Abstract
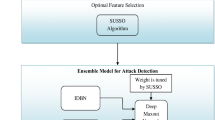
Utilizing the cloud environment is one of the most preferable option in every information technology (IT) organization for running its business due to its flexible nature of services for its users. Cloud computing is vulnerable to various types of known and unknown attacks due to its distributed nature and open architecture. Hence, privacy and security is a primary concern of the cloud computing environment. A lot of machine learning approaches are utilized to improve the accuracy of Intrusion detection system (IDS) but dealing with redundant and non-relevant datasets with a large number of attributes (multi-dimensional) is still a problem. In this study, better and fast IDS has been proposed to detect anomaly for the cloud network environment which uses Improved squirrel search algorithm (ISSA) and Modified-deep belief network (MDBN) on the UNSW-NB15 dataset. ISSA extracts the relevant features from a set of features to deal with network traffic data of high dimension. It selects the relevant and optimal feature subset to be utilized for the training process and testing process. Meanwhile, a MDBN is introduced which uses the extracted features for anomaly detection for binary class classification and multi class classification. MDBN also helps to deal with the unbalanced nature of the dataset. The proposed IDS model has been evaluated based on the statistical measures namely accuracy, false alarm rate (FAR) and execution time, which are the popular parameters for evaluation of an IDS model. The proposed ISSA-MDBN model for IDS reduces the training from 103.51 to 0.108 s and testing time from 29.62 to 0.054 s on the UNSW-NB15 dataset. The proposed IDS model has been compared with other existing recent approaches and the proposed approach achieves the highest accuracy of 99.8% and lowest FAR of 0.02%.










Similar content being viewed by others
Data availability
Enquiries about data availability should be directed to the authors.
References
Wang, Z.: Deep learning-based intrusion detection with adversaries. IEEE Access 6, 38367–38384 (2018)
Xin, Y., Kong, L., Liu, Z., Chen, Y., Li, Y., Zhu, H., Gao, M., Hou, H., Wang, C.: Machine learning and deep learning methods for cybersecurity. IEEE Access 6, 35365–35381 (2018)
Ambusaidi, M.A., He, X., Nanda, P., Tan, Z.: Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Trans. Comput. 65(10), 2986–2998 (2016)
Moustafa, N., Slay, J., Unsw-nb15: a comprehensive data set for network intrusion detection systems (unsw-nb15 network data set). In: Military Communications and Information Systems Conference (MilCIS), pp. 1–6. IEEE (2015)
G. Gülmez, H., Tuncel, E., Angin, P.: A big data analytical approach to cloud intrusion detection. In: International Conference on Cloud Computing, pp. 377–388. Springer, New York (2018)
Nikolai, J., Wang, Y.: Hypervisor-based cloud intrusion detection system. In: 2014 International Conference on Computing, Networking and Communications (ICNC), pp. 989–993. IEEE (2014)
Cherkaoui, R., Zbakh, M., Braeken, A., Touhafi, A.: Performance analysis of intrusion detection systems in cloud-based systems. In: International Symposium on Ubiquitous Networking, pp. 206–213. Springer, New York (2017)
De la Hoz, E., De La Hoz, E., Ortiz, A., Ortega, J., Prieto, B.: PCA filtering and probabilistic SOM for network intrusion detection. Neurocomputing 164, 71–81 (2015)
Guo, C., Zhou, Y., Ping, Y., Zhang, Z., Liu, G., Yang, Y.: A distance sum-based hybrid method for intrusion detection. Appl. Intell. 40(1), 178–188 (2014)
Gaikwad, D., Thool, R.C.: Intrusion detection system using bagging with partial decision treebase classifier. Procedia Comput. Sci. 49, 92–98 (2015)
Ravale, U., Marathe, N., Padiya, P.: Feature selection based hybrid anomaly intrusion detection system using k means and RBF kernel function. Procedia Comput. Sci. 45, 428–435 (2015)
Mukherjee, S., Sharma, N.: Intrusion detection using Naive Bayes classifier with feature reduction. Procedia Technol. 4, 119–128 (2012)
Al-Yaseen, W.L., Othman, Z.A., Nazri, M.Z.A.: Multi-level hybrid support vector machine and extreme learning machine based on modified k-means for intrusion detection system. Expert Syst. Appl. 67, 296–303 (2017)
Mazraeh, S., Ghanavati, M., Neysi, S.H.N.: Intrusion detection system with decision tree and combine method algorithm. Int. Acad. J. Sci. Eng. 3(8), 21–31 (2016)
Kumar, N., Keserwani, P.K., Samaddar, S.G.: A comparative study of machine learning methods for generation of digital forensic validated data. In: 2017 Ninth International Conference on Advanced Computing (ICoAC), pp. 15–20. IEEE (2017)
Kuang, F., Zhang, S., Jin, Z., Xu, W.: A novel SVM by combining kernel principal component analysis and improved chaotic particle swarm optimization for intrusion detection. Soft. Comput. 19(5), 1187–1199 (2015)
Snapp, S., Brentano, J., Dias, G., Goan, T., Heberlein, L., Ho, C., Levitt, K., Mukherjee, B., Smaha, S., Grance, T.: et al.: Dids (distributed intrusion detection system)-motivation, architecture, and an early prototype. In: Proc. of the 14th National Computer Security Conference, Washington:[sn]
Hosseinpour, F., Ramadass, S., Meulenberg, A., Amoli, P.V., Moghaddasi, Z.: Distributed agent based model for intrusion detection system based on artificial immune system. Int. J. Digital Content Technol. Appl. 7(9), 206 (2013)
Seresht, N.A., Azmi, R.: MAIS-IDS: a distributed intrusion detection system using multi-agent AIS approach. Eng. Appl. Artif. Intell. 35, 286–298 (2014)
Wagh, S.K., Pachghare, V.K., Kolhe, S.R.: Survey on intrusion detection system using machine learning techniques. Int. J. Comput. Appl. 78(16), 30–37 (2013)
Qiu, C., Shan, J., Shandong, B., et al.: Research on intrusion detection algorithm based on BP neural network. Int. J. Secur. Appl. 9(4), 247–258 (2015)
Altwaijry, H.: Bayesian based intrusion detection system. In: IAENG Transactions on Engineering Technologies, pp. 29–44. Springer, New York (2013)
Gupta, M., Shrivastava, S.: Intrusion detection system based on SVM and bee colony. Int. J. Comput. Appl. 111(10)
Shrivas, A.K., Dewangan, A.K.: An ensemble model for classification of attacks with feature selection based on kdd99 and NSL-KDD data set. Int. J. Comput. Appl. 99(15), 8–13 (2014)
Chung, C.-J., Khatkar, P., Xing, T., Lee, J., Huang, D.: Nice: Network intrusion detection and countermeasure selection in virtual network systems. IEEE Trans. Dependable Secure Comput. 10(4), 198–211 (2013)
Bhat, A.H., Patra, S., Jena, D.: Machine learning approach for intrusion detection on cloud virtual machines. Int. J. Appl. Innov. Eng. Manag. 2(6), 56–66 (2013)
Sahi, A., Lai, D., Li, Y., Diykh, M.: An efficient DDOS TCP flood attack detection and prevention system in a cloud environment. IEEE Access 5, 6036–6048 (2017)
Girma, A., Garuba, M., Li, J., Liu, C.: Analysis of DDOS attacks and an introduction of a hybrid statistical model to detect DDOS attacks on cloud computing environment. In: 2015 12th International Conference on Information Technology-New Generations, pp. 212–217. IEEE (2015)
Patil, R., Dudeja, H., Modi, C.: Designing an efficient security framework for detecting intrusions in virtual network of cloud computing. Comput. Secur. 85, 402–422 (2019)
Sakr, M.M., Tawfeeq, M.A., El-Sisi, A.B.: Network intrusion detection system based PSO-SVM for cloud computing. Int. J. Comput. Netw. Inf. Secur. 11(3), 22 (2019)
Zong, W., Chow, Y.-W., Susilo, W.: Interactive three-dimensional visualization of network intrusion detection data for machine learning. Futur. Gener. Comput. Syst. 102, 292–306 (2020)
Prasad, K.M., Reddy, A.R.M., Rao, K.V.: Bartd: bio-inspired anomaly based real time detection of under rated app-DDOS attack on web. J. King Saud Univ.-Comput. Inf. Sci.
Geetha, T., Deepa, A.: A FKPCA-GWO wdbilstm classifier for intrusion detection system in cloud environments. Knowl.-Based Syst. 253, 109557 (2022)
Velliangiri, S., Premalatha, J.: Intrusion detection of distributed denial of service attack in cloud. Clust. Comput. 22(Suppl 5), 10615–10623 (2019)
Sethi, K., Kumar, R., Prajapati, N., Bera, P.: Deep reinforcement learning based intrusion detection system for cloud infrastructure. In: 2020 International Conference on COmmunication Systems & NETworkS (COMSNETS), pp. 1–6. IEEE (2020)
Rana, P., Batra, I., Malik, A., Imoize, A.L., Kim, Y., Pani, S.K., Goyal, N., Kumar, A., Rho, S.: Intrusion detection systems in cloud computing paradigm: analysis and overview. Complexity (2022)
Vashishtha, L.K., Singh, A.P., Chatterjee, K.: Hidm: a hybrid intrusion detection model for cloud based systems. Wirel. Pers. Commun. 1–30 (2022)
Kumar, C.O., Bhama, P.R.S.: Efficacious intrusion detection on cloud using improved bes and hybrid skinet-eknn. In: Emerging Research in Computing, Information, Communication and Applications: Proceedings of ERCICA 2022, pp. 61–72. Springer, New York (2022)
Hassan, M.M., Gumaei, A., Alsanad, A., Alrubaian, M., Fortino, G.: A hybrid deep learning model for efficient intrusion detection in big data environment. Inf. Sci. 513, 386–396 (2020)
Tian, Q., Li, J., Liu, H.: A method for guaranteeing wireless communication based on a combination of deep and shallow learning. IEEE Access 7, 38688–38695 (2019)
Khan, F.A., Gumaei, A., Derhab, A., Hussain, A.: A novel two-stage deep learning model for efficient network intrusion detection. IEEE Access 7, 30373–30385 (2019)
Kumar, V., Sinha, D., Das, A.K., Pandey, S.C., Goswami, R.T.: An integrated rule based intrusion detection system: analysis on unsw-nb15 data set and the real time online dataset. Clust. Comput. 1–22(2019)
Meftah, S., Rachidi, T., Assem, N.: Network based intrusion detection using the unsw-nb15 dataset. Int. J. Comput. Digital Syst. 8(5), 478–487 (2019)
Babaei, K., Chen, Z., Maul, T.: Data augmentation by autoencoders for unsupervised anomaly detection, arXiv preprint arXiv:1912.13384
Kumar, V., Das, A.K., Sinha, D.: Uids: a unified intrusion detection system for IoT environment. Evolut. Intell. 1–13 (2019)
Moustafa, N., Slay, J.: The evaluation of network anomaly detection systems: statistical analysis of the unsw-nb15 data set and the comparison with the kdd99 data set. Inf. Secur. J. 25(1–3), 18–31 (2016)
Papamartzivanos, D., Mármol, F.G., Kambourakis, G.: Dendron: genetic trees driven rule induction for network intrusion detection systems. Futur. Gener. Comput. Syst. 79, 558–574 (2018)
Nawir, M., Amir, A., Yaakob, N., Lynn, O.B.: Effective and efficient network anomaly detection system using machine learning algorithm. Bull. Electr. Eng. Inform. 8(1), 46–51 (2019)
Jain, M., Singh, V., Rani, A.: A novel nature-inspired algorithm for optimization: squirrel search algorithm. Swarm Evol. Comput. 44, 148–175 (2019)
Balamurugan, V., Saravanan, R.: Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Clust. Comput. 1–13 (2017)
Li, D.: Membership clouds and membership cloud generators. Comput. Res. Dev. 32(6), 15–20 (1995)
Bagui, S., Kalaimannan, E., Bagui, S., Nandi, D., Pinto, A.: Using machine learning techniques to identify rare cyber-attacks on the unsw-nb15 dataset. Secur. Priv. 2(6), e91 (2019)
Ren, J., Guo, J., Qian, W., Yuan, H., Hao, X., Jingjing, H.: Building an effective intrusion detection system by using hybrid data optimization based on machine learning algorithms. Secur. Commun. Netw. (2019)
Gao, J., Chai, S., Zhang, B., Xia, Y.: Research on network intrusion detection based on incremental extreme learning machine and adaptive principal component analysis. Energies 12(7), 1223 (2019)
Seiffert, C., Khoshgoftaar, T.M., Van Hulse, J., Napolitano, A.: Rusboost: a hybrid approach to alleviating class imbalance. IEEE Trans. Syst. Man Cybern. Part A 40(1), 185–197 (2009)
Jelonek, J., Krawiec, K., Stefanowski, J.: Comparative study of feature subset selection techniques for machine learning tasks. In: Proceedings of the 7th Workshop on Intelligent, Information Systems (1998)
Vladimir S, C., Mulier, F.: et al.: Learning from data: concepts, theory, and methods (2007)
Witten, I.H., Frank, E., Hall, M.A.: Practical Machine Learning Tools and Techniques, vol. 578. Morgan Kaufmann (2005)
Masamila, B.: State of mobile banking in tanzania and security issues
Bhamare, D., Salman, T., Samaka, M., Erbad, A., Jain, R.: Feasibility of supervised machine learning for cloud security. In: 2016 International Conference on Information Science and Security (ICISS), pp. 1–5. IEEE (2016)
Anwer, H.M., Farouk, M., Abdel-Hamid, A.: A framework for efficient network anomaly intrusion detection with features selection. In: 2018 9th International Conference on Information and Communication Systems (ICICS), pp. 157–162. IEEE (2018)
Nguyen, K.K., Hoang, D.T., Niyato, D., Wang, P., Nguyen, D., Dutkiewicz, E., Cyberattack detection in mobile cloud computing: a deep learning approach. In: IEEE Wireless Communications and Networking Conference (WCNC), pp. 1–6. IEEE (2018)
Saurabh, P., Verma, B.: An efficient proactive artificial immune system based anomaly detection and prevention system. Expert Syst. Appl. 60, 311–320 (2016)
Moustafa, N., Slay, J., Creech, G.: Novel geometric area analysis technique for anomaly detection using trapezoidal area estimation on large-scale networks. IEEE Trans. Big Data
Mogal, D.G., Ghungrad, S.R., Bhusare, B.B.: Nids using machine learning classifiers on unsw-nb15 and kddcup99 datasets. Int. J. Adv. Res. Comput. Commun. Eng. 6(4), 533–537 (2017)
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Contributions
NS: Writing- Original draft preparation, Conceptualization, Methodology. Dr. PKK: Supervision. Prof. MCG: Visualization Writing- Reviewing and Editing
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sarkar, N., Keserwani, P.K. & Govil, M.C. A better and fast cloud intrusion detection system using improved squirrel search algorithm and modified deep belief network. Cluster Comput 27, 1699–1718 (2024). https://doi.org/10.1007/s10586-023-04037-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-023-04037-3