Abstract
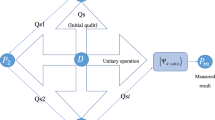
Quantum secret sharing is an important technology in quantum cryptography, and it is used in the fields of secure multiparty computation, quantum auction and fiber network configuration. In this paper, we construct two quantum secret sharing schemes with adversary structure by using three-qudit GHZ state and three qubits. In the proposed scheme, the dealer first generates the private keys based on the adversary structure, then the participants in authorized subset use their private keys to perform the unitary operations on the quantum state and recover the original secret. The security analysis shows the attacks of intercept-and-resend, entangle-and-measure and participant are impossible in our schemes. Compared with the existing quantum secret sharing schemes, we realize the sharing of classical information and quantum state, and need less computational cost. Moreover, our schemes are more efficient when the adversary structure can be obtained directly.




Similar content being viewed by others
Data Availability
All data generated or analysed during this study are included in the published article.
References
Gutub, A., Al-Juaid, N., Khan, E.: Counting-based secret sharing technique for multimedia applications. Multimed. Tools Appl. 78(5), 5591–5619 (2019)
AlKhodaidi, T., Gutub, A.: Trustworthy target key alteration helping counting-based secret sharing applicability. Arab. J. Sci. Eng. 45(4), 3403–3423 (2020)
Alkhodaidi, T., Gutub, A.: Scalable shares generation to increase participants of counting-based secret sharing technique. Int. J. Inf. Secur. 17(1-2), 119–146 (2022)
Al-Ghamdi, M., Al-Ghamdi, M., Gutub, A.: Security enhancement of shares generation process for multimedia counting-based secret-sharing technique. Multimed. Tools Appl. 78(12), 16283–16310 (2019)
Hureib, E., Gutub, A.: Enhancing medical data security via combining Elliptic Curve cryptography with 1-LSB and 2-LSB image steganography. Int. J. Comput. Sci. Net. Sec. 20(12), 232–241 (2020)
Gutub, A.: Boosting image watermarking authenticity spreading secrecy from counting-based secret-sharing. https://doi.org/10.1049/cit2.12093 (2022)
Kheshaifaty, N., Gutub, A.: Engineering graphical captcha and AES crypto hash functions for secure online authentication. https://doi.org/10.36909/jer.13761 (2021)
Al-Shaarani, F., Gutub, A.: Increasing participants using counting-based secret sharing via involving matrices and practical steganography. Arab. J. Sci. Eng. 47(2), 2455–2477 (2022)
Gutub, A.: Secure shares generation via M-Blocks partitioning for counting-based secret sharing. J. Eng. Res. 8(3), 91–117 (2020)
Al-Shaarani, F., Gutub, A.: Securing matrix counting-based secret-sharing involving crypto steganography. https://doi.org/10.1016/j.jksuci.2021.09.009 (2021)
Gutub, A., AlKhodaidi, T.: Smart expansion of target key for more handlers to access multimedia counting-based secret sharing. Multimed. Tools Appl. 79(25-26), 17373–17401 (2020)
Al-Juaid, N., Gutub, A.: Combining RSA and audio steganography on personal computers for enhancing security. SN Appl. Sci. 1, 830 (2019)
Gutub, A.: Regulating watermarking semi-authentication of multimedia audio via counting-based secret sharing. Pamukkale U J. Eng. Sci. 28(2), 324–332 (2022)
Shamir, A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Blakley, G. R.: Safeguarding Cryptographic Keys. In: AFIPS, p. 313. IEEE Computer Society (1979)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829–1834 (1999)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162–168 (1999)
Tokunaga, Y., Okamoto, T., Imoto, N.: Threshold quantum cryptography. Phys. Rev. A 71(1), 012314 (2005)
Tavakoli, A., Herbauts, I., Zukowski, M., Bourennane, M.: Secret sharing with a single d-level quantum system. Phys. Rev. A 92(R), 030302 (2015)
Karimipour, V., Asoudeh, M., Gheorghiu, V., Looi, S. Y., Griffiths, R. B.: Quantum secret sharing and random hopping: Using single states instead of entanglement. Phys. Rev. A 92(R), 030301 (2015)
Cleve, R., Gottesman, D., Lo, H. K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
Tyc, T., Sanders, B. C.: How to share a continuous-variable quantum secret by optical interferometry. Phys. Rev. A 65, 042310 (2002)
Li, B.K., Yang, Y.G., Wen, Q.Y.: Threshold quantum secret sharing of secure direct communication. Chin. Phys. Lett. 26(1), 010302 (2009)
Cao, H., Ma, W.: (t, n) threshold quantum state sharing scheme based on linear equations and unitary operation. IEEE Photonics J. 9, 1–7 (2017)
Yang, Y. H., Gao, F., Wu, X., Qin, S. J., Zuo, H. J., Wen, Q. Y.: Quantum secret sharing via local operations and classical communication. Sci. Rep. 5, 16967 (2015)
Sarvepalli, P. K., Klappenecker, A.: Sharing classical secrets with Calderbank-Shor-Steane codes. Phys. Rev. A 80, 022321 (2009)
Sarvepalli, P.: Nonthreshold quantum secret-sharing schemes in the graph-state formalism. Phys. Rev. A 86, 042303 (2012)
Wang, M. M., Chen, X. B., Yang, Y. X.: Quantum secret sharing for general access structures based on multiparticle entanglements. Quantum Inf. Process. 13, 429–443 (2014)
Bai, C. M., Li, Z. H., Li, Y. M.: Sequential quantum secret sharing using a single qudit. Commun. Theor. Phys. 69(5), 513–518 (2018)
Yang, W., Huang, L., Shi, R., He, L.: Secret sharing based on quantum Fourier transform. Quantum Inf. Process. 12, 2465–2474 (2013)
Qin, H., Dai, Y.: Verifiable (t, n) threshold quantum secret sharing using d-dimensional Bell state. Inf. Process. Lett. 116, 351–355 (2016)
Song, X., Liu, Y., Deng, H., Xiao, Y.: (t, n) Threshold d-level quantum secret sharing. Sci. Rep. 7, 6366 (2017)
Lu, C., Miao, F., Hou, J., et al.: Verifiable threshold quantum secret sharing with sequential communication. Quantum Inf Processing. 17(11), 310 (2018)
Mashhadi, S.: General secret sharing based on quantum Fourier transform. Quantum Inf. Process. 18, 114 (2019)
Sutradhar, K., Om, H.: Efficient quantum secret sharing without a trusted player. Quantum Inf. Process. 19 (2020)
Liu, L., Li, Z., Han, Z., et al.: A quantum secret sharing scheme with verifiable function. Eur. Phys. J.D 74 (2020)
Zhi, D. L., Li, Z. H., Han, Z. W., Liu, L. J.: Verifiable quantum secret sharing based on a single qudit. Int. J. Theor. Phys. 59(12), 3672–3684 (2020)
Bai, C., Zhang, S., Liu, L.: Verifiable quantum secret sharing scheme using d-dimensional GHZ state. Int. J. Theor. Phys. 60(10), 3993–4005 (2021)
Kao, S. H., Hwang, T.: Comment on (t,n) threshold d-level quantum secret sharing. arXiv:1803.00216v1 (2018)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett 83(3), 648–651 (1999)
Qin, H., Zhu, X., Dai, Y.: (t, n) Threshold quantum secret sharing using the phase shift operation. Quantum Inf. Process. 14(8), 2997 (2015)
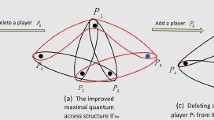
Qin, H., Dai, Y.: d-Dimensional quantum state sharing with adversary structure. Quantum Inf. Process. 15, 1689–1701 (2016)
Lu, C., Miao, F., Meng, K., et al.: Threshold quantum secret sharing based on single qubit. Quantum Inf. Process. 17 (2018)
Qin, H., Tso, R., Dai, Y.: Multi-dimensional quantum state sharing based on quantum Fourier transform. Quntum Inf. Process. 17, 48 (2018)
Li, F., Yan, J., Zhu, S.: General quantum secret sharing scheme based on two qudit. Quantum Inf Processing. 20(10), 1–19 (2021)
Malkhi, D., Reiter, M.K.: Byzantine quorum systems. Distributed Comput 11(4), 203–213 (1998)
Hirt, M., Maurer, U.: Player simulation and general adversary structures in perfect multiparty computation. Journal of Cryptology. 13(1), 31–60 (2000)
Cai, Q. Y., Li, W. B.: Deterministic secure communication without using entanglement. Chin. Phys. Lett. 21, 601–603 (2004)
Deng, F. G., Long, G. L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69, 052319 (2004)
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grant No. U21A20428 and No. 12171134.
Ethics declarations
Competing interests
The authors declare that they have no conflicts of interest to this work.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wu, T., Zhu, S., Li, F. et al. Two Quantum Secret Sharing Schemes with Adversary Structure. Int J Theor Phys 61, 206 (2022). https://doi.org/10.1007/s10773-022-05176-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05176-w