Abstract
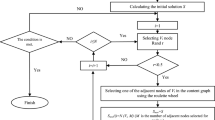
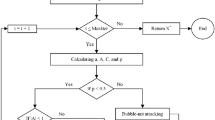
The dismantling and protection of networks is a significant problem that has wide-ranging applications and attracts many researchers. Most current studies only focus on single-layer or one-to-one interdependent networks. However, this paper considers the more realistic case where the links between layers in interdependent networks are one-to-many, and the networks’ robustness is studied accordingly. To solve the problem of dissolving interdependent networks under the premise of heterogeneous costs, we propose a cost-constrained elite quadratic evolutionary algorithm (CCEEA) based on cost constraints. Based on the network’s prior information, the initial optimal feasible solutions derived from four classical algorithms are regarded as the initial elite individuals of CCEEA. The set of attack nodes is then continuously updated interactively according to a new evolutionary mechanism with flexible updates so that the combination of nodes in the final set of attack nodes can maximally facilitate the disintegration of the network. We conducted experiments on a series of representative networks and showed that on synthetic networks, the CCEEA algorithm outperforms the other four state-of-the-art attack strategies by more than 13% in terms of disintegration, which is up to 25% higher. In particular, it can be up to more than 90% higher in real networks.










Similar content being viewed by others
Data Availability
The datasets generated and analyzed during the current study are available from the corresponding author on reasonable request.
References
McInnes BIA, McBride JS, Evans NJ, Lambert DD, Andrew AS (1999) Emergence of scaling in random networks
Watts DJ, Strogatz SH (1998) Collective dynamics of small-world networks. Nature 393:440–442
Kumar S, Panda AK (2021) Identifying influential nodes in weighted complex networks using an improved wvoterank approach. Appl Intell 52:1838–1852
Li CW, Chen HM, Li TR, Yang XL (2021) A stable community detection approach for complex network based on density peak clustering and label propagation. Appl Intell 52:1188–1208
Li XY, Zhang HK (2020) A multi-agent complex network algorithm for multi-objective optimization. Appl Intell 1–28
Chen ZH, Wu JJ, Xia YX, Zhang X (2018) Robustness of interdependent power grids and communication networks: A complex network perspective. IEEE Trans Circuits Syst II: Express Briefs 65:115–119
Majumder I, Dash PK, Dhar S (2021) Real-time energy management for pv-battery-wind based microgrid using on-line sequential kernel based robust random vector functional link network. Appl Soft Comput 101:107059
Liu QX, Wang B (2022) Neural extraction of multiscale essential structure for network dismantling. Neural Netw : Official J Int Neural Netw Soc 154:99–108
Liang YJ, Gao ZY, Gao JM, Wang RX, Liu QQ, Cheng YH (2020) A new method for multivariable nonlinear coupling relations analysis in complex electromechanical system. Appl Soft Comput 94:106457
Liu Q, Ding N, Li J, Yi XH (2022) Identification of critical nodes and accident chains of power systems under the effect of geomagnetic storms. Math Problems Eng
Mosetlhe TC, Hamam Y, Shengzhi D, Monacelli É (2022) Identification of critical nodes in water distribution networks. IOP Conference Series: Earth and Environmental Science 987
Bröhl T, Lehnertz K (2019) Centrality-based identification of important edges in complex networks. Chaos 29(3):033115
Wang LJ, Zheng SH, Wang YG, Wang LF (2021) Identification of critical nodes in multimodal transportation network. Phys A-statistical Mech Its Appl 580:126170
Purevsuren D, Cui G (2019) Efficient heuristic algorithm for identifying critical nodes in planar networks. Comput Oper Res 106:143–153
Summa MD, Faruk SMO (2022) Critical node/edge detection problems on trees. 4OR 21:439–455
Ma J, Ju Z (2019) Cascading failure model of scale-free networks for avoiding edge failure. Peer-to-Peer Netw Appl 12:1627–1637
Zhou DY, Hu FN, Wang SL, Chen J (2021) Power network robustness analysis based on electrical engineering and complex network theory. Phys A-statistical Mech Its Appl 564:125540
Musciotto F, Miccich’e S (2022) Exploring the landscape of community-based dismantling strategies
Li Q, Liu SY, Yang XS (2020) Neighborhood information-based probabilistic algorithm for network disintegration. arXiv:2003.04713
Paul S, Ding F, Utkarsh K, Liu W, O’Malley MJ, Barnett J (2022) On vulnerability and resilience of cyber-physical power systems: A review. IEEE Syst J 16:2367–2378
Lu KD, Wu ZY (2022) Genetic algorithm-based cumulative sum method for jamming attack detection of cyber-physical power systems. IEEE Trans Instrument Measure 71:1–10
Li X, Pan TY, Pan K (2023) Identification of key components after unintentional failures for cascading failure protection. IEEE Trans Netw Sci Eng 10:1003–1014
Feng XY, Shen T, Zhang HJ, Yang HP, Zhang L (2023) Multi-objective optimization of critical node detection based on both cascading and non-cascading scenarios in complex networks. In: 2023 IEEE Congress on evolutionary computation (CEC), pp 1–9
Li P, Wang SL, Chen GW, Bao CQ, Yan GH (2022) Identifying key nodes in complex networks based on local structural entropy and clustering coefficient. Math Problems Eng
Zhao Y, Yang CJ, Sun YH, Ren H, Cheng XY, Xie KG (2021) Reliability evaluation of cyber-physical power systems considering random failures in measurement and remote control. Electric Power Components Syst 49:532–546
Dong GG, Yao QY, Wang F, Du RJ, Vilela ALM, Stanley HE (2021) Percolation on coupled networks with multiple effective dependency links. Chaos 31(3):033152
Zhang HY, Peng MF, Guerrero JM, Gao XL, Liu YC (2019) Modelling and vulnerability analysis of cyber-physical power systems based on interdependent networks. Energies
Bai Y, Gong Y, Li Q, Song W, Aljmiai A, Liu S (2021) Nsksd: Interdependent network dismantling via nonlinear-metric. IEEE Trans Circuits Syst II: Express Briefs 69:1722–1726
Chen L, Gorbachev S, Yue D, Dou C-x, Li S, Ge H, Cheng Z (2022) Protection strategies of active defense in cyber-physical power systems. Europhys Lett 136
Chen L, Gorbachev S, Yue D, Dou CX, Li SQ, Ge H, Cheng ZH (2021) Protection strategies of active defense in cyber-physical power systems. Europhys Lett 136
Liu J (2020) Improving robustness of complex networks by a new capacity allocation strategy. Chinese Phys B 30
Zhang XK, Wu J, Wang H, Xiong J, Yang KW (2016) Optimization of disintegration strategy for multi-edges complex networks. In: 2016 IEEE Congress on evolutionary computation (CEC), pp 522–528
Patron A, Cohen R, Li D, Havlin S (2017) Optimal cost for strengthening or destroying a given network. Phys Rev E 95(5–1):052305
Holme P, Kim BJ, Yoon C, Han SK (2002) Attack vulnerability of complex networks. Phys Rev E, Stat, Nonlinear, Soft Matter Phys 65(5 Pt 2):056109
Callaway DS, Newman MEJ, Strogatz SH, Watts DJ (2000) Network robustness and fragility: percolation on random graphs. Phys Rev Lett 85(25):5468–71
Morone F, Makse HA (2015) Influence maximization in complex networks through optimal percolation. Nature 524:65–68
Wang JE, Liu SY, Aljmiai A, Bai YG (2021) Detection of influential nodes with multi-scale information. Chinese Phys B 30
Deng Y, Wu J, Xiao Y, Li YP (2018) Efficient disintegration strategies with cost constraint in complex networks: The crucial role of nodes near average degree. Chaos 28(6):061101
Felbermayr G, Groeschl J, Heiland I (2022) Complex europe: Quantifying the cost of disintegration. CEPR: International Trade & Regional Economics (Topic)
Cohen R, Erez K, ben-Avraham D, Havlin S (2001) Breakdown of the internet under intentional attack. Phys Rev Lett 86(16):3682–5
Barabási A (1999) Emergence of scaling in random networks. Science 286(5439):509–12
Barabasi AL (2009) Scale-free networks: A decade and beyond. Science 325:412–413
Erdos PL, Rényi A (1984) On the evolution of random graphs. Trans Am Math Soc 286:257–257
Asgari F, Sultan A, Xiong H, Gauthier V, El-Yacoubi MA (2016) Ct-mapper: Mapping sparse multimodal cellular trajectories using a multilayer transportation network. Comput Commun 95:69–81
Peña I, Martínez-Anido CB, Hodge B-MS (2018) An extended ieee 118-bus test system with high renewable penetration. IEEE Trans Power Syst 33:281–289
Yılmaz BG, Yımaz ÖF (2022) Lot streaming in hybrid flowshop scheduling problem by considering equal and consistent sublots under machine capability and limited waiting time constraint. Comput Indust Eng
Yılmaz ÖF, Durmusoglu MB (2019) A multi-objective scheduling of hybrid manufacturing systems with walking workers. Int J Indust Eng-theory Appl Practice 26
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant Nos. 61877046, 12271419, and 62106186), the Natural Science Basic Research Program of Shaanxi (Program No. 2022JQ-620), the Fundamental Research Funds for the Central Universities (Grant Nos. XJS220709, JB210701, and QTZX23002).
Author information
Authors and Affiliations
Contributions
Yonghui Li wrote the main manuscript text and Sanyang Liu was responsible for the algorithm design and Yiguang Bai guided the design of the algorithm and the entire process of improving and revising the manuscript. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Ethics approval
No participation of humans takes place in this implementation process. Human and animal rights No violation of Human and Animal Rights is involved.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Li, Yh., Liu, Sy. & Bai, Yg. Cost-constrained network dismantling using quadratic evolutionary algorithm for interdependent networks. Appl Intell 54, 2767–2782 (2024). https://doi.org/10.1007/s10489-024-05289-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-024-05289-1