variables remain at their benchmarks.
Sixth, increasing the contest intensity over player 1’s asset causes player 1’s defense and player 2’s attack to increase until all their resources are exploited, eventually approaching zero expected utility to both players. Player 1’s production and attack decrease towards zero, and player 2’s production and attack increase until all its resources are exploited.
Seventh, increasing the contest intensity over player 2’s asset causes the same result as when increasing the contest intensity over player 1’s asset, except that the two players’ roles are interchanged. That is, production and attack for one player is interchanged with defense for the other player, and vice versa.
Eighth, decreasing the Cobb Douglas output elasticity for player 1’s stockpiled zero-days to zero causes its attack to increase to equal its production, since stockpiling is useless. Its defense increases somewhat, and its expected utility reaches its maximum. In contrast, player 2 suffers the attack and receives its minimum expected utility. Increasing the same elasticity to its maximum causes player 1 not to attack, which also gives it high expected utility, compared to intermediate elasticity, while player 2 receives its maximum expected utility due to not being attacked.
Ninth, decreasing the Cobb Douglas output elasticity for player 1’s contest success when defending its own asset to zero eliminates its useless defense, causes intermediate attack, and maximum production and expected utility. Player 2 also receives maximum expected utility for zero elasticity due to not spending resources on attack. Maximum elasticity eliminates player 1’s useless attack, and both players receive their same maximum expected utilities as for zero elasticity.
Future research should incorporate the time dimension and complexity more thoroughly, making stockpiling a time discounted version of the future expected utility of attack and defense. Future research should also include more players and outside regulation, estimate the parameter values, and furnish empirical support from contemporary and historical records.
References
Arbatskaya, M., & Mialon, H. M. (2010). Multi-activity contests. Economic Theory, 43(1), 23–43. https://doi.org/10.1007/s00199-008-0424-y.
Baliga, S., de Mesquita, E. B., & Wolitzky, A. (2020). Deterrence with imperfect attribution. American Political Science Review. https://www.cambridge.org/core/journals/american-political-science-review/article/deterrence-with-imperfect-attribution/FAA1B972880D47696942E89628E81383.
Crossler, R., Bélanger, F., & Ormond, D. (2019). The quest for complete security: An empirical analysis of users’ multi-layered protection from security threats. Information Systems Frontiers, 21(2), 343–357. https://doi.org/10.1007/s10796-017-9755-1.
Do, C. T., Tran, N. H., Hong, C., Kamhoua, C. A., Kwiat, K. A., Blasch, E., et al. (2017). Game theory for cyber security and privacy. ACM Computing Surveys (CSUR), 50(2), 30.
Edwards, B., Furnas, A., Forrest, S., & Axelrod, R. (2017). Strategic aspects of cyberattack, attribution, and blame. Proceedings of the National Academy of Sciences, 201700442.
Enders, W., & Sandler, T. (2003). What Do we know about the substitution effect in transnational terrorism? In A. Silke & G. Ilardi (Eds.), Researching terrorism: Trends, achievements, failures. Frank Cass: Ilfords.
Hausken, K. (2006a). Income, interdependence, and substitution effects affecting incentives for security investment. Journal of Accounting and Public Policy, 25(6), 629–665. https://doi.org/10.1016/j.jaccpubpol.2006.09.001.
Hausken, K. (2006b). Returns to information security investment: The effect of alternative information security breach functions on optimal investment and sensitivity to vulnerability. Information Systems Frontiers, 8(5), 338–349.
Hausken, K. (2007). Information sharing among firms and cyber attacks. Journal of Accounting and Public Policy, 26(6), 639–688. https://doi.org/10.1016/j.jaccpubpol.2007.10.001.
Hausken, K. (2014). Returns to information security investment: Endogenizing the expected loss. Information Systems Frontiers, 16(2), 329–336.
Hausken, K. (2015). A strategic analysis of information sharing among cyber attackers. Journal of Information Systems and Technology Management, 12(2), 245–270. https://doi.org/10.4301/S1807-17752015000200004.
Hausken, K. (2017a). Information sharing among cyber hackers in successive attacks. International Game Theory Review, 19(2), 1750010, 33 pages. https://doi.org/10.1142/S0219198917500104.
Hausken, K. (2017b). Security investment, hacking, and information sharing between firms and between hackers. Games, 8(2), 23 pages. https://doi.org/10.3390/g8020023.
Hausken, K. (2018a). A cost-benefit analysis of terrorist attacks. Defence and Peace Economics, 29(2), 111–129. https://doi.org/10.1080/10242694.2016.1158440.
Hausken, K. (2018b). Proactivity and retroactivity of firms and information sharing of hackers. International Game Theory Review, 20(1), 1750027, 1750030 pages. https://doi.org/10.1142/S021919891750027X.
Hausken, K. (2020). Additive multi-effort contests. Theory and Decision, 89(2), 203–248. https://doi.org/10.1007/s11238-11020-09749-11231.
Hausken, K., & Levitin, G. (2008). Efficiency of even separation of parallel elements with variable contest intensity. Risk Analysis, 28(5), 1477–1486. https://doi.org/10.1111/j.1539-6924.2008.01090.x.
Hausken, K., & Levitin, G. (2012). Review of systems defense and attack models. International Journal of Performability Engineering, 8(4), 355–366.
Lakdawalla, D., & Zanjani, G. (2002). Insurance, self-protection, and the economics of terrorism. RAND and NBER, Federal Reserve Bank of New York.
Levitin, G., Hausken, K., Taboada, H. A., & Coit, D. W. (2012). Data Survivability vs. Security in Information Systems. Reliability Engineering & System Safety, 100, 19–27.
Miaoui, Y., & Boudriga, N. (2019). Enterprise security investment through time when facing different types of vulnerabilities. Information Systems Frontiers, 21(2), 261–300. https://doi.org/10.1007/s10796-017-9745-3.
Nagurney, A., & Shukla, S. (2017). Multifirm models of cybersecurity investment competition vs. cooperation and network vulnerability. European Journal of Operational Research, 260(2), 588–600.
Nakashima, E. (2012, June 2, 2012). Stuxnet was work of U.S. and Israeli experts, officials say. The Washington Post.
Roy, S., Ellis, C., Shiva, S., Dasgupta, D., Shandilya, V., & Wu, Q. (2010). A survey of game theory as applied to network security. Paper presented at the system sciences (HICSS), 2010 43rd Hawaii international conference on.
Trang, S., & Brendel, B. (2019). A meta-analysis of deterrence theory in information security policy compliance research. Information Systems Frontiers, 21(6), 1265–1284. https://doi.org/10.1007/s10796-019-09956-4.
Tullock, G. (1980). Efficient rent-seeking. In J. M. Buchanan, R. D. Tollison, & G. Tullock (Eds.), Toward a theory of the rent-seeking society (pp. 97–112). College Station: Texas A. & M. University Press.
Welburn, J. W., Grana, J., & Schwindt, K. (2019). Cyber deterrence or: How we learned to stop worrying and love the signal. Santa Monica: RAND National Security Research Division.
Xu, F., Luo, X., Zhang, H., Liu, S., & Huang, W. (2019). Do strategy and timing in IT security investments matter? An empirical investigation of the alignment effect. Information Systems Frontiers, 21(5), 1069–1083. https://doi.org/10.1007/s10796-017-9807-6.
Acknowledgements
Two anonymous referees of this journal are thanked for useful comments.
Funding
Open Access funding provided by the University of Stavanger.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix 1 Nomenclature
1.1 Parameters
- R i :
-
Player i’s cyber resources, i = 1, 2, Ri ≥ 0.
- a i :
-
Player i’s unit effort cost of defense, i = 1, 2, ai ≥ 0
- b i :
-
Player i’s unit effort cost of developing zero-day capabilities, i = 1, 2, bi ≥ 0
- V 1 :
-
Player 1’s valuation of its own asset, V1 ≥ 0
- V 2 :
-
Player 2’s valuation of player 1’s asset, V2 ≥ 0
- W 1 :
-
Player 1’s valuation of player 2’s asset, W1 ≥ 0
- W 2 :
-
Player 2’s valuation of its own asset, W2 ≥ 0
- v :
-
Contest intensity over player 1’s asset, v ≥ 0
- w :
-
Contest intensity over player 2’s asset, w ≥ 0
- α i :
-
Cobb Douglas output elasticity for player i’s stockpiled non-used zero-days Zi − zi, i = 1, 2, 0 ≤ αi ≤ 1
- μ i :
-
Cobb Douglas output elasticity for player i’s contest success when defending its own asset, i = 1, 2, 0 ≤ μi ≤ 1
- 1-αi -μi:
-
Cobb Douglas output elasticity for player i’s contest success when attacking its opponent’s asset, i = 1, 2, 0 ≤ 1− αi − μi ≤ 1
1.2 Strategic choice variables
- Z i :
-
Player i’s effort to develop zero-day capabilities, i = 1, 2
- z i :
-
Player i’s part of zero-day capabilities used in the attack, 0 ≤ zi ≤ Zi, i = 1, 2
1.3 Dependent variables
- F i :
-
Player i’s defense effort, i = 1, 2
- p i :
-
Player i’s expected contest success over its own asset, i = 1, 2
- q i :
-
Player i’s expected contest success over its opponent’s asset, i = 1, 2
- U i :
-
Player i’s expected utility, i = 1, 2
Appendix 2 Proof of Property 1
Differentiating (8) gives
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Hausken, K., Welburn, J.W. Attack and Defense Strategies in Cyber War Involving Production and Stockpiling of Zero-Day Cyber Exploits. Inf Syst Front 23, 1609–1620 (2021). https://doi.org/10.1007/s10796-020-10054-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10796-020-10054-z